| Oracle® Access Manager Installation Guide 10g (10.1.4.0.1) Part Number B25353-01 |
|
|
View PDF |
| Oracle® Access Manager Installation Guide 10g (10.1.4.0.1) Part Number B25353-01 |
|
|
View PDF |
Oracle Access Manager supports the Microsoft Active Directory Application Mode (ADAM) as a standalone directory server. This chapter includes the following discussions:
Upgrading to Oracle Access Manager 10g (10.1.4.0.1) is explained in the Oracle Access Manager Upgrade Guide.
This discussion introduces ADAM in general terms and provides details about using ADAM as a directory server for Oracle Access Manager. Differences between ADAM and Active Directory are also discussed.
|
Note: Oracle Access Manager supports storing user data on a separate type of directory server and storing Oracle Access Manager configuration and policy data on one or more instances of ADAM. This means that, for example, you may store user data on Active Directory and configuration and policy data on ADAM. Configuration and policy data must be stored on the same directory server type. |
Whether you install Oracle Access Manager on a single machine with ADAM or in a distributed environment, as shown in Figure B-1, Oracle Access Manager supports ADAM as a standalone directory server.
Figure B-1 ADAM as a Standalone Directory Server for Oracle Access Manager
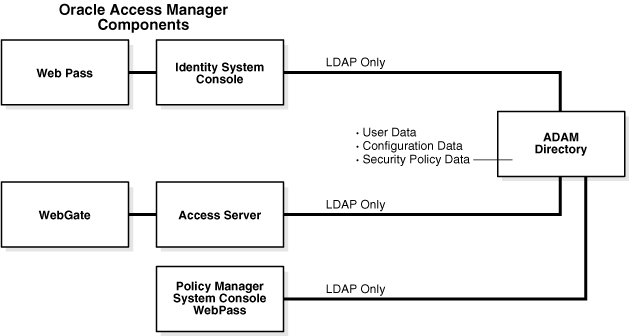
ADAM uses the same storage management and the same programming model as the .NET Active Directory. In addition, ADAM provides a similar replication and administration model as Active Directory. However, ADAM is independent of Active Directory and Active Directory domains and forests. ADAM does not include Active Directory infrastructure features, does not include directory services for the Windows operating system, and does not require a domain controller. ADAM runs as an independent service, not an operating system service.
ADAM typically provides dedicated directory services for applications, including a data store and services to access the data store. For example, ADAM can provide an application-specific directory store for a small business unit. The information in ADAM may require specific local schema changes, may be relevant to only a small group of users, and may not require wide distribution.
During installation of each unique ADAM instance, you specify a name and port for the instance. The name ties the files, service, registry, and ports together. Ports may be configured for LDAP and SSL. An open LDAP port is required to extend the ADAM schema with Oracle Access Manager-related information. There have been no changes to the Oracle Access Manager schema for ADAM.
For more information, see:
During installation of a unique ADAM instance, a schema directory partition (SDP) and configuration directory partition (CDP) are created. With ADAM, there is no domain partition. Each unique instance can be configured independently and may include multiple application directory partitions (ADPs) created either during ADAM installation and setup or later.
|
Important: Be sure to create your application directory partitions within ADAM before installing Oracle Access Manager. Oracle Access Manager does not create an ADP within ADAM. |
ADAM ADPs are similar to Active Directory ADPs. Each ADAM ADP contains the data (objects) for an ADAM instance. However, ADAM ADPs cannot store a security principal (an account holder that is automatically assigned a security identifier (SID) to control access to resources). Applications and services can use ADAM ADPs to store application-specific data, which may contain highly volatile information with high replication requirements that could strain resources if stored in your Network Operating System (NOS) directory.
Originally Oracle Access Manager supported a single ADP within a single ADAM instance. As shown in Figure B-2, an ADP can include application-specific data as well as the user tree, the Oracle Access Manager configuration tree, and the Oracle Access Manager policy tree.
