Installing WebLogic Server v8.1 Security Service Module
|
|
Integrating with AquaLogic Data Services Platform
This section covers the following topics:
Introduction
AquaLogic Enterprise Security (ALES) can provide fine-grained entitlements for Data Services serviced by AquaLogic Data Services Platform (ALDSP) 2.1 (formally Liquid Data). AquaLogic Enterprise Security can be used to manage access control to entire services or elements of those services. AquaLogic Enterprise Security allows you to have common set of security policies for a heterogeneous environment, and a single security infrastructure that supports WebLogic Portal, Server, and custom applications.
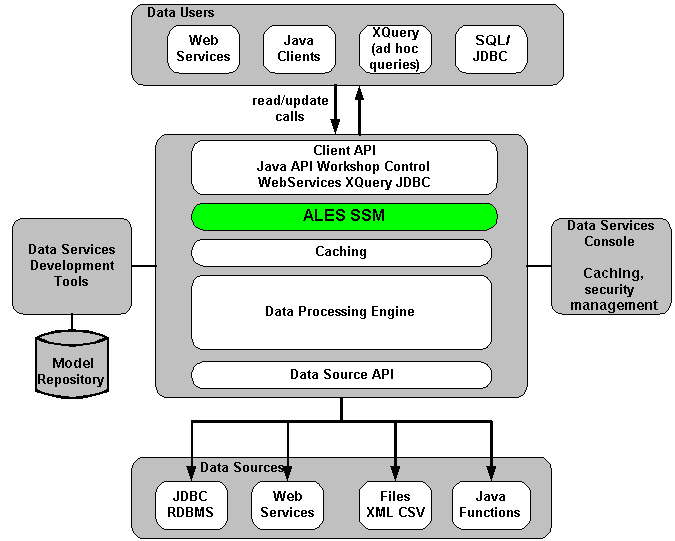
The ALES service does not replace all of the management functionality provided by the ALDSP. The ALDSP Administrative console (ldconsole) is still used to manage all of the attributes of the various data services aggregated by ALDSP (see Figure 6-1).
Figure 6-1 ALDSP Integration Overview
The AquaLogic Enterprise Security WebLogic SSM enables you to write, deploy, and manage fine-grained policy for controlling access to all WebLogic server application resources, including data services. A specific resource type ld allows a security administrator to represent the data services in the ALES resource hierarchy. Elements of that data service are also converted to the ALES format for evaluation by the ASI authorization engine.
For more information, see the following topics:
- Integration Features on page 6-3
- Supported Use-case Scenario on page 6-3
- Constraints and Limitations on page 6-3
Integration Features
AquaLogic Data Service Platform (ALDSP) 2.1 requires WebLogic Server 8.1 Service Pack 5. While the ALES framework allows for different security providers to be used with ALDSP, the following providers were certified:
- The ASI Authorization and Role Mapping providers enables you to use AquaLogic Enterprise Security to write, deploy, and manage fine-grained authorization of Data Services.
- The Database Authentication provider performs authentication services for for the SSM.
Supported Use-case Scenario
The following use-case scenario is supported when you integrate AquaLogic Enterprise Security with AquaLogic Data Services Platform:
- The AquaLogic Enterprise Security Administration Server assumes responsibility for management and policy of data services and elements of those services through the ALES console or Policy Management API.
- The AquaLogic Enterprise Security Administration Server is responsible for access control of J2EE application deployed on the ALDSP WebLogic Server.
- The ALDSP Administration Console continue to be the management point for data services.
Constraints and Limitations
AquaLogic Enterprise Security integration with ALDSP has the following constraints and limitations:
- Liquid Data 8.1 is not supported
- Data service elements must be enabled for security through the ALDSP Admin console before ALES can manage element-based access control.
- ALES cannot provide entitlements and control which records are returned by the data service. This can still be done, but must be performed through the ALDSP Admin Console.
Integration Pre-Requisites
Before you begin, you must ensure that the following pre-requisites are satisfied:
- WebLogic Platform 8.1 Service Pack 5
- WebLogic Server v8.1 Security Service Module, Version 2.1
- You must have access to an Administration Console that is running on the AquaLogic Enterprise Security Administration Server, Version 2.1 on either the local machine or a remote machine.
