Table 2-6 Context Attributes and Administrative Access
|
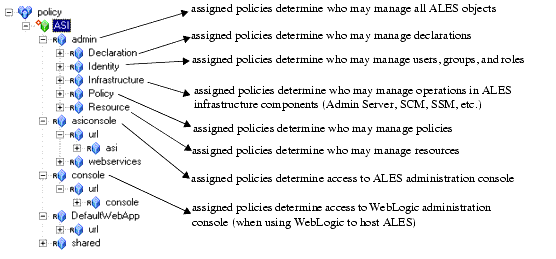
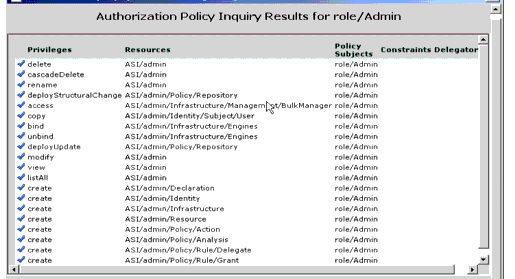
Admin Resource
|
Privilege
|
Context attributes
|
Description
|
|
Declaration/Attribute
|
create
|
declaration
|
Queried when user attempts to create a new attribute declaration.
|
|
delete
|
declaration
|
Queried when user attempts to delete an attribute declaration.
|
|
rename
|
declaration, new_name
|
Queried when user attempts to rename an attribute declaration.
|
|
modify
|
declaration
|
Queried when user attempts to modify an attribute declaration.
|
|
Declaration/
Constant
|
create
|
declaration, value
|
Queried when user attempts to create a new constant.
|
|
delete
|
declaration, value
|
Queried when user attempts to delete a constant.
|
|
rename
|
declaration, value, new_name
|
Queried when user attempts to rename a constant.
|
|
modify
|
declaration, value, new_value
|
Queried when user attempts to modify a constant.
|
|
Declaration/ Enumeration
|
create
|
declaration, value
|
Queried when user attempts to create a new enumeration.
|
|
delete
|
declaration, value
|
Queried when user attempts to delete an enumeration.
|
|
rename
|
declaration, value, new_name
|
Queried when user attempts to rename an enumeration.
|
|
modify
|
declaration, value, new_value
|
Queried when user attempts to modify an enumeration.
|
|
Declaration/Evaluation Function
|
create
|
declaration
|
Queried when user attempts to create an evaluation function.
|
|
delete
|
declaration
|
Queried when user attempts to delete an evaluation function.
|
|
rename
|
declaration, new_name
|
Queried when user attempts to rename an evaluation function.
|
|
Identity/Directory/Instance
|
create
|
directory
|
Queried when user attempts to create a directory.
|
|
delete
|
directory
|
Queried when user attempts to delete a directory.
|
|
cascade Delete
|
directory
|
Queried when user attempts to delete a directory and all its users.
|
|
rename
|
directory, new_name
|
Queried when user attempts to rename a directory.
|
|
Identity/Directory/ AttributeMapping/Single
|
create
|
attribute, default_value, directory
|
Queried when user attempts to add a scalar attribute to an attribute schema of a directory.
|
|
delete
|
attribute, default_value, directory
|
Queried when user attempts to delete a scalar attribute from an attribute schema of a directory.
|
|
modify
|
attribute, default_value, directory, new_default_value
|
Queried when user attempts to modify a scalar attribute in an attribute schema for a directory.
|
|
Identity/Directory/ AttributeMapping/List
|
create
|
attribute, default_value, directory
|
Queried when user attempts to add a vector attribute to an attribute schema of a directory.
|
|
delete
|
attribute, default_value directory
|
Queried when user attempts to delete a vector attribute from an attribute schema of a directory.
|
|
modify
|
attribute, default_value, directory, new_default_value
|
Queried when user attempts to modify a vector attribute in an attribute schema of a directory.
|
|
Identity/Subject/User
|
create
|
subject_name
|
Queried when user attempts to create a new user.
|
|
copy
|
subject_name, new_subject_name
|
Queried when user attempts to copy a user.
|
|
delete
|
subject_name
|
Queried when user attempts to delete a user.
|
|
cascade Delete
|
subject_name
|
Queried when user attempts to cascade a user and all policies associated with the user.
|
|
rename
|
subject_name, new_subject_name
|
Queried when user attempts to rename a user.
|
|
Identity/Subject/Group
|
create
|
subject_name
|
Queried when user attempts to create a new group.
