28 Configuring WS-Security for WebCenter Applications and Components
This chapter describes how to set up WS-Security for WebCenter applications (including WebCenter Spaces and custom WebCenter applications) and related services and components based on your topology. This section covers the following configurations:
-
a simple topology, with the WebCenter application and all components sharing the same domain,
-
a typical topology, with the WebCenter application and components divided across two domains, and
-
a complex topology, with the WebCenter application and components divided across multiple domains.
Within these three topologies, configuration is described for the WebCenter application (WebCenter Spaces, for example), Oracle WebCenter Discussions, the Worklist service, and WSRP producers. These configurations and the steps for securing OWLCS and applications consuming WebCenter Spaces APIs are covered in the following sections:
-
Section 28.1, "Configuring WS-Security for a Simple Topology"
-
Section 28.2, "Configuring WS-Security for a Typical Topology"
-
Section 28.3, "Configuring WS-Security for a Complex Topology"
-
Section 28.4, "Securing Oracle WebLogic Communication Services (OWLCS) with WS-Security"
The content of this chapter is intended for Fusion Middleware administrators (users granted the Admin role through the Oracle WebLogic Server Administration Console). Users with the Monitor or Operator roles can view security information but cannot make changes. See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
28.1 Configuring WS-Security for a Simple Topology
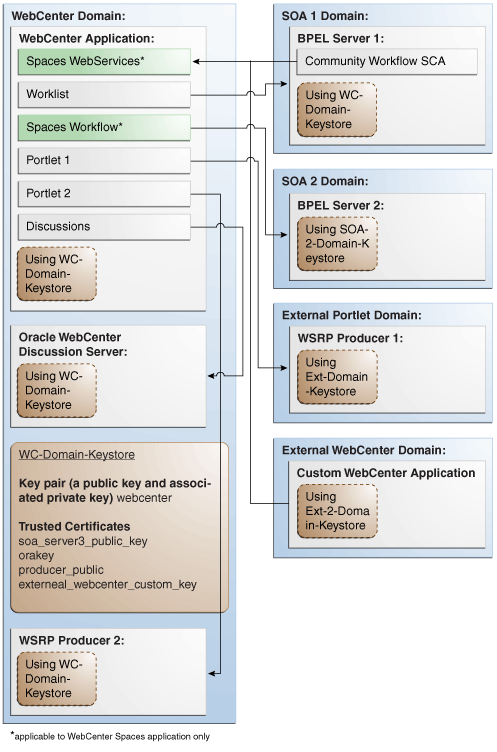
This section describes how to configure WS-Security for a topology where the WebCenter application, the BPEL server, and WSRP producers share the same domain (Figure 28-1).
Figure 28-1 WS-Security for a Simple Configuration
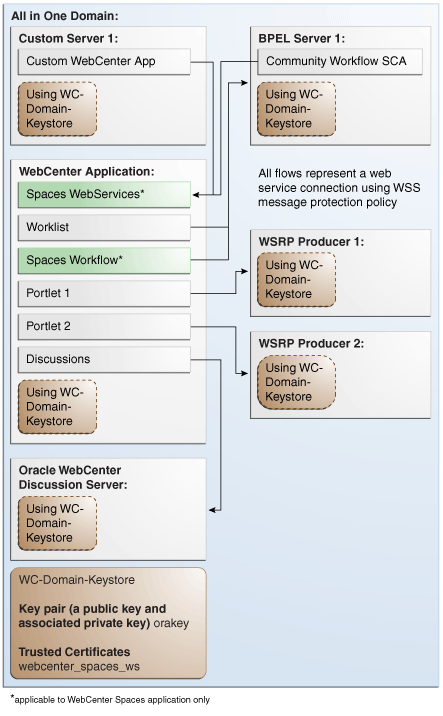
Description of "Figure 28-1 WS-Security for a Simple Configuration"
The steps to configure WS-Security for a simple single-domain WebCenter topology are described in the following sections:
-
Section 28.1.2, "Configuring the Discussions Server for a Simple Topology"
-
Section 28.1.3, "Configuring the BPEL Server for a Simple Topology"
28.1.1 Setting Up the WebCenter Domain Keystore
The security credentials of the WebCenter application, discussions server, BPEL server, and WSRP producers can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See the Oracle Fusion Middleware Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
-
Section 28.1.1.3, "Configuring the Keystore Using Fusion Middleware Control"
-
Section 28.1.1.4, "Unconfiguring a Keystore Provider Using Fusion Middleware Control"
28.1.1.1 Creating the WebCenter Domain Keystore
This section describes how to create a keystore and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias orakey -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias orakey -keystore keystore -storepass keystore_password -rfc -file orakey.cer
Where:
-
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Import the certificate with the alias
webcenter_spaces_ws(choose Yes when prompted whether to overwrite the existing certificate with the aliasorakey):keytool -importcert -alias webcenter_spaces_ws -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Continue by configuring the keystore using either WLST as described in Section 28.1.1.2, "Configuring the Keystore with WLST," or using Fusion Middleware Control as described in Section 28.1.1.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 28-1 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 28-1 WebCenter Domain Keystore Contents for a Simple Topology
Key Alias Description orakeyKey pair used to sign and encrypt outbound messages from WebCenter Spaces. This key is used by both OWSM (Portlets and Worklist) and Discussions.
webcenter_spaces_wsCertificate containing the public key for the
orakeyprivate key used in the WebCenter domain. The certificate is used to encrypt outbound WebService messages from the Workflow application on BPEL Server1 in the WebCenter domain, to the WebService APIs on WebCenter domain.
28.1.1.2 Configuring the Keystore with WLST
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the credential store:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password=keystore_password, desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password=private_key_password, desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password=private_key_password, desc="Signing key")
Where:
-
keystore_passwordis the keystore password specified in step 2 of Section 28.1.1.1, "Creating the WebCenter Domain Keystore," (for example,welcome1) -
private_key_passwordis the private key password specified in step 2 of Section 28.1.1.1, "Creating the WebCenter Domain Keystore," (for example,welcome1)
Example 28-4 Updating the Credential Store
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password="welcome1", desc="Signing key")
-
-
Restart all servers.
28.1.1.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.1.1.4, "Unconfiguring a Keystore Provider Using Fusion Middleware Control." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
webcenterby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-2).
Figure 28-2 Security Provider Configuration Page
Description of "Figure 28-2 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
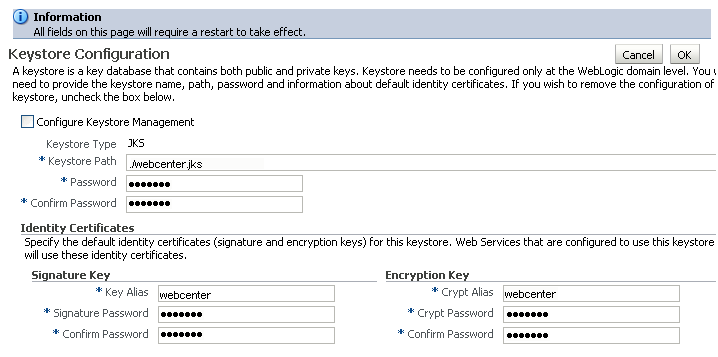
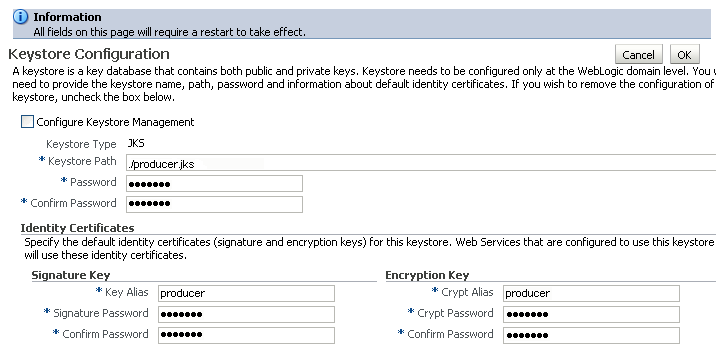
The Keystore Configuration page displays (see Figure 28-3).
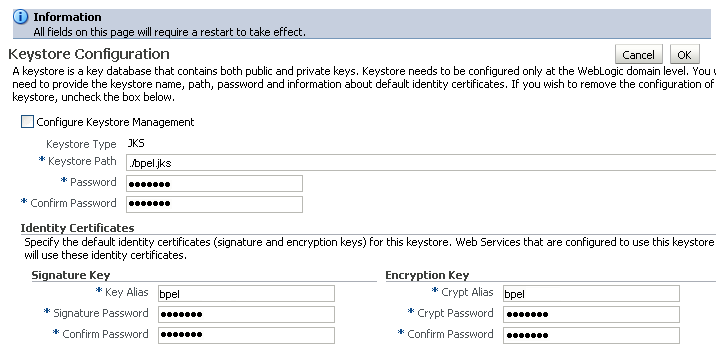
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
orakey -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
orakey -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.1.1.4 Unconfiguring a Keystore Provider Using Fusion Middleware Control
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, ignore this section and continue with the steps to configure the keystore in Section 28.1.1.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-4).
