| Oracle® OpenSSO STS Administrator's Guide Release 11gR1. Version 11.1.1.3.0 Part Number E17844-01 |
|
|
View PDF |
| Oracle® OpenSSO STS Administrator's Guide Release 11gR1. Version 11.1.1.3.0 Part Number E17844-01 |
|
|
View PDF |
The following topics are contained in this chapter:
Configuring Administrator Single Sign-On with Oracle Access Manager
Configuring OpenSSO STS to Work with Oracle Internet Directory and Oracle Virtual Directory
You can deploy OpenSSO STS in an environment where Oracle Access Manager already exists. When OpenSSO STS and Oracle Access Manager are configured for single sign-on, an administrator who has authenticated to Oracle Access Manager can access OpenSSO STS without having to present credentials a second time. The administrator single sign-on use case requires that Oracle HTTP Server is deployed in the environment to act as a proxy for OpenSSO STS, and OpenSSO STS must be configured with the Oracle Access Manager authentication module. The following diagram illustrates a typical single sign-on topology.
Figure 8-1 Single Sign-On Using Oracle Access Manager and OpenSSO STS
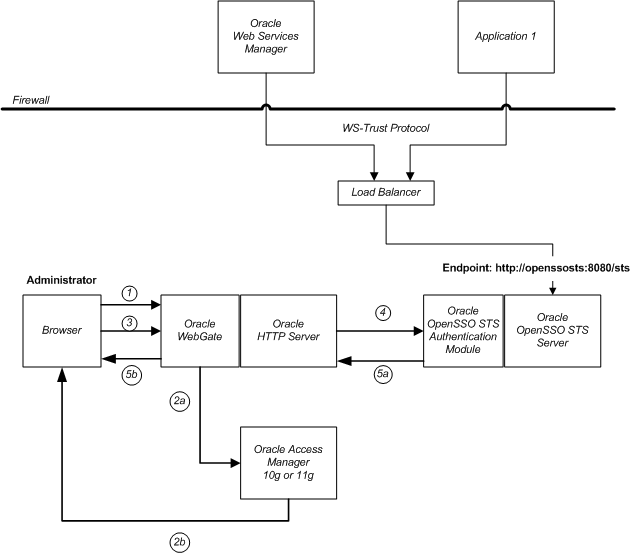
In this topology, Oracle WebGate is installed on the Oracle HTTP Server. The HTTP Server must be configured in proxy mode for OpenSSO STS, and OpenSSO STS must be deployed on a supported web container.
When an administrator attempts to access OpenSSO STS, Oracle WebGate intercepts the request. Then Oracle Access Manager presents a login page. The administrator presents credentials, which are then authenticated to Oracle Access Manager. Once the administrator has been authenticated, the access request is redirected to the browser, and then to OpenSSO STS. OpenSSO STS is configured with the Oracle Access Manager authentication module, enabling Oracle Access Module to validate the administrator based on a list of allowed users. If the administrator is on the list of allowed users, then the administrator can access the OpenSSO STS console without having to present credentials.
The following list summarizes high-level steps you must take to configure administrator single sign-on with Oracle Access Manager. Follow the detailed installation and configuration instructions in the documentation for each Oracle product in your environment. See http://www.oracle.com/technology/documentation/index.html.
Install OpenSSO STS on Oracle WebLogic Server.
Install Oracle Access Manager.
Install Oracle HTTP Server and configure it to proxy for OpenSSO STS.
Install Oracle Webgate on Oracle HTTP Server.
Configure single sign-on between Oracle HTTP Server and Oracle Access Manager to protect the OpenSSO STS login URL:
http://HostName.Domain.com:port/openssosts/UI/Login?module=OAMAuthModule
Configure Oracle HTTP Server for proxying.
Edit $OH_INSTANCE_DIR/config/OHS/ohs1/mod_w1_ohs.conf to include the following:
WebLogicHost:HostName.Domain.com WeblogiPort: 7001 MatchExpression: openssosts
Access the Webgate URL using the OpenSSO STS URI (the proxy URL). Example:
http://HostName.Domain.com:port/openssosts/UI/Login?module=OAMAuthModule
The browser redirects the user request to the Oracle Access Manager console.
Log in to Oracle Access Manager using OpenSSO STS administrator credentials.
By default, Oracle Access Manager sets the remote user as OAM_REMOTE_USER. The OpenSSO STS validates OAM_REMOTE_USER, and provides access to the OpenSSO STS administration console.
