
![BEA BEA Tuxedo Release [Release Number]](../images/top.gif)

|
![BEA BEA Tuxedo Release [Release Number]](../images/top.gif)
|
|
|
|
Overview of the CORBA Security Features
This topic includes the following sections:
Note: Release 8.0 of the BEA Tuxedo product includes environments that allow you to build both Application-to-Transaction Monitor Interfaces (ATMI) and CORBA applications. This topic explains how to implement security in a CORBA application. For information about implementing security in an ATMI application, see Using Security in ATMI Applications.
The CORBA Security Features
Security refers to techniques for ensuring that data stored in a computer or passed between computers is not compromised. Most security measures involve proof material and data encryption, where the proof material is a secret word or phrase that gives a user access to a particular program or system, and data encryption is the translation of data into a form that cannot be interpreted.
Distributed applications such as those used for electronic commerce (e-commerce) offer many access points for malicious people to intercept data, disrupt operations, or generate fraudulent input; the more distributed a business becomes, the more vulnerable it is to attack. Thus, the distributed computing software, or middleware, upon which such applications are built must provide security.
The CORBA security features of the BEA Tuxedo product lets you establish secure connections between client and server applications. It has the following features:
To access the full security features of the CORBA environment, you need to install a license that enable the use of the SSL protocol, LLE, and PKI. For information about installing the license for the security features, see the Installing the BEA Tuxedo System.
Note: Using Security in CORBA Applications describes the security features of the CORBA environment in the BEA Tuxedo product. For a complete description of using the security features in the ATMI environment in the BEA Tuxedo product, see Using Security in ATMI Applications.
Table 1-1 summarizes the features in the CORBA security features in the BEA Tuxedo product.
.
The CORBA Security Environment
Direct end-to-end mutual authentication in a distributed enterprise middleware environment such as the BEA Tuxedo CORBA environment can be prohibitively expensive, especially when accomplished through security mechanisms optimized for long duration connections. It is not efficient for principals to establish direct network connections with each server application, nor is it practical to exchange and verify multiple authentication messages as part of processing each service request. Instead, CORBA applications in a BEA Tuxedo product implements a delegated trust authentication model as shown in Figure 1-1.
Figure 1-1 Delegated Trust Model
In a delegated trust model, principals (generally users of client applications) authenticate to a trusted system gateway process. In the case of the CORBA applications, the trusted system gateway process is the IIOP Listener/Handler. As part of successful authentication, security tokens are assigned to the initiating principal. A security token is an opaque data structure suitable for transfer between processes. When a request from an authenticated principal reaches the IIOP Listener/Handler, the IIOP Listener/Handler attaches the principal's security tokens to the request and delivers the request to the target server application for authorization and auditing purposes. In a delegated trust authentication model, the IIOP Listener/Handler trusts that the authentication software in the BEA Tuxedo domain will verify the identity of the principal and generates the appropriate security tokens. Server applications, in turn, trust that the IIOP Listener/Handler will attach the correct security tokens. Server applications also trust that any other server applications involved in the process of a request from a principal will safely deliver the security tokens. A session is established between the initiating client application and the IIOP Listener/Handler in the following way: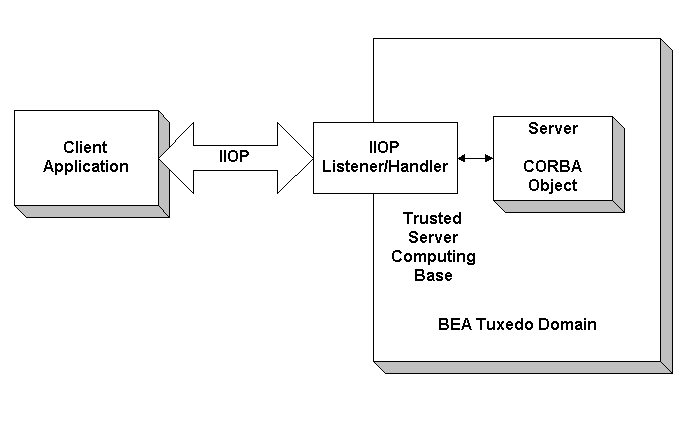
The IIOP Listener/Handler retrieves the authorization and auditing tokens from the security context. Together, the authorization and auditing tokens represent the principal's identity associated with the security context.
