4.2 Configuring Security for Oracle UCM and Content Server
This section describes how to configure Oracle UCM and Content Server security to work with Fusion Middleware including Oracle WebLogic Server. Topics include general integration information for Oracle UCM and Content Server deployment, and tasks for setting up specific configurations.
4.2.1 Using an LDAP Authentication Provider
Oracle WebLogic Server includes an embedded LDAP server that acts as the default security provider data store for the Default Authentication, Authorization, Credential Mapping, and Role Mapping providers. Oracle UCM provides a default JpsUserProvider to communicate with Oracle WebLogic Server. For information on the embedded LDAP server, see "Managing the Embedded LDAP Server" in Oracle Fusion Middleware Securing Oracle WebLogic Server, and "Configure the Embedded LDAP Server" in Oracle WebLogic Server Administration Console Online Help.
If you choose to use an external LDAP provider, you must reassociate the identity store with the external LDAP server rather than use the embedded LDAP server. For information on configuration for an external LDAP provider, see "Reassociating the Identify Store with an External LDAP Authentication Provider" in Installation Guide for Oracle Enterprise Content Management Suite.
4.2.2 Configuring Oracle UCM to Use SSL
You can configure Oracle Fusion Middleware to secure communications between Oracle UCM using SSL, which is an industry standard for securing communications. Oracle Fusion Middleware supports SSL version 3, as well as TLS version 1.
For information, see the related SSL documentation listed in Table 4-1 and the following topics:
-
"Invoking References in One-Way SSL Environments in Oracle JDeveloper"
-
"Configuring Oracle ECM Suite, Oracle HTTP Server for SSL Communication"
-
"Switching from Non-SSL to SSL Configurations with Oracle UCM"
-
"Configuring SSL Between Oracle UCM Instances and Oracle WebCache"
-
"Using a Custom Trust Store for One-Way SSL During Design Time"
-
"Enabling an Asynchronous Process to Invoke Another Asynchronous Process"
| For Information On... | See The Following Guide... |
|---|---|
|
Configuring SSL with Oracle Fusion Middleware: Web Tier, Middle Tier, and Data Tier |
|
|
Configuring SSL with Oracle WebLogic Server |
Oracle Fusion Middleware Security Oracle WebLogic Server Guide: Chapter 12, Configuring SSL |
4.2.2.1 Configuring Oracle UCM for Two-Way SSL Communication
Oracle ECM Suite uses both the Oracle WebLogic Server and Sun secure socket layer (SSL) stacks for two-way SSL configurations.
-
For the inbound Web service bindings, Oracle ECM Suite uses the Oracle WebLogic Server infrastructure and, therefore, the Oracle WebLogic Server libraries for SSL.
-
For the outbound Web service bindings, Oracle ECM Suite uses JRF HttpClient and, therefore, the Sun JDK libraries for SSL.
Due to this difference, start Oracle WebLogic Server with the following JVM option.
-
Open the following file:
-
On UNIX operating systems, open
$MIDDLEWARE_HOME/user_projects/domains/domain_name/bin/setDomainEnv.sh. -
On Window operating systems, open
MIDDLEWARE_HOME\user_projects\domains\domain_name\bin\setDomainEnv.bat.
-
-
Add the following lines in the
JAVA_OPTIONSsection, if the server is enabled for one-way SSL (server authorization only):-Djavax.net.ssl.trustStore=your_truststore_locationFor two-way SSL, the keystore information (location and password) is not required.
In addition, perform the following steps to enable two-way SSL for Oracle UCM to invoke another application.
Note:
Both the server and client are assumed to have been configured for SSL with mutual authentication.-
On the client side, provide the keystore location.
-
From the SOA Infrastructure menu, select SOA Administration then Common Properties.
-
At the bottom of the page, click More SOA Infra Advanced Configuration Properties.
-
Click KeystoreLocation.
-
In the Value column, enter the keystore location.
-
Click Apply.
-
Click Return.
-
-
During design time in Oracle JDeveloper, update the reference section in the
composite.xmlfile with theoracle.soa.two.way.ssl.enabledproperty.<reference name="Service1" ui:wsdlLocation=". . ."> <interface.wsdl interface=". . ."/> <binding.ws port=". . ."> <property name="oracle.soa.two.way.ssl.enabled">true</property> </binding.ws> </reference> -
In Oracle Enterprise Manager Fusion Middleware Control Console, select WebLogic Domain, then domain_name.
-
Right-click domain_name and select Security then Credentials.
-
Click Create Map.
-
In the Map Name field, enter a name (for example,
SOA), and click OK. -
Click Create Key.
-
Enter the following details.
Field Description Select Map Select the map created in Step 6 (for this example, SOA). Key Enter the key name ( KeystorePasswordis the default).Type Select Password. User Name Enter the keystore user name ( KeystorePasswordis the default).Password Enter the password that you created for the keystore. Note:
When you set up SSL in Oracle WebLogic Server, a key alias is required. You must entermykeyas the alias value. This value is required. -
Set the keystore location in Oracle Enterprise Manager Fusion Middleware Control Console. See Step 1 for instructions.
-
Modify the
composite.xmlsyntax to usehttpsandsslportto invoke Oracle UCM. For example, change the syntax shown in bold:<?xml version="1.0" encoding="UTF-8" ?> <!-- Generated by Oracle SOA Modeler version 1.0 at [4/1/09 11:01 PM]. --> <composite name="InvokeEchoBPELSync" revision="1.0" label="2009-04-01_23-01-53_994" mode="active" state="on" xmlns="http://xmlns.oracle.com/sca/1.0" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy" xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy" xmlns:ui="http://xmlns.oracle.com/soa/designer/"> <import namespace="http://xmlns.oracle.com/CustomApps/InvokeEchoBPELSync/BPELProcess1" location="BPELProcess1.wsdl" importType="wsdl"/> <import namespace="http://xmlns.oracle.com/CustomApps/EchoBPELSync/ BPELProcess1"location="http://hostname:port/soa-infra/services/default/EchoBPEL Sync/BPELProcess1.wsdl" importType="wsdl"/>
to use
httpsandsslport:location="https://hostname:sslport/soa-infra/services/default/EchoBPELSync /BPELProcess1.wsdl"
4.2.2.2 Invoking References in One-Way SSL Environments in Oracle JDeveloper
When invoking a Web service as an external reference from Oracle UCM in one-way SSL environments, ensure that the certificate name (CN) and the host name of the server exactly match. This ensures a correct SSL handshake.
