4 Configuring Request Filtering
This chapter introduces the request filters provided by Oracle Web Cache and explains how you can enable them to protect against common HTTP request attacks.
This chapter includes the following topics:
-
Section 4.5, "Configuring Rules for the Privileged IP Filter"
-
Section 4.6, "Configuring Rules for the Client IP Request Filter"
-
Section 4.7, "Configuring Rules for the Method Request Filter"
-
Section 4.9, "Configuring Rules for the Header Request Filter"
-
Section 4.10, "Configuring Rules for the Query String Request Filter"
-
Section 4.11, "Configuring Rules for the Format Request Filter"
-
Section 4.13, "Monitoring Statistics for Request Filter Types and Rules"
4.1 Introduction to Request Filtering
Oracle Web Cache provides request filters to filter incoming HTTP or HTTPS requests to configured sites on the origin server.
Request filtering aids administrators in controlling access to Web sites:
-
The planting of malicious code within the Web site that, when executed by a user, steals the user's identity or personal information
-
Attacks that try to exploit software vulnerabilities in the site that enable the attacker to execute arbitrary code on the application server.
-
Attacks that try to render a Web site unusable by bombarding it with extremely high volumes of bogus requests that effectively consume the application server resources or bandwidth thereby preventing access for other users.
In addition, request filtering controls which clients and requests are allowed to access to a Web site or certain parts of a Web site.
To defend against Web site attacks, you can enable a series of filters that each request must pass through before being processed. Each filter is composed of customizable rules that can either identify the requests to allow or deny.
You can configure filters and filter rules for specific sites or undefined sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
The requests filters are processed in the order presented in the Request Filter Summary page. To access this page:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
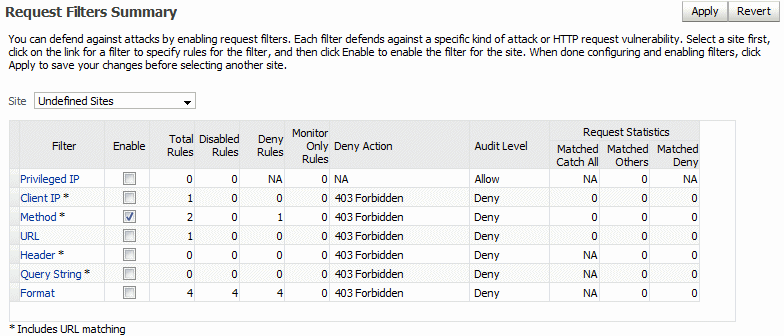
Description of the illustration request_sum.gif
You select an individual filter from the Filter column, and specify individual rules for the filter. When configuring rules, you order the rules based on the order you want Oracle Web Cache to match requests. When ordering caching rules, give allow rules a higher priority than deny rules.
After configuring rules for a filter and enabling or disabling the rules, you return to the Request Filters Summary page to enable the filters. If you do not click Enable for a filter, then you are disabling the rule, which means Oracle Web Cache ignores any configured rules for that filter.
4.2 Types of Request Filters
Oracle Web Cache provides the following filters, each designed to focus on a particular type of HTTP request vulnerability.
The privileged IP filter permits allow-only rule; the header, query string, and format filters permit deny-only rules; and the client IP, method, and URL filters permit both allow and deny rules. Because the list of rules in the header, query string, and format filters are independent of each other, permitting allow rules could result in the skipping of other deny rules. Therefore, these filters only permit deny rules.
The privileged IP filter enables Oracle Web Cache to bypass the other request filters. You use this filter to allow specified privileged IP addresses access.
The client IP filter allows or denies site access to specific IP addresses.
It enables Oracle Web Cache to restrict access to a site URL prefix within the site to only certain IP addresses. This filter restricts clients from certain IP addresses from launching attacks on a system. Not restricting access could allow clients access to the application or to areas of the site that contain sensitive information. An attacker from a certain IP address can continue making malicious attacks if Oracle Web Cache does not deny access.
