5 Setting Up Security
Multiple layers and types of security are available in Oracle URM, including roles, rights, security groups, and access control lists. As with the standard Oracle UCM security model, the final determination of permissions and privileges is determined by the intersection of all security mechanisms in place.
Access control lists and supplemental markings are required for compliance with the DoD 5015.2 specification. Classification levels are required for compliance with Chapter 4 of DoD 5015.2. Custom security fields can be created and additional security added to individual fields. See Chapter 6, "Additional Security Settings" for details.
You can also use the accounts security model in addition to the options provided by the system. For more information about the account security model, see the Oracle Fusion Middleware System Administrator's Guide for Content Server. See "Fusion Middleware Security Considerations" for details about user roles, accounts, and permission considerations.
This section covers the following topics:
5.1 Retention Management in an Organization
The figure below shows a typical retention management structure in an organization.
Figure 5-1 Typical Retention Management Organization
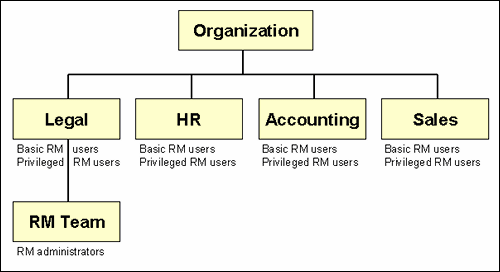
Description of "Figure 5-1 Typical Retention Management Organization"
Most people in the various departments of an organization can file content or check in content items, search for items, and view them. These are basic Records Users.
A much smaller group of people ("privileged users") is typically granted rights to perform some additional functions not allowed for basic users (for example, altering classifications or creating triggers or retention schedules). These are people with the Records Officer right.
A very limited number of people are administrators, who are typically responsible for setting up and maintaining the management infrastructure. Records Administrators have the widest range of rights to perform management tasks. For example, they can usually perform all and disposition actions, including those assigned to others. The administrators are often in the legal department of an organization, which can drive the efforts for effective and efficient management.
The software comes with predefined management roles called 'rma', 'rmalocalrecordsofficer', and 'rmaadmin', designated in the documentation as Records User, Records Officer, and Records Administrator. Each of these standard roles provides a default set of permissions and rights, which coincide with the typical responsibilities of basic users, privileged users, and administrators, respectively. However, these roles can easily be modified to suit specific management needs. New roles can be created with assigned management rights or different management rights can be given to existing roles.
Users without specific rights can still apply life cycles to content items.
Important:
Record management consists of more than just software. You also need to have the appropriate organizational structures and policies in place in your organization.5.2 Roles
The system comes with predefined user roles, discussed in detail in "Security Groups":
-
rma (denoted as "Records User" in this documentation): This role is generally assigned to basic users and allows them to perform basic management tasks. Users with this role have read permission (R) to the Public security group, and read and write permission (RW) to the special Record Group security group.
-
rmalocalrecordsofficer (denoted by "Records Officer" in this documentation): This role is generally assigned to "privileged" users, who have all the permissions assigned to basic users ('rma' role) but are also granted rights to perform additional functions (for example, creating triggers or folders, and modifying content attributes).
Users with the this role have read permission (R) to the Public security group, and read and write permission (RW) to the special Records Group security group.
-
rmaadmin (denoted by "Records Administrator" in this documentation): This role is generally assigned to administrators who are responsible for setting up and maintaining the management infrastructure and environment.
These users have the widest range of rights to perform management tasks (for example, defining users in this role to have read permission (R) to the Public security group, and read, write, delete, and write permission (RWDA) to the special Records Group security group). The Records Administrator can create variations to provide a fine level of granularity in security. In this documentation, only the default roles or Records Administrator, Records Officer, or Records User are discussed.
If Physical Content Management is enabled, the following roles are also available:
-
pcmrequestor (denoted by "PCM Requestor" in this documentation): This role is generally assigned to users who have all the permissions assigned to basic users without a PCM role but are also granted additional rights to perform some functions not allowed for basic users (for example, making reservations for physical items). Users with the 'pcmrequestor' role have read and write permissions (RW) for the special RecordsGroup security group.
-
pcmadmin (denoted by "PCM Administrator" in this documentation): This role is generally assigned to administrators who are responsible for setting up and maintaining the physical content management infrastructure and environment. These users have the widest range of rights to perform physical content management tasks (for example, setting up the storage space, editing and deleting reservations, and printing user labels). Users with the 'pcmadmin' role have read, write, delete, and admin permissions (RWDA) for the special RecordsGroup security group.
The PCM Administrator can create variations to provide a fine level of granularity in security. In this documentation, only the default roles or PCM Administrator or PCM Requestor are discussed.
If users have no PCM role assigned to them, they can still search for physical items.
Note that Physical Content Management is treated as an 'external' source, just as an adapter is treated. Therefore, if Physical Content Management is enabled, two additional roles are created. Those roles are not discussed in this documentation because the tasks associated with those roles are not discussed here but should be discussed in the appropriate adapter documentation.
-
ermrequestor: This role is generally assigned to users who can read, edit, or create content on the external source.
-
ermadmin: This role is generally assigned to administrators who can read, edit or delete content on the external source.
Each of these predefined roles comes with a default set of permissions and rights, but these can be modified to suit specific needs. New roles and management rights can be created. This functionality enables provides the opportunity for a very granular security model.