Figure B-2 Single ADAM Instance and Partitions
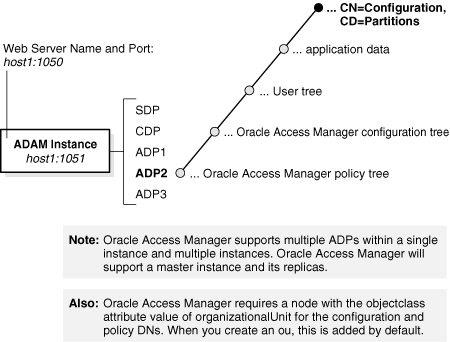
ADAM, like Active Directory on Windows Server 2003 platforms, supports dynamically-linked auxiliary classes. Oracle Access Manager supports both dynamically-linked and statically-linked auxiliary classes.
The ADAM schema contains definitions of the object classes that ADAM can access within a configuration set. The schema also includes definitions of the attributes that ADAM can access in an ADAM object. For more information about configuration sets, see "Replication of an ADAM Instance".
The ADAM schema is flexible. There are no namespace restrictions. ADAM can use X.500-style naming contexts (o=,c=) for various types of information (schema, sites, partitions, and services). Within the ADP, the user searchbase, configuration DN, and policy base may be the same (o=company,c=us) or may differ.
|
Note: Oracle Access Manager requires a node with the objectclass attribute value of organizationalUnit (ou) for the configuration and policy DNs. When you create an ou, this is added by default. |
An example of different name spaces is shown:
|
Note: When storing user data on a separate type of directory server and Oracle Access Manager configuration and policy data on one or more ADPs or one or more ADAM instances, different name spaces are required. |
While the ADAM schema is similar to the Active Directory schema, the user object class is described differently in ADAM than in Active Directory. There is no security principal attached to ADAM. For example, saMAccountName is mandatory with Active Directory for user and group but does not exist in ADAM. However, grouptype is still required.
The grouptype attribute in the ADAM group object class "group" can have only the following values, which should be configured in the meta-attribute configuration applet (Identity System Console, Group Manager, Configure Tab, Modify Attributes) for the object class with a Display Type of radio button:
In Active Directory, the password attribute is unicodePwd. The password attribute on ADAM is userpassword. The uid attribute is assigned the Semantic Type "Login" by default.
The Active Directory Application Mode (ADAM) schema is extensible using the Ldifde.exe command-line tool.
The Oracle Access Manager schema extension for ADAM must be loaded using a Windows Security Principal credential. At runtime, however, Oracle Access Manager communicates only with users within ADAM, not with security principals. For more information, see "Windows Users and Security Principals".
When you install Oracle Access Manager, you must manually update the ADAM schema. If the user data directory instance is separate from the configuration and policy data directory instance, you must manually upload the ADAM_user_schema_add.ldif file.
On the configuration data directory instance, you must manually upload the ADAM_oblix_schema_add.ldif file. When using static auxiliary classes, you must manually upload the ADAMAuxSchema.ldif file.
If the policy data directory instance is separate from the configuration data directory instance, you must manually upload the ADAM_oblix_schema_add.ldif file. When using static auxiliary classes, you must manually upload the ADAMAuxSchema.ldif file.
Oracle Access Manager supports both InetOrgperson and GroupofUniqueNames as standard Person and Group object classes, respectively, in addition to user and group. You may have an object class already in use and do not need to use a specific object class. Oracle Access Manager also supports both statically-linked and dynamically-linked auxiliary classes
The ADAM schema cannot be modified with a simple LDAP bind and must be modified using ldifde, not ldapmodify. Currently, ldifde does not support binding to an SSL port on ADAM; therefore, the ADAM schema may be extended for Oracle Access Manager only on an open port. During Identity Server installation, you can specify an SSL connection and obtain the SSL certificate for ADAM, then specify an open port number for the schema update.