The protection of messages between the client application and the IIOP Listener/Handler is dependent on the security technology used in the CORBA application. The default behavior of the BEA Tuxedo product is to encrypt the authentication information but not to protect the message sent between the client application and the BEA Tuxedo domain. The message is sent in clear text. The SSL protocol can be used to protect the message. If the SSL protocol is configured to protect messages for integrity and confidentiality, the request is digitally signed and sealed (encrypted) before it is sent to the IIOP Listener/Handler.
Single Sign-on in the CORBA Security Environment
A WebLogic Server security realm and a BEA Tuxedo domain are considered separate scopes of security definitions. Each contains it own security database of users and access control. However, by using WebLogic Enterprise Connectivity (WLEC), the identity of a principal authenticated in a WebLogic Server security realm can be presented and used to form the identity of an authenticated principal in a BEA Tuxedo domain over a connection that is part of a trusted pool of connections.
Note: The single sign-on functionality in the CORBA security environment of the BEA Tuxedo product is unidirectional. You can only propagate a principal's identity from the WebLogic Server security realm to the BEA Tuxedo domain.
Figure 1-2 illustrates how single sign-on works in the CORBA security environment.
Figure 1-2 Single Sign-on in the CORBA Security Environment
When using single sign-on, the security identity of a WebLogic Server User is propagated as part of the service context of a IIOP request sent to a CORBA object in a BEA Tuxedo domain over a network connection that is part of a trusted connection pool. Each network connection in a trusted connection pool has been authenticated using a defined principal identity. Both password and certificate authentication can be used to establish a trusted connection pool. The propagated security identity is used by the IIOP Listener/Handler to impersonate a principal identity in the BEA Tuxedo domain. The impersonated identity is represented as a pair of tokens: one for authorization and one for auditing. These tokens are propagated to the target CORBA object in the BEA Tuxedo domain where they are used for authorization and auditing purposes. To facilitate the mapping of principal identities, the IIOP Listener/Handler uses an authentication plug-in. This plug-in is responsible for mapping the principal identity into the authorization and auditing tokens. These tokens are propagated as part of the request being forwarded to the target CORBA object. The target CORBA object can then use these tokens to determine information about the initiator of the request, including the identity of the principal. The SSL protocol can be used to protect the confidentiality and integrity of the request from the WebLogic Server realm. SSL encryption is provided for IIOP requests to CORBA objects in the BEA Tuxedo domain. In order to protect the request, both WebLogic Connectivity and the CORBA application must be configured to use the SSL protocol. For information about implementing single sign-on, see Configuring Single Sign-on.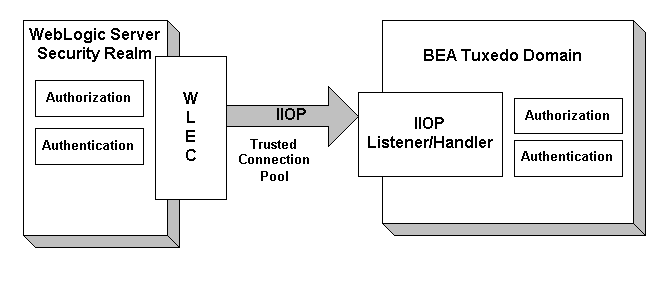
BEA Tuxedo Security SPIs
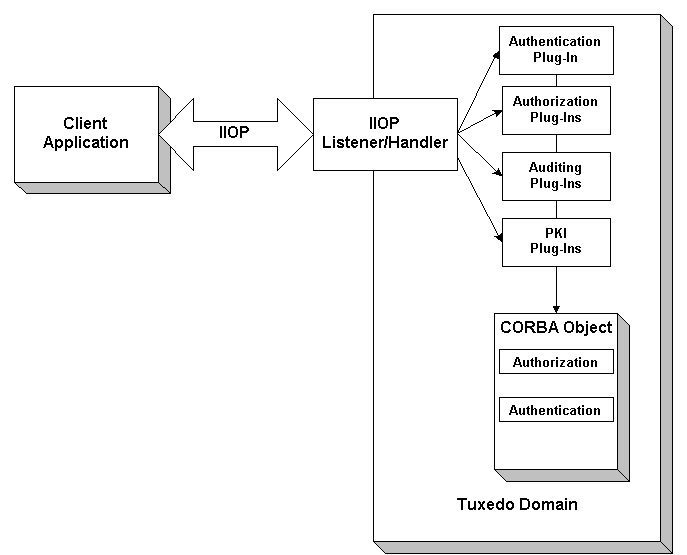
As shown in Figure 1-3, the authentication, authorization, auditing, and public key security features available with the BEA Tuxedo product are implemented through a plug-in interface, which allows security plug-ins to be integrated into the CORBA environment. A security plug-in is a code module that implements a particular security feature.
Figure 1-3 Architecture for the BEA Tuxedo Security Service Provider Interfaces
The BEA Tuxedo product provides interfaces for the types of security plug-ins listed in Table 1-2.
The specifications for the SPIs are currently only available to third-party security vendors who have entered into a special agreement with BEA Systems, Inc. Customers who want to customize a security feature must contact one of these vendors or BEA Professional Services. For example, a BEA customer who wants a custom implementation of public key security must contact a third-party vendor who can provide the appropriate security plug-in or BEA Professional Services.
For more information about security plug-ins, including installation and configuration procedures, see your BEA account executive.

|
|

|
|
|
|
Copyright © 2001 BEA Systems, Inc. All rights reserved.
|