Role permissions are additive, just as in Oracle UCM. If your organization uses accounts, the accounts are a hierarchical overlay to your current security model.
Access to the majority of functions is controlled by rights assigned to user roles. The predefined management roles each have a default set of rights assigned to them, but the roles can easily be modified to restrict or expand their access to management functions (see "Assigning Rights to User Roles" for details).
To see what roles are assigned to a user, click the user name in the top upper right corner of the screen. The roles assigned to the logged-in user are displayed at the top of the User Profile information.
To see rights assigned to the logged-in user, click Records then Rights from the Top menu. The Assigned Rights Page is displayed. This screen shows the rights assigned to the current user for the enabled components. To view details about each component, click the Show link for that component.
To view details about all rights, click the Show All Rights link at the top of the screen. To hide rights again, click the Hide link in the component section or at the top of the screen.
For information about adding new roles and assigning roles to users, see the Oracle Fusion Middleware System Administrator's Guide for Content Server.
5.3 Tasks and Default Rights for Roles
If the Related Content component is enabled, the Record.CreateLink and Record.Unlink rights are set by default for users.
The ability to browse and view the retention schedule not only depends on assigned rights, but also on any other applied security features, such as supplemental markings and access control lists (ACLs). See Chapter 10, "Setting Up a Retention Schedule" for details about retention schedules. See Chapter 6, "Additional Security Settings" and "Access Control Lists (ACLs)" for further details.
The following sections give more detailed information about common tasks that can be performed and the rights required to perform each task. See each designated chapter for further details about the specific permissions required for individual tasks.
See Appendix B, "Summary of Security Rights and Roles" for this information presented in tabular form.
Important:
This section describes the default configuration. The security model is highly customizable, which means it can be modified to suit the needs of your specific environment.5.3.1 Trigger Tasks and Defaults for Predefined RM Roles
For more information about triggers, see Chapter 11, "Setting up Triggers".
-
To view information about triggers, the Admin.Triggers right or the Admin.RecordManager right is required. These rights are assigned by default to the Records Officer and Records Administrator roles.
-
To create a trigger or edit a trigger, the Admin.RecordManager right is required to perform these tasks. This right is assigned by default to the Records Officer and Records Administrator roles.
-
To delete a trigger, the Admin.Triggers right and Delete permission for the trigger's security group is required. This right is assigned by default to the Records Officer (delete permission not granted by default) and Records Administrator roles.
5.3.2 Time Period Tasks and Defaults for Predefined Roles
For more information, see Chapter 12, "Configuring Time Periods".
-
To view information about time periods, the Admin.Triggers or Admin.RecordManager is required. These rights are assigned by default to the Records Officer and Records Administrator roles.
-
To create, edit, or delete a time period, the RM Admin.RecordManager right is required. This right is assigned by default to the Records Administrator role.
5.3.3 Supplemental Markings Tasks and Defaults for Predefined Roles
For more details, see Chapter 6, "Additional Security Settings".
-
To view information about supplemental markings, the Admin.Triggers or Admin.RecordManager right is required. These rights are assigned by default to the Records Officer and Records Administrator roles.
-
To create, enable, disable, edit, or delete a supplemental marking, the Admin.RecordManager right is required. This right is assigned by default to the Records Administrator role.
5.3.4 Security Classifications Tasks and Defaults for Predefined Roles
For more information, see Chapter 6, "Additional Security Settings".
The Admin.RecordManager and Admin.SecurityClassifications rights are required to perform the following tasks involving classification. These rights are assigned by default to the Records Administrator role.
-
Enable security classification
-
Disable security classification
-
Create security classifications
-
Edit security classifications
-
Delete security classifications
-
Reorder security classifications
5.3.5 Classification Guides Tasks and Defaults for Predefined Roles
For more information, see "Classification Guides"
The Admin.ClassificationGuide right is required to perform these tasks involving classification guides. This right is assigned by default to the Records Administrator role.
-
View information about classification guides
-
Create classification guides
-
Edit classification guides
-
Delete classification guides
-
View information about classification topics
-
Create classification topics
-
Edit classification topics
-
Delete classification topics
5.3.6 Custom Security Tasks and Defaults for Predefined Roles
For more information, see Chapter 6, "Additional Security Settings".
-
To view information about custom security fields, the Admin.Triggers or Admin.RecordManager right is required. These rights are assigned by default to the Records Officer and Records Administrator roles.
-
To create, enable, disable, edit, or delete a custom security field, the Admin.RecordManager right is required. This right is assigned by default to the Records Administrator role.
5.3.7 Custom Category or Folder Metadata Tasks and Defaults for Predefined Roles
For more information, see Chapter 13, "Creating Custom Metadata".
The Admin.RecordManager right is required to perform these tasks involving custom category or folder metadata. This right is assigned by default to the Records Administrator role.
-
Create a custom category or folder metadata field
-
Edit a custom category or folder metadata field
-
Delete a custom category or folder metadata field
5.3.8 Freezes Tasks and Defaults for Predefined Roles
For more information, see Chapter 15, "Setting Up Freezes".
The Admin.RecordManager right is required to perform these tasks involving freezes. This right is assigned by default to the Records Administrator role.
-
View information about freezes.
-
Create a freeze.
-
Edit freezes.
-
Send e-mail notifications about freezes.
-
To delete a freeze, the Admin.RecordManager right and Delete permission for the freeze's security group is required. This right is assigned by default to the Records Administrator role.
