1 About the Connector
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with third-party applications. This guide discusses the procedure to deploy the connector that is used to integrate Oracle Identity Manager with Oracle Internet Directory.
Note:
At some places in this guide, Oracle Internet Directory has been referred to as the target system.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
Note:
It is recommended that you do not configure the target system as both an authoritative (trusted) source and a managed (target) resource.
This chapter contains the following sections:
-
Section 1.5, "Lookup Definitions Used During Connector Operations"
-
Section 1.6, "Connector Objects Used During Target Resource Reconciliation"
-
Section 1.7, "Connector Objects Used During Trusted Source Reconciliation"
-
Section 1.9, "Roadmap for Deploying and Using the Connector"
1.1 Certified Components
Table 1-1 lists certified components for the connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
You can use one of the following releases of Oracle Identity Manager:
|
|
|
Oracle Internet Directory release 10.1.x, or 11gR1 |
|
|
JDK |
The JDK version can be one of the following:
|
|
Target system user account |
User account to which the BROWSE, ADD, DELETE, READ, WRITE, and SEARCH rights have been assigned You provide the credentials of this user account configuring the IT resource. The procedure is described later in this guide. If you try to perform an operation for which the required permission has not been assigned to the user account, then the "Insufficient Access Rights" message is displayed. |
1.2 Certified Languages
The connector supports the following languages:
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
See Also:
Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager for information about supported special characters
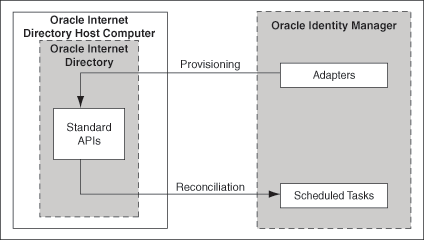
1.3 Connector Architecture
The architecture of the connector is the blueprint for the functionality of the connector. Figure 1-1 shows the architecture of the connector.
The connector can be configured to run in one of the following modes:
Note:
In Oracle Identity Manager release 11.1.1, a scheduled job is an instance of a scheduled task. In this guide, the term scheduled task used in the context of Oracle Identity Manager release 9.1.0.x is the same as the term scheduled job in the context of Oracle Identity Manager release 11.1.1.
See Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager for more information about scheduled tasks and scheduled jobs.
-
Identity reconciliation
In the identity reconciliation mode, Oracle Internet Directory is used as the trusted source and users are directly created and modified on it.
During reconciliation, a scheduled task establishes a connection with the target system and sends reconciliation criteria to the APIs. The APIs extract user records that match the reconciliation criteria and hand them over to the scheduled task, which brings the records to Oracle Identity Manager. The next step depends on the mode of connector configuration.
Each record fetched from the target system is compared with existing OIM Users. If a match is found, then the update made to the record on the target system is copied to the OIM User attributes. If no match is found, then the target system record is used to create an OIM User.
-
Account Management
In the account management mode, Oracle Internet Directory is used as a target resource. The connector enables the target resource reconciliation and provisioning operations. Through provisioning operations performed on Oracle Identity Manager, user accounts are created and updated on the target system for OIM Users. During reconciliation from the target resource, the Oracle Internet Directory connector fetches into Oracle Identity Manager data about user accounts that are created or modified on the target system. This data is used to add or modify resources allocated to OIM Users.
During provisioning operations, adapters carry provisioning data submitted through the process form to the target system. APIs on the target system accept provisioning data from the adapters, carry out the required operation on the target system, and return the response from the target system to the adapters. The adapters return the response to Oracle Identity Manager.
During reconciliation, a scheduled task establishes a connection with the target system and sends reconciliation criteria to the APIs. The APIs extract user records that match the reconciliation criteria and hand them over to the scheduled task, which brings the records to Oracle Identity Manager. The next step depends on the mode of connector configuration.
1.4 Features of the connector
-
Section 1.4.1, "Support for Both Target Resource and Trusted Source Reconciliation"
-
Section 1.4.4, "Support for Reconciliation of Deleted User Records"
-
Section 1.4.5, "Support for Both Full and Incremental Reconciliation"
-
Section 1.4.7, "Support for High-Availability Configuration of the Target System"
1.4.1 Support for Both Target Resource and Trusted Source Reconciliation
You can use the connector to configure Oracle Internet Directory as either a target resource or trusted source of Oracle Identity Manager.
