The reference pages for these subcommands and other /Domain commands have been modified for the BEA Connect SNA product. Use Appendix A, "Reference Pages," in preference to similar pages in the BEA TUXEDO Reference Manual.
The SNACRM and PU 2.1 Servers
The SNACRM communicates directly with the PU 2.1 server to provide SNA connectivity. These servers are not BEA TUXEDO-based and can be started manually or via the DMINIT server. In either case, the PU 2.1 server must always be started before the SNACRM. Both servers must be started before starting the associated SNA Domain gateway group. Once the SNACRM and PU2.1 servers are started, there is no reason to restart them, outside of a catastrophic failure.
Starting the PU2.1 Server
Please refer to SNACRM in Appendix A, "Reference Pages," of this guide for information about starting the PU2.1 server.
Starting the SNACRM
You can manually start SNACRM from the command line or during tmboot with the DMINIT server. You can either start all SNACRM processes with a single DMINIT process or individually start each one with a DMINIT server that is defined to each gateway server group.
When you start SNACRM from the UNIX command line, the SNACRM Command Line Console puts its prompt in this window, and if exited, shuts down all of the active links. When started from DMINIT, the console is redirected to the null device. In this case, you can use the xsnacrm command to monitor the console and enable/disable tracing of SNACRM and the SNA stack.
Please refer to SNACRM in Appendix A, "Reference Pages," of this guide.
Using DMINIT
Please refer to SNACRM in Appendix A, "Reference Pages," of this guide for information about using DMINIT.
Security
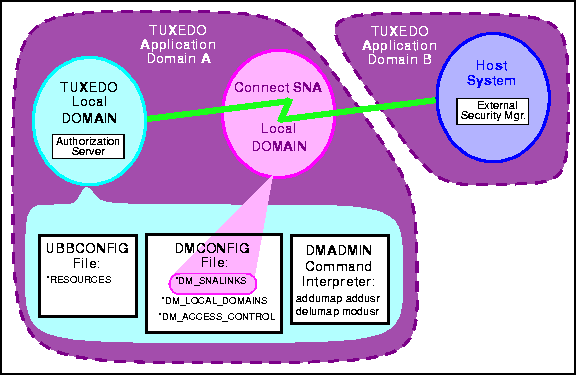
In order for any security checking to occur, the TUXEDO Local Domain and the Host System must have security mechanisms in place. For the Local Domain, this is the Authorization Server. For the Host System, this is the External Security Manager. Figure 5-1 shows these elements.
There are four sections in two BEA TUXEDO configuration files in which you specify parameters bearing on Local Domain security. The two configuration files are DMCONFIG and UBBCONFIG.
Userid and password mapping between the Local Domain and the Host System also bears on security. There are five DMADMIN subcommands which you use to enter userids and passwords, set up mappings, remove mappings, remove userids and passwords, and modify passwords.
Caution: Mixed environment security is more complex than depicted in Figure 5-1. A domain without an operational security mechanism in place accepts all transaction requests by treating userids as "trusted users." Refer to TUXEDO documentation for more detailed information about domain security.
Figure 5-1 Connect SNA Security Elements
Where You Specify Security Parameters
The configuration sections where security is specified are: