| Oracle® Identity Manager Design Console Guide Release 9.0 B25940-01 |
|
 Previous |
 Next |
| Oracle® Identity Manager Design Console Guide Release 9.0 B25940-01 |
|
 Previous |
 Next |
This chapter describes the administration of Oracle Identity Manager (Xellerate). It contains the following topics:
The Oracle Identity Manager (Xellerate) Administration folder provides System Administrators with the tools necessary to manage Oracle Identity Manager administrative features. This folder contains the following forms:
Form Information: This form is used to specify the class name, form label, form type, menu item, graphic icon, and online Help topic to be associated with a given Oracle Identity Manager form. You can also use this form to modify the folders and folder items that appear within the Oracle Identity Manager Explorer.
Lookup Definition: This form is used to create and manage lookup definitions. A lookup definition represents a lookup field and the values that are accessible from that lookup field.
User Defined Field Definition: This form is used to create and manage user-defined fields. A user-defined field allows you to store additional information for Oracle Identity Manager forms.
System Configuration: This form is used to define and set the value of properties that control the behavior of the Client and/or Server. In addition, you may specify the users and/or user groups to which the value of a property setting applies. Alternately, you may specify that the value of a property setting apply to all users.
Remote Manager: This form displays information about the servers that Oracle Identity Manager uses to communicate with third-party programs. These servers are known as remote managers.
Task Scheduler: This form is used to set up the schedules that will determine when scheduled tasks are to be run.
The Form Information form, as shown in Figure 8-1, is located in the Oracle Identity Manager Administration folder. It is used to specify the class name, label (that appears in the Oracle Identity Manager Explorer), form type, graphic icon, and help context to be associated with a given Oracle Identity Manager form. You can also use this form to modify the folders and folder items that appear within the Oracle Identity Manager Explorer.
The following table describes the data fields of this form.
To add an Oracle Identity Manager form or folder, perform the following steps:
Access the Form Information form.
Enter the name of the class that will be used to render the form in the Class Name field.
Enter the label you wish to be displayed for the form or folder in the Oracle Identity Manager Explorer in the Description field.
|
Note: For forms of childform type, this value must include the name of the parent form and adhere to the following naming convention: <parent_form_name>.<child_form_name>. |
Select the desired item from the Type combo box.
For folders, select folder.
For forms related to export procedures, select export.
For forms related to a process, select processform.
For tabs that appear within other forms, or for forms that are nested within other forms, select childform.
For general forms, select javaform.
For forms related to import procedures, select import.
For menu items associated with the Oracle Identity Manager Administrative and User Console, select menuitem.
|
Note: For more information on the Oracle Identity Manager Web Guide, refer to Oracle Identity Manager Administrative and User Console Guide. |
Enter the name of the icon or graphic image file to be used within the Oracle Identity Manager Explorer for the form or folder in the Graphic Filename field.
Enter the URL of the online Help topic for the form in the Context Sensitive Help URL field. This will be the file displayed if the user presses F1 when the form is active.
Click Save. The form is added. In addition, a system-generated ID for the form or folder appears within the Key field.
The Oracle Identity Manager Explorer and layout of its folders and folder items can be modified based on different user group levels.
|
Note: Click the plus sign (+) to expand a folder, and show folder items, or click the minus sign (-) to hide folder items. |
The folders and folder items that a user can access are based on the user groups of which the user is a member. For example, suppose the IT DEPARTMENT user group can open the System Configuration form, and the HR DEPARTMENT user group is able to launch the Lookup Definition form. If a user belongs to both user groups, he or she can access the System Configuration form and the Lookup Definition form.
The Lookup Definition form, as shown in Figure 8-2, is located within the Oracle Identity Manager Administration folder. It is used to create and manage lookup definitions.
A lookup definition represents:
The name and description of a text field;
A lookup field and the values that are accessible from that lookup field (by double-clicking it); or;
A combo box, and the commands that can be selected from that combo box.
These items, which contain information pertaining to the text field, lookup field, or combo box, are known as lookup values.
Users can access lookup definitions from one of two locations:
A form or tab that comes packaged with Oracle Identity Manager; or
A user-created form or tab (built using the Form Designer form).
The following table describes the data fields of the Lookup Definition form.
| Field Name | Description |
|---|---|
| Code | The name of the lookup definition. |
| Field | The name of the table column of the form or tab from which the text field, lookup field, or combo box field will be accessible. |
| Lookup Type/Field Type | These radio buttons are used to designate whether the lookup definition is to represent a text field, a lookup field, or a combo box.
By selecting the Field Type radio button, the lookup definition will represent a text field. If you select the Lookup Type radio button, the lookup definition is to represent either a lookup field or a combo box, along with the values that are to be accessible from that lookup field or combo box. Note: For forms or tabs that come packaged with Oracle Identity Manager, the lookup definition has already been set as either a lookup field or a combo box. This cannot be changed. However, you can add or modify the values that are accessible from the lookup field or combo box. For forms or tabs that are user-defined, the user determines whether the lookup definition will represent a lookup field or a combo box through the Additional Columns tab of the Form Designer form. For more information on specifying the data type of a lookup definition, refer to "Additional Columns". |
| Required | By selecting this check box, the lookup definition is designated as required. As a result, Oracle Identity Manager will not allow the contents of the corresponding form or tab to be saved to the database until the field or combo box, represented by the lookup definition, is supplied with data. |
| Group | The name of the Oracle Identity Manager or user-defined form on which the lookup definition is to appear. |
Now that we have reviewed the data fields of this form, you will learn how to create a lookup definition.
To create a lookup definition, perform the following steps:
Open the Lookup Definition form.
In the Code field, enter the name of the lookup definition.
In the Field field, enter the name of the table column of the Oracle Identity Manager or user-created form or tab, from which the text field, lookup field, or combo box field will be accessible.
If the lookup definition is to represent a lookup field or combo box, select the Lookup Type radio button.
|
Note: For more information on specifying whether the lookup definition will represent a lookup field or a combo box, refer to the table that appears earlier in this section. |
If the lookup definition is to represent a text field, select the Field Type radio button.
Optional. If you want to set Oracle Identity Manager to save the contents of the corresponding form or tab to the database only when the field or combo box, represented by the lookup definition, is supplied with data, select the Required check box. Otherwise, proceed to Step 6.
In the Group field, enter the name of the Oracle Identity Manager or user-defined form on which the lookup definition appears.
|
Note: You must adhere to certain naming conventions for the text you enter into the Code, Field, and Group text boxes.For more information on these naming conventions, refer to Chapter8, "The Lookup Definition Form". |
Click Save. The lookup definition is created. The associated text field, lookup field, or combo box will now appear in the Oracle Identity Manager or user-defined form or tab you specified.
The Lookup Code Information tab is located in the lower half of the Lookup Definition form. It is used to create and manage detailed information related to the selected lookup definition. This information, which includes the names, descriptions, language codes, and country codes of a value pertaining to the lookup definition, is known as a lookup value.
The following procedures show how to create, modify, and delete a lookup value.
|
Caution: For internationalization purposes, a lookup value must be supplied with both a language and country code.When creating a new lookup definition, ensure to save it before adding lookup values to it. |
To create or modify a lookup value, perform the following steps:
Open the Lookup Definition form.
Access a lookup definition.
If you are creating a lookup value, click Add. A blank row appears within the Lookup Code Information tab.
If you are modifying a lookup value, highlight the lookup value that you want to edit.
Add or edit the information in the Code Key field. This field contains the name of the lookup value.
In addition, if the Lookup Type radio button is selected, this field also represents what appears within the lookup field or combo box once the user makes a selection.
Add or edit the information in the Decode field. This field contains a description of the lookup value.
Also, if the Lookup Type radio button is selected, this field also represents:
The items that appears within a lookup window (once the user double-clicks the corresponding lookup field); or
The commands that are to be displayed within the associated combo box.
Add or edit the information in the Language field. This field contains a two-character language code for the lookup value.
Add or edit the information in the Country field. This field contains the lookup value's two-character country code.
Click Save. The lookup value you created or modified will now reflect the settings you have entered.
Sometimes, other than the fields that Oracle Identity Manager provides by default, you may need to store additional information. When this occurs, you can create the fields that will contain this information, and add them to various Oracle Identity Manager forms. These fields, which you create, are known as user-defined fields.
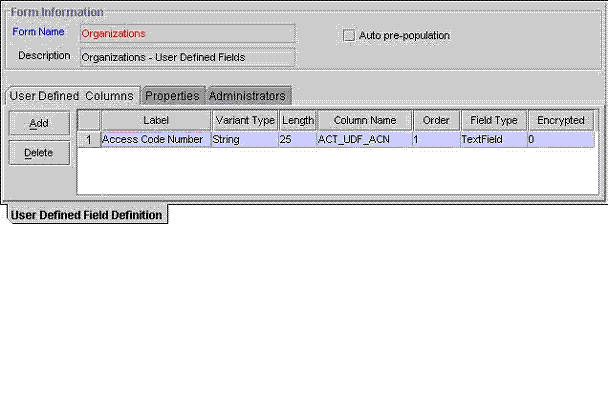
The User Defined Field Definition form, as shown in Figure 8-3, is located in the Oracle Identity Manager Administration folder. It is used to create and manage user-defined fields for the Organizations, Users, Requests, Resource Objects, User Groups, and Form Designer forms.
Figure 8-3 The User Defined Field Definition Form
|
Note: The user-defined field appears on the User Defined Fields tab of the form that appears in the Form Name data field. For this example, the Access Code Number user-defined field will be added to the User Defined Fields tab of the Organizations form. |
Now that we have reviewed user-defined fields, you will learn about the data fields of the User Defined Field Definition form. The following table describes the fields of this form.
| Field Name | Description |
|---|---|
| Form Name | The name of the form that the user-defined fields, which are displayed within the User Defined Columns tab, appears.
