| Oracle® Identity Manager Design Console Guide Release 9.1.0.2 Part Number E14762-01 |
|
|
View PDF |
| Oracle® Identity Manager Design Console Guide Release 9.1.0.2 Part Number E14762-01 |
|
|
View PDF |
This chapter describes resource management in the Design Console. It contains the following sections:
The Resource Management folder provides you with tools to manage Oracle Identity Manager resources. This folder contains the following forms:
IT Resources Type Definition: Use this form to create resource types that are displayed as lookup values on the IT Resources form.
IT Resources: Use this form to define and manage IT resources.
Rule Designer: Use this form to create rules that can be applied to password policy selection, automatic group membership, provisioning process selection, task assignment, and prepopulating adapters.
Resource Objects: Use this form to create and manage resource objects. These objects represent resources that you want to make available to users and organizations.
See Also:
See Oracle Identity Manager Tools Reference for more information about adapters and adapter tasksThe IT Resources Type Definition form is in the Resource Management folder. You use the IT Resources Type Definition form to classify IT resource types, for example, AD, Microsoft Exchange, and Solaris. Oracle Identity Manager associates resource types with resource objects that it provisions to users and organizations.
After you define an IT resource type on this form, it is available for selection when you define a resource. The type is displayed in the Type field on the IT Resources form.
IT resource types are templates for the IT resource definitions that reference them. If an IT resource definition references an IT resource type, the resource inherits all of the parameters and values in the IT resource type. The IT resource type is the general IT classification, for example, Solaris. The resource is an instance of the type, for example, Solaris for Statewide Investments. You must associate every IT resource definition with an IT resource type.
Figure 5-1 shows the IT Resources Type Definition form.
Figure 5-1 The IT Resources Type Definition Form
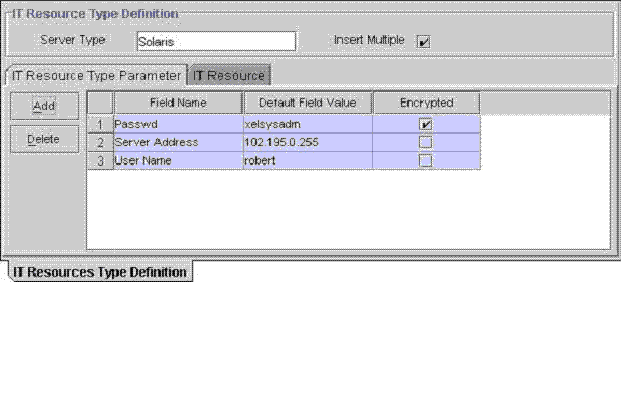
Table 5-1 describes the fields of the IT Resources Type Definition form.
Table 5-1 Fields of the IT Resources Type Definition Form
| Field Name | Description |
|---|---|
|
Server Type |
The name of the IT resource type |
|
Insert Multiple |
Specifies whether or not this IT resource type can be referenced by more than one IT resource |
Note:
If an IT resource must access an external resource but is not able to do so by using the network, then you must associate it with a remote manager. For more information, see Oracle Identity Manager Tools Reference.To define an IT resource type:
Enter the name of the IT resource type in the Server Type field, for example, Solaris.
To make the IT resource type available for multiple IT resources, select Insert Multiple.
Click Save.
The IT resource type is defined. You can select it from the Type field when defining IT resources in the IT Resources form.
After you save the basic information for a new IT resource type, and when an IT resource type is returned on a query, the fields on the tabs of the IT Resources Type Definition form's lower region are enabled.
The IT Resources Type Definition form contains the following tabs:
IT Resource Type Parameter tab
IT Resource tab
You use the IT Resource Type Parameter tab to specify default values and encryption settings for all connection parameters for the IT resource type, as shown in Figure 5-1. Oracle recommends that you do not specify default values for passwords and encrypted fields. Parameters and values on this tab are inherited by all IT resources that reference this IT resource type.
When you define a new parameter, the parameter and its values and encryption settings are added to the current IT resource type and to any new or existing IT resource definitions that reference this IT resource type. For an applicable resource definition, the new parameter is displayed in the Parameters tab of the IT Resources form.
Note:
You can customize the values and encryption settings for these parameters within each IT resource.Adding a Parameter to an IT Resource Type
To add a parameter to an IT Resource Type:
Click Add.
A new row is displayed in the IT Resource Type Parameter tab.
In the Field Name field, enter the name of the parameter.
In the Default Field Value field, enter a default value.
This value is inherited by all IT resources that reference this IT resource type
Select or clear the Encrypted option.
This check box determines if this parameter's value is masked, that is, represented with asterisk (*) in a form field.
If you want the parameter's value to be masked, select this check box.
Click Save.
Removing a Parameter from an IT Resource Type
To remove a parameter from an IT Resource Type:
Select the parameter you want to remove.
Click Delete.
The parameter and its associated value are removed from the IT resource type and from IT resource definitions that reference this type.
The IT Resource Type Definition Table displays the following information:
| Field Name | Description |
|---|---|
| Server Type | The name of the resource asset type, as defined in the IT Resource Type Definition form |
| Insert Multiple | Indicates whether or not multiple instances of this IT Resource Definition can be created |
The IT Resources form is in the Resource Management folder. You use this form to view and configure IT resources. IT resource definitions usually represent hardware, for example, a server or a computer where one or more resources are located. Each IT resource definition represents an instance of an IT resource type.
During a provisioning event, resource objects reference IT resource definitions. The definition specifies where the resource is located and how to connect to it. A resource object must be associated with an IT resource definition.
You can map the variables of an Oracle Identity Manager adapter to the values of any parameter for an IT resource. The parameters represent information about the hardware, for example, a server domain name or the ID of the user who accesses this IT resource.
See Also:
Oracle Identity Manager Tools Reference for more information about adapters and their mappingsTable 5-2 describes the fields of the IT Resources form.
Table 5-2 Fields of the IT Resources Form
| Field Name | Description |
|---|---|
|
Name |
The name of the IT resource. |
|
Type |
The classification type of the IT Resource, as defined in the IT Resources Type Definition form. |
|
Remote Manager |
If the IT resource can be accessed by using a remote manager, then this field displays the name of the remote manager. Otherwise, this field is empty. |
To define an IT Resource:
Enter the name of the IT resource in the Name field.
Double click the Type lookup field, and in the Lookup dialog box, select the IT resource type to associate with this IT resource.
You define the IT resource types by using the IT Resource Type definition form.
Click OK.
To access the IT resource by using a remote manager, double-click the Remote Manager lookup field, and in the Lookup dialog box select a remote manager.
If the IT resource is not accessed by using a remote manager, then go to Step 6.
Click OK.
Click Save.
The saved IT resource is displayed on the IT Resource tab of the IT Resources Type Definition form for the associated IT resource type. The parameters and default values for the IT resource classification type are displayed in the Parameters tab.
Optionally, to specify IT resource-specific values for the parameters on the Parameters tab, select the Value field for the parameter you want to change, enter the new value, and click Save.
Use the Administrators tab to specify the access permissions for administrative groups and the level of security for the IT Resource APIs.
To set access permissions:
Click the Administrators tab.
By default, the administrative group associated with this IT Resource Instance is displayed.
Click Assign to add a new administrative group.
For example, you can assign G2 as an administrative group for the ramone IT Resource instance.
Select the appropriate check box for the permissions listed in the following table:
Click Save.
Rules are criteria that enable Oracle Identity Manager to match conditions and take action based on them. A rule can be assigned to a specific resource object or process, or a rule can apply to all resource objects or processes.
The following are examples of rule usage:
Determining a password policy to apply to a resource object of type Application.
Enabling users to be added to user groups automatically.
Specifying the approval and provisioning processes that apply to a resource object after that resource object is assigned to a request.
Determining how a process task is assigned to a user.
Specifying which prepopulate adapter is executed for a given form field.
See Also:
Oracle Identity Manager Tools Reference for more information about prepopulate adaptersThe Rule Designer form shown in Figure 5-2 is in the Resource Management folder. You use this form to create and manage rules that are used with resources.
There are four types of rules:
General: Enables Oracle Identity Manager to add a user to a user group automatically and to determine the password policy that is assigned to a resource object.
Process Determination: Determines the approval process for a request, and the approval and provisioning processes for a resource object.
Task Assignment: Specifies the user or user group that is assigned to a process task.
Prepopulate: Determines which prepopulate adapter is executed for a form field.
A rule contains the following items:
A rule element: Consists of an attribute, an operator, and a value. In Figure 5-2, the attribute is User Login, the operator is ==, and the value is XELSYSADM.
A nested rule: If one rule must be placed inside another rule for logic purposes, the internal rule is known as a nested rule. In Figure 5-2, a Rule to Prevent Solaris Access is nested in a Rule for Solaris.
An operation: When a rule contains multiple rule elements or nested rules, an operation shows the relationship among the components. In Figure 5-2, if the AND operation is selected, the User Login==XELSYSADM rule element and the Rule to Prevent Solaris Access nested rule must both be true for the rule to be successful.
Table 5-3 describes the fields of the Rule Designer form.
Table 5-3 Fields of the Rule Designer Form
| Field Name | Description |
|---|---|
|
Name |
The rule's name. |
|
AND/OR |
These options specify the operation for the rule. To stipulate that a rule is successful only when all the outer rule elements and nested rules are true, select AND. To indicate that a rule is successful if any of its outer rule elements or nested rules are TRUE, select OR. Important: These options do not reflect the operations for rule elements that are contained within nested rules. In Figure 5-2, the AND operation applies to the |
|
Type |
The rule's classification status. A rule can belong to one of four types:
|
|
Sub-Type |
A rule of type Process Determination, Task Assignment, or Prepopulate can be categorized into one of four subtypes:
For Task Assignment or Prepopulate rule types, the approval and standard approval items are not displayed in the Sub-Type box. The Sub-Type box is grayed out for the General rule type. |
|
Object |
The resource object to which this rule is assigned. |
|
All Objects |
If selected, the rule can be assigned to all resource objects. |
|
Process |
The process to which this rule is assigned. |
|
All Processes |
If selected, the rule can be assigned to all processes. |
|
Description |
Explanatory information about the rule. |
To create a rule:
Note:
In the following procedure, note that the options do not apply to rule elements within nested rules. For example, in Figure 5-2 the AND operation applies to theUser Login==XELSYSADM rule element and the Rule to Prevent Solaris Access nested rule. But this operation has no effect on the Object Name != Solaris rule element in the Rule to Prevent Solaris Access rule.Open the Rule Designer form.
In the Name field, enter the name of the rule.
To stipulate that a rule is successful only when all of its rule elements or nested rules are true, select the AND option.
To indicate that a rule is successful if any of its rule elements or nested rules are true, select the OR option.
Click the Type box, and in the custom menu select the classification status (General, Process Determination, Task Assignment, or Prepopulate) to associate with the rule.
For Process Determination, click Sub-Type and select the classification status (Organizational Provisioning, User Provisioning, Approval, or Standard Approval) to associate with the rule.
For Task Assignment or Prepopulate, click Sub-Type and select the classification status (Organization Provisioning or User Provisioning) to associate with the rule.
If you select General from the Type box, go to Step 7.
To associate the rule with a single resource object, double-click the Object lookup field, and in the Lookup dialog box select a resource object.
If you want the rule to be available to all resource objects, select the All Objects option.
To assign a rule to one process, double-click the Process lookup field, and from the Lookup dialog box, select the process to associate with the rule.
Note:
The only processes that are displayed in this Lookup window are the ones that are associated with the resource object you selected in Step 5.If you want the rule to be available to all processes, select the All Processes option.
Note:
If you select a resource object in Step 5 by selecting the All Processes option, then this rule is available to every process that is associated with the selected resource object.In the Description field, enter explanatory information about the rule.
Click Save.
The Rule Designer form contains the following tabs:
Rule Elements tab
Usage tab
Each of these tabs is discussed in the following sections.
From this tab, you can create and manage elements and nested rules for a rule. For example, in Figure 5-3, the Rule for Solaris contains the User Login==XELSYSADM rule element. It also has a nested Rule to Prevent Solaris Access. Figure 5-3 displays the Rule Elements tab of the Rule Designer form.
Figure 5-3 Rule Elements Tab of the Rule Designer Form
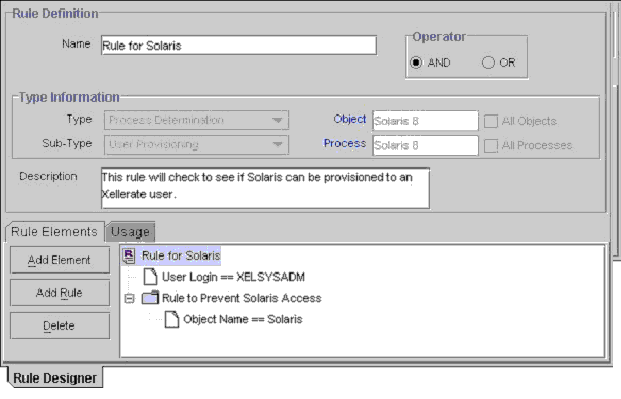
The rule in Figure 5-3 can be applied to a provisioning process for the Solaris resource object. After this resource object is assigned to a request, the rule is triggered. If the target user's login is XELSYSADM, and the name of the resource object is Solaris, the Solaris resource object is provisioned to the user. Otherwise, the user cannot access Solaris.
When a rule element or nested rule is no longer valid, remove it from the rule.
The following procedures describe how to:
Add a rule element to a rule
Add a nested rule to a rule
Remove a rule element or nested rule from a rule
Adding a Rule Element to a Rule
To add a rule element to a rule:
Click Add Element.
The Edit Rule Element dialog box is displayed.
The custom menus in the boxes on the Edit Rule Element dialog box reflect the items in the Type and Sub-Type boxes of the Rule Designer form.
Table 5-4 describes the data fields in the Edit Rule Element dialog box.
Table 5-4 Fields of the Edit Rule Element Dialog Box
| Name | Description |
|---|---|
|
Attribute Source |
From this box, select the source of the attribute. For example, if the attribute you wish to select is Object Name, the attribute source to select would be Object Information. |
|
User-Defined Form |
This field displays the user-created form that is associated with the attribute source that is displayed in the adjacent box. Note: If Object Data or Process Data are not displayed in the Attribute Source box, the User-Defined Form field will be empty. |
|
Attribute |
From this box, select the attribute for the rule. |
|
Operation |
From this box, select the relationship between the attribute and the attribute value (== or !=) |
|
Attribute Value |
In this field, enter the value for the attribute. Note: The attribute's value is case-sensitive. |
Set the parameters for the rule you are creating, as shown in Figure 5-4.
In this example, if the Login ID of the target user is XELSYSADM, the rule element is true. Otherwise, it is false.
See Also:
For more information about the parameters, see "Rule Elements Tab".From the Toolbar of the Edit Rule Element dialog box, click Save, and then click Close.
The rule element is displayed in the Rule Elements tab of the Rule Designer form.
From the main screen's toolbar, click Save.
The rule element is added to the rule.
Adding a Nested Rule to a Rule
To nest a rule within a rule:
Note:
In the following procedure, only rules of the same type and subtype as the parent rule are displayed in the Select Rule window.Click Add Rule.
The Select Rule dialog box is displayed.
Select a nested rule and click Save.
Click Close.
The nested rule is displayed in the Rule Elements tab of the Rule Designer form.
From the main screen's Toolbar, click Save.
The nested rule is added to the rule.
Removing a Rule Element or Nested Rule from a Rule
To remove a rule element or a nested rule:
Select the rule element or nested rule that you want to remove.
Click Delete.
The rule element or nested rule is removed from the rule.
This tab is displayed on the Rule Designer form. The information in the Usage tab reflects the rule's classification type. For example, if a rule type is prepopulate, the user-created field that this rule is applied to is displayed in this tab.
Figure 5-5 shows the Usage tab.
Figure 5-5 Usage Tab of the Rule Designer Form
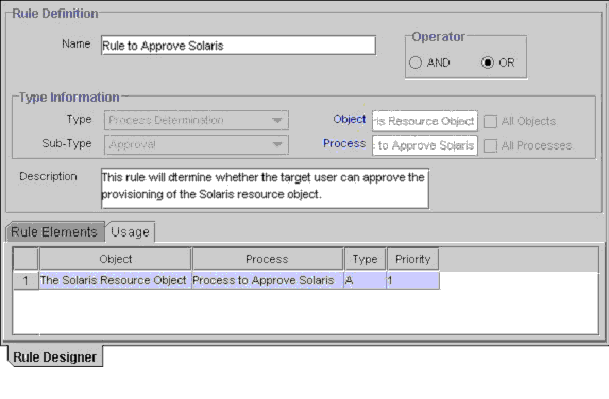
This tab displays the following items:
The password policy, resource object, process, process task, auto-group membership criteria, user group, Oracle Identity Manager form field, and prepopulate adapter associated with a rule.
A one-letter code, signifying the rule's classification type: A=Approval and P=Provisioning.
This code is displayed for process determination rules only.
The rule's priority number.
In Figure 5-5, the Rule to Approve Solaris definition was assigned to the Solaris Resource Object and the Process to Approve Solaris. Because this is an approval rule, its classification type is A. The priority of this rule is 1, indicating that it was the first approval rule that Oracle Identity Manager was scheduled to evaluate, after the corresponding resource object was assigned to the request.
The Rule Designer Table, as shown in Figure 5-6, displays all available rules defined in the Rule Designer form.
Table 5-5 shows the information displayed in the Rule Designer Table.
Table 5-5 Information in the Rule Designer Table
| Field Name | Description |
|---|---|
|
Rule Name |
The name of the rule. |
|
Rule Type |
A rule can belong to one of four types:
|
|
Rule Sub-Type |
A rule of type Process Determination, Task Assignment, or Pre-Populate can be categorized into one of four sub-types:
|
|
Rule Operator |
The relationship between the attribute and the attribute value represented by the == or != operators. |
|
Description |
Explanatory information about the rule. |
|
Last Updated |
The date when the rule was last updated. |
The Resource Objects form is in the Resource Management folder. You use this form to create and manage the resource objects for the Oracle Identity Manager resources that you want to provision for organizations or users. Resource object definitions are templates for provisioning the resource. However, the approval and provisioning of the resource depends on the design of the approval and provisioning processes that you link to the resource object.
See Also:
"Administrative Queues Form" for more information about requests and their relationship with resource objectsTable 5-6 describes the data fields of the Resource Objects form.
Table 5-6 Fields of the Resource Objects Form
| Field Name | Description |
|---|---|
|
Name |
The resource object's name. |
|
Table Name |
The name of the resource object form that is associated with this resource. (This is actually the name of the table that represents the form.) |
|
Order For User/Order For Organization |
Options that determine whether or not the resource object can be requested for users or organizations. To request the resource object for a user, select Order For User. To request the resource object for an organization, select Order For Organization. |
|
Auto Pre-Populate |
Option that determines whether or not a custom form will be populated by Oracle Identity Manager or a user. This applies to the following kinds of forms:
If the Auto Pre-Populate check box is selected, after the associated custom form is displayed, the fields with pre-populate adapters are populated with data. If this check box is deselected, a user must populate the fields by clicking the Pre-Populate button on the toolbar. Note: This setting does not control the triggering of the pre-populate adapter. It determines if the contents resulting from the execution of the adapter are displayed in the associated field because of Oracle Identity Manager or a user. For more information about prepopulate adapters, see Oracle Identity Manager Tools Reference. Note: This check box is only relevant if you have created a form that is to be associated with the resource object. |
|
Type |
The resource object's classification status. A resource object can belong to one of three types:
|
|
Allow Multiple |
Designates if the resource is provisioned more than once to a user or organization. If it is selected, the resource object can be provisioned more than once for each user or organization. |
|
Auto Save |
By selecting this check box, Oracle Identity Manager saves the data in any resource-specific form that was created by using the Form Designer form without first displaying the form. If you select this check box, you must supply system data, a rule generator adapter, or an entity adapter to populate the form with the required data. The user will not have access to the form if you do not populate the form with the required data. Note: This check box is only relevant if you have created a form for the provisioning of the resource object. |
|
Self Request Allowed |
By selecting this check box, users as well as the system administrator can request the resource object for themselves. Note: This functionality only applies to the Oracle Identity Manager Design Console. It is not applicable to the Oracle Identity Manager Administrative and User Console. |
|
Allow All |
By selecting this check box, the resource object can be requested for all Oracle users. This setting takes precedence over whether or not the organization to which a user belongs has allowed the resource that can be requested for its users. |
|
Auto Launch |
By default, this check box is checked at the time of object creation. Oracle Identity Manager automatically initiates the provisioning process when the resource's approval process is in Completed status. Oracle Identity Manager automatically makes all resource objects set to Auto Launch, even though this check box is cleared. |
|
Provision by Object Admin Only |
This check box determines who can provision this resource, either by using direct provisioning or by manually initiating the provisioning process when the Auto Launch check box is deselected. If this check box is selected, only users who are members of the groups listed on the Object Administrators tab will be able to provision this resource object (either directly or by manually initiating the provisioning process from the request). If this check box is deselected, no restrictions are placed on who can directly provision this resource. |
|
Sequence Recon |
If you select this check box, then reconciliation events are processed in the sequence in which they are created. The application of this feature can be illustrated by the following example: Suppose there are two reconciliation events for the OIM User resource object for user
The second reconciliation event (E2) data is as follows:
Between the first and second events, the first name and last name of the user was changed. During trusted source reconciliation, if events are processed in the order in which they are created, then this change in first and last names is correctly reconciled into Oracle Identity Manager. However, if the second event is processed before the first one, then data in the target system does not match data in Oracle Identity Manager at the end of the reconciliation run. This inconsistency will be reflected in the auditing tables, and will remain until another event from the trusted source is created for this user. If you enable the Sequence Recon option, then you can ensure that events for the same entity (for example, same user or same process form) are processed in the order in which they were created. |
|
Trusted Source |
You can select this check box if you want to use the resource object for trusted user reconciliation. By default, this check box is not selected. It is selected by default only for the Xellerate User resource object. |
To create a resource object:
Open the Resource Objects form.
In the Name field, enter the name of the resource object.
If required, you can attach a resource form to the resource object. To do this, double-click the Table Name lookup field. From the Lookup dialog box, select the table that represents the form that will be associated with the resource object.
To request the resource object for a user, select Order For User.
To request the resource object for an organization, select Order For Organization.
Note:
A resource object can be requested for either one user or one organization.If a custom form is to be associated with the resource object, this form contains fields that have prepopulate adapters attached to them, and you want these fields to be populated automatically by Oracle Identity Manager, select the Auto Pre-Populate option.
If the fields of this form are to be populated manually (by a user clicking the Pre-Populate button on the Toolbar), clear the Auto Pre-Populate option.
Note:
If the resource object has no custom form associated with it, or this form's fields have no prepopulate adapters attached to them, deselect the Auto Pre-Populate check box. For more information about prepopulate adapters, see Oracle Identity Manager Tools Reference.Double-click the Type lookup field.
From the Lookup dialog box that is displayed, select the classification status (Application, Generic, or System) to associate with the resource object.
If you want multiple instances of the resource object to be requested for a user or an organization, select the Allow Multiple option. Otherwise, go to Step 8.
When you want Oracle Identity Manager to save the data in any resource-specific form (created by using the Form Designer form) without first displaying the form, select the Auto Save option.
Otherwise, proceed to Step 9.
Note:
If you select this check box, you must supply system data, a rule generator adapter, or an entity adapter to populate the form with the required data because the user will be unable to access the form.Select this check box only if you have created a form for provisioning the resource object.
If you want to be able to request the resource object for yourself, select the Self Request Allowed option. Otherwise, go to Step 10.
To provision the resource object for all users, regardless of whether the organization to which the user belongs has the resource object assigned to it, select the Allow All check box. Otherwise, go to Step 11.
If you want to use the resource object for trusted source user reconciliation, you must select the Trusted Source option. Otherwise, go to Step 12.
Note:
You must deselect the Self Request Allowed and Allow All check boxes to ensure that the resource object is not available for provisioning requests and resource profiles.If you want Oracle Identity Manager to automatically initiate the provisioning process when the resource object's approval process has achieved a status of Completed, select the Auto Launch option. Otherwise, go to Step 13.
Caution:
By default, Oracle Identity Manager sets all resource objects to Auto Launch, even though this check box is not selected.To restrict the user groups that can provision this resource object to groups that are displayed in the Object Authorizers tab of the Resource Objects form, select the Provision by Object Admin Only option. This applies to resource objects that are provisioned directly or by assignment to a request. Otherwise, go to Step 14.
Click Save.
The resource object is created.
When you start the Resource Objects form and create a resource object, the tabs of this form become functional.
The Resource Objects form contains the following tabs:
From this tab, you can select resource objects that Oracle Identity Manager must provision before provisioning the current resource object. If Oracle Identity Manager can provision the current resource object without first provisioning a resource object that is displayed on the Depends On tab, you must remove that resource object from the tab.
The following topics are related to the Depends On tab:
Selecting a resource object on which the current resource object is dependent
Removing the dependent resource object
Selecting a Dependent Resource Object
To select a dependent resource object:
Click Assign.
The Assignment dialog box is displayed.
Select the resource object, and assign it to the request.
Click OK.
The dependent resource object is selected.
Removing a Dependent Resource Object
To remove a dependent resource object:
Select the dependent resource object that you want to remove.
Click Delete.
The resource object is removed from the Depends On tab.
Use this tab to specify user groups that are the object authorizers for this resource. You can select users who are members of the Object Authorizers groups as targets for task assignments.
Each user group on the Object Authorizers tab has a priority number. When a task assignment target is Object Authorizer user with highest priority, Oracle Identity Manager uses the priority number to determine which user to assign to a task. The priority number can also be referenced when a task assigned to a group is escalated due to lack of action. You can increase or decrease the priority number for any user group on this tab.
For example, suppose that you configure members of the SYSTEM ADMINISTRATORS user groups to be object authorizers. Also suppose that a process task associated with this resource object has a task assignment rule attached to it, and the assignment criteria is Object Authorizer User with Highest Priority. The first user authorized to complete this process task is the user with the highest priority who belongs to the SYSTEM ADMINISTRATORS user group because its priority number is 1. If the user does not complete the process task in a user-specified time, Oracle Identity Manager reassigns the task to the user with the next highest priority in the SYSTEM ADMINISTRATORS user group.
See Also:
"Rule Designer Form" and "Assignment Tab of the Editing Task Window" for more information about task assignment rules and process tasksAssigning a User Group to a Resource Object
To assign a user group to a resource object:
Click Assign.
The Assignment dialog box is displayed.
Select a user group, and assign it to the resource object.
Click OK.
The user group is selected.
Removing a User Group from a Resource Object
To remove a user group from a resource object:
Select the desired user group.
Click Delete.
The user group is removed from the Object Authorizers tab.
Changing the Priority Number of a User Group
To change a user group's priority number:
Select the user group whose priority number you want to change.
To increase the selected user group's priority number by one, click Increase.
To decrease this user group's priority by one, click Decrease.
To increase or decrease a user group's priority number by more than one, click the appropriate button repeatedly. For example, to increase the priority number of a user group by two, click the Increase button twice.
Click Save.
The user group's priority number is changed to the value you selected.
A request is a mechanism for provisioning resources to users or organizations. A user interacts with a request to approve the provisioning of resources to target users or organizations. Each request must have a resource object assigned to it. Each resource object consists of one or more provisioning processes and one or more approval process.
A resource object is a template for the resource that is provisioned to users or organizations. This template can be linked to multiple approval and provisioning processes. Oracle Identity Manager uses process determination rules to select an approval and provisioning process when a resource is requested or directly provisioned.
Process determination rules provide the following criteria:
Which approval and provisioning process to select when a resource is requested
Which provisioning process to select when a resource is provisioned directly
Each approval process and provisioning process has a process determination rule. Each rule and process combination has a priority number that indicates the order in which Oracle Identity Manager will evaluate it.
If the condition of a rule is false, then Oracle Identity Manager evaluates the rule with the next highest priority. If a rule is true, then Oracle Identity Manager executes the process associated with it. For example, when a resource is requested or provisioned directly, Oracle Identity Manager evaluates a Rule to See if Solaris is Needed and Rule to Check Provisioning of Solaris for IT Dept. Both rules have the highest priority. If the conditions of these rules are true, then Oracle Identity Manager executes the processes associated with them—in this example, these are the Check if Solaris is Needed approval process and the Provision Solaris for IT Dept. provisioning process.
As a variation of the example, if the resource is requested or provisioned directly and the Rule to Check Provisioning of Solaris for IT Dept. rule is false, then Oracle Identity Manager evaluates the Rule to Check Provisioning of Solaris for Developers rule. If this rule is true, Oracle Identity Manager executes the Provision Solaris for Devel. provisioning process associated with that rule.
Adding a Process Determination Rule to a Resource Object
To add a process determination rule to a resource object:
Click Add in either the Approval Processes or Provisioning Processes region, depending on the rule or process combination you intend to create.
From the row that is displayed, double-click the Rules lookup field.
From the Lookup dialog box, select a rule, and assign it to the resource object (only rules of Process Determination type are available for selection).
Click OK.
In the adjacent column, double-click the Processes lookup field.
From the Lookup dialog box, select a process, and assign it to the rule.
Click OK.
Enter a numeric value in the Priority field.
This determines the order in which Oracle Identity Manager evaluates the rule and process combination.
Click Save.
The rule and process combination is added to the resource object.
Remove a Process Determination Rule From a Resource Object
To remove a process determination rule from a resource object:
Select a rule and process combination.
Click Delete.
The rule and process combination is removed from the resource object.
A resource object's provisioning process contains tasks that must be completed automatically. When this occurs, you must assign an event handler or an adapter to the resource object. An event handler is a software routine that provides the processing of this specialized information. An adapter is a specialized type of event handler that generates Java code, which enables Oracle Identity Manager to communicate and interact with external resources.
When an event handler or adapter that is assigned to a resource object that is no longer valid, you must remove it from the resource object.
For this example, the adpAUTOMATEPROVISIONINGPROCESS adapter was assigned to the Solaris resource object. Once this resource object is assigned to a request, Oracle Identity Manager triggers the adapter, and the associated provisioning process is executed automatically.
Assigning an Event Handler or Adapter to a Resource Object
To assign an event handler to an adapter or a resource object:
Click Assign.
The Assignment dialog box is displayed.
Select an event handler, and assign it to the resource object.
Click OK.
The event handler is assigned to the resource object.
Remove an Event Handler or Adapter from a Resource Object
To remove an event handler or adapter from a resource object, perform the following steps:
Select an event handler.
Click Delete.
The event handler is removed from the resource object.
The Resource Objects form in the Design Console is enhanced and now includes a new resource attribute named Resource Audit Objectives. This resource attribute helps you link resources to regulatory mandates.
A new lookup is defined for the values of the Resource Audit Objectives resource attribute. The predefined values in the Resource Audit Objectives list are:
SOX (Hosts Financially Significant Information)
HIPAA (Hosts Private Healthcare Information)
GLB (Hosts Non-Public Information)
Requires Quarterly Review
Requires Annual Review
You can extend this list by editing the Lookups.Resource Audit Objective.Type lookup by using the Lookup Definition Form in the Design Console.
A new Resource Audit Objectives tab is now on the Resource Profile form in the Design console, which lets you select the value of this attribute.
You use this tab to set provisioning status for a resource object. A provisioning status indicates the status of a resource object throughout its lifecycle, until it is provisioned to the target user or organization. You can view the provisioning status of a resource object from the Status region of the Currently Provisioned tab.
Every provisioning status of a resource object is associated with a task status for the relevant provisioning process. Oracle Identity Manager selects the provisioning process when the resource object is assigned to a request. For example, if the Provision for Developers process is selected, and a task in this process achieves Completed status, the corresponding status of the resource object can be set to Provisioned. This way, you can see how the resource object relates to the provisioning process, quickly and easily.
A resource object has the following predefined statuses:
Waiting: This resource object depends on other resource objects that have not yet been provisioned.
Revoked: The resources represented by the resource object are provisioned to target users or organizations that have been permanently deprovisioned from using the resources.
Ready: This resource object either does not depend on any other resource objects, or all resource objects upon which this resource object depends are provisioned.
After a resource is assigned to a request and the resource object's status is Ready, Oracle Access Manager evaluates the process determination rules to determine the approval and provisioning processes. When this happens, the status of the resource object changes to Provisioning.
Provisioning: The resource object is assigned to a request, and an approval process and a provisioning process were selected.
Provisioned: The resources represented by the resource object are provisioned to the target users or organizations.
Provide Information: Additional information is required before the resources represented by the resource object can be provisioned to the target users or organizations.
None: This status does not represent the provisioning status of the resource object. Rather, it signifies that a task that belongs to the provisioning process that Oracle Identity Manager selects has no effect on the status of the resource object.
Enabled: The resources represented by the resource object are provisioned to the target users or organizations, and these users or organizations have access to the resources.
Disabled: The resources represented by the resource object are provisioned to the target users or organizations, but these users or organizations have temporarily lost access to the resources.
Each provisioning status has a corresponding Launch Dependent check box. If the check box is selected and the resource object achieves that provisioning status, Oracle Identity Manager enables dependent resource objects to start their own provisioning processes.
For example, suppose that the Exchange resource object has the Launch Dependent check box selected for the Provisioned and Enabled provisioning statuses. Once the provisioning status of this resource object changes to Provisioned and Enabled, Oracle Identity Manager verifies that there are other resource objects upon which the Exchange resource object depends. If there are, Oracle Identity Manager starts the approval and provisioning processes of the dependent objects. Then, Oracle Identity Manager selects an approval and provisioning process for the Exchange.
You might want to add additional provisioning statuses to a resource object to reflect the various task statuses of a provisioning process. For example, when the status of a task that belongs to a provisioning process is Rejected, you might want to set the corresponding provisioning status of the resource object to Revoked.
Similarly, when an existing provisioning status is no longer valid, you must remove it from the resource object.
The following sections discuss how to add a provisioning status to a resource object and remove a provisioning status from a resource object.
Adding a Provisioning Status to a Resource Object
To add a provisioning status to a resource object:
Click Add.
Add a provisioning status in the Status field.
When you want other, dependent resource objects to launch their own approval and provisioning processes once the resource object achieves the provisioning status you are adding, select the Launch Dependent check box. Otherwise, go to Step 4.
Click Save.
The provisioning status is added to the resource object.
Removing a Provisioning Status from a Resource Object
The following procedure describes removing a provisioning status from a resource object:
Select a provisioning status.
Click Delete.
The provisioning status is removed from the resource object.
This tab is used to select user groups that can view, modify, and delete the current resource object.
When the Write check box is selected, the corresponding user group can modify the current resource object. When the Delete check box is selected, the associated user group can delete the current resource object.
For example, the SYSTEM ADMINISTRATORS user group can view, modify, and delete the Solaris resource object. The OPERATORS user group can only view and modify this resource object; its Delete check box is deselected.
The following sections describe how to assign a user group to a resource object, and remove a user group from a resource object.
Assigning a User Group to a Resource Object
To assign a user group to a resource object:
Click Assign.
The Assignment dialog box is displayed.
Select the user group, and assign it to the resource object.
Click OK.
The user group is displayed in the Administrators tab. By default, all members of this group can view the active record.
If you want this user group to be able to modify the current resource object, select the corresponding Write check box.
Otherwise, go to Step 5.
If you want this user group to be able to delete the current resource object, select the associated Delete check box.
Otherwise, go to Step 6.
Click Save.
The user group is assigned to the resource object.
Removing a User Group from a Resource Object
To remove a user group from a resource object:
Highlight the user group that you want to remove.
Click Delete.
The user group is removed from the resource object.
If a resource object is of type Application, and you want to provision the resource object to a user or organization, you might want that user or organization to meet password criteria before accessing the resource object. This password criteria is created and managed in the form of password policies. These policies are created by using the Password Policies form.
Because the resource object definition is only a template for governing how a resource is to be provisioned, Oracle Identity Manager must be able to make determinations about how to provision the resource based on actual conditions and rules. These conditions might not be known until the resource is actually requested. Therefore, rules must be linked to the various processes and password policies associated with a resource. This enables Oracle Identity Manager to decide which ones to invoke in any given context.
Oracle Identity Manager determines which password policy to apply to the resource when creating or updating a particular user's account. This is done by evaluating the password policy rules of the resource and applying the criteria of the policy associated with the first rule that is satisfied. Each rule has a priority number, which indicates the order in which Oracle Identity Manager will evaluate it.
For this example, Oracle Identity Manager will trigger the Rule to Prevent Solaris Access rule (because it has the highest priority). If this rule were TRUE, Oracle Identity Manager would apply the criteria of the Restrict Solaris password policy to the password of the account being created or updated.
If the rule is false, Oracle Identity Manager will evaluate the rule by using the next highest priority. If this rule is true, Oracle Identity Manager applies the password policy associated with it to the password of the account being created or updated.
The following sections discuss how to add and remove a password policy rule from a resource object.
Adding a Password Policy Rule to a Resource Object
To add a password policy rule to a resource object:
Click Add.
From the row that is displayed, double-click the Rule lookup field.
From the Lookup dialog box, select a rule, and assign it to the resource object.
Click OK.
In the adjacent column, double-click the Policy lookup field.
From the Lookup dialog box, select an associated password policy, and assign it to the resource object.
Click OK.
Add a numeric value in the Priority field.
This field contains the rule's priority number.
Click Save.
The password policy rule is added to the resource object.
Note:
If the resource type is Order for Organisation, then you cannot attach a password policy to the resource object. The exception to this rule is the Xellerate User resource object. Although this resource object is of Order for Organisation type, password policies can be attached to it.
If two or more rules evaluate to True, then the password policy attached to the rule with the highest priority is applied.
A Default rule is predefined in Oracle Identity Manager. This rule always evaluates to True. If no rules have been created through the Rule Designer, then a password policy can be attached to the Default rule.
Removing a Password Policy Rule from a Resource Object
To remove a password policy from a resource object:
Select a password policy rule.
Click Delete.
The password policy rule is removed from the resource object.
You use this tab to view and access user-defined fields that were created for the Resource Objects form. After a user-defined field is created, it is displayed on this tab and can accept and supply data.
See Also:
See "User Defined Field Definition Form" for instructions about how to create user-defined fields on existing Oracle Identity Manager formsThe Process tab displays all approval and provisioning processes that are associated with the current resource object. The Default check boxes on this tab indicate what approval or provisioning processes are the defaults for the resource.
Note:
You create approval and provisioning processes and associate them with a resource by using the Process Definition form. Each process can then be linked to a process determination rule by using the Process Determination Rules tab of the Resource Object form.For example, suppose that the Solaris resource object has one approval processes assigned to it and one provisioning processes (Provision Solaris for Devel.) associated with it. The Provision Solaris for Devel. has been designated as the default provisioning process for this resource object.
The Object Initial Reconciliation Date field on the Object Reconciliation Tab displays the date when initial reconciliation was performed for the resource.
Note:
The purpose of initial reconciliation is to bring all the user accounts from the target system into Oracle Identity Manager.The date value stored in the Object Initial Reconciliation Date field is used to distinguish between initial reconciliation and subsequent reconciliations events. This date value is used by the two exception reports introduced in release 9.1.0. These exception reports display differences in the entitlements a user must have as compared to what the user actually has in the target system. The differences in entitlements are determined by using reconciliation data, along with other data items. The exception reports return data associated with only those reconciliation events that are created after the date stored in the Object Initial Reconciliation Date field. In addition, exception data is generated only if the Initial Object Reconciliation Date field displays a date value that is in the past. If required, you can enter a date value in this field so that the exception reports are generated.
The Object Reconciliation tab contains two subtabs, Reconciliation Fields and Reconciliation Action Rules.
The Reconciliation Fields tab is used to define the fields on the target resources or trusted sources that are to be reconciled with (for example, mapped to) information in Oracle Identity Manager
The Reconciliation Action Rules tab is used to specify the actions Oracle Identity Manager is to take when particular matching conditions are met.
Reconciliation Fields Tab
This tab is used to define the fields on the target resources or trusted sources that are to be reconciled with (for example, mapped to) information in Oracle Identity Manager. For each field on the target system or trusted source, the following information will be listed:
Name of the field on the target resource or trusted source that is to be reconciled with data in Oracle Identity Manager (for example, targetfield1)
Data type associated with the field (for example, String). Possible values are multi-valued, string, number, date, IT resource
Indicator that designates whether or not this field is required in a reconciliation event
Note:
Oracle Identity Manager will not begin to match provisioning processes, users or organizations to the reconciliation event until all fields are processed on the Reconciliation Data tab of the Reconciliation Manager form.The following is an example of a target system field definition:
TargetField1 [String], Required
In the Reconciliation Fields tab, you can perform the following:
Add a reconciliation field
The following procedure adds fields from the target system or trusted source to the list of fields that are to be reconciled with information in Oracle Identity Manager. For a trusted source, this must be the user resource definition.
Note:
Before Oracle Identity Manager can successfully perform reconciliation with an external target resource or target source, the fields you have defined on this tab must be mapped to the appropriate Oracle Identity Manager fields by using the Field Mappings tab of the resource's default provisioning process.To add a reconciliation field:
Click Add Field.
The Add Reconciliation Field dialog box is displayed.
Enter the name of the field on the target resource or trusted source in the Field Name field.
This is the name that will reference the target resource or trusted source field in Oracle Identity Manager.
Select one of the following values from the menu in the Field Type field:
Multi-Valued
This is meant for use with fields that contain one or more component fields.
String
String
Date
IT resource
During reconciliation event creation, the value this field receives must be the same as the name of an IT resource defined in Oracle Identity Manager.
Select the Required check box.
If selected, the reconciliation field must be processed on the Reconciliation Data tab of the Reconciliation Manager form before Oracle Identity Manager will begin matching a provisioning process, user, or organization to the reconciliation event. If this check box is not selected, the inability to process this field in a reconciliation event will not prevent matching from occurring.
Click Save.
The field will be available for mapping in the resource's default provisioning process.
Delete a reconciliation field
Use the following procedure to remove a target system field from the list of fields that are to be reconciled with information in Oracle Identity Manager. For a trusted source, this must be the user resource definition.
To delete a reconciliation field:
Select the field you wish to remove.
Click Delete Field.
The selected field will be removed from the list of fields with which Oracle Identity Manager reconciles data on the target system (this will have no effect on the data in the target system itself).
Reconciliation Action Rules Tab
By using this tab, you can specify the actions that Oracle Identity Manager will perform when some matches within reconciliation event records are encountered. Each record in this tab is a combination of:
The matching condition criteria
The action to be performed
The conditions and actions from which you can select are predefined. Depending on the matching conditions, certain actions might not be applicable. A complete list of the available options is provided in Table 5-7.
Table 5-7 Rule Conditions and Possible Rule Actions
| Rule Condition | Possible Rule Actions |
|---|---|
|
No matches found |
None Assign to Administrator with Least Load Assign to Authorizer with Highest Priority Assign to Authorizer with Least Load Assign to User Assign to Group Create User (only available with the trusted source) |
|
One Process Match Found |
None Assign to Administrator with Least Load Assign to Authorizer with Highest Priority Assign to Authorizer with Least Load Assign to User Assign to Group Establish Link |
|
Multiple Process Matches Found |
None Assign to Administrator with Least Load Assign to Authorizer with Highest Priority Assign to Authorizer with Least Load Assign to User Assign to Group |
|
One Entity Match Found |
None Assign to Administrator with Least Load Assign to Authorizer with Highest Priority Assign to Authorizer with Least Load Assign to User Assign to Group Establish Link |
|
Multiple Entity Matches Found |
None Assign to Administrator with Least Load Assign to Authorizer with Highest Priority Assign to Authorizer with Least Load Assign to User Assign to Group |
See Also:
"Assignment Tab of the Editing Task Window" for a description of the classification types for the users and groups listed in the preceding tableAdding a Reconciliation Action Rule
To add a reconciliation action rule:
Click Add Field.
The Add a new Action Rule dialog box is displayed.
Select the desired value from the Rule Condition menu.
This is the matching condition that will cause the associated action to be executed. Each match condition can only be assigned to a single rule action.
Select a value from the Rule Action menu.
This is the action that will be executed if the matching condition is met.
Click Save, and close the Add a new Action Rule dialog box.
Deleting a Reconciliation Action Rule
To delete a reconciliation action rule:
Select the matching action combination to delete.
Click Delete.
The reconciliation action rule will be removed and the action associated with its condition will not be executed automatically.
In earlier releases, you could set up only the Xellerate User resource object as a trusted source to reconcile identities. Now, you can do this by creating the reconciliation fields, reconciliation action rules, field mappings, and matching roles for the Xellerate User resource object and the process definition.
If there are two trusted sources from which you want to reconcile identities to create OIM Users, then you are not able to configure a single resource object (Xellerate User) for both the trusted sources. Even if you create reconciliation fields for both the trusted sources in the Xellerate User resource object, you cannot create the corresponding reconciliation field mappings in the Xellerate User process definition.
From release 9.1.0 onward, you can configure resource objects other than Xellerate User as trusted sources for identity reconciliation. You can do this by selecting the Trusted Source check box in the Resource Objects form while creating a resource object.
For a resource object to which the Trusted Source flag is attached, you can create multiple reconciliation fields to denote the target system fields. You can also configure the reconciliation action rule in which if there are no process matches found, then either a user is created or the data is sent to the administrator or authorizer for identity creation. If a process match is found, then the link is established.
When defining provisioning process for trusted source resources, do not attach user-defined forms. For these provisioning processes, reconciliation field mappings can be created between reconciliation fields defined on the resource and OIM User attributes.
Note:
If the resource object is for target resource reconciliation, then the mapping is between the reconciliation fields and process data fields.Do not use any resource objects that are defined as a trusted source for provisioning activities. These resources are meant to be used only for OIM Users' reconciliation.
Another addition in this release is the attribute authoritative sources feature. This means sources are trusted for only attributes of the identities and not the identities themselves. You can configure attribute authoritative source reconciliation by creating appropriate reconciliation action rules. If no process match is found, then it is assigned to the administrator. This ensures that a user is not created by mistake even if there are no matches found. If a process match is found, then the reconciliation action rule will establish a link.
The following sections discuss two use cases in which you can implement multiple trusted source reconciliation.
Note:
At some places in this document:- Multiple trusted source reconciliation has been referred to as MTS.
- The terms fields and attributes have been used interchangeably.
Note:
To determine whether or not your connector is MTS-compatible, see connector-specific documentation.The following sections discuss scenarios in which you can implement multiple trusted source reconciliation by using MTS-compatible connectors:
Configuring MTS-Compatible Connectors for Trusted Source Reconciliation by User Type
In this context, user type refers to the type of users whose records you want to reconcile. Examples of user types are Employee and Customer.
To implement trusted source reconciliation by user type, perform the procedure to implement trusted source reconciliation while deploying the connectors of each target system that you want to configure as a trusted source.
During reconciliation, all the target system records of the specified user types are reconciled. If the target systems contain multiple user types, then you can use the Limited Reconciliation feature to specify the user type for which records must be reconciled from each target system.
Configuring MTS-Compatible Connectors for Trusted Source Reconciliation of Specific OIM User Attributes
You might want to configure trusted source reconciliation for specific OIM User attributes from multiple target systems. The procedure to implement this is described with the help of the following sample scenario:
You want to reconcile identities from one target system, for example TS1, and specific attributes of these identities (for example attr1, attr2, and attr3) from another target system, for example TS2. This means that TS1 is the trusted source for the identities, and TS2 is the trusted source for specific attributes of those identities and not the identities themselves. TS1 must provide all the mandatory OIM User attributes for the successful creation of an OIM User. TS2 will provide only those OIM User attributes (either a mandatory OIM User attribute or a non-mandatory one) for which TS2 is the trusted source. If you reconcile a mandatory OIM User attribute from TS2, then the value of this attribute overwrites the value contained in this attribute after the OIM User is created from TS1. If you want to reconcile only non-mandatory OIM User attributes from TS2, then you can choose not to reconcile these attributes from TS1 during OIM User creation.
For the TS1 connector:
Perform all the steps required to deploy the TS1 connector and configure it for trusted source reconciliation.
See Also:
The documentation for the connector you are deploying for information about the procedure to configure trusted source reconciliationIn the Reconciliation Fields tab on the Object Reconciliation page, delete all the TS1 attributes that you want to reconcile from TS2 (in this case attr1, attr2, and attr3).
In the Reconciliation Field Mappings tab on the Process Definition page, delete all the mappings other than the ones you want to retain.
Instead of deleting reconciliation fields, you can remove the reconciliation field mappings of those fields for which you do not want to reconcile the values into the OIM User created through reconciliation.
In the Reconciliation Action Rules tab on the Object Reconciliation page, ensure that the following rule condition and action mappings exist:
Rule Condition: No Matches Found
Action: Create User
For the TS2 connector:
Perform all the steps required to deploy the TS2 connector and configure it for trusted source reconciliation.
See Also:
The documentation for the connector you are deploying for information about the procedure to configure trusted source reconciliationIn the Reconciliation Fields tab on the Object Reconciliation page, delete all the TS2 attributes other than attr1, attr2, and attr3. In addition, retain the attributes that you want to use to match OIM Users with existing TS2 accounts. This means that you retain only those attributes that will be used for reconciliation rule evaluation. For example, you might want to use the username attribute in Oracle Identity Manager to match the value of the first name attribute in TS1.
In the Reconciliation Field Mappings tab on the Process Definition page, delete all the mappings other than the ones you want to retain.
Instead of deleting reconciliation fields, you can also choose to just remove the reconciliation field mappings of those fields for which you do not want to reconcile the values into the OIM User created through reconciliation.
In the Reconciliation Action Rules tab on the Object Reconciliation page, create rule conditions and action mappings. One of these rule condition-action mappings must be the following:
Rule Condition: No Matches Found
Action: Anything other than Create User
Note:
To determine whether or not your connector is MTS-compatible, see connector-specific documentation.For a connector that is not MTS-compatible, the following prerequisites must be addressed before you can use the connector in a multiple trusted source reconciliation setup:
i. Only one of the trusted source resource objects can be Xellerate User. In your operating environment, if the Xellerate User resource object is already in use by a connector for trusted source reconciliation, then for the trusted source connector that you want to configure, you must create a new resource object and process definition.
ii. The scheduled task of the connector must have an attribute that accepts the name of the resource object used for trusted source user reconciliation as its value.
The following sections discuss scenarios in which you can implement multiple trusted source reconciliation by using non-MTS-compatible connectors:
Configuring Non-MTS-Compatible Connectors for Trusted Source Reconciliation by User Type
Configuring Non-MTS-Connectors for Trusted Source Reconciliation of Specific OIM User Attributes
Configuring Non-MTS-Compatible Connectors for Trusted Source Reconciliation by User Type
In this context, user type refers to the type of users whose records you want to reconcile. Examples of user types are Contractor, Employee, and Customer.
You use Microsoft Active Directory and Oracle e-Business Suite as trusted sources in your operating environment. Active Directory is used to store information about identities that belong to the Contractor user type. Oracle e-Business Suite is used to store information about identities that belong to the Customer and Employee user type. You want to reconcile Contractor records from Active Directory and Employee records from Oracle e-Business Suite. To do this, perform the following:
For Active Directory:
Perform all the steps required to deploy the Active Directory connector and configure it for trusted source reconciliation.
See Also:
The documentation for the connector you are deploying for information about the procedure to configure trusted source reconciliationWhen you import the connector XML file for trusted source reconciliation, information specific to Active Directory is added in the Xellerate User resource object and process definition.
On the Resource Object tab, create the ActDir resource object for trusted source reconciliation with Active Directory.
Note:
You can assign any name to the resource object. This procedure is based on the use ofActDir as the name assigned to the resource object.
For detailed information about the procedure to create a resource object, see "Resource Objects Form".
While creating the resource object:
Select the Trusted Source check box on the Resource Object tab.
On the Object Reconciliation>>Reconciliation Fields tab, see Xellerate User resource object and add the Active Directory-specific fields that you want to reconcile in ActDir. All the mandatory OIM User fields must be covered by the fields that you add on this tab.
On the Object Reconciliation>>Reconciliation Action Rules tab, create rule conditions and action mappings. One of these rule condition-action mappings must be the following:
Rule Condition: No Matches Found
Action: Create User
Delete the fields specific to Active Directory and the corresponding rules from the Xellerate User resource object.
Create the ActDir process definition in the Process Definition form.
For detailed information about the procedure to create a process definition, see "Process Definition Form". Based on the reconciliation field mappings in the Xellerate User process definition, on the Reconciliation Field Mappings tab, add the reconciliation field mappings for the ActDir process definition.
Delete the Active Directory-specific field mappings in the Xellerate User resource object.
In the Reconciliation Rule Builder form on the Reconciliation Rules page, query and open the reconciliation rule for this connector and change the value of the Object field to map to the resource object that you have created. By default, the value of this field is mapped to that of the Xellerate User resource object.
For Oracle e-Business Suite, repeat all the steps you performed for Active Directory. Perform the following steps of that procedure differently for the Oracle e-Business Employee Reconciliation connector:
On the Resource Object tab, create the EmpRecon resource object for trusted source reconciliation with Oracle e-Business Suite.
Note:
You can assign a name to the resource object. This procedure is based on the use ofEmpRecon as the name assigned to the resource object.On the Object Reconciliation>>Reconciliation Action Rules tab, create rule conditions and action mappings. One of these rule condition-action mappings must be the following:
Rule Condition: No Matches Found
Action: Create User
Use the Limited Reconciliation feature to specify that only identities that belongs to the Employee user type must be reconciled.
After you add the fields and the reconciliation rules, delete the Oracle e-Business Suite-specific fields and the corresponding rules created in the Xellerate User resource object.
Create the EmpRecon process definition in the Process Definition form. For detailed information about the procedure to create a process definition, see "Process Definition Form". Based on the Xellerate User reconciliation field mappings, on the Reconciliation Field Mappings tab, add the field mappings for the EmpRecon process definition.
Delete the Oracle e-Business Suite-specific field mappings in the Xellerate User resource object.
On the Reconciliation Rules>>Reconciliation Rule Builder form, query and open the reconciliation rule for this connector and change the value of the Object field to map to the resource object that you have created. By default, the value of this field is mapped to that of the Xellerate User resource object.
For both Active Directory and Oracle e-Business Suite, perform the rest of the steps required to configure trusted source reconciliation. For example, while configuring the reconciliation scheduled task for each connector, specify the name of the trusted source resource object that must be used during trusted source user reconciliation.
The current value of the scheduled task attribute would be Xellerate User and it must be updated with the name of the new resource object configured for trusted source user reconciliation for this connector.
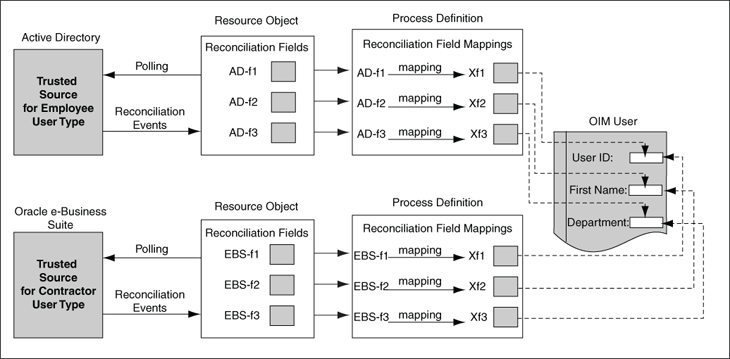
Figure 5-7 shows the design time implementation of trusted source reconciliation based on the user type.
Figure 5-7 Trusted Source Reconciliation by User Type
Configuring Non-MTS-Connectors for Trusted Source Reconciliation of Specific OIM User Attributes
You might want to configure trusted source reconciliation for specific OIM User attributes from multiple target systems. The procedure to implement this is described with the help of the following sample scenario:
You use Microsoft Active Directory and IBM Lotus Notes as your target systems. You want to reconcile identities from Active Directory and only the value of the e-mail address attribute of each identity (reconciled into Oracle Identity Manager from Active Directory) from Lotus Notes. To achieve this:
For the Active Directory connector:
Perform all the steps required to deploy the Active Directory connector and configure it for trusted source reconciliation.
See Also:
The documentation for the connector you are deploying for information about the procedure to configure trusted source reconciliationWhen you import the connector XML file for trusted source reconciliation, Active Directory-specific information is added in the Xellerate User resource object and process definition.
On the Resource Object tab, create the ActDir resource object for trusted source reconciliation with Active Directory.
Note:
You can assign any name to the resource object. This procedure is based on the use of ActDir as the name assigned to the resource object.
For detailed information about the procedure to create a resource object, see "Resource Objects Form".
While creating the resource object:
i. Select the Trusted Source check box on the Resource Object tab.
ii. On the Object Reconciliation>>Reconciliation Fields tab, see Xellerate User resource object and add the Active Directory-specific fields that you want to reconcile in ActDir. All the mandatory OIM User fields must be covered by the fields that you add on this tab.
On the Object Reconciliation>>Reconciliation Action Rules tab, create rule conditions and action mappings. One of these rule condition-action mapping must be the following:
Rule Condition: No Matches Found
Action: Create User
Delete the Active Directory-specific fields and the corresponding rules from the Xellerate User resource object.
Create the ActDir process definition in the Process Definition form. For detailed information about the procedure to create a process definition, see "Process Definition Form". Based on the reconciliation field mappings in the Xellerate User process definition, on the Reconciliation Field Mappings tab, create the field mappings for the ActDir process definition.
Delete the Active Directory-specific field mappings in the Xellerate User resource object.
On the Reconciliation Rules>>Reconciliation Rule Builder form, query and open the reconciliation rule for this connector and change the value of the Object field to map to the resource object that you have created. By default, the value of this field is mapped to that of the Xellerate User resource object.
For IBM Lotus Notes, repeat all the steps you performed for Active Directory. Perform the following steps of that procedure differently for the Lotus Notes connector:
On the Resource Object tab, create the LotNotes resource object for trusted source reconciliation with Lotus Notes.
Note:
You can assign a name to the resource object. This procedure is based on the use ofLotNotes as the name assigned to the resource object.When you create the resource object, add only the e-mail address attribute.
On the Object Reconciliation>>Reconciliation Action Rules tab, create rule conditions and action mappings. Create any rule condition other than user creation if no matches are found. If a match is found, then the link is established.
After you have added the fields and the reconciliation rules, delete the Lotus Notes-specific fields and the corresponding rules created in the Xellerate User resource object.
Create the LotNotes process definition in the Process Definition form. For detailed information about the procedure to create a process definition, see "Process Definition Form". Based on the Xellerate User reconciliation field mappings, on the Reconciliation Field Mappings tab, add the field mappings for the LotNotes process definition.
Delete the Lotus Notes-specific field mappings in the Xellerate User resource object.
For both Active Directory and Lotus Notes, perform the rest of the steps required to configure trusted source reconciliation. For example, while configuring the reconciliation scheduled task for each connector, specify the name of the trusted source resource object that must be used during reconciliation.
The current value of the scheduled task attribute would be Xellerate User and it must be updated with the name of the new resource object configured for trusted source user reconciliation for this connector.
Figure 5-8 shows the design time implementation of trusted source reconciliation of specific OIM User attributes.
Figure 5-8 Trusted Source Reconciliation for Specific OIM User Attributes

Oracle Identity Manager supports service accounts. Service accounts are general administrator accounts (for example, admin1, admin2, admin3, and so on) that are used for maintenance purposes, and are typically shared by a set of users. The model for managing and provisioning service accounts is slightly different from normal provisioning.
Service accounts are requested, provisioned, and managed in the same manner as regular accounts. They use the same resource objects, provisioning processes, and process and object forms as regular accounts. A service account is distinguished from a regular account by an internal flag.
When a user is provisioned with a service account, Oracle Identity Manager manages a mapping from the user's identity to the service account. When the resource is revoked, or the user gets deleted, the provisioning process for the service account does not get canceled (which would cause the undo tasks to starts). Instead, a task is inserted into the provisioning process (the same way Oracle Identity Manager handles Disable and Enable actions). This task removes the mapping from the user to the service account, and returns the service account to the pool of available accounts.
This management capability is available through APIs.