Programming Web Services for WebLogic Server
|
|
Security Policy Assertion Reference
The following sections provide reference information about the security assertions you can configure in a WS-Policy file:
- Overview of a WS-Policy File That Contains Security Assertions
- Graphical Representation
- Example of a Policy File With Security Elements
- Element Description
- Using MessageParts To Specify Parts of the SOAP Messages that Must Be Encrypted or Signed
Overview of a WS-Policy File That Contains Security Assertions
You use WS-Policy files to configure the messgae-level security of a WebLogic Web Service. Use the @Policy and @Policies JWS annotations in the JWS file that implements the Web Service to specify the name of the WS-Policy file that is associated with a WebLogic Web Service.
A WS-Policy file is an XML file that conforms to the WS-Policy specification. The root element of a WS-Policy file is always <wsp:Policy>. To configure message-level security, you add policy assertions that specify the type of tokens supported for authentication and how the SOAP messages should be encrypted and digitally signed.
Note: These security policy assertions are based on the assertions described in the December 18, 2002 version of the Web Services Security Policy Language (WS-SecurityPolicy) specification. This means that although the exact syntax and usage of the assertions in WebLogic Server are different, they are similar in meaning to those described in the specification. The assertions in this release of WebLogic Server are not based on the latest update of the specification (13 July 2005.)
WebLogic Server includes three WS-Policy files (Auth.xml, Sign.xml, and Encrypt.xml) that contain typical security assertions that you can use if you do not want to create your own WS-Policy file. For details about these files, see Using WS-Policy Files for Message-Level Security Configuration.
See Configuring Message-Level Security (Digital Signatures and Encryption) for task-oriented information about creating a message-level secured WebLogic Web Service.
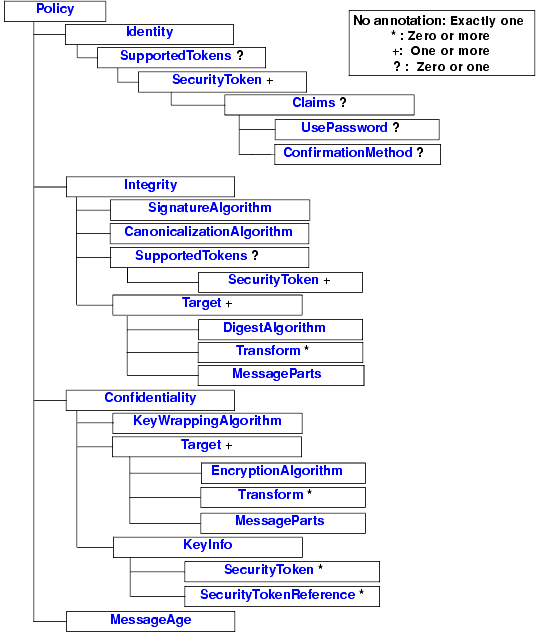
Graphical Representation
The following graphic describes the element hierarchy of the security assertions in a WS-Policy file.
Figure 13-2 Element Hierarchy of Security WS-Policy Assertions
Example of a Policy File With Security Elements
<?xml version="1.0"?>
<wsp:Policy
xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wssp="http://www.bea.com/wls90/security/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
xmlns:wls="http://www.bea.com/wls90/security/policy/wsee#part"
>
<wssp:Identity>
<wssp:SupportedTokens>
<wssp:SecurityToken TokenType="http://docs.oasis-open.org/wss/2004/01/oasis-2004-01-saml-token-profile-1.0#SAMLAssertionID">
<wssp:Claims>
<wssp:ConfirmationMethod>sender-vouches</wssp:ConfirmationMethod>
</wssp:Claims>
</wssp:SecurityToken>
</wssp:SupportedTokens>
</wssp:Identity>
<wssp:Confidentiality>
<wssp:KeyWrappingAlgorithm
URI="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<wssp:Target>
<wssp:EncryptionAlgorithm
URI="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
<wssp:MessageParts
Dialect="http://www.bea.com/wls90/security/policy/wsee#part">
wls:SecurityHeader(Assertion)
</wssp:MessageParts>
</wssp:Target>
<wssp:Target>
<wssp:EncryptionAlgorithm
URI="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
<wssp:MessageParts
Dialect="http://schemas.xmlsoap.org/2002/12/wsse#part">
wsp:Body()</wssp:MessageParts>
</wssp:Target>
<wssp:KeyInfo />
</wssp:Confidentiality>
</wsp:Policy>
Element Description
CanonicalizationAlgorithm
Specifies the algorithm used to canonicalize the SOAP message elements that are digitally signed.
Note: The WebLogic Web Services security runtime does not support specifing an InclusiveNamespaces PrefixList that contains a list of namespace prefixes or a token indicating the presence of the default namespace to the canonicalization algorithm.
|
The algorithm used to canonicalize the SOAP message being signed. You can specify only the following canonicalization algorithm: |
Claims
Specifies additional metadata information that is associated with a particular type of security token. Depending on the type of security token, you can or must specify the following child elements:
- For username tokens, you can define a
<UsePassword>child element to specify whether you want the SOAP messages to use password digests. - For SAML tokens, you must define a
<ConfirmationMethod>child element to specify the type of SAML confirmation (sender-vouchesorholder-of-key).
This element has no attributes.
Confidentiality
Specifies that part or all of the SOAP message must be encrypted, as well as the algorithms and keys that are used to encrypt the SOAP message.
For example, a Web Service may require that the entire body of the SOAP message must be encrypted using triple-DES.
This element has no attributes.
ConfirmationMethod
Specifies the type of confirmation method that is used when using SAML tokens for identity. You must specify one of the following two values for this element: sender-vouches or holder-of-key. For example:
<wssp:Claims>
<wssp:ConfirmationMethod>sender-vouches</wssp:ConfirmationMethod>
</wssp:Claims>
This element has no attributes.
The <ConfirmationMethod> element is required only if you are using SAML tokens.
The exact location of the <ConfirmationMethod> assertion in the WS-Policy file depends on the type configuration method you are configuring. In particular:
Specify the <ConfirmationMethod> assertion within an <Identity> assertion, as shown in the following example:
<?xml version="1.0"?>
<wsp:Policy
xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wssp="http://www.bea.com/wls90/security/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
xmlns:wls="http://www.bea.com/wls90/security/policy/wsee#part"
>
<wssp:Identity>
<wssp:SupportedTokens>
<wssp:SecurityToken
TokenType="http://docs.oasis-open.org/wss/2004/01/oasis-2004-01-saml-token-profile-1.0#SAMLAssertionID">
<wssp:Claims>
<wssp:ConfirmationMethod>sender-vouches</wssp:ConfirmationMethod>
</wssp:Claims>
</wssp:SecurityToken>
</wssp:SupportedTokens>
</wssp:Identity>
</wsp:Policy>
Specify the <ConfirmationMethod> assertion within an <Integrity> assertion. The reason you put the SAML token in the <Integrity> assertion for this confirmation method is that the Web Service runtime must prove the integrity of the message, which is not required by sender-vouches.
<?xml version="1.0"?>
<wsp:Policy
xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wssp="http://www.bea.com/wls90/security/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
xmlns:wls="http://www.bea.com/wls90/security/policy/wsee#part">
<wssp:Integrity>
<wssp:SignatureAlgorithm
URI="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<wssp:CanonicalizationAlgorithm
URI="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<wssp:Target>
<wssp:DigestAlgorithm
URI="http://www.w3.org/2000/09/xmldsig#sha1" />
<wssp:MessageParts
Dialect="http://schemas.xmlsoap.org/2002/12/wsse#part">
wsp:Body()
</wssp:MessageParts>
</wssp:Target>
<wssp:SupportedTokens>
<wssp:SecurityToken
IncludeInMessage="true"
TokenType="http://docs.oasis-open.org/wss/2004/01/oasis-2004-01-saml-token-profile-1.0#SAMLAssertionID">
<wssp:Claims>
<wssp:ConfirmationMethod>holder-of-key</wssp:ConfirmationMethod>
</wssp:Claims>
</wssp:SecurityToken>
</wssp:SupportedTokens>
</wssp:Integrity>
</wsp:Policy>
For more information about the two SAML confirmation methods (sender-vouches or holder-of-key), see SAML Token Profile Support in WebLogic Web Services.
DigestAlgorithm
Specifies the digest algorithm that is used when digitally signing the specified parts of a SOAP message. Use the <MessageParts> sibling element to specify the parts of the SOAP message you want to digitally sign.
|
The digest algorithm that is used when digitally signing the specified parts of a SOAP message. |
EncryptionAlgorithm
Specifies the encryption algorithm that is used when encrypting the specified parts of a SOAP message. Use the <MessageParts> sibling element to specify the parts of the SOAP message you want to digitally sign.
Identity
Specifies the type of security tokens (username, X.509, or SAML) that are supported for authentication.
This element has no attributes.
Integrity
Specifies that part or all of the SOAP message must be digitally signed, as well as the algorithms and keys that are used to sign the SOAP message.
For example, a Web Service may require that the entire body of the SOAP message must be digitally signed and only algorithms using SHA1 and an RSA key are accepted.
KeyInfo
Used to specify the security tokens that are used for encryption.
This element has no attributes.
KeyWrappingAlgorithm
Specifies the algorithm used to encrypt the message encryption key.
|
The algorithm used to encrypt the SOAP message encryption key. |
MessageAge
Specifies the acceptable time period before SOAP messages are declared stale and discarded.
When you include this security assertion in your WS-Policy file, the Web Services runtime adds a <Timestamp> header to the request or response SOAP message, depending on the direction (inbound, outbound, or both) to which the WS-Policy file is associated. The <Timestamp> header indicates to the recipient of the SOAP message when the message expires.
For example, assume that your WS-Policy file includes the following <MessageAge> assertion:
<wsp:Policy
xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wssp="http://www.bea.com/wls90/security/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
>
...
<wssp:MessageAge Age="300" />
</wsp:Policy>
The resulting generated SOAP message will have a <Timestamp> header similar to the following excerpt:
<wsu:Timestamp
wsu:Id="Dy2PFsX3ZQacqNKEANpXbNMnMhm2BmGOA2WDc2E0JpiaaTmbYNwT"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2005-11-09T17:46:55Z</wsu:Created>
<wsu:Expires>2005-11-09T17:51:55Z</wsu:Expires>
</wsu:Timestamp>
In the example, the recipient of the SOAP message discards the message if received after 2005-11-09T17:51:55Z, or five minutes after the message was created.
The Web Services runtime, when generating the SOAP message, sets the <Created> header to the time when the SOAP message was created and the <Expires> header to the creation time plus the value of the Age attribute of the <MessageAge> assertion.
The following table describes the attributes of the <MessageAge> assertion.
|
Specifies the actual maximum age time-out for a SOAP message, in seconds. |
The following table lists the properties that describe the timestamp behavior of the WebLogic Web Services security runtime, along with their default values.
You typically never need to change the values of the preceding timestamp properties. However, if you do need to, you must use the Administration Console to create the default_wss Web Service Security Configuration, if it does not already exist, and then update its timestamp configuration by clicking on the Timestamp tab. See Create a Web Service security configuration for task information and Domains: Web Services Security: Timestamp for additional reference information about these timestamp properties.
MessageParts
Specifies the parts of the SOAP message that should be signed or encrypted, depending on the grand-parent of the element. You can use either an XPath 1.0 expression or a set of pre-defined functions within this assertion to specify the parts of the SOAP message.
The MessageParts assertion is always a child of a Target assertion. The Target assertion can be a child of either an Integrity assertion (to specify how the SOAP message is digitally signed) or a Confidentiality assertion (to specify how the SOAP messages are encrypted.)
See Using MessageParts To Specify Parts of the SOAP Messages that Must Be Encrypted or Signed for detailed information about using this assertion, along with a variety of examples.
|
Identifies the dialect used to identity the parts of the SOAP message that should be signed or encrypted. If this attribute is not specified, then XPath 1.0 is assumed. The value of this attribute must be one of the following:
See Using MessageParts To Specify Parts of the SOAP Messages that Must Be Encrypted or Signed for examples of using these dialects. |
SecurityToken
Specifies the security token that is supported for authentication, encryption or digital signatures, depending on the parent element.
For example, if this element is defined in the <Identity> parent element, then is specifies that a client application, when invoking the Web Service, must attach a security token to the SOAP request. For example, a Web Service might require that the client application present a SAML authorization token issued by a trusted authorization authority for the Web Service to be able to access sensitive data. If this element is part of <Confidentiality>, then it specifies the token used for encryption.
The specific type of the security token is determined by the value of its TokenType attribute, as well as its parent element.
SecurityTokenReference
You should never include this security assertion in your custom WS-Policy file; it is described in this section for informational purposes only. The WebLogic Web Services runtime automatically inserts this security assertion in the WS-Policy file that is published in the dynamic WSDL of the deployed Web Service. The security assertion specifies WebLogic Server's public key; the client application that invokes the Web Service then uses it to encrypt the parts of the SOAP message specified by the WS-Policy file. The Web Services runtime then uses the server's private key to decrypt the message.
SignatureAlgorithm
Specifies the cryptographic algorithm used to compute the digital signature.
SupportedTokens
Specifies the list of supported security tokens that can be used for authentication, encryption, or digital signatures, depending on the parent element.
This element has no attributes.
Target
Encapsulates information about which targets of a SOAP message are to be encrypted or signed, depending on the parent element.
The child elements also depend on the parent element; for example, when used in <Integrity>, you can specify the <DigestAlgorithm>, <Transform>, and <MessageParts> child elements. When used in <Confidentiality>, you can specify the <EncryptionAlgorithm>, <Transform>, and <MessageParts> child elements.
You can have one or more targets.
Transform
Specifies the URI of a transformation algorithm that is applied to the parts of the SOAP message that are signed or encrypted, depending on the parent element.
You can specify zero or more transforms, which are executed in the order they appear in the <Target> parent element.
|
Specifies the URI of the transformation algorithm. For detailed information about these transform algorithms, see XML-Signature Syntax and Processing. |
UsePassword
Specifies that whether the plaintext or the digest of the password appear in the SOAP messages. This element is used only with username tokens.
Using MessageParts To Specify Parts of the SOAP Messages that Must Be Encrypted or Signed
When you use either the Integrity or Confidentiality assertion in your WS-Policy file, you are required to also use the Target child assertion to specify the targets of the SOAP message to digitally sign or encrypt. The Target assertion in turn requires that you use the MessageParts child assertion to specify the actual parts of the SOAP message that should be digitally signed or encrypted. This section describes various ways to use the MessageParts assertion.
See Example of a Policy File With Security Elements for an example of a complete WS-Policy file that uses the MessageParts assertion within a Confidentiality assertion. The example shows how to specify that the entire body, as well as the Assertion security header, of the SOAP messages should be encrypted.
You use the Dialect attribute of MessageParts to specify the dialect used to identify the SOAP message parts. The WebLogic Web Services security runtime supports the following three dialects:
Be sure that you specify a message part that actually exists in the SOAP messages that result from a client invoke of a message-secured Web Service. If the Web Services security runtime encounters an inbound SOAP message that does not include a part that the WS-Policy file indicates should be signed or encrypted, then the Web Services security runtime returns an error and the invoke fails. The only exception is if you use the WebLogic-specific wls:SystemHeader() function to specify that any WebLogic-specific SOAP header in a SOAP message should be signed or encrypted; if the Web Services security runtime does not find any of these headers in the SOAP message, the runtime simply continues with the invoke and does not return an error.
XPath 1.0
This dialect enables you to use an XPath 1.0 expression to specify the part of the SOAP message that should be signed or encrypted. The value of the Dialect attribute to enable this dialect is http://www.w3.org/TR/1999/REC-xpath-19991116.
You typically want to specify that the parts of a SOAP message that should be encrypted or digitally signed are child elements of either the soap:Body or soap:Header elements. For this reason, BEA provides the following two functions that take as parameters an XPath expression:
wsp:GetBody(xpath_expression)—Specifies that the root element from which the XPath expression starts searching issoap:Body.wsp:GetHeader(xpath_expression)—Specifies that the root element from which the XPath expression starts searching issoap:Header.
You can also use a plain XPath expression as the content of the MessageParts assertion, without one of the preceding functions. In this case, the root element from which the XPath expression starts searching is soap:Envelope.
The following example specifies that the AddInt part, with namespace prefix n1 and located in the SOAP message body, should be signed or encrypted, depending on whether the parent Target parent is a child of Integrity or Confidentiality assertion:
<wssp:MessageParts
Dialect="http://www.w3.org/TR/1999/REC-xpath-19991116"
xmlns:n1="http://www.bea.com/foo">
wsp:GetBody(./n1:AddInt)
</wssp:MessageParts>
The preceding example shows that you should define the namespace of a part specified in the XPath expression (n1 in the example) as an attribute to the MessageParts assertion, if you have not already defined the namespace elsewhere in the WS-Policy file.
The following example is similar, except that the part that will be signed or encrypted is wsu:Timestamp, which is a child element of wsee:Security and is located in the SOAP message header:
<wssp:MessageParts
Dialect="http://www.w3.org/TR/1999/REC-xpath-19991116">
wsp:GetHeader(./wsse:Security/wsu:Timestamp)
</wssp:MessageParts>
In the preceding example, it is assumed that the wsee: and wse: namespaces have been defined elsewhere in the WS-Policy file.
Note: It is beyond the scope of this document to describe how to create XPath expressions. For detailed information, see the XML Path Language (XPath), Version 1.0, specification.
Pre-Defined wsp:Body() Function
The XPath dialect described in XPath 1.0 is flexible enough for you to pinpoint any part of the SOAP message that should be encrypted or signed. However, sometimes you might just want to specify that the entire SOAP message body be signed or encrypted. In this case using an XPath expression is unduly complicated, so BEA recommends you use the dialect that pre-defines the wsp:Body() function for just this purpose, as shown in the following example:
<wssp:MessageParts
Dialect="http://schemas.xmlsoap.org/2002/12/wsse#part">
wsp:Body()
</wssp:MessageParts>
WebLogic-Specific Header Functions
BEA provides its own dialect that pre-defines a set of functions to easily specify that some or all of the WebLogic security or system headers should be signed or encrypted. Although you can achieve the same goal using the XPath dialect, it is much simpler to use this WebLogic dialect. You enable this dialect by setting the Dialect attribute to http://www.bea.com/wls90/security/policy/wsee#part.
The wls:SystemHeaders() function specifies that all of the WebLogic-specific headers should be signed or encrypted. These headers are used internally by the WebLogic Web Services runtime for various features, such as reliable messaging and addressing. The headers are:
wsrm:SequenceAcknowledgementwsrm:AckRequestedwsrm:Sequencewsa:Actionwsa:FaultTowsa:Fromwsa:MessageIDwsa:RelatesTowsa:ReplyTowsa:Towsax:SetCookiewsu:Timestamp
The following example shows how to use the wls:SystemHeader() function:
<wssp:MessageParts
Dialect="http://www.bea.com/wls90/security/policy/wsee#part">
wls:SystemHeaders()
</wssp:MessageParts>
Use the wls:SecurityHeader(header) function to specify a particular part in the security header that should be signed or encrypted, as shown in the following example:
<wssp:MessageParts
Dialect="http://www.bea.com/wls90/security/policy/wsee#part">
wls:SecurityHeader(wsu:Timestamp)
</wssp:MessageParts>
In the example, only the wsu:Timestamp security header is signed or encrypted. You can specify any of the preceding list of headers to the wls:SecurityHeader() function.