1 About the Connector
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide discusses the connector that enables you to use IBM AS/400 either as a managed (target) resource or as an authoritative (trusted) source of identity data for Oracle Identity Manager.
The advanced connector for IBM AS/400 provides a native interface between IBM AS/400 and Oracle Identity Manager. The connector functions as a trusted virtual administrator on the target system, performing tasks related to creating and managing user profiles.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system is reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manager.
In the IBM AS/400 context, the term "user profile" is synonymous with "user account." If IBM AS/400 is configured as a target resource, then user profiles on IBM AS/400 correspond to accounts or resources assigned to OIM Users. In contrast, if IBM AS/400 is configured as a trusted source, then user profiles on IBM AS/400 correspond to OIM Users.
Note:
In earlier releases, IBM AS/400 was known as IBM AS/400 or IBM i5/AS. Because the connector development project started before the change in nomenclature was formally announced by IBM, the IBM AS/400 connector code, scripts, and nomenclature applied in the connector pack may contain instances of IBM AS/400 or IBM i5/AS. These instances are not documentation errors in this guide.
This chapter is divided into the following sections:
1.1 Certified Components
Table 1-1 lists the certified components.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
|
|
JDK |
The JDK version can be one of the following:
|
|
IBM i5/AS and AS/400 releases V5R2, V5R3, V5R4, V6R1 |
|
|
Infrastructure Requirements: Message transport layer between the Oracle Identity Manager and the mainframe environment |
JTOpen versions 5.1.1 and 5.2 (open source or commercially supported version) |
|
IBM AS/400-authorized account with SystemAdministrators privileges Section 2.9, "Installing and Configuring the LDAP Gateway" describes the procedure to specify the credentials of this user. |
1.2 Usage Recommendation
Depending on the Oracle Identity Manager version that you are using, you must deploy and use one of the following connectors:
-
If you are using an Oracle Identity Manager release that is 9.1.0.1 or later and earlier than Oracle Identity Manager 11g Release 1 (11.1.1.5.0), then use the 9.0.4.x version of this connector.
-
If you are using Oracle Identity Manager 11g Release 1 (11.1.1.5.0) or later, then use the latest 11.1.1.x version of this connector.
1.3 Certified Languages
The connector supports the following languages:
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
See Also:
On Oracle Identity Manager release 9.1.0.x, see Oracle Identity Manager Globalization Guide.
On Oracle Identity Manager release 11.1.1, see Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
1.4 Connector Architecture
The connector architecture is described in the following sections:
1.4.1 Connector Components
The connector contains the following components:
-
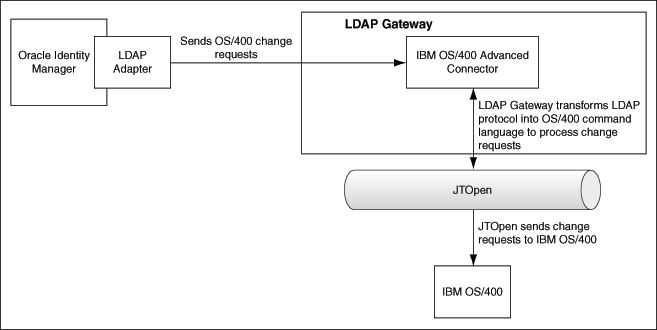
LDAP Gateway: The LDAP Gateway receives instructions from Oracle Identity Manager in the same way as any LDAP version 3 identity store. These LDAP commands are then converted into native commands for IBM AS/400 and sent to the Provisioning Agent. The response, which is also native to IBM AS/400, is parsed into an LDAP-format response and returned to Oracle Identity Manager.
-
JTOpen Provisioning Agent: The connector provides the provisioning functionality through the JTOpen Provisioning Agent. The Provisioning Agent receives IBM AS/400 identity and authorization change events from the LDAP Gateway. These events are processed against the IBM AS/400 authentication repository, in which all provisioning updates from the LDAP Gateway are stored. The response is parsed and returned to the LDAP Gateway.
-
Message Transport Layer: The message transport layer enables the exchange of messages between the LDAP Gateway and the Provisioning Agent. JTOpen is used as the messaging protocol for the message transport layer.