|
Note: With ADAM the schema update must be completed using an open port and a Windows security principal credential. |
Oracle Access Manager provides the following schema files for Oracle Access Manager configuration and user directories. To update the schema manually, you must use the following files:
In addition, if you are using statically-linked auxiliary classes, you also need to run the ldifde command with the following file:
A sample ldifde command to manually update the schema follows and is also described in Table B-1. For more information, see your Microsoft documentation:
Table B-1 ldifde Command Description for ADAM
| Option | Description |
|---|---|
|
-k |
This option ignores errors. |
|
-b "<user_distinguished_name>" "<domain_name>" "<user_password>For example:cn=administrator,o=oblix.com,c=us password |
To extend the schema, the values represent: |
|
-c "<GUID>" <ADAM_instance_ID> |
In this option, "<GUID>" should be retained as is, not replaced by any value; do include the quotes. <ADAM_instance_ID> should be substituted by the ADAM root DSE using tools like ldp.exe. When the initial connection is made, the root DSE is shown. For example, an ADAM root DSE value may be EC31B31B-19FC-4FD4-8590-3BD57D6A3E77. |
|
-i -f <filename> |
The -i option specifies the import option.The -f option identifies a file name; the value identifies the file you are importing. For example: ADAM_oblix_schema_add.ldifADAMAuxSchema.ldif |
|
-s <ADAM_server_name> |
This value is the name of the machine where ADAM is installed. |
|
-t <port > |
This value is the port number on which this instance listens for the schema update (an open port is needed). |
ADAM supports user credentials and uses Windows security principal credentials for authentication and access control. For example, the Windows security principal provides the rights to define users and replicate an instance of the ADAM directory store. However, Oracle Access Manager requires Windows security principal credentials only to update the ADAM schema.
Windows Security Principal for Schema Updates: When you install the Oracle Access Manager Identity Server with ADAM and update the schema, you must supply directory server details as follows:
Automatic Schema Updates: Not available. You must manually update the schema.
Manual Schema Updates: When you manually extend the schema, you must supply the Windows security principal name and password with the ldifde command as discussed in "The Oracle Access Manager Schema Extension for ADAM". For example:
-b "<user_distinguished_name>""<domain_name>""<user_password>"
Windows User within ADAM for Root (Bind) DN: At runtime, Oracle Access Manager communicates only with users within ADAM, not with a Windows security principal. During Identity System setup you must specify the Root (bind) DN for ADAM and password for that user on the page where you specify Directory Server with User Data Configuration. This must be the name of a bindable user within ADAM with administrator privileges:
You create a bindable user in ADAM by adding the ms-bindable-object auxiliary object class to the object class you are using for people objects, inetOrgPerson, for example.
The Oracle Access Manager Administrator must be a bindable user in ADAM with administrative privileges, not a Windows Security Principal.
When you setup Oracle Access Manager, individual directory profiles are created for the Identity Server, Policy Manager, and Access Server, as usual. During Identity System setup, you specify the SSL-enabled port to properly configure the directory profile within Oracle Access Manager.
For details about configuring directory profiles after Oracle Access Manager installation, see the Oracle Access Manager Identity and Common Administration Guide.
Replication of an ADAM instance creates a configuration set. All ADAM instances within a configuration set replicate a common schema partition and configuration partition, and can also replicate ADPs such as o=company,c=US. Only complete replicas are supported by Oracle Access Manager.
Oracle Access Manager will provide failover and load balancing between a master instance and its replicas; however, Oracle Access Manager does not support ADSI with ADAM. For more information, see "ADSI with Oracle Access Manager and ADAM".
Typically, multiple instances of ADAM may run concurrently on a single server, each with its own schema and configuration.
|
Note: You cannot replicate ADAM instances across the forest. In a production environment, ADAM instances within the same configuration set cannot reside on the same machine. See your Microsoft documentation for more information. |
ADSI provides failover support in Active Directory environments and Oracle Access Manager supports ADSI with Active Directory. ADAM supports Active Directory Service Interfaces (ADSI). However, Oracle Access Manager does not support ADSI with ADAM.
With ADAM there is no domain controller, therefore, the native Oracle Access Manager directory server failover and connection management toolkits are recommended. For details about configuring failover and load balancing, see the Oracle Access Manager Deployment Guide.
ADAM uses standard application programming interfaces (APIs) to access application data. These include Active Directory APIs, Lightweight Data Access Protocol, and System-Directory Services.
ADAM does not support the Messaging Application Programming Interface (API). Therefore, Microsoft Exchange cannot use ADAM. For more information, see your Microsoft documentation.
Authentication and authorization processes should be managed in Oracle Access Manager, rather than in ADAM. This will avoid contentions between Oracle Access Manager "rules" and ADAM "rules" regarding authentication and authorization. Oracle Access Manager authentication and authorization processes are the same whether you are using ADAM or Active Directory. For more information, see the Oracle Access Manager Identity and Common Administration Guide.
With Oracle Access Manager, ADAM cannot use proxy objects that point to Active Directory. Users must be enabled within ADAM and must have a password.
