







|
The Java SSM is a java-based product that allows an application developer to access sets of interfaces to define and implement security related information and requirements specific to a Java application. These interfaces support the most commonly required security functions and are organized into services that are logically grouped by functionality.
After you use the Java SSM interfaces to implement security functions in your Java application, you can deploy and run your application on any instance of a Java SSM runtime that supports the configuration requirements of your application.
The Java SSM offers five security services: Authentication Service, Authorization Service, Auditing Service, Role Service, and Credential Mapping Service. The name of each service indicates the type of function it is used to implement within a Java application. Each of these services is discussed in more detail later.
Because most major functions required by Java applications developed using the Java SSM are performed within the security framework, this architecture has several benefits, including:
The following topics provide more information on the Java SSM:
Figure 2-1 shows the major components that make up the SSM environment.
The Administration Console allows you to manage and configure multiple SSMs. While SSMs specify and consume configuration data and then services security requests accordingly, the Administration Console allows you to display the security providers that are plugged into the security framework and to display and modify the configuration data for those providers.
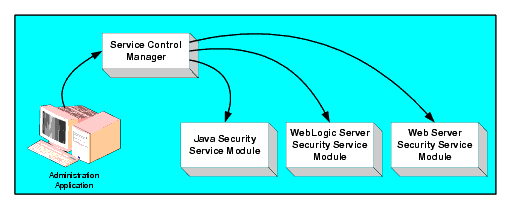
The Service Control Manager (SCM) is an essential component of the Oracle Entitlements Server configuration provisioning mechanism and of a fully-distributed security enforcement architecture.
| Note: | Not all SSM machines require an SCM. When no SCM is installed, the SSM(s) can obtain configuration information from data that is exported from the policy database to an XML file. |
An SCM is a machine agent that exposes a provisioning interface to the Administration Console to facilitate the management of a potentially large number of distributed SSMs. An SCM can receive and store metadata updates, both full and incremental, initiated by the Administration Console.
The Administration Console uses the provisioning mechanism of the SCM to distribute configuration and policy data to each SSM where it is consumed locally (see Figure 2-2). SSMs (which can be distributed throughout an enterprise) can be embedded in Java applications, application servers, and web servers. After you use the Administration Console to configure an instance of an SSM with configuration and policy data, the SSM does not require any additional communication with the SCM to perform security functions. However, the SCM maintains communication with the SSM to distribute full and incremental updates.
Figure 2-3 shows the major components of the Java SSM. The Java SSM comprises the security service APIs, the security framework, and the security providers that you configure in any given instance of a Java SSM runtime.
The following topics describe these components:
The Java SSM supports the following security service APIs:
The Authentication Service provides functions to an application related to establishing, verifying, and transferring a person or a process. Thus, the Authentication Service provides two main functions: authentication and identity assertion.
The Authorization Service is a service that allows an application to determine if a specific identity is permitted to access a specific resource. This decision may then be enforced in the application directly at the policy enforcement point.
The Auditing Service allows an application to log events based upon activity related to enterprise security. The Java SSM runtime uses these mechanisms to log appropriate data when events occur.
The Role Service allows an application to extract role information about specific identities and resources within the context of the application. These roles may then be used to customize interfaces.
| Note: | Roles themselves should not be used for authorization, as many policies allowing or disallowing access to a resource may be written against a role. It is best that you use the Authorization Service to determine actual rights. |
The Credential Mapping Service allows an application to fetch credentials of certain types that are associated with a specific identity for a specific resource. These credentials may then be used on behalf of that identity to provide some privileged function, such as logging into a database or sending e-mail.
The primary function of the Security Framework is to provide an application programming interface (API) that security and application developers use to implement security functions in Java applications. Within that context, the Security Framework also acts as an intermediary between security functions that you implement in Java applications using the Java security service APIs and security providers configured into the Java SSM. For more information on the Security Framework, see Introduction to Oracle Entitlements Server.
When you install the Java SSM, a JAR file is deployed that contains all the default security providers that ship with the product. However, before any of the security providers can be used, you must use the Administration Console to configure them in the Java SSM. You have the option of configuring either the default security providers that ship with the product or custom security providers, which you develop or purchase from third-party security vendors. The Java SSM supports the following types of security providers:
For more information on the security providers, see Introduction to Oracle Entitlements Server. For information on developing custom security providers, see Developing Security Providers for Oracle Entitlements Server.


|