See Section 3.3, "Configuring Reconciliation" for more information.
1.4.2 Support for Limited Reconciliation
You can set a reconciliation filter as the value of the SearchFilter attribute of the scheduled tasks. This filter specifies the subset of newly added and modified target system records that must be reconciled.
See Section 3.3.2, "Limited Reconciliation" for more information.
1.4.3 Support for Paged Reconciliation
Paged reconciliation is the reconciliation of a specified set of target system records at a time, within a reconciliation run. Multiple pages of records are fetched to complete the reconciliation run. This feature helps reduce memory issues that might arise when there are a large number of records to be reconciled.
Paged reconciliation is implemented using the PageSize attribute of the scheduled task.
See Section 3.3.3, "Paged Reconciliation" for more information about paged reconciliation.
1.4.4 Support for Reconciliation of Deleted User Records
You can configure the connector for reconciliation of deleted user records. In target resource mode, if a record is deleted on the target system, then the corresponding Oracle Internet Directory resource is revoked from the OIM User. In trusted source mode, if a record is deleted on the target system, then the corresponding OIM User is deleted.
See Section 3.3.4.1, "Scheduled Tasks for User Reconciliation" for more information about scheduled tasks used for reconciling deleted user records.
1.4.5 Support for Both Full and Incremental Reconciliation
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, change-based or incremental reconciliation is automatically enabled from the next run of the user reconciliation.
You can perform a full reconciliation run at any time.
See Section 3.3.1, "Full Reconciliation vs. Incremental Reconciliation" for more information.
1.4.6 Support for Adding New Single-Valued and Multivalued Attributes for Reconciliation and Provisioning
If you want to add to the standard set of single-valued and multivalued attributes for reconciliation and provisioning, then perform the procedures described in Chapter 4, "Extending the Functionality of the Connector"
1.4.7 Support for High-Availability Configuration of the Target System
The connector can be configured to work with high-availability target system environments. If the primary installation becomes unavailable, then the connector reads information about backup target system installations from the Lookup.OID.Backup server lookup definition and uses this information to switch to a backup target system installation. The timeout interval stored in the ldapConnectTimeOut entry of the Lookup.OID.Configuration lookup definition is used to determine when to switch to the backup target system installation.
See Section 2.3.1.7, "Configuring High Availability of the Target System" for more information.
1.5 Lookup Definitions Used During Connector Operations
Lookup definitions used during connector operations can be divided into the following categories:
1.5.1 Lookup Definitions Synchronized with the Target System
The following lookup definitions are populated with values fetched from the target system by the scheduled tasks for lookup field synchronization.
See Also:
Section 3.2, "Scheduled Tasks for Lookup Field Synchronization" for information about these scheduled tasks
-
For organizations and organization units: Lookup.OID.Organization
-
For groups: Lookup.OID.Group
-
For roles: Lookup.OID.Role
1.5.2 Other Lookup Definitions
Table 1-2 describes the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
Table 1-2 Other Lookup Definitions
| Lookup Definition | Description of Values | Method to Specify Values for the Lookup Definition |
|---|---|---|
|
Lookup.OID.Configuration |
This lookup definition holds connector configuration entries that are used during reconciliation and provisioning. |
Some of the entries in this lookup definition are preconfigured. See Section 2.3.1.6.1, "Setting Up the Lookup.OID.Configuration Lookup Definition" for information about the entries for which you can set values. |
|
Lookup.OID.Constants |
This lookup definition stores values that are used internally by the connector. The connector development team can use this lookup definition to make minor configuration changes in the connector. |
You must not modify the entries in this lookup definition. |
|
AttrName.Recon.Map.OID |
This lookup definition holds mappings between the OID User resource object fields and target system attributes. |
This lookup definition is preconfigured. It is used for both trusted source reconciliation and target resource reconciliation. You can add entries in this lookup definition if you want to map new target system attributes for user reconciliation. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
AttrName.Prov.Map.OID |
This lookup definition holds mappings between OID User process form fields and target system attributes. |
