 Understanding Security Workbench
Understanding Security Workbench
This chapter provides an overview of Security Workbench (P00950) and discusses how to:
Create security overrides.
Manage application security.
Manage action security.
Manage row security.
Manage column security.
Manage processing option security.
Manage tab security.
Manage hyper exit security.
Manage exclusive application security.
Manage external calls security.
Manage miscellaneous security.
Manage push button, link, and image security.
Manage text block control and chart control security.
Manage media object security.
Manage Data Browser security.
Manage published business services security.
Copy security from one user or role to another.
Review and delete security records on the Work With User/Role Security form.
Run the Security Workbench Records reports.
 Understanding Security Workbench
Understanding Security Workbench
Use Security Workbench to apply security to JD Edwards EnterpriseOne applications, application versions, forms, and other objects within JD Edwards EnterpriseOne that are described in this chapter. You can apply security for these objects to users, roles, or *PUBLIC. JD Edwards EnterpriseOne stores security information in the F00950 table and caches the security information in the web server's memory for the web clients and each workstation's memory on Microsoft Windows clients. Changes that you make to security are applied after the user exits JD Edwards EnterpriseOne and signs back in. For the security changes to take affect on web clients, you must restart the web server or clear the web server's cache using the Server Administration Workbench (SAW) application.
When applying object level security, you need to consider how JD Edwards EnterpriseOne checks for security. When a user signs in, the system first checks the user ID for security. If no object security is assigned to the user ID, then it checks the role (if the user is part of a specific role), and then finally it checks *PUBLIC.
Note. You can access Security Workbench on the JD Edwards EnterpriseOne web client, as well as the Microsoft Windows client.
 Creating Security Overrides
Creating Security Overrides
This section provides an overview of security overrides, provides a prerequisite, and discusses how to add security overrides.

 Understanding Security Overrides
Understanding Security Overrides
Security overrides operate as exceptions to existing security records. They specify that users are unsecured from a JD Edwards EnterpriseOne object. In other words, security overrides allow users access to a particular object, even if another security record in the system specifies that access is not allowed.
Security overrides enable you to create object security more efficiently, with fewer security records to manage. For example, you might have a scenario that requires securing four out of five versions of an application from a group of users. Instead of creating four security records to prevent users from accessing each of the four versions, you can create two security records to achieve the same result. First, you would create a security override for the application version that you want users to access. This security override would specify that this version is not secured. These are the high level steps to create security overrides in Security Workbench:
Create a security record for the version, making sure that the security options are cleared.
Create a security record that secures users from accessing the application, including all versions of the application. In Security Workbench, you would select the application and then select the Run security option, which secures users from running the application.
As a result, when users try to access the application version, the security override for the version operates as an exception to the second application security record, allowing users access to the version of the application. All other versions of the application are secured.
You can create security overrides for these JD Edwards EnterpriseOne objects:
Applications
Actions
Processing options
Tabs
Hyper exits
External calls
Push buttons, links, and images
Media objects
Creating security overrides simplifies the process of applying security to various JD Edwards EnterpriseOne items. The following table provides some scenarios in which you could use security overrides to set up your security:
|
Scenario |
Method |
|
Allow a user or group of users access to a single form in an application. These users are otherwise restricted from using the application. |
To set up:
|
|
Secure users from using all but one push button on a form in an application. This security shall apply to all versions of the application as well. |
To set up:
|
|
Allow only one user in a role access to an external application. |
To set up:
|
|
Secure users from all action buttons except Add and Copy on a form in a particular version of an application. |
To set up:
|

 Prerequisite
Prerequisite
Before you can create a security override for a JD Edwards EnterpriseOne object, you must first understand how a standard security record for the object is created in Security Workbench. See the appropriate sections in this chapter for instructions on how to apply security to JD Edwards EnterpriseOne objects such as applications, processing options, tabs, and media objects.

 Adding Security Overrides
Adding Security Overrides
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, and then select the menu for the type of object for which you want to create a security override.
On the security form, enter the user or role ID in the User / Role field.
Enter a complete user or role, which includes *PUBLIC.
In the Display UnSecured Items region, complete the appropriate fields, and then click Find.
This step provides a list of unsecured items for the user, role, or *PUBLIC in the UnSecured node.
Expand the UnSecured node to view the individual applications or versions, and the forms associated with each, that do not already have security set for them.
After you expand the node, each item that you select appears in the grid.
Select the item in the node that you want to create a security override for.
In the Create with region, make sure that the security options are cleared or not selected.
Drag the item from the UnSecured node to the Secured node.
This action creates a security override for the user or role that can operate as an exception to a another security record for the user or role.
 Managing Application Security
Managing Application SecurityThis section provides an overview of application security and discusses how to:
Review the current application security settings for a user or role.
Add security to an application.
Secure a user or role from all JD Edwards EnterpriseOne objects.
Remove security from an application.

 Understanding Application Security
Understanding Application Security
Application security enables you to secure these types of items from users:
Applications
When you secure an application, you secure all versions and forms associated with the application.
Versions
You can secure access to a version of an application while leaving other versions available to the user.
Forms
You can secure access to a single form in an application or application version.
You can secure users from running or installing (or both) a particular application, version, or form within an application.
This section also explains how to add a *ALL object and change all of the applications for a particular user or role from unsecured to secured.

 Reviewing the Current Application Security Settings for a User or Role
Reviewing the Current Application Security Settings for a User or Role
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Application.
On the Application Security form, enter the user or role ID in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
In the Display UnSecured Items region, complete the appropriate fields to determine which items have already been secured for the user or role, and then click Find:
Application
Enter an application name, such as P01012. You can also enter *ALL to display all applications.
Version
Enter a version name, such as ZJDEC0001, if you want to check only a specific version of an application. You can also use an asterisk to display all versions.
Form Name
Enter a form name, such as W01012A. You can also enter an asterisk to display all forms.
Expand the Secured node to view the security settings for the user or role in the detail area.

 Adding Security to an Application
Adding Security to an Application
Enter P00950 in the Fast Path.
Note. You cannot secure the Data Browser program using the Application Security form. Security Workbench provides a separate option for securing this program.
See Managing Data Browser Security.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Application.
On the Application Security form, enter the user or role ID in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
In the Display UnSecured Items region, complete the appropriate fields, and then click Find.
Application
Version
Enter a particular version of the application that you entered in the Application field. If you leave this field blank, the system displays all versions associated with the application in the UnSecured node.
Product Code
Enter a product code to display all applications, versions, and forms associated with a particular product code. This field does not work in conjunction with the Application or Version fields.
The search results appear under the UnSecured node.
Expand the UnSecured node to view the individual applications or versions, and the forms associated with each, that do not already have security set for them.
After you expand the node, the individual items also appear in the grid.
In the Create with region, select one or both of these security options:
Run Security
Select this option to secure users from running the application.
Install Security
Select this option to prevent the just-in-time installation (JITI) of anything necessary to run the application.
Complete one of these steps:
Drag applications, versions, or forms from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move all applications to the Secured node.
From the Row menu, select Secure to All to move all objects that are under the UnSecured node to the Secured node.
If you secured an individual form, only the form appears under the Secured node. If you secured an application or version, the application or version and the forms associated with each appear under the Secured node.
To change the security on an item, select the item under the Secured node, select the appropriate security option, and then, from the Row menu, select Revise Security.
In the grid, the values under the Run and Install fields change accordingly.

 Securing a User or Role from All JD Edwards EnterpriseOne Objects
Securing a User or Role from All JD Edwards EnterpriseOne Objects
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Application.
On the Application Security form, enter the user or role ID in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
In the Display UnSecured Items area, enter *ALL in the Application field to select all JD Edwards EnterpriseOne objects, and then click Find.
Expand the UnSecured node and then click *ALL in the detail area.
In the Create with region, select one or both of these options:
Run Security
Use this option to secure users from running all applications.
Install Security
Use this option for JITI only.
Complete one of these steps:
Drag *ALL from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move *ALL to the Secured node.
From the Row menu, select Secure to All to move *ALL from UnSecured node to the Secured node.

 Removing Security from an Application
Removing Security from an Application
Access the Application Security form.
On the Application Security form, perform one of these steps:
Under the Secured node, select an application, version, or form and click Delete.
Drag an application, version, or form from the Secured node to the UnSecured node.
Select Remove All from the Row menu to move all items from the Secured node to the UnSecured node.
 Managing Action Security
Managing Action Security
This section provides an overview of action security and discusses how to:
Review the current action security settings for a user or role.
Add action security.
Remove action security.

 Understanding Action Security
Understanding Action Security
Action security enables you to secure the buttons that enable users to perform particular actions, such as adding, deleting, inquiring, revising, or copying a record. These buttons typically reside on the toolbar in a form. Do not confuse these buttons with buttons that are located on other parts of a form.
See Also
Managing Push Button, Link, and Image Security

 Reviewing the Current Action Security Settings
Reviewing the Current Action Security Settings
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Action.
On the Action Security form, enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
Current action security settings for the user or role appear under the Secured node in the tree.
To see if an action security is applied to a particular application, version, or form, complete a combination of these fields in the Display Secured Item region, and then click Find:
Application
Enter an application name, such as P01012.
Version
Enter a version of the application entered in the Application field to see if action security is applied to the version.
Form Name
Enter a form name, such as W01012A.
Expand the Secured node and click a secured item to view the current security settings for the user or role in the detail area.

 Adding Action Security
Adding Action SecurityEnter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Action.
On the Action Security form, enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
Current action security settings for the user or role appear under the Secured node in the tree.
To find the applications, versions, or forms to which you want to apply action security, complete any of these fields under the Display UnSecured Items heading, and then click Find:
Application
Enter an application name, such as P01012. Enter *ALL to display all applications.
Version
Enter a version of the application you entered in the Application field. If you leave this field blank, all versions associated with the application will appear in the UnSecured node.
Product Code
Expand the Unsecured node to view individual applications, versions, and forms in the detail area.
In the Create with region, select any of these options:
Change
Add
Delete
OK/Select
Copy
Scroll To End
To secure the actions on an application, version, or form, perform one of these steps:
Drag the application, version, or form from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move all items to the Secured node.
From the Row menu, select Secure to All to move all objects under the UnSecured node to the Secured node.
For example, to set delete security on an application, select the Delete option. Next, drag the application from the UnSecured node to the Secured node. The detail area will reflect the delete security that you set for this application, which means that the user you entered cannot perform the delete action on this application.
The applications or forms now appear under the Secured node and they have the appropriate action security.
To change the security on an item, select the item under the Secured node, select the appropriate security option, and then, from the Row menu, select Revise Security.
In the grid, the values for the security options change accordingly.

 Removing Action Security
Removing Action SecurityEnter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Action.
On the Action Security form, enter the user or role for which you want to change action security in the User / Role field, and then click Find.
To delete action security from an application, version, or form, do one of these:
Under the Secured node, select an application, version, or form and click Delete.
Under the Secured node, drag an application, version, or form from the Secured node to the UnSecured node.
Select Remove All from the Row menu to move all applications and forms from the Secured node to the UnSecured node.
 Managing Row Security
Managing Row Security
This section provides an overview of row security and discusses how to:
Add row security
Remove row security

 Understanding Row Security
Understanding Row Security
Row security enables you to secure users from accessing a particular range or list of data in any table. Use row security sparingly because it can adversely affect system performance. Additional processing occurs for each data item that you set with row security.
You can set up row security at three levels:
User
Group
*PUBLIC
JD Edwards EnterpriseOne first looks for row security at the user level, then at the group level, and then at the *PUBLIC level. If you set any of the security at a higher level, such as at the user level, the software ignores lower-level security settings, such as the group or *PUBLIC levels.
Before you set up row security for an item in a table, you should verify that the item is actually in that table. For example, the F0101 table contains the data item AN8. Therefore, you can set up row security for that item. However, the same table does not contain data item PORTNUM. Setting row security on this item for the F0101 table has no effect.
You set up row security on a table, not on a business view. You should verify that the object that you want to secure uses a business view over a table containing the object. For example, the Work With Environments application (P0094) uses business view V00941 over the F00941 table. You could secure the data item RLS (Release) because it is in the F00941 table. On the other hand, the same item is not in the F0094 table. If you attempt to secure the item on the F0094 table, data item RLS is not secured.
Note. You can find the tables, applications, forms, business views, and so on that use a data item by launching the Cross Reference application (P980011) after you build cross-reference tables (F980011and F980021).

 Prerequisite
Prerequisite
Before you can set up row security, you must activate row security in Data Dictionary Design.
See Creating a Data Dictionary Item.

 Adding Row Security
Adding Row Security
Enter P92001 in the Fast Path.
On the Work With Data Items form, click Find.
Note. You can enter search criteria in the Search Description field and the query by example (QBE) row to narrow your search.
Select the data item that you want to secure, and click Select.
The Data Item Specifications form appears.
On the Item Specifications tab, select the Row Security option and click OK.
This option must be selected for row security to work.
Click OK.
Exit the data dictionary application.
In Solution Explorer, enter P00950 in the Fast Path and press Enter.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Row.
On the Row Security form, complete the User / Role field and then click Find to display current row security.
Complete these fields, either in the first open detail area row (to add security) or in a pre-existing detail area row (to change security):
Table
You can enter *ALL in this field.
Data Item
This field is required.
From Value
This field is required.
Thru Value
Add
Change
Delete
View
Click OK to save the security information.

 Removing Row Security
Removing Row Security
On the Work With User/Role Security form, select an object.
From the Form menu, select Set Up Security, Row.
On the Row Security form, complete the User / Role field and click Find.
Note. If you accessed the Row Security form from the Work With User/Role Security form for a specific record, the user or role associated with the security record appears in the User / Role field by default.
Select the security record or records in the detail area, and then click Delete.
On Confirm Delete, click OK.
Click OK when you finish deleting row security.
If you do not click OK after you delete the row security records, the system does not save the deletion.
 Managing Column Security
Managing Column Security
This section provides an overview of column security and discusses how to:
Add column security
Remove column security

 Understanding Column Security
Understanding Column Security
This section explains how to add and revise column security. You can secure users from viewing a particular field or changing the value for a particular field. This item can be a database field, or a field that is defined in the data dictionary but is not in the database.
Note. You can find the tables, applications, forms, business views, and so on, that use a data item by launching the Cross Reference application (P980011) after you build the cross-reference tables (F980011and F980021).
You can set up column security on a table, an application, an application version, or a form. Even if an application uses a business view that does not contain the data item that you want to secure, you can still secure it, as long as the item appears on a form in the application.
Column Security on a Table
Before you set up column security on a table, do these:
Verify that the object that you want to secure is in the table.
Verify that the object that you want to secure is part of an application that uses a business view over a table containing the object.
Verify that the object that you want to secure uses a business view that includes the column containing the object.
For example, if you want to apply column security to data item RLS (Release Number) in the F00941 table, RLS must be an item in that table, and it must also be part of an application using a business view over that table. Finally, the business view over the F00941 table must include a column containing the data item RLS.
If all of these conditions are met, you can successfully apply column security to the data item. Setting column security on a table also means that you set security on the data item for any other applications that use the F00941 table.
Column Security on an Application
Before you set up column security on an application, do these:
Verify that the object that you want to secure is in the application.
Verify that you are securing the correct data item in an application (data item descriptions can be similar, if not identical).
For example, if you want to apply column security to data item UGRP (UserRole) in the Object Configuration Manager application (P986110), you first verify that the item is in the application. Because it is in the application, you can apply security to the data item. However, note that data items UGRP, MUSE, USER, and USR0 all contain the identical data description of User ID. Verify the item by its alias, not by its data description.
Column Security on an Application Version
You can secure users from using columns (or fields) in a version of an application. When you secure a column in a version, the system secures the column in all forms associated with that application version.
Before you set up column security on an application version, do these:
Verify that the object that you want to secure is in the version of the application.
Verify that you secure the correct data item in an application (data item descriptions can be very similar, if not identical). Verify the item by its alias, not by its data description.
Column Security on a Form
Security Workbench enables you to secure the column in one particular form, either in an application or in a version of an application.
Before you set up column security on a form, do these:
Verify that the object that you want to secure is in the form.
Verify that you secure the correct data item in the form (data item descriptions can be very similar for different data items).

 Adding Column Security
Adding Column Security
On the Work With User/Role Security form, select the Form menu, Set Up Security, Column.
On the Column Security form, complete the User / Role field, and then click Find to display current column security for the user or role.
To add new security, go to the last row of the detail area and enter information into any of these fields:
Table
Application
Version
If you want to add column security to a particular version, enter a version of the application that you entered in the Application field.
Form Name
You can enter *ALL in any of these fields; however, after *ALL is entered for a table, application, or form for a specific data item, you cannot enter *ALL again for that data item.
Complete these fields:
Data Item
View
Add
Change
To change security, change the row values in the detail area.
Click OK to save the security information.

 Removing Column Security
Removing Column Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Column.
On the Column Security form, complete the User / Role field, and then click Find.
Note. If you accessed the Column Security form from the Work With User/Role Security for a specific record, the user or role associated with the security record appears in the User/Role field by default.
Highlight the security record or records in the detail area and click Delete,and then click OK on Confirm Delete.
Click OK when you finish deleting column security.
If you do not click OK after you delete the security records, the system does not save the deletion.
 Managing Processing Option Security
Managing Processing Option Security
This section provides an overview of processing option security and discusses how to:
Review the current processing option security settings.
Add security to processing options.
Remove security from processing options.

 Understanding Processing Option Security
Understanding Processing Option Security
You can secure users from changing, prompting for values, and prompting for versions of specific processing options. By itself, setting security that prohibits users from prompting for versions does not prevent them from changing values in the processing option. If you do not want users to use processing option values, you might want to set security so that users are secured from the "prompt for" value and "prompt for" versions.
For example, to set prompt-for-values security, which also automatically sets change security, select the Prompt for Values option. Next, drag one application at a time from the UnSecured node to the Secured node. The detail area reflects the prompt-for-values and change security that you set for these applications. This procedure means that the user you entered cannot prompt for values or change processing options on any applications that you dragged to the Secured node.
This task also explains how to add a *ALL object and how to move all of the applications for a particular user or role from unsecured to secured.

 Reviewing the Current Processing Option Security Settings
Reviewing the Current Processing Option Security Settings
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select Set Up Security, Processing Option.
On the Processing Option Security form, enter a user or role ID in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
In the Display Secured Item region, complete these fields and then click Find:
Application
Enter an application name, such as P01012. Enter *ALL to display all applications.
Version
Enter a version of the application you entered in the Application field.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications. After you expand the node, the applications that are secured also appear in the detail area.

 Adding Security to Processing Options
Adding Security to Processing Options
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Processing Option.
On the Processing Option Security form, enter the user or role ID in the User / Role field and then click Find.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
In the Display UnSecured Items region, complete the appropriate fields and then click Find:
Application
Enter an application name, such as P01012. Enter *ALL to display all applications.
Version
You can enter a particular version of the application that you entered in the Application field. If you leave this field blank, all versions associated with the application will appear in the UnSecured node.
Product Code
You must perform this step before you can add new security. This step provides a list of applications from which you can apply processing option security.
The search results appear under the UnSecured node. Expand the node to view applications (interactive and batch) and menus with interactive or batch applications. After you expand the node, the applications appear in the detail area.
For example, to set security on applications within the 00 product code, you enter 00 in the Product Code field and click Find. All of the applications (interactive and batch) attached to product code 00 appear after you expand the UnSecured node.
In the Create with region, select one or more of these options and drag applications from the UnSecured node to the Secured node:
Change
Prompt for Values
When you select this option, you automatically activate the Change option.
Prompt for Versions
Prompt for Data Selection
Perform one of these actions:
Drag applications from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move all applications to the Secured node.
From the Row menu, select Secure to All to move all objects under the UnSecured node to the Secured node.
The applications now appear under the Secured node and have the appropriate security.
To change the security on an item, select the item under the Secured node, select the appropriate security option, and then, from the Row menu, select Revise Security.
In the grid, the values for the security options change accordingly.

 Removing Security from Processing Options
Removing Security from Processing Options
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Processing Option.
On the Processing Option Security form, enter a user or role ID to which you want to remove processing option security in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Click Find.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications. After you expand the node, the applications that are secured also appear in the detail area.
Perform one of these steps:
Under the Secured node, select an application or application version and click Delete.
Under the Secured node, drag an application or application version from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all items from the Secured node to the UnSecured node.
 Managing Tab Security
Managing Tab Security
This section provides an overview of tab security and discusses how to:
Add tab security
Remove tab security

 Understanding Tab Security
Understanding Tab Security
You can secure users from changing the name of the tab and viewing the form that you call by using the tab. For example, to set up change security, select the Change option. Next, drag tabs one at a time from the UnSecured node to the Secured node. The detail area reflects the changed security that you set for the tabs. This security means that the user you entered cannot change the tabs that you dragged to the Secured node.
Note. If you secure a user from an application, you cannot also secure the user from certain tabs on a form in that application. This restriction prevents redundant double security. Similarly, if you secure a user from a tab, you cannot secure the user from the application that contains the tab.

 Adding Tab Security
Adding Tab Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Tab Security.
On the Tab Exit Security form, complete these fields and click Find:
User / Role
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Application
You can view security for a specific application or enter *ALL to display all applications.
Current security settings for the user or role appear under the Secured node in the tree. Expand the nodes to view the secured tabs. After you expand the node, the secured tabs also appear in the grid.
Complete only one of these fields in the Display UnSecured Items region and click Find:
Application
Enter *ALL in this field to select all JD Edwards EnterpriseOne objects.
In the detail area, this special object appears as *ALL and displays the security that you defined for the object, such as Run Security or Install Security. The *ALL object acts as any other object, and you can use the Revise Security and Remove All options from the Row menu.
Product Code
You must perform this step before you can add new security. This step provides a list of applications from which to select.
The search (application or product code) appears under the UnSecured node. Expand the node to view applications (interactive and batch) and the associated tabs. After you expand the node, the applications or tabs also appear in the detail area.
For example, to set security for tabs in applications within the 00 product code, you enter 00 in the Product Code field and click Find. All of the applications (interactive and batch) attached to product code 00 appear after you expand the UnSecured node.
In the Create with region, select one or more of these options:
Change
Select this option to prohibit a user or role from changing information on the tab page.
View
Select this option to hide the tab from the user or the role.
Drag tabs from the UnSecured node to the Secured node.
These tabs now appear under the Secured node.
To change the security on an item, select the item under the Secured node, select the appropriate security option, and then, from the Row menu, select Revise Security.
In the grid, the values for the security options change accordingly.

 Removing Tab Security
Removing Tab SecurityAccess the Work With User/Role Security form.
From the Form menu, select Set Up Security, Tab Security.
On the Tab Exit Security form, complete these fields and click Find:
User / Role
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Application
You can view security for a specific application or enter *ALL to display all applications.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the secured tabs. After you expand the node, the secured tabs also appear in the grid.
Perform one of these steps:
Under the Secured node, select a tab and then click Delete.
Under the Secured node, drag a tab from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all tabs from the Secured node to the UnSecured node.
 Managing Hyper Exit Security
Managing Hyper Exit Security
Menu bar exits, also referred to as hyper exits, call applications and allow users to manipulate data. You can secure users from using these exits. Hyper exit security also provides restrictions for menu options. This section discusses how to:
Add hyper exit security
Remove hyper exit security.

 Adding Hyper Exit Security
Adding Hyper Exit Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Hyper Exit Security.
On the Hyper Exit Security form, complete these fields and click Find:
User / Role
Enter a complete user or role ID, which includes *PUBLIC but not wildcards.
Application
View security for a specific application. Enter *ALL to display all applications.
Current security settings for the user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications, such as interactive and batch. After you expand the node, the secured hyper-button exits also appear in the detail area.
In the Display Unsecured Items region, complete only one of these fields to locate the applications to which you want to apply exit security, and click Find:
Application
You can enter *ALL in this field.
Product Code
You can search for all of the applications within a product code. For example, to set security on hyper-buttons in applications within the 00 product code, you enter 00 in the Product Code field and click Find. All of the applications (interactive and batch) attached to product code 00 appear after you expand the UnSecured node.
The search (application, product code, or menu) appears under the UnSecured node. Expand the node to view applications (interactive and batch) and hyper-button exits. After you expand the node, the hyper-button exits also appear in the detail area.
Expand the UnSecured node to view and select applications (interactive and batch) and hyper-button exits.
After you expand the node, the hyper-button exits also appear in the detail area.
In the Create with region, select the Run Security option.
Drag exits one at a time from the UnSecured node to the Secured node.
The exits that you dragged now appear under the Secured node. The grid reflects the security that you set for these exits. This security prevents the user that you entered from using the exit.

 Removing Hyper Exit Security
Removing Hyper Exit SecurityEnter P00950 in the Fast Path..
On the Work With User/Role Security form, select the Form menu, Set Up Security, Hyper Exit Security.
Complete these fields and click Find:
User / Role
Enter a complete user or role ID, which includes *PUBLIC but not wildcards.
Application
View security for a specific application. Enter *ALL to display all applications.
Current security settings for the user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications, such as interactive and batch. After you expand the node, the secured hyper-button exits also appear in the detail area.
Perform one of these steps:
Under the Secured node, select a hyper exit and click Delete.
Under the Secured node, drag a hyper exit from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all hyper exits from the Secured node to the UnSecured node.
 Managing Exclusive Application Security
Managing Exclusive Application Security
This section provides an overview of exclusive application security and discusses how to:
Add exclusive application security.
Remove exclusive application access.

 Understanding Exclusive Application Security
Understanding Exclusive Application Security
Exclusive application security enables you to grant access to otherwise secured information through one exclusive application. For example, assume that you use row security to secure a user from seeing a range of salary information; however, the user needs to run a report for payroll that includes that salary information. You can grant access to the report, including the salary information, using exclusive application security. JD Edwards EnterpriseOne continues to secure the user from all other applications in which that salary information might appear.

 Adding Exclusive Application Security
Adding Exclusive Application Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Exclusive Application.
On the Exclusive Application Security form, complete the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Complete these fields in the detail area:
Object Name
Enter the name of the exclusive application for which you want to allow access (the security). For example, to change the security for a user of the Vocabulary Overrides application, enter P9220 in this field.
Run Application
Click OK to save the information.

 Removing Exclusive Application Access
Removing Exclusive Application Access
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Exclusive Application.
On the Exclusive Application Security form, complete the User / Role field and click Find.
Note. If you accessed the Exclusive Application Security form from a specific record in the Work With User/Role Security form, the user or role associated with the security record appears in the User/Role field by default.
Highlight the security records in the grid and click Delete.
On the Confirm Delete message form, click OK.
Click OK when you finish deleting exclusive application security.
If you do not click OK after you delete the security records, JD Edwards EnterpriseOne does not save the deletion.
 Managing External Calls Security
Managing External Calls Security
This section provides an overview of external call security and discusses how to:
Add external call security.
Remove external call security.

 Understanding External Call Security
Understanding External Call Security
In JD Edwards EnterpriseOne, certain applications exist that are not internal to JD Edwards EnterpriseOne; they are standalone executables. For example, the Report Design Aid, which resides on the Cross Application Development Tools menu (GH902), is a standalone application. You can also call this application externally using the RDA.exe. By default, this file resides in the \E810\SYSTEM\Bin32 directory.

 Adding External Call Security
Adding External Call Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, External Calls.
On the External Calls Security form, complete these fields and click Find:
User / Role
Enter a complete user or group ID, which includes *PUBLIC but not wildcards.
Executable
Enter the name of the external application, such as debugger.exe. When you enter information into this field, the software searches only for the indicated application.
Current security settings for that user or group appear under the Secured node in the tree. Expand the node to view the individual secured applications, such as debugger.exe.
In the Create with region, select the Run Security option.
Complete one of these steps:
Drag applications from the UnSecured node to the Secured node.
To move all applications to the Secured node, select All Objects from the Row menu.
The external call applications now appear under the Secured node and have the appropriate security.
For example, to set run security on the Business Function Design application, select the Run Security option and then drag the Business Function Design node from the UnSecured node to the Secured node. The detail area reflects the run security that you set for this application, which means that the user you entered could not run the Business Function Design application.
To change the security on an item, select the item under the Secured node, select the Run Security option, and then, from the Row menu, select Revise Security.
In the grid, the value in the Run field changes accordingly.

 Removing External Call Security
Removing External Call Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, External Calls.
On the External Calls Security form, complete these fields and click Find:
User / Role
Enter a complete user or group ID, which includes *PUBLIC but not wildcards.
Executable
Enter the name of the external application, such as debugger.exe. When you enter information into this field, the software searches only for the indicated application.
Current security settings for that user or group appear under the Secured node in the tree. Expand the node to view the individual secured applications, such as debugger.exe.
Perform one of these steps:
Under the Secured node, select an application and click Delete.
Under the Secured node, drag an application from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all applications from the Secured node to the UnSecured node.
 Managing Miscellaneous Security
Managing Miscellaneous Security
This section provides an overview of miscellaneous security and discusses how to manage miscellaneous security features.

 Understanding Miscellaneous Security
Understanding Miscellaneous Security
JD Edwards EnterpriseOne security enables you to secure users and roles from:
Read/write reports
Workflow status monitoring
Read/Write Reports Security
JD Edwards EnterpriseOne enables administrators to prevent specific users and roles from running reports that update JD Edwards EnterpriseOne database tables (read/write reports). Administrators can assign users to a user profile called No Update Report Creation User (NUR), which restricts users to running only read-only reports. When an NUR user runs a report, JD Edwards EnterpriseOne prevents the report from making table input/output (I/O) calls to databases that can affect business data. Users assigned to this profile can create and run read-only reports, but are restricted from creating or running existing UR reports. NUR users can copy existing UR reports and run the copied report, although the software disables the report's ability to change business data and displays a warning that the copied report cannot be updated. NUR users can edit NUR reports in Report Design Aid, but are prevented from even opening existing UR reports in RDA.
Workflow Status Monitoring Security
Users can access Workflow Modeler, (a scaled-down version of Process Modeler) to design JD Edwards EnterpriseOne workflow models. Process Modeler Server includes a JD Edwards EnterpriseOne Portal-based component called Model Viewer, which enables users with appropriate access to monitor the status of a workflow and perform workflow administration tasks directly from the Viewer.
Miscellaneous security includes these Workflow Status Monitoring settings, which determine the operations a user can perform from the Model Viewer:
Secured
Restricts users from accessing any Model Viewer tasks using the Portal.
Partial
Allows users to view workflow models and to monitor their status, but restricts these users from performing any administrative tasks.
Full
Allows users to access all Model Viewer tasks using the JD Edwards Collaborative Portal. Users can view workflow statuses and perform administrative tasks.

 Managing Miscellaneous Security Features
Managing Miscellaneous Security Features
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Misc Security.
On the Miscellaneous Security form, complete the User / Role field and click Find.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
To change Read-Only Report security, select one of these options:
Read / Write
Read Only
To change Workflow Status Monitoring security, select one of these options:
Secured
Prevents users from viewing or administering workflow.
View
Allows users to view workflow but prevents them from making changes.
Full
Allows users to view and administer workflow.
Click OK to accept the changes.
 Managing Push Button, Link, and Image Security
Managing Push Button, Link, and Image Security
This section provides an overview of push button, link, and image security and discusses how to:
Add push button, link, and image security.
Remove push button, link, and image security.
Note. Push button, link, and image security is enforced only for interactive applications in the JD Edwards EnterpriseOne HTML client and the Portal. It is not supported on the Microsoft Windows client.

 Understanding Push Button, Link, and Image Security
Understanding Push Button, Link, and Image Security
JD Edwards EnterpriseOne enables you to secure users from using or viewing push button, link, and image controls. You can secure users from using a control but still allow them to view it. Or you can prevent users from both using and viewing a control.
Note. In JD Edwards EnterpriseOne forms, static text and text boxes can be made into links. However, you can only apply security to static text links, not to text box links.
Security Workbench displays the objects that you want to secure in a hierarchical tree structure that contains nodes for each application, application version, and form. Security Workbench only displays the forms that contain push button, link, and image controls. You can secure an individual control by dragging the control from the UnSecured node to the Secured node. In addition, you can secure all controls—push buttons, links, or images—on a form by dragging the form node to the Secured node. You can perform the same action on applications and application versions. For example, to secure all the links within an entire application, you drag the application from the UnSecured node to the Secured node to secure all the links in every form within the application as well as within any versions of the application. If you drag an application version node to the Secured node, only the links in that application version are secured.
Note. For security purposes JD Edwards EnterpriseOne does not allow cross site scripting to be executed.
Push Button, Link, and Image Security on Subforms
You can secure push buttons, links, and images on both embedded and reusable subforms in JD Edwards EnterpriseOne. If you secure controls on an embedded subform, only the controls within that subform are secured. For reusable subforms, the behavior of the security depends upon the context in which the reusable subforms are used in power forms. If you apply security to a reusable subform under a power form, then only the controls in that reusable subform for that particular power form are secured, even if the reusable subform is used by another power form, as shown in this diagram:
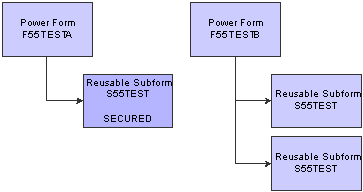
Push Button, Link, and Image Security on a Reusable Subform - Scenario 1
However, if you apply security to a reusable subform under a power form, and that subform is reused in the same power form, the security is applied to both subforms, as shown in this diagram:
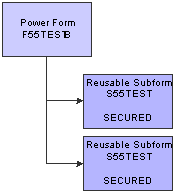
Push Button, Link, and Image Security on a Reusable Subform - Scenario 2
Because security functions differently on embedded subforms than it does on reusable subforms, Security Workbench provides a way for you to distinguish between the two forms. To make this distinction, the tree structure in Security Workbench displays the embedded subform using its form ID, and it displays the reusable subform using its form title.

 Adding Push Button, Link, and Image Security
Adding Push Button, Link, and Image Security
Enter P00950 in the Fast Path to access the Work With User/Role Security form.
From the Form menu, select Set Up Security, and then select the menu for push buttons, links, or images, depending on the type of object that you want to secure.
Complete the User / Role field and click Find.
Enter a complete user or role, which includes *PUBLIC.
In the Display UnSecured Items region, complete the appropriate fields and then click Find:
Application
Enter an interactive application name, such as P01012. Enter *ALL to display all applications.
Note. Batch applications are not supported.
Version
You can enter a particular version of the application that you entered in the Application field. If you leave this field blank, Security Workbench displays all unsecured versions associated with the application in the UnSecured node.
Product Code
Enter a product code to display all applications, versions, and forms associated with a particular product code. This field does not work in conjunction with the Application and Version fields.
The search results appear under the UnSecured node.
Expand the UnSecured node to view the individual applications or versions, and the forms associated with each.
Only the forms that contain controls are displayed.
Under the Create with region, select the type of security that you want to apply:
View
This option prevents the user from using and viewing the control.
Enable
This option prevents the user from using the control. However, the control is still visible.
Use one of these actions to secure the items:
Drag items from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move all applications to the Secured node.
The system displays the items under the Secured node that have the appropriate security. You can view the security for each item in the grid.

 Removing Push Button, Link, and Image Security
Removing Push Button, Link, and Image Security
Enter P00950 in the Fast Path.
On the Work with User/Role Security form, select the Form menu, Set Up Security, and then the menu for push buttons, links, or images.
Enter a user or role ID from which you want to remove the security in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Click Find.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications. After you expand the node, the applications that are secured also appear in the detail area.
Perform one of these steps:
Under the Secured node, select an application or application version and click Delete.
Under the Secured node, drag an application or application version from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all items from the Secured node to the UnSecured node.
 Managing Text Block Control and Chart Control Security
Managing Text Block Control and Chart Control Security
This section provides an overview of text block control and chart control security and discusses how to:
Review current text block control and chart control security settings.
Add text block control and chart control security.
Remove text block control and chart control security.

 Understanding Text Block Control and Chart Control Security
Understanding Text Block Control and Chart Control Security
JD Edwards EnterpriseOne enables you to secure users from using or viewing text block and chart controls. You can secure users from using a control but still allow them to view it. Or you can prevent users from both using and viewing a control.
In JD Edwards EnterpriseOne, a text block or chart control can have separate segments that contain links to other objects. You cannot secure these individual segments of a control. When you secure a text block or chart control, security is applied to the entire control.
See Also
Understanding Text Block Controls

 Reviewing Current Text Block Control and Chart Control Security Settings
Reviewing Current Text Block Control and Chart Control Security Settings
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select Set Up Security from the Form menu, and then select the menu for text block control or chart control.
Enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
The system displays the control security settings for the user or role under the Secured node in the tree.
To see if control security is applied to a particular application, version, or form, complete a combination of these fields in the Display UnSecured Items region, and then click Find:
Application
Enter an application name, such as P01012.
Version
Enter a version of the application entered in the Application field to see if control security is applied to the version.
Form Name
Enter a form name, such as W0101G.
Expand the Secured node and click a secured item to view the current security settings for the user or role in the detail area.

 Adding Text Block Control and Chart Control Security
Adding Text Block Control and Chart Control Security
Enter P00950 in the Fast Path to access the Work With User/Role Security form.
From the Form menu, select Set Up Security, and then select the menu for text block control or chart control, depending on the type of control that you want to secure.
Complete the User / Role field and click Find.
Enter a complete user or role, which includes *PUBLIC.
In the Display UnSecured Items region, complete the appropriate fields and then click Find:
Application
Enter an interactive application name, such as P01012. Enter *ALL to display all applications.
Note. Batch applications are not supported.
Version
You can enter a particular version of the application that you entered in the Application field. If you leave this field blank, Security Workbench displays all unsecured versions associated with the application in the UnSecured node.
Product Code
Enter a product code to display all applications, versions, and forms associated with a particular product code. This field does not work in conjunction with the Application and Version fields.
The search results appear under the UnSecured node.
Expand the UnSecured node to view the individual applications or versions, and the forms associated with each.
Only the forms that contain controls are displayed.
Under the Create with region, select the type of security that you want to apply:
View
This option prevents the user from using and viewing the control.
Enable
This option prevents the user from using the control. However, the control is still visible.
Use one of these actions to secure the items:
Drag the text block or chart control from the UnSecured node to the Secured node.
Select the control that you want to secure and then select Secure Selected from the Row menu.
From the Row menu, select All Objects to move all applications to the Secured node.
The system displays the items under the Secured node that have the appropriate security. You can view the security for each item in the grid.

 Removing Text Block Control and Chart Control Security
Removing Text Block Control and Chart Control Security
Enter P00950 in the Fast Path.
On the Work with User/Role Security form, select the Form menu, Set Up Security, and then the menu for text block control or chart control security.
Enter a user or role ID from which you want to remove the security in the User / Role field.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Click Find.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications. After you expand the node, the applications that are secured also appear in the detail area.
Perform one of these steps:
Under the Secured node, select an application or application version and click Delete.
Under the Secured node, drag an application or application version from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all items from the Secured node to the UnSecured node.
 Managing Media Object Security
Managing Media Object Security
This section provides an overview of media object security and discusses how to:
Review the current media object security settings for a user or role.
Add media object security.
Remove media object security.

 Understanding Media Object Security
Understanding Media Object Security
JD Edwards EnterpriseOne enables you to secure users from adding, changing, deleting, or viewing media objects within interactive applications, forms, or application versions. You can apply media object security to ensure that media object attachments cannot be modified or tampered with after they have been added.
If you apply view security to media object attachments, Security Workbench automatically prevents the user from adding, deleting, or changing media objects. If you apply change security to media object attachments, Security Workbench automatically prevents the user from deleting the media object.
Media object security enables you to use media object attachments as a mechanism for recording justifications for transactions and for legal purposes. For example, your company may have a business process that requires clerks to use media object attachments to document the reason or justification for adjusting a price on an item in a transaction. In this case, you would allow the clerks to add and view media object attachments in an application, but secure them from deleting or modifying them. In addition, this type of security prevents users from modifying or deleting attachments that others have added. As a result, the media object attachments provide secured information about previous transactions. This information can be reviewed by interested parties for legal or other purposes.
Note. Media object security is enforced only in interactive applications on the JD Edwards EnterpriseOne web client and the Portal.
It is not supported on the Microsoft Windows client.
Also, media object system functions enforce media object security in the web client. When running applications that have media
object security applied to them, the system logs the security information for the system functions in the web client debug
log file.

 Reviewing the Media Object Security Settings
Reviewing the Media Object Security Settings
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Media Object.
On the Media Object Security form, enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
The system displays current media object security settings for the user or role under the Secured node in the tree.
To see if a media object security is applied to a particular application, version, or form, complete a combination of these fields in the Display UnSecured Items region, and then click Find:
Application
Enter an application name, such as P01012.
Version
Enter a version of the application entered in the Application field to see if media object security is applied to the version.
Form Name
Enter a form name, such as W0101G.
Expand the Secured node and click a secured item to view the current security settings for the user or role in the detail area.

 Adding Media Object Security
Adding Media Object SecurityEnter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Media Object.
On the Media Object Security form, enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
Current media object security settings for the user or role appear under the Secured node in the tree.
To find the applications, versions, or forms to which you want to apply media object security, complete any of these fields in the Display UnSecured Items region, and then click Find:
Application
Enter an application name, such as P01012. Enter *ALL to display all applications.
Version
Enter a version of the application you entered in the Application field. If you leave this field blank, all versions associated with the application will appear in the UnSecured node.
Product Code
Expand the Unsecured node to view individual applications, versions, and forms in the detail area.
In the Create with region, select any of these options:
Change
Add
Delete
View
Note. If you apply view security to media object attachments, Security Workbench automatically prevents the user from adding, deleting, or changing media objects. If you apply change security to media object attachments, Security Workbench automatically prevents the user from deleting the media object.
To secure the media objects on an application, application version, or form, perform one of these steps:
Drag the application, version, or form from the UnSecured node to the Secured node.
From the Row menu, select All Objects to move all items to the Secured node.
From the Row menu, select Secure to All to move all objects beneath the UnSecured node to the Secured node.
For example, to set delete security, select the Delete option. Next, drag the application from the UnSecured node to the Secured node. The detail area will reflect the media object security that you set for this application.
The applications or forms now appear under the Secured node, and they have the appropriate media object security.

 Removing Media Object Security
Removing Media Object Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Media Object.
In the User / Role field, enter a user or role ID from which you want to remove media object security.
Enter a complete user or role, which includes *PUBLIC but not wildcards.
Click Find.
Current security settings for that user or role appear under the Secured node in the tree. Expand the node to view the individual secured applications. After you expand the node, the applications that are secured also appear in the detail area.
Perform one of these steps:
Under the Secured node, select an application or application version and click Delete.
Under the Secured node, drag the item that is secured from the Secured node to the UnSecured node.
On the Row menu, select Remove All to move all items from the Secured node to the UnSecured node.
 Managing Data Browser Security
Managing Data Browser Security
This section provides an overview of Data Browser security and discusses how to:
Add Data Browser security.
Remove Data Browser security.

 Understanding Data Browser Security
Understanding Data Browser Security
Data Browser security enables you to grant permission to users, roles, or *PUBLIC to access the Data Browser program. There are two levels of Data Browser security that you can assign to users. The first level grants access to the Data Browser, which users can use to perform public or personal queries. After you grant this access, you can grant an additional level of security that allows Data Browser users to select a particular table or business view that they wish to query.
You can also use the Copy feature in Security Workbench to copy Data Browser security from one user or role to another.
See Also
Viewing the Data in Tables and Business Views

 Adding Data Browser Security
Adding Data Browser Security
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, Set Up Security, Data Browser.
On the Data Browser Security form, enter the user or role ID in the User / Role field and click Find.
You can enter *PUBLIC but not wildcards.
In the Data Browser hierarchical security permissions region, select one or both of these options, depending on the level of security that you want to grant:
Allow access to launch Data Browser.
This option gives users access to the Data Browser, which they can use to perform personal or public queries.
Allow access to Search and Select for Tables or Business View Queries.
This option gives users the ability to search and select the table or business view that they want to query.
Note. This option is enabled only after you select the first option.
Click OK.
Note. To activate Data Browser security changes, you must refresh the jdbj security cache using the SAW.

 Removing Data Browser Security
Removing Data Browser Security
You can remove Data Browser security using the Data Browser Security form or the Work With User/Role Security form. To remove security using the Data Browser Security form, clear the security check boxes for a user, role, or *PUBLIC. Using the Work With User/Role Security form, search for the security record and then delete the Data Browser security record from the grid.
 Managing Published Business Services Security
Managing Published Business Services Security
This section provides an overview of published business services security and discusses how to:
Review the current published business services security records.
Authorize access to published business services.
Add multiple published business services security records at a time.
Delete published business services security.

 Understanding Published Business Services Security
Understanding Published Business Services Security
JD Edwards EnterpriseOne provides security to ensure that web service consumers are authenticated in the JD Edwards EnterpriseOne system and authorized to access published business services. The authentication of users of published business service users is handled by the Business Services Server and EnterpriseOne security server. After a user is authenticated by the JD Edwards EnterpriseOne security server, the system checks if the user is authorized to run a published business service by retrieving records from the JD Edwards EnterpriseOne F00950 security table, which contains all the object security records.
Note. This section discusses only the authorization of users to access published business services.
For published business services, JD Edwards EnterpriseOne uses a “secure by default” security model which means that users cannot access a published business service unless a security record exists that authorizes access. For all other objects in JD Edwards EnterpriseOne, access is granted unless otherwise secured or restricted.
You manage published business services security using Security Workbench (P00950), the application used to manage all object security in JD Edwards EnterpriseOne. In P00950, you can add, copy, modify, or delete security records for published business services. When a user tries to access or run a published business service, verification of authorization is done through an API that queries records in the F00950 security table.
As with all object security in JD Edwards EnterpriseOne, you can assign published business service security to a user, role, or *PUBLIC. You can create a security record that allows a user or role access to:
A particular method in a published business service.
All methods in a published business service.
All published business services.
It is recommended that you set up security by role first. This method makes setting up published business services security easier; instead of defining security for individual users, you can define security for the role and then assign users to the appropriate roles. If an individual in a role needs a different security setup, you can assign security at the user level, which overrides the role settings.
In addition, you can create a security record that disallows access to a published business service. Typically, there is no need to add security records that disallow access because by default, access to published business services is not allowed. However, creating a security record that disallows access can be an efficient method to set up published business services security. For example, to allow a role access to all but a small subset of published business services, you can:
Enter *ALL in the fields for the published business service and published business service method to create a security record that allows the role access to all published business services.
Create security records for the same role that disallows access to a subset of published business services.
Inherited Security
When creating a published business service, a developer can configure it to pass its context to any published business service that it calls. In this configuration, authorization for the called published business service is inherited; that is, if the calling business service is authorized, then the called business service is authorized as well. In this scenario, the system does not check the security for the called business service.
However, it is possible (though not supported) to configure a published business service so that it does not pass its context to another business service. In this scenario, the security or authorization for the called published business service is not inherited. Even if a user is authorized to access the calling or parent business service, the system also checks if access to the called business service is allowed. As a result, if there is not a security record that allows access to the called business service, the system will produce an exception or error, denying access to the called business service.
How JD Edwards EnterpriseOne Checks Published Business Services Security
JD Edwards EnterpriseOne checks security for published business services in the same sequence that it checks security for all other JD Edwards EnterpriseOne objects—first by user, then role, and finally *PUBLIC. The system applies the first security record found. In addition, for the user, role, and *PUBLIC, the system checks for published business services security in this sequence:
Published business service + method.
Published business service.
*ALL.
Note. Using *ALL to set up object security in Security Workbench is not related to the *ALL functionality that is used to sign into JD Edwards EnterpriseOne. *ALL in Security Workbench enables you to assign a user, role, or *PUBLIC to all objects of a particular type. *ALL during sign-in enables users to sign into JD Edwards EnterpriseOne with all the roles that have been assigned to them.
This illustration shows how the system checks for published business services security for a user signed in with *ALL and a user signed in with a specific role:
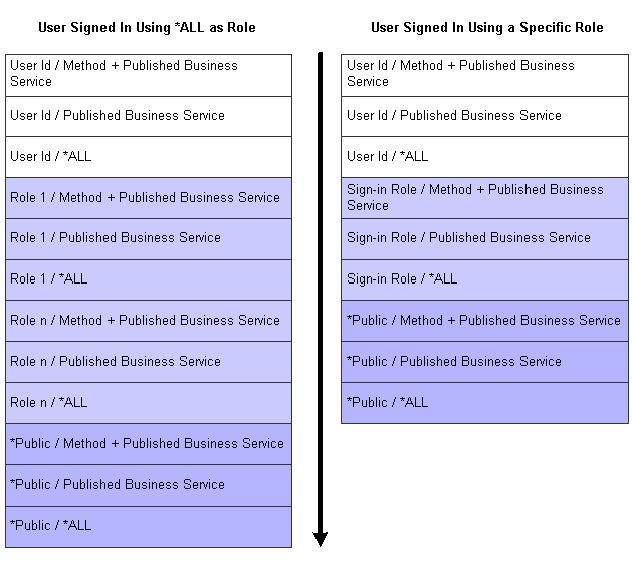
*Role 1 has the highest role sequence.
If a user is assigned to multiple roles and signs in as *ALL, the system uses role sequencing to determine which security record is used. A system administrator sets up role sequencing when setting up user and role profiles.
See Sequencing Roles.
Published Business Services Security Log Information
The log file provides administrators with information that you can use for troubleshooting business service security without revealing details that could possibly create a gap in the security.
When a web service attempts to access a published business service in JD Edwards EnterpriseOne, the system records the authorization information in the log file. If the logging level is set to “Debug,” the log file records whether authorization was granted or denied. If the log level is set to “Severe,” the system only logs information if the attempt to access a web service fails. This is an example of the information provided in the log file:
Access to <method name> in <published business service name> is <granted/denied> for <user name> with <role name>.
See Also
Server Manager Guide for information on how to view business service security log file information.
JD Edwards EnterpriseOne Business Services Server Reference Guide for information on how to configure JD Edwards EnterpriseOne to authenticate users of published business services.

 Reviewing the Current Published Business Services Security Records
Reviewing the Current Published Business Services Security Records
You can use the Work With User/Role Security form in P00950 to review existing published business services security records. The query by example row of the grid enables you to display all security records for published business services. You can further narrow the search by locating the records for a user, role, or a particular published business service.
In addition, you can review published business services security records by running the Security Audit Reports—Security by Object (R009501) and Security by User/Role (R009502).
See Running a Report that Lists Published Business Service Security Records.
From the Security Maintenance menu (GH9052), select Security Workbench (P00950).
On the Work with User/Role Security form, enter S in the Security Type column and then click Find.
To narrow the search by user or role, enter a user or role in the query by example field in the User / Role column and then click Find.
To view the security records for a particular published business service, complete the query by example field at the top of the Published BSSV column and then click Find.

 Authorizing Access to Published Business Services
Authorizing Access to Published Business Services
In P00950, you can create security records that allow a user, role, or *PUBLIC access to:
A particular method in a published business service.
A published business service.
All published business services.
From the Security Maintenance menu (GH9052), select Security Workbench (P00950).
On Work with User/Role Security, select the Form menu, Set Up Security, Published BSSV.
By default, *PUBLIC is in the User / Role field. If any records exist for *PUBLIC, those records appear in the grid.
On Published Business Service Security Revision, enter the user, role, or *PUBLIC to which you want to allow access to a published business service.
To allow access to a particular method in a published business service:
On Published Business Service Security Revision, click the visual assist in the Published BSSV column to search for and select a published business service.
On the same form, click the visual assist in the Published BSSV Method column to select the method that you want to allow access to.
On Published BSSV Method, you must enter the published business service again in the Published BSSV column to see a list of all the methods for the published business service. The system displays published business services by the method that is being exposed in the published business service. A published business service that contains multiple methods will have multiple rows in the grid, one for each method.
Select the row that contains the method that you want to secure and then click the Select button.
On Published Business Service Security Revision, click the visual assist in the Execute Allowed column and then select Y to allow access to the published business service method.
To allow access to a published business service (including all its methods):
Click the visual assist in the Published BSSV column to search for published business services.
On Select Business Service, complete the Business Service field and click the Find button.
Select the published business service that you want to secure and then click the Select button.
On Published Business Service Security Revision, in the row that contains the published business service, enter *ALL in the Published BSSV Method column.
In the same row, click the visual assist in the Execute Allowed column and then select Y to allow access to the published business service.
To allow access to all published business services:
Enter *ALL in the row under the Published BSSV column.
Enter *ALL in the row under the Published BSSV Method column.
Click OK.
In the same row, click the visual assist and then select Y to allow access to the published business services objects.
By default, users are not allowed access to published business services objects in JD Edwards EnterpriseOne. However, you can select N to create a security override that disallows access to an object.

 Adding Multiple Published Business Services Security Records at a Time
Adding Multiple Published Business Services Security Records at a Time
Security Workbench provides a form that you can use to add multiple published business services security records at a time.
From the Security Maintenance menu (GH9052), select Security Workbench (P00950).
On Work with User/Role Security, select the Form menu, Set Up Security, Published BSSV.
On Published Business Service Security Revision, from the Form menu, select Secure by Method.
On the Secure by Method form, enter the user, role, or *PUBLIC for which you want to set up published business services security, and then click the Find button.
The system displays published business services by the method that is being exposed in the published business service. A published business service that contains multiple methods will have multiple rows, one for each method.
Use the query-by-example fields at the top of the grid to refine your search. For example, if you want to set up security for all methods that perform an add or delete, you search for those methods by typing add* or delete* in the Published BSSV Method query by example field in the grid.
Select the check box next to the items that you want to secure.
Click either the Allow Execute or Disallow Execute button.
On Confirm Batch Secure, click OK.
The system displays the number of records that were added or updated.

 Deleting Published Business Services Security
Deleting Published Business Services Security
To delete published business services security records, you can use the same form that you used to authorize access to published business services.
In addition to this method, you can use the Work with User/Role Security form in P00950 to delete the records in the same way that you would delete any other object security record.
See Deleting Security on the Work With User/Role Security Form.
From the Security Maintenance menu (GH9052), select Security Workbench (P00950).
On Work With User/Role Security, select the Form menu, Set Up Security, Published BSSV.
On Published Business Service Security Revision, enter the user, role, or *PUBLIC from which you want to delete a published business services security record and then click Find.
Click the check box next to the each record that you want to delete and then click the Delete button.
Click OK to confirm the delete.
 Copying Security for a User or a Role
Copying Security for a User or a Role
This section provides an overview of copying security for a user or a role and discusses how to:
Copy all security records for a user or a role.
Copy a single security record for a user or a role.

 Understanding How to Copy Security for a User or a Role
Understanding How to Copy Security for a User or a RoleYou can copy the security information for one user or role, and then use this information for another user or role. When you copy security, you can either overwrite the current security for the user or role, or you can add the new security information to the existing security information. You can also copy all of the security records for a user or role, or you can copy one security record at a time for a user or role.

 Copying All Security Records for a User or a Role
Copying All Security Records for a User or a Role
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, select the Form menu, and then select Copy Security.
Select one of these options:
Copy and Add
When you copy and add security settings, you do not overwrite preexisting security for user or role.
Copy and Replace
When you copy and replace security settings, the software deletes the security information for a user or role, and then copies the new security information from the selected user or role.
Complete these fields and click OK:
From User / Role
To User / Role
The system saves the security information and returns you to the Work With User/Role Security form.

 Copying a Single Security Record for a User or a Role
Copying a Single Security Record for a User or a Role
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, locate a security record.
Select the security record row that you want to copy, and then click Copy.
Complete the To User / Role field and click OK.
The system saves the security information and returns you to the Work With User/Role Security form.
 Reviewing and Deleting Security Records on the Work With User/Role Security Form
Reviewing and Deleting Security Records on the Work With User/Role Security FormThis section provides an overview on how to review security records and discusses how to:
Review security on the Work With User/Role Security form.
Delete security on the Work With User/Role Security form.

 Understanding How to Review Security Records
Understanding How to Review Security Records
On the Work With User/Role Security form in P00950, you can review security records for a user or role based on security type, such as action, application, row, or any of the other types of security that can be added in P00950. The system displays all the security records for the user or role based on the security type that you select. For example, when you search for application security records for the AP Role, the system displays all the application security records for the AP role in the application grid.
The settings for each security type are displayed as columns in the grid. The columns that appear in the grid are based on the security type that you select. For example, application security provides two different levels of security: run and install. When you search for application security records, P00950 displays only the columns for Run and Install in the grid. However, action security contains several settings, such as OK/Select, Copy, Delete, OK, and so forth. When you search for action security records, the grid displays only columns for each of these security settings. The value in the column, either Y or N, indicates whether or not each setting is secured.
In addition, you can search on all security records of a particular security type. As a result, the system displays records for every user and role with the security type that was specified. You can search on all Security Workbench records by clicking the Find button.
Note. You can also review and delete security records on the form used to add a particular type of object security record, such as application, action, row, and so forth. Refer to the section on how to manage a particular type of object security for more information.

 Reviewing Security on the Work With User/Role Security Form
Reviewing Security on the Work With User/Role Security Form
Enter P00950 in the Fast Path to access the Work With User/Role Security form..
On the Work With User/Role Security form, click Find.
To search for records by user or role, complete the User/Role field and then click Find.
To narrow the search by security type, click the Search button in the Security Type column to select a code and then click the Find button.

 Deleting Security on the Work With User/Role Security Form
Deleting Security on the Work With User/Role Security Form
Enter P00950 in the Fast Path.
On the Work With User/Role Security form, click Find.
To search for records by user or role, complete the User/Role field and then click Find.
To narrow the search by security type, click the Search button in the Security Type column to select a code and then click the Find button.
Select a record in the grid, and then click Delete.
On Confirm Delete, click OK.
Security Workbench deletes the security record and refreshes the grid.
 Running Security Workbench Records Reports
Running Security Workbench Records Reports
This section provides an overview of the Security Workbench Records reports and discusses how to:
Run the Security Audit Report by Object version (R009501, XJDE0001).
Run the Security Audit Report by User version (R009502, XJDE0001).
Run the Security Audit Report by Role version (R009502, XJDE0002).

 Understanding the Security Workbench Records Reports
Understanding the Security Workbench Records Reports
JD Edwards EnterpriseOne provides two Security Workbench Records reports—Security by Object (R009501) and Security by User/Role (R009502)—that you can run to review the current security records by object type and user or role. The Security Workbench Records reports list security records for these objects:
Interactive and batch applications.
Tables (rows and columns).
Published business services.
Before choosing which report to run, you should consider the data that you want the report to produce. Run the Security by Object report (R009501) to generate a report that lists the security records based on a particular object, object type, or product code. You can refine the data selection for this report to list only records for a particular user ID, role, or a combination of user ID and role. Run the Security by User/Role report (R009502) to generate a report that lists all the application, row, column, and published business service security records for a particular user ID, role, or *PUBLIC.
Each report contains processing options that you can use to define the output of the report. Along with the processing options, you can use the Data Selection form in the Batch Version program (P98305W) to further refine the data that the report produces.
Each security record in the report indicates the level of security, or type of security, that is applied to the object. For application security, each record indicates if a user or role has permission to install, run, or both install and run the application. For row security, each record indicates if view, add, change, or delete security have been applied. For column security, each record indicates if view, add, or change security have been applied. For published business service security, each record indicates whether a user or role has access to the published business service object.
How you set up your report determines how readily you can find gaps in your security plan. For example, if you have a highly sensitive application and you want to ensure that only the appropriate users have access to it, you can refine the R009501 report (Security Audit Report by Object) to list only the security records for that particular application.
Example of Security by Object Report (R009501)
This example shows the results of running the R009501 report. The report has been set up to list all the security records for the P00950 program.
Example of Security by Object Report.
Example of Security Audit Report by User (R009502, XJDE0001)
This example shows the results of running the Security Audit Report by User version of the R009502 report. The report lists the security records for a particular user in order of application, row, and then column. This example shows only the first page of the report, which lists the application security records for the user ID.
Example of Security Audit Report by User Report
Example of Security Audit Report by Role (R009502, XJDE0002)
This example shows the results of running the Security Audit Report by Role version of the R009502 report. The data selection of the report has been defined to list security records for the OWTOOL role. This example shows the third page of the report, which lists the row and column security records for the OWTOOL role.
Example of Security Audit Report by Role

 Run the Security Audit Report by Object Version (R009501, XJDE0001)
Run the Security Audit Report by Object Version (R009501, XJDE0001)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
In the Batch Application field, enter R009501 and click the Find button.
Select the Security Audit Report by Object version.
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
User ID or Role (optional)
Enter a user ID or role to refine the report to generate only records based on that particular user ID or role.
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
Report on Column Security
Leave blank if you want the report to list application security records. Enter 1 to exclude application security records.
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
Note. In addition, to generate a report that displays published business service security records, you need to add an additional condition in the Data Selection form, as discussed below.
On the Work With Batch Versions - Available Versions form, click Select.
On the Versions Detail form, select the Data Selection check box and click the Submit button.
On the Data Selection form, you can add a condition to filter on a particular object, object type, or product code.
If the processing option is set to list published business service security records, you must add the following condition after the default Where condition:
And BC Source Language (F9860) (SRCLNG) [BC] is equal to "SBF"
Click the OK button.
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.

 Run the Security Audit Report by User Version (R009502, XJDE0001)
Run the Security Audit Report by User Version (R009502, XJDE0001)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
In the Batch Application field, enter R009502 and click the Find button.
Select the Security Audit Report by User version.
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
Role (optional)
To refine the report to generate only records based on a particular role of the user, enter a role.
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
Report on Column Security
Leave blank if you want the report to list column security records. Enter 1 to exclude column security records.
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
On the Work With Batch Versions - Available Versions form, click Select.
On the Versions Detail form, select the Data Selection check box and click the Submit button.
On the Data Selection form, use the User ID left operand to define the user ID that you want the report to list security records for.
Click OK.
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.

 Run the Security Audit Report by Role Version (R009502, XJDE0002)
Run the Security Audit Report by Role Version (R009502, XJDE0002)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
In the Batch Application field, enter R009502 and click the Find button.
Select the Security Audit Report by Role version.
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
Role (optional)
Do not use this option for this report. Instead, enter the role in the Data Selection form.
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
Report on Column Security
Leave blank if you want the report to list application security records. Enter 1 to exclude application security records.
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
On the Work With Batch Versions - Available Versions form, click Select.
On the Versions Detail form, select the Data Selection check box and click the Submit button.
On the Data Selection form, use the User ID left operand to define the role that you want the report to list security records for.
Click OK on the Data Selection form.
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.

 Running a Report that Lists Published Business Service Security Records
Running a Report that Lists Published Business Service Security Records
You can use the Security Workbench Records reports to generate a list of published business service security records by object, user, or role. However, before you run the report, you must use the Data Selection form to specify the published business service object type.
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
In the Batch Application field, enter either R009501or R009502 and click the Find button.
Select the version of the report that you want to run.
On the Work With Batch Versions - Available Versions form, click Select.
On the Versions Detail form, select the Data Selection check box and click the Submit button.
On the Data Selection form, enter these conditions and then click OK:
Where BC Object Type (F9860) (FUNO) is equal to "BSFN" And BC Source Language (F9860) (SRCLNG) [BC] is equal to "SBF"
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.