Important: Since the user-defined fields for a user pertain to the user's profile information, they are displayed within the User Profile tab of the Users form. |
| Description | Additional information about the user-defined field definition. |
| Auto Pre-Population | This check box designates whether the user-defined fields for a form, which have pre-populated adapters attached to them, will be populated by Oracle Identity Manager or a user.
If the Auto Pre-Population check box is selected, the user-defined fields that have pre-populate adapters attached to them will be populated by Oracle Identity Manager. When this check box is cleared, these fields must be populated by a user (by clicking the Pre-Populate button on the Toolbar or by a user manually entering the data). Important: This setting does not control the triggering of the pre-populate adapter. It merely determines whether the contents resulting from the execution of the adapter appear within the associated user-defined field (s) because of Oracle Identity Manager or a user. For more information on pre-populate adapters, refer to Oracle Identity Manager Tools Reference Guide. Note: Setting this checkbox is relevant only if you have created a user-defined field, and a pre-populate adapter is associated with that field. |
Now that we have reviewed the data fields of this form, you will learn how to select a target form for the user-defined fields you will be creating.
To select the target form for a user-defined field, perform the following steps:
Open the User Defined Field Definition form.
Double-click the Form Name lookup field. From the Lookup window that appears, select the Oracle Identity Manager form (Organizational Defaults, Policy History, Group Entitlements, Resource Objects, or Form Designer) that will display the user-defined field you will be creating.
Click Query. The form to which you will be adding the user-defined field is selected.
Once you launch the User Defined Field Definition form, and select a target form for the user-defined fields you will be creating, the tabs of this form become functional.
The User Defined Field Definition form contains the following tabs:
Each of these tabs is covered in greater detail in the sections that follow.
Figure 8-4 displays the User Defined columns tab of the User Defined Field Definition Form.
Figure 8-4 User Defined Columns Tab of the User Defined Field Definition Form
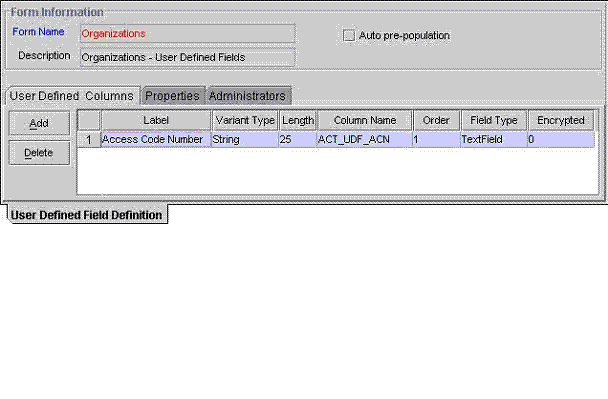
This tab is used to:
Create a user-defined field.
Set the variant type, length, and field type for the user-defined field.
Specify the order in which the user-defined field appears on the User Defined Fields tab of the target form.
Determine whether the information, which is associated with the user-defined field, is to be encrypted when it is exchanged between the Client and the Server.
Remove a user-defined field, when it is no longer valid.
|
Caution: the field's order number determines the order in which a user-defined field appears on a form. For this example, the Access Code Number user-defined field has an order number of 1. Therefore, this field appears first on the User Defined Fields tab of the Organizations form. |
Now that we have reviewed the User Defined Columns tab, you will learn how to add a user-defined field to an Oracle Identity Manager form, and remove a user-defined field from an Oracle Identity Manager form.
Add a User-Defined Field to an Oracle Identity Manager Form
Click Add. The User Defined Fields dialog box is displayed, as shown in Figure 8-5.
Figure 8-5 The User Defined Fields Dialog Box
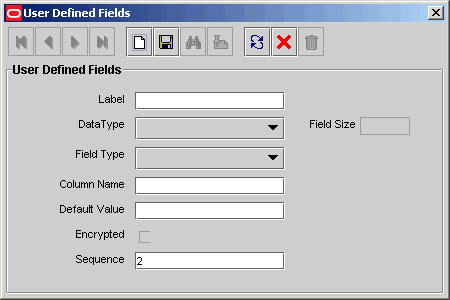
Set the parameters for the user-defined field you are adding to a form, as shown in Figure 8-6.
Figure 8-6 The User Defined Fields Dialog Box - Filled
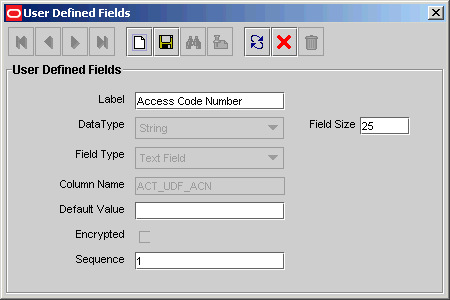
For this example, the Access Code Number user-defined field appears first on the User Defined Fields tab of the Organizations form. The data type of this field is String, and a user can enter up to 25 digits into it.
From this window, click Save.
Click Close. The user-defined field appears within the User Defined Columns tab. Once the target form is launched, this user-defined field appears within the User Defined Fields tab of that form.
|
Caution: Since the user-defined fields for a user pertain to the user's profile information, they are displayed within the User Profile tab of the Users form. |
Remove a User-Defined Field from an Oracle Identity Manager Form
Highlight the desired user-defined field.