For example, if a Web service is named adfbc and the certificate has a server name of myhost05, the following results in an SSL handshake exception.
<import namespace="/adfbc1/common/"
@ location="https://myhost05.us.oracle.com:8002/CustomApps-adfbc1-context-root/Ap
pModuleService?WSDL"
importType="wsdl"/>
<import namespace="/adfbc1/common/" location="Service1.wsdl"
importType="wsdl"/>
If you switch the order of import, the SSL handshake passes.
<import namespace="/adfbc1/common/" location="Service1.wsdl"
importType="wsdl"/>
<import namespace="/adfbc1/common/"
@ location="https://myhost05.us.oracle.com:8002/CustomApps-adfbc1-context-root/Ap
pModuleService?WSDL"
importType="wsdl"/>
Note the following restrictions around this issue:
-
There are no options for ignoring host name verification in Oracle JDeveloper as exist with the Oracle WebLogic Server Administration Console. This is because the SSL kit used by Oracle JDeveloper is different. Only the trust store can be configured from the command line. All other certificate arguments are not passed.
-
In the WSDL file,
https://hostnamemust match with that in the certificate, as described above. You cannot perform the same procedures as you can with a browser. For example, if the host name ismyhost05.us.oracle.comin the certificate's CN, then you can usemyhost05,myhost05.us.oracle.com, or the IP address from a browser. In Oracle JDeveloper, always use the same name as in the certificate (that is,myhost05.us.oracle.com).
4.2.2.3 Configuring Oracle ECM Suite, Oracle HTTP Server for SSL Communication
Follow these procedures to configure SSL communication between Oracle ECM Suite and Oracle HTTP Server.
Configure Oracle HTTP Server for SSL Communication
-
Update
mod_ssl.confwith the<Location /integration/services>location directive.LoadModule weblogic_module ${ORACLE_HOME}/ohs/modules/mod_wl_ohs.so <IfModule mod_weblogic.c> WebLogicHost host.domain.com WLLogFile <logdir>/ohs_ssl.log Debug ALL DebugConfigInfo ON SecureProxy ON MatchExpression *.jsp WlSSLWallet <OHS_ HOME>/instances/instance1/config/OHS/ohs1/keystores/default </IfModule> <Location /soa-infra> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /b2bconsole> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /b2b> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /integration/worklistapp> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /integration/services> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /DefaultToDoTaskFlow> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /OracleBAM> WebLogicPort 9002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> <Location /OracleBAMWS> > WebLogicPort 9002 > SetHandler weblogic-handler > ErrorPage http://host.domain.com:port/error.html > </Location> <Location /sdpmessaging/userprefs-ui/> WebLogicPort 8002 SetHandler weblogic-handler ErrorPage http://host.domain.com:port/error.html </Location> -
Start the Oracle WebLogic Servers as described in "Configuring Oracle UCM for Two-Way SSL Communication"
Configure Certificates for Oracle Client, Oracle HTTP Server, and Oracle WebLogic Server
-
Export the user certificate from the Oracle HTTP Server wallet.
orapki wallet export -wallet . -cert cert.txt -dn 'CN=\"Self-Signed Certificate for ohs1 \",OU=OAS,O=ORACLE,L=REDWOODSHORES,ST=CA,C=US'
-
Import the above certificate into the Oracle WebLogic Server truststore as a trusted certificate.
keytool -file cert.txt -importcert -trustcacerts -keystore DemoTrust.jks
-
Export the certificate from the Oracle WebLogic Server truststore.
keytool -keystore DemoTrust.jks -exportcert -alias wlscertgencab -rfc -file certgencab.crt
-
Import the above certificate to the Oracle HTTP Server wallet as a trusted certificate.
orapki wallet add -wallet . -trusted_cert -cert certgencab.crt -auto_login_only
-
Restart Oracle HTTP Server.
-
Restart the Oracle WebLogic Servers as described in "Configuring Oracle UCM for Two-Way SSL Communication"
4.2.2.4 Switching from Non-SSL to SSL Configurations with Oracle UCM
Switching from non-SSL to SSL configurations with Oracle UCM requires the Frontend Host and Frontend HTTPS Port fields to be set in the Oracle WebLogic Server Administration Console. Not doing so results in exception errors when you attempt to create to-do tasks.
-
Log in to Oracle WebLogic Server Administration Console.
-
In the Environment section, select Servers.
-
Select the name of the managed server (for example, ucm_server1).
-
Select Protocols, then select HTTP.
-
In the Frontend Host field, enter the host name on which Oracle UCM is located.
-
In the Frontend HTTPS Port field, enter the SSL listener port.
-
Click Save.
4.2.2.5 Configuring SSL Between Oracle UCM Instances and Oracle WebCache
The Test Web Service page, in an Oracle WebCache and Oracle HTTP Server environment, may require communication back through Oracle WebCache. Therefore, SSL must be configured between the Oracle UCM instance and Oracle WebCache (that is, export the user certificate from the Oracle WebCache wallet and import it as a trusted certificate in the Oracle WebLogic Server truststore).