You can configure a black list by denying requests if the IP address and URL match or a white list if the IP address and URL match.
The method filter allows or denies site access based on the HTTP request method. For example, if only GET and POST methods are allowed, Oracle Web Cache would refuse all other requests.
This filter protects against clients attempting to read restricted files or modifying files using various HTTP methods. In addition to the HTTP request method, you can configure a URL to limit the rule to only requests that match the method and the specified URL.
The URL filter allows or denies site access based on a URL.
This filter protects against Internet attacks to an application server through a specific URL.
The header filter denies site access based on HTTP header values. In addition to the HTTP header value, you can configure a URL to limit the rule to only requests that match the header value and the specified URL.
Incoming requests matching the HTTP header and URL are compared to the expression in the rule. The expression can be either a substring or a regular expression. For both substring and regular expression comparisons, a rule can deny requests in which the request's header value matches the rule's value expression.
This filter protects against clients attempting to break into an application by manually creating header values and clients submitting unwanted content in header values.
The query string filters denies site access based on query string parameters. For a POST request, Oracle Web Cache checks both the query string, if is present, and the POST body. In addition to the query string, you can configure a URL to limit the rule to only requests that match the query string and the specified URL.
Incoming requests matching the query string and URL are compared to the expression in the rule. The expression can be either a substring or a regular expression. For both substring and regular expression comparisons, a rule can deny requests in which the request's query string matches the rule's value expression.
This filter protects against clients attempting to break into a site by manually manipulating the query string parameters and values and clients submitting unwanted content within parameter values.
The format filter denies site access based on the format of the HTTP request. This filter checks for embedded null byte characters, strict encoding and valid Unicode, and double URL encoding. Oracle Web Cache checks the format for each enabled type and denies the request if the format is invalid.
This filter checks the components of the URL, including the path, filename, query string, and for POST requests, the request entity body. It protects against hackers attempting to disrupt a Web application by either sending a request which is not well formed or sending characters not expected to be in the URL.
4.3 About Learned Rules
Oracle Web Cache automatically creates learned rules for the method and URL filters. You can then choose to activate these learned rules.
Client requests that match the filter's Catch All rule are evaluated to see if there is some commonality to them that might warrant a new rule. These common patterns are shown as learned rules. You can then chose to activate or ignore these learned rules. After a rule is activated in the configuration, you can select to enable or disable it just like any other rule. Even if you select not to activate learned rules, Oracle Web Cache continues to collect and evaluate all common patterns for requests that fall into the Catch All rule.
See Section 4.7.1 and Section 4.8.1 to enable learned rules.
4.4 About the Monitor Only Mode
When you configure rules for the filters, you can select the Monitor Only option. When you enable this option for a rule, Oracle Web Cache treats the rule as if it was disabled. However, Oracle Web Cache tracks matches in the statistics and writes them to the event log (if verbosity is set to TRACE or higher) and to the audit log if audit logging is enabled for the match action.
When monitoring is enabled, requests are allowed, so you can examine results in the Request Statistics section. When you disable Monitor Only for a deny rule, the deny action is enforced. You typically set Monitor Only on to see the match activity of the rule. When results are expected, then disable Monitor Only to enforce the rule's action.
4.5 Configuring Rules for the Privileged IP Filter
The privileged IP request filter enables Oracle Web Cache to bypass all request filters for certain privileged IP addresses. Any request from a privileged IP address does not pass through the other request filters.
See Section 4.2 for further information about the privileged IP request filter.
To configure the privileged IP request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Privileged IP link.
The Privileged IP Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in the audit log for the request filter.
-
-
Click Create to create a row in the table.
-
In the IP Address field, enter the IP address, either as an IP version 4 or IP version 6 address mask of the client.