Figure 28-4 Security Provider Configuration Page

Description of "Figure 28-4 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
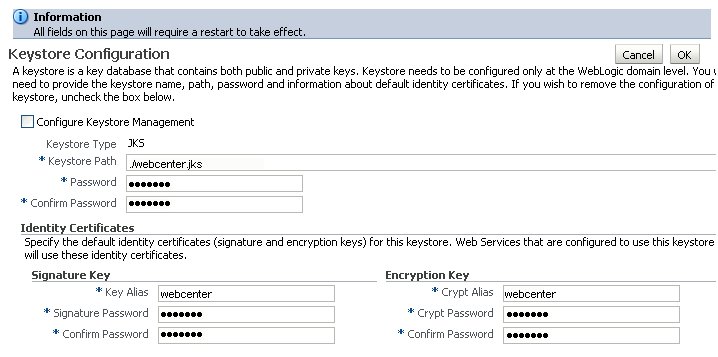
The Keystore Configuration page displays (see Figure 28-5).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.1.2 Configuring the Discussions Server for a Simple Topology
To use the Oracle WebCenter Discussions with WebCenter Spaces or a custom WebCenter application, you must enable Web Services Security (WS-Security) trusted authentication. WS-Security establishes a trust relationship between your WebCenter application and Oracle WebCenter Discussions so that the application can pass the user identity information to the discussions server without knowing the user's credentials.
Note:
Discussions-specific Web Services messages sent by WebCenter applications to the Oracle WebCenter Discussions server are not encrypted. For message confidentiality, the discussions server URL must be accessed over Secure Socket Layer (SSL). For more information, see Chapter 27, "Securing WebCenter Applications and Components with SSL."To set WS-Security-related properties on the discussions server connection that is configured for WebCenter Spaces or your custom WebCenter application, refer to Table 12-4, "Additional Discussion Connection Properties" in Section 12.3.1, "Registering Discussions Servers Using Fusion Middleware Control."
To configure WS-Security on the discussions server side, you must create a keystore certificate properties file, specify it for the ClassLoader, and modify the webservices.soap.custom.crypto.fileName system property. These configuration steps are described in the following sub-sections:
-
Section 28.1.2.1, "Importing the WebCenter Domain Certificate"
-
Section 28.1.2.2, "Creating the Keystore Certificate Properties File"
-
Section 28.1.2.3, "Specifying the Properties File for ClassLoader"
-
Section 28.1.2.4, "Updating the System Properties for WS-Security"
28.1.2.1 Importing the WebCenter Domain Certificate
Create a keystore by importing the certificate containing the public key of the WebCenter domain.
To import the WebCenter domain certificate:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, import the certificate containing the public key of the WebCenter domain:
keytool -importcert -alias df_orakey_public -file orakey.cer -keystore owc_discussions.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
At the prompt "Trust this certificate?", choose
yes.
28.1.2.2 Creating the Keystore Certificate Properties File
The server-side keystore certificate configuration must be stored in a properties file (keystore.properties) and specified as a system property on the discussions server. The properties file must then be loaded in the ClassLoader for the WS-Secure Handler to pick it up.
Note:
When you are updating the properties file, be sure to remove any spaces from the property names and values. The properties file should not contain any extraneous spaces.To create the properties file:
-
Create a properties file with the following entries:
org.apache.ws.security.crypto.provider= <Specify your crypto provider (typically org.apache.ws.security.components.crypto.Merlin)> org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=<Specify the keystore password of your server certificate. Note that the password stored in this file is in clear text because of a limitation of the Ws-Security provider WSS4J used in Oracle Discussions Server.> org.apache.ws.security.crypto.merlin.keystore.alias=df_orakey_public org.apache.ws.security.crypto.merlin.file=<Absolute path of directory containing the certificate file created above>/owc_discussions.jks
-
Save the file as
keystore.properties.
28.1.2.3 Specifying the Properties File for ClassLoader
There are two ways you can choose to specify your keystore.properties file based on your setup. Using the same file mounted across different servers is recommended when using a Clustered Discussions Server installation in Linux.
To specify the properties file for ClassLoader, do one of the following:
-
Specify the properties file as the
CLASSPATHinsetDomainEnv.sh.For Linux:
-
Place the
keystore.propertiesfile in a directory (for example,. /home/user/keystore/) -
Open
DOMAIN_HOME/bin/setDomainEnv.sh. -
Towards the end of the file, add the following lines to specify this directory as the
CLASSPATH.if [ "${CLASSPATH}" != "" ] ; then CLASSPATH="${CLASSPATH}${CLASSPATHSEP}/home/user/keystore/" export CLASSPATH else CLASSPATH="/home/user/keystore/" export CLASSPATH fiNote that the
CLASSPATHdirectory name must end with "/".
For Windows:
-
Place the
keystore.propertiesfile in a directory (for example,c:\keystore\). -
Open
DOMAIN_HOME\bin\setDomainEnv.cmd. -
Towards the end of the file, add the following lines to specify this directory in
CLASSPATH.if NOT "%CLASSPATH%"=="" ( set CLASSPATH=%CLASSPATH%;c:\keystore\ ) else ( set CLASSPATH=c:\keystore\ )Note that the
CLASSPATHdirectory name must end with "\".
-
-
Or, add the
keystore.propertiesfile to a.JARfile and place the.JARfile in yourDOMAIN_HOME/libdirectory. Be sure to also set the system propertywebservices.soap.custom.crypto.fileNametokeystore.propertiesas described in Section 28.1.2.4, "Updating the System Properties for WS-Security."
28.1.2.4 Updating the System Properties for WS-Security
To update your system properties:
-
Log in to the Oracle WebCenter Discussions Administration Console at the following URL:
http://host:port/owc_discussions/adminWhere
hostandportare the address and the port number of the server where you deployed Oracle WebCenter Discussions (for example,http://localhost:7001/owc_discussions). -
Click System Properties under Forum System to display the Jive Properties page.
-
Modify the system property
webservices.soap.custom.crypto.fileNameand specify the properties file that you created (that is,keystore.properties).Ensure that you specify the name of the file, and not the directory or
.JARname. -
Click OK.
-
Restart the
WLS_ServicesManaged Server.
28.1.2.5 Configuring the Discussions Server Connection Settings
After setting the system properties, you must supply the WS-Security client certificate information within the discussions server connection that is configured for WebCenter Spaces or your custom WebCenter application, as described in Section 12.3, "Registering Discussions Servers." Figure 28-6 shows example settings for the Edit Discussions and Announcement Connection page.
Figure 28-6 Edit Discussions and Announcement Connection Page
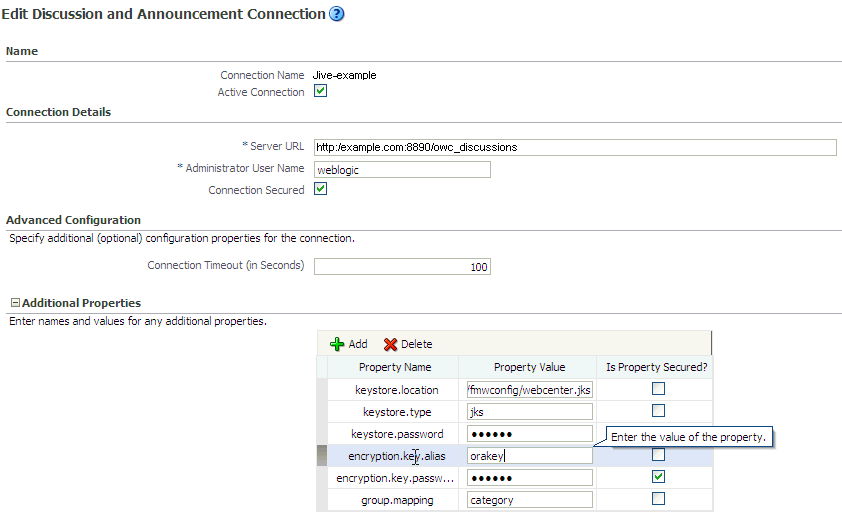
Description of "Figure 28-6 Edit Discussions and Announcement Connection Page"
28.1.3 Configuring the BPEL Server for a Simple Topology
The BPEL server's Worklist connection must be configured to use message protected SAML service policy. The BPEL server's oracle-webservices.xml file must also be edited so that the server-side SAML policy matches that of the client's policy.
To configure the BPEL server:
-
To configure the Worklist connection on the BPEL server to use the SAML policy with message protection, follow the steps in Section 20.3.2, "Registering Worklist Connections" selecting
SAML Token With Message Client Policyin Fusion Middleware Control, or enteringoracle/wss10_saml_token_with_message_protection_client_policyas the policy value if using WLST. -
Use
grepto find the stringsTaskQueryServicePortSAMLandprovider-namein all the BPEL server'soracle-webservices.xmlfiles. For example:cd <domain home> find . | grep webservices.xml | xargs grep TaskQueryServicePortSAML | grep provider-name ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml: <provider-name>TaskQueryServicePortSAML</provider-name>
-
Back up the file. For example:
cp ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml.original
-
Edit the file, replacing:
<policy-reference uri="oracle/wss10_saml_token_service_policy" category="security" enabled="true"/>
with:
<policy-reference uri="oracle/wss10_saml_token_with_message_protection_service_policy" category="security" enabled="true"/>
-
Save the file and restart the Managed Servers. The message protected SAML access is now configured. Examine the managed server diagnostic logs for exception stack information should the worklist service still not work to obtain information about configuration issues.