With Active Directory and Oracle Access Manager, you can use native password management or Oracle Access Manager. Password management is available with ADAM. Both Active Directory and ADAM support changing passwords over a secure connection, either SSL or ADSI. However, Oracle Access Manager does not support ADSI with ADAM, therefore, SSL must be used for password changes with ADAM.
Differences between ADAM and Active Directory are summarized in the following table:
Table B-2 Differences between ADAM and Active Directory with Oracle Access Manager
| Description |
|---|
|
ADAM and Active Directory can operate concurrently in the same network; Oracle Access Manager supports the use of both independently and together. |
|
The information in ADAM may require specific local schema changes, may be relevant to only a small group of users, and may not require wide distribution. |
|
Applications and services can use ADAM ADPs to store application-specific data, which may contain highly volatile information with high replication requirements. |
|
There is no security principal attached to ADAM. For example, saMAccountName is mandatory with Active Directory for user and group but does not exist in ADAM. |
|
The password attribute on ADAM is userpassword. |
|
Oracle Access Manager requires Windows security principal credentials to update the ADAM schema. At runtime, Oracle Access Manager communicates only with users within ADAM, not with security principals. |
|
Both Active Directory and ADAM support ADSI. However, Oracle Access Manager supports ADSI only with Active Directory. An implicit bind is available only with Active Directory, not ADAM. |
|
Both Active Directory and ADAM support changing passwords. Oracle Access Manager with ADAM requires an SSL-enabled port for password changes. |
For more information about ADAM, see your Microsoft documentation.
ADAM and Active Directory can operate concurrently within the same network. Oracle Access Manager supports the use of ADAM alone. In addition, Oracle Access Manager supports ADAM with Active Directory and ADAM with other directory server types for storing user data separately from configuration and policy data:
All user data must be stored on the same directory server type.
Configuration and policy data must be stored on the same type of directory server.
Oracle Access Manager requires a node with the objectclass attribute value of organizationalUnit (ou) for the configuration and policy DNs.
For LDAP support with Oracle Access Manager 10g (10.1.4.0.1), see the Certify tab at https://metalink.oracle.com.
The schema update must be performed manually using the ldifde command. For more information, see "The Oracle Access Manager Schema Extension for ADAM".
The following tasks are included in the installation procedures:
Task overview: Installing Oracle Access Manager with ADAM
Prepare your environment, as described in Part I, "Installation Planning and Prerequisites".
Prepare ADAM, as described in "Preparing ADAM for Oracle Access Manager".
|
Note: Oracle Access Manager requires a node with the objectclass attribute value of organizationalUnit (ou) for the configuration and policy DNs. |
Install and setup the Identity System, as described in "Installing and Setting the Identity System with ADAM".
Install and setup the Access System, if this is part of your environment, as described in "Installing the Access System with ADAM".
Complete any of the following activities after successful Oracle Access Manager installation and setup:
Add ADAM users to Oracle Access Manager, as described in the Oracle Access Manager Identity and Common Administration Guide.
Replicate an ADAM instance, as described in your Microsoft documentation.
Configure failover and load balancing, for the ADAM master and replicas, as described in the Oracle Access Manager Deployment Guide.
The steps that follow outline how to prepare your ADAM instance and ADP so that Oracle Access Manager can manage authentication and authorization. You will install a unique ADAM instance, create an ADP and a top DN for user data, and create users in ADAM. Remember the following important points:
ADPs: You must create the application directory partition within ADAM. Oracle Access Manager does not create the ADP.
Administrators: At least one account should be designated as the ADAM instance administrator. An ADAM instance administrator should also be designated as a Master Administrator during Identity System setup. The Master Administrator must be a bindable user in ADAM with administrative privileges, not a Windows Security Principal.
Configuration and Policy DNs: Oracle Access Manager requires a node with the objectclass attribute value of organizationalUnit (ou) for the configuration and policy DNs.
ADSI: Oracle Access Manager does not support ADSI with ADAM. You will need to use native Oracle Access Manager directory server failover and connection management toolkits with ADAM.