See Section 2.5 for examples of IP addresses.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 6 for any additional rules.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Privileged IP row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.6 Configuring Rules for the Client IP Request Filter
This client IP request filter restricts application access to specific IP addresses or range of IP addresses. Not restricting access enables access to restricted information and potential attackers from particular IP addresses.
See Section 4.2 for further information about the client IP request filter.
To configure rules for the client IP request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Client IP link.
The Client IP Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in the audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
Create a new rule:
-
Click Create to create a row in the table.
-
In the IP Address field, enter the IP address, either as an IP version 4 or IP version 6 address mask of the client.
See Section 2.5 for examples of IP addresses.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
In the URL field, based on the URL Type you select, enter an optional URL string. If no URLs are specified, then all requests are checked. It is equivalent to specifying a URL with a prefix /.
- Path Prefix: Enter the path prefix of the objects. Start the path with
/; do not start the path withhttp://host_name:port/. The prefix is interpreted literally, including reserved regular expression characters. These characters include periods (.), question marks (?), asterisks (*), brackets ([]), curly braces ({}), carets (^), dollar signs ($), and backslashes (\).- File Extension: Enter the file extension. Because Oracle Web Cache internally starts the file extension with a period (.), it is not necessary to enter it.
- Regular Expression: Enter the regular expression of the objects. Remember to use "^" to denote the start of the URL and "$" to denote the end of the URL.
-
From the URL Type list, select an option to determine how the rule's URL is compared to the request's URL:
- Path Prefix: Select to allow or deny access to requests matching a path prefix.
- File Extension: Select to allow or deny access to requests matching a particular file extension.
- Regular Expression: Select to allow or deny access to requests matching regular expression syntax.
-
Click the Case Insensitive Match check box to match requests regardless of the case. If you do not select this check box, the rule bases the match on the case.
-
Click the Allow check box for Oracle Web Cache to allow requests matching the IP address and URL fields; deselect the check box for Oracle Web Cache to deny requests matching the IP address and URL fields.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 7 for any additional rules.
-
Modify the Catch All rule, keeping in mind it is applied to all requests that do not match a defined rule.
Oracle recommends creating allow rules, followed by a Catch All deny rule.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Client IP row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.7 Configuring Rules for the Method Request Filter
The method request filter enables Oracle Web Cache to restrict access based on the HTTP request method.
See Section 4.2 for further information about the method request filter.
To configure rules for the method request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Method link.
The Method Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in the audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
In the Defined Rules section, create a new rule:
-
Click Create to create a row in the table.
-
In the Method field, enter the HTTP request method, such as GET, POST, or PUT.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
In the URL field, based on the URL Type you select, enter an optional URL string. If no URLs are specified, then all requests are checked. It is equivalent to specifying a URL with a prefix /.
- Path Prefix: Enter the path prefix of the objects. Start the path with
/; do not start the path withhttp://host_name:port/. The prefix is interpreted literally, including reserved regular expression characters. These characters include periods (.), question marks (?), asterisks (*), brackets ([]), curly braces ({}), carets (^), dollar signs ($), and backslashes (\).- File Extension: Enter the file extension. Because Oracle Web Cache internally starts the file extension with a period (.), it is not necessary to enter it.
- Regular Expression: Enter the regular expression of the objects. Remember to use "^" to denote the start of the URL and "$" to denote the end of the URL.
-
From the URL Type list, select an option to determine how the rule's URL is compared to the request's URL:
- Path Prefix: Select to allow or deny access to requests matching a path prefix.
- File Extension: Select to allow or deny access to requests matching a particular file extension.
- Regular Expression: Select to allow or deny access to requests matching regular expression syntax.
-
Click the Case Insensitive Match check box to match requests regardless of the case. If you do not select this check box, the rule bases the match on the case.
-
Select the Allow check box for Oracle Web Cache to allow requests matching the method and URL fields; deselect the check box for Oracle Web Cache to deny requests matching the method and URL fields.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 7 for any additional rules. You can also add learned rules, as described in Section 4.7.1.
