| Oracle® Adaptive Access Manager Developer's Guide Release 10g (10.1.4.5) Part Number E12052-03 |
|
|
View PDF |
| Oracle® Adaptive Access Manager Developer's Guide Release 10g (10.1.4.5) Part Number E12052-03 |
|
|
View PDF |
This chapter describes the process for integrating Oracle Adaptive Access Manager's Adaptive Strong Authenticator with Oracle Access Manager. Integrating the two will allow you to use Oracle Adaptive Access Manager's Adaptive Strong Authenticator virtual authentication pads to identify users attempting to access Oracle Access Manager's protected applications.
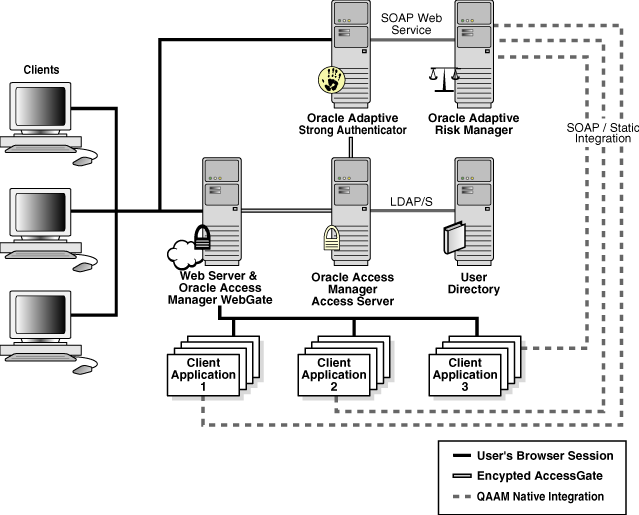
Using these products in combination will allow you fine control over the authentication process and full capabilities of pre-/post- authentication checking against Adaptive Risk Manager models.
This integration process assumes that the Oracle Access Manager environment has been configured to protect simple HTML resources using two different authentication schemes. Authentication schemes protect the client application's url.
The first authentication scheme uses Basic Over LDAP.
The second authentication scheme is a higher-security level and integrates Adaptive Strong Authenticator by using a custom form-based authentication scheme.
For more information, refer to the Oracle Access Manager Integration Guide.
The following set of components is required for this implementation:
Oracle Adaptive Access Manager
Oracle Access Manager 10_1_4_01 with Patch 6158232
an Application Server
Oracle Access Manager SDK
Except where specified, the following procedures are required to complete the integration of Oracle Access Adaptive Manager and Oracle Access Manager.
Configure Oracle Access Manager AccessGate for Adaptive Strong Authenticator Embedded AccessGate
Configure Oracle Access Manager AccessGate for Adaptive Strong Authenticator Front-End Web Server
Configure Oracle Access Manager Authentication Scheme for the Adaptive Strong Authenticator
Configure Oracle Access Manager Host Identifiers for Adaptive Strong Authenticator (Optional)
Install WebGate for Adaptive Strong Authenticator Front-End Web Server
Add ASDK Library Path to Adaptive Strong Authenticator Application Properties
Add ASDK Library Path to Adaptive Strong Authenticator Server Properties
Configure Oracle Access Manager Domain to use Adaptive Strong Authenticator Authentication
Before installing the Access Server SDK (ASDK), you must define the Oracle Access Manager server-side settings for the AccessGate that the ASDK will use for communication.
This section shows you how to define the new AccessGate for the embedded Adaptive Strong Authenticator AccessGate.
Note:
This chapter will not explain in detail all of the settings involved with Oracle Access Manager AccessGates.Steps
Launch Internet Explorer.
Log in to Oracle Access Manager.
For example, http://<oam_hostname>/access/oblix.
Click Access System Console.
Log in as <Administrator>.
Click Access System Configuration.
Click Add New AccessGate.
Using the oaamAccessGate configuration settings shown below, create a new AccessGate and assign it to an Access Server.
Table 8-1 oaamAccessGate Configuration
| Parameter | Value |
|---|---|
|
AccessGate Name |
oaamAccessGate |
|
Description |
AccessGate for Oracle Adaptive Access Manager-Adaptive Strong Authenticator authentication |
|
Hostname |
<hostname> |
|
Port |
<port> |
|
AccessGate Password |
<passwd> |
|
Debug |
<Off> |
|
Maximum user session time (seconds) |
3600 |
|
Idle Session Time (seconds) |
3600 |
|
Maximum Connections |
1 |
|
Transport Security |
<Open> |
|
IP Validation |
<On> |
|
IP Validation Exception |
<leave blank> |
|
Maximum Client Session Time (hours) |
24 |
|
Failover Threshold |
1 |
|
Access server timeout threshold |
<leave blank> |
|
Sleep for (seconds) |
60 |
|
Maximum elements in cache |
10000 |
|
Cache timeout (seconds) |
1800 |
|
Impersonation Username |
<leave blank> |
|
Impersonation Password |
<leave blank> |
|
Access Management Service |
<On> |
|
Preferred HTTP Cookie Domain |
<domain_name> |
|
Preferred HTTP Host |
<hostname>:<port> |
|
Deny on not protected |
<Off> |
|
CachePragmaHeader |
no-cache |
|
CacheControlHeader |
no-cache |
|
LogOutURLs |
<leave blank> |
|
User Defined Parameters |
<leave blank> |
|
Assign An Access Server (Primary |
<hostname>:<port> |
|
Number of Connections |
1 |
The Oracle Adaptive Access Manager's Adaptive Strong Authenticator/Oracle Access Manager integration involves two Oracle Access Manager AccessGates: one for fronting the Web server (a traditional WebGate) to Adaptive Strong Authenticator and one for the embedded AccessGate. This section explains how to configure the Oracle Access Manager AccessGate that fronts the Web server to Adaptive Strong Authenticator.