4.2.2.6 Using a Custom Trust Store for One-Way SSL During Design Time
To invoke Oracle UCM over HTTPS when using a custom trust store created with a tool such as keytool or orapki, perform the following actions in Oracle JDeveloper.
-
To fetch a WSDL file in the reference section, set the trust store information in Tools, then Preferences, then Http Analyzer, then HTTPS Setup, then Client Trusted Certificate Keystore.
-
During deployment to an SSL-enabled server, use the JSSE property at the command line:
jdev -J-Djavax.net.ssl.trustStore=your_trusted_location
4.2.2.7 Enabling an Asynchronous Process to Invoke Another Asynchronous Process
To enable an asynchronous process deployed to an SSL-enabled, managed server to invoke another asynchronous process over HTTP, start by assuming you create the following environment:
-
Asynchronous BPEL process A that invokes asynchronous BPEL process B
-
Asynchronous BPEL process A is deployed to a one-way SSL enabled, managed server
-
All WSDL reference and bindings use plain HTTP
At run time, the WSDL is looked for over HTTPS, and the callback message from asynchronous BPEL process B fails.
To resolve this issue, the callbackServerURL property must be passed at the reference binding level in the composite.xml file. This explicitly indicates the value of the callback URL for the given reference invocation. If the client composite is running in an SSL-managed server, then the callback defaults to SSL.
<reference name="Service1"
ui:wsdlLocation="http://localhost:8000/soa-infra/services/default/AsyncSecondB
PELMTOM/BPELProcess1.wsdl">
<interface.wsdl
interface="http://xmlns.oracle.com/Async/AsyncSecondBPELMTOM/BPELProcess1#wsdl
.interface(BPELProcess1)"
callbackInterface="http://xmlns.oracle.com/Async/AsyncSecondBPELMTOM/BPELProce
ss1#wsdl.interface(BPELProcess1Callback)"/>
<binding.ws
port="http://xmlns.oracle.com/Async/AsyncSecondBPELMTOM/BPELProcess1#wsdl.endp
oint(bpelprocess1_client_ep/BPELProcess1_pt)"
location="http://localhost:8000/soa-infra/services/default/AsyncSecondBPELMTOM
/bpelprocess1_client_ep?WSDL">
<wsp:PolicyReference URI="oracle/wss_username_token_client_policy"
orawsp:category="security"
orawsp:status="enabled"/>
<wsp:PolicyReference URI="oracle/wsaddr_policy"
orawsp:category="addressing"
orawsp:status="enabled"/>
.
<property name="callbackServerURL">http://localhost:8000/</property>
.
</binding.ws>
.
<callback>
<binding.ws
port="http://xmlns.oracle.com/Async/AsyncSecondBPELMTOM/BPELProcess1#wsdl.endp
oint(bpelprocess1_client_ep/BPELProcess1Callback_pt)">
<wsp:PolicyReference
URI="oracle/wss_username_token_service_policy"
orawsp:category="security"
orawsp:status="enabled"/>
</binding.ws>
</callback>
.
</reference>
4.2.2.8 Configuring RIDC SSL for Valid Certificate Path
To use Remote Intradoc Client (RIDC) and self-signed certificates, you must import the certificate into your local JVM certificate store so the certificate will be trusted.
-
Retrieve the key from the Content Server. For example:
openssl s_client -connect dadvmc0022.us.company.com:7045 2>/dev/null CONNECTED(00000003)---Certificate chain 0 s:/C=US/ST=MyState/L=MyTown/O=MyOrganization/OU=FOR TESTING ONLY/CN=dadvmc0022 i:/C=US/ST=MyState/L=MyTown/O=MyOrganization/OU=FOR TESTING ONLY/CN=CertGenCAB---Server certificate-----BEGIN CERTIFICATE-----MIIB6zCCAZUCEItVMwHDFXAnYG//RoVbXQgwDQYJKoZIhvcNAQEEBQAweTELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUGA1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkxEzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDkwMzI5MjM0NDM0WhcNMjQwMzMwMjM0NDM0WjB5MQswCQYDVQQGEwJVUzEQMA4GA1UECBYHTXlTdGF0ZTEPMA0GA1UEBxYGTXlUb3duMRcwFQYDVQQKFg5NeU9yZ2FuaXphdGlvbjEZMBcGA1UECxYQRk9SIFRFU1RJTkcgT05MWTETMBEGA1UEAxYKZGFkdm1jMDAyMjBcMA0GCSqGSIb3DQEBAQUAA0sAMEgCQQCmxv+h8kzOc2xyjMCdPM6By5LY0Vlp4vzWFKmPgEytp6Wd87sG+YDBPeFOz210XXGMx6F/14/yFlpCplmazWkDAgMBAAEwDQYJKoZIhvcNAQEEBQADQQBnuF/s6EqCT38Aw7h/406uPhNh6LUF7XH7QzmRv3J1sCxqRnA/fK3JCXElshVlPk8GhwE4G1zxpr/JZu6+jLrW-----END CERTIFICATE-----subject=/C=US/ST=MyState/L=MyTown/O=MyOrganization/OU=FOR TESTING ONLY/CN=dadvmc0022issuer=/C=US/ST=MyState/L=MyTown/O=MyOrganization/OU=FOR TESTING ONLY/CN=CertGenCAB---No client certificate CA names sent---SSL handshake has read 625 bytes and written 236 bytes---New, TLSv1/SSLv3, Cipher is RC4-MD5Server public key is 512 bitCompression: NONEExpansion: NONE SSL-Session: Protocol : TLSv1 Cipher : RC4-MD5 Session-ID: 23E20BCAA4BC780CE20DE198CE2DFEE4 Session-ID-ctx: Master-Key: 4C6F8E9B9566C2BAF49A4FD91BE90DC51F1E43A238B03EE9B700741AC7F4B41C72D2990648DE103BB73B3074888E1D91 Key-Arg : None Start Time: 1238539378 Timeout : 300 (sec) Verify return code: 21 (unable to verify the first certificate)---