-
Modify the Catch All rule, keeping in mind it is applied to all requests that do not match a defined rule.
Oracle recommends creating allow rules, followed by a Catch All deny rule.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Method row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.7.1 Activating Learned Rules for the Method Request Filter
See Section 4.3 for further information about how learned rules are collected from the Catch All rule. You can add learned rules to the method request filter.
To enable learned rules for the method request filter:
-
Navigate to the Method Request Filter page.
-
In the Learned Rules section, if you see that some learned rules have been suggested, monitor the statistics for these rules by watching this page for awhile. When you decide that one or more learned rules make sense, proceed.
If no learned rules display under Catch All Rule, then there are no learned rules.
-
Select the row, and click Add Rule to Defined Rules to activate the rule and move it the Defined Rules section.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
-
Click Apply to save the configuration for the request filter.
4.8 Configuring Rules for the URL Request Filter
The URL request filter enables Oracle Web Cache to allow or deny access to a specific site URL.
See Section 4.2 for further information about the URL request filter.
To configure rules for the URL request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the URL link.
The URL Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in the audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
In the Defined Rules section, create a new rule:
-
Click Create to create a row in the table.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
In the URL field, based on the URL Type you select, enter an optional URL string. If no URLs are specified, then all requests are checked. It is equivalent to specifying a URL with a prefix /.
- Path Prefix: Enter the path prefix of the objects. Start the path with
/; do not start the path withhttp://host_name:port/. The prefix is interpreted literally, including reserved regular expression characters. These characters include periods (.), question marks (?), asterisks (*), brackets ([]), curly braces ({}), carets (^), dollar signs ($), and backslashes (\).- File Extension: Enter the file extension. Because Oracle Web Cache internally starts the file extension with a period (.), it is not necessary to enter it.
- Regular Expression: Enter the regular expression of the objects. Remember to use "^" to denote the start of the URL and "$" to denote the end of the URL.
-
From the URL Type list, select an option to determine how the rule's URL are compared to the request's URL:
- Path Prefix: Select to allow or deny access to requests matching a path prefix.
- File Extension: Select to allow or deny access to requests matching a particular file extension.
- Regular Expression: Select to allow or deny access to requests matching regular expression syntax.
-
Click the Case Insensitive Match check box to match requests regardless of the case. If you do not select this check box, the rule bases the match on the case.
-
Click the Allow check box for Oracle Web Cache to allow requests matching the URL fields; deselect the check box for Oracle Web Cache to deny requests matching the IP address and URL fields.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 7 for any additional rules. You can also add learned rules, as described in Section 4.8.1.
-
Modify the Catch All rule, keeping in mind it is applied to all requests that do not match a defined rule.
Oracle recommends creating allow rules, followed by a Catch All deny rule.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the URL row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.8.1 Activating Learned Rules for the URL Request Filter
See Section 4.3 for further information about how learned rules are collected from the Catch All rule. You can add learned rules to the URL request filter.
To enable learned rules for the URL request filter:
-
Navigate to the URL Request Filter page. See Section 2.7.2.
-
In the Learned Rules section, if you see that some learned rules have been suggested, monitor the statistics for these rules by watching this page for awhile. When you decide that one or more learned rules make sense, proceed.
If no learned rules display under Catch All Rule, then there are no learned rules.
-
Select the row, and click Add Rule to Defined Rules to activate the rule and move it the Defined Rules section.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
-
Click Apply to save the configuration for the request filter.
4.9 Configuring Rules for the Header Request Filter
The header request filter enables Oracle Web Cache to deny access based on HTTP header values. Rules for the header request filter are most effective for white box lists.
See Section 4.2 for further information about the header request filter.
To configure rules for the header request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Header link.
The Header Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in the audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
Create a new rule:
-
Click Create to create a row in the table.
-
In the Header Name field, enter the name of the HTTP request header name, such as
Cookie. -
In the Value Expression field, enter the expression, as a substring or regular expression, for the header's value used to compare against an incoming request.