|
|
delete
|
subject_name
|
Queried when user attempts to delete a group.
|
|
rename
|
subject_name, new_subject_name
|
Queried when user attempts to rename a group.
|
|
addMember
|
subject_name, member_subject
|
Queried when user attempts to add a member to a group.
|
|
remove Member
|
subject_name, member_subject
|
Queried when user attempts to remove a member from a group.
|
|
Identity/Subject/ AttributeAssignment/Single
|
create
|
attribute, value, subject_name
|
Queried when user attempts to set a value to a currently unset scalar subject attribute.
|
|
delete
|
attribute, value, subject_name
|
Queried when user attempts to unset a currently set scalar subject attribute.
|
|
modify
|
attribute, value, subject_name, new_value
|
Queried when user attempts to modify the value of a currently set scalar subject attribute.
|
|
Identity/Subject/ AttributeAssignment/List
|
create
|
attribute, value, subject_name
|
Queried when user attempts to set a value to a currently unset vector subject attribute.
|
|
delete
|
attribute, value, subject_name
|
Queried when user attempts to unset a currently set vector subject attribute.
|
|
modify
|
attribute, value, subject_name, new_value
|
Queried when user attempts to modify the value of a currently set vector subject attribute.
|
|
Identity/Subject/
Password
|
modify
|
subject_name
|
Queried when user attempts to modify the password for a user. The subject_name attribute contains the name of the user for which the password is associated.
|
|
Resource/Instance
|
create
|
resource, resource_type
|
Queried when user attempts to create a new resource.
|
|
delete
|
resource
|
Queried when user attempts to delete a resource.
|
|
cascade Delete
|
resource
|
Queried when user attempts to cascade delete a resource. This includes deletion of all child resources and associated policies.
|
|
rename
|
resource, new_name
|
Queried when user attempts to rename a resource.
|
|
Resource/Attribute
Assignment/Single
|
create
|
attribute, resource, value
|
Queried when user attempts to set a value to a currently unset scalar resource attribute.
|
|
delete
|
attribute, resource, value
|
Queried when user attempts to unset a currently set scalar resource attribute.
|
|
modify
|
attribute, resource, value, new_value
|
Queried when user attempts to modify the value of a currently set scalar resource attribute.
|
|
Resource/Attribute
Assignment/List
|
create
|
attribute, resource, value
|
Queried when user attempts to set a value to a currently unset vector resource attribute.
|
|
delete
|
attribute, resource, value
|
Queried when user attempts to unset a currently set vector resource attribute.
|
|
modify
|
attribute, resource, value, new_value
|
Queried when user attempts to modify the value of a currently set vector resource attribute.
|
|
Resource/MetaData/
IsApplication
|
modify
|
resource, value, new_value
|
Queried when user attempts to toggle the "is application" resource metadata.
|
|
Resource/MetaData/
IsDistributionPoint
|
modify
|
resource, value, new_value
|
Queried when user attempts to toggle the "is distribution point" resource metadata.
|
|
Resource/MetaData/
Logical Name
|
create
|
logical_name, resource
|
Queried when user attempts to create a logical name for a resource.
|
|
delete
|
logical_name, resource
|
Queried when user attempts to delete a logical name for a resource.
|
|
rename
|
logical_name, resource, new_name
|
Queried when user attempts to rename a logical name for a resource.
|
|
Policy/Grant
|
create
|
action, resource, subject_name, constraint
|
Queried when user attempts to create a new grant policy. "action", "resource", and "subject_name" attributes are lists.
|
|
delete
|
action, resource, subject_name, constraint
|
Queried when user attempts to delete a grant policy. The "action", "resource", and "subject_name" attributes are lists.
|
|
modify
|
action, resource, subject_name, constraint, new_action, new_resource, new_subject_name, new_constraint
|
Queried when user attempts to modify a grant policies "action", "resource", and "subject_name" attributes are lists.
|
|
Policy/Deny
|
create
|
action, resource, subject_name, constraint
|
Queried when user attempts to create a new deny policy. "action", "resource", and "subject_name" attributes are lists.
|
|
delete
|
action, resource, subject_name, constraint
|
Queried when user attempts to delete a deny policy. The "action", "resource", and "subject_name" attributes are lists.
|
|
modify
|
action, action_type, resource, subject_name, subject_type, constraint, new_effect, new_action, new_action_type, new_resource, new_subject_name, new_subject_type, new_constraint
|
Queried when user attempts to modify a deny policy. The "action", "resource", and "subject_name" attributes are lists.