Click Delete. The user-defined field is removed.
Figure 8-7 displays the Properties tab of the User Defined Field Definition form.
Figure 8-7 The Properties Tab of the User Defined Field Definition Form
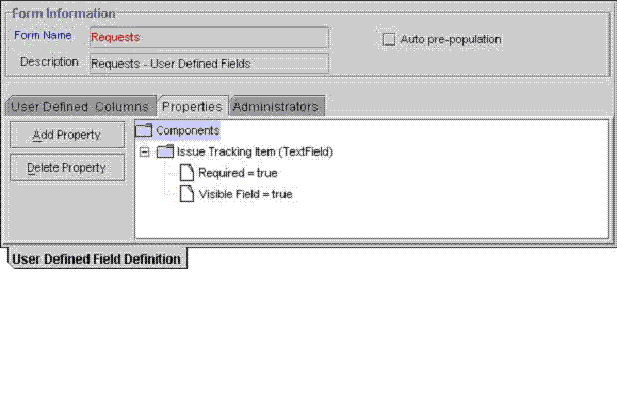
This tab is used to assign properties and property values to the data fields, which appear on the User Defined Fields tabs of various Oracle Identity Manager forms.
For this example, the User Defined Fields tab of the Requests form displays one data field: Issue Tracking Item. This data field contains the following properties:
Required, which determines whether the data field needs to be populated for the Requests form to be saved. The default property value for the Required property is false.
Visible Field, which establishes whether the data field appears on the Requests form. The default property value for the Visible Field property is true.
Since the property values for the Required and Visible Field properties are true for this data field, once the Requests form is launched, the Issue Tracking Item data field appears within the User Defined Fields tab. In addition, this field needs to be populated for the form to be saved.
The following section describes how to add and remove a property and property value to a data field.
|
Note: To learn how to add a property and property value to a data field, or remove a property and property value from a data field, refer to "The Form Designer Form". |
Figure 8-8 displays the Administrators tab of the User Defined Field Definition form.
Figure 8-8 Administrators Tab of the User Defined Field Definition Form
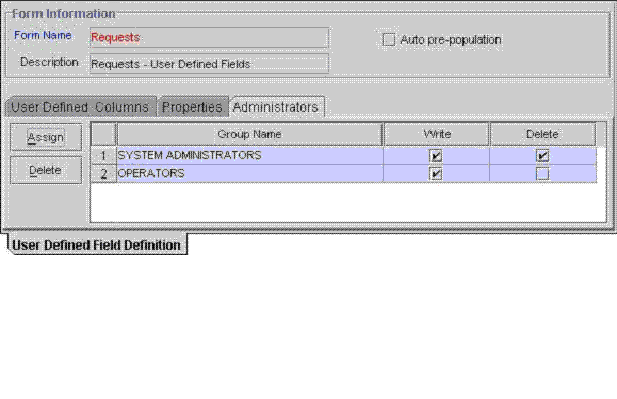
This tab is used to specify the user groups that have administrative privileges over the current record of the User Defined Field Definition form. In addition, the Write and Delete check boxes on this form are used to designate whether these administrative groups can modify and/or delete information pertaining to the current user-defined field (UDF) definition.
Now that we have reviewed the Administrators tab, you will learn how to assign administrative privileges to a user group for a UDF definition, and remove administrative privileges from a user group for a UDF definition.
Assign Administrative Privileges to a User Group for a UDF Definition
Click Assign. The Assignment dialog box is displayed.
Select the user group, and assign it to the UDF definition.
Click OK. The user group appears in the Administrators tab.
If you want this user group to be able to view and/or modify information pertaining to the current definition, double-click the corresponding Write check box. Otherwise, proceed to Step 5.
If you want this user group to be able to delete information contained within the current definition, double-click the associated Delete check box. Otherwise, proceed to Step 6.
Click Save. The user group is assigned to the UDF definition. The members of this user group can view, modify, and/or delete information contained within this definition.
Remove Administrative Privileges From a User Group for a UDF Definition
Highlight the user group that you want to remove.
Click Delete. The user group is removed from the UDF definition. Its members no longer have administrative privileges for the definition.
The System Configuration form, as shown in Figure 8-9, is located in the Oracle Identity Manager Administration folder. It is used to define and set the value of properties that control the behavior of the Oracle Identity Manager Client and/or Server. In addition, you may specify the users and/or user groups to which the value of a property setting applies. Alternately, you may specify that the value of a property setting apply to all users.
The following table describes the data fields of this form:
| Field Name | Description |
|---|---|
| Key | The system-generated ID for one instance of the property definition. There may be more than one instance of a definition (for example, one for System Administrators, another for all users). |
| System | This check box is used to designate whether this instance of the property definition applies to all users in Oracle Identity Manager (i.e., it is a system-wide instance) or only to select users and user groups.