Steps
Click Add New AccessGate.
Use the settings in the table below to create a new AccessGate and assign it an Access Server
Note:
The Adaptive Strong Authenticator AccessGate settings (described in the Configure Oracle Access Manager AccessGate for Adaptive Strong Authenticator Embedded AccessGate section) and the OHS WebGate settings are identical (except for the AccessGate names) because OHS is also a server for the Adaptive Strong Authenticator application. In some deployments, these might differ.Table 8-2 ohsWebGate Configuration
| Parameter | Value |
|---|---|
|
AccessGate Name |
ohsWebGate |
|
Description |
AccessGate for Web server hosting Adaptive Strong Authenticator application |
|
Hostname |
<hostname> |
|
Port |
<port> |
|
AccessGate Password |
<passwd> |
|
Debug |
<Off> |
|
Maximum user session time (seconds) |
3600 |
|
Idle Session Time (seconds) |
3600 |
|
Maximum Connections |
1 |
|
Transport Security |
<Open> |
|
IP Validation |
<On> |
|
IP Validation Exception |
<leave blank> |
|
Maximum Client Session Time (hours) |
24 |
|
Failover Threshold |
1 |
|
Access server timeout threshold |
<leave blank> |
|
Sleep for (seconds) |
60 |
|
Maximum elements in cache |
10000 |
|
Cache timeout (seconds) |
1800 |
|
Impersonation Username |
<leave blank> |
|
Impersonation Password |
<leave blank> |
|
Access Management Service |
<On> |
|
Preferred HTTP Cookie Domain |
.<domain_name> |
|
Preferred HTTP Host |
<hostname>:<port> |
|
Deny on not protected |
<Off> |
|
CachePragmaHeader |
no-cache |
|
CacheControlHeader |
no-cache |
|
LogOutURLs |
<leave blank> |
|
User Defined Parameters |
<leave blank> |
|
Assign An Access Server (Primary) |
<oam_hostname>:<port> |
|
Number of Connections |
1 |
Click AccessGate Configuration.
Click OK to search for all AccessGates.
The new AccessGate is now listed
To leverage Adaptive Strong Authenticator as an authentication mechanism, Oracle Access Manager must have a defined Authentication Scheme to understand how to direct authentications to Adaptive Strong Authenticator.
Steps
Click Authentication Management.
Click New.
Using the settings in the table below, begin creating the new Adaptive Strong Authenticator authentication scheme:
Table 8-3 OAAM ASA Authentication Scheme Configuration
| Parameter | Value |
|---|---|
|
Name |
Adaptive Strong Authentication |
|
Description |
Oracle Adaptive Access Manager-Adaptive Strong Authenticator virtual authentication pad auth scheme |
|
Level |
3 |
|
Challenge Method |
Form |
|
Challenge Parameter(s) |
form:/oasa/loginPage.jsp |
|
creds:userid password |
|
|
action:/oasa/dummy.jsp |
|
|
SSL Required |
<No> |
|
Challenge Redirect |
<Redirect Url> |
|
Enabled |
<Disabled/Greyed Out> |
Note:
For the challenge parameter, do not use "action:/oasa". Use "action:/oasa/dummy.jsp". If you do not do this, you will receive a "technical error" message from Oracle Adaptive Access Manager authentication. "dummy.jsp" does not need to exist.Click Save.
Click Ok to confirm the saved operation.
Click Plugins.
Click Modify.
Click Add.
Create the plugin configurations using the information presented in the table below.
Click Save.
Click General.
Click Modify.
Set Enabled to Yes.
Click Save.
The AccessGates used by Adaptive Strong Authenticator must have host identifier entries. Use the Host Identifiers feature to enter the official name for the host, and every other name by which the host can be addressed by users.
A request sent to any address on the list is mapped to the official host name, and applicable rules and policies are implemented. This is primarily used in virtual site hosting environments.
Install the ASDK that will be used by the Adaptive Strong Authenticator for communication with the Oracle Access Manager Access Server.
Adaptive Strong Authenticator requires ASDK to communicate with the Oracle Access Manager Access Server.
After installing the ASDK for the Adaptive Strong Authenticator, the ASDK must be configured for use.
Use a command-line tool (configureAccessGate) to specify the settings for the ASDK to use for communication with the Oracle Access Manager Access Server.
