1 Overview
This chapter covers the following topics:
1.1 About This Guide
This guide describes how to configure the Siebel Adapter for Oracle Universal Content Management (Oracle UCM). It includes the following sections:
-
Chapter 1, "Overview," lists supported Siebel entities and describes attachment options, authentication, and document security.
-
Chapter 2, "Configuring the Adapter," lists system requirements and describes how to configure Oracle UCM and Siebel for adapter use. It also describes optional configuration, such as scanning via Oracle Distributed Document Capture, passing additional metadata parameters from Siebel to Oracle UCM, and customizing the adapter iFrame display.
-
Appendix A, "Siebel Object Locking," lists Siebel objects locked during adapter configuration and instructions for activating or deactivating them.
1.2 About the Adapter
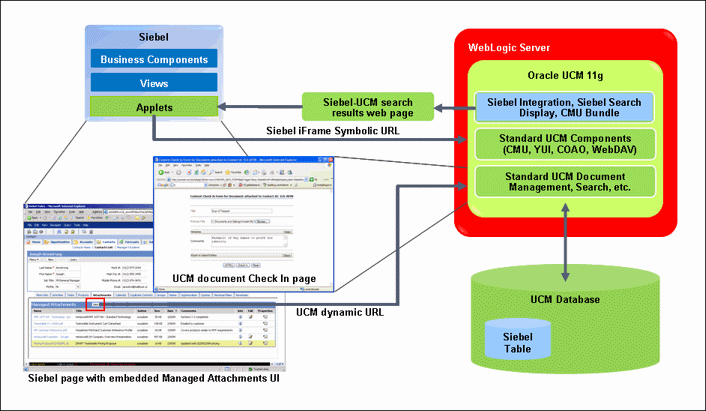
The Siebel Adapter for Oracle UCM allows Siebel CRM users to scan, attach, store, and retrieve attachments stored in an Oracle UCM Content Server repository. Oracle UCM documents are displayed as managed attachments to Siebel entities in a customizable iFrame within the Siebel application.
1.3 Supported Siebel Entities
The Managed Attachments iFrame is supported for the following Siebel entities:
1.4 System Architecture
Figure 1-1 illustrates the iFrame configuration for the Siebel adapter.
1.5 Managed Attachments Options
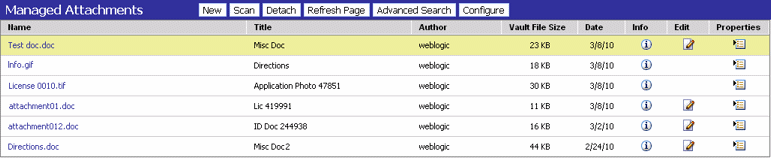
When a Siebel user displays a Siebel record such as a contact, Content Server lists the attachments to which the user has access in a Managed Attachments iFrame.
Siebel users can perform the following tasks in the attachments iFrame:
-
Open documents in their native application or Web-viewable format
-
Check in new documents to Content Server and attach them to the selected Siebel entity
-
Detach documents from a Siebel entity
-
Refresh the iFrame's list of attachments
-
Select and order fields for display in the attachments iFrame
-
Search Content Server using advanced search options
-
View an attached document's information
-
Check out documents, locking them to changes by other users
-
Modify a document's metadata values
-
Scan and import documents using Oracle Distributed Document Capture, attaching them to a selected Siebel entity
For details about how users work with Oracle UCM documents in a Siebel application, see the Oracle Fusion Middleware User's Guide for Oracle Enterprise Content Management Solutions for Oracle Siebel.
1.6 User Authentication
Siebel users must have a Content Server account to display the Managed Attachments iFrame within the supported Siebel entity. In addition, the authentication model configured for Content Server and Siebel determines how users are authenticated the first time they display a Siebel record that includes the attachments iFrame:
-
Content Server configured for Oracle Single Sign-On: If Siebel is not configured for single sign-on, the Oracle UCM single sign-on login prompt is displayed. (If Siebel is configured for single sign-on, the user has been authenticated, so no login prompt is displayed.)
-
Content Server not configured for Oracle Single Sign-On: The Content Server login prompt is displayed, regardless of the selected Siebel authentication model.
1.7 Document Security
Users set a document's security when checking it into Content Server. In the attachments iFrame, Siebel users see only those attachments to which their Content Server account allows them access. So a document attached to a Siebel entity does not appear in the search results for an unauthorized user. It is recommended to use a profile that specifies default security values for document check-in.