-
Copy and paste the Server Certificate including the surrounding
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----lines. Save the certificate into a new file. For example:/tmp/dadvmc0022.pem: -----BEGIN CERTIFICATE----- MIIB6zCCAZUCEItVMwHDFXAnYG//RoVbXQgwDQYJKoZIhvcNAQEEBQAweTELMAkG A1UEBhMCVVMxEDAOBgNVBAgTB015U3RhdGUxDzANBgNVBAcTBk15VG93bjEXMBUG A1UEChMOTXlPcmdhbml6YXRpb24xGTAXBgNVBAsTEEZPUiBURVNUSU5HIE9OTFkx EzARBgNVBAMTCkNlcnRHZW5DQUIwHhcNMDkwMzI5MjM0NDM0WhcNMjQwMzMwMjM0 NDM0WjB5MQswCQYDVQQGEwJVUzEQMA4GA1UECBYHTXlTdGF0ZTEPMA0GA1UEBxYG TXlUb3duMRcwFQYDVQQKFg5NeU9yZ2FuaXphdGlvbjEZMBcGA1UECxYQRk9SIFRF U1RJTkcgT05MWTETMBEGA1UEAxYKZGFkdm1jMDAyMjBcMA0GCSqGSIb3DQEBAQUA A0sAMEgCQQCmxv+h8kzOc2xyjMCdPM6By5LY0Vlp4vzWFKmPgEytp6Wd87sG+YDB PeFOz210XXGMx6F/14/yFlpCplmazWkDAgMBAAEwDQYJKoZIhvcNAQEEBQADQQBn uF/s6EqCT38Aw7h/406uPhNh6LUF7XH7QzmRv3J1sCxqRnA/fK3JCXElshVlPk8G hwE4G1zxpr/JZu6+jLrW -----END CERTIFICATE-----
-
Import the certificate into the local JVM certificate store. You will need the keystore password. For example (the password is
changeit):sudo /opt/java/jdk1.6.0_12/bin/keytool -import -alias dadvmc0022 -keystore /opt/java/jdk1.6.0_12/jre/lib/security/cacerts -trustcacerts -file /tmp/dadvmc0022.pem Enter keystore password: changeit Owner: CN=dadvmc0022, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=USIssuer: CN=CertGenCAB, OU=FOR TESTING ONLY, O=MyOrganization, L=MyTown, ST=MyState, C=USSerial number: -74aaccfe3cea8fd89f9000b97aa4a2f8Valid from: Sun Mar 29 16:44:34 PDT 2009 until: Sat Mar 30 16:44:34 PDT 2024Certificate fingerprints: MD5: 94:F9:D2:45:7F:0D:E3:87:CF:2B:32:7C:BF:97:FF:50 SHA1: A8:A5:89:8B:48:9B:98:34:70:56:11:01:5C:14:32:AC:CB:18:FF:1F Signature algorithm name: MD5withRSA Version: 1Trust this certificate? [no]: yesCertificate was added to keystore
4.2.3 Configuring Oracle UCM to Use Single Sign-On
Oracle Access Manager (OAM), part of Oracle's suite of enterprise class products for identity management and security, provides a wide range of identity administration and security functions, including several single sign-on (SSO) options for Fusion Middleware and custom Fusion Middleware applications. OAM is the recommended single sign-on solution for Oracle Fusion Middleware 11g enterprise-class installations.
If your enterprise uses Microsoft desktop logins that authenticate with a Microsoft domain controller with user accounts in Active Directory, then configuring SSO with Microsoft Clients may be an option.
Basic setup required for these SSO solutions is described in the documents listed in Table 4-2. Specific setup required for Oracle UCM, Content Server, and SSO solutions is described in the following sections:
Table 4-2 Single Sign-on Documentation
| For Information On... | See The Following Guide... |
|---|---|
|
Configuring OAM |
|
|
Configuring OSSO |
Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management |
|
Using Windows Native Authentication for Single Sign-on |
Oracle WebLogic Server Admin Console Help: Configure Authentication and Identify Assertion Providers |
4.2.3.1 Configuring Oracle Access Manager (OAM)
Oracle Access Manager provides flexible and extensible authentication and authorization, and provides audit services. This section provides the minimum requirements to configure OAM as a single sign-on (SSO) authentication provider and describes how to configure Oracle WebLogic Server and the Content Server application as the partner application participating in SSO.
4.2.3.1.1 Concepts and Topology
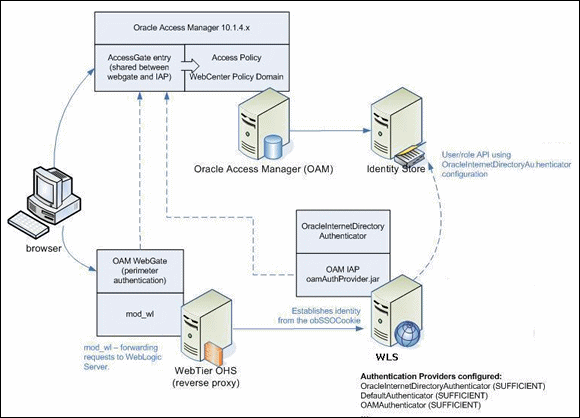
The following concepts are important to configuring OAM:
-
Access Server: A standalone server that provides authentication, authorization, and auditing services for AccessGates. There is one Access Server set up on OAM, which is done as part of the OAM install itself.
-
WebGate: An out-of-the-box plug-in that intercepts Web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization.