Binding through Proxy Objects: Oracle Access Manager does not support binding through an ADAM proxy object.
|
Note: Failure to complete the following steps may result in an unsuccessful installation with Oracle Access Manager. For complete details about installing ADAM, setting up the instance, and other tasks, as well as details about tools such as ADAM ADSI Edit and Ldp.exe, see the Microsoft documentation that accompanies your ADAM download. |
To install ADAM for Oracle Access Manager
Familiarize yourself with ADAM concepts, practices, and tools, as described in the Microsoft documentation that accompanies your ADAM download.
Install a unique ADAM instance on a machine with Windows Server 2003 by running ADAMSetup.exe from the ADAM installation directory.
The installation program will prompt you with the following screens:
A unique instance
A valid Instance name (for example, OracleAccessManager)
Port number where you want this instance to run.
Creation of application directory partition. (Yes/No).
* Yes to create a new partition For example, o=company, c=us, (Default)
* No will refer it to an already existing partition.
Directory to install ADAM.
Service Account selection (Select an account you would like to use for further processing).
* Network Service Account (Default)
* Custom Account (Make sure this account is active)
Assign Permissions to the selected account
Import user LDIF file (for example, MS_User.ldf)
Be sure to:
Specify an open LDAP port number to extend the ADAM schema for Oracle Access Manager, and an SSL-enabled port for password changes, authentication, and authorization with Oracle Access Manager.
Create an Application Directory Partition (naming context) to contain user data and Oracle Access Manager configuration and policy data by specifying any distinguished name that does not already exist within the instance--or to contain configuration and policy data while storing user data on another directory server type.
Start the ADAM instance.
For example: Start, Programs, ADAM, ADAM ADSI EDIT
Right-click ADAM ADSI EDIT then select Connect to from the menu.
A user screen appears with the following options:
Connection Name: For example, OAM
Host Name: Local Host
Port: Port number of the instance you have created
DN: The bind DN
Credentials
|
Note: The ms-bindable-object should be added to ADAM. For more information, see "Windows Users and Security Principals". |
Create and enable a bindable ADAM user account and use ADAM ADSI Edit to add the user you want to designate as the Master Administrator to the member attribute of the following:
CN=Administrators,CN=Roles,CN=Configuration,CN={your GUID}
Reset the user password.
Activate the user.
Manage directory partitions in the ADAM instance.
Manage ADAM configuration sets.
Ensure that your ADAM installation is operating properly before you continue.
Procedures in this discussion presume that you have completed all steps in "Preparing ADAM for Oracle Access Manager". Following are several important items to review before you begin:
Schema Update: The ADAM schema update for Oracle Access Manager must be completed using an open port. For more information, see "The Oracle Access Manager Schema Extension for ADAM".
The schema update must be completed with a Windows security principal credential. However, the root (bind) DN you specify during Identity System setup must be a user with an explicit physical location within ADAM. For more information, see "Windows Users and Security Principals".
Identity System Setup: During Identity System setup, an SSL-enabled connection should be specified for password changes. For more information, see "Authentication, Authorization, and Password Changes".
Administrators: The Master Administrator you designate during Identity System setup must be an ADAM user with administrative privileges, not a Windows Security Principal.
The steps that follow provide specific information for Oracle Access Manager and ADAM. For additional information about installing each Oracle Access Manager component, see chapters elsewhere in this guide.
To install the Identity Server and update the ADAM schema
Start the installation by selecting the Identity Server installation package that you downloaded.
Supply your installation directory, transport security mode, and Identity Server configuration details for Oracle Access Manager.
Select Yes to use SSL between the Identity Server and ADAM (required for password changes) then respond to all questions about certificates. Later you may specify an open port to extend the ADAM schema for Oracle Access Manager.
Supply the following details for ADAM:
Directory Server Type: Select Active Directory Application Mode from the Directory Server drop-down list to specify ADAM.
Data Location: Identity whether configuration data and user data are stored separately.
Schema Update: Review the instructions to manually update the schema when these appear.
You continue the installation process, then update the schema as described in steps 6 and 7.
Finish the installation and start the Identity Server, as described in the "To install the Identity Server and update the ADAM schema".