- ALDSP 2.1
Integrating with AquaLogic Data Services Platform
This section describes how to integrate AquaLogic Enterprise Security with AquaLogic Data Services Platform. Once integrated, you can use the AquaLogic Enterprise Security Administration Console to write and deploy a set of authorization and role mapping policies to protect Data Services and elements of those services.
Note: The instructions provided is this section use the ALDSP sample application RTL App that ships with the ALDSP 2.1 software distribution. This procedure is representative of any integration of AquaLogic Enterprise Security with ALDSP.
To integrate AquaLogic Enterprise Security with AquaLogic Data Services Platform, perform the following tasks:
- Enabling Elements for Access Control
- Creating the SSM configuration
- Binding the SSM configuration
- Distributing the SSM configuration
- Creating an Instance of the Security Service Module
- Enrolling the Instance of the Security Service Module
- Creating the WebLogic Server startWeblogicALES File
- Modifying the WebLogic Server setDomainEnv script
- Creating the security.properties File
- Configuring Policy for Data Services
- Discovering Data Services
- Distributing Policy and SSM configuration
- Starting the WebLogic Server
- Accessing the ALDSP Application
Enabling Elements for Access Control
Before enabling your ALDSP domain for ALES, open the ALDSP Administration console by:
- Browse to the Data services elements that are to be controlled by ALES. For this example, enable the following:
Creating the SSM configuration
This section describes how to create a new SSM configuration named aldsprealm. A SSM configuration defines the set of security providers to use for adjudication, authentication, auditing, authorization, role mapping, and credential mapping services.
Note: To implement the use-case scenario described in Supported Use-case Scenario, the recommended configuration as described in this section, however, you may be able to extend this with other providers.
Refer to Table 6-1and use the AquaLogic Enterprise Security Administration Server to configure the security providers listed there. Set the Configuration ID to aldsprealm. For instructions on creating a SSM configuration, see Configuring a Security Service Module in the Administration and Deployment Guide and the Console Help.
Binding the SSM configuration
The SSM configuration must be bound to a Service Control Manager (SCM).
To bind the aldsprealm SSM configuration, see "Binding a Security Service Module to a Service Control Manager" in the Console Help
Distributing the SSM configuration
The aldsprealm SSM configuration must be distributed.
To distribute the aldsprealm SSM configuration, see "Distributing Configuration" in the Console Help.
Creating an Instance of the Security Service Module
Before starting a WebLogic Server 8.1 Security Service Module, you must first create an instance of the WebLogic Server 8.1 Security Service Module using the Create New Instance Wizard.
To create an instance of a WebLogic Server 8.1 Security Service Module, see Creating an Instance of the WebLogic 8.1 Security Service Module.
Enrolling the Instance of the Security Service Module
You must have the Administration Server running prior to enrolling the Security Service Module.
Note: While you can use the demonstration digital certificate in a development environment, you should never use it in a production environment.
To enroll a security service module, see Enrolling the Instance of the Security Service Module.
Creating the WebLogic Server startWeblogicALES File
This document assumes that you have created an ALDSP domain on the local machine.
Before you can start a WebLogic server that uses BEA AquaLogic Enterprise Security, you must create the startWeblogicALES file based on the startWeblogic file that is located in the WebLogic domain.
The startWeblogic file for the ALDSP domain for RTLApp is located at: <bea_home>\weblogic81\samples\domains\ldplatform\startWebLogic[.sh|.cmd]
To create the startWeblogicALES.cmd file for Windows, perform the steps:
- Add a line in the startWeblogicALES to call the environment batch file set-wls-env.bat. For example, add it below the line: set SAVE_JAVA_OPTIONS=
- Add the AquaLogic Enterprise Security classpath variables to the classpath. For example, add the following text before the line: echo CLASSPATH=%CLASSPATH%
-
echo %JAVA_HOME%\bin\java %JAVA_VM% %MEM_ARGS% %JAVA_OPTIONS%%WLES_JAVA_OPTIONS%-Dweblogic.Name=%SERVER_NAME% -Djava.security.policy=%WL_HOME%\server\lib\weblogic.policy %PROXY_SETTINGS% %SERVER_CLASS%%JAVA_HOME%\bin\java %JAVA_VM% %MEM_ARGS% %JAVA_OPTIONS%%WLES_JAVA_OPTIONS%-Dweblogic.Name=%SERVER_NAME% -Djava.security.policy=%WL_HOME%\server\lib\weblogic.policy %PROXY_SETTINGS% %SERVER_CLASS%echo Redirecting output from WLS window to %WLS_REDIRECT_LOG%%JAVA_HOME%\bin\java %JAVA_VM% %MEM_ARGS% %JAVA_OPTIONS%%WLES_JAVA_OPTIONS%-Dweblogic.Name=%SERVER_NAME% -Djava.security.policy=%WL_HOME%\server\lib\weblogic.policy %PROXY_SETTINGS% %SERVER_CLASS% > "%WLS_REDIRECT_LOG%" 2>&1
Note: Similar changes must be made for UNIX platforms as well.
Modifying the WebLogic Server setDomainEnv script
Edit the setDomainEnv script to use Sun java compiler (BEA jRockit is the default java compiler in a platform domain start script).
set SUN_JAVA_HOME=c:\bea\j2sdk1.4.2_05
Creating the security.properties File
Create a text file named security.properties and place it in the domain directory. You use this file to define the AquaLogic Enterprise Security realm and the default realm.
# AquaLogic Enterprise Security Configuration File
#
# This file contains AquaLogic Enterprise Security configuration
# properties. By default, the AquaLogic Enterprise Security runtime
# looks for a property file called 'security.properties' in the
# working directory
wles.realm=aldsprealm
wles.default.realm=aldsprealm
Configuring Policy for Data Services
Developing a set of policies typically begins by determining which resources you need to protect and your access control requirements. You then create the identity directory, resources, groups, users, and roles that you will use to write policies to protect those resources. Next you write a set of authorization and role mapping policies to define access control on those resources. Finally, you deploy the set of polices to the WebLogic Server 8.1 Security Service Module that you use to control access to your data services.
For more information on how to use the Administration Console to write policy, see the Policy Managers Guide and the Console Help.
This section covers the following topics:
- Creating the Identity Directory and Users
- Configuring Resources and Privilege
- Creating the Role Mapping Policies
- Creating Authorization Policies
Creating the Identity Directory and Users
This section describes how to use the ALES Administration Console to create an identity directory, groups, and users for an ALDSP application.
Note: This procedure uses aldspusers as the name of the Identity directory; however, you can use a different name.
To create the Identity directory and users:
Configuring Resources and Privilege
This section describes how to use the Administration Console to define the application resources that you will protect using ALES.
To configure resources, perform the following tasks:
Creating the RTLApp Application Resources
Note: You can choose any application name for your ALDSP application.
To create application resources, perform the following steps:
- In the Resources page, select the Policy node, and click New. The Create Resource dialog box appears.
- In the Name text box, enter aldsprealm, select Binding from the Type drop-down list box, and click Ok. The aldsprealm resource appears under the Policy node.
- From the Type drop-down list box, select Binding Application, check the Distribution Point and Allow Virtual Resources check boxes, and click Ok.
- Refer to Table 6-2 and modify the configuration of the ASI Authorization provider and the ASI Role Mapper Provide as described there.
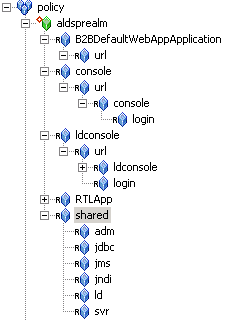
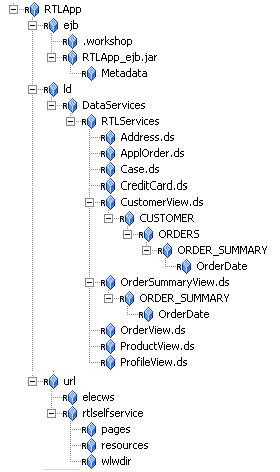
Creating the ALDSP Resources
Figure 6-2 shows the ALDSP resource tree with all nodes expanded except the RTLApp node. The resources under that RTLApp node are shown in Figure 6-3. You must create the resources shown in Figure 6-2 and Figure 6-3.
Figure 6-2 ALDSP Resource Tree with RTLApp Node Collapsed
Figure 6-3 ALDSP Resource Tree with RTLApp Node Expanded
Creating the Role Mapping Policies
This section describes how to use the Administration Console to create the role mapping policies that will be used to control access the sample ALDSP application.
Table 6-3 lists the role mapping policies required for the WebLogic domain.
To create the role mapping policies, refer to Table 6-3 and perform the following steps.