-
Identity Assertion Provider (IAP): A type of authenticator that asserts the identity of the user based on some header information that is set by perimeter authentication. The OAM integration provides an OAMAuthenticator that can be configured as the OAM IAP. The OAMAuthenticator can be used for authentication or for identity assertion. For OAM SSO integration, the OAMAuthenticator should be configured as an Identity Assertion Provider (IAP), by specifying the
obSSOCookieunder Active Types in the provider's general settings. -
Content Server: Content management server also referred to as ECM, UCM, or CS.
Figure 4-1 shows the topology involved in setting up Content Server deployed on an Oracle WebLogic Server with OAM for single sign-on.
4.2.3.1.2 Oracle WebLogic Server and Oracle UCM
Ensure that Oracle WebLogic Server is installed and Oracle UCM is deployed. For information, see Oracle Fusion Middleware Installation Guide for Oracle Enterprise Content Management Suite.
4.2.3.1.3 Oracle Internet Directory
Ensure that Oracle Internet Directory (OID) 11g is installed and configured. For information about installation, see Oracle Fusion Middleware Installation Guide for Oracle Enterprise Content Management Suite. For information about administration, see Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
4.2.3.1.4 Install and Configure Oracle HTTP Server (OHS)
Install and configure the WebTier, which contains Oracle WebCache and Oracle HTTP Server (OHS). Oracle Access Manager requires OHS. Oracle WebCache may be installed, although Oracle Access Manager does not require it.
When you link OHS to the Oracle WebLogic Server where Oracle UCM and Content Server are deployed, the default listening port of OHS is 7777.
Configure mod_weblogic (mod_wl_ohs.conf)
After you install OHS, append the following entries to the files in the module mod_wl_ohs in the WebTier OHS, so that the module forwards requests to the Oracle WebLogic Server for Content Server. In the following entries, <ucm-hostname> represents the hostname of the machine hosting Oracle UCM, and <ucm-server-port> represents the port of the Oracle WebLogic Server hosting Oracle UCM.
<Location /cs>
SetHandler weblogic-handler
WebLogicHost <ucm-hostname>
WebLogicPort <ucm-server-port>
</Location>
4.2.3.1.5 Create an AccessGate Object on OAM Access Server
Before WebGate installation, an AccessGate object must be created in the Access Admin Console and associated with an Access Server.
Note:
The Oracle Access Manager Configuration tool (OAM Configuration tool) is a command line utility that enables you to configure OAM. The OAM Configuration tool runs a series of scripts and sets up the required policies. You have the option to use this tool instead of the following procedure to configure an AccessGate object. For details, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.The following procedure assumes you have access to an existing OAM Access Server.
-
In the OAM Access Server, click the Access System Console link.
-
Click the Access System Configuration tab and then click the Host Identifier link.
-
Add a new host identifier similar to the following examples:
Name: your_host_machine.company.com
Hostname variations: your_host_machine.company.com:7777
your_host_machine.company.com:16200
your_host_machine.company.com:8888 -
Click the Add New Access Gate link.
-
Enter the following values, and keep defaults for the non-specified values:
Element Description AccessGate Name Pick a unique name (for example, ohs11gwg_sta00834_7777) Description Webgate for hostname WLS-ECM-OAM integration Hostname your_host_machine .company.com Port 7777 (Port number that OHS is listening on) Access Gate Password welcome1 (or password for your system) Failover Threshhold 1 Impersonation username your choice (for example, wlscs)Impersonation password welcome1 (or password for your system0 Access Management Service On Primary HTTP Cookie Domain .company.com Preferred HTTP Host your_host_machine.company.com -
Add the Access Server to the newly created Access Gate.
4.2.3.1.6 Install a WebGate Client on Your OHS
Before you start the installation, run the following commands as root in a shell window:
cd /tmp mkdir bin.$$ cd bin.$$ cat > mount <<EOF #! /bin/sh exec /bin/true EOF chmod 755 mount export PATH=`pwd`:$PATH
The Webgate requires the following libraries prior to installation: libgcc_s.so.1 and libstdc++.so.5. The files must be installed in a local directory (for example: /root/username/gcc). Change the access mode of the copied files to full access: chmod 777 *. This local directory is specified later during the installation of the WebGate.
Run the OAM Webgate 10.1.4.3.0 installer as root (./Oracle_Access_Manager10_1_4_3_0_linux_OHS11g_WebGate) and follow the prompts:
-
Specify the user/group running webserver.
-
Specify the installation directory for Oracle Access Manager 10.1.4.3.0 Webgate (for example: /root/username/webgate). Note that the OAM 10.1.4.3.0 Webgate installation directory would be: /root/username/webgate/access.
-
For "Location of GCC runtime libraries", specify the directory where you installed
libgcc_s.so.1andlibstdc++.so.5. -
For "transport security mode'', select Open mode.
-
For "Webgate ID", enter the AccessGate Name you specified in Create an AccessGate Object on OAM Access Server.
-
For "Access Server ID" enter the name listed in the hosted Oracle Access Manager's Access System Configuration > Access Server Configuration > Details for Access Server screen.
-
For "Hostname where Access Server is installed", enter the host name where OAM Access Server is running.
-
For "Port number", enter the port for the hosted OAM server's Access Server ID.
-
Select Automatic update of httpd.conf.
-
For "Enter the absolute path of httpd.conf in your Web server config directory", enter the OHS instance path. For example: /root/username/ohs/instances/instance1/config/OHS/ohs1/httpd.conf
-
For '"Please restart your WebServer to complete the installation of WebGate", follow these steps:
-
Open a new session as root.
-
Go to the bin directory of your OHS instance (for example: /root/username/ohs/instances/instance1/bin).
-
Run
opmnctl stopall. -
Run
opmnctl startall.
When the installer is finished running, you can run the following command to clean the temporary directory:
rm -r /tmp/bin.$$ -
The installation of WebGate provides a login page.
