| Oracle® Adaptive Access Manager Concepts Release 10g (10.1.4.5) Part Number E12049-03 |
|
|
View PDF |
| Oracle® Adaptive Access Manager Concepts Release 10g (10.1.4.5) Part Number E12049-03 |
|
|
View PDF |
Adaptive Risk Manager, a core component of Oracle Adaptive Access Manager, enables an enterprise to evaluate and score risk. It can do so for each online login and transaction. As a result, the solution increases authentication security in real-time for high-risk situations.
Adaptive Risk Manager provides a strong second- and third-factor of security for the enterprise. It can serve as a standalone solution that offers increased security, with no change to the user experience, and it can also be used in combination with Adaptive Strong Authenticator. Together the components provide further anti-identity theft and fraud protection.
Adaptive Risk Manager verifies each user's computer and location ("something you have"). It also verifies a user's behavior patterns to confirm identity ("something you are"). These verifications are added to existing enterprise requirements for login/password credentials and additional knowledge-based authentication ("something you know"). This offers the enterprise multiple strong factors of antifraud protection.
Adaptive Risk Manager uses dozens of "tentacles," including proprietary one-time use secure cookies, Flash objects, and other patent-pending technologies. These serve to recognize and fingerprint the device you typically use to log in to your computer, laptop, a kiosk and so on. In this way, Adaptive Risk Manager makes your personal computer your second factor-without requiring any change in your behavior.
Also patent pending is the unique process used for device fingerprinting. It is a process that creates a fingerprint good for use one-time only. Therefore, it is immediately invalidated if a fraudster attempts to reuse it.
Adaptive Risk Manager evaluates the pre-, post-, and in-session characteristics of each transaction. This ensures fraud detection and transactional integrity.
The solution's proprietary, real-time device and location fingerprinting can determine whether a login attempt is high risk. Prior to authentication, these determinations are made with a high probability. Subsequently, each individual transaction attempted in session is further scored for risk, resulting in an even higher level of confidence for the user.
Adaptive Risk Manager then governs the institution's response to risk, whether it is an alert, user challenge, or secondary authentication. This is done in real-time using Adaptive Strong Authenticator.
Adaptive Risk Manager is an open, standards-based system. It is available as a single-server installation or a cluster of servers that can be integrated with existing enterprise Web applications using prepackaged APIs.
Adaptive Risk Manager includes the following standard features:
An Engine. State-of-the-art, real-time rules and risk-scoring is provided.
Integration support. Third-party integration is supported via open APIs and shared authentication and fraud services infrastructure.
Proprietary fingerprinting. Patent-pending fingerprinting methods for device, location, and workflow use second and third factors for identification.
Models and rules. Customizable scenarios invoke any set of rules. They are driven entirely by the needs of the organization and the level of security defenses required.
Administration tools. Comprehensive user interfaces are provided to maximize leverage and usage of the application. This includes dashboards, reports, and modeling tools.
The Adaptive Risk Manager engine offers state-of-the-art, real-time rules and risk scoring. The robust engine combines analytics, including states, rules, and pattern recognition. This ensures intelligent real-time operations and maximum enterprise protection against online fraud.
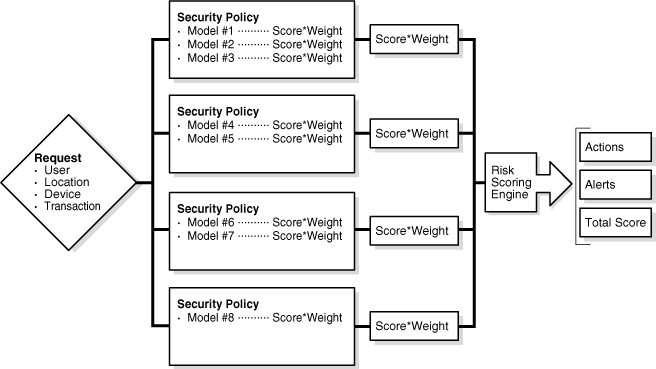
Adaptive Risk Manager analytics are designed for high performance and scalability. The Adaptive Risk Manager engine works by automatically preanalyzing policies (sets of modules) and models (sets of rules). Then it actively monitors each user's transactional data flows to identify those elements that might impact the models.