See Also:
-
JTOpen Web site at the following URL for information about the JTOpen project:
-
IBM Toolbox for Java documentation at the following URL for information about the JTOpen functionality:
http://www-03.ibm.com/servers/eserver/iseries/toolbox/overview.html
-
1.4.2 Connector Operations
This section provides an overview of the following connector processes:
1.4.2.1 Full Reconciliation Process
Full reconciliation involves fetching existing user profile data from the mainframe to Oracle Identity Manager. If you configure the target system as a target resource, then the user profile data is converted into accounts or resources for OIM Users. If you configure the target system as a trusted source, then the user profile data is used to create OIM Users.
The following is a summary of the full reconciliation process:
Note:
Detailed instructions are provided later in this guide.
-
You specify the full reconciliation configuration in the AS400 User Reconciliation scheduled task (located in the Oracle Identity Manager 9.x Design console).
-
In the scheduled task form, you enter a list of user IDs of the user profiles that you want to reconcile. If no users are specified, then all existing users on the target system will be reconciled.
-
You specify whether you want to configure IBM AS/400 as a target resource or trusted source of Oracle Identity Manager.
-
You set a start time for the task and run the scheduled task. The task sends the list of user IDs to the LDAP Gateway.
-
The LDAP Gateway encrypts the list of user IDs and then sends it to the Provisioning Agent on the mainframe. The user ID and status of each user profile is stored in an internal meta-store, and a flag is set for the user profile in the meta-store.
-
The Provisioning Agent encrypts user profile data for the specified user IDs and then passes this data to the LDAP Gateway.
-
The LDAP Gateway decrypts the user profile data and passes it to Oracle Identity Manager.
-
The next step depends on the setting in the scheduled task:
-
If you configure the target system as a target resource, then the user profile data is converted into accounts or resources assigned for OIM Users.
-
If you configure the target system as a trusted source, then the user profile data is used to create OIM Users.
-
1.4.2.2 Incremental Reconciliation Process
The following is a summary of the incremental reconciliation process:
-
IBM AS/400 identity and authorization events take place in the target system. After each event, the modified time stamp on the changed profile is updated.
Note:
Identity and authorization events in the IBM AS/400 system include the running of a command, real-time password synchronization, creation or deletion of a user, or a change in user data.
-
You specify a date/time timestamp in the OIM As400 IT Resource. The AS400 User Reconciliation scheduled task, using the LDAP Gateway, sends scheduled requests to the Provisioning Agent to search the target system for events made after the specified timestamp.
-
The Provisioning Agent encrypts user profile data for the events and then passes this data to the LDAP Gateway.
-
The LDAP Gateway decrypts the user profile data and passes it to Oracle Identity Manager.
-
The next step depends on the setting in the scheduled task:
-
If you configure the target system as a target resource, then the user profile data is converted into accounts or resources assigned for OIM Users.
-
If you configure the target system as a trusted source, then the user profile data is used to create OIM Users.
-
1.4.2.3 Incremental (Real-Time) Reconciliation Process
Real-time reconciliation is initiated by the EXIT(s) that work in conjunction with the Reconciliation Agent. See Figure 1-1.
Figure 1-1 Incremental (Real-Time) Reconciliation Process
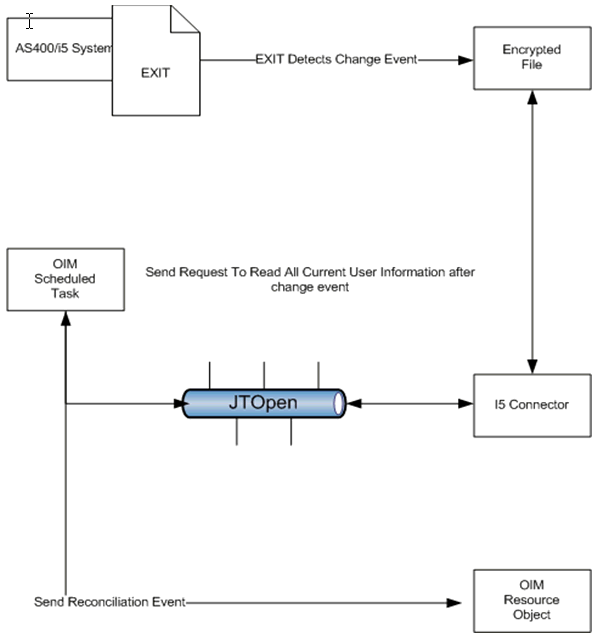
Description of "Figure 1-1 Incremental (Real-Time) Reconciliation Process"
-
IBM AS/400 identity and authorization events take place in the target system. After each event the EXIT will populate an encrypted file on the OS that contains all changed events.