28.1.4 Command Summary for a Simple Topology
Use the following command summary to quickly configure the keystore and DF properties for a simple topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias orakey -keypass welcome1 -keystore default-keystore.jks -storepass welcome1 -validity 1064
keytool -exportcert -v -alias orakey -keystore default-keystore.jks -storepass welcome1 -rfc -file orakey.cer
keytool -importcert -alias webcenter_spaces_ws -file orakey.cer -keystore default-keystore.jks -storepass welcome1
When prompted that the certificate already exists, say yes.
keytool -importcert -alias df_orakey_public -file orakey.cer -keystore owc_discussions.jks -storepass welcome1
When prompted to trust the certificate, say yes.
Copy the default-keystore.jks file to your domain_home/config/fmwconfig directory.
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password="welcome1", desc="Signing key")
Configure the DF Keystore Properties File
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=welcome1 org.apache.ws.security.crypto.merlin.keystore.alias=df_orakey_public org.apache.ws.security.crypto.merlin.file=<dir_containing_keystore>/owc_discussions.jks
Note:
Be sure to trim any spaces from the line endings. If you are working in a Windows environment, also be sure to use "\\" as the file path separator.Additional DF Connection properties are shown in Table 28-2.
Table 28-2 Additional DF Connection Properties
| Property Name | Property Value | Secured |
|---|---|---|
|
|
|
No |
|
|
|
No |
|
|
|
Yes |
|
|
|
No |
|
|
|
Yes |
|
|
|
No |
28.2 Configuring WS-Security for a Typical Topology
This section describes how to configure WS-Security for a topology where the WebCenter application and the WSRP producers share the same domain, but the BPEL server is in an external domain - the SOA domain (see Figure 28-7).
Figure 28-7 Typical WS-Security Configuration
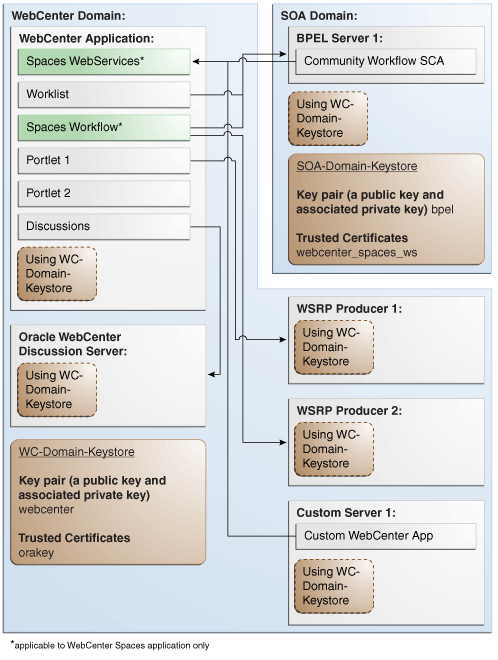
Description of "Figure 28-7 Typical WS-Security Configuration"
The steps to configure WS-Security for a typical two domain WebCenter topology are described in the following sections:
-
Section 28.2.2, "Configuring the Discussions Server for a Typical Topology"
-
Section 28.2.4, "Configuring the BPEL Server for a Typical Topology"
28.2.1 Setting Up the WebCenter Domain Keystore
The security credentials of a WebCenter application, discussions server, BPEL server (in a separate domain), and WSRP producers can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See the Oracle Fusion Middleware Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
28.2.1.1 Creating the WebCenter Domain Keystore
This section describes how to create a keystore and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias webcenter -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias webcenter -keystore keystore -storepass keystore_password -rfc -file webcenter_public.cer
Where:
-
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST, as described in Section 28.2.1.2, "Configuring the Keystore Using WLST," or Fusion Middleware Control, as described in Section 28.2.1.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 28-3 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 28-3 WebCenter Domain Keystore Contents for a Typical Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Spaces. This key is used by both OWSM (Portlets and Worklist) and Discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA domain. The certificate is used to encrypt outbound WebService messages from the Workflow application on BPEL Server1 in the WebCenter domain, to the Worklist service to the SOA server on the SOA domain.
28.2.1.2 Configuring the Keystore Using WLST
After creating the WebCenter domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password=keystore_password, desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password=private_key_password, desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password=private_key_password, desc="Signing key")
Where:
-
keystore_passwordis the keystore password specified in step 2 of Section 28.2.1.1, "Creating the WebCenter Domain Keystore," (for example,welcome1) -
private_key_passwordis the private key password specified in step 2 of Section 28.2.1.1, "Creating the WebCenter Domain Keystore," (for example,welcome1)
Example 28-8 Updating the Credential Store
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="welcome1", desc="Signing key")
-
-
Restart all servers.
28.2.1.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.2.1.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
webcenterby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-8).
Figure 28-8 Security Provider Configuration Page

Description of "Figure 28-8 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
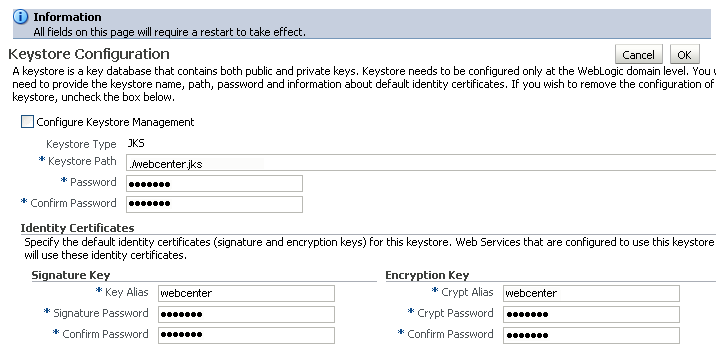
The Keystore Configuration page displays (see Figure 28-9).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
webcenter -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
webcenter -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.2.1.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.2.1.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-10).
Figure 28-10 Security Provider Configuration Page

Description of "Figure 28-10 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-11).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.2.2 Configuring the Discussions Server for a Typical Topology
To use Oracle WebCenter Discussions with WebCenter Spaces or custom WebCenter applications, you must enable Web Services Security (WS-Security) trusted authentication. WS-Security establishes a trust relationship between your WebCenter application and Oracle WebCenter Discussions so that the application can pass the user identity information to the discussions server without knowing the user's credentials.
Note:
Discussions-specific Web Services messages sent by WebCenter applications to the Oracle WebCenter Discussions server are not encrypted. For message confidentiality, the Discussions server URL must be accessed over Secure Socket Layer (SSL). For more information, see Chapter 27, "Securing WebCenter Applications and Components with SSL."This section describes how to add the WS-Security-related properties within the discussions server connection that is configured for WebCenter Spaces or your custom WebCenter application. For information on how to add new properties, see Table 12-4, "Additional Discussion Connection Properties" in Section 12.3.1, "Registering Discussions Servers Using Fusion Middleware Control."
To configure WS-Security on the discussions server side, you must create a keystore certificate properties file, specify it for the ClassLoader, and modify the webservices.soap.custom.crypto.fileName system property.
These configuration steps are described in the following sub-sections:
-
Section 28.2.2.1, "Importing the WebCenter Domain Certificate"
-
Section 28.2.2.2, "Creating the Keystore Certificate Properties File"
-
Section 28.2.2.3, "Specifying the Properties File for ClassLoader"
-
Section 28.2.2.4, "Updating the System Properties for WS-Security"
-
Section 28.2.2.5, "Configuring the Discussions Server Connection Settings"
28.2.2.1 Importing the WebCenter Domain Certificate
Create a keystore by importing the certificate containing public key of the WebCenter domain.
To import the WebCenter domain certificate:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, import the certificate containing the public key of the WebCenter domain:
keytool -importcert -alias df_webcenter_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
28.2.2.2 Creating the Keystore Certificate Properties File
The server-side keystore certificate configuration must be stored in a properties file (keystore.properties) and specified as a system property on the discussions server. The properties file must then be loaded in the ClassLoader for the WS-Secure Handler to pick it up.
Note:
When you are updating the properties file, be sure to remove any spaces from the property names and values. The properties file should not contain any extraneous spaces.To create the properties file:
-
Create a properties file with the following entries:
org.apache.ws.security.crypto.provider=<Specify your crypto provider (typically org.apache.ws.security.components.crypto.Merlin)> org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=<Specify the keystore password of your server certificate. Note that the password stored in this file is in clear text because of a limitation of the Ws-Security provider WSS4J used in Oracle Discussions Server.> org.apache.ws.security.crypto.merlin.keystore.alias=df_orakey_public org.apache.ws.security.crypto.merlin.file=<Absolute path of directory containing the keystore (owc_discussions.jks) created above.>
-
Save the file as
keystore.properties.
28.2.2.3 Specifying the Properties File for ClassLoader
There are two ways you can choose to specify your keystore.properties file based on your setup. Using the same file mounted across different servers is recommended when using a Clustered Discussions Server installation in Linux.