The Adaptive Risk Manager engine uses a proprietary structure to simultaneously maintain the necessary parameters. It then updates and tests them against the relevant models.
The Adaptive Risk Manager engine triggers actions and alerts based upon rules. These rules are housed in models configurable by the institution and are established according to the institution's policies:
Security policies (pre- and post-authentication)
Fraudster rules (subset)
Transaction policies (in session)
Third-party data
Security policies (pre- and post-authentication)
Security policies use standards for detecting fraudster behavior developed from cross-industry best practices:
Anomaly detections
Misuse detections
Intrusion detections
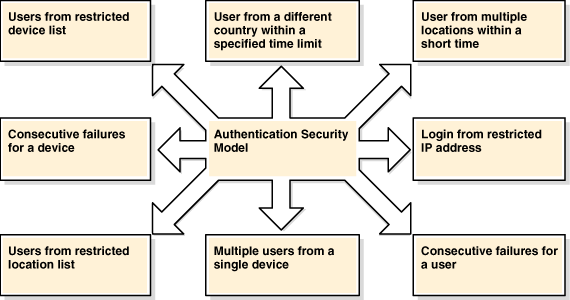
Predefined fraudster models (the figure shows a subset of the fraudster rules that are standard in Adaptive Risk Manager)
Customizable models
Adaptive Risk Manager's extensive fraudster models are enriched by Oracle's cross-industry customer base. Its customer base covers financial services, e-commerce, health care, and the military, among others.
Fraudster rules are a collection of some basic anti-fraud rules.
Transaction policies (in session)
Transaction policies invoke rules based upon parameters established by the business for mitigation of transaction risk, including
In-session transaction monitoring
Business-defined transaction rules
Key value-driven logic
Customizable models
Third-party data offers prepackaged integration with third-party data providers, developed through Oracle's strategic partnerships. Thus, third-party data can be called and evaluated in Adaptive Risk Manager as part of the risk score:
Adaptive Risk Manager risk scoring is a product of numerous fraud detection inputs such as a valid user, device, location, or pattern. Also included are third-party data and historical customer data. These inputs are weighted and analyzed in real-time within Adaptive Risk Manager's fraud analytics engine.
Design
Adaptive Risk Manager's design features are listed below:
Any custom rule can be set, according to business need, to become activated if a transaction is scored above a certain risk threshold.
Nested models can be assigned to ensure a higher degree of accuracy for the risk score. A nested model is a secondary model. It is used to further quantify the risk score in instances where the original result output by the system is inconclusive. A nested model is run only when a specific sequence of answers is returned from the primary model. Nested models therefore reduce false positives and negatives.
Adaptive Risk Manager is configured, based upon rules, to initiate a response to an elevated risk score (see "Models and Rules"). Responses are documented below.
Internal flag/watch list is used for follow-up investigation within the institution.
Secondary Authentication - Out of Band
One-Time-Password (OTP) through Interactive Voice Response (IVR) is available from our partners.
Secondary Authentication - Online
Challenge questions.
Adaptive Strong Authenticator can be used to provide further defenses against in-session attacks. It can also enable "weakest link" security by protecting the challenge/response process.
Tokens, smart cards, identity proofing, and so forth (available from partners).
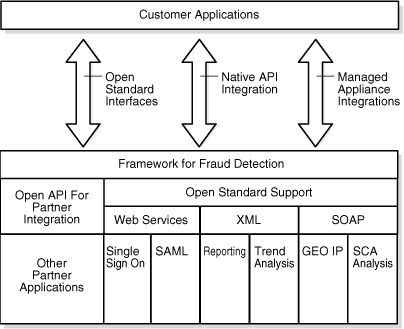
Adaptive Risk Manager is an open, standards-based platform. It is designed for minimal integration work and maximum compatibility with existing enterprise and third-party systems. Adaptive Risk Manager features best-of-breed integration capabilities that enable the institution to speed up and simplify its deployment. These capabilities also enable the institution to leverage data from external systems for Adaptive Risk Manager.
Oracle Adaptive Access Manager is standard J2EE WAR. It doesn't have EJB component and supports all standard J2EE servlet containers out of the box. There is no special configuration required on the container side, except setting the JNDI and Access Control Roles using the container provided mechanism.
