









|
This section describes the general architecture of the BEA AquaLogic Enterprise Security services, providers and service modules. Each Security Service Module comes with a set of security providers. Although applications can leverage the services offered through the existing security providers, the flexible infrastructure also allows security vendors, integrators, and customers to write their own security providers. The BEA AquaLogic Enterprise Security providers and third-party security providers can be mixed and matched to create unique security solutions, allowing organizations to take advantage of new technology advances in some areas while retaining proven methods in others. The Administration Server allows you to configure and manage all your security providers and service modules through one unified management console.
The architecture comprises the following major components, which are discussed in the following sections:
BEA AquaLogic Enterprise Security lets you control all of your security policies and configuration data from a single console.
| Note: | This release of AquaLogic Enterprise Security supports any of the WebLogic 9.x security providers. However, the Security Service Module for WebLogic Server 9.x is configured differently, as described in Integrating ALES with Application Environments. |
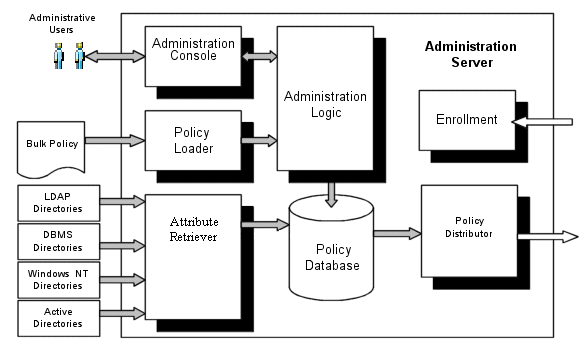
The Administration Server gives you the enterprise-wide visibility you need to analyze security policies and ensure that applications and resources are properly protected. BEA AquaLogic Enterprise Security also lets you delegate security administration to remote administrators who often better understand local users and business needs and who are better positioned to manage the security policies. By combining centralized control with delegated administration, you can define and manage overall policies while specifying the management responsibilities to be handled by organizational administrators. For additional information on the Administration Server features, see Security Administration. The Administration Server consists of several components (as shown in Figure 3-1), including:
Policy Distributor—Ensures that the correct policies are provided to each Security Service Module and maintains policy synchronization.
Policy Database—Maintains policy data managed by the Administration Server in a relational database. The database management system provides the authoritative source of configuration and policy. Data from the policy database is distributed to the Security Service Modules by the Policy Distributor.
Policy Exporter—Exports policy data from the policy database for later use with the same Administration Server or another instance of the Administration Server.
Policy Loader—Imports policy data from an external file, generated in another system, exported from another instance of an Administration Server, or manually coded.
Administration Console—Supports administrative policy security and administration delegation through a web browser-based user interface. Security configuration, policy configuration, user attributes (if required), resources, and rules are all managed through the console.
Administration Logic—Maintains the Policy Database used by both the Administration Console and the Policy Loader.
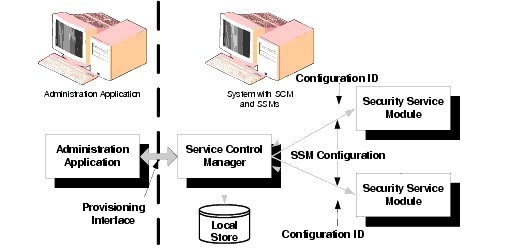
BEA AquaLogic Enterprise Security employs a fully-distributed security enforcement architecture consisting of Security Service Modules embedded in applications, application servers, and web servers throughout an enterprise (see Figure 3-2). To facilitate the management of a potentially large number of distributed Security Service Modules, the Administration Server uses a remote administration mechanism to distribute appropriate configuration and policy data to each Security Service Module. (The Security Service Module for WebLogic Server 9.x is configured differently, as described in Integrating ALES with Application Environments.)