5.3.9 Series Tasks and Defaults for Predefined Roles
For more information, see "Using a Series".
-
To browse/view information about series, the Series.Read right is required. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
To create a series, the RM Series.Create right is required. This right is assigned by default to the Records Administrator role.
-
To edit a series, the RM Series.Edit right is required. This right is assigned by default to the Records Administrator role.
-
To hide or unhide a series, the RM Series.Hide/Unhide right is required. This right is assigned by default to the Records Administrator role.
-
To move a series, the RM Series.Move right is required. This right is assigned by default to the Records Administrator role.
-
To delete a series, the RM Series.Delete right is required. This right is assigned by default to the Records Administrator role.
5.3.10 Retention Category Tasks and Defaults for Predefined Roles
For more information, see "Retention Categories".
-
To browse/view information about a category, the Category.Read right is required. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
To create a category, the RM Category.Create right is required. This right is assigned by default to the Records Administrator role.
-
To edit a category, the RM Category.Edit right is required. This right is assigned by default to the Records Administrator role.
-
To edit review information for a category, the RM Category.EditReview right is required. This right is assigned by default to the Records Administrator role.
-
To move a category, the RM Category.Move right is required. This right is assigned by default to the Records Administrator role.
-
To delete a category, the RM Category.Delete right is required. This right is assigned by default to the Records Administrator role.
-
To apply/reapply disposition rules to specific/all content in a retention category, the RM Category.Edit right is required. This right is assigned by default to the Records Administrator role.
5.3.11 Folder Tasks and Defaults for Predefined Roles
For more information, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The Folder.Read right is required to perform these tasks involving folders. These rights are assigned by default to all Records roles.
-
Browse and view information about record folders.
-
View the life cycle of a record folder.
-
View the review history of a record folder.
-
View the metadata history of a record folder.
The following tasks can be performed for record folders:
-
To create a folder, the Folder.Create right is required. It is assigned by default to the Records Officer and Records Administrator roles.
-
To edit a folder (if the user is the author of that folder), the Folder.EditIfAuthor right is required. It is assigned by default to the Records Officer role.
-
To edit the review information of a record folder, the Folder.EditReview right is required. It is assigned by default to the Records Officer and Records Administrator roles.
-
To delete a record folder, the Folder.Delete right is required. It is assigned by default to the Records Officer and Records Administrator roles.
-
To close/unclose a folder, the Folder.Open/Close right is required. It is assigned by default to the Records Officer and Records Administrator roles.
-
To freeze/unfreeze a folder, the Folder.Freeze/Unfreeze right is required. This right is assigned by default to the Records Administrator role.
-
To undo the cutoff of a folder, the Folder.UndoCutoff right is required. This right is assigned by default to the Records Administrator role.
-
To review a folder, the Admin.PerformPendingReviews right is required.It is assigned by default to the Records Officer and Records Administrator roles.
The Folder.Edit right is required to perform these tasks involving folders. This right is assigned by default to the Records Administrator role.
-
Edit a folder (if the user is not the author of that folder).
-
Move a record folder
-
Cancel a record folder
-
Expire a record folder
-
Rescind a record folder
-
Make a record folder obsolete
-
Undo the obsolete status of a record folder
The Category.Edit right is required to perform these tasks involving folders. This right is assigned by default to the Records Administrator role.
-
Apply a disposition rule to a specific record folder
-
Apply a disposition rule to all record folders
5.3.12 Archive Tasks and Defaults for Predefined Roles
For more information about archiving, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The Admin.RetentionSchedulesArchive and other rights for specific items in the import or export are required to import or export an archive. This right is assigned by default to the Records Administrator role.
5.3.13 Screening Tasks and Defaults for Predefined Roles
For more information about screening, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The Admin.Screening right is required to perform these tasks involving screening. This right is assigned by default to the Records Administrator role.
-
Enable/disable advanced screening
-
Screen retention categories
-
Screen record folders
-
Screen content
The Admin.RecordManager right is required to enable/disable user-friendly screening captions. This right is assigned by default to the Records Administrator role.
5.3.14 Audit Trail Tasks and Defaults for Predefined Roles
For more information about using the audit trail, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The Admin.Audit right is required to perform these tasks involving audit trails. This right is assigned by default to the Records Administrator role.
-
Configure the audit trail
-
Generate and view an audit trail
-
Search with audit trails
-
Set default metadata for checking in audit trails
-
Check in and archive audit trails (with the addition of Admin.RecordManager right)
-
Search archived audit trails
The Admin.SelectMeta right is required to select what metadata fields to include in the audit trail. This right is assigned by default to the Records Administrator role.
5.3.15 Disposition Tasks and Defaults for Predefined Roles
For more information about disposition tasks, see Chapter 14, "Defining Disposition Instructions".
The following rights are assigned by default to the Records Administrator role.
-
To view disposition information, the Category.Read right is required.
-
To enable/disable user-friendly disposition captions, the Admin.RecordManager right is required.
-
To create disposition rules, the Category.Create right is required.
-
To edit disposition rules, the Category.Edit right is required.
-
To delete disposition rules, the Category.Delete right is required.
5.3.16 Link Tasks and Defaults for Predefined Roles
For more information about linking and link types, see the Oracle Fusion Middleware User's Guide for Universal Records Management.
The Admin.ConfigureLinkTypes right is required to perform these tasks involving links. This right is assigned by default to the Records Administrator role.
-
Add custom link types
-
Edit custom link types
-
Delete custom link types
To create or remove links between content items, the Record.CreateLink or Record.Unlink right is required. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
5.3.17 Default Report Tasks and Defaults for Predefined Roles
For more information about reports, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management .
The Admin.Reports right is required to perform these tasks. This right is assigned by default to the Records Administrator role.
-
Create a user/group report
-
Create a role report
-
Create a group report
5.3.18 Content Management Tasks and Defaults for Predefined Roles
For more information about managing content, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The Record.Read right is required to perform these tasks. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
Download an item for viewing
-
Search for content items
-
View information about a content item
-
View the life cycle of a content item
-
View the review history of a content item
-
View the metadata history of a content item
-
View the classification history of a content item
The Record.Edit right is required to perform these tasks involving content. This right is assigned by default to the Records Officer and Records Administrator roles.
-
Review the classification of a content item
-
Cancel a content item
-
Expire a content item
-
Rescind a content item
-
Make a content item obsolete
-
Undo the obsolete status of a content item
-
Remove a supplemental marking from a content item
-
Move an item to another category or folder.
The following rights are required to perform the following tasks:
-
To edit metadata before a cutoff, the Record.UndoCutoff right is required. Users can edit metadata for content items after cutoff and before cutoff. It is assigned by default to the Records Administrator role.
-
To upgrade or downgrade the security classification of an item, the Record.Upgrade/Downgrade right is required. It is assigned by default to the Records Officer and Records Administrator roles.
-
To review a content item, the Admin.PerformPendingReviews right is required. This right is assigned by default to the Records Officer, Records User and Records Administrator roles.
-
To undo the cutoff of a content item, the Record.UndoCutoff right is required. It is assigned by default to the Records Administrator role.
-
To undo the status of a content item, the Record.UndoRecord right is required. It is assigned by default to the Records Administrator role.
-
To edit the review information for a content item, the Record.EditReview right is required. This right is assigned by default to the Records Officer, Records User, and Records Administrator roles.
-
To delete the metadata history of a content item, the Record.DeleteHistoryFile right is required. This right is assigned by default to the Records Officer and Records Administrator roles.
-
To create or check in a content item, the Record.Create right is required. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
To link or unlink content items, the Record.CreateLink or Record.Unlink right is required. This right is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
To delete a content item, the Record.Delete right is required. This right is assigned by default to the Records Administrator role.
-
To freeze or unfreeze a content item, the Record.Freeze/Unfreeze right is required. This right is assigned by default to the Records Administrator role.
5.3.19 Customization Tasks
The Rma.Admin.Customization right is required to perform the following tasks. This right is not assigned by default to any role. A detailed knowledge of services and their uses is required to perform these tasks. See Appendix C, "Customizing Your System" for more details.
-
Define custom dispositions
-
Define custom barcode actions
-
Define custom reports
5.4 Common Physical Content Management Tasks and Roles
Access to the majority of Physical Content Management (PCM) functions is controlled by rights assigned to Oracle UCM or Oracle URM roles. The two predefined physical content management roles (PCM Requestor and PCM Administrator) each have a default set of rights assigned to them, but the roles can easily be modified to restrict or expand their access to physical content management functions. New roles can be created with specific physical content management rights assigned to them.
5.4.1 Storage Space Tasks and Defaults for Predefined Roles
For more information about storage, see Chapter 9, "Setting Up PCM Storage Space".
The following rights are required to perform the following tasks:
-
To view information about storage locations, the PCM.Storage.Read right is required. It is assigned by default to the PCM Requestor and PCM Administrator roles.
-
To create individual storage locations, the PCM.Storage.Create right is required. This right is assigned by default to the PCM Administrator role.
-
To create storage locations in batches, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
-
To edit storage locations, the PCM.Storage.Edit right is required. This right is assigned by default to the PCM Administrator role.
-
To delete storage locations, the PCM.Storage Delete right is required. This right is assigned by default to the PCM Administrator role.
-
To reserve storage locations, the PCM.Storage.Reserve right is required. This right is assigned by default to the PCM Requestor and PCM Administrator roles.
-
To block storage locations, the PCM.Storage.Block right is required. This right is assigned by default to the PCM Administrator role.
-
To print labels for storage locations, the PCM.Admin.PrintLabel right is required. This right is assigned by default to the PCM Administrator role.
-
To import batch-created storage hierarchy, the Admin.RetentionScheduleArchive right is required. This right is not assigned by default to any predefined role.
5.4.2 Reservation Tasks and Defaults for Predefined Roles
For more information about reservations, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights are required to perform the following tasks:
-
To view reservation information about physical items, the PCM.Reservation.Read right is required. This right is assigned by default to the PCM Requestor and PCM Administrator roles.
-
To create a reservation request, the PCM.Reservation.Create right is required. This right is assigned by default to the PCM Requestor and PCM Administrator roles.
-
To edit a reservation request, the PCM.Reservation.Edit right is required. This right is assigned by default to the PCM Administrator role.
-
To delete a reservation request, the PCM.Reservation.Delete right is required. This right is assigned by default to the PCM Administrator role.
-
To process a reservation request, the PCM.Reservation.Process right is required. This right is assigned by default to the PCM Administrator role.
-
To run request reports, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
-
To configure default metadata for reservations, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
5.4.3 Physical Item Tasks and Defaults for Predefined Roles
For more information about physical items, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights are required to perform the following tasks:
-
To view information about physical items, the PCM.Physical.Read right and PCM.Storage.Read rights are required. These rights are assigned by default to the PCM Requestor and PCM Administrator roles.