4.2.3.1.7 Create a Domain Policy in OAM
Follow the steps below to create a Domain Policy in the OAM Access Server:
Note:
The Oracle Access Manager Configuration tool (OAM Configuration tool) is a command line utility you can use to configure OAM. The OAM Configuration tool runs a series of scripts and sets up the required policies. You have the option to use this tool instead of the following procedure to configure a Domain Policy in OAM. For details, see Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management.-
Access the Oracle Access Manager admin page, then click the Policy Manager link, and click the Create Policy Domain link.
-
Give the Policy Domain a name and description. For example:
Name: OAM WLS-CS Policy Domain Description: OAM WLS-CS Policy Domain
-
Click Resources, then Add, and specify values for the following settings:
Host Identifier: your_hosted_machine.company.comURL Prefix: /cs/idcplg
-
Click Resources, then Add, and specify values for the following settings:
Host Identifier: your_hosted_machine.company.comURL Prefix: /cs/groups
-
Click Authorization Rules, then Add.
-
On the General tab, specify values for the following settings:
Name: Name of your choice (for example: OAM WLS-CS Authz rule). Description: Authorization rule for allowing access to anyone. This rule provides anyone access to Oracle WebLogic Server applications. Enabled: Yes
-
Click Default Rule and specify values for the following settings:
Name: Name of your choice (for example: WLS-CS SSO Login) Description: Authentication rule for Form based Login. Authentication Scheme: Form Authentication scheme_PSL-QA Authorization Expression: Select OAM WLS-CS Authz Rule (specified in step 5).
-
Click Save.
-
For Creating Policy for Domain (Policies tab), create the following General Policy:
Name: Name of your choice (for example: WLS-CS Protection Policy). Description: Protected resources in WLS-CS that should require authentication. Resource Type: http Resource Operation(s): GET, POST, PUT Resource: all Host Identifiers: your_hosted+machine.compan.com
-
Add header variables to the authorization expression action. Select Policy Domains, then Default Rules, then Authorization Expression, then Actions, then Authorization Failure.
Return Type: Name: Return Attribute: WL_REALM obmygroups obmygroups WL_REALM uid uid
4.2.3.1.8 Configure Oracle UCM Domain for OAM
When configuring the Oracle Universal Content Management (UCM) domain for Oracle Access Manager (OAM), there are several authenticators to be configured:
-
OAMAuthenticator (OAM authenticator configured for Identity Assertion mode to support SSO). The OAMAuthenticator must be configured to complete the support for Oracle Access Manager.
-
OracleInternetDirectoryAuthenticator (assuming Oracle Internet Directory is backing the OAM identity store). This authenticator must be configured for the LDAP server that is used as the identity store for OAM.
-
DefaultAuthenticator. This is the default authenticator.
Before configure the authenticators, be sure to back up the boot.properties file for the Oracle WebLogic Server Admin Server, and back up the relevant configuration files:
-
/config/config.xml
-
/config/fmwconfig/jps_config.xml
-
/config/fmwconfig/system-jazn-data.xml
Configuring the Identity Store
To configure the identity store to use LDAP, set the proper authenticator using the Oracle WebLogic Server Administration Console:
-
Log in to the Oracle WebLogic Server Administration Console.
-
Click the Security Realms link on the side navigation bar.
-
Click the myrealm default realm entry to configue it.
-
Click the Providers tab within the realm.
Note that there is a DefaultAuthenticator provider configured for the realm.
-
Click New to create a new Authentication provider.
-
Enter a name for the provider, such as "OIDAuthenticator" for a provider that will authenticate the user to the Oracle Internet Directory.
-
Select the OracleInternetDirectoryAuthenticator type from the list of authenticators.
-
Click OK.
-
In the Providers screen, click the newly created OIDAuthenticator.
-
Set the control flag to SUFFICIENT. This flag indicates that if a user can be authenticated successfully by this authenticator, then the authentication should be accepted and no additional authenticators are invoked. If the authentication fails, it will fail through to the next authenticator in the chain.
Make sure that all subsequent authenticators also have their control flag set to SUFFICIENT. In particular, check that the DefaultAuthenticator is set to SUFFICIENT.
-
Click Save.
-
Click the Provider Specific tab.
-
Enter the details specific to your LDAP server.
-
Click Save when you have entered all the detail for the LDAP server.
Configuring the OAM ID Asserter
To set up the OAM ID Asserter, complete these steps:
-
Log in to the Oracle WebLogic Server Administration Console.
-
Click the Security Realms link on the side navigation bar.
-
Click the myrealm default realm entry to configure it.
-
Click the Providers tab within the realm.
-
Click New and select OAM Identity Asserter from the menu.
-
Click the newly added asserter to see the configuration screen for OAM Identity Asserter.
-
Set the control flag to REQUIRED.
-
Click Save.
-
Open the Provider Specific tab to configure the following required settings.
-
Primary Access Server: provide OAM server endpoint information in HOST:PORT format.
-
Access Gate Name: name of the access gate (for example, WebCenter_EDG_AG).
-
Access Gate Password: password for the access gate (optional).
-
-
Click Save.
Setting the Order of Providers
Re-order the OAM Identity Asserter, OID Authenticator, and Default Authenticator by ensuring that the control flag for each authenticator is set as follows:
-
OAMAuthenticator (REQUIRED)
-
OracleInternetDirectoryAuthenticator (SUFFICIENT)
-
DefaultAuthenticator (SUFFICIENT)
Configuring Oracle UCM for Global SSO Logout
Configure a system property to integrate Oracle UCM with global Single Sign-On (SSO) to support acquiring the correct URL for logging out of the system. Edit the DOMAIN_HOME/ucm/short-product-id/config/config.cfg file and append the following entry:
LogoutServerUrl=/oamsso/logout.html?end_url=<$HttpBrowserFullWebRoot$>
Note:
if this file does not exist, start the Oracle UCM managed server and access the Oracle UCM application, then restart the server.4.2.3.2 Configuring Oracle Single Sign-On for Oracle UCM
To configure Oracle Single Sign-On (OSSO) for Oracle Universal Content Management (UCM), follow this procedure:
-
Install Oracle UCM.