To specify the properties file for ClassLoader, do one of the following:
-
Specify the properties file as the
CLASSPATHinsetDomainEnv.sh.For Linux:
-
Place the
keystore.propertiesfile in a directory (for example,. /home/user/keystore/) -
Open
DOMAIN_HOME/bin/setDomainEnv.sh. -
Towards the end of the file, add the following lines to specify this directory as the
CLASSPATH.if [ "${CLASSPATH}" != "" ] ; then CLASSPATH="${CLASSPATH}${CLASSPATHSEP}/home/user/keystore/" export CLASSPATH else CLASSPATH="/home/user/keystore/" export CLASSPATH fiNote that the
CLASSPATHdirectory name must end with "/".
For Windows:
-
Place the
keystore.propertiesfile in a directory (for example,c:\keystore\). -
Open
DOMAIN_HOME\bin\setDomainEnv.cmd. -
Towards the end of the file, add the following lines to specify this directory in
CLASSPATH.if NOT "%CLASSPATH%"=="" ( set CLASSPATH=%CLASSPATH%;c:\keystore\ ) else ( set CLASSPATH=c:\keystore\ )Note that the
CLASSPATHdirectory name must end with "\".
-
-
Or, add the
keystore.propertiesfile to a.JARfile and place the.JARfile in yourDOMAIN_HOME/libdirectory. Be sure to also set the system propertywebservices.soap.custom.crypto.fileNametokeystore.propertiesas described in Section 28.2.2.4, "Updating the System Properties for WS-Security."
28.2.2.4 Updating the System Properties for WS-Security
To update your system properties:
-
Log in to the Oracle WebCenter Discussions Admin Console at the following URL:
http://host:port/owc_discussions/adminWhere
hostandportare the address and the port number of the server where you deployed Oracle WebCenter Discussions (for example,http://localhost:7001/owc_discussions). -
Click System Properties under Forum System to display the Jive Properties page.
-
Modify the system property
webservices.soap.custom.crypto.fileNameand specify the properties file that you created (that is,keystore.properties).Be sure to specify the name of the file, and not the directory or
.JARname. -
Click OK.
-
Restart the
WLS_ServicesManaged Server.
28.2.2.5 Configuring the Discussions Server Connection Settings
After setting the system properties, you must supply the WS-Security client certificate information within the discussion server connection settings, as described in Section 12.3, "Registering Discussions Servers." Figure 28-12 shows example settings for the Edit Discussions and Announcement Connection page.
Figure 28-12 Edit Discussions and Announcement Connection Page
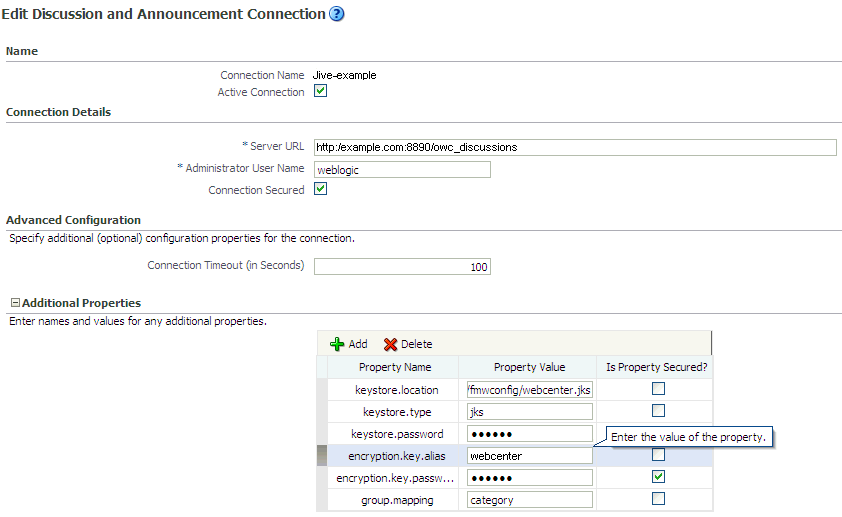
Description of "Figure 28-12 Edit Discussions and Announcement Connection Page"
28.2.3 Setting Up the SOA Domain
This section describes how to set up the SOA domain keystore and contains the following subsections:
28.2.3.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Create a keystore by importing the public certificate (
webcenter_public.cer) from the WebCenter domain:keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass keystore_password
Where:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias bpel -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=bpel,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,bpel.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter domain using the
orakeyalias:keytool -exportcert -v -alias orakey -keystore keystore -storepass keystore_password -rfc -file orakey.cer
Where:
-
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Import the certificate with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
orakey):keytool -importcert -alias orakey -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
28.2.3.2 Configuring the Keystore Using WLST
After creating the SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
bpel.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./bpel.jks. -
Use the following WLST commands to configure the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="welcome1", desc="Signing key")
-
Restart all servers.
28.2.3.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.2.3.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
webcenterby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-13).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
orakey -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
orakey -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.2.3.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.2.3.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-14).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.2.4 Configuring the BPEL Server for a Typical Topology
The BPEL server's Worklist connection must be configured to use message protected SAML service policy. The BPEL server's oracle-webservices.xml file must also be edited so that the server-side SAML policy matches that of the client's policy.
To configure the BPEL server:
-
To configure the Worklist connection on the BPEL server to use the SAML policy with message protection, follow the steps in Section 20.3.2, "Registering Worklist Connections," selecting
SAML Token With Message Client Policyin Fusion Middleware Control, or enteringoracle/wss10_saml_token_with_message_protection_client_policyas the policy value if using WLST. -
Use
grepto find the stringsTaskQueryServicePortSAMLandprovider-namein all the BPEL server'soracle-webservices.xmlfiles. For example:cd <domain home> find . | grep webservices.xml | xargs grep TaskQueryServicePortSAML | grep provider-name ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml: <provider-name>TaskQueryServicePortSAML</provider-name>
-
Back up the file. For example:
cp ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml ./servers/BPEL Server 1/tmp/_WL_user/soa-infra/ugh7wb/war/WEB-INF/oracle-webservices.xml.original
-
Edit the file, replacing:
<policy-reference uri="oracle/wss10_saml_token_service_policy" category="security" enabled="true"/>
with:
<policy-reference uri="oracle/wss10_saml_token_with_message_protection_service_policy" category="security" enabled="true"/>
-
Save the file and restart the Managed Servers. The message protected SAML access is now configured. Examine the managed server diagnostic logs for exception stack information should the worklist service still not work to obtain information about configuration issues.
28.2.5 Command Summary for a Typical Topology
Use the following command summary to quickly configure the keystore and DF properties for a typical topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias webcenter -keypass welcome1 -keystore webcenter.jks -storepass welcome1 -validity 1064
keytool -exportcert -v -alias webcenter -keystore webcenter.jks -storepass welcome1 -rfc -file webcenter_public.cer
keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass welcome1
When prompted that the certificate already exists, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=bpel,dc=example,dc=com" -alias bpel -keypass welcome1 -keystore bpel.jks -storepass welcome1 -validity 1024
keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass welcome1 -rfc -file orakay.cer
keytool -importcert -alias orakey -file orakay.cer -keystore webcenter.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -importcert -alias df_webcenter_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass welcome1
When prompted to trust the certificate, say yes.
Copy the webcenter.jks file to your domain_home/config/fmwconfig directory, and the bpel.jks file to your soa_domain_home/config/fmwconfig directory.
Configure the WebCenter Domain Keystore
Follow the steps below to configure the service instance reference for the WebCenter domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
webcenter.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./webcenter.jks. -
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="welcome1", desc="Signing key")
Configure the SOA Domain Keystore
Follow the steps below to configure service instance reference for the SOA domain:
-
Navigate to the
<SOA_DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
bpel.jksto the<SOA_DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./bpel.jks. -
Using WLST, connect to the SOA domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="welcome1", desc="Signing key")
Configure the DF Keystore Properties File
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=welcome1 org.apache.ws.security.crypto.merlin.keystore.alias=df_webcenter_public org.apache.ws.security.crypto.merlin.file=<dir_containing_keystore>/owc_discussions.jks
Note:
Be sure to trim any spaces from the line endings. If you are working in a Windows environment, also be sure to use "\\" as the file path separator.Additional DF Connection properties are shown in Table 28-2.
28.3 Configuring WS-Security for a Complex Topology
This section describes how to configure WS-Security for a complex topology where the WebCenter application, the discussions server (Jive), and a WSRP producer are in the same domain, two BPEL servers are in separate SOA domains, and one WSRP producer is in an external portlet domain (see Figure 28-15).
The steps to configure WS-Security for a typical two domain WebCenter topology are described in the following sections:
-
Section 28.3.2, "Configuring the Discussions Server for a Complex Topology"
-
Section 28.3.5, "Configuring the BPEL Server for a Complex Topology"
-
Section 28.3.6, "Setting Up the External Portlet Domain Keystore"
-
Section 28.3.7, "Setting Up the External WebCenter Domain Keystore"
28.3.1 Setting Up the WebCenter Domain Keystore
The security credentials of WebCenter Spaces, discussions server, BPEL servers (in separate domains), and WSRP producers (also in separate domains) can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See the Oracle Fusion Middleware Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
28.3.1.1 Creating the WebCenter Domain Keystore
This section describes how to create a keystore and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias webcenter -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias webcenter -keystore wecenter.jks -storepass keystore_password -rfc -file webcenter_public.cerWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST, as described in Section 28.3.1.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control, as described in Section 28.3.1.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 28-5 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 28-5 WebCenter Domain Keystore Contents for a Complex Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Spaces. This key is used by both OWSM (Portlets and Worklist) and Discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA 1 domain. The certificate is used to encrypt outbound messages from the Worklist service to SOA_Server3 in the SOA 1 domain.soa_server3_public_keyCertificate containing the public key for the soa_server3 private key used in the SOA 2 domain. The certificate is used to encrypt outbound messages from the Worklist service to BPEL Server2 in SOA 2 domain.
producer_public_keyCertificate containing public key for the producer private key used in the external portlet domain that hosts the WSRP Producer 1 application. This certificate is used to encrypt outbound messages from WebCenter Spaces to WSRP Producer 1 registered in the WebCenter Spaces application.
external_webcenter_custom_public_keyCertificate containing the public key for the external_webcenter_custom private key used in the external WebCenter domain that hosts the custom WebCenter application that makes WebService call to the WebCenter Spaces WebService. This certificate is used to encrypt outbound messages from WebCenter Spaces to custom WebCenter applications in the external WebCenter domain.
28.3.1.2 Configuring the Keystore Using WLST
After creating the WebCenter domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for thekeystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="welcome1", desc="Signing key")
-
Restart all servers.
28.3.1.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.3.1.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-16).
Figure 28-16 Security Provider Configuration Page

Description of "Figure 28-16 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-17).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
webcenter -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
webcenter -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.3.1.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.3.1.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-18).
Figure 28-18 Security Provider Configuration Page

Description of "Figure 28-18 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-19).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.3.2 Configuring the Discussions Server for a Complex Topology
To use the Oracle WebCenter Discussions with WebCenter Spaces or custom WebCenter applications, you must enable Web Services Security (WS-Security) trusted authentication. WS-Security establishes a trust relationship between your WebCenter application and Oracle WebCenter Discussions so that the application can pass the user identity information to the discussions server without knowing the user's credentials.
Note:
Discussions-specific Web Services messages sent by WebCenter applications to the Oracle WebCenter Discussions server are not encrypted. For message confidentiality, the Discussions server URL must be accessed over Secure Socket Layer (SSL). For more information, see Chapter 27, "Securing WebCenter Applications and Components with SSL."This section describes how to add WS-Security-related properties to the discussion server connection that is configured for WebCenter Spaces or your custom WebCenter application. For information on how to add new properties, see Table 12-4, "Additional Discussion Connection Properties" in Section 12.3.1, "Registering Discussions Servers Using Fusion Middleware Control."
To configure WS-Security on the discussions server side, you must create a keystore certificate properties file, specify it for the ClassLoader, and modify the webservices.soap.custom.crypto.fileName system property. These configuration steps are described in the following sub-sections:
-
Section 28.3.2.1, "Importing the WebCenter Domain Certificate"
-
Section 28.3.2.2, "Creating the Keystore Certificate Properties File"
-
Section 28.3.2.3, "Specifying the Properties File for ClassLoader"
-
Section 28.3.2.4, "Updating the System Properties for WS-Security"
28.3.2.1 Importing the WebCenter Domain Certificate
Create a keystore by importing the certificate containing public key of the WebCenter domain.
To import the WebCenter domain certificate:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, import the certificate containing the public key of the WebCenter domain:
keytool -importcert -alias df_orakey_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
28.3.2.2 Creating the Keystore Certificate Properties File
The server-side keystore certificate configuration must be stored in a properties file (keystore.properties) and specified as a system property on the discussions server. The properties file must then be loaded in the ClassLoader for the WS-Secure Handler to pick it up.
Note:
When you are updating the properties file, be sure to remove any spaces from the property names and values. The properties file should not contain any extraneous spaces.To create the properties file:
-
Create a properties file with the following entries:
org.apache.ws.security.crypto.provider= <Specify your crypto provider (typically org.apache.ws.security.components.crypto.Merlin)> org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=<Specify the keystore password of your server certificate. Note that the password stored in this file is in clear text because of a limitation of the Ws-Security provider WSS4J used in Oracle Discussions Server.> org.apache.ws.security.crypto.merlin.keystore.alias=df_webcenter_public org.apache.ws.security.crypto.merlin.file=<Absolute path of directory containing the keystore created above.>
-
Save the file as
keystore.properties.
28.3.2.3 Specifying the Properties File for ClassLoader
There are two ways you can choose to specify your keystore.properties file based on your setup. Using the same file mounted across different servers is recommended when using a Clustered Discussions Server installation in Linux.
To specify the properties file for ClassLoader, do one of the following:
-
Specify the properties file as the
CLASSPATHinsetDomainEnv.sh.For Linux:
-
Place the
keystore.propertiesfile in a directory (for example,. /home/user/keystore/) -
Open
DOMAIN_HOME/bin/setDomainEnv.sh. -
Towards the end of the file, add the following lines to specify this directory as the
CLASSPATH.if [ "${CLASSPATH}" != "" ] ; then CLASSPATH="${CLASSPATH}${CLASSPATHSEP}/home/user/keystore/" export CLASSPATH else CLASSPATH="/home/user/keystore/" export CLASSPATH fiNote that the
CLASSPATHdirectory name must end with "/".
For Windows:
-
Place the
keystore.propertiesfile in a directory (for example,c:\keystore\). -
Open
DOMAIN_HOME\bin\setDomainEnv.cmd. -
Towards the end of the file, add the following lines to specify this directory in
CLASSPATH.if NOT "%CLASSPATH%"=="" ( set CLASSPATH=%CLASSPATH%;c:\keystore\ ) else ( set CLASSPATH=c:\keystore\ )Note that the
CLASSPATHdirectory name must end with "\".
-
-
Or, add the
keystore.propertiesfile to a.JARfile and place the.JARfile in yourDOMAIN_HOME/libdirectory. Be sure to also set the system propertywebservices.soap.custom.crypto.fileNametokeystore.propertiesas described in Section 28.3.2.4, "Updating the System Properties for WS-Security."
28.3.2.4 Updating the System Properties for WS-Security
To update your system properties:
-
Log in to the Oracle WebCenter Discussions Administration Console at the following URL:
http://host:port/owc_discussions/adminWhere
hostandportare the address and the port number of the server where you deployed Oracle WebCenter Discussions (for example,http://localhost:7001/owc_discussions). -
Click System Properties under Forum System to display the Jive Properties page.
-
Modify the system property
webservices.soap.custom.crypto.fileNameand specify the properties file that you created (that is,keystore.properties).Be sure to specify the name of the file, and not the directory or
.JARname. -
Click OK.
-
Restart the
WLS_ServicesManaged Server.
28.3.2.5 Configuring the Discussions Server Connection Settings
After setting the system properties, you must supply the WS-Security client certificate information within the discussion server connection settings, as described in Section 12.3, "Registering Discussions Servers." Figure 28-20 shows example settings for the Edit Discussions and Announcement Connection page.
Figure 28-20 Edit Discussions and Announcement Connection Page

Description of "Figure 28-20 Edit Discussions and Announcement Connection Page"
28.3.3 Setting Up the First SOA Domain
This section describes how to set up the SOA domain keystore and contains the following subsections:
28.3.3.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Create a keystore by importing the public certificate (
webcenter_public.cer) from the WebCenter domain:keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias bpel -keypass key_password -keystore bpel.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=bpel,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter domain using the
orakeyalias:keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass keystore_password -rfc -file orakey.cerWhere:
-
keystore_passwordis the keystore password (for example,welcome1)
-
-
Import the certificate to the WebCenter domain again with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
orakey):keytool -importcert -alias orakey -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST as described in Section 28.3.3.2, "Configuring the Keystore Using WLST,", or using Fusion Middleware Control as described in Section 28.3.3.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 28-6 shows the keystore contents you should wind up with after creating and configuring the SOA 1 domain keystore.
Table 28-6 SOA 1 Domain Keystore Contents for a Complex Topology
Key Alias Description bpelPrivate key used to sign outbound messages from the SOA 1 domain servers. This key is used by the Worklist application deployed on the SOA 1 domain's SOA server.
webcenter_spaces_wsCertificate containing the public key for the
webcenterprivate key used in the WebCenter domain. The certificate is used to encrypt outbound Workflow messages on BPEL Server1 in the SOA 1 domain to WebService APIs on the Spaces domain.
28.3.3.2 Configuring the Keystore Using WLST
After creating the SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
bpel.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./bpel.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="welcome1", desc="Signing key")
-
Restart all servers.
28.3.3.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.3.3.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the SOA domain.
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-21).
-
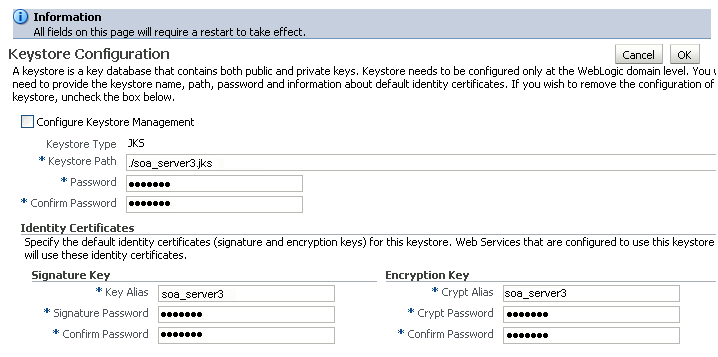
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./bpel.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
bpel -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
bpel -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.3.3.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.3.3.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-22).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.3.4 Setting Up the Second SOA Domain
This section describes how to set up a second SOA domain keystore and contains the following subsections:
28.3.4.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias soa_server3 -keypass key_password -keystore soa_server3.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=soa_server3,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter domain using the
orakeyalias:keytool -exportcert -v -alias soa_server3 -keystore soa_server3.jks -storepass keystore_password -rfc -file soa_server3_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Import the certificate to the WebCenter domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
soa_server3_public_key):keytool -importcert -alias soa_server3_public_key -file soa_server3_public_ key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST as described in Section 28.3.4.2, "Configuring the Keystore Using WLST,", or using Fusion Middleware Control as described in Section 28.3.4.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 28-7 shows the keystore contents you should wind up with after creating and configuring the SOA 2 domain keystore.
Table 28-7 SOA 2 Domain Keystore Contents for a Complex Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Spaces. This key is used by both OWSM (Portlets and Worklist) and Discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA 1 domain. The certificate is used to encrypt outbound messages from the Worklist service to SOA_Server3 in the SOA 1 domain.soa_server3_public_keyCertificate containing the public key for the soa_server3 private key used in the SOA 2 domain. The certificate is used to encrypt outbound messages from the Worklist service to BPEL Server2 in SOA 2 domain.
producer_public_keyCertificate containing public key for the producer private key used in the external portlet domain that hosts the WSRP Producer 1 application. This certificate is used to encrypt outbound messages from WebCenter Spaces to WSRP Producer 1 registered in the WebCenter Spaces application.
external_webcenter_custom_public_keyCertificate containing the public key for the external_webcenter_custom private key used in the external WebCenter domain that hosts the custom WebCenter application that makes WebService call to the WebCenter Spaces WebService. This certificate is used to encrypt outbound messages from WebCenter Spaces to custom WebCenter applications in the external WebCenter domain.
28.3.4.2 Configuring the Keystore Using WLST
After creating the second SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
soa_server3.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./soa_server3.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="soa_server3", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="soa_server3", password="welcome1", desc="Signing key")
-
Restart all servers.
28.3.4.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.3.4.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the SOA domain.
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-23).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./soa_server3.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
soa_server3 -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
soa_server3 -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.3.4.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.3.4.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-24).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.3.5 Configuring the BPEL Server for a Complex Topology
WebCenter Spaces Worklist connections use oracle/wss10_saml_token_with_message_protection_client_policy as the secure OWSM policy for generating outbound SOAP messages to the SOA server. However, by default, this policy uses orakey to encrypt outbound messages.
When the WebCenter domain (where WebCenter Spaces is installed) is configured to use two or more Worklist connections simultaneously, and those connections use a secure message propagation OWSM policy, an additional OWSM policy must be created. This policy must be configured so that the recipient key alias matches the alias by which the certificate of the intended SOA server is stored on the WebCenter Spaces side.
The following steps are required to use more than one external SOA Domain configuration simultaneously on the WebCenter Spaces server:
-
Export the certificate from the external SOA domain and import it into the WebCenter domain under a specific alias (soa_server3_key in the following example).
-
Use Fusion Middleware Control to create a new OWSM policy, and override the recipient key alias to use the same alias as in step 1 above.
-
Create a connection to a BPEL server and use WLST to set the security policy to the policy created in step 2 above.
The following steps show how to perform steps 2 and 3 above. Note that the keystore should already have been created in Section 28.3.4, "Setting Up the Second SOA Domain."
To configure the BPEL server for multiple Worklist connections:
-
Create an OWSM security policy and register the new policy in WebCenter Spaces using Fusion Middleware Control.
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Web Services > Policies.
The Web Services Policies page displays (see Figure 28-25).
-
Select a client policy to use as a base for creating a new policy and click Create Like.
The Create Policy page displays (see Figure 28-26).
-
Name the policy
oracle_wss10_saml_token_with_message_protection_client_policy_soa_server3. -
On the Configuration tab, select the row for
recipient.key.aliasand click Edit. -
Enter
soa_server3_keyas the Value and click OK. -
On the Create Policy page, click Save. The new policy should now be listed on the Web Services Policies page.
-
-
Create a BPEL connection that uses the new security policy with the following WLST command:
setBPELConnection(appName='webcenter', name='WebCenter-Worklist-SOAServer3',url='<your_url>', policy='oracle/wss10_saml_token_with_message_protection_client_policy_soa_server3')
28.3.6 Setting Up the External Portlet Domain Keystore
This section describes how to set up the keystore for the external portlet domain used by one of the WSRP producers for this complex topology.
This section contains the following subsections:
-
Section 28.3.6.1, "Creating the External Portlet Domain Keystore"
-
Section 28.3.6.3, "Configuring the Keystore Using Fusion Middleware Control"
28.3.6.1 Creating the External Portlet Domain Keystore
To create the external portlet domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate the keystore by importing the WebCenter domain's public certificate:
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore producer.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias producer -keypass key_password -keystore producer.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=producer,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate containing the public key so that it can be imported into the WebCenter Spaces domain's keystore:
keytool -exportcert -v -alias producer -keystore producer.jks -storepass keystore_password -rfc -file producer_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Import the certificate to the WebCenter domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
producer_public_key):keytool -importcert -alias producer_public_key -file producer_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST as described in Section 28.3.6.2, "Configuring the Keystore Using WLST,", or using Fusion Middleware Control as described in Section 28.3.6.3, "Configuring the Keystore Using Fusion Middleware Control."
28.3.6.2 Configuring the Keystore Using WLST
After creating the external portlet domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
producer.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./producer.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="producer", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="producer", password="welcome1", desc="Signing key")
-
Restart all servers.
28.3.6.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.3.6.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
webcenterby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-27).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./producer.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
producer -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
producer -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.3.6.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.3.6.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-28).
Figure 28-28 Security Provider Configuration Page

Description of "Figure 28-28 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-29).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.3.7 Setting Up the External WebCenter Domain Keystore
This section describes how to set up an external WebCenter domain used by a custom WebCenter application making WebCenter Spaces WebService calls.
This section contains the following subsections:
-
Section 28.3.7.1, "Creating the External WebCenter Domain Keystore"
-
Section 28.3.7.3, "Configuring the Keystore Using Fusion Middleware Control"
28.3.7.1 Creating the External WebCenter Domain Keystore
To create the external WebCenter domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate the keystore by importing the WebCenter domain's public certificate:
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore external_webcenter_custom.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias external_webcenter_custom -keypass key_password -keystore external_webcenter_custom.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=external_webcenter_custom,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the certificate containing the public key so that it can be imported into the WebCenter Spaces domain's keystore:
keytool -exportcert -v -alias external_webcenter_custom -keystore external_ webcenter_custom.jks -storepass keystore_password -rfc -file external_ webcenter_custom_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,welcome1)
-
-
Import the certificate to the WebCenter domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias external_webcenter_custom_public_key):
keytool -importcert -alias external_webcenter_custom_public_key -file external_ webcenter_custom_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,welcome1)
-
-
Continue by configuring the keystore using either WLST as described in Section 28.3.7.2, "Configuring the Keystore Using WLST,", or using Fusion Middleware Control as described in Section 28.3.7.3, "Configuring the Keystore Using Fusion Middleware Control."
28.3.7.2 Configuring the Keystore Using WLST
After creating the external WebCenter domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="external_webcenter_custom", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="external_webcenter_custom", password="welcome1", desc="Signing key")
-
Restart all servers.
28.3.7.3 Configuring the Keystore Using Fusion Middleware Control
If a keystore provider is already configured, you must first unconfigure the existing keystore provider as described in Section 28.3.7.4, "Unconfiguring a Keystore Provider." Otherwise, continue with the steps below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter domain (
webcenterby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-30).
-
Check Configure Keystore Management and use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./external_webcenter_custom.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
external_webcenter_custom -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
external_webcenter_custom -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.3.7.4 Unconfiguring a Keystore Provider
If a keystore provider is already configured, you must unconfigure the existing keystore provider before configuring a new provider. If a keystore provider is not already configured, continue with the steps to configure the keystore in Section 28.3.7.3, "Configuring the Keystore Using Fusion Middleware Control."
To unconfigure a keystore provider using Fusion Middleware Control:
-
Open Fusion Middleware Control and log in to the target domain.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-31).
-
Uncheck Configure Keystore Management.
-
Click OK.