Note:
Identity and authorization events in the IBM AS/400 system include the running of a command, real-time password synchronization, creation or deletion of a user, or a change in user data.
-
To retrieve these events you run the newAS400 Reconcile All Changed Users scheduled task. This process will read the file and store the contents of event changes in an internally configured directory in the LDAP (based on the domainOu configuration). After the contents have been stored in the Internal LDAP the Task will query the internal store based on the Last Mod Timestamp in the OIM As400 IT Resource and reconcile any changes during that time to OIM.
-
The next step depends on the setting in the scheduled task:
-
If you configure the target system as a target resource, then the user profile data is converted into accounts or resources assigned for OIM Users.
-
If you configure the target system as a trusted source, then the user profile data is used to create OIM Users.
-
1.4.2.4 Provisioning Process
Figure 1-2 shows the flow of data during provisioning.
The following is a summary of the provisioning process:
-
Provisioning data submitted from the Administrative and User Console is sent to the LDAP Gateway.
-
The LDAP Gateway translates the provisioning data to IBM AS/400 commands.
-
The data is encrypted and then sent to the JTOpen Provisioning Agent, which also functions as the message transport layer.
-
The connector also updates the internal meta-store of the LDAP Gateway with the changes in user data.
-
JTOpen decrypts the data, sends the data to the IBM AS/400 repository, and returns a success or error message to the LDAP Gateway.
1.5 Features of the Connector
This section discusses the following topics:
-
Section 1.5.1, "Target Resource and Trusted Source Reconciliation"
-
Section 1.5.3, "Encrypted Communication Between the Target System and Oracle Identity Manager"
1.5.1 Target Resource and Trusted Source Reconciliation
You can use the connector to configure IBM AS/400 as either a target resource or trusted source of Oracle Identity Manager.
1.5.2 Full and Incremental Reconciliation
After you deploy the connector, you can perform full reconciliation to bring all existing user profile data from the target system to Oracle Identity Manager. Additionally, change-based or incremental reconciliation is available. Both forms of reconciliation are configured using the scheduled reconciliation task.
Section 4.1, "Configuring Reconciliation" describes the procedure.
You can perform a full reconciliation run at any time.
1.5.3 Encrypted Communication Between the Target System and Oracle Identity Manager
AES-128 encryption is used to encrypt data that is exchanged between the LDAP Gateway and the Provisioning Agent on the mainframe.
1.5.4 High Availability Feature of the Connector
If you have multiple installations of the target system, then you can configure one LDAP Gateway to work with each installation of the target system. Alternatively, you can configure a single LDAP Gateway installation to work with multiple installations of the target system. Section 5.5, "Configuring the Connector for Multiple Installations of the Target System" describes the procedure.
1.6 Connector Objects Used During Reconciliation and Provisioning
The following sections provide information about connector objects used during reconciliation and provisioning:
-
Section 1.6.1, "Supported Functions for Target Resource and Trusted Source Reconciliation"
-
Section 1.6.3, "User Attributes for Target Resource Reconciliation and Provisioning"
-
Section 1.6.4, "User Attributes for Trusted Source Reconciliation"
1.6.1 Supported Functions for Target Resource and Trusted Source Reconciliation
The connector supports reconciliation of user data from the following events:
-
Create user
-
Modify user
-
Delete user
-
Password change
-
Disable user
-
Enable user
1.6.2 Supported Functions for Provisioning
Table 1-2 lists the provisioning functions supported by the connector.
Table 1-2 Supported Provisioning Functions
| Function | Description | Mainframe Command |
|---|---|---|
|
Create users |
Adds new users on IBM AS/400 |
CRTUSRPRF |
|
Modify users |
Modifies user data on IBM AS/400 |
CHGUSRPRF |
|
Delete users |
Removes users from IBM AS/400 |
DLTUSRPRF |
|
Change passwords |
Changes user passwords on IBM AS/400 in response to password changes made on Oracle Identity Manager through user self-service |
CHGUSRPRF |
|
Reset passwords |
Resets user passwords on IBM AS/400 The passwords are reset by the administrator. |
CHGUSRPRF |
|
Revoking user accounts |
Sets IBM AS/400 users to a REVOKED state |
CHGUSRPRF |
|
Resuming user accounts |
Sets IBM AS/400 users to an ENABLED state |
CHGUSRPRF |
1.6.3 User Attributes for Target Resource Reconciliation and Provisioning
Table 1-3 lists attribute mappings between IBM AS/400 and Oracle Identity Manager for target resource reconciliation and provisioning.
Note:
You can add new attributes for target resource reconciliation. Section 5.1, "Adding New Attributes for Target Resource Reconciliation" describes the procedure.
Table 1-3 User Attributes for Target Resource Reconciliation and Provisioning
| Oracle Identity Manager Field | IBM AS/400 Field | Description |
|---|---|---|
|
uid |
USER |
User login ID |
|
cn |
NAME |
User full name |
|
sn |
NAME |
User last name |
|
userPassword |
PASSWORD |
Password used to login |
|
owner |
OWNER |
Owner of the user profile |
|
status |
STATUS |
User status (enable, disable) |
|
spcaut |
SPECAUTH |
Special access permissions for the user |
|
usrcls |
USRCLS |
Special access control for the user |
|
inlprg |
INLPRG |
User initial program |
|
text |
TEXT |
Free form text field |
|
lmtcpb |
LMTCPB |
Limit capabilities |
|
jobd |
JOBD |
Job description |
|
supgrpprf |
SUPGRPPRF |
Supplemental group |
|
inlmnu |
INLMNU |
Initial menu |
|
grpprf |
GRPPRF |
Group profile |
|
passwordExpire |
PWDEXP |
User password is set to expire |
1.6.4 User Attributes for Trusted Source Reconciliation
Table 1-4 lists attribute mappings between IBM AS/400 and Oracle Identity Manager for trusted source reconciliation.
1.6.5 Reconciliation Rule
See Also:
Oracle Identity Manager Connector Concepts for generic information about reconciliation matching and action rules
During target resource reconciliation, Oracle Identity Manager tries to match each user profile fetched from IBM AS/400 with existing IBM AS/400 resources provisioned to OIM Users. This is known as process matching. A reconciliation rule is applied for process matching. If a process match is found, then changes made to the user profile on the target system are copied to the resource on Oracle Identity Manager. If no match is found, then Oracle Identity Manager tries to match the user profile against existing OIM Users. This is known as entity matching. The reconciliation rule is again applied during this process. If an entity match is found, then an IBM AS/400 resource is provisioned to the OIM User. Data for the newly provisioned resource is copied from the user profile.
During trusted reconciliation, the same reconciliation rule is applied for entity matching. If an entity match is found, then an OIM User is created out of the data in the reconciliation event.
The following is the reconciliation rule for both target resource and trusted source reconciliation:
Rule name: AS400AdvReconRule
Rule element: User Login Equals uid
In this rule element:
-
User Login is the User ID field on the process form and the OIM User form.
-
uid is the USER attribute on IBM AS/400.
After you deploy the connector, you can view this reconciliation rule by performing the following steps:
-
On the Design Console, expand Development Tools and then double-click Reconciliation Rules.
-
Search for and open the AS400AdvReconRule rule.
1.6.6 Reconciliation Action Rules
Reconciliation action rules specify actions that must be taken depending on whether or not matching IBM AS/400 resources or OIM Users are found when the reconciliation rule is applied. Table 1-5 lists the reconciliation action rules for this connector.
Table 1-5 Reconciliation Action Rules
| Rule Condition | Action |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Note:
No action is performed for rule conditions that are not predefined for this connector. You can define your own action rules for such rule conditions. See Oracle Identity Manager Design Console Guide for information about modifying or creating reconciliation action rules.
After you deploy the connector, you can view the reconciliation action rules for target resource reconciliation by performing the following steps:
-
On the Design Console, expand Resource Management and double-click Resource Objects.
-
Search for and open the OIMAs400ResourceObject resource object.
-
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector.