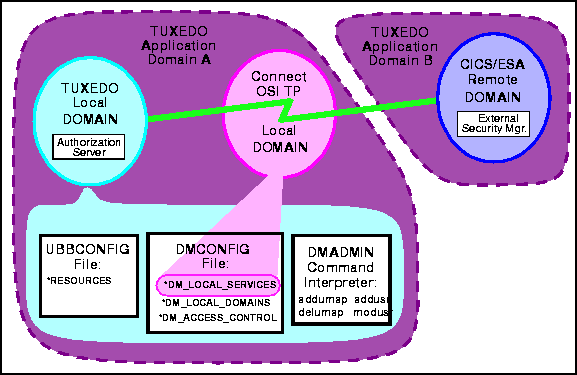
In order for any security checking to occur, each domain must have a security mechanism in place. For the TUXEDO domain, this is the Authorization Server. Figure 4-1 shows these elements.
Note: A domain without an operational security mechanism in place accepts all transaction requests by treating userids as "trusted users."
There are four sections in two BEA TUXEDO configuration files in which you specify parameters bearing on security. The two configuration files are DMCONFIG and UBBCONFIG.
Userid and password mapping between domains also bears on security. There are five DMADMIN subcommands which you use to enter userids and passwords, set up mappings, remove mappings, remove userids and passwords, and modify passwords.
Figure 4-1 Connect OSI TP Security Elements

The configuration sections where security is specified are:
The where UBBCONFIG File Security Parameters
*RESOURCES section in this file contains a SECURITY parameter which works in conjunction with the SECURITY parameter in the DMCONFIG file to establish how Connect OSI TP controls access to the local TUXEDO domain. This parameter takes the form:
SECURITY = value
value is:
NONE
APP_PW
USER_AUTH
ACL
MANDATORY_ACL
In most cases, the UBBCONFIG file has already been configured and you do not need to establish the SECURITY parameter settings, but examining this file enables you to ascertain how Connect OSI TP enforces security.
If this parameter is set to NONE, no security is enforced. If set to APP_PW, the local TUXEDO domain's Authorization Server prompts for the application password. If set to USER_AUTH, ACL, or MANDATORY_ACL, the qualified security is enforced as specified.
Three sections in the DMCONFIG file contain parameters affecting Connect OSI TP control of access to the local TUXEDO domain:
The SECURITY parameter settings in this section work in conjunction with the SECURITY parameter in the *RESOURCES section of the TUXEDO domain's UBBCONFIG file to establish how Connect OSI TP controls access to the TUXEDO local domain. The parameter takes the form:
where *DM_LOCAL_DOMAINS section
SECURITY = value
value is:
NONE
APP_PW
DM_USER_PW
If this parameter is set to NONE or APP_PW, the Connect OSI TP domain takes no action with regard to security. If this parameter is set to DM_USR_PW, the Connect OSI TP domain enforces security according to the setting in the TUXEDO domain's UBBCONFIG file (refer to "UBBCONFIG File Security Parameters" on page 4-3).
The ACL parameter in this section works in conjunction with the ACL_NAME defined in the *DM_ACCESS_CONTROL section to restrict requests made to the local services by remote domains.
After setting up and/or checking the security settings for the TUXEDO domain and the OSI domain, you must relate the security information in both domains to each other. To do this, use the addusr and addumap subcommands provided with the dmadmin command interpreter.
Once the user security information in both domains is mapped, you can perform administration on the affected security files in each domain. To do this, use the delumap, modusr, and delusr subcommands.
The following paragraphs discuss how you enter these commands. Refer to the associated reference pages in Appendix B, "Reference Pages" for detailed information about each subcommand.
Use the addusr subcommand to define a TUXEDO local domain's user ID and password to the remote domain's External Security Manager. Enter the following command:
addusr -dlocal_domain_id-Rremote_domain_id-uremote_userid
where:
-d
-R
-u
Use the addumap subcommand to map a local domain userid to a remote domain userid. The userid must be added before it can be mapped. Enter the following command:
addumap -dlocal_domain_id-Rremote_domain_id-plocal_principal_userid-uremote_userid
where:
-d
-R
-p
-u
Use the delumap subcommand to remove the mapping for a local domain userid to a remote domain userid. Enter the following command:
delumap -dlocal_domain_id-Rremote_domain_id-plocal_principal_userid-uremote_userid
where:
-d
-R
-p
-u
Use the delusr subcommand to remove a local TUXEDO domain's user ID and password from the remote domain's External Security Manager. The mapping for a userid must be removed before the userid can be removed. Enter the following command:
delusr -dlocal_domain_id-Rremote_domain_id-uremote_userid
where:
-d
-R
-u
Use the modusr subcommand to modify a local TUXEDO domain user's password recorded in a remote domain's External Security Manager. Enter the following command:
modusr -dlocal_domain_id-Rremote_domain_id-uremote_userid
where:
-d
-R
-u