Warning: If you do not create the Everyone role mapping policy correctly, none of the authorization policies defined in Figure 6-4 will work.
Creating Authorization Policies
This section describes how to use the Administration Console to create authorization policies to protect data services and application resources. Table 6-4 lists the authorization policies required for WebLogic server, the WebLogic server console, and the RTL sample application.
Perform the following steps create the authorization policies listed in Table 6-4.
- Expand the Policy folder in the left pane, and click Authorization Policies. The Authorization Policies page appears.
- To create the first authorization policy listed in Table 6-4.
Note: If Table 6-4 lists multiple resources for a single privilege and role, you may define all of the resources in one authorization policy.
- Repeat steps 4 to 6 for each of the remaining authorization policies listed in Table 6-4.
Discovering Data Services
When developing policies for use with a Security Service Module, you can use the Discovery mode feature to help define your policy components. Instructions for using Discovery mode are provided in the Resource Discovery section in the Policy Managers Guide.
Distributing Policy and SSM configuration
Distribute policy and SSM configuration to the WebLogic Server 8.1 SSM.
For information on how to distribute policy and SSM configuration, see "Deployment" in the Console Help. Be sure to verify the results of your distribution.
Starting the WebLogic Server
To start a WebLogic server, perform the following steps:
Accessing the ALDSP Application
To access the RTLApp running on an ALDSP server:
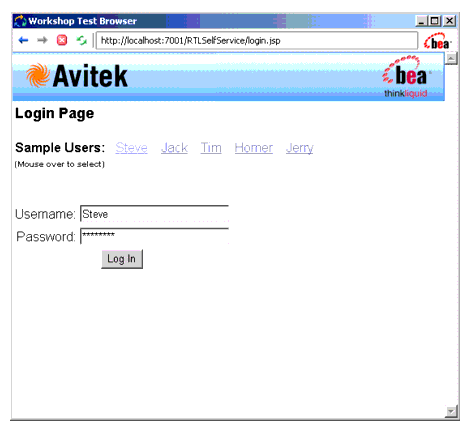
- Open browser to visit http://<host_name>:<port>/RTLSelfService, where <host_name> is the machine on which RTL application is running. The browser is redirected to authentication page (see Figure 6-4).
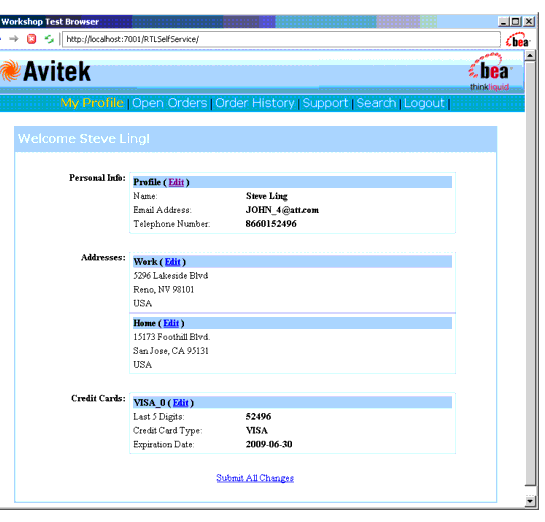
- Set username as Steve by dragging over link, then click Login button. Client should be granted access to Profile Page (see Figure 6-5).
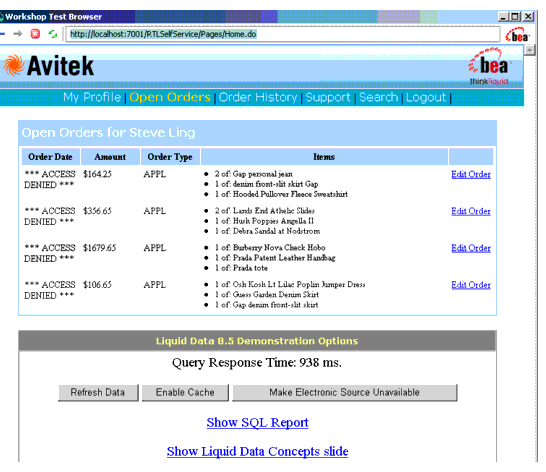
- Select Open Orders Page from top menu. Open orders should be visible (see Figure 6-6). Order Data should have "ACCESS DENIED".
Figure 6-4 Authentication Page