This lookup definition is preconfigured. Table 1-10 lists the default entries in this lookup definition. You can add entries in this lookup definition if you want to map new target system attributes for user provisioning. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
Lookup.OIDGroupReconciliation.FieldMap |
This lookup definition holds mappings between OID Group resource object fields and target system attributes. |
This lookup definition is preconfigured. Table 1-4 lists the default entries in this lookup definition. You can add entries in this lookup definition if you want to map new target system attributes for group reconciliation. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
AttrName.Group.Prov.Map.OID |
This lookup definition holds mappings between OID Group process form fields and target system attributes. |
This lookup definition is preconfigured. Table 1-12 lists the default entries in this lookup definition. You can add entries in this lookup definition if you want to map new target system attributes for group provisioning. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
Lookup.OIDRoleReconciliation.FieldMap |
This lookup definition holds mappings between OID Role resource object fields and target system attributes. |
This lookup definition is preconfigured. Table 1-5 lists the default entries in this lookup definition. You can add entries in this lookup definition if you want to map new target system attributes for role reconciliation. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
AttrName.Role.Prov.Map.OID |
This lookup definition holds mappings between OID Role process form fields and target system attributes. |
This lookup definition is preconfigured. Table 1-13 lists the default entries in this lookup definition. You can add entries in this lookup definition if you want to map new target system attributes for group provisioning. Chapter 4, "Extending the Functionality of the Connector" provides more information. |
|
Lookup.OID.Backup server |
This lookup definition holds mappings between primary Oracle Internet Directory servers and secondary Oracle Internet Directory servers. |
It is optional to enter values in this lookup definition. Section 2.3.1.7, "Configuring High Availability of the Target System" provides information about this lookup definition. |
|
Lookup.OID.PrefLang |
During a provisioning operation, you use this lookup definition to specify a language for the user. |
Section 2.3.1.6.2, "Setting Up the Lookup.OID.PrefLang Lookup Definition" provides information about creating entries in this lookup definition. |
1.6 Connector Objects Used During Target Resource Reconciliation
This section discusses the following topics:
-
Section 1.6.1, "User Attributes for Target Resource Reconciliation"
-
Section 1.6.2, "Group Attributes for Target Resource Reconciliation"
-
Section 1.6.3, "Role Attributes for Target Resource Reconciliation"
-
Section 1.6.4, "Reconciliation Rules for Target Resource Reconciliation"
-
Section 1.6.5, "Reconciliation Action Rules for Target Resource Reconciliation"
1.6.1 User Attributes for Target Resource Reconciliation
Table 1-3 lists the user attributes of the target system from which values are fetched during reconciliation. The OID User Target Recon Task scheduled task is used to reconcile user data.
Table 1-3 User Attributes for Target Resource Reconciliation
| Resource Object Field | Target System Attribute | Description |
|---|---|---|
|
User ID |
uid |
Unique ID of a user account |
|
First Name |
givenname |
First name |
|
Last Name |
sn |
Last name |
|
Middle Name |
middleName |
Middle name |
|
Department |
departmentNumber |
Department |
|
Location |
l |
Location |
|
Telephone |
telephoneNumber |
Telephone number |
|
|
|
E-mail address |
|
Time Zone |
orclTimeZone |
Timezone |
|
Preferred Language |
preferredlanguage |
Preferred language for communication |
|
Title |
title |
Designation |
|
Start Date |
orclActiveStartDate |
Date from which the user account is active |
|
End Date |
orclActiveEndDate |
Date up to which the user account is active |
|
orclGUID |
orclGuid |
GUID |
|
manager |
manager |
Distinguished name (DN) of the user's manager. |
|
Container DN |
NA |
Container in which the user account is present on the target system For example: |
|
Common Name |
cn |
Common name on the target system |
|
UserGroup |
groupOfUniqueNames |
Name of the group to which a user account belongs |
|
UserRole |
OrganizationalRole |
Name of the role that is assigned to a user account |
1.6.2 Group Attributes for Target Resource Reconciliation
Note:
If you are using Oracle Identity Manager release 11.1.1, then you cannot reconcile data from group attributes of the target system. This is tracked by Bug 9799541 in Chapter 6, "Known Issues"
Table 1-4 lists the group attributes of the target system from which values are fetched during reconciliation. The OID Group Recon Task scheduled task is used to reconcile group data.