Steps
Navigate to the configureAccessGate directory at <ASDK install dir>\AccessServerSDK\oblix\tools\configureAccessGate.
Run following command and press Enter.
configureAccessGate -i < Installation directory of the AccessServerSDK> -t AccessGate -w <Enter the name of the defined oaamAccessGate> -p <port> -h <hostname> -a <Name of the Access Server> -m open
For example:
configureAccessGate -i E:\oracle\oaam\AccessServerSDK -t AccessGate -w oaamAccessGate -p 6021 -h www.otherdomain.com -a accessSvr1 -m open
Install an Apache HTTP server 2.x and configure it with the WebLogic Server Plug-in.
For instructions on installing and configuring the Apache HTTP Server Plug-In, refer to:
http://e-docs.bea.com/wls/docs92/plugins/apache.html
To correctly handle the cookies for authentication and the required HTTP headers for the Adaptive Strong Authenticator application, Adaptive Strong Authenticator must be protected with a standard WebGate and Web server.
Steps
Stop the application server (and Web server).
Run the WebGate installation program
For the WebGate configuration, use the following settings:
Table 8-5 ohsWebGate Configuration
| Attribute | Value |
|---|---|
|
WebGate ID |
ohsWebGate |
|
Password for WebGate |
<password> |
|
Access Server ID |
<Access ServerId> |
|
Host Name |
<hostname> |
|
Port |
<port |
Note:
Oracle Application Server installs an Oracle HTTP Server (OHS) with the application server and OC4J container.If a different application server or servlet container (for example, BEA WebLogic, JBoss, or Tomcat) is used for Adaptive Strong Authenticator/Adaptive Risk Manager, a front-end Web server with the appropriate proxy plug-in (for example, mod_wl_20.so or mod_jk) would be necessary before installing the WebGate on the Web server.
Installation instructions for "mod_wl_20.so" is documented at:
http://e-docs.bea.com/wls/docs92/plugins/apache.html
Unpack the Adaptive Strong Authenticator plug-in for Oracle Access Manager from the oaam_plugins folder and copy the required files to the Adaptive Strong Authenticator installation.
Steps
Copy oasa_oam_override.jar from … oaam_plugins\oaam_oam_plugin\oasa\war\WEB-INF\lib to <OASA_HOME>\WEB-INF\lib.
Copy the client folder to <OASA_HOME>\.
Rename <OASA_HOME>\WEB-INF\struts-config.xml to <OASA_HOME>\WEB-INF\struts-config.xml.bak.
Copy struts-config.xml from … oaam_plugins\oaam_oam_plugin\oasa\war\WEB-INF to <OASA_HOME>\WEB-INF\.
Copy bharosauio_client.properties from … oaam_plugins\oaam_oam_plugin\oasa\war\WEB-INF\classe to <OASA_HOME>\WEB-INF\classes\bharosauio_client.properties.
Copy bharosauio_client.properties from plugin.zip to <OASA_HOME>\WEB-INF\classes\bharosauio_client.properties
Check lookup.properties under <OASA_HOME>\WEB-INF \classes to verify that bharosauio_client.properties is listed.
Copy the key Java AccessGate library file from the ASDK to the Adaptive Strong Authenticator installation for use.
For example, copy <ASDK install>oblix\lib\jobaccess.jar to <OASA_HOME>\WEB-INF\lib.
If the jar files are not copied, the Adaptive Strong Authenticator installation will not identify the ASDK Java Access Gate library.
Modify bharosa_client.properties under <OASA_HOME>\WEB-INF\classes to include the path of the Oracle Access Manager Java AccessGate (jobaccess.jar). The application properties for Adaptive Strong Authenticator must be updated to locate the AccessGate configuration information you specified with the configureAccessGate utility previously.
For example
bharosa.accesserversdk.path=E:\\oracle\\oaam\\AccessServerSDK
Note:
There are 2 s's in a row in "accesserversdk" not 3 s's.If we do not have this in our path, Adaptive Strong Authenticator will not be able to located the Access Gate configuration.
The Oracle Adaptive Access Manager AccessGate used by Adaptive Strong Authenticator must use the supporting library files from the ASDK directories. Please update your Application Server PATH variable to include the libraries from the ASDK.
For example,
Add E:\oracle\oaam\AccessServerSDK\oblix\lib to your Environment Variables
If this setting is not there, Adaptive Strong Authenticator will not be able to identify the AccessGate libraries during startup.
The Adaptive Strong Authenticator authentication should now be operable for Oracle Access Manager policy domains. Please modify your application Oracle Access Manager policy domain to use the Adaptive Strong Authenticator authentication scheme (Adaptive Strong Authentication).
Steps
Log in to the Oracle Access Manager host. For example, http://<hostname>/access/oblix.
Click Policy Manager.
Log in as an admin user
Click My Policy Domains
Click <ApplicationPolicy >.
Click Default Rules.
Click Modify
From the Authentication Scheme drop-down selector, select Adaptive Strong Authentication.
Click OK to confirm the change in authentication schemes.
Ensure that Update Cache is checked.
Click Save.
Close Internet Explorer.