The Service Control Module (SCM) is an essential component of this remote administration mechanism. Each Service Control Module is responsible for storing and maintaining the configuration data for all Security Service Modules running its machine. Once started, a Security Service Module receives its configuration data from the local Service Control Module. When a change is made and distributed from the Administration Server, the Service Control Manager receives the change and updates the cached copy of the configuration. On restart, the Security Service Module receives updated configuration data from the Service Control Manager. Policy data does not require a restart, but is applied based on the desired provisioning characteristics.
| Note: | In this release of AquaLogic Enterprise Security it is possible to deploy an SSM without the SCM. You can use the PolicyIX tool, described in PolicyIX in the Administration Reference, to communicate directly with the BLM and retrieve configuration data. The PolicyIX tool allows you to export configuration data (configured either through the ALES Administration Console or directly via the BLM API) for a given SSM to an XML file, and use it with the configured SSMs when the SCM is not available. See Installing Security Service Modules for additional information. |
| Note: | The SCM is always installed on the ALES Administration server. |
In addition to facilitating management, the Service Control Manager enables Security Service Modules to operate in the absence of the Administration Server. Because the Service Control Manager maintains a persistent copy of each configuration, new Security Service Modules can be started and existing Security Service Modules continue to function, even if the Administration Server goes down or is intentionally unavailable, such as in occasionally connected computing environments.
BEA AquaLogic Enterprise Security supports a variety of Security Service Modules that you integrate with the security framework and provision as needed. The primary function of the security framework is to provide a simple application programming interface (API) that can be used by security and application developers to define security services. For a complete discussion of BEA AquaLogic Enterprise Security services, see Security Services. You may incorporate as many Security Service Modules as you need to secure the enterprise, and configure and manage them directly through a central Administration Server as shown in Figure 3-2. The distributed nature of the architecture allows you to configure, manage and distribute policy throughout the enterprise.
Configuration data for each Security Service Module is maintained within each machine and handled by a Service Control Manager. One additional benefit of this architecture is that even if the administration server goes down (either for maintenance or due to failure), there is no impact on the applications or security services provided by those Security Service Modules. At this time, the following Security Service Modules are available:
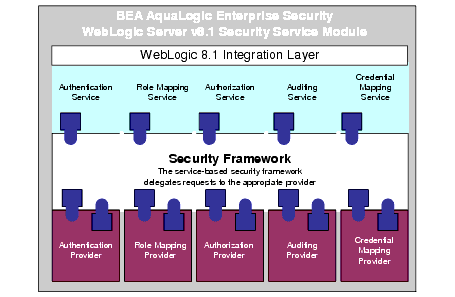
The WebLogic Server 8.1 Security Service Module is a security enhancement product that supports BEA WebLogic Server, Version 8.1. Further, the Security Service Module ties the application server into the Administration Server so that all application server administrative security activities are performed through the Administration Server. The application server with the Security Service Module add-on supports enterprise-level security by making security for WebLogic Server host applications an integral part of the enterprise policy. All WebLogic Server security-related functions remain available, but those functions are provided through the Security Service Module. Figure 3-3 shows the major components of the WebLogic Server 8.1 Security Service Module.
The WebLogic Server 9.x Security Service Module is a security enhancement product that supports BEA WebLogic Server, Version 9.x.
The WebLogic Server 9.x Security Service Module integrates AquaLogic Enterprise Security with BEA WebLogic Server versions 9.1 and 9.2. It uses a different security framework from the one used in the WebLogic Server 8.1 SSM and the other AquaLogic Enterprise Security SSMs. When you install the WebLogic Server 9.x SSM, AquaLogic Enterprise Security uses the WebLogic Server 9.x security framework. As a consequence, when you use the WebLogic Server 9.x SSM, you configure security providers and other aspects of the SSM in the WebLogic Administration Console, rather than the AquaLogic Enterprise Security Administration Console.
You still use the AquaLogic Enterprise Security Administration Console to write security policies for all SSMs, and to configure SSMs other than the WLS 9.x SSM. You must also use the AquaLogic Enterprise Security Administration Console to configure the ASI Authorizer and ASI Role Mapper providers.