1.6.3 Role Attributes for Target Resource Reconciliation
Note:
If you are using Oracle Identity Manager release 11.1.1, then you cannot reconcile data from role attributes of the target system. This is tracked by Bug 9799541 in Chapter 6, "Known Issues"
Table 1-5 lists the role attributes of the target system from which values are fetched during reconciliation. The OID Role Recon Task scheduled task is used to reconcile role data.
1.6.4 Reconciliation Rules for Target Resource Reconciliation
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for generic information about reconciliation matching and action rules
The following sections provide information about the reconciliation rules for this connector:
1.6.4.1 Reconciliation Rule for Target Resource Reconciliation
The following is the process-matching rule:
Rule name: OID User Recon Rule
Rule element: (ORCLGUID Equals orclGuid) OR (User Login Equals User ID)
In the first rule component:
-
User Login is the User ID field on the OIM User form.
-
User ID is the user ID field of the OID account.
In the second rule component:
-
ORCLGUID is the ORCLGUID field on the OIM User form.
-
orclGuid is the orclguid field on the target system.
1.6.4.2 Viewing Reconciliation Rules for Target Resource Reconciliation in the Design Console
After you deploy the connector, you can view the reconciliation rule for reconciliation by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for and open OID User Recon Rule. Figure 1-2 shows this reconciliation rule.
Figure 1-2 Reconciliation Rule for Target Resource Reconciliation
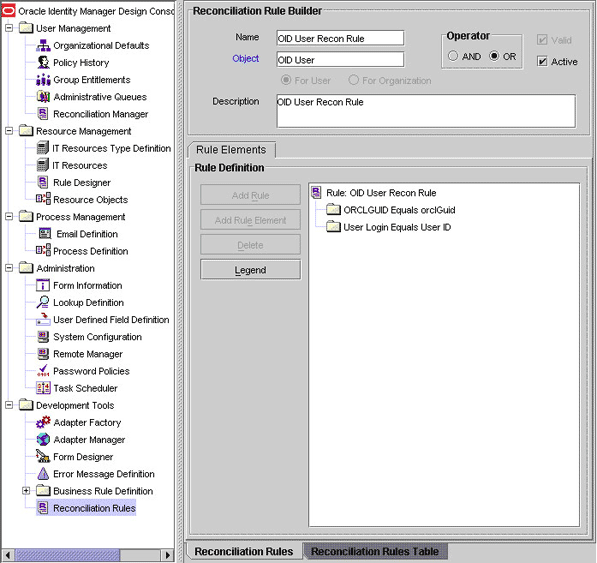
Description of "Figure 1-2 Reconciliation Rule for Target Resource Reconciliation"
1.6.5 Reconciliation Action Rules for Target Resource Reconciliation
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See Oracle Fusion Middleware User's Guide for Oracle Identity Manager for information about modifying or creating reconciliation action rules.
The following sections provide information about the reconciliation rules for this connector:
1.6.5.1 Reconciliation Action Rules for Target Resource Reconciliation
Table 1-6 lists the action rules for target resource reconciliation.
1.6.5.2 Viewing Reconciliation Action Rules for Target Resource Reconciliation in the Design Console
After you deploy the connector, you can view the reconciliation action rules for reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Resource Management, and double-click Resource Objects.
-
If you want to view the reconciliation action rules for reconciliation, then search for and open the OID Resource Object resource object.
-
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-3 shows the reconciliation action rules for reconciliation.