Oracle Adaptive Access Manager provides generic groups, which can be populated with external data and can be used in the rules engine. The rule engine itself is JSR94 compliant and can be used to write customized rules. Additionally, it provides interface classes, which can be overwritten to extend the product (configurable action infrastructure to support custom rule actions, configurable Adaptive Strong Authenticator web application for supporting complex integration, encryption algorithm options, etc.).
A list of prepackaged APIs is available in the current version of Adaptive Risk Manager. APIs are available in the areas of Active Directory, Lightweight Directory Access Protocol, fraud, Annotation Markup Language, customer relationship management, Single Sign-On, compliance, and mainframe systems.
Much of Adaptive Risk Manager's power lies is in its patent-pending fingerprinting methods for device and location. Adaptive Risk Manager stores and uses multiple second and third factors to establish these fingerprints. The figure below shows a partial list. Additions are ongoing via industry partnerships and Oracle's own research and development.
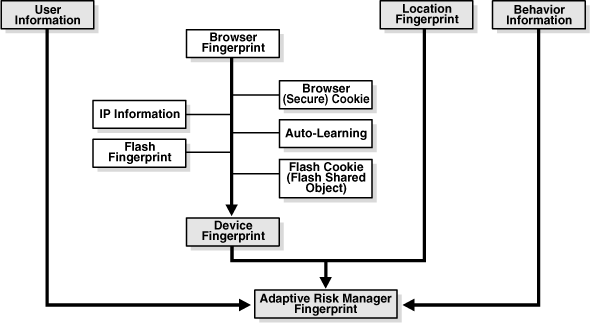
Adaptive Risk Manager monitors a comprehensive list of device attributes. If any attributes are not available the device can still be fingerprinted.
Adaptive Risk Manager's patent-pending method for device fingerprinting generates a one-time fingerprint for each user session. That fingerprint is unique to the individual's device. It is replaced upon each subsequent visit with another unique fingerprint. This ensures that a fingerprint cannot be stolen and reused for fraud
For 10.1.4.5, a device registration feature is available that allows a user to flag the computer he is using as a safe device. The customer can then configure the rules to challenge a user that is not coming from one of his registered devices. Device registration is available as a standard feature in Oracle Adaptive Access Manager. The feature can be turned on, although it is turned off by default in the product.
Adaptive Risk Manager contains sophisticated location fingerprinting capabilities. A blend of IP intelligence data is used to identify locations by geography and many other data points crucial to accurate fraud detection.
The benefits of Adaptive Risk Manager fingerprinting and risk scoring are cumulative. Device and location fingerprints are already verified by the time a user attempts a transaction in session. Thus, Oracle Adaptive Access Manager achieves an additional level of confidence.
To further enhance Oracle's proprietary methods, Adaptive Risk Manager also features prepackaged integration with partners. These partner solutions also monitor the customer experience at the individual user level.
Third-party data can be fed into the Adaptive Risk Manager analytics engine as part of the fingerprint. This enhances the overall picture of customer activity.
Auto-learning, a feature available in the 10.1.4.5 release, is a profiling process in which Adaptive Risk Manager identifies behavior patterns (buckets) based on the parameters the administrator specifies. Adaptive Risk Manager then automatically records/maintains the bucket memberships of the users/devices/locations (entities in general) over time so that the data that is gathered can be used as a way to evaluate risk.
Institutions can deploy Adaptive Risk Manager in a variety of customizable scenarios to invoke any set of rules. These rules are driven entirely by the needs of the institution and the level of security required. Rules can also be applied in any combination to different segments of users. This can be done in any way the institution wants to segment its user population.
As previously discussed, Adaptive Risk Manager monitors and evaluates activity by four main criteria: user, device, location, and workflow. Each criterion contains various pieces of Adaptive Risk Manager data. That data is used to detect fraud risk (and, optionally, data seamlessly integrated from third parties as well).
Within Adaptive Risk Manager, data is organized into groups corresponding to these criteria. These groups are then linked to compatible models containing rules used to evaluate activity.
Over time, there are several ways the institution can continue to expand and develop the models. For more information about Rules and Models, refer to Chapter 4, "Rules and Models."