28.3.7.5 Calling WebCenter Spaces WebServices
In your client project, where you are setting up the GroupSpaceWSContext, set the recipient key alias to be the same as the WebCenter Spaces certificate alias as shown below:
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("webcenter_public");
28.3.8 Command Summary for a Complex Topology
Use the following command summary to quickly configure the keystore and DF properties for a complex topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias webcenter -keypass welcome1 -keystore webcenter.jks -storepass welcome1 -validity 1064
keytool -exportcert -v -alias webcenter -keystore webcenter.jks -storepass welcome1 -rfc -file webcenter_public.cer
keytool -importcert -alias df_webcenter_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=bpel,dc=example,dc=com" -alias bpel -keypass welcome1 -keystore bpel.jks
keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass welcome1 -rfc -file orakay.cer
keytool -importcert -alias orakey -file orakay.cer -keystore webcenter.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=soa_server3,dc=example,dc=com" -alias soa_server3 -keypass welcome1 -keystore soa_server3.jks -storepass welcome1 -validity 1024
keytool -exportcert -v -alias soa_server3 -keystore soa_server3.jks -storepass welcome1 -rfc -file soa_server3_public_key.cer
keytool -importcert -alias soa_server3_public_key -file soa_server3_public_key.cer -keystore webcenter.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore producer.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=producer,dc=example,dc=com" -alias producer -keypass welcome1 -keystore producer.jks -storepass welcome1 -validity 1024
keytool -exportcert -v -alias producer -keystore producer.jks -storepass welcome1 -rfc -file producer_public_key.cer
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore external_webcenter_custom.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=external_webcenter_custom,dc=example,dc=com" -alias external_webcenter_custom -keypass welcome1 -keystore external_webcenter_custom.jks
-storepass welcome1 -validity 1024
keytool -exportcert -v -alias external_webcenter_custom -keystore external_webcenter_custom.jks -storepass welcome1 -rfc -file external_webcenter_custom_public_key.cer
keytool -importcert -alias producer_public_key -file producer_public_key.cer -keystore webcenter.jks -storepass welcome1
When prompted to trust the certificate, say yes.
keytool -importcert -alias external_webcenter_custom_public_key -file external_ webcenter_custom_public_key.cer -keystore webcenter.jks -storepass welcome1
When prompted to trust the certificate, say yes.
Copy webcenter.jks to your domain_home/config/fmwconfig directory, bpel.jks to your SOA1_domain_home/config/fmwconfig directory, soa_server3.jks to your SOA_2_domain_home/config/fmwconfig directory, producer.jks to your External_Portlet_domain_home/config/fmwconfig directory, and external_webcenter_custom.jks to your External_WebCenter_domain_home/config/fmwconfig directory.
Configure the WebCenter Domain Keystore
Follow the steps below to configure the service instance reference for the WebCenter domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
webcenter.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./webcenter.jks. -
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="welcome1", desc="Signing key")
Configure the SOA1 Domain Keystore
Follow the steps below to configure the service instance reference for the SOA1 domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
bpel.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./bpel.jks. -
Using WLST, connect to the SOA1 domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="welcome1", desc="Signing key")
Configure the SOA2 Domain Keystore
Follow the steps below to configure the service instance reference for the SOA2 domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
soa_server3.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./soa_server3.jks. -
Using WLST, connect to the SOA2 domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="soa_server3", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="soa_server3", password="welcome1", desc="Signing key")
Configure the External Portlet Producer Domain Keystore
Follow the steps below to configure the service instance reference for the External Portlet Producer domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
producer.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./producer.jks. -
Using WLST, connect to the External Portlet Producer domain as an admin user and run the following commands:
createCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="welcome1", desc="Keystore key") createCred(map="oracle.wsm.security", key="enc-csf-key", user="external_webcenter_custom", password="welcome1", desc="Encryption key") createCred(map="oracle.wsm.security", key="sign-csf-key", user="external_webcenter_custom", password="welcome1", desc="Signing key")
Configure the DF Keystore Properties File
Using WLST, connect to the WebCenter Spaces domain as an admin user and run the following commands:
org.apache.ws.security.crypto.merlin.keystore.type=jks org.apache.ws.security.crypto.merlin.keystore.password=welcome1 org.apache.ws.security.crypto.merlin.keystore.alias=df_webcenter_public org.apache.ws.security.crypto.merlin.file=<dir_containing_keystore>/owc_discussions.jks
Note:
Be sure to trim any trailing spaces from the line endings. If you are working in a Windows environment, also be sure to use "\\" as the file path separator.Additional DF Connection properties are shown in Table 28-2.
Table 28-8 Additional DF Connection Properties
| Property Name | Property Value | Secured |
|---|---|---|
|
|
|
No |
|
|
|
No |
|
|
|
Yes |
|
|
|
No |
|
|
|
Yes |
|
|
|
No |
28.4 Securing Oracle WebLogic Communication Services (OWLCS) with WS-Security
Follow the steps below to configure WS-Security for Oracle WebLogic Communication Services (OWLCS):
-
Provide the policyURI when creating the Instant Messaging and Presence (IMP) connection.
When you create the connection to the WS-Security enabled OWLCS server, you must provide the
policyURI. The value ofpolicyURIshould be set tooracle/wss11_saml_token_with_message_protection_client_policy. If nopolicyURIis supplied, the application uses a non-secure connection. See also Section 14.1, "What You Should Know About Instant Messaging and Presence Connections." -
Supply an alias name for the private key to the IMP connection.
Provide an additional property in the WebCenter IMP connection named
recipient.alias. Set the value of this property to the alias under which to import the OWLCS certificate. Ensure that this value is unique and is not used already by some other service. If no alias name is supplied, the application uses the default valuewebcenter_owlcs. See also Section 14.3, "Registering Instant Messaging and Presence Servers." -
Determine the private key in the OWLCS keystore (located on the OWLCS instance at
DOMAIN_HOME/config/fmwconfig).Use the following command to list the keystore contents:
keytool -list -v -keystore Serversidekeystore.jks -storepass password
Find the entry with the Entry type set to
keyEntry. The alias name of this entry is the private key (orakeyby default). -
Export the private key from the OWLCS server keystore.
Use the following command to export
orakeyto a certificate file (for example,orakey.cer).keytool -exportcert -v -alias orakey -keystore Serversidekeystore.jks -storepass welcome -rfc -file orakey.cer -
Determine the private key in the WebCenter keystore (on the WebCenter instance at
DOMAIN_HOME/config/fmwconfig).If no keystore is found, proceed to step 6. Otherwise, use the following command to list the keystore contents:
keytool -list -v -keystore default-keystore.jks -storepass welcome
Find the entry with Entry type set to
keyEntryorPrivateKeyEntry. The alias name of this entry is the private key.If no such entry is found, proceed to step 6. Otherwise, continue at step 7.
-
Generate a private key on WebCenter.
Go to
DOMAIN_HOME/config/fmwconfigin your WebCenter installation and run the following command to add a key pair to the keystore. The command creates a keystore nameddefault-keystore.jksif it does not exist, and adds a new private key entry with aliasorasigand the password set towelcome1. You can optionally change the alias, password and domain name command when you run the command.keytool -genkeypair -keyalg RSA -dname "cn=consumer,dc=example,dc=com" -alias orasig -keypass welcome1 -keystore default-keystore.jks -storepass welcome1 -validity 360
-
Configure OWLCS on your WebCenter instance to use the private key.
Run the WLST
createCredcommand substituting the values foruserandpasswordin the first two commands with your private key alias and password.createCred(map='oracle.wsm.security', key='enc-csf-key', user='orasig', password='welcome1', desc='EncryptionKey') createCred(map='oracle.wsm.security', key='sign-csf-key', user='orasig', password='welcome1', desc='SigningKey') createCred(map='oracle.wsm.security', key='keystore-csf-key', user='owsm', password='welcome1', desc='KeystoreKey')
-
Export the private key pair to a certificate.
Export the private key found in step 5 or created in step 6 to a certificate file using the following command:
keytool -exportcert -v -alias orasig -keystore default-keystore.jks -storepass welcome1 -rfc -file orasig.cer
-
Import the certificate generated on the OWLCS Server to the WebCenter keystore.
Copy the certificate generated in step 4 to a temporary location on the WebCenter instance. Import the certificate in the WebCenter instance using the alias name from step 2.
Use the following command to import the certificate in the WebCenter keystore:
keytool -importcert -alias webcenter_owlcs -file orakey.cer -keystore default-keystore.jks -storepass welcome1
-
Import the WebCenter certificate on the OWLCS instance.
Copy the certificate created in step 8 to a temporary location on the OWLCS instance. Go to
DOMAIN_HOME/config/fmwconfigand import the certificate in the keystore under a meaningful alias (for example,webcenter_key) using the following command:keytool -importcert -alias webcenter_key -file orasig.cer -keystore Serversidekeystore.jks -storepass welcome
28.5 Securing WebCenter Spaces for Applications Consuming Spaces Client APIs with WS-Security
This section describes the administrator tasks required to configure WS-Security for WebCenter Spaces so that the communication between the an application exposing WebCenter Spaces APIs (the consumer) and WebCenter Spaces (the producer) is secure, and that the identity of the user invoking the APIs is protected.
