| Oracle® Identity Manager Design Console Guide Release 9.1.0.2 Part Number E14762-01 |
|
|
View PDF |
| Oracle® Identity Manager Design Console Guide Release 9.1.0.2 Part Number E14762-01 |
|
|
View PDF |
This chapter describes managing users in the Design Console. It contains the following sections:
The User Management folder provides system administrators with tools to create and manage information about a company's organizations, users, user groups, requests, form templates, locations, process tasks, and reconciliation events.
This folder contains the following forms:
Organizational Defaults: Use this form to view records that reflect the internal structure of your organization and to designate information related to these entities.
Policy History: Use this form to view user records that your employees require.
Group Entitlements: Use this form to view records for groups of users to whom you can assign some common functionality.
Administrative Queues: Use this form to create and manage mass-assignment privileges for user groups for other Design Console forms.
Reconciliation Manager: Use this form to manage reconciliation events in Oracle Identity Manager.
The Organizational Defaults form is in the User Management folder. You use this form to view records that reflect the structure of your organization and to enter and modify information related to organizational entities. An organization record contains information about an organizational unit, for example, a company, department, or branch.
A suborganization is an organization that is a member of another organization, for example, a department in a company. The organization that the suborganization belongs to is referred to as a parent organization.
You use the Organizational Defaults tab to specify default values for parameters on the custom process form for resources that can be provisioned for the current organization. Each process form is associated with a resource object that is allowed for the organization, or with a resource that has the Allow All option on the associated Resource Objects form selected.
The values that you provide on the Organizational Defaults tab become the default values for all users in the organization. Oracle recommends that you do not specify default values for passwords and encrypted parameters.
Figure 4-1 shows the Organizational Defaults form.
Table 4-1 describes the fields of the Organizational Default form.
Table 4-1 Fields of the Organizational Defaults Form
| Field Name | Description |
|---|---|
|
Organization Name |
Name of the organization. |
|
Type |
The classification type of the organization, for example, Company, Department, Branch. |
|
Status |
The current status of the organization (Active, Disabled, or Deleted). |
|
Parent Organization |
The organization to which this organization belongs. If a parent organization is displayed in this field, this organization is displayed on the Sub Organizations tab for the parent organization. If this field is empty, this organization is a top-level organization. |
You use the Policy History form to view information about the resources that are allowed or disallowed for a user.
There are two types of users in Oracle Identity Manager:
End-user administrators: This user can access the Design Console and the Administrative and User Console. The system administrator sets permissions to enable end-user administrators to access a subset of the forms in the Design Console.
End-users: This user can access only the Administrative and User Console and generally has fewer permissions than end-user administrators. Only resource objects that are defined as self-service on the Objects Allowed tab of the user's organization are available for provisioning requests by using the Administrative and User Console.
Figure 4-2 shows this form.
Table 4-2 describes the fields of the Policy History form.
Table 4-2 Fields of the Policy History Form
| Field Name | Description |
|---|---|
|
User ID |
The user's Oracle Identity Manager login ID. |
|
First Name |
The user's first name. |
|
Middle Name |
The user's middle name. |
|
Last Name |
The user's last name. |
|
Email Address |
The user's e-mail address. |
|
Start Date |
The date on which the user's account will be activated. |
|
Status |
The current status of the user (Active, Disabled, or Deleted). |
|
Organization |
The organization to which the user belongs. |
|
User Type |
The user's classification status. Valid options are End-User and End-User Administrator. Only end-user administrators have access to the Design Console. |
|
Employee Type |
The employment status of the user at the parent organization (for example, full-time, part-time, intern, and so on). |
|
Manager ID |
The user's manager. |
|
End Date |
The date on which the user's account will be deactivated. |
|
Created on |
The date and time when the user record was created. |
Use this tab to view resource objects that are allowed or disallowed for a user, based on the following:
Access policies for the user group to which the user belongs
Resource objects that are allowed by the organization to which the user belongs
The Policy History tab contains a Display Selection region. To organize the contents of this tab, go to the uppermost box in this region and select an item from one of its menus, as follows:
Resource Policy Summary: Displays resource objects that are allowed or disallowed based on the user's organization and applicable access policies.
Not Allowed by Org: Displays only resource objects that are disallowed, based on the user's organization.
Resources by Policy: Displays a second box that contains the access policies for the user groups to which the user is a member.
Select an access policy from this box to display the resource objects that are allowed or disallowed for the user, based on this access policy.
A tracking system enables you to view resources that are allowed or disallowed for a user, based on the organizations the user is a member of and the access policies that apply to the user.
The resource objects that are allowed for the user are displayed in the Resources Allowed list. This list represents resource objects that can be provisioned for the user. It does not represent the resource objects that are provisioned for the user.
The resource objects that are disallowed for the user are displayed in the Resources Not Allowed list.
To view the tracking system:
Go to the Policy History tab.
Find the Display Selection region on this tab.
Click Policy History.
From the User Policy Profile History window, you can view resources that are allowed or disallowed for a user for the date and time you selected, as follows:
From the History Date box, you can select a date.
From the Display Type box, you can display resources that are allowed or disallowed based on the organizations the user is a member of, the access policies that apply to the user, or both.
From the Policy box, you can display the access policy that determines what resource objects are allowed or disallowed for the user.
The Group Entitlements form is displayed in the User Management folder. You use it to create and move forms, and to designate the forms and folders that members of a user group can access through the Explorer.
To designate forms and folders to user groups by using the Group Entitlements form:
In the Explorer, double-click Group Entitlements.
The User Group Information page is displayed.
In the Group Name field, enter the name of the user group.
Click Assign.
The User Form Assignment lookup table is displayed.
From the lookup table, select the user form for this user group.
Use the arrow buttons to either add or delete from the Assigned Forms list.
Click OK.
The User Group Information dialog box is displayed, as shown:
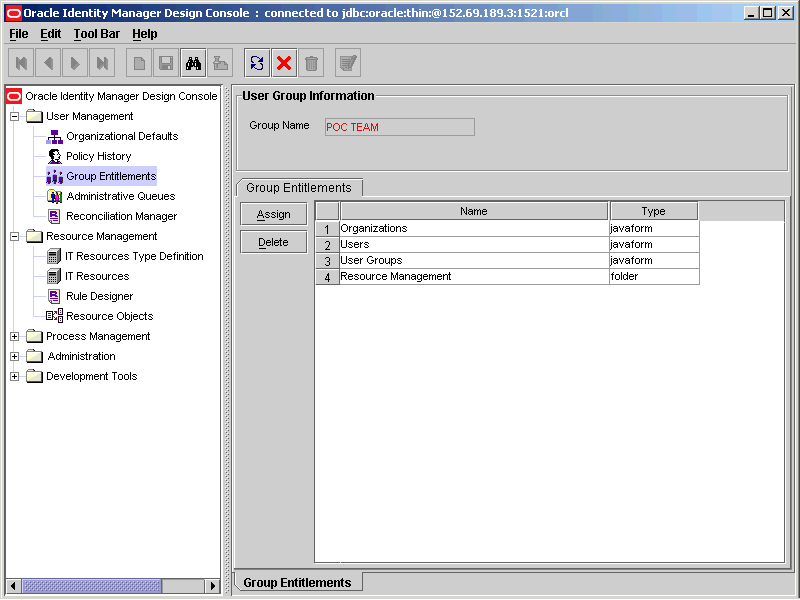
The newly added user forms are listed in a Group Entitlements table. The Group Entitlements Table displays all available user groups. This table shows the name of the user form and the type. In the Group Entitlements table, there are two types, javaform and folder. A javaform is a Java-based, graphical interface. A folder is a container of one or many javaforms.
Oracle Identity Manager provides four default user group definitions:
System Administrators
Operators
All Users
Self Operators
You can modify the permissions associated with these user groups, and you can create additional user groups.
Members of the System Administrators user group have full permission to create, edit, and delete records in Oracle Identity Manager, except for system records.
Members of the Operators user group can view Organizational Defaults and Policy History forms, and can perform limited functions with these forms.
Members of the All Users user group have minimal permissions. These permissions include but are not limited to access to the user's own record. Each user automatically belongs to the All Users user group.
A user cannot be removed from the All Users group.
The Self Operators user group is added to Oracle Identity Manager by default. This user group contains one user, XELSELFREG, who is responsible for modifying the privileges that users have when performing self-registration actions in the Oracle Identity Manager Administrative and User Console.
Note:
Do not modify the permissions associated with the Self Operators user group or assign any users to this group.You assign groups of users to manage a provisioning request by using an entity called a queue. A queue is a collection of group definitions. Queues can be nested within other queues.
Administrative queues increase the efficiency and manageability of requests. A queue that you assign to one request can be reused for other requests.
A request can specify different administrative privileges for each group in the queue. For example, suppose that you assign a queue with three user groups to a request. The members of the three groups can have different administrative privileges for the request. The first user group is allowed to read, modify, and delete the request. The second user group is allowed to read and modify the request. The third user group is allowed to read and delete the request.
Note:
The Administrative Queues form in the Design Console is deprecated. Although the form can still be viewed in the Design Console, you must use the Oracle Identity Manager APIs to access administrative queue features.See Oracle Identity Manager API Usage Guide for more information.
This form is located in the User Management folder. It enables you to view, analyze, correct, link, and manage information in reconciliation events received from target resources and trusted source. A designated person can manually analyze and link information in reconciliation events, or analysis and linking can be done automatically by Oracle Identity Manager based on action rules you define. These rules are based on whether or not an event is associated with an existing record, if it represents a new account, or if it can allow the linking of the information in the event to be manually initiated.
The reconciliation classes that you define periodically poll your target resources and trusted source. Any changes on these systems generate reconciliation events that are written to the Reconciliation Manager. Oracle Identity Manager analyzes event information according to mappings defined in a relevant provisioning process.
Figure 4-3 shows the Reconciliation Form.
Note:
You can use the Design Console Task Scheduler form to define a schedule and set timing parameters to control how often a reconciliation class is run, or to use a third-party scheduling tool to set the polling frequency.The Reconciliation Manager form works as follows:
If the information in the event relates to an existing user or organization record, you can use this form to manually link the data in the event to the record.
You can also review information that was automatically linked to the user or organization.
If the event represents the creation of a new employee on a trusted source (user discovery) or provisioning of an existing employee with a new resource (account discovery), you can use this form to manually update Oracle Identity Manager with new data.
You can also review information that was automatically linked to a user. For trusted sources, the data in the event is used to create a new user account. For target resources, the data in the event is used to populate the relevant resource-specific process form.
If the event represents the creation of a new organization on a trusted source (organization discovery) or provisioning of an existing organization with a new resource (account discovery), you can use the form to manually update Oracle Identity Manager with the new data.
You can also use the form to review the information that was automatically linked to a organization.
If the event represents the deletion of an account on a target system or trusted source, this form can be used to instruct Oracle Identity Manager to delete a particular account or to review an account that was automatically deleted.
For trusted sources, the deletion of an account on a target system or trusted source deletes the user's Oracle Identity Manager account and revokes all accounts with which that user have been provisioned on any target resource.
For target resources, Oracle Identity Manager is notified of revoked user accounts.
The upper portion of the Reconciliation Manager form contains the following fields, as shown in Table 4-3.
Table 4-3 Fields of the Reconciliation Manager Form
| Field Name | Description |
|---|---|
|
Event ID |
The numeric ID of the reconciliation event. |
|
Delete Event (Yes or No flag) |
Indicates if the corresponding record was deleted from the target resource or the trusted source. Yes indicates a delete event. If this event is associated with a user account on a target resource, the account is marked as revoked. If the event is associated with a user account, the account is deleted. Note: This field is set by Oracle Identity Manager. |
|
Object Name |
The target resource or trusted source that is associated with this reconciliation event. For trusted sources, this is the user. |
|
For User/For Organization |
Indicates that the event for a resource object is associated with a user record or organization record. |
|
Status |
The current status of the reconciliation event:
|
|
Event Date |
The date and time that this event was received. |
|
Assigned to User |
The user to whom this event is assigned. |
|
Assigned to Group |
The user group to which this event is assigned. |
|
Linked To (region) |
The fields in this section are User Login, Organization Name, Process Instance Key, and Process Descriptive Data. |
|
User Login |
The Oracle Identity Manager ID of the user record to which the event is linked. |
|
Organization Name |
The Oracle Identity Manager ID of the organization record to which the event is linked. If you are conducting organization discovery with a trusted source, then Oracle recommends that you do this before performing user discovery, because every user record in Oracle Identity Manager must be associated with an organization record. |
|
Process Instance Key |
Numeric instance of the provisioning process that is linked to the event. |
|
Process Descriptive Data |
Instance-specific descriptive data for the provisioning process that is defined in the Map Descriptive Field window in the Process Definition form. |
|
Close Event |
Closes the reconciliation event. If the event is closed, no additional matching attempts or linking can be performed on it. |
|
Re-apply Matching Rules |
Reapplies the reconciliation matching rules. This includes both process data and user-matching or organization-matching rules that are associated with the resource object. If Oracle Identity Manager is not generating satisfactory matches, you can change and reapply the resource's reconciliation matching rules, or you can change the mappings for the provisioning process. Reapplying these rules after changing them can cause different records to be displayed on the Processes Matched, Matched Users, or Matched Organizations tabs. Reconciliation rules are only applied to target resource reconciliation events when no provisioning process matches are generated because the process matches should be more accurate. |
|
Create Organization (Only available on events related to the trusted source) |
Creates an organization record in Oracle Identity Manager based on the information in the reconciliation event. Click this button only when you are certain that the reconciliation event represents the creation of a new organization on the trusted source. |
|
Create User (Only available on events related to the trusted source) |
Creates a user record in Oracle Identity Manager based on the information in the reconciliation event. Click this button only when you are certain that the reconciliation event represents the creation of a new user on the trusted source. |
To view and manage reconciliation events:
Note:
Depending on how you define your reconciliation action rules, Oracle Identity Manager automatically links data in a reconciliation event to a user or organization record when only one match is found or when no matches are found for the trusted source.Go to the Reconciliation Manager form.
Use the query feature to locate a reconciliation event.
You can also query reconciliation events by their associated resource in the Object Name field or status in the Status field.
If you are querying a deleted event, that is, the corresponding record was deleted from the target resource or the trusted source, Delete Event is set to Yes. Otherwise, it is set to No.
After locating the desired reconciliation event, use the tabs on this form to:
Correct any unprocessed data.
Browse and link to matching provisioning process form instances, or user-record or organization-record candidates.
View the audit history of the event.
The information about each tab is described in the tabs on the Reconciliation Manager form section. When evaluating the matches that Oracle Identity Manager generates, you can do the following:
Link the reconciliation event to a particular provisioning process, user, or organization: It is assumed that the event is associated with an existing user or organization record.
To do this, click Link on the applicable tab. You might have defined rules that instruct Oracle Identity Manager to automatically link the data when only a single match is found.
For user-based reconciliation with the trusted source: Create a new user in Oracle Identity Manager if the event represents the creation of a new user on the trusted source.
To do this, click Create User. Or, you can have defined action rules that instruct Oracle Identity Manager to automatically create the user when no match is found.
For organization-based reconciliation with the trusted source: Create a new organization in Oracle Identity Manager if the event represents the creation of a new organization on the trusted source.
To do this, click Create Organization. Or, you can have defined action rules that instruct Oracle Identity Manager to automatically create the organization when no match is found.
Refine the reconciliation rules: These are rules associated with this resource. Re-apply the rule to generate more accurate matches.
To do this, refine the applicable reconciliation rule, save it, then click Re-apply Matching Rules.
Note:
If you refine a reconciliation rule and reapply it or create or link a user or provisioning process or organization, then these actions are logged in the Reconciliation Event History tab. To view a log of the actions that were performed on the reconciliation event, click the Reconciliation Event History tab.After locating the reconciliation event that you want to examine, you can use tabs to do the following:
View any processed or unprocessed data in the event
View provisioning process, user, or organization matches that were generated
Link the event to the appropriate record or create a new user
The data on this tab is displayed under one of two branches: Processed Data and Unprocessed Data.
The fields in the Processed Data branch are defined on the Reconciliation Fields tab of the associated resource. In the reconciliation event, these fields were successfully processed, for example, they did not violate any data type requirements. For each successfully processed field, the following is provided:
Name of the field as defined on the Reconciliation Fields tab of the associated resource, for example, field1.
Data type associated with the field that was reconciled, for example, string. Possible values are Multi-Valued, String, Number, Date, IT resource.
Value of the field that was received in the reconciliation event, for example, Newark. This might be one of several values that changed on the target resource or trusted source that initiated the reconciliation event.
The following is an example of a processed data field:
Location [String] = Newark
Note:
If a field is of type multivalue (only allowed for target resources, not trusted sources), it will not have a value. Instead, its component fields (contained in its subbranch) will each have their own values.The fields listed in the Unprocessed Data branch are reconciliation events that could not be processed. For example, these can be items that were not defined or that conflicted with the data type set on the Reconciliation Fields tab of the associated resource. For each unprocessed field, the following information is displayed:
Name of the field, for example, user_securityid.
Value of the field that was received in the reconciliation event, for example, capital. This might be one of several values that changed on the target resource or trusted source that initiated the reconciliation event.
Reason why the data received from the target system was unable to be automatically processed, for example, <Not Numeric>. One of the following codes is displayed next to the unprocessed field:
| Error code | Reason generated |
|---|---|
| NOT MULTI-VALUED ATTRIBUTE | The field value is a multivalued attribute. Only the component fields of a multivalue attribute, not the multivalue field itself, can accept values. |
| NOT NUMERIC | A numeric field value was nonnumeric. |
| DATE PARSE FAILED | The system failed to recognize the value of a date field as a valid date. |
| SERVER NOT FOUND | The value for a field of type IT Resource was not recognized as the name of an existing IT Resource instance. |
| FIELD NOT FOUND | The name of the field in the event was not defined on the resource. |
| PARENT DATA LINK MISSING | The parent data field (of type multivalue) is not yet linked to a reconciliation field. As a result, this component field cannot be linked to a child reconciliation field. |
| FIELD LINKAGE MISSING | The corresponding reconciliation field is not defined on the Reconciliation Fields tab of the associated resource. |
| ATTRIBUTE LINKAGE MISSING | This applies only to fields of type multivalue. One or more of the multivalue field's component (child) fields' data is not linked to reconciliation fields. |
| TABLE ATTRIBUTE LINKAGE MISSING | This applies only to fields of type multivalue. Some of the component (child) fields of type MultiValued Attribute are not linked to a reconciliation field of type MultiValued Attribute. |
The name of the resource field that this event field was mapped to, if the unprocessed field is successfully mapped to a resource field.
The following is an example of an unprocessed data field:
user_securityid = capital <Not Numeric>
Note:
Oracle Identity Manager does not match processes for target resources, or users or organizations for trusted sources, until all fields that are set on the Reconciliation Fields tab of the associated resource are successfully processed.Use the following procedure to correct or map unprocessed fields in the reconciliation event to the relevant fields as defined on the applicable resource.
To map or correct unprocessed fields:
Double-click the unprocessed field.
For a multivalue field, you must map it to the appropriate child process form or select the individual component field.
For multivalue fields, double-click and correct the component fields.
The Edit Reconciliation Field Data dialog box is displayed.
Note:
To map an unprocessed multivalued component field to one of the multivalue fields defined on the Reconciliation Fields tab of the associated resource, double-click the Linked to field, select the desired field, and click OK. Click Save and close the Edit Reconciliation Field Data dialog box.To map the unprocessed field to one of the fields defined on the Reconciliation Fields tab of the associated resource, double-click the Linked To field, select the desired field, click OK, click Save, and close the Edit Reconciliation Field Data dialog box.
To change the value of the unprocessed field, enter the correct value in the Corrected Value field, click Save, and close the Edit Reconciliation Field Data dialog box.
If the field's data is successfully processed, the entry in the Unprocessed Data branch is updated to reflect the field to which it was linked. A new entry for the field is added to the Processed Data branch.
After the required data elements (on the Object Reconciliation tab of the applicable resource definition) in the reconciliation event are marked as processed on the Reconciliation Data tab, Oracle Identity Manager displays the following:
For trusted sources:
All user or organization records that match the relevant data in the reconciliation event, as specified in the logic of all applicable user or organization-matching reconciliation rules that are associated with the resource. These records represent accounts on the trusted source for which a potential owner was found in Oracle Identity Manager (user update) based on the application of user-matching rules. If no matches are found, the reconciliation event represents the creation of a new user account on the trusted source (that is, user creation).
For target resources:
All provisioning process form instances where the values of all key fields (as set on the Reconciliation Field Mappings tab of the applicable process definition) match the values for all key fields in the reconciliation event. This represents an account in the target system for which a possible matching account was found in Oracle Identity Manager (account update).
If no process instances match these values, Oracle Identity Manager evaluates the applicable user-matching or organization-matching reconciliation rules and displays users or organizations that match data in the reconciliation event. These matches represent accounts on the target system for which the reconciliation engine did not find a matching account record in Oracle Identity Manager. Oracle Identity Manager is not aware that the user was provisioned with an account on that system, but did find potential owners of the account (account creation). If more than one matching record is found, an administrator must examine the records and decide to which Oracle Identity Manager account to link it. If no matches are found, then there might be a mismatch between the data in your trusted source and the target application. This event can be a rogue account on the target system or an existing employee was provisioned with a new account on the target system. However, Oracle Identity Manager is unable to decide with which user that account is associated.
After all required fields defined on the Reconciliation Fields tab of the associated resource are processed, the tab displays all provisioning process form instances where the values of all key fields match the values for all key fields in the reconciliation event.
Note:
This only occurs for reconciliation events that are associated with target resources. Because the trusted source is linked to the user resource or organization and its provisioning process, it cannot have a custom process form. As a result, it cannot possess the matches required to populate this tab. For trusted sources, after all required fields are processed, Oracle Identity Manager evaluates the user-matching or organization-matching rules.For each matched provisioning process, the following is displayed:
The name of provisioning process associated with the process form instance that matched the values of the key fields in the reconciliation event, for example, windows2000_prov.
The numeric ID of the particular process instance, for example, 445.
The user ID, for example, jdoe, or Organization Name, for example, Finance, associated with this process instance. That is, the user who was provisioned with the resource by that instance of the provisioning process.
An example of a matched provisioning process is similar to the following:
Windows2000_prov [445] for User=jdoe
If no provisioning processes are listed on this tab, Oracle Identity Manager was unable to match any values in the key fields in the reconciliation event to any values for fields in process form instances associated with that resource. If this occurs, then Oracle Identity Manager applies any user-matching or organization-matching rules that are defined for the resource. If matches are found, then they are displayed on the Matched Users or Matched Organizations tab.
To link a provisioning process instance to the reconciliation event:
After you determine which provisioning process instance to link to the reconciliation event, select the process instance and click Establish Link.
Oracle Identity Manager updates the relevant process form instance with the information in the reconciliation event according to the mappings defined on the relevant provisioning process. This also inserts the Reconciliation Update Received task in that process.
This tab displays the user records that match the relevant data in the reconciliation event, as specified in the criteria of the resource's reconciliation rules.
For trusted sources, Oracle Identity Manager evaluates these rules and displays any matching user records as soon as all required fields (as defined on the Reconciliation Fields tab of the associated resource) are processed.
For a target resource, Oracle Identity Manager evaluates the rules and displays any matching user records only after all required fields (as defined on the Reconciliation Fields tab of the associated resource) are processed and no matches are generated on the Processes Matched Tree tab.
For each matching record, the Design Console displays the user's ID, first name, and last name.
Note:
If matching records are present on the Processes Matched Tree tab, no records are displayed on the Matched Users tab. The process matches are more likely to be accurate.To link a user record to a reconciliation event:
Note:
A record must exist for you to perform the following procedure. For trusted sources, if you determine that the reconciliation event represents the creation of a new user on the trusted source, click Create User. This creates a new user record by using the information in the reconciliation event.Determine the user to link to the reconciliation event, select the user, and click Link.
If you click Link and the reconciliation event is for a target resource, then Oracle Identity Manager:
Creates an instance of the resource's provisioning process for the selected user, suppresses any adapters associated with the process' tasks, completes the process, and inserts the Reconciliation Insert Received task.
Creates an instance of the resource's process form with the data from the reconciliation event according to the mappings defined on the provisioning process.
If you click Link and the reconciliation event is for a trusted source, then Oracle Identity Manager:
Updates the user record with the data from the reconciliation event according to the mappings defined on the user provisioning process.
Inserts the Reconciliation Insert Received in the instance of the user provisioning process for the user record to which the reconciliation event is linked.
This tab displays Oracle Identity Manager organization records that match the data in the reconciliation event, as specified the resource's reconciliation rules.
For trusted sources, Oracle Identity Manager evaluates these rules and displays matching organization records when all required fields (as defined on the Reconciliation Fields tab of the associated resource) are processed.
For target resources, Oracle Identity Manager evaluates these rules and displays matching organization records only after all required fields (as defined on the Reconciliation Fields tab of the associated resource) are processed and no matches are generated on the Processes Matched Tree tab.
For each matching record, Oracle Identity Manager displays the user's ID, first name, and last name.
Note:
If matching records are present on the Processes Matched Tree tab, no records are displayed on the Matched Organizations tab because the process matches are and more likely to be accurate.To link an organization record to a reconciliation event:
Note:
The following procedure assumes a record already exists. For trusted sources, if you determine that the reconciliation event is the creation of a new organization on the trusted source, click Create Organization. This creates a new organization record by using the information in the reconciliation event.After you determine what organization to link to the reconciliation event, select the event and click Link.
If the reconciliation event is for a target resource, Oracle Identity Manager does the following:
Creates an instance of the resource's provisioning process for the selected organization, suppresses any adapters associated with the process' tasks, completes the process, and inserts the Reconciliation Insert Received task.
Creates an instance of the resource's process form with the data from the reconciliation event, according to the mappings defined on the provisioning process.
If the reconciliation event is for a trusted source, Oracle Identity Manager does the following:
Updates the organization record with the data from the reconciliation event, according to the mapping defined on the Oracle Identity Manager Organization provisioning process.
Inserts the Reconciliation Insert Received task in the existing instance of the Oracle Identity Manager Organization provisioning process for the organization record to which the reconciliation event is linked.
The Reconciliation Event History tab displays a history of the actions performed on this reconciliation event. For each action, the date and time on which it took place is shown. Oracle Identity Manager tracks and logs the following reconciliation events:
Event Received: This action is logged when Oracle Identity Manager receives a reconciliation event.
Data Sorted: This action is logged when the data in a reconciliation event is sorted into processed and unprocessed fields.
Rules Reapplied: This action is logged when a user clicks the Re-apply Matching Rules button.
Processes Matched: This action is logged when one or more process form instances and their associated provisioning process were matched to values of key fields in the reconciliation event.
Users Matched: This action is logged when one or more user records are matched with data in the reconciliation event by using user-matching reconciliation rules.
Organization Matched: This action is logged when one or more Oracle Identity Manager organization records are matched with data in the reconciliation event by using organization-matching reconciliation rules.
Linked to User: This action is logged when the data in the reconciliation event is linked to a particular user.
Linked to Organization: This action is logged when the data in the reconciliation event is linked to a particular organization.