Both Oracle Internet Directory and Oracle Virtual Directory are LDAP-compliant directory services. You can add an LDAP authentication module to OpenSSO STS, and then configure the LDAP authentication module to use either Oracle Internet Directory or Oracle Virtual Directory as a user data store.
The following figure illustrates a topology in which Oracle Internet Directory is the sole user directory used for authentication and attribute retrieval.
Figure 8-2 OpenSSO STS Integrated with Oracle Internet Directory
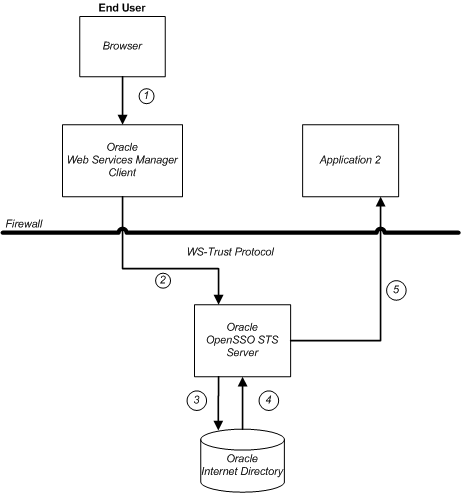
Oracle Virtual Directory provides an abstraction layer that enables external directories to connect to OpenSSO STS. When OpenSSO STS receives a WS-Trust request with a UserName token (or UserName On-Behalf-Of token) as either an inbound or outbound token, OpenSSO STS validates the user, though Oracle Virtual Directory, against one of the connected directories. The following figure illustrates a typical topology using Oracle Virtual Directory and two LDAP directories.
Figure 8-3 OpenSSO STS Integrated with Oracle Virtual Directory
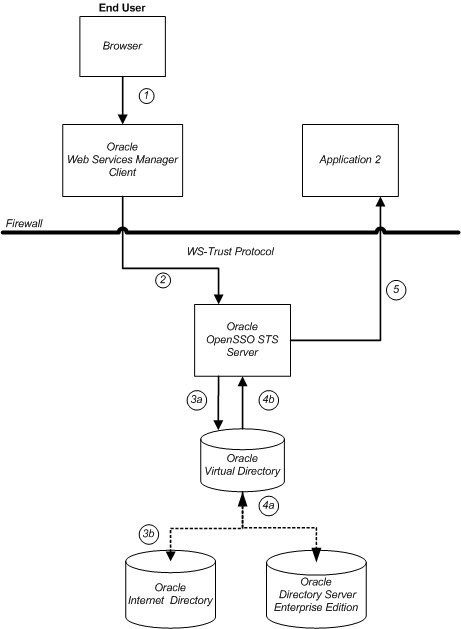
An inbound request is sent through Oracle Web Services Manager client in the form of a SOAP request. OpenSSO STS receives the request and authenticates it, through Oracle Virtual Directory, against Oracle Internet Directory. OpenSSO STS reads the attributes from the UserName token, and generates a SAML assertion response.
The following summarizes high-level steps you must take to configure Oracle Internet Directory for user authentication.
In the OpenSSO STS console, add and configure an Oracle Internet Directory or Oracle Virtual Directory authentication module instance.
See Section 6.3.10, "To Add an New LDAP Authentication Module Instance" and Section 6.3.11, "To Configure an LDAP Authentication Module Instance."
Create and configure an authentication chain for inbound security tokens.
Create and configure an authentication chain for outbound security tokens.
Configure the Security Token Service.
See Section 4.2, "To Configure the Security Token Service."
The OpenSSO STS authentication service determines the security mechanism registered by the web service provider, and retrieves the appropriate security tokens.
Enable both inbound and outbound authentication chains based on the authentication chain security mechanism specified when the web service provider agent profile was created.
See Section 4.4, "To Register a Web Service Provider to OpenSSO STS."
Each time you add a web service provider to OpenSSO STS, you must be sure that the web service provider is configured for SAML attribute retrieval, and that SAML attribute mapping is defined in OpenSSO STS. The following summarizes high-level steps you must take to use Oracle Internet Directory or Oracle Virtual Directory for SAML attribute generation and retrieval in a web service provider.
Add a new LDAP data store and configure it to communicate with Oracle Internet Directory or Oracle Virtual Directory.
In the web service provider profile, configure the SAML attribute mapping.