-
To create (check in) physical items, the PCM.Physical.Create and PCM.Storage.Read rights are required. These rights are assigned by default to PCM Requestor and PCM Administrator roles.
-
To edit physical items, the PCM.Physical.Edit and PCM.Storage.Read rights are required. These rights are assigned by default to PCM Requestor and PCM Administrator roles.
-
To move physical items, the PCM.Physical.Edit, PCM.Physical.Move, and PCM.Storage.Read rights are required. These rights are assigned by default to the PCM Administrator role.
-
To delete physical items, the PCM.Physical.Delete and PCM.Storage.Read rights are required. These rights are assigned by default to the PCM Administrator role.
-
To search for physical items, the PCM.Physical.Read and PCM.Storage.Read rights are required. These rights are assigned by default to the PCM Requestor and PCM Administrator roles.
-
To print labels for physical items, the PCM.Admin.PrintLabel right is required. This right is assigned by default to the PCM Administrator role.
-
To freeze or unfreeze physical items, the Record.Freeze/Unfreeze right is required. This right is not assigned by default to any role.
-
To manually override external freeze errors, the Admin.PerformActions right is required. This right is not assigned by default to any role.
-
To screen for physical items, the Admin.Screening right is required. This right is not assigned by default to any role.
5.4.4 Location, Object, and Media Types Tasks and Defaults for Predefined Roles
For more information about locations, objects, and media, see Chapter 8, "Configuring Physical Content Management".
The following rights are required to perform the following tasks:
-
To set up location types, the PCM.Admin.Manager and PCM.Admin.LocationTypes rights are required. These rights are assigned by default to the PCM Administrator role.
-
To set up object types, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
-
To set up media types, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
-
To set up custom metadata fields, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
5.4.5 Chargeback Tasks and Defaults for Predefined Roles
For more information about chargebacks, see Chapter 8, "Configuring Physical Content Management" and the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights are required to perform the following tasks:
-
To set up chargeback types, payment types, and customers, the PCM.Admin.Manager and CBC.ChargeBacks.Admin rights are required. These rights are assigned by default to the PCM Administrator role.
-
To view information on chargeback-related items (transactions, invoices, and so on), the PCM.Admin.Manager, CBC.ChargeBacks.Admin, and CBC.ChargeBacks.Read rights are required. These rights are assigned by default to the PCM Administrator role.
-
To create chargeback-related items (transactions, invoices, and so on), the PCM.Admin.Manager, CBC.ChargeBacks.Admin, and CBC.ChargeBacks.Read rights are required. These rights are assigned by default to the PCM Administrator role.
-
To edit chargeback-related items (transactions, invoices, and so on), the PCM.Admin.Manager, CBC.ChargeBacks.Admin, and CBC.ChargeBacks.Edit rights are required. These rights are assigned by default to the PCM Administrator role.
-
To delete chargeback-related items (transactions, invoices, and so on), the PCM.Admin.Manager, CBC.ChargeBacks.Admin, and CBC.ChargeBacks.Delete rights are required. These rights are assigned by default to the PCM Administrator role.
-
To screen for charges, the PCM.Admin.Manager and CBC.ChargeBacks.Admin rights are required. These rights are assigned by default to the PCM Administrator role.
-
To browse invoices, the PCM.Admin.Manager and CBC.ChargeBacks.Admin rights are required. These rights are assigned by default to the PCM Administrator role.
-
To print invoices, the PCM.Admin.Manager and CBC.ChargeBacks.PrintInvoice rights are required. These rights are assigned by default to the PCM Administrator role.
-
To adjust invoices (for example, to manually change invoice amounts), the PCM.Admin.Manager and CBC.ChargeBacks.Adjust rights are required. These rights are not assigned by default to any role.
5.4.6 Barcode and Label Tasks and Defaults for Predefined Roles
For more information about barcodes, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights are required to perform the following tasks:
-
To process barcode files, the PCM.Barcode.Process right is required. This right is assigned by default to the PCM Administrator role.
-
To print labels for users, the PCM.Admin.PrintLabel right is required. This right is assigned by default to the PCM Administrator role.
-
To print storage location labels, the PCM.Admin.PrintLabel right is required. This right is assigned by default to the PCM Administrator role.
-
To print physical location labels, the PCM.Admin.PrintLabel right is required. This right is assigned by default to the PCM Administrator role.
5.4.7 Additional PCM Administrative Tasks and Defaults for Predefined Roles
For more information about PCM administration, see Chapter 8, "Configuring Physical Content Management".
The following rights are required to perform the following tasks:
-
To configure the environment, including enabling or disabling the use of Offsite Storage, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
-
To run batch services, the PCM.Admin.Manager right is required. This right is assigned by default to the PCM Administrator role.
5.5 External Source Management Tasks and Roles
The following tasks and roles are used when managing external sources (adapters).
5.5.1 External Source Tasks and Defaults for Predefined Roles
For more information about adapters, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights are required to perform the following tasks:
-
To read external items, the ECM.External.Read right is required. This right is assigned by default to the ERM Requestor and ERM Administrator roles.
-
To create an external item, the ECM.External.Create right is required. This right is assigned by default to the ERM Requestor and ERM Administrator roles.
-
To edit an external item, the ECM.External.Edit right is required. This right is assigned by default to the ERM Administrator role.
-
To delete an external item, the ECM.External.Delete right is required. This right is assigned by default to the ERM Administrator role.
-
To perform administrative functions involving the external source, the ECM.External.Admin right is required. This right is assigned by default to the ERM Administrator role.
5.6 Security Groups
A security group defines security for a group of content. Oracle URM is shipped with a predefined security group called "RecordsGroup." This group defines security for a group of content designated as that being tracked and/or retained.
Users with the predefined Records User, Records Officer, or Records Administrator roles have read and write permission (RW) to the RecordsGroup security group. Users with the Records Administrator role have read, write, delete, and admin permission (RWDA) to this security group.
Note:
Even though the default Records User and Records Officer roles appear to be identical, they are not. The default Records Officer role has subadministrator access to certain administrator functions that the default Records User role does not (for example, creating triggers and folders). For details about rights that can be assigned to roles, see "Tasks and Default Rights for Roles".5.7 Aliases
When the product software is enabled, several aliases are created to help administrators manage large groups of people. Although the aliases are created, no default users are added to those groups. An administrator should add users as needed to the following alias lists:
-
OffSiteRequestReviewGroup
-
ReservationGroup
-
DispositionReviewGroup
Several default aliases are also created if the FOIA/PA functionality is enabled. Default users are added to those alias lists but the users themselves are not created automatically. An administrator will need to create those users and assign appropriate permissions to them:
-
FOIAOfficers
-
FOIAProcessors
-
FOIASpecialists
-
JAG
5.8 Access Control Lists (ACLs)
Important:
Enabling or disabling ACLs affects existing ACL settings system-wide. For example, if ACLs are enabled in Oracle UCM and Oracle URM is configured to one of the DoD settings (which re-enables ACLs), the Oracle UCM ACLs are overridden. And if the Typical or Minimal Oracle URM settings are used, ACLs are disabled because ACL-based security is not enabled by default for those options. It is enabled by default for the DoD options.Access control lists (ACLs) are intended to manage the security for dispositions. ACLs can be assigned to the following retention schedule components:
-
triggers
-
retention categories
-
record folders
ACLs can be used to control user and group access permissions for triggers, categories, and record folders. ACLs can be assigned for each category, folder, and trigger.
Be aware that searching for items takes more time when using ACLs because the permissions are checked on all parent folders and categories.
If not required, consider disabling ACLs for faster search retrieval performance. The default security, custom security fields, and supplemental markings provide excellent security.
5.8.1 Setting ACLs During Software Use
ACLs for individual users and groups and aliases can be adjusted while setting up elements of Oracle URM. Not all procedures allow the setting of all three types of permissions. The following procedure can be followed to adjust ACLs regardless of which type of permission are being set (user, group, or alias).
-
In the Group, User, or alias permission section of the Access Control Edit Section of the page in use, begin typing the user name of the person to add. A list appears and the user can be selected. Or type two asterisks (**) in the name field or group field. A list of users and groups appears.
-
Scroll to the name to use and click Add User, Add Alias or Add.
-
To the right of the displayed name is a grouping of permissions. Click on a permission to add or remove it.
-
To remove a user or group from the permissions box, click the X next to the name.
5.9 Security Matrix
The table below shows a matrix of content and retention schedule components, and the corresponding permissions for each predefined role. Supplemental markings have the most restrictive access capabilities. See Chapter 6, "Additional Security Settings" for details.
| Objects and Retention Schedule Components | Subject to Additional Security of Type | Records User (rma) | Records Officer (recordsofficer) | Records Administrator (rmaadmin) |
|---|---|---|---|---|
| Content Items | Rights; supplemental markings; custom security field; ACLs | RW | RW | RWDA |
| Folders | Rights; supplemental markings; ACLs | R | RWD | RWD |
| Categories | Rights; supplemental markings; ACLs | R | R | RWD |
| Series | Rights | R | R | RWD |
| Triggers | Rights; ACLs | RW
RWD permission required to delete triggers. |
RWDA
Only custom triggers can be deleted. |
|
| Periods | Rights | R | RWD
Only custom periods can be deleted. |
|
| Supplemental markings | Rights | RWD | ||
| Classification guides | Rights | RWD |
5.10 Setting Security Preferences
Security preferences are set on the Configure Retention Settings Page. The security preferences set on that page are in addition to those provided with Oracle UCM. The available security depends on what type of installation was chosen (for example, Minimal or a DoD setting).
Important:
After your production environment is underway, it is recommended that you do not change the security settings for ACLs or the default security.To configure security settings, complete the following steps:
-
Click Records then Configure from the Top menu. Click Retention then Settings.
The Configure Retention Settings Page is displayed. If necessary, click the plus icon (+) to expand the Security section on the page.
-
(Optional based on the security model): To make use of Access Control List Security, click the ACL-based security box.
-
(Recommended): To activate the default security inherent in Universal Content Management for extra security on categories, folders, and triggers, click the Default Content Server security on Categories, Folders, and Triggers box. To not set the additional security, clear the box.
-
(Required for DOD 5015.2 compliance): To use supplemental markings, click the Supplemental Marking box.
-
(Optional based on the security model): To make users match all supplemental markings on a record folder, click the User must match all Supplemental Markings box. This is the most restrictive setting for supplemental markings. To allow a user to match only one supplemental marking to a folder to access its content or a content item (in the case of multiple supplemental markings), clear the box. For more information, see "Supplemental Markings Details".
-
(Optional): To create custom security fields at the content field level to further restrict users, click the Custom Security Fields box. To not use custom security fields, clear the box.
-
(Optional): To use classified security, click the Classified Security box. To not use classified security fields, clear the box. For more information, see "About Records Classification".
-
Click Submit Update. A message is displayed saying the settings have been configured successfully.
5.11 Assigning Rights to User Roles
The system is shipped with several predefined roles. Each of these roles has several default rights, which define what users with that role are allowed to do. For further details about roles and their default rights, see "Tasks and Default Rights for Roles" and "Common Physical Content Management Tasks and Roles".
5.11.1 Setting Rights for Roles
Rights define what actions users are allowed to perform. To assign rights to user roles, complete the following steps:
-
Click Admin Applets from the Administration menu.
The Administration Applets for the server are displayed.
-
Click the User Admin icon.
The User Admin utility starts.
-
Choose Security then Permissions by Role from the menu.
-
Select the role to review or modify. Click Edit RMA Rights or Edit ECM Rights for PCM.
The appropriate Edit Rights Page is displayed.
-
Set the rights by selecting or clearing the boxes on the various tabs.
-
Click OK when done.
-
Click Close to exit the Permissions by Role screen.
5.12 Default Rights for Roles
This section describes the features of the Edit Rights screen, and the default rights for each of the predefined roles.
Some of the rights are interconnected. Enabling or disabling certain options automatically enables or disables other options. For example, if you disable the Record.Create option on the Record tab, some of the other options on that tab are disabled as well. Conversely, if you enable the Category.Create option on the Category tab and the Category.Read option is not yet enabled, it will be enabled automatically.
5.12.1 The Series Tab
For more information, see "Using a Series".
The following rights appear on the Series tab of the Edit Rights Page:
-
Read: allows the user to view information about a series. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role.
5.12.2 The Category Tab
For more information, see "Retention Categories".
The following rights appear on the Category tab of the Edit Rights Page.
-
Read: allows the user to view information about a retention category. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role:
5.12.3 Folder Tab
For more information about folders, see the Oracle Fusion Middleware Administrator's Guide for Universal Records Management.
The following rights appear on the Folder tab of the Edit Rights Page:
-
Read: allows the user to view information about a folder. It is assigned by default to the Records User, Records Officer, and Records Administrator roles.
-
EditIfAuthor: allows a user to edit a folder, but only if the user is the author of that folder. It is not assigned by default to any role.
The following rights are assigned by default to the Records Officer and Records Administrator roles:
The following rights are assigned by default to the Records Administrator role:
5.12.4 Record Tab
The following rights appear on the Record tab of the Edit Rights Page. These rights are assigned by default to the Records User, Records Officer, and Records Administrator roles:
-
CreateLink: allows the user to link content items. See the Oracle Fusion Middleware User's Guide for Universal Records Management for details.
-
Create: allows a user to create content or check it in to the retention schedule. For details, see the Oracle Fusion Middleware User's Guide for Universal Records Management.
-
Unlink: allows a user to unlink content. See the Oracle Fusion Middleware User's Guide for Universal Records Management for details.
The following rights are assigned by default to the Records Officer, Records User, and Records Administrator roles:
-
Edit: allows the user to edit content, including moving, canceling, expiring, rescinding, making obsolete, and reviewing.
-
EditReview: allows a user to edit content that is subject to review.
-
DeleteHistoryFile: allows a user to delete the metadata history file of content. This box is only available if the 'Classified Security' option has been enabled.
-
Upgrade/Downgrade: allows a user to upgrade and downgrade the security classification of content. This box is only available if the 'Classified Security' option has been enabled on the Configure Retention Settings Page.
The following rights are assigned by default to the Records Administrator role:
5.12.5 Admin Tab
The following rights appear on the Admin tab of the Edit Rights Page.
-
PerformPendingReviews: allows a user to perform pending reviews. This right is assigned by default to the Records Officer, Records User, and Records Administrator roles. See the Oracle Fusion Middleware Administrator's Guide for Universal Records Management for more details.
-
PrivilegedEnvironment: allows a user to set the declassification time frame (see "Setting the Declassification Time Frame"). This right is assigned by default to the Records Officer and Records Administrator roles. This box is only available if the 'Classified Security' option has been enabled on the Configure Retention Settings Page.
-
ClassificationGuide: allows a user to work with classification guides. This right is assigned by default to the Records Officer and Records Administrator roles.
-
Triggers: allows the user to work with global triggers, custom direct triggers, and indirect triggers. See Chapter 11, "Setting up Triggers". To delete a trigger, Delete permission (D) for the trigger's security group is also required. This right is assigned by default to the Records Officer and Records Administrator roles.
-
ShareFavorites: allows users to share the contents of their Favorites list with other users. This right is assigned by default to the Records Officer and Records Administrator roles.
The following rights are assigned by default to the Records Administrator role:
-
RecordManager: allows a user to configure several settings and also set up and administer periods, supplemental markings, security classifications, custom security fields, custom category and folder metadata fields, classification guides and freezes.
-
Screening: allows a user to screen retention categories, folders, and content.
-
PerformActions: allows a user to process content assignments.
-
SelectMeta: allows a user to specify metadata fields to be audited.
-
RetentionScheduleArchive: allows a user to import and export a retention schedule archive.
-
SelectAuthor: allows a user to select a different filer (author) for a category than him/herself.