You must create a Java keystore and update the credential store so that WebCenter Spaces can verify the authenticity of the SAML-based security tokens received from your application. You must then register this keystore and update the credential store. For information about the developer tasks for developing applications that consume WebCenter Spaces client APIs, see "How to Set Up Your Custom WebCenter Application to Use the WebCenter Spaces APIs" in the Oracle Fusion Middleware Developer's Guide for Oracle WebCenter.
This section includes the following subsections:
28.5.1 Generating the Keystores
Follow the steps below to generate Java keystores for the consumer (the custom WebCenter application) and producer (WebCenter Spaces).
To generate keystores for the consumer and producer:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias consumer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the distinguished name of the consumer (for example,cn=consumer,dc=example,dc=com). The value could be anything but typically matches the distinguished name (DN) of the machine on which the keystore would reside. -
consumer_aliasis the alias of the consumer (for example,consumer) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,consumer.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,360).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle WebServices Security Manager requirements. -
-
Export the public key for the consumer:
keytool -exportcert -v -alias consumer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
-
consumer_aliasis the alias of the consumer (for example,consumer) -
keystoreis the keystore name, (for example,consumer.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
certificate_fileis the file name for the certificate to export the key to (for example,consumer.cer)
-
-
Generate the producer keystore by importing the trusted certificate of the consumer:
keytool -importcert -alias consumer_alias -file certificate_file -keystore keystore -storepass keystore_password
Where:
-
consumer_aliasis the alias of the consumer -
certificate_fileis the certificate file name -
keystoreis the keystore name -
keystore_passwordis the keystore password
-
-
Generate the key pair for the producer:
keytool -genkeypair -keyalg RSA -dname "producer_dname" -alias producer_alias -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
producer_dnameis the name of the producer (for example,cn=producer,dc=example,dc=com) -
producer_aliasis the alias of the producer (for example,producer) -
key_passwordis the password for the new public key, (for example,welcome1) -
keystoreis the keystore name, (for example,producer.jks) -
keystore_passwordis the keystore password, (for example,welcome1) -
days_validis the number of days for which the key password is valid (for example,1024)
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used by keytool for generating the key will not work. -
-
List the contents of the keystore:
keytool -list -v -keystore keystore_name -storepass password
Where:
-
keystore_nameis the name of the consumer keystore file (for example,portal.jks) -
passwordis the keystore password.
The keystore should now have two key entries.
-
-
Export the public key of the producer:
keytool -exportcert -v -alias producer_alias -keystore keystore -storepass keystore_password -rfc -file certificate_file
Where:
-
producer_aliasis the alias of the producer (for example,producer) -
keystoreis the keystore name (for example,producer.jks) -
keystore_passwordis the keystore password, (for example,welcome1 -
certificate_fileis the certificate file name (for example,producer.cer)
-
-
Import the trusted certificate of the producer:
keytool -importcert -alias producer_alias -file certificate_file -keystore keystore_name -storepass keystore_password
Where:
-
producer_aliasis the alias of the producer (for example,producer) -
certificate_fileis the file name or path for the producer's certificate file (for example,../producer/producer.cer) -
keystore_nameis the keystore name (for example,consumer.jks) -
keystore_passwordis the keystore password, (for example,welcome1)
-
28.5.2 Providing the Keystores and Keystore Information to the Application Developer
Before registering the keystores, ensure that you have provided the following to the developer who is creating the application that will be consuming the WebCenter Spaces APIs:
-
The consumer keystore to be used to secure the connection. This is a
.jksfile (for example,consumer.jks). -
The consumer public alias key stored in the keystore (for example,
consumer). -
The password of the consumer public alias key (for example,
welcome1). -
The producer public alias key stored in the consumer keystore (for example,
producer). This is the alias used when importing the trusted certificate of the producer, and created in step 8 of Section 28.5.1, "Generating the Keystores." -
The consumer keystore password (for example,
welcome1).
28.5.3 Registering the Keystores
After you have created the keystores, configure the keystore for WS-Security by performing the following steps. If a keystore provider is already configured, unconfigure the existing keystore provider before proceeding as described in Section 28.1.1.4, "Unconfiguring a Keystore Provider Using Fusion Middleware Control."
To register the keystore provider:
-
Copy the
producer.jksfile to the file system where your producer application is running (for example,DOMAIN_HOME/config/fmwconfig). -
Log in to Fusion Middleware Control.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the domain (for example,
webcenter). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 28-32).
Figure 28-32 Security Provider Configuration Page
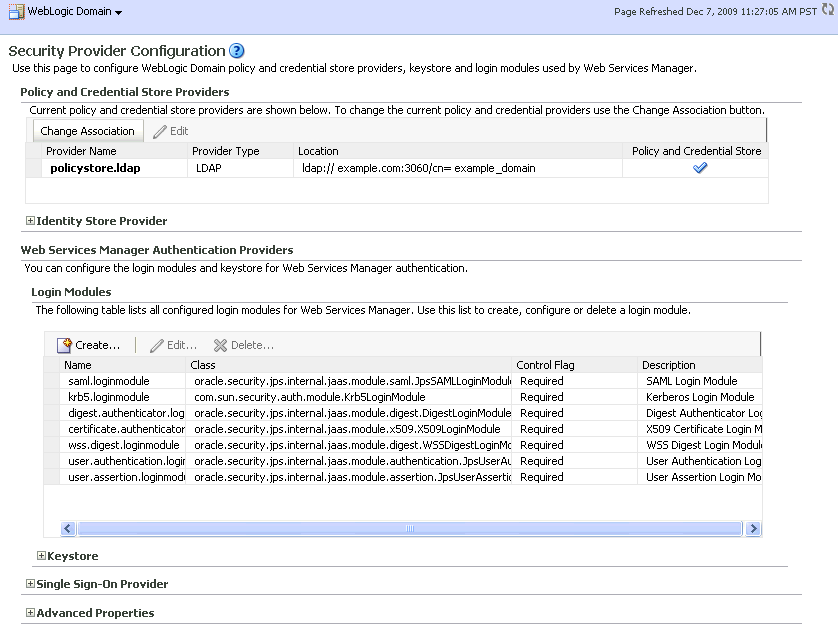
Description of "Figure 28-32 Security Provider Configuration Page"
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 28-33).
-
In the Keystore Path field, specify the location of the keystore that contains the certificate and private key that is used for signing some parts (security token and SOAP message body) of the SOAP message, and enter and confirm the keystore Password.
-
In the Signature Key section, enter
sign-csf-keyas the Key Alias, and enter and confirm the signature key Password (the value used for<key_password>above) for the new public key, (for example,welcome1). -
In the Encryption Key section, enter
enc-csf-keyin the Crypt Alias field, and enter and confirm the encryption key Password (the value used for<key_password>above) for the new public key, (for example,welcome1). -
Click OK to save your settings.
-
Restart the Administration server for the domain.
28.5.4 Updating the Credential Stores
Follow the steps below to update the credential stores from the command line using WLST, or using Fusion Middleware Control.
This section contains the following subsections:
-
Section 28.5.4.1, "Updating the Credential Store Using WLST"
-
Section 28.5.4.2, "Updating the Credential Store Using Fusion Middleware Control"
28.5.4.1 Updating the Credential Store Using WLST
Update the credential store using the WLST createCred command. Use the following example values to add the keystore-csf-key, enc-csf-key, and sign-csf-key encryption keys. Before running the command, be sure to back up the cwallet.sso file.
Example 28-32 keystore-csf-key
createCred(map="oracle.wsm.security",key="keystore-csf-key",user="keystore-csf-key",password="welcome1",desc="Keystore Password")
createCred(map="oracle.wsm.security",key="enc-csf-key",user="producer",password="welcome1",desc="Enc Password")
28.5.4.2 Updating the Credential Store Using Fusion Middleware Control
-
Log in to Fusion Middleware Control.
For information on logging in to Fusion Middleware Control, see Section 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the domain (for example,
webcenter). -
From the WebLogic Domain menu, select Security -> Credentials.
The Credentials page displays (see Figure 28-34).
-
Click Create Map.
-
On the Create Map pop-up, enter
oracle.wsm.securityas the map name and click OK. -
Click Create Key.
-
On the Create Key pop-up, select
oracle.wsm.securityas the map, enterkeystore-csf-keyas the Key, selectPasswordas the Type, enterkeystore-csf-keyas the User Name, supply the Password (in this case, the keystore password ofproducer.jks) from when you created the keystores (for example,welcome1), enter an optional description, and click OK. -
Click Create Key.
-
On the Create Key pop-up, select
oracle.wsm.securityas the map, entersign-csf-keyas the Key, selectPasswordas the Type, enter the public key alias of the keystore used in the custom WebCenter application as the User Name, enter the password of the public key used in the custom WebCenter application as the Password, enter an optional description, and click OK. -
Click Create Key.
-
On the Create Key pop-up, select
oracle.wsm.securityas the map, enterenc-csf-keyas the Key, selectPasswordas the Type, enter the public key alias of the keystore used in the WebCenter instance (for example,webcenter)as the User Name, enter the password of the public key used in the custom WebCenter application as the Password, enter an optional description, and click OK. -
Restart the Administration server and
WLS_Customor managed server on which the custom WebCenter application is hosted.