Figure 1-3 Action Rules for Target Resource Reconciliation
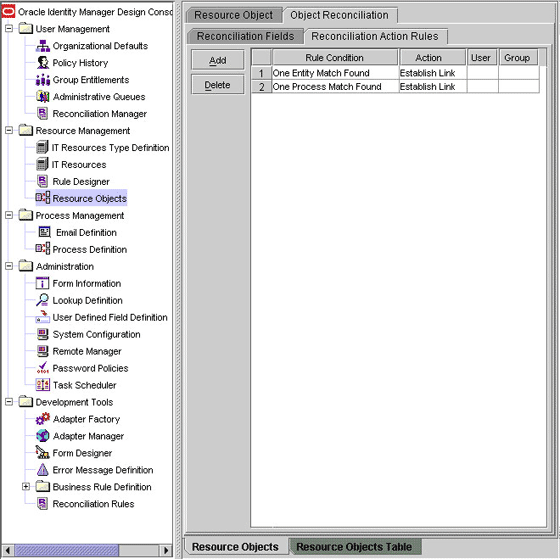
Description of "Figure 1-3 Action Rules for Target Resource Reconciliation"
1.7 Connector Objects Used During Trusted Source Reconciliation
This section discusses the following topics:
-
Section 1.7.1, "User Attributes for Trusted Source Reconciliation"
-
Section 1.7.2, "Reconciliation Rule for Trusted Source Reconciliation"
-
Section 1.7.3, "Reconciliation Action Rules for Trusted Source Reconciliation"
1.7.1 User Attributes for Trusted Source Reconciliation
Table 1-7 provides information about user attribute mappings for trusted source reconciliation.
Table 1-7 User Attributes for Trusted Source Reconciliation
| Field on the Xellerate User Resource Object | Target System Attribute | Description |
|---|---|---|
|
User ID |
uid |
User's logon name |
|
First Name |
givenname |
First name |
|
Last Name |
sn |
Last name |
|
Middle Name |
middleName |
Middle name |
|
Organization |
ou |
Name of the organization on the target system to which a user account belongs |
|
User Type |
NA |
Default value: |
|
Employee Type |
NA |
Default value: |
|
Start Date |
orclActiveStartDate |
Start date for the user account on the target system |
|
End Date |
orclActiveEndDate |
End date for the user account on the target system |
|
|
|
E-mail address |
|
Status |
orclisEnabled |
This field stores the status of a user account on the target system. |
|
manager |
manager |
Distinguished name (DN) of the user's manager. |
1.7.2 Reconciliation Rule for Trusted Source Reconciliation
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for generic information about reconciliation matching and action rules
The following sections provide information about the reconciliation rules for this connector:
1.7.2.1 Reconciliation Rule for Trusted Source Reconciliation
The following is the process-matching rule:
Rule name: Trusted Source Recon Rule
Rule element: User Login Equals User ID
In this rule element:
-
User Login is the User ID field on the OIM User form.
-
User ID is the user ID of the OID account.
1.7.2.2 Viewing Reconciliation Rules for Trusted Source Reconciliation in the Design Console
After you deploy the connector, you can view the reconciliation rule for reconciliation by performing the following steps:
Note:
Perform the following procedure only after the connector is deployed.
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Development Tools.
-
Double-click Reconciliation Rules.
-
Search for and open Trusted Source Recon Rule. Figure 1-4 shows this reconciliation rule.
Figure 1-4 Reconciliation Rule for Trusted Source Reconciliation

Description of "Figure 1-4 Reconciliation Rule for Trusted Source Reconciliation"
1.7.3 Reconciliation Action Rules for Trusted Source Reconciliation
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See Oracle Fusion Middleware User's Guide for Oracle Identity Manager for information about modifying or creating reconciliation action rules.
The following sections provide information about the reconciliation rules for this connector:
1.7.3.1 Reconciliation Action Rules for Trusted Source Reconciliation
Table 1-8 lists the action rules for reconciliation.
1.7.3.2 Viewing Reconciliation Action Rules for Trusted Source Reconciliation in the Design Console
After you deploy the connector, you can view the reconciliation action rules for reconciliation by performing the following steps:
-
Log in to the Oracle Identity Manager Design Console.
-
Expand Resource Management, and double-click Resource Objects.
-
If you want to view the reconciliation action rules for reconciliation, then search for and open the Xellerate User resource object.
-
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-5 shows the reconciliation action rules for reconciliation.