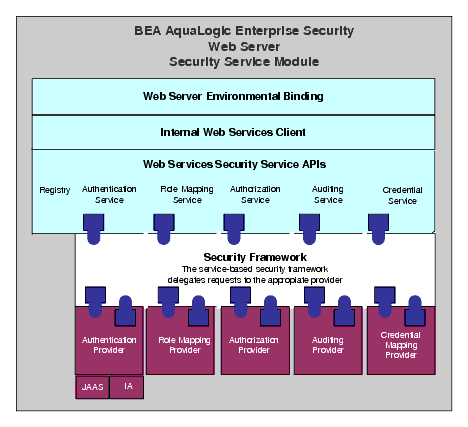
The Web Server Security Service Module (SSM) provides an environmental binding between the AquaLogic Enterprise Security infrastructure and IIS and Apache web servers. The SSM consists of three components, a Web Server Environmental Binding, an Internal Web Services Client, and the Web Services SSM (which includes the Security Service APIs, Security Framework and security providers) (See Figure 3-4). The AquaLogic Enterprise Security infrastructure provides six distinct services: Registry, Authentication, Authorization, Auditing, Role Mapping, and Credential Mapping. Each of these services is expressed in a way that is understandable to applications running within a web server that is protected by the AquaLogic Enterprise Security infrastructure. Therefore, the SSM can be used to configured and enforce security for web server applications and resources.
The Web Server SSM makes access control decisions for the web server to which it is bound. The security configuration on which the access control decisions are based is defined and deployed by the Administration Server via the Security Control Module.
You can tailor the Web Server SSM to meet your specific needs. Using templates provided as part of the product, security developers can customize the look and feel of authentication pages and configure parameters that allow fine tuning for a particular installation. Web applications can have information added to the HTTP request by the security framework, such as roles and response attributes. Additionally, the Web Server SSM enables security administrators and web developers to perform security tasks for applications running on a web server.
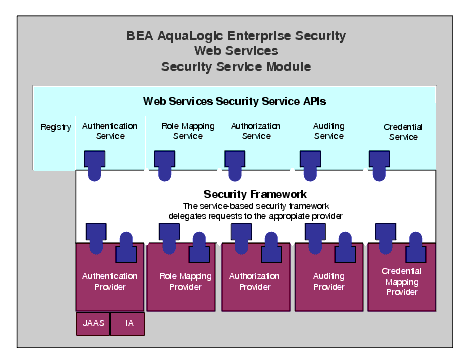
The Web Services Security Service Module (SSM) provides five security services: Authentication, Authorization, Auditing, Role Mapping, and Credential Mapping (see Figure 3-5). The WSDL provided for these services can be used to developed web services clients to access the AquaLogic Enterprise Security infrastructure and use it to make access control decisions for custom applications.
Figure 3-5 shows the components of the Web Services SSM.
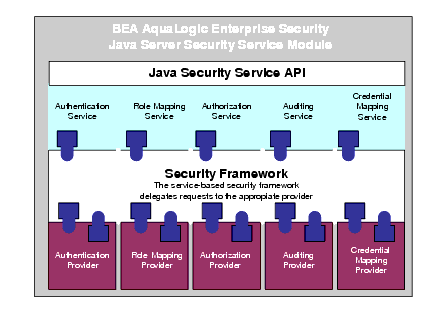
The Java Security Service Module provides an application programming interface (API) that allows security developers to insert security into their applications. These interfaces support the most commonly required security functions and are organized into services that are logically grouped by functionality.
After you use the Java Security Service Module interfaces to implement security functions in your Java application, you can deploy and run your application on any instance of a Java Security Service Module that supports the configuration requirements of your application. The Java Security Service Module offers five security services: Authentication Service, Authorization Service, Auditing Service, Role Service, and Credential Mapping Service. The name of each service indicates a type of function that can be implemented within a Java application. Each of these services is discussed in Security Services. Figure 3-6 shows the major components of the Java Security Service Module. The Java Security Service Module comprises the security service APIs, the security framework, and the security providers that you configure.


|