-
Install Oracle Single Sign-On.
-
Start the Oracle WebLogic Server Admin server and navigate the Domain Structure to Security Realms, then myrealm.
-
Select myrealm from the Summary of Security Realms.
-
Select the Providers tab in the Settings for myrealm, then click New in the Authentication Providers list.
-
Select OSSOIdentityAsserter from the menu, then enter the name for the provider (for example, "MyAssertionProvider")
-
Click OK.
-
Return to the Providers tab in the Settings for myrealm screen, and select the provider you named (in this example, "MyAssertionProvider"). Change the control flag to REQUIRED.
-
Follow the instructions in "Configure Oracle UCM Domain for OAM".
-
Edit the mod_wl_ohs.conf file in OHS so the locations point to Oracle WebLogic Server:
LoadModule weblogic_module ${ORACLE_HOME}/ohs/modules/mod_wl_ohs.so <ifModule mod_weblogic.c> Debug ON WLLogFile /tmp/weblogic.log MatchExpression <Location /cs> WebLogicHost wlshost.company.com WebLogicPort port-number SetHandler weblogic_handler </Location> </IfModule> -
Register the OHS in OSSO. Go to ORACLE_HOME/sso/bin and run ssoreg.sh.
./ssoreg.sh -oracle_home_path <path_to_10.1.4 SSO_Oracle_Home> -site_name <any_site_name> -config_mod_osso TRUE - mod_osso_url <front-ending-OHSSHost:port> - update_mode CREATE -remote_midtier - config_file <path_where_osso.conf_will_get_generated>
For example:
./ssoreg.sh _oracle_home_path /root/<domain>/OraHome -site_name wls_server -config_mod_osso TRUE -mod_osso_url http://<domain>.<company-name>.<suffix>:7777 - update_mode CREATE -remote_midtier - config_file /tmp/osso.conf
-
Edit the file mod_osso.conf (at ORACLE_HOME/ohs/conf/) to include the following code:
LoadModule osso_module modules/mod_osso.so <IfModule mod_osso.c> OssoIdletimeout off OssoIpCheck on OssoConfigFile /tmp/osso.conf <IfModule mod_osso.c> OssoIpCheck off OssoIdleTimeout off OssoSecureCookies off OssoConfigFile /root/username/Oracle/ECM_version/osso.conf <Location /cs/groups> require valid-user AuthType Osso </Location> <Location /cs/idcplg> require valid-user AuthType Osso </Location> </IfModule>For the two Location settings in the code, as appropriate replace /cs/ with /ibr/ for Inbound Refinery, or /urm/ for Universal Records Management.
4.2.3.3 Configuring SSO with Microsoft Clients
Configuring Single Sign-On (SSO) with Microsoft clients requires configuring the Microsoft Active Directory, the client, and the Oracle WebLogic Server domain as described in the section “Configuring Single Sign-On with Microsoft Clients” in Oracle Fusion Middleware Security Oracle WebLogic Server.
In addition to that configuration, you must redeploy each Oracle UCM application (Content Server, Inbound Refinery, or Universal Records Management) that will be used in the Windows Native Authentication (WNA) environment, using an associated deployment plan. A deployment plan is an XML document, which Oracle provides for each of the three Oracle UCM applications. The plans are listed in the sections: Plan-cs.xml, Plan-ibr.xml, and Plan-urm.xml. You also can implement a deployment plan using the Oracle WebLogic Scripting Tool.
To redeploy Oracle UCM for a WNA environment:
-
Log in to the Oracle WebLogic Server Administration Console.
-
Click Deployments in the Domain Structure navigation tree.
-
On the Control tab, click Next until you see the Oracle UCM deployment you want to change:
-
Oracle Universal Content Management - Content Server
-
Oracle Universal Content Management - Inbound Refinery
-
Oracle Universal Records Management
-
-
Select the check box to the left of the deployment to be changed.
-
Click Update.
-
Under the Deployment plan path, select Change Path.
-
Navigate to and select the appropriate plan file:
-
plan-cs.xml(for Content Server) -
plan-ibr.xml(for Inbound Refinery) -
plan-urm.xml(for Universal Records Management)
-
-
Verify that Redeploy this application using the following deployment files is selected.
-
Click Next.
-
Click Finish.
Use the provided plan-cs.xml file, or create an .xml file and name it plan-cs.xml.
<?xml version='1.0' encoding='UTF-8'?>
<deployment-plan
xmlns="http://xmlns.oracle.com/weblogic/deployment-plan"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.oracle.com/weblogic/deployment-plan http://xmlns.oracle.com/weblogic/deployment-plan/1.0/deployment-plan.xsd"
global-variables="false">
<application-name>cs.ear</application-name>
<variable-definition>
<variable>
<name>url-pattern</name>
<value>/*</value>
</variable>
<variable>
<name>http-only</name>
<value>false</value>
</variable>
</variable-definition>
<module-override>
<module-name>cs.war</module-name>
<module-type>war</module-type>
<module-descriptor external="false">
<root-element>web-app</root-element>
<uri>WEB-INF/web.xml</uri>
<variable-assignment>
<name>url-pattern</name> <xpath>/web-app/security-constraint/[display-name="UCMConstraint"]/web-resource-collection/[web-
resource-name="idcauth"]/url-pattern</xpath>
<operation>replace</operation>
</variable-assignment>
</module-descriptor>
<module-descriptor external="false">
<root-element>weblogic-web-app</root-element>
<uri>WEB-INF/weblogic.xml</uri>
<variable-assignment>
<name>http-only</name>
<xpath>/weblogic-web-app/session-descriptor/cookie-http-only</xpath>
</variable-assignment>
</module-descriptor>
</module-override>
</deployment-plan>
Use the provided plan-ibr.xml file, or create an .xml file and name it plan-ibr.xml.