Figure 1-5 Action Rules for Trusted Source Reconciliation
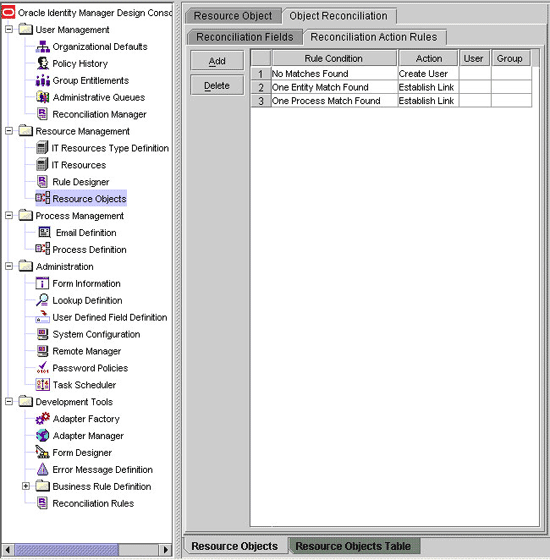
Description of "Figure 1-5 Action Rules for Trusted Source Reconciliation"
1.8 Connector Objects Used During Provisioning
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
See Also:
The "Provisioning" section in Oracle Fusion Middleware User's Guide for Oracle Identity Manager for conceptual information about provisioning
This section discusses the following topics:
1.8.1 User Provisioning Functions
Table 1-9 lists the user provisioning functions that are supported by the connector. The Adapter column gives the name of the adapter that is used when the function is performed.
See Also:
Oracle Fusion Middleware User's Guide for Oracle Identity Manager for generic information about process tasks and adapters
Table 1-9 User Provisioning Functions Supported by the Connector
| Function | Description | Adapter |
|---|---|---|
|
Create User |
Creates a user in Oracle Internet Directory |
OID Create User |
|
Delete User |
Deletes a user in Oracle Internet Directory |
OID Delete User |
|
Enable User |
Enables a user in Oracle Internet Directory |
OID Modify User |
|
Disable User |
Disables a user in Oracle Internet Directory |
OID Modify User |
|
Move User |
Moves a user account from one container to another in Oracle Internet Directory. |
OID Move User |
|
Update Password |
Updates the password of a user in Oracle Internet Directory |
OID Modify User |
|
Update First Name |
Updates the first name of a user in Oracle Internet Directory |
OID Modify User |
|
Update Last Name |
Updates the last name of a user in Oracle Internet Directory |
OID Modify User |
|
Update Department Name |
Updates the department name of a user in Oracle Internet Directory |
OID Modify User |
|
Update E-mail Address |
Updates the e-mail address of a user in Oracle Internet Directory |
OID Modify User |
|
Update Location |
Updates the location of a user in Oracle Internet Directory |
OID Modify User |
|
Update the Middle Name |
Updates the middle name of a user in Oracle Internet Directory |
OID Modify User |
|
Update Preferred Language |
Updates the preferred language for a user in Oracle Internet Directory |
OID Modify User |
|
Update Telephone Number |
Updates the telephone number of a user in Oracle Internet Directory |
OID Modify User |
|
Update Time Zone |
Updates the time zone of a user in Oracle Internet Directory |
OID Modify User |
|
Update Title |
Updates the title of a user in Oracle Internet Directory |
OID Modify User |
|
Update Container DN |
Updates the container DN of a user in Oracle Internet Directory |
OID Move User |
|
Add User to Group |
Adds a user to a group in Oracle Internet Directory |
OID Add User to Group |
|
Remove User from Group |
Removes a user from a group in Oracle Internet Directory |
OID Remove User from Group |
|
Add User to Role |
Adds a user to a role in Oracle Internet Directory |
OID Add User to Role |
|
Remove User from Role |
Removes a user from a role in Oracle Internet Directory |
OID Remove User from Role |
|
Create OU |
Creates an organizational unit |
OID Create OU |
|
Rename OU |
Changes the name of an organizational unit |
OID Change Org Name |
|
Delete OU |
Deletes an organizational unit |
OID Delete OU |
|
Move OU |
Moves the organization sub unit to another parent organizational unit |
OID Move OU |
|
Create OID group |
Creates an Oracle Internet Directory group |
OID Create Group |
|
Delete OID group |
Deletes an Oracle Internet Directory group |
OID Delete Group |
|
Update Group Name |
Updates a group name |
Update OID Group Details |
|
Create OID Role |
Creates an Oracle Internet Directory role Note: In this guide, OID Role refers to an organizational role (object class organizationalRole) in the target system, not to an EUS role (object class orclDBEnterpriseRole) stored in the target system. An EUS role is an OID Group. However, you can change OID Role to refer to EUS roles by modifying the Lookup.OID.Role lookup definition appropriately. |
OID Create Role |
|
Delete OID Role |
Deletes an Oracle Internet Directory role |
OID Delete Role |
|
Update Role Name |
Updates a role name |
Update OID Role Details |
1.8.2 User Attributes for Provisioning
Table 1-10 lists the process form fields for which you can specify or modify values during provisioning operations.