In 10.1.4.5, a Rule Template Editor feature is available that allows the user to create and edit rule templates without having to go to the XML and write them.
Comprehensive user interfaces are a standard part of Adaptive Risk Manager to help the institution leverage the system.
The dashboard provides real-time visibility into potential fraudulent activities. It provides performance and summary statistics as well as reports on locations, scoring, devices, security, and performance. These help analyze online traffic; identify suspicious behavior; and design rules for proactive fraud prevention, risk monitoring, and case management.
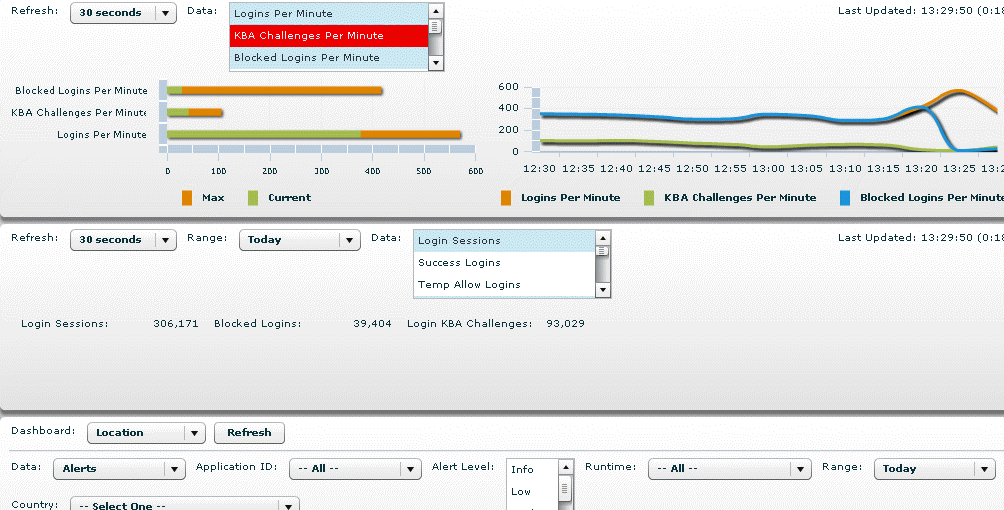
Performance and Summary
The performance and summary panels provide views of statistics on the current rate of logins and an overview of activity. This includes login sessions, successful logins, blocked logins, alerts, rules triggered, and rules run.
Dashboards
The dashboard panel provides access to five dashboard types: Location, Scoring, Device, Security, and Performance. The dashboard offers a real-time view of the secured site. It delivers a high-level personalized business view of the current status of user behavior and key transactions.
Location
Location provides aggregated location statistics including location, device, and users detected.
Scoring
Scoring displays statistics on risk score, runtime, and the number of sessions.
Devices.
Device provides statistics on the browser, OS, number of sessions, and percent of total.
Security
Security displays statistics on alerts that were run during the time frame, including runtime; alert level and type; and information on rules that were run during the time frame, such as model, runtime, action, and count.
Performance
Performance displays statistics on models, rules, actions, and APIs performance.
Oracle Adaptive Access Manager's comprehensive reporting area contains reports to assist with enterprise-level and individual customer-level fraud management. The reports enable detailed risk management and analysis through drill-down capabilities for viewing information. Such views are by location, device, user, and transactions over specific time ranges and schedules. Reports are editable through the BI Publisher. Column labels and contents can be editable. Also, aggregates and graphing can be added to reports.
Configurable Actions allow a user to create new supplementary actions that occur after the running of rules.
Oracle Adaptive Access Manager provides a framework to support any kind of transaction by mapping client-specific data into the generic data model that supports the framework.
Starting in the 10.1.4.5 release, existing enumerations and their elements and properties can be edited in Adaptive Risk Manager. New enumerations can also be created to customize Adaptive Risk Manager.
Investigation management offers tools needed by fraud investigators (agents) to conduct investigation process. A new case type, agent cases enable fraud investigation agents to obtain information and track the progress of the investigation (case lifecycle). Linked sessions and related sessions and cases provide investigators a way to quickly narrow in on the important data they need to resolve a case.