<?xml version='1.0' encoding='UTF-8'?>
<deployment-plan xmlns="http://xmlns.oracle.com/weblogic/deployment-plan" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation= "http://xmlns.oracle.com/weblogic/deployment-plan http://xmlns.oracle.com/weblogic/deployment-plan/1.0/deployment-plan.xsd" global-variables="false">
<application-name>ibr.ear</application-name>
<variable-definition>
<variable>
<name>url-pattern</name>
<value>/*</value>
</variable>
<variable>
<name>http-only</name>
<value>false</value>
</variable>
</variable-definition>
<module-override>
<module-name>ibr.war</module-name>
<module-type>war</module-type>
<module-descriptor external="false">
<root-element>web-app</root-element>
<uri>WEB-INF/web.xml</uri>
<variable-assignment>
<name>url-pattern</name>
<xpath>/web-app/security-constraint/[display-name="UCMConstraint"]/web-resource-collection/[web-
resource-name="idcauth"]/url-pattern</xpath>
<operation>replace</operation>
</variable-assignment>
</module-descriptor>
<module-descriptor external="false">
<root-element>weblogic-web-app</root-element>
<uri>WEB-INF/weblogic.xml</uri>
<variable-assignment>
<name>http-only</name>
<xpath>/weblogic-web-app/session-descriptor/cookie-http-only</xpath>
</variable-assignment>
</module-descriptor>
</module-override>
</deployment-plan>
Use the provided plan-urm.xml file, or create an .xml file and name it plan-urm.xml.
<?xml version='1.0' encoding='UTF-8'?>
<deployment-plan
xmlns="http://xmlns.oracle.com/weblogic/deployment-plan"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.oracle.com/weblogic/deployment-plan http://xmlns.oracle.com/weblogic/deployment-plan/1.0/deployment-plan.xsd"
global-variables="false">
<application-name>urm.ear</application-name>
<variable-definition>
<variable>
<name>url-pattern</name>
<value>/*</value>
</variable>
<variable>
<name>http-only</name>
<value>false</value>
</variable>
</variable-definition>
<module-override>
<module-name>urm.war</module-name>
<module-type>war</module-type>
<module-descriptor external="false">
<root-element>web-app</root-element>
<uri>WEB-INF/web.xml</uri>
<variable-assignment>
<name>url-pattern</name>
<xpath>/web-app/security-constraint/[display-name="UCMConstraint"]/web-resource-collection/[web-
resource-name="idcauth"]/url-pattern</xpath>
<operation>replace</operation>
</variable-assignment>
</module-descriptor>
<module-descriptor external="false">
<root-element>weblogic-web-app</root-element>
<uri>WEB-INF/weblogic.xml</uri>
<variable-assignment>
<xpath>/weblogic-web-app/session-descriptor/cookie-http-only</xpath>
</variable-assignment>
</module-descriptor>
</module-override>
</deployment-plan>
4.2.4 Configuring OID as the First Authentication Provider
Oracle Internet Directory (OID) stores user and group information for enterprise platforms. When Oracle WebLogic Server is configured to use OID instead of its embedded LDAP server for user authentication, the OID Authentication provider must be the first provider listed in the security realm configuration.
If the OID Authentication provider is not listed first (for example, it is listed below the Oracle WebLogic Server provider, DefaultAuthenticator), then Oracle UCM will fail to successfully load the users' Group membership and therefore fail to load any of the users' privileges. You can use the Oracle WebLogic Server Administration Console to change the order in which the configured Authentication providers are called.
When you use OID, all Oracle UCM administrator and other users must be defined in OID.
Note:
Content Server assigns a Content Server administrator role to administrative users defined in the internal Oracle WebLogic Server user store. This is true regardless of whether Oracle Internet Directory is used or not used. However, if you use Oracle Internet Directory and the Oracle Internet Directory Authentication provider is not listed first, then any request by the Content Server to retrieve the roles of the Oracle WebLogic Server defined administrative users will fail.For information about changing the order of authentication providers, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
4.2.5 Configuring Oracle WebLogic Server Web Services
Oracle WebLogic Server Web Services are implemented according to the Web Services for Java EE 1.2 specification, which defines the standard Java EE runtime architecture for implementing Web Services in Java. The specification also describes a standard Java EE Web Service packaging format, deployment model, and runtime services, all of which are implemented by Oracle WebLogic Server Web Services. For information, see the documentation listed in Table 4-3.
4.2.6 Additional Security Configuration Documentation
Most security procedures do not require steps unique to Oracle UCM and can be performed by following the documentation listed in Table 4-4.
Table 4-4 Security Documentation
| For Information On... | See The Following Guide... |
|---|---|
|
Securing Oracle Fusion Middleware |
|
|
Securing and administering Web services |
|
|
Understanding Oracle WebLogic Server security |
Oracle Fusion Middleware Understanding Security for Oracle WebLogic Server |
|
Securing an Oracle WebLogic Server production environment |
Oracle Fusion Middleware Securing a Production Environment for Oracle WebLogic Server |
|
Securing Oracle WebLogic Server |
|
|
Developing new security providers for use with Oracle WebLogic Server |
Oracle Fusion Middleware Developing Security Providers for Oracle WebLogic Server |
|
Securing Web service for Oracle WebLogic Server |
Oracle Fusion Middleware Securing WebLogic Web Services for Oracle WebLogic Server |
|
Programming security for Oracle WebLogic Server |
Oracle Fusion Middleware Programming Security for Oracle WebLogic Server |