To apply this setting to all users, select this check box (the Users and Groups tabs will be disabled). To specify that an instance of the property apply to certain users and groups, clear this check box. Note: The System check box will be disabled if the Server radio button (described below) is selected. |
| Client
Client/Server Server [Radio buttons] |
These three radio buttons are used to designate whether this instance of the property definition applies to the Client, the Server, or both.
If the Client radio button is selected, the property value only applies to the Client. If the Client/Server radio button is selected, the property value applies to both the Client and Server. If the Server radio button is selected, the property value only applies to the Server. Selecting this option will disable the System checkbox (since system-wide settings do not apply to the Server). |
| Name | The name of the property. This should be an intuitive description of what the property controls. It does not need to be unique. |
| Keyword | The property's unique ID.
This must be identical for each instance of this property. For example, if you wish to set the Record Read Limit property (the maximum number of records a user's query may retrieve) differently for two separate users, you would need to create two instances of this property definition. Note: For more information on the various properties you can set for the Client and/or the Server, refer to the "System Properties". |
| Value | The value to which this instance of the property definition has been set. This will be the value applied to those users/groups assigned to this instance of the property (unless the System checkbox is selected, denoting that the instance applies to all users). |
Now that we have reviewed the basic characteristics of a system property, you are ready to define instances of property definitions, and assign users or groups to these instances. Also, when an instance of a property definition no longer applies to a user or group, you will learn how to remove the user or group from this instance.
To create a new instance or edit an existing instance of a property definition, perform the following steps:
Access the System Configuration form.
If you are creating a new instance of a property definition, click New on the Toolbar. Ensure that the values in the Name and Keyword fields are the same for all instances of this property definition (for example, Record Read Limit, XL.READ_LIMIT).
|
Note: It is recommended that you copy these values from the other instances of this property definition to minimize any chance of a typing error. |
If you are editing an existing instance of a property definition, query for the property definition.
Select the Client, Client/Server, or Server radio button depending on whether the instance of this property definition will apply to the Client only, both the Client and the Server, or just the Server.
Designate whether you wish this instance of the property definition to apply to all users or only to select users and user groups by selecting or clearing the System check box.
Enter the desired value in the Value field. This will be the value of the property for this instance of the definition.
Click Save. The instance of the property definition is created or modified.
Now that you have added or edited an instance of a property definition, you will learn how to assign users and groups to this instance.
To assign a user or group to an instance of a property definition, perform the following steps:
|
Caution: If this is a system-wide instance (i.e., the System check box is selected), it will be applied to all users and groups. As a result, you do not need to assign it to a particular user or group. |
Access the System Configuration form.
Query for the instance of the property definition you wish to assign to a user or group.
|
Note: To learn more about the various property definitions to which you can assign users and groups, refer to "System Properties". |
Select the Client, Client/Server, or Server radio button, depending on whether the instance of this property definition will apply to the Client only, both the Client and the Server, or just the Server.
To assign the property instance to one or more users, click the Users tab. Otherwise, to assign the property instance to one or more user groups, click the Groups tab.
Click Assign. The Assignment dialog box is displayed.
Select and assign the desired users or groups and then, click OK.
Click Save. The instance of the property definition is assigned to the user(s) and/or group(s) you selected in Step 6.
To remove a user or group from an instance of a property definition, perform the following steps:
Access the System Configuration form.
Query for the instance of the property definition from which you wish to remove a user or group.
Highlight the desired user or group (from the Users or Groups tabs, respectively).
Click Delete. The user or group is removed from the instance of the property definition. As a result, the property is no longer associated with the user or group.
The Remote Manager is a light-weight network component (server) that enables to integrate with target systems whose APIs do not have the ability to communicate over a network, or do have network awareness but are not secure. This is accomplished by having a Remote Manager work as a server on the target system, and an Oracle Identity Manager Server work as its client, such that the Oracle Identity Manager Server sends a request for the Remote Manager to instantiate the target system APIs on the target system itself, and invokes methods on its behalf.
The Remote Manager form, as shown in Figure 8-10, is located in the Oracle Identity Manager Administration folder. It is used to display the following:
The names and IP addresses of the remote managers that communicate with Oracle Identity Manager.
Whether the remote manager is running.
Whether it represents IT resource(s) that Oracle Identity Manager can use.
For this example, there are two remote managers that can communicate with Oracle Identity Manager: Australia Server and UKSERVER.
The Australia Server remote manager has an IP address of 215.0.255.192. Though it can handshake with Oracle Identity Manager, because the Running check box is cleared, the remote Server is down. Lastly, the IT Resource check box is selected, signifying that this remote manager represents IT resource(s) that can be used by Oracle Identity Manager.
The UKSERVER remote manager has an IP address of 192.168.0.45. Since the Running check box is selected, the remote Server is operable. However, because the IT Resource check box is cleared, this remote manager does not represent IT resource(s) that Oracle Identity Manager can use.
|
Note: To learn how the Remote Manager form is used with other Oracle Identity Manager forms, refer to Oracle Identity Manager Tools Reference Guide. |
The Password Policies form, as shown in Figure 8-11, is located in the Oracle Identity Manager Administration/Policies folder. It is used to:
Set password restrictions (for example, defining a password's minimum and maximum length).
See the rules and resource objects that are associated with a password policy.
You will now learn about the data fields of the Password Policies form. The following table describes the data fields of this form.
| Field Name | Description |
|---|---|
| Policy Name | The password policy's name. |
| Policy Description | Explanatory information about the password policy. |
Now that we have reviewed password policies and the data fields of the Password Policies form, you are ready to create a password policy.
To create a password policy, perform the following steps:
Open the Password Policies form.
In the Policy Name field, enter the name of the password policy 3.
In the Policy Description field, enter explanatory information about the password policy.
Click Save. The password policy is created.
|
Note: Once a password policy is created, it must be supplied with criteria and associated with a resource. To supply your password policy with criteria, use the Policy Rules tab of this form. To associate your password policy with a resource, use the Password Policies Rule tab of the Resource Object form to create a password policy/rule combination that will be evaluated when accounts are created or updated on the resource. The password policy will then be invoked and applied when that rule's criteria are satisfied. Multiple resources can use each password policy. |
Once you launch the Password Policies form, and create a password policy, the tabs of this form become functional.
The Password Policies form contains the following tabs:
Each of these tabs is covered in greater detail in the following sections.
Figure 8-12 displays the Policy Rules tab of the Password Policies Form.
Figure 8-12 The Policy Rules Tab of the Password Policies Form
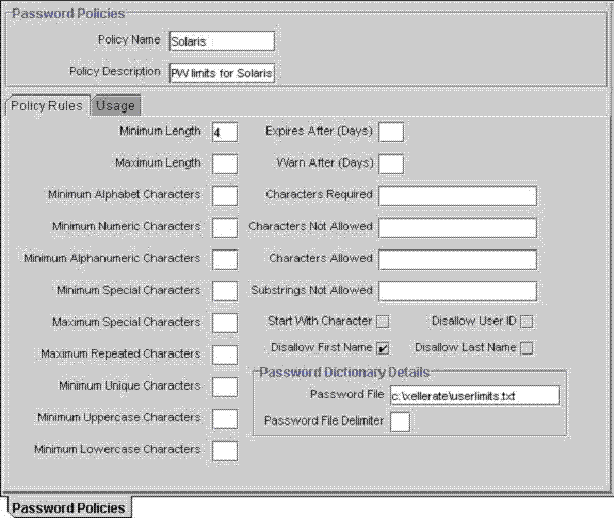
This tab is used to specify the criteria of your password policy (for example, defining a password's minimum and maximum length).
You may use either or both of the following methods to set password restrictions:
Enter information into the appropriate text boxes or select the desired check boxes. As an example, to indicate that a password must have a minimum length of four characters, type 4 into the Minimum Length text box. For another example, to prohibit Oracle Identity Manager from accepting a user's first name as a valid password, select the Disallow First Name check box.
Enter a path and filename into the Password File text box (for example, c:\xellerate\userlimits.txt). This file contains pre-defined terms that are not allowed as passwords. The delimiter specified in the Password File Delimiter field separates these terms.
Now that we have reviewed password restrictions, you will learn about the data fields of the Policy Rules tab. These are the fields into which you will specify the password limitations.
|
Note: If a data field is empty, the password does not have to meet the criteria of that field for it to be valid. For example, when the Minimum Numeric Characters and Maximum Numeric Characters data fields are blank, Oracle Identity Manager will accept the password, regardless of how many digits it has. |
The following table describes the data fields of the Policy Rules tab.
| Field Name | Description |
|---|---|
| Minimum Length | The fewest number of characters that a password can have for it to be valid.
For example, if 4 appear in the Minimum Length text box, the password must have at least four characters for it to be accepted. |
| Maximum Length | The highest number of characters that a password can have for it to be valid.
As an example, if 8 appear in the Maximum Length text box, the password will not be accepted if it has more than eight characters. |
| Minimum Alphabet Characters | The fewest number of letters that a password can have for it to be valid.
For example, if 2 appear in the Minimum Alphabet Characters text box, the password will not be accepted if it has fewer than two letters. |
| Minimum Numeric Characters | The fewest number of digits that a password can have for it to be valid.
As an example, if 1 appears in the Minimum Numeric Characters text box, the password must have at least one number for it to be accepted. |
| Minimum Alphanumeric Characters | The fewest number of letters or digits that a password can have for it to be valid.
For example, if 6 appear in the Minimum Alphanumeric Characters text box, the password must be comprised of at least six letters or numbers for it to be accepted. |
| Minimum Special Characters | The fewest number of non-alphanumeric characters (for example, #, %, or &) that a password can have for it to be valid.
As an example, if 1 appears in the Minimum Special Characters text box, the password must have at least one non-alphanumeric character for it to be accepted. |
| Maximum Special Characters | The highest number of non-alphanumeric characters that a password can have for it to be valid.
For example, if 3 appear in the Maximum Special Characters text box, the password will not be accepted if it has more than three non-alphanumeric characters. |
| Maximum Repeated Characters | The highest number of duplicate characters that a password can have for it to be valid.
As an example, if 2 appear in the Maximum Repeated Characters text box, the password will not be accepted if more than two characters are repeated. So, for this example, RL112233 would not be a valid password (three characters of the password are repeated). |
| Minimum Unique Characters | The fewest number of non-repeating characters that a password can have for it to be valid.
As an example, if 1 appears in the Minimum Unique Characters text box, the password will not be accepted if every character of the password is repeated at least once. Therefore, for this example, 1a23a321 would not be a valid password (each character of the password is repeated). |
| Minimum Uppercase Characters | The fewest number of uppercase letters that a password can have for it to be valid.
For example, if 8 appear in the Minimum Uppercase Characters text box, the password will not be accepted if it has fewer than eight uppercase letters. |
| Minimum Lowercase Characters | The fewest number of lowercase letters that a password can have for it to be valid.
As an example, if 8 appear in the Minimum Lowercase Characters text box, the password will not be accepted if it has fewer than eight lowercase letters. |
| Expires After (Days) | The maximum number of days for which a password is valid.
For example, if 30 appear in the Expires After (Days) text box, and the password is created on November 1, it will not be valid on December 1 (31 days will have elapsed). |
| Warn After (Days) | The number of days that will pass before a user is notified that a password will expire on a designated date.
As an example, suppose 30 appear in the Expires After (Days) text box, 10 is displayed in the Warn After (Days) text box, and the password is created on November 1. On November 11, the user will be informed that the password will expire on December 1. |
| Characters Required | The characters that a password must have for it to be valid.
For example, if x appears in the Characters Required text box, the password will be accepted only if it contains an "x". |
| Characters Not Allowed | The characters that a password must not have for it to be valid.
As an example, if ! appears in the Characters Not Allowed text box, the password will not be accepted if it contains an "!". |
| Characters Allowed | The characters that a password can have for it to be valid.
For example, if % appears in the Characters Allowed text box, the password will be accepted if it contains a "%". |
| Substrings Not Allowed | A series of consecutive alphanumeric characters that a password must not have for it to be valid.
As an example, if IBM appears in the Substrings Not Allowed text box, the password will not be accepted if it contains the letters "I", "B", and "M", in successive order. |
| Start With Character | This check box is used to specify whether a password is to begin with a character.
By selecting this check box, the password must start with a character for it to be valid. If you clear this check box, the password will be accepted, even if it does not begin with a character. |
| Disallow First Name | This check box is used to specify whether the user's first name is to be accepted as all or a portion of the password.
By selecting this check box, the password will not be valid if the user's first name is entered into the Password field. If you clear this check box, the password will be accepted, even if it contains the user's first name. |
| Disallow User ID | This check box is used to specify whether the User ID is to be accepted as all or a portion of the password.
By selecting this check box, the password will not be valid if the User ID is entered into the Password field. If you clear this check box, the password will be accepted, even if it contains the User ID. |
| Disallow Last Name | This check box is used to specify whether the user's last name is to be accepted as all or a portion of the password.
By selecting this check box, the password will not be valid if the user's last name is entered into the Password field. If you clear this check box, the password will be accepted, even if it contains the user's last name. |
| Password File | The path and name of a file that contains pre-defined terms, which are not allowed as passwords.
Note: If any settings in the Policy Rules tab differ from the specifications in the password file, Oracle Identity Manager will defer to the tab's settings. |
| Password File Delimiter | The character used to separate terms in the password file from one another.
For example, if a "," appears in the Password File Delimiter text box, the terms of the password file will be separated by commas. |
Now that we have reviewed the data fields of the Policy Rules tab, you are ready to specify the criteria (or rules) for the password policy.
Set the Criteria for a Password Policy
Access the desired password policy definition.
Click the Policy Rules tab.
Enter information into the appropriate text boxes.
AND/OR
Select the desired check boxes.
Click Save. The rules for the password policy are set.
Figure 8-13 displays the Usage tab of the Password Policies form.
Figure 8-13 The Usage Tab of the Password Policies Form
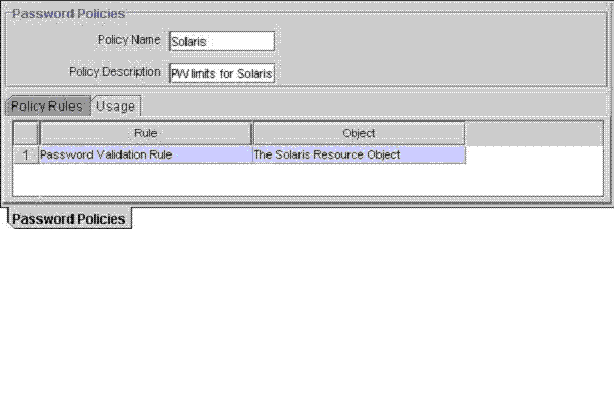
Within this tab, you can see the rules and resource objects that are associated with the current password policy.
For this example, the Solaris password policy and the Password Validation Rule have been assigned to The Solaris Resource Object.
|
Note: For more information on the relationship between password policies and resource objects, refer to "Password Policies Rule". |
The Task Scheduler form, as shown in Figure 8-14, is located in the Oracle Identity Manager Administration/Job Scheduling Tools folder. It is used to define:
When your tasks are scheduled to be run
The attributes of these scheduled tasks
|
Caution: As stated above, the Task Scheduler form is used to determine when a task is scheduled to be run. However, the Oracle Identity Manager program that triggers the execution of this task is referred to as the scheduler daemon.Since the scheduler daemon cannot perform its designated function if it is not running, you must verify that is it active. For more information on modifying the value of a system property, refer to "The System Configuration Form". |
The following table lists and describes the data fields of the Task Scheduler form.
| Field Name | Description |
|---|---|
| Scheduled Task | The name of the task that is scheduled to be run. |
| Class Name | The name of the Java class that executes the scheduled task.
Important: The scheduler daemon triggers the execution of a scheduled task. The Java class actually executes the task. |
| Status | The task's status. Currently, a scheduled task has four status levels:
|
| Max Retries | If the task is not completed, the number of times that Oracle Identity Manager attempts to complete the task before assigning a status of ERROR to it. |
| Disabled | This check box is used to designate whether the scheduler daemon triggers a scheduled task.
If this check box is selected, the scheduler daemon does not trigger the task, even when the date and time that appears in the Start Time or Next Start Time fields matches the current date and time. When this check box is cleared, and the date and time that is displayed in the Start Time or Next Start Time fields matches the current date and time, the scheduler daemon triggers the task. |
| Stop Execution | This check box is used to designate whether the scheduler daemon can stop a scheduled task with a status of RUNNING.
If this check box is selected, and the task's status is RUNNING, the scheduler daemon stops the task from being executed. In addition, the task's status changes to INACTIVE. When this check box is cleared, the scheduler daemon does not stop a task with a status of RUNNING from being executed. |
| Start Time | The date and time of when the task is scheduled to run for the first time.
Note: If the task is set to be run more than once, the scheduler daemon refers to the date and time that appears in the Next Start Time field. |
| Last Start Time | The latest date and time of when the task started to run. |
| Last Stop Time | The most recent date and time of when the task stopped running. |
| Next Start Time | The subsequent date and time of when the task is scheduled to run.
Note: If the task is set to be run only once, the scheduler daemon refers to the date and time that is displayed in the Start Time field. |
| Daily, Weekly, Monthly, Yearly | These radio buttons are used to designate whether the task is to be run daily, weekly, monthly, or annually, respectively.
If one of these radio buttons are selected, the scheduler daemon triggers the associated task once a day, week, month, or year, at the date and time specified in the Start Time field. When all of these radio buttons are cleared, the scheduler daemon does not trigger the associated task on a daily, weekly, monthly, or annual basis. |
| Recurring Intervals | This radio button is used to designate that the task is to be run on a fixed, recurring basis.
If this radio button is selected, the scheduler daemon triggers the associated task on a recurring basis. When this radio button is cleared, the scheduler daemon does not trigger the associated task on a recurring basis. Note: If the Recurring Intervals radio button is selected, you must set the interval by entering a value into the text field below the radio button, and selecting a unit of measure from the adjacent combo box. |
| Once | This radio button is used to designate that the task is to be run only once.
If this radio button is selected, the scheduler daemon triggers the associated task once, at the date and time specified in the Start Time field. When this radio button is cleared, the scheduler daemon triggers the associated task more than once. |
To create a task schedule, perform the following steps:
Access the Task Scheduler form.
Enter the name of the scheduled task in the Scheduled Task field.
Enter the name of the Java class that executes the scheduled task in the Class Name field.
Enter a number into the Max Retries field. This number represents how many times Oracle Identity Manager attempts to complete the task before assigning a status of ERROR to it.
Ensure that the Disabled and Stop Execution check boxes are cleared.
Double-click the Start Time field. From the Date & Time window that appears, set the date and time that the task is scheduled to run. If you have specified that the task is to be executed on a recurring basis (by selecting the Recurring Intervals radio button), the date and time that is displayed in this field is referenced to determine when next to run the associated task.
Set the scheduling parameters (in the Interval region):
To set the task to run on a recurring basis, select the Daily, Weekly, Monthly, or Yearly radio buttons.
To set the task to run only once, select the Once radio button.
To set the task to run on a fixed, recurring basis, select the Recurring Intervals radio button. Then, set the interval by entering a value into the text field below the radio button. Then select a unit of measure from the adjacent combo box.
Click Save. The task schedule is created. In addition, INACTIVE is displayed within the Status field (since the task is not currently running). However, once the date and time that you set in Step 6 matches the current date and time, the scheduler daemon triggers the scheduled task.
Now that you have defined a schedule for a task, if the task needs attributes, you must set them. Otherwise, the task schedule is not functional.
Also, when an existing task attribute is no longer relevant, you must remove it from the task schedule.
The following procedures show you how to add an attribute to a task schedule, and remove a task attribute from the task schedule.