-
From the Type list, select to base the match evaluation on the substring or regular expression in the Value Expression field.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
In the URL field, based on the URL Type you select, enter an optional URL string. If no URLs are specified, then all requests are checked. It is equivalent to specifying a URL with a prefix /.
- Path Prefix: Enter the path prefix of the objects. Start the path with
/; do not start the path withhttp://host_name:port/. The prefix is interpreted literally, including reserved regular expression characters. These characters include periods (.), question marks (?), asterisks (*), brackets ([]), curly braces ({}), carets (^), dollar signs ($), and backslashes (\).- File Extension: Enter the file extension. Because Oracle Web Cache internally starts the file extension with a period (.), it is not necessary to enter it.
- Regular Expression: Enter the regular expression of the objects. Remember to use "^" to denote the start of the URL and "$" to denote the end of the URL.
-
From the URL Type list, select an option to determine how the rule's URL is compared to the request's URL:
- Path Prefix: Select to allow or deny access to requests matching a path prefix.
- File Extension: Select to allow or deny access to requests matching a particular file extension.
- Regular Expression: Select to allow or deny access to requests matching regular expression syntax.
-
Click the Case Insensitive Match check box to match requests regardless of the case. If you do not select this check box, the rule bases the match on the case.
-
Click the Match If Found check box for Oracle Web Cache to match incoming requests in which the header value matches the substring or regular expression specified in the Value Expression field. If there is a match with a request and the rule is enabled, the filter denies the request.
Do not select the Match If Found check box for Oracle Web Cache to match incoming requests in which the header value does not match the substring or regular expression specified in the Value Expression field. Oracle Web Cache denies the request only if the string or expression is not found, meaning that the request is allowed if the string is found.
Create a rule with the Match If Found check box selected, followed by rules without the check box selected.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 7 for any additional rules.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Header row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.10 Configuring Rules for the Query String Request Filter
The query string request filter enables Oracle Web Cache to deny access based on query string parameter values.
See Section 4.2 for further information about the query-string request filter.
To configure rules for the query string request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Query String link.
The Query String Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in its audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
Create a new rule:
-
Click Create to create a row in the table.
-
In the Query String Expression field, enter the query string, as a substring or regular expression, to compare against an incoming request.
-
Click the Enable check box to enable the rule; deselect the check box to disable the rule temporarily without losing the rule definition.
-
From the Type list, select to base the match evaluation on the substring or regular expression in the Query String Expression field.
-
Click the Match If Found check box for Oracle Web Cache to match incoming requests in which the query string matches the substring or regular expression specified in the Value Expression field. If there is a match with a request and the rule is enabled, the filter denies the request.
Do not select the Match If Found check box for Oracle Web Cache to match incoming requests in which the query string does not match the substring or regular expression specified in the Value Expression field. Oracle Web Cache denies the request only if the string or expression is not found, meaning that the request is allowed if the string is found.
For example, if you specify a rule with a Query String Expression of
abc, Type of substring, and do not select the Match If Found check box, the filter would deny a request which did not contain the stringabcin the query string (or POST body). It would allow a request which contains the stringabc.You can create multiple rules to allow requests with a certain string and deny requests with another string. For example, if you specify a second rule with a Query String Expression of
def, Type of substring, and click the Match If Found check box, the filter would allow a request withabcin the query string but would deny a request withdefin the query string. -
In the URL field, based on the URL Type you select, enter an optional URL string. If no URLs are specified, then all requests are checked. It is equivalent to specifying a URL with a prefix /.
- Path Prefix: Enter the path prefix of the objects. Start the path with
/; do not start the path withhttp://host_name:port/. The prefix is interpreted literally, including reserved regular expression characters. These characters include periods (.), question marks (?), asterisks (*), brackets ([]), curly braces ({}), carets (^), dollar signs ($), and backslashes (\).- File Extension: Enter the file extension. Because Oracle Web Cache internally starts the file extension with a period (.), it is not necessary to enter it.
- Regular Expression: Enter the regular expression of the objects. Remember to use "^" to denote the start of the URL and "$" to denote the end of the URL.
-
From the URL Type list, select an option to determine how the rule's URL are compared to the request's URL:
- Path Prefix: Select to allow or deny access to requests matching a path prefix.
- File Extension: Select to allow or deny access to requests matching a particular file extension.
- Regular Expression: Select to allow or deny access to requests matching regular expression syntax.
-
Click the Case Insensitive Match check box to match requests regardless of the case. If you do not select this check box, the rule bases the match on the case.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Perform Step 7 for any additional rules.
-
Use the Move Up and Move Down icons to change the order in which the rules are matched against requests.
The order of the rules is important. Oracle Web Cache matches higher priority rules first.
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Query String row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.11 Configuring Rules for the Format Request Filter
The format request filter enables Oracle Web Cache to deny access based on well-formed and valid URLs.
See Section 4.2 for further information about the format request filter.
To configure rules for the format request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
From the Site list, select the site to apply the filter. See Section 2.11.3 and Section 2.11.4 to create additional sites.
You can configure filters and filter rules for specific sites or Undefined Sites. Oracle Web Cache directs client requests that do not match a defined site to the request filters configured for Undefined Sites.
-
Click the Query String link.
The Query String Request Filter page displays.
-
From the Audit list, select the level of action for Oracle Web Cache to include in its audit log for the request filter.
-
From the Response to deny list, select the HTTP response for Oracle Web Cache to return to browsers for requests that are denied by this request filter.
The Close Connection option does not return any HTTP responses. It just closes the connection.
-
Define a rule for the validation type:
-
Click the Enable check box to enable the validation check:
- Null Byte: This validation checks for encoding as a null byte as
%00. Most applications do not expect null bytes in the URL. This may cause a string which contains tricks after a null byte to pass an application check because the application stops checking when it hits the null byte, thinking that it is the end of string marker.- Valid Unicode: This validation checks for Unicode characters, either encoded or raw in the URL for an application that is not set up to handle Unicode.
- Strict Encoding: This validation checks for unencoded characters, such as a space, backslash (\), or non-printable characters.
- Double Encoding: This validation checks for
%XYsequences using%XYencoding, in an attempt to get the%XYsequence to be passed to the application. This could allow the hacker to specify a character that would otherwise be rejected.- Uencoded Unicode Characters: This validation checks for Unicode characters, either encoded or raw in the URL for an application that is not set up to handle Unicode.
-
Click the Check Query String check box to verify the format of the URL, as well as the query string or request body for a POST request; leave this option unchecked to verify only the format of the URL.
-
Click the Allow check box for Oracle Web Cache to allow requests containing the invalid format; deselect the check box for Oracle Web Cache to deny requests containing the invalid format.
-
Click the Monitor Only check box to see the match activity of the rule without enforcing the rule.
When results are expected, then disable Monitor Only to enforce the rule. See Section 4.4 for further information about the Monitor Only option.
-
Click Apply to save the rule settings.
-
-
Click the Request Filters Summary breadcrumb at the top of the page, or from the Web Cache menu, select Administration and then Request Filters to navigate back to the Request Filters Summary page.
-
In the Format row, click Enable to enable the filter.
If you do not click Enable, Oracle Web Cache ignores any configured filter rules for this filter.
-
Click Apply to save the configuration for the request filter.
4.12 Deleting Rules for a Request Filter
To delete a rule for a request filter:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
Click the filter you want to modify.
-
From the Site list, select the site.
-
Select a rule in the table and click the Delete icon.
-
Repeat Step 5 for each additional rule you want to remove.
-
Click Apply to save the configuration for the request filter.