|
|
Policy/Delegate
|
create
|
action, resource, subject_name, delegator, constraint
|
Queried when user attempts to create a new delegate policy. "action", "resource", and "subject_name" attributes are lists.
|
|
delete
|
action, resource, subject_name, delegator, constraint
|
Queried when user attempts to delete a delegate policy. The "action", "resource", and "subject_name" attributes are lists.
|
|
modify
|
action, resource, subject_name, delegator, constraint, new_action, new_resource, new_subject_name, new_delegator, new_constraint
|
Queried when user attempts to modify a delegate policy. The "action", "resource", and "subject_name" attributes are lists.
|
|
Policy/Action/Role/
Instance
|
create
|
action
|
Queried when user attempts to create a new role.
|
|
delete
|
action
|
Queried when user attempts to delete a role.
|
|
rename
|
action, new_name
|
Queried when user attempts to rename a role.
|
|
Policy/Action/
Privilege/Instance
|
create
|
action
|
Queried when user attempts to create a privilege.
|
|
delete
|
action
|
Queried when user attempts to delete a privilege.
|
|
rename
|
action, new_name
|
Queried when user attempts to rename a privilege.
|
|
Policy/Action/
Privilege/Group
|
create
|
action_group
|
Queried when user attempts to create a privilege group.
|
|
delete
|
action_group
|
Queried when user attempts to delete a privilege group.
|
|
rename
|
action_group, new_name
|
Queried when user attempts to rename a privilege group.
|
|
addMember
|
action_group, action
|
Queried when user attempts to add a privilege to a privilege group.
|
|
remove Member
|
action_group, action
|
Queried when user attempts to remove a privilege from a privilege group.
|
|
Policy/Analysis/
Inquiry Query
|
create
|
title, owner, effect_type, subjects, actions, resources, delegator
|
Queried when user attempts to create a new policy query.
|
|
delete
|
title, owner
|
Queried when user attempts to delete a policy query.
|
|
modify
|
title, owner, effect_type, subjects, actions, resources, delegator
|
Queried when user attempts to modify a policy query.
|
|
execute
|
title, owner, effect_type, subjects, actions, resources, delegator
|
Queried when user attempts to execute a policy query. If this is an unsaved query "title" and "owner" will be set to an empty string.
|
|
Policy/Analysis/
Verification Query
|
create
|
title, owner, actions, resources
|
Queried when user attempts to create a new policy verification query.
|
|
delete
|
title, owner
|
Queried when user attempts to delete a policy verification query.
|
|
modify
|
title, owner, actions, resources
|
Queried when user attempts to modify a policy verification query.
|
|
execute
|
title, owner, actions, resources
|
Queried when user attempts to execute a policy verification query. If this is an unsaved query "title" and "owner" will be set to an empty string.
|
|
Policy/Repository
|
deploy Update
|
resource, directory
|
Queried when user attempts to deploy a policy update.
"resource" is the distribution node and all nodes below it may be effected. This check is made for each chosen distribution point.
|
|
deploy Structural Change
|
deleted_directories, deployed_engines, deleted_engines, deleted_bindings, deleted_applications
|
Queried when user attempts to deploy a structural change.
|
|
Infrastructure/Engines/ARME
|
create
|
engine
|
Queried when user attempts to create a new Security Service Module.
|
|
delete
|
engine
|
Queried when user attempts to delete a Security Service Module.
|
|
rename
|
engine, new_name
|
Queried when user attempts to rename a Security Service Module.
|
|
bind
|
engine, resource
|
Queried when user attempts to bind a resource to a Security Service Module.
|
|
unbind
|
engine, resource
|
Queried when user attempts to unbind a resource from a Security Service Module.
|
|
Infrastructure/Engines/SCM
|
create
|
engine
|
Queried when user attempts to create a Service Control Manager.
|
|
delete
|
engine
|
Queried when user attempts to delete a Service Control Manager.
|
|
rename
|
engine, new_name
|
Queried when user attempts to rename a Service Control Manager.
|
|
bind
|
engine, resource
|
Queried when user attempts to bind a Security Service Module to a Service Control Manager. The "resource" contains the name of the Security Service Module.
|
|
unbind
|
engine, resource
|
Queried when user attempts to unbind a Security Service Module from a Service Control Manager. The "resource" contains the name of the Security Service Module.
|
|
Infrastructure/ Management/Console
|
login
|
|
Queried when user attempts to login to the Administration Console.
|
|
Infrastructure/ Management/BulkManager
|
login
|
|
Queried when user attempts to login to the Policy Import tool.
|