Manual Schema Update Preparation: Modify the following files to replace <guid> with {your GUID} before you run a manual schema update using step 7:
ADAM_oblix_schema_add.ldif
ADAM_oblix_user_schema_add.ldif
ADAMAuxSchema_add.ldif
Manual Schema Updates: Update the schema manually as a domain user if needed, using the appropriate file and ldifde command, then restart the Identity Server. For example:
IdentityServer_install_dir\identity\oblix\data.ldap\common\
ldifde -k -b <cn=administrator,o=company,c=us password> -c"<GUID>" <ADAM_instance_ID> -i -f ADAM_oblix_schema_add.ldif -s <ADAM_server_name> -t <port> ldifde -k -b <cn=administrator,o=company,c=us password> -c"<GUID>" <ADAM_instance_ID -i -f ADAM_oblix_user_schema_add.ldif -s ADAM_server_name -t <port>
|
Note: The Windows security principal name and domain in the preceding example are samples only. Your environment will differ. |
After executing the preceding command, if you do not plan to use dynamic auxiliary classes:
Use the ldifde command to import the Oracle Access Manager schema file ADAMAuxSchema.ldif for statically-linked auxiliary classes from the IdentityServer_install_dir\identity\oblix\data.ldap\common directory.
Ensure that the object classes "oblixorgperson" and "oblixgroup" are explicitly attached as auxiliary classes to the Person and Group object classes, respectively.
|
Note: Be sure to restart the Identity Server after updating the schema manually. |
The steps that follow summarize the information you need to supply when you install the WebPass and set up the Identity System with ADAM.
To install WebPass and set up the Identity System
Install the WebPass your downloaded, as described in "To install WebPass and set up the Identity System".
Start the Identity System setup, as described in the "Installing and Setting the Identity System with ADAM", then specify the following details for ADAM:
Directory Server Type: Select Microsoft Active Directory Application Mode when you specify a directory server type, and select Dynamic Auxiliary Object Class if appropriate for your environment.
Location of Directory Server: Specify the following for ADAM:
Port Number: Specify the port to be used during runtime (SSL is required for password changes).
Root DN: The name of a bindable user in ADAM with administrator privileges as the bind DN; do not specify a Windows security principal.
Root Password: Password for the bindable user in ADAM
Directory Server Security Mode: Specify SSL for password changes.
Finish setting up the Identity System, as usual.
Continue with any of the following activities when Identity System setup is finished:
Install the Access System with ADAM, if this is included in your environment, as described in "Installing the Access System with ADAM".
Add ADAM users to Oracle Access Manager, as described in the Oracle Access Manager Identity and Common Administration Guide.
Replicate an ADAM instance, as described in your Microsoft documentation.
Configure failover and load balancing, for the ADAM master and replicas, as described in the Oracle Access Manager Deployment Guide.
The Access System, which is optional, includes the Policy Manager, Access Server, and WebGate. The steps that follow provide specific details to install and setup the optional Access System with ADAM.
For details, see the following procedures:
With ADAM, policy data may be stored with user and Oracle Access Manager configuration data. Alternatively, Oracle Access Manager supports separate ADAM instances for configuration, user and policy data.
To install the Policy Manager with ADAM
Locate and launch the Policy Manager installation and specify your installation directory, as described in "To install the Policy Manager with ADAM" .
Select Microsoft Active Directory Application Mode when asked for the directory server type.
Select Yes if dynamically-linked auxiliary object classes are enabled in your environment, otherwise select No.
Manually update the schema after installation.
|
Note: Automatic schema updates are not supported. |
Specify the directory server security mode: SSL-enabled is required for password change with ADAM.
Specify a transport security mode for the Access System, configure your Web server, and complete the Policy Manager installation, as described in the "To install the Policy Manager with ADAM".
Continue with the next procedure to set up the Policy Manager.
To set up the Policy Manager with ADAM
Start the Policy Manager setup process, as described in "To install the Policy Manager with ADAM" , and specify the following details for ADAM:
Directory Server Type: Select Microsoft Active Directory Application Mode when you specify a directory server type, and select Dynamic Auxiliary Object Class if this is appropriate for your environment.
Directory Server Details: Specify the following for ADAM:
Port Number: Specify the port to be used during runtime (SSL is required for password changes).
Root (bind) DN: Specify the Root DN you provided when setting up the Identity Server; do not use a Windows security principal.
Password: Specify the password of the bind DN user.
Directory Server Security Mode: Specify SSL for password changes.
Specify the searchbase, configuration DN, and policy base for ADAM, see "The ADAM Schema" for details.