4.13 Monitoring Statistics for Request Filter Types and Rules
Fusion Middleware Control provides statistics for assessing the effectiveness of configured request filters and rules. By analyzing the rules, you can determine if you prioritized the rules incorrectly. For example, if the you notice a deny rule is matched but configured allow rules are never matched, then prioritize the allow rules first.
If you make changes to the configuration settings for Oracle Web Cache, Oracle Web Cache disables the request-filter statistics and labels them as NA.
To view request-filter statistics:
-
Navigate to the Web Cache Home page in Fusion Middleware Control. See Section 2.6.2.
-
From the Web Cache menu, select Administration and then Request Filters.
The Request Filters Summary page displays.
-
Scroll to the far right, to view the Request Statistics and Post Allow Statistics. The Request Statistics display the run time statistics for tracking how the configured request filters handle the incoming requests:
-
Matched Catch All: Displays the number of requests that matched the Catch All rules.
-
Matched Others: Displays the number of requests that matched the rules that were not Catch All requests.
-
Matched Denied: Displays the number of requests that matched the rule and were denied by Oracle Web Cache.
If there are few requests matching the filter, then consider changing the rules for the filter to improve its effectiveness.
The Post Allow Statistics display the statistics for allowed requests:
-
Succeeded: Displays the number of requests that were allowed and succeeded.
-
Denied Later: Displays the number of requests that were allowed, but subsequently denied by another filter.
-
Failed: Displays the number of requests that were allowed, but the request failed with an error.
-
-
To gather more information for a particular filter, click the filter to view the individual rules and accompanying statistics.
4.14 Reducing Time to Configure Request Filters
This section covers the following configuration tasks for easing configuration work. These features are only available in Oracle Web Cache Manager.
4.14.1 Copying Rules from a Source Site to a Target Site
You can reduce the time spent configuring filters and associated rules by completing the configuration for one site and applying the configuration to other sites. You can copy the complete configuration for all filters, or you can copy the configuration for the rules for a specific filter.
To copy the complete configuration for all the filters from a source site to a target site:
-
Configure settings for the various filters, as described in Section 4.5 to Section 4.11.
-
From Oracle Web Cache Manager, in the navigator frame, select Filtering > Request Filters. See Section 2.7.2.
The Request Filters Summary page displays.
-
From the For Site list, select the source site with the complete configuration you want to copy.
-
Click Copy All Filters toward the bottom of the page.
-
In the Copy All Request Filter dialog, from the To Site list, select the target site to apply the configuration settings, and then click Submit.
-
Click Apply Changes.
To copy the rule configuration for a specific filter from a source site to a target site:
-
Configure settings for the various filters, as described in Section 4.5 to Section 4.11.
-
From Oracle Web Cache Manager, in the navigator frame, select Filtering > Request Filters. See Section 2.7.2.
The Request Filters Summary page displays.
-
Select a specific filter from the Filter Type column.
The configuration page for the selected filter displays.
-
From the For Site list, select the source site with the complete configuration you want to copy.
-
Click Copy Filter toward the bottom of the page.
-
In the Copy Request Filter dialog, from the To Site list, select the target site to apply the configuration settings, and then click Submit.
-
Click Apply Changes.
4.14.2 Reverting Configuration Settings
You can revert to the original configuration settings provided by Oracle Web Cache for all filters or a specific filter.
To revert the configuration settings for all filters:
-
From Oracle Web Cache Manager, in the navigator frame, select Filtering > Request Filters. See Section 2.7.2.
The Request Filters Summary page displays.
-
From the For Site list, select the site you want to revert configuration settings.
-
Click Clear All Filters.
-
Click Apply Changes.
To revert the configuration settings for a specific filter:
-
From Oracle Web Cache Manager, in the navigator frame, select Filtering > Request Filters. See Section 2.7.2.
The Request Filters Summary page displays.
-
Select a specific filter from the Filter Type column.
The configuration page for the selected filter displays.
-
From the For Site list, select the site you want to revert configuration settings.
-
Click Clear Filter.
-
Click Apply Changes.