
 |
| e-docs > Tuxedo > Using Tuxedo ATMI on Windows > Configuring BEA Tuxedo ATMI for Windows 2000 |
|
Using Tuxedo ATMI on Windows
|
Configuring BEA Tuxedo ATMI for Windows 2000
The following sections describe how to configure BEA Tuxedo ATMI on a Windows 2000 server system:
Introducing the BEA Administration Program
In addition to the BEA Tuxedo Administration Console, the BEA Tuxedo 7.1 or later software for Windows provides a BEA Administration program and two Windows services (Tlisten and BEA procMGR) for configuring the BEA Tuxedo system on a Windows 2000 system. Only if the installation included BEA Tuxedo server components will these additional administration tools be installed on the Windows 2000 system.
Note: The BEA Tuxedo Administration Console offers extensive online help: instructions for all the administrative tasks that can be performed through the console, plus reference information for all configuration tool folders. For information about how to use the BEA Tuxedo Administration Console, see BEA Tuxedo Administration Console Online Help.
Invoking the BEA Administration Program
With BEA Tuxedo release 7.1 or later software installed on your Windows 2000 system, perform the following steps to access the BEA Administration program:
Figure 2-1 Microsoft Windows Control Panel
Figure 2-2 BEA Administration Window with Machines Page Displayed
You can use the BEA Administration window to perform the following tasks:
Accessing Other Machines on a Network
The Machines page of the BEA Administration window enables you, as the BEA Tuxedo system administrator, to access any machine (where you have login privileges) on the Microsoft Windows Network running Microsoft Windows 2000. You can then set environment variables remotely; determine the location of BEA Tuxedo event logging; add, remove, stop, or start tlisten services; and tune IPC resources.
To access a remote machine, locate and click the machine's icon on the network tree. If you know the name of a remote machine, but do not know its work group, perform the following steps to select it:
At this point, all subsequent actions performed on other pages (Environment, Logging, Listener, and IPC Resources) in the BEA Administration window will take place on the selected machine (intrepid in this example).
Setting and Modifying Environment Variables
The Environment page enables you to view, set, or modify BEA Tuxedo environment variables on your Windows 2000 system.
Figure 2-3 BEA Administration Window with Environment Page Displayed
To add, modify, or delete environment variables using the Environment page, follow these steps.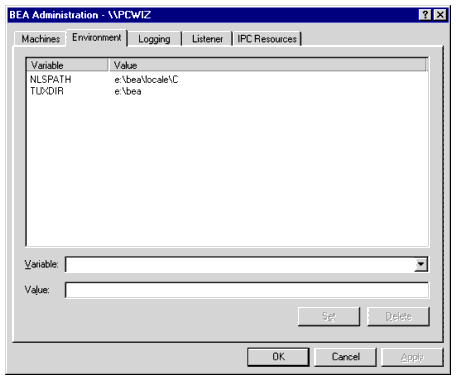
Directing BEA Tuxedo Messages to the Windows 2000 Event Log
The Logging page enables you to direct BEA Tuxedo system messages to the Event Log on your Windows 2000 system, to the traditional user log (ULOG) disk file, or both.
Figure 2-4 BEA Administration Window with Logging Page Displayed
You may select the Event Log option, the traditional user log (ULOG) Disk File option, or both. No setup is required for the Event Log. Setting Up a ULOG If you want to set up the traditional user log (ULOG) messages, perform the following steps to select a storage directory: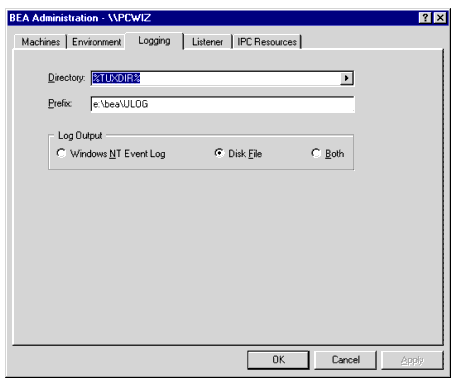
Viewing Windows 2000 Event Log Entries
To view Windows 2000 Event Log entries, follow these steps:
Figure 2-5 Event Viewer Window
Figure 2-6 Event Detail Window
This window provides the following information:
Viewing ULOG Entries
A ULOG is a text file. You can use any text editor to open a ULOG and view its contents.
