5 Business Operations Center Security
This chapter provides information about installing and implementing Oracle Communications Billing and Revenue Management (BRM) Business Operations Center and its components in a secure configuration.
About Installing Business Operations Center
Before installing Business Operations Center, you must properly install and configure several Oracle products, including Java, Oracle WebLogic Server, Oracle Identity and Access Management components, and Oracle Communications Billing and Revenue Management. For installation instructions, including all the required products and related tasks, such as setting up keystores and SSL for WebLogic Server, see Oracle Communications Business Operations Center Installation Guide.
About Implementing Business Operations Center Security
Business Operations Center supports stringent authorization and authentication requirements. This section describes how to implement the security capabilities supported by Business Operations Center.
About Identity and Access Management
To authenticate users when they log in and to control user access to functionality, Business Operations Center uses the following Oracle Identity and Access Management components in a production environment:
-
Oracle Identity Manager for authentication
-
Oracle Entitlements Server for authorization
Oracle Identity Manager and Oracle Entitlements Server are required in a Business Operations Center implementation.
For more information, see the following documentation:
-
Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager
-
Oracle Fusion Middleware Administrator's Guide for Oracle Entitlements Server
About Authentication
Authentication is the process of verifying the identity of a user. The Business Operations Center authentication scheme is designed for deployments in which a central user identity repository, storing all enterprise users, authenticates Business Operations Center sign-in requests.
Business Operations Center supports the following security for authentication:
-
Authenticating users against an LDAP-based user ID repository
-
Enabling single-sign-on capabilities
-
Supporting user's password policies
Oracle Identity Manager manages user password policies. For more information, see Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
About Authorization
Authorization is the process of granting users those access privileges (entitlements) appropriate for their job functions while denying access to other functionality. Oracle Entitlements Server handles all authorization tasks for Business Operations Center.
A user who has not been granted any entitlements in Oracle Entitlements Server is denied access to Business Operations Center.
To grant entitlements, you use authorization policies, which contain a collection of the following components combined to form a logical entitlement:
-
Resource type: Specifies the full scope of traits for a resource, such as job execution history, and defines all actions that can be performed on the resource.
-
Resource: Represents the aspect of an application's functionality being secured, such as billing, payment collection, and invoicing. Each resource must belong to a resource type.
-
Action: Represents an operation that can be performed on a resource, such as view, define, modify, and delete.
You map authorization policies to enterprise (external) roles, which represent job functions for the users in your company. If you do not map enterprise roles to authorization policies, you must map each user to an authorization policy.
For more information about authorization policies and enterprise roles, see Oracle Fusion Middleware Administrator's Guide for Oracle Entitlements Server.
Business Operations Center includes an authorization policy component file (system-jazn-data.xml), which defines all the resource types, resources, and actions available for Business Operations Center authorization policies (see Table 5-1).
Table 5-1 Business Operations Center Authorization Policy Components
| Resource Type | Resource | Action | Description |
|---|---|---|---|
|
Job Execution History |
Billing |
View |
Permits users to view the run history of billing jobs. |
|
Job Execution History |
Payment Collection |
View |
Permits users to view the run history of payment-collection jobs. |
|
Job Execution History |
Invoicing |
View |
Permits users to view the run history of invoicing jobs. |
|
Job Execution History |
G/L |
View |
Permits users to view the run history of general ledger (G/L) jobs. |
|
Metrics |
Subscribers |
View |
Permits users to view subscriber metrics. |
|
Metrics |
Subscriptions |
View |
Permits users to view subscription metrics. |
|
Metrics |
Billed Revenue |
View |
Permits users to view billed-revenue metrics. |
|
Metrics |
Payments Received |
View |
Permits users to view payments-received metrics. |
|
Metrics |
A/R |
View |
Permits users to view accounts receivable (A/R) metrics. |
|
Job |
Jobs |
Any |
Permits users to view, create, modify, and delete any type of job. |
|
Any |
Any |
Any |
Permits users to perform all operations. |
The system-jazn-data.xml file also includes the following sample authorization policies:
-
OperationsAdminPolicy
-
FinancialsAdminPolicy
-
FullAdminPolicy
The file is located in the Domain_home/lib/oes_config directory, where Domain_home is the WebLogic Server domain home directory location of the Oracle Entitlements Server client domain in which Business Operations Center is deployed.
Important:
Do not change the system-jazn-data.xml file.Creating Authorization Policies for Business Operations Center
To create authorization policies for Business Operations Center:
-
Import the Business Operations Center authorization policy component file:
Domain_home/lib/oes_config/system-jazn-data.xml
For detailed instructions, see "Importing the Business Operations Center Security Policies into OES" in Business Operations Center Installation Guide.
-
In Oracle Entitlements Server, map an authorization policy to one or more resources, which may have one or more actions.
For more information, see Oracle Fusion Middleware Administrator's Guide for Oracle Entitlements Server.
-
Associate the authorization policy with a user or an enterprise role.
For more information, see Oracle Fusion Middleware Administrator's Guide for Oracle Entitlements Server.
-
Redeploy all changes made in Oracle Entitlements Server.
Figure 5-1 shows how authorization policies are mapped to resources and enterprise roles or users:
Figure 5-1 Mapping Authorization Policies to Resources and Enterprise Roles or Users
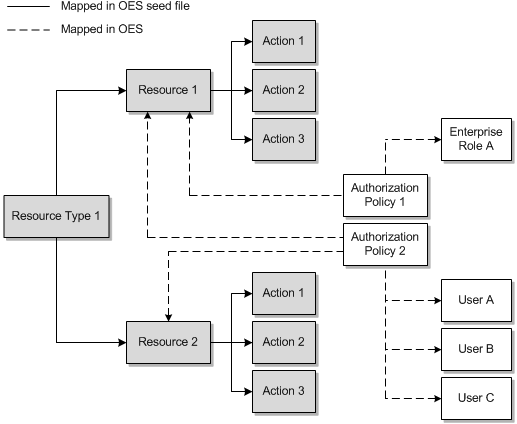
Description of ''Figure 5-1 Mapping Authorization Policies to Resources and Enterprise Roles or Users''