Developing Security Providers
|
|
Introduction to Developing Security Providers
This section cover the following topics:
Overview of the Development Process
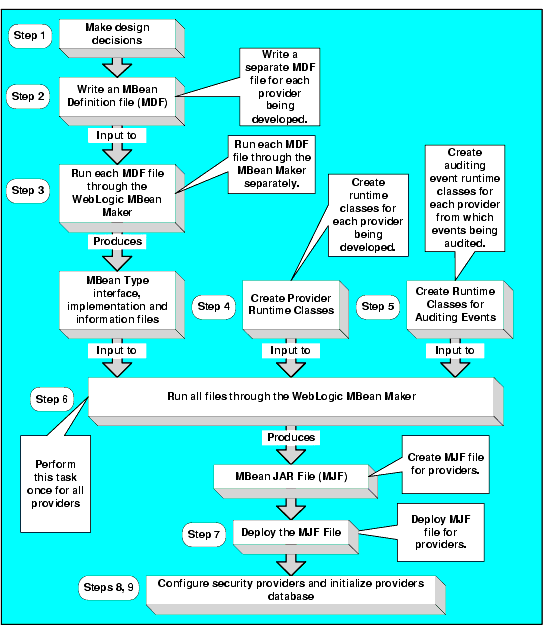
To develop a custom security provider, you perform the following tasks:
- Create the auditing event classes for each security provider from which events are audited (optional).
- Run the files generated by the MBean Maker and the runtime class files through the WebLogic MBean Maker to produce an MBean JAR file.
- Deploy the MJF file to the BEA AquaLogic Enterprise Security systems from which you want to use the providers.
Note: An MBean JAR file can contain multiple security providers, therefore you only need to run the MBean Maker once to produce the MBean JAR file.
Note: This includes copying the JAR file to both the Administration Application and the Security Service Module provider directories.
Figure 1-1 illustrates the security provider development process. For detailed instructions for each of the development tasks, see Developing Custom Security Providers.
Figure 1-1 Developing Custom Security Provider Tasks
Types of Providers
You use the SSPI provided with the product to create runtime classes for custom security providers, which are located in the weblogic.security.spi package. For more information about this package, see Javadocs for Security Service Provider Interfaces.
Table 1-1 maps the types of security providers and their components with the SSPI and other interfaces you use to develop them.