Configuring tlisten Processes to Start Automatically
The Listener page enables you to view, create, or modify Tlisten services on your Windows 2000 system.
Figure 2-7 BEA Administration Window with Listener Page Displayed
During the BEA Tuxedo installation, the installer program installed a Tlisten service on your Windows 2000 system. Each time you boot your system, the Tlisten service starts a tlisten process on port 3050 of your machine. The password associated with the tlisten process is the one you entered during the installation. A tlisten process must be started on each machine of a networked BEA Tuxedo application before the BEA Tuxedo system and application servers can boot. You use the tlisten process to perform administrative actions across multiple machines. To learn more about tlisten processes, see tlisten(1)in BEA Tuxedo Command Reference. To add, remove, stop, or start Tlisten services using the Listener page, follow these steps.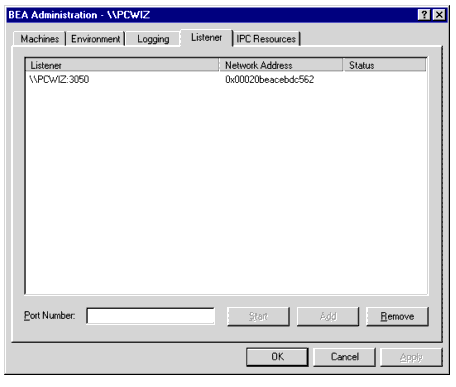
Besides viewing and controlling Tlisten services using the Listener page, you can click Start
Configuring IPC Resources to Maximize System Performance
The IPC Resources page enables you to configure the interprocess communication (IPC) resources on your Windows 2000 system to maximize BEA Tuxedo performance.
Figure 2-8 BEA Administration Window with IPC Resources Page Displayed
During the BEA Tuxedo installation, the installer program installed a BEA ProcMGR service on your Windows 2000 system. Each time you boot your system, the BEA ProcMGR service configures the IPC resources on your machine to whatever values you set on the IPC Resources page. The values shown in the preceding display are the default IPC values set by the installer program. On most machines, BEA ProcMGR runs as installed; however, you can use the IPC Resources page to tune the IPC resources and maximize performance. To determine the minimum IPC Resource values required for a BEA Tuxedo application, see the following table and Checking IPC Requirements in Installing the BEA Tuxedo System. The following table maps the names of the IPC Resources on a Windows 2000 system to the traditional names on a UNIX system.
To modify IPC Resource values using the IPC Resources page, follow these steps:
When interpreting the Maximum Number of Processes Using IPC parameter on the IPC Resources page, keep the following information in mind:
You can view the performance of a running BEA Tuxedo application on the Windows 2000 Performance Monitor. Choose Start
Figure 2-9 Performance Monitor
Reviewing the Windows 2000 Registry Content
The Windows 2000 Registry is the repository for all hardware, software, and application configuration settings for the Windows 2000 system. During the BEA Tuxedo installation, the installer program writes general installation information as well as IPC Resource values to the Registry. The structure of the Registry relevant to BEA Tuxedo is as follows.
HKEY_LOCAL_MACHINE\Software\BEA Systems\Tuxedo\8.1\...
To view this structure, choose Start
Developer Key
The Developer key stores product information, including the major and minor version numbers of the release, and user and company names.
Environment Key
The Environment key stores the locations referenced by the BEA Tuxedo environment variables set on your Windows 2000 system. It also stores other values such as IPC resource settings.
Security Key
The Security key holds the access permissions for BEA Tuxedo processes and services. The following permissions are mandatory:
BEA recommends that the Administrator have full control permissions.
|

|

|