Table 1-10 User Attributes for Provisioning
| Process Form Field | Target System Attribute | Description | Adapter |
|---|---|---|---|
|
User ID |
uid |
Unique ID of a user account |
OID Modify User |
|
First Name |
givenname |
First name |
OID Modify User |
|
Last Name |
sn |
Last name |
OID Modify User |
|
Middle Name |
middleName |
Middle name |
OID Modify User |
|
Common Name |
cn |
Common name on the target system |
OID Modify User |
|
Department |
departmentNumber |
Department |
OID Modify User |
|
Location |
l |
Location |
OID Modify User |
|
Telephone |
telephoneNumber |
Telephone number |
OID Modify User |
|
|
|
E-mail address |
OID Modify User |
|
Communication Language |
PreferredLanguage |
Preferred language for communication |
OID Modify User |
|
Title |
title |
Designation |
OID Modify User |
|
Container DN |
NA |
Container in which the user is present on the target systemFor example: |
OID Move User |
|
Time Zone |
orclTimeZone |
Timezone |
OID Modify User |
|
Start Date |
orclActiveStartDate |
Date from which the user account is active |
OID Modify User |
|
End Date |
orclActiveEndDate |
Date up to which the user account is active |
OID Modify User |
|
manager |
manager |
Distinguished name (DN) of the user's manager. |
OID Modify User |
|
Group |
groupOfUniqueNames |
Name of the group to which a user account belongs |
OID Add User to Group |
|
Role |
OrganizationalRole |
Name of the role that is assigned to the user account |
OID Add User to Role |
Table 1-11 lists special characters that are supported in process form fields:
Table 1-11 Special Characters Supported in Process Form Fields
| Name of the Character | Character |
|---|---|
|
ampersand |
& |
|
asterisk |
* |
|
at sign |
@ |
|
caret |
^ |
|
comma |
, |
|
dollar sign |
$ |
|
equal sign |
= |
|
exclamation point |
! |
|
hyphen |
- |
|
left brace |
{ |
|
left bracket |
[ |
|
number sign |
# |
|
percent sign |
% |
|
period |
. |
|
plus sign |
+ |
|
question mark |
? |
|
right brace |
} |
|
right bracket |
] |
|
slash |
/ |
|
single quotation |
' |
|
underscore |
_ |
Note:
The following special characters are not supported in process form fields:
-
Double quotation mark (")
-
Left parenthesis (()
-
Right parenthesis ())
1.8.3 Group Attributes for Provisioning
Table 1-12 provides information about group attribute mappings for provisioning.
1.8.4 Role Attributes for Provisioning
Table 1-13 provides information about role attribute mappings for provisioning.
1.9 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
-
Chapter 2, "Deploying the Connector" describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
-
Chapter 3, "Using the Connector" describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
-
Chapter 4, "Extending the Functionality of the Connector" describes the procedures to perform if you want to extend the functionality of the connector.
-
Chapter 5, "Testing and Troubleshooting" describes the procedure that you must perform to test the connector. In addition, this chapter provides instructions for identifying and resolving some commonly encountered errors.
-
Chapter 6, "Known Issues" lists known issues associated with this release of the connector.
-
Appendix A, "Attribute Mappings Between Oracle Identity Manager and Oracle Internet Directory" provides information about attribute mappings between Oracle Identity Manager and Oracle Internet Directory.