14 Understanding Single Sign-On Between JD Edwards EnterpriseOne and Oracle
This chapter contains the following topics:
-
Section 14.1, "Single Sign-On Between JD Edwards EnterpriseOne and Oracle"
-
Section 14.3, "Supported JD Edwards EnterpriseOne and Oracle Single Sign-On Configurations"
-
Section 14.4, "Single Sign-On when Running JD Edwards EnterpriseOne on Oracle Application Server"
-
Section 14.5, "Single Sign-On When Running JD Edwards EnterpriseOne on IBM WebSphere"
-
Section 14.6, "Non-Web Client Sign-On in the Oracle Single Sign-On Configuration"
14.1 Single Sign-On Between JD Edwards EnterpriseOne and Oracle
Single sign-on between JD Edwards EnterpriseOne and Oracle enables users to sign in once to access both JD Edwards EnterpriseOne and Oracle single sign-on enabled applications.
Note:
In addition, you can enable support of long user IDs and passwords in a JD Edwards EnterpriseOne single sign-on configuration with Oracle Access Manager or Oracle AS Single Sign-On Server. For more information, see "Using Long User IDs and Passwords in JD Edwards EnterpriseOne" in the Red Paper Library on the My Oracle Support Web site.14.1.1 Prerequisites
The Oracle Identity Management infrastructure must be installed as part of the Oracle Application Server setup. See the Oracle Fusion Middleware Installation Guide for Oracle Identity Management for more information.
If you are running JD Edwards EnterpriseOne web applications on Oracle Application Server, the instructions in this section require that you use the JD Edwards EnterpriseOne Tools HTML Web Server for Oracle Application Server.
See JD Edwards EnterpriseOne Tools Release 8.98 HTML Web Server Reference Guides for Oracle Application Server 10.1.3.1 on the My Oracle Support Web site.
See JD Edwards EnterpriseOne Tools Minimum Technical Requirements for WebServers on the My Oracle Web site.
If you are running JD Edwards EnterpriseOne web applications on IBM WebSphere Application Server instead of Oracle Application Server, the PeopleSoft SSO Plug-In must be installed on the OracleAS Single Sign-On server.
See the My Oracle Support Web site for information on how to install this plug-in.
14.2 Oracle Single Sign-On Components
Configuring single sign-on between JD Edwards EnterpriseOne and Oracle applications requires a thorough understanding of the Oracle Identity Management infrastructure within Oracle Application Server. Oracle Identity Management provides the framework that supports single sign-on. OracleAS Single Sign-On is the component within Oracle Identity Management that works with these other components to enable single sign-on:
-
Single sign-on server.
-
Partner applications.
-
mod_osso.
-
Oracle Internet Directory.
-
Oracle Identity Management infrastructure.
14.2.1 Single Sign-On Server
The single sign-on server consists of program logic in the Oracle Application Server database, Oracle HTTP Server, and OC4J server that enables you to sign in securely to applications. The single sign-on server enables access to several applications by authenticating only once.
14.2.2 Partner Applications
OracleAS applications delegate the authentication function to the single sign-on server. For this reason, they are called partner applications. An authentication module called mod_osso enables these applications to accept authenticated user information instead of a user name and password once users have signed in to the single sign-on server. A partner application is responsible for determining whether a user authenticated by OracleAS Single Sign-On is authorized to use the application.
Examples of partner applications include OracleAS Portal, OracleAS Discoverer, and Oracle Delegated Administration Services. When JD Edwards EnterpriseOne is installed on Oracle Application Server, it is also considered a partner application.
14.2.3 mod_osso
mod_osso is an Oracle HTTP Server module that provides authentication to OracleAS applications. Located on the application server, mod_osso simplifies the authentication process by serving as the sole partner application to the single sign-on server. In this way, mod_osso renders authentication transparent to partner applications.
14.2.4 Oracle Internet Directory
Oracle Internet Directory is the repository for all single sign-on user accounts and passwords—administrative and non-administrative. The single sign-on server authenticates users against their entries in the directory. At the same time, it retrieves user attributes form the directory that enables applications to validate users.
14.2.5 Oracle Identity Management Infrastructure
OracleAS Single Sign-On is just one link in an integrated infrastructure that also includes these components:
-
Oracle Internet Directory
-
Oracle Directory Integration and Provisioning
-
Oracle Delegated Administrative Services
-
OracleAS Certificate Authority
Working together, these components, called the Oracle Identity Management infrastructure, manage the security life cycle of users and other network entities in an efficient, cost-effective way.
See Also:
-
Oracle Application Server Single Sign-On Administrator's Guide.
-
Oracle Identity Management Integration Guide.
14.3 Supported JD Edwards EnterpriseOne and Oracle Single Sign-On Configurations
Single sign-on is supported between JD Edwards EnterpriseOne web applications and OracleAS Single Sign-On enabled applications.
Note:
JD Edwards EnterpriseOne non-web client applications, such as Windows client, JAVA Connector, and COM Connector, do not use OracleAS Single Sign-On for authentication.How single sign-on works between JD Edwards EnterpriseOne and Oracle depends upon your implementation:
-
JD Edwards EnterpriseOne HTML Web Server installed on Oracle Application Server.
In this configuration, single sign-on is bi-directional. This means that whichever system users sign in to first, JD Edwards EnterpriseOne or Oracle, they do not have to sign in again to access an application in the other system.
-
JD Edwards EnterpriseOne HTML Web Server installed on IBM WebSphere.
In this configuration, single sign-on is unidirectional. If users have already signed in to Oracle Application Server, they can access a JD Edwards EnterpriseOne application without having to re-enter a user name and password. However, in this configuration, if users sign in to JD Edwards EnterpriseOne first, they cannot access an Oracle application through single sign-on. They will have to re-enter a user ID and password.
In addition, JD Edwards EnterpriseOne provides single sign-on from Oracle Portal, enabling users to access a JD Edwards EnterpriseOne application inside Oracle Portal. For more information, see the JD Edwards EnterpriseOne Tools 8.96 Portlet Installation for the Oracle Portal Guide.
14.4 Single Sign-On when Running JD Edwards EnterpriseOne on Oracle Application Server
When JD Edwards EnterpriseOne HTML Web Server is running on Oracle Application Server, JD Edwards EnterpriseOne delegates user authentication to the OracleAS Single Sign-On server. The mod_osso authentication module enables JD Edwards EnterpriseOne applications to accept authenticated user information instead of a user name and password once users have signed in to OracleAS Single Sign-On server. JD Edwards EnterpriseOne determines whether a user authenticated by OracleAS Single Sign-On is authorized to use the application.
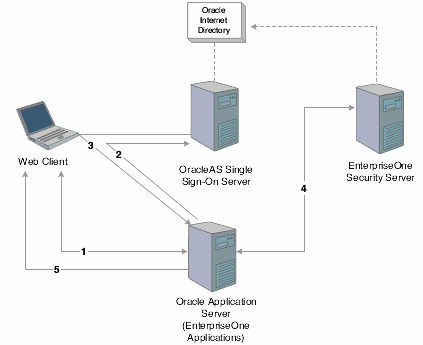
This diagram shows the single sign-on process when JD Edwards EnterpriseOne HTML Web Server is running on Oracle Application Server:
Figure 14-1 JD Edwards EnterpriseOne and OracleAS single sign-on
Description of "Figure 14-1 JD Edwards EnterpriseOne and OracleAS single sign-on"
These steps explain the single sign-on process illustrated in the diagram:
-
A user signs in to an Oracle partner application (either a JD Edwards EnterpriseOne or Oracle web application).
-
Using mod_osso, the partner application redirects the request to the OracleAS Single Sign-On server.
-
The OracleAS Single Sign-On server authenticates the user ID and password, generates an Oracle SSO cookie, and redirects the request to the JD Edwards EnterpriseOne partner application on Oracle Application Server.
-
Based on the Oracle SSO cookie, JD Edwards EnterpriseOne generates an authenticate token (PS_TOKEN) and sends it to the JD Edwards EnterpriseOne security server to validate the token, which enables the user to sign in.
-
A session is established for the web user.
Note:
In the diagram, Oracle Internet Directory can be used as an LDAP directory for the JD Edwards EnterpriseOne security server.14.4.1 Single Sign-Off
Signing off of a JD Edwards EnterpriseOne application terminates the single sign-on session, which in turn signs off all active Oracle partner applications. When you click Sign Out in a JD Edwards EnterpriseOne application, the system takes you to the single sign-off page, where sign-off occurs. If you signed off successfully, each of the applications listed on the single sign-off page has a check mark next to the application name. A broken image next to an application name denotes an unsuccessful sign-off.
Once all of the application names activated in a session have a check mark, you can click Return to go to the application from which you initiated sign-off.
Signing off an Oracle application takes you to the single sign-off page as well. This closes any Oracle applications that are running. However, any JD Edwards EnterpriseOne applications that are open remain active. Only when a user accesses the JD Edwards EnterpriseOne application does JD Edwards EnterpriseOne check if the Oracle SSO cookie is present. If it is not, the system ends the JD Edwards EnterpriseOne session and redirects the user to the Oracle Single Sign-On page for sign-in.
14.4.2 JD Edwards EnterpriseOne Single Sign-On Settings when Running on Oracle Application Server
Part of configuring single sign-on between JD Edwards EnterpriseOne and Oracle involves configuring the jas.ini and tokengen.ini files.
14.4.2.1 JD Edwards EnterpriseOne jas.ini Settings for Single Sign-On
The jas.ini file of the JD Edwards EnterpriseOne HTML Web Server contains a setting that you can configure to delegate JD Edwards EnterpriseOne user authentication to OracleAS Single Sign-On. This setting is in the [SECURITY] section of the jas.ini file:
| Setting | Purpose |
|---|---|
| OracleSSO= | Determines if OracleAS Single Sign-On is used for user authentication. Valid values are:
|
In addition, you can configure this setting in the [SECURITY] section to control the functionality of the Return link on the Single Sign-Off web page:
| Setting | Purpose |
|---|---|
| OracleSSOSignOffURL= | Determines the web page that the Return link accesses from the Oracle Single Sign-Off web page when the user signs off from JD Edwards EnterpriseOne. Enter a URL for the web page that you want users to access from the Return link. The default is the URL for accessing the JD Edwards EnterpriseOne web client. |
14.4.2.2 JD Edwards EnterpriseOne TokenGen.ini Settings
JD Edwards EnterpriseOne uses the TokenGen.ini file to generate an authenticate token (PS_TOKEN). A common key is required for the encryption and decryption of the authenticate token. This key is set during the JD Edwards EnterpriseOne HTML Web Server installation and is saved in the TokenGen.ini file. The key consists of the node name and node password, as well as other parameters that must not be modified:
| Setting | Default Value |
|---|---|
| NodeName= | NodeName |
| NodePwd= | NodePassword |
| CLIENTTYPE= | 1 |
| CODEPAGE | 0 |
| VERSION= | 700 |
| TOOLSVERSION= | 8.10 |
| SIGNATURETYPE= | N |
| MNRD | 0 |
If you configured single sign-on settings on the JD Edwards EnterpriseOne security server, you can change the NodeName and NodePassword settings during the JD Edwards EnterpriseOne HTML Web Server installation. When the single sign-on node has not been configured on the JD Edwards EnterpriseOne security server, the installer displays the default values for the Node Name and Node Password.
After the JD Edwards EnterpriseOne HTML Web Server is installed, you can change the values for the node name and node password to correspond to the entries on your JD Edwards EnterpriseOne security server, if necessary. It will require the restart of JD Edwards EnterpriseOne HTML Web Server.
14.4.3 Settings for Configuring JD Edwards EnterpriseOne Virtual Hosts with Oracle Single Sign-On
Single sign-on partner applications are integrated with mod_osso, which is registered automatically by the OracleAS installer. In essence, partner applications are registered by way of mod_osso. Registering the module creates an entry for it in the identity management infrastructure database as well as on the application computer.
When the JD Edwards EnterpriseOne HTML Web Server is configured with a port other than the default port (which is typically 80), you should register JD Edwards EnterpriseOne HTML Web Server with the other port using mod_osso. The commands in this section should be executed on the Oracle Identity Manager Host.
Using port 7778 as an example, these commands show how to register JD Edwards EnterpriseOne HTML Web Server using mod_osso:
SET ORACLE_HOME=C:\OracleAppSrv $ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path $ORACLE_HOME -config_mod_osso TRUE -site_name AppServer90.eone.jdedwards.com -remote_midtier
You must run an update after running the ssoreg.sh command. Use this command to run an update:
$ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path $ORACLE_HOME -config_mod_osso TRUE -site_name AppServer90.eone.jdedwards.com -remote_midtier -⇒ ⇒ ⇒ config_file $ORACLE_HOME/Apache/Apache/conf/osso/myosso.conf -mod_osso_url http:// App⇒ Server90.eone.jdedwards.com:7778
The resulting configuration file is an obfuscated osso configuration file. You must copy this file to the Oracle Application Server middle-tier instance. Lastly, on the middle-tier host, run this script to complete the registration:
(UNIX) $ORACLE_HOME/Apache/Apache/bin/osso1013 config_file
For additional information on how to configure virtual hosts with Oracle Single Sign-On, see:
-
"Configuring Instances to Use 10.1.4 or 10.1.2 Oracle Identity Management" in the Oracle® Application Server Administrator's Guide
-
"Configuring mod_osso with Virtual Hosts" in the Oracle® Application Server Single Sign-On Administrator's Guide.
14.5 Single Sign-On When Running JD Edwards EnterpriseOne on IBM WebSphere
When JD Edwards EnterpriseOne HTML Web Server is running on IBM WebSphere, single sign-on is unidirectional. Users must first sign in to an Oracle application using Oracle Single Sign-On. Only then can they access a JD Edwards EnterpriseOne application in the same session without having to re-enter their user ID and password. If users access a JD Edwards EnterpriseOne web application first, the JD Edwards EnterpriseOne sign-in screen appears; the sign-in request does not redirect users to the Oracle Single Sign-On page.
This solution is similar to JD Edwards EnterpriseOne single sign-on from the PeopleSoft Enterprise Portal, which uses the authenticate token.
See Configuring Single Sign-On Between PeopleSoft Enterprise Portal and JD Edwards EnterpriseOne.
In this configuration, Oracle AS Single Sign-On uses the PeopleSoft SSO Plug-In to achieve single sign-on with JD Edwards EnterpriseOne. The plug-in, which must be installed on the OracleAS Single Sign-On server, generates an authenticate token that IBM WebSphere uses to achieve single sign-on.
See the My Oracle Web site for information on how to download and install this plug-in.
Note:
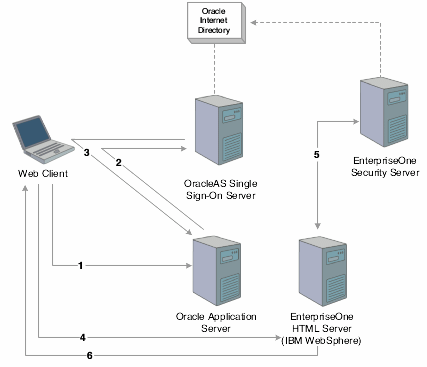
Single sign-off between Oracle and JD Edwards EnterpriseOne is not supported when JD Edwards EnterpriseOne is running on IBM WebSphere. When you sign off of JD Edwards EnterpriseOne, the system ends the JD Edwards EnterpriseOne session, but any Oracle application sessions that are open continue to run. You must close the browser to sign in to JD Edwards EnterpriseOne again. Signing off of an Oracle application ends the OracleAS Single Sign-On session, as well as any other Oracle applications that were active in the session; however, any JD Edwards EnterpriseOne applications that are open will remain active.This illustration shows the single sign-on process when JD Edwards EnterpriseOne HTML Web Server is running on IBM WebSphere:
Figure 14-2 JD Edwards EnterpriseOne and OracleAS single sign-on with IBM WebSphere
Description of "Figure 14-2 JD Edwards EnterpriseOne and OracleAS single sign-on with IBM WebSphere"
These steps explain the single sign-on process illustrated in the diagram:
-
A user signs in to an Oracle partner application on Oracle Application Server.
-
Using mod_osso, the partner application redirects the request to the OracleAS Single Sign-On server.
-
OracleAS Single Sign-On authenticates the user ID and password, generates an Oracle SSO cookie and PS_TOKEN cookie, and redirects the request to the partner application on Oracle Application Server.
-
When the same user tries to launch a JD Edwards EnterpriseOne application in the same session, the browser sends the request to the JD Edwards EnterpriseOne HTML Web Server running on IBM WebSphere.
-
The JD Edwards EnterpriseOne HTML Web Server sends the PS_TOKEN to the JD Edwards EnterpriseOne security server to validate the token.
-
Upon validation, IBM WebSphere establishes a session for the web user.
Note:
In this diagram, Oracle Internet Directory can be used as an LDAP directory for JD Edwards EnterpriseOne.14.5.1 Time Zone Setting Adjustment
When JD Edwards EnterpriseOne is running on IBM WebSphere, you must configure the ENTERPRISE TIMEZONE ADJUSTMENT setting in the JD Edwards EnterpriseOne enterprise server jde.ini file. This setting enables you to enter the difference in time between Greenwich Mean Time (GMT) and OracleAS Single Sign-On node time. You should change this setting whenever daylight saving time changes to reflect the difference between GMT time and the OracleAS Single Sign-On node time.
In this example of the ENTERPRISE TIMEZONE ADJUSTMENT setting, the difference between the GMT and OracleAS Single Sign-On time is entered in minutes for an OracleAS Single Sign-On server that is running in Mountain Standard Time (MST):
[ENTERPRISE TIMEZONE ADJUSTMENT]
OracleSSONode=-360
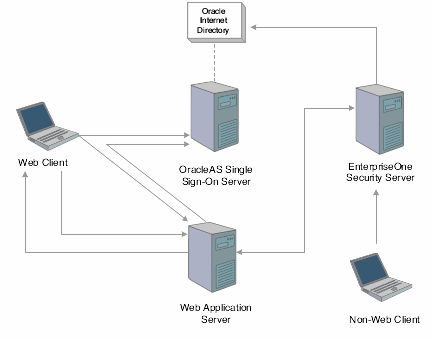
14.6 Non-