Complete the Policy Manager setup process, as described in "To set up the Policy Manager with ADAM".
|
Note: A warning may appear at the end of this setup instructing you to create the Anonymous user before enabling Oracle Access Manager policies. |
Ensure that the OblixAnonymous user has been created within ADAM at the top of the searchbase you specified during Policy Manager setup.
Continue with the next procedure to install the Access Server.
To install the Access Server
Create an Access Server instance in the Access System Console, as described in "Creating an Access Server Instance" on page 191.
Locate and launch the Access Server installation package and specify your installation directory, as described in "To install the Access Server".
Select the transport security mode for the Access Server.
Specify ADAM details when asked.
SSL: SSL is required for password changes.
Port Number: The directory server port to be used during runtime.
Bind (root) DN: The Root DN you provided when setting up the Identity Server and Policy Manager; do not use a Windows security principal.
Password: The password for the bind DN.
Directory Server Type: Active Directory Application Mode.
Select Yes if dynamically-linked auxiliary classes are enabled in your environment, otherwise select No.
Provide the path to the directory server's certificate file.
Specify the Access Server ID and the configuration DN and policy base, which may be unique within the ADP. For example:
Access Server ID: Access_Server_1014_A
Configuration DN: ou=config,o=company,c=us
Policy base: ou=policy,o=company,c=us
|
Note: The preceding example presumes you are storing all data within a single ADAM instance and ADP. |
Finish Access Server installation, as described in "Finishing the Access Server Installation" on page 197.
Continue with the next procedure to install the WebGate.
To install the WebGate
Create a WebGate instance in the Access System Console, as described in "To install the WebGate".
Associate the WebGate with the Access Server, as described in "Associating a WebGate and Access Server" on page 207.
Install the WebGate, as described in "To install the WebGate".
Complete any of the following activities when the Access System installation and setup is finished:
Add ADAM users to Oracle Access Manager, as described in the Oracle Access Manager Identity and Common Administration Guide.
Replicate an ADAM instance, as described in your Microsoft documentation.
Configure failover and load balancing, for the ADAM master and replicas, as described in the Oracle Access Manager Deployment Guide.
Several parameter changes have been made in the Oracle Access Manager silent mode installer to support ADAM as a standalone directory server. For details, see:
|
Note: The dynamic-auxiliary flag can be configured for ADAM in Oracle Access Manager as it is for Active Directory on Windows 2003. |
The following changes have been made for ADAM in the Identity Server silent installer:
Windows User Name and Windows Domain: Specify a Windows security principal name, Windows domain name, and password to update the ADAM schema; this will not be used as a bind DN.
Schema Update, Automatic: Not supported for ADAM.
Schema Update, Manual: To specify a manual schema update when installing the first Identity Server on Windows Server 2003, use:
-W updateDSInfo.updateDSInfoChoice="No"
Where:
-W updateDSInfo.updateDSInfoChoice="No" specifies a manual schema update.
Windows Domain Name for ADAM—To specify a Windows domain name for ADAM use:
-W dsInfoInput.domainName="domainname.com
Where:
-W dsInfoInput.domainName specifies the Windows Domain Name for ADAM when -W dsTypeInput.dsType=9 (ADAM).
"domainname.com" is the domain name in which the ADAM machine resides. If an incorrect domain name is given, the authentication to the directory will fail.
|
Note: This is a new parameter and does not alter or replace an existing silent installer parameter. |
To specify ADAM as the directory server type during Policy Manager installation use the following:
-W dsTypeInput.dsType="9"
Where:
-W dsTypeInput.dsType specifies the directory server type where policy data is stored.
The following types are supported:
2 - Sun 5.x
3 - NDS
5 - Active Directory
7 - Active Directory (Windows Server 2003)
9 - Active Directory Application Mode
Later select Dynamic Auxiliary Object Class if this is appropriate for your environment. For ADAM, the option -W updateDSInfo.updateDSInfoChoice is not applicable. Otherwise, use -W updateDSInfo.updateDSInfoChoice = "Yes" to specify the Policy directory server type.
To specify ADAM as the directory server type during Access Server installation use:
-W oblixDSInfoBean.dsType="MSADAM"
Where:
-W oblixDSInfoBean.dsType specifies the Configuration directory server type.
"MSADAM" stands for Microsoft Active Directory Application Mode
For information, see "ADAM Issues".