-
ConfigureLinkTypes: allows a user to manage custom content links.
-
AllowDispositionUpgrade/Downgrade: allows a user to perform upgrade and downgrade classification actions.
See the Oracle Fusion Middleware Administrator's Guide for Universal Records Management for more details about screening, creating reports, audits, archives, and configuring link types.
The following rights are not assigned by default to any role.
-
NoPostFilterSearch: allows users to unfilter search results. The results include content the user has no access to based on security classifications, supplemental markings, custom security fields, and ACLs. If the user has no access to a content item in the search results, clicking on it results in an "access denied" error. By enabling this option, search queries are executed much faster because no complex post-filtering must be performed.
Users with this right can still only access content items they have been explicitly granted access privileges to based on security groups and accounts. They will see other results in the search results list, but cannot access them. However, they will see some metadata information about the content item (for example, their title), which may interfere with an organization's security model.
-
NoSecurity: allows users to become "immune" to security classifications, supplemental markings, custom security fields, and ACLs. Their access to content is unrestricted by these security features. In addition, this option turns off search post-filtering, so search results include content the user has not been explicitly granted access to. For example, a user would have access to content marked as "Top Secret" even if that security classification has not been assigned to the user. This right can be used to give sysadmins the privilege to access every content item in the system.
Access to content items continues to be restricted by security groups and accounts.
-
CustomDispositionActions: allows users to define custom disposition actions or to delete any disposition action. See Appendix C, "Customizing Your System" for details.
-
SecurityClassifications: new installs only. If enabled (with the Admin.RecordManager option), the user is allowed to set up security classification levels. See "Security Classifications". This box is only available if the 'Classified Security' option has been enabled.
-
GetAllFilePlan: allows a user to get all series, categories, and folders when the GET_FILE_PLAN_ALL service is called. Without this right, inaccessible objects are excluded. The service is typically used by Oracle URM Adapters.
Important:
When a user has Admin permission to a security group but does not have the Admin.SelectAuthor right, the user is still able to select an author at checkin. The Admin.SelectAuthor right is used only to add that functionality to a user who does not have Admin permission to a group.5.12.6 CBC Tab
Chargebacks are used with Physical Content Management, which is only available when that software is enabled.
The following rights are assigned by default to the PCM Administrator role:
-
ChargeBacks.Read: allows the user to view information about chargeback-related items (transactions, invoices, and so on).
-
ChargeBacks.Create: allows a user to create chargeback-related items.
-
ChargeBacks.Edit: allows a user to edit chargeback-related items.
-
ChargeBacks.Delete: allows users to delete chargeback-related items.
-
ChargeBacks.MarkPaid: allows users to mark invoices as paid.
-
ChargeBacks.Adjust: allows users to manually adjust invoices.
-
ChargeBacks.Admin: allows users to perform administrative tasks such as define new payment types, define customers, and so on.
5.12.7 PCM Tab
The following rights are assigned by default to the PCM Requestor and PCM Administrator roles:
-
Physical.Read: allows the user to view information about physical items.
-
Storage.Read: allows users to view information about a storage location.
-
Storage.Reserve: allows users to reserve a storage location.
-
Reservation.Read: allows users to view information about reservations.
The following rights are assigned by default to the PCM Administrator role only:
-
Physical.Move: allows users to move a physical item (change the location)
-
Storage.Edit: allows users to edit an existing storage location.
-
Storage.Block: allows users to block or unblock a storage location.
-
Reservation.Process: allows users to process reservations by modifying the status of request items.
-
Admin.Manager: allows a user to access all of PCM's administrative functions.
-
Admin.Location.Types: allows users to configure location types, providing the user also has the Admin.Manager right.
-
Admin.PrintLabel: allows users to generate labels for users, locations, and physical items.
5.13 Specifying PCM Barcode Values for Users
Barcodes are used with Physical Content Management, which is only available when that software is enabled.
By default, the barcode value for a user consists of a user's login name in all upper-case letters, for example 'JSMITH' or 'MJONES'. If you do not want to use the login name of a user as the barcode value, use the User Admin utility to specify a different value for the user.
This is especially useful for login names containing characters other than the basic letters (a-z, A-Z) or numbers (0-9) (for example, accented letters such as 'kmüller'). By default, the barcode values generated for such users include hexadecimal representations of the accented letters (for example, 'KMC39CLLER'). To avoid this behavior set specific barcode values for these users (for example, 'KMULLER'), which are then used rather than the (converted) user login names.
You can run the Update Users with no Barcode batch service to automatically set the barcode values for all users who currently do not have a barcode value. This is useful for users who are already in the system before Physical Content Management was enabled. The barcode values are set in accordance with the rules above.
To manually set a specific barcode value for a user, complete the following steps:
-
Log in as an administrator.
-
Click Administration then click Admin Applets.
-
Click the User Admin icon.
The User Admin utility is started.
-
On the Users tab, select the user whose barcode value should be set and click Edit.
The Edit User dialog is displayed.
-
In the Barcode field, specify a unique value for the user. This value will be used in the barcode label for the user rather than the user's login name (in all upper-case letters) as specified in the Name field.
The specified value must be unique for each user in the system. An error message will be displayed if a value is used that is not unique.
Do not use any accented letters in the barcode value (an error message is displayed if you try). Also, any lower-case letters are automatically converted to upper case after clicking OK.
-
Click OK when finished.
-
Close the User Admin utility.