| Oracle® Adaptive Access Manager Concepts Release 10g (10.1.4.5) Part Number E12049-03 |
|
|
View PDF |
| Oracle® Adaptive Access Manager Concepts Release 10g (10.1.4.5) Part Number E12049-03 |
|
|
View PDF |
Common authentication methods today have many weaknesses:
Data remains raw between the point of creation and where the encryption process is invoked. Moving raw data over open lines increases the opportunity for theft.
Every protection implemented on a data source depends on a human being to maintain its state of security, which can be compromised.
Any new computing environment can be well-studied and misused because of its predictable behavior.
Oracle Adaptive Access Manager's Adaptive Strong Authenticator was designed specifically to overcome these limitations.
Leveraging a soft, two-factor authentication solution, Adaptive Strong Authenticator provides fraud protection against online identity theft. It does so by encrypting credential data inputs at the point of entry. This ensures maximum user protection because information never resides on a user's computer nor does information reside anywhere on the Internet where it can be vulnerable to theft.
As corporations embrace the Internet, they must ensure that customer transactions and data are safe. Adaptive Strong Authenticator enables corporations to deploy a highly effective security solution that offers their customers the required protection as well as the ease-of-use needed to engage in and grow online relationships.
Adaptive Strong Authenticator is hardware- and software-independent and does not rely upon cached data. End-users can invoke the authentication process from any browser, over any network (public, private, Wi-Fi, and kiosk). They can also use any user touch-point to protect their information during session initiation or during in-session transactions.
Low Cost of Ownership
An added benefit of Adaptive Strong Authenticator is that it offers a low cost of ownership. This is in comparison to other authentication alternatives. The solution does not require any special databases, proprietary software, extra hardware, or third-party servers. Furthermore, there are no customer support needs to consider associated with lost or damaged cards and tokens.
Using Adaptive Strong Authenticator, corporations can defend their customers and their data against the most potent fraudulent attacks.
Table 2-1 Potent Fraudulent Attacks
| Attack | Defense |
|---|---|
|
The PIN data required to authenticate only exists in a form understood by the user and the server. Therefore, it can't be interpreted and used for fraud. An impostor Internet site cannot simulate the operational aspects of the authentication. |
|
|
Equipping end-users with their own personalized device is the first step. Ensuring Adaptive Strong Authenticator is used for entry of all sensitive credentials (password, PIN, challenge questions, and others) is the second. Finally, Adaptive Risk Manager prevents the fraudulent use of credentials if end-users have fallen prey to phishing. |
|
|
Adaptive Strong Authenticator foils keyboard, mouse-click, and screen-capture loggers; cookie hijackers; "over the shoulder" spies; and all other forms of known attacks. This is because no sensitive data is entered using the keyboard, mouse, or cookies nor is any sensitive data handled by the browser. |
|
|
Adaptive Risk Manager collects and evaluates end-user data points. These data points can be used to authorize, challenge, deny, or put online transactions on hold. |
|
|
Adaptive Strong Authenticator generates a unique set of random data for every user session. It is virtually difficult for a password to be guessed and reused. |
Adaptive Strong Authenticator is an enterprise-licensed platform that includes a number of user interfaces. These interfaces are for managing fraud and identity theft protection. Whether making payments, accessing sensitive documents, entering passwords, or answering challenge questions, users and data are protected.
QuestionPad takes data entry to another security level. With challenge questions becoming more commonly used in financial institutions and other enterprises, it opens up another target for fraudsters. QuestionPad addresses this issue by changing the way users enter these new credentials.

QuestionPad offer several deployment options. Oracle can host the challenge questions and provide the question bank. Alternatively, the question bank can be integrated with internal customer information databases. They can also be integrated with external third-party question providers.
PinPad is an authentication entry device used to enter a numeric PIN. It can be invoked at the time of login or transaction.

KeyPad is a configurable virtual keyboard. It can be used to enter alphanumeric and special characters found on a traditional keyboard. That makes it ideal for entering passwords and other sensitive alphanumeric information.
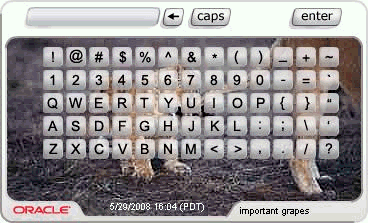
Two deployment options are available:
Without Oracle Adaptive Access Manager Web Application
With Oracle Adaptive Access Manager Web Application
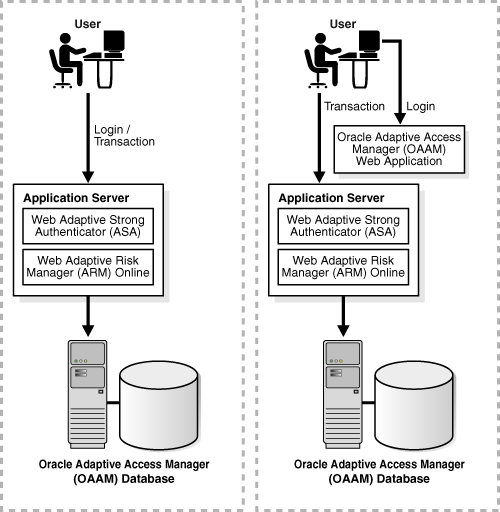
With this deployment approach, the client stores all credentials. The client also uses the Adaptive Strong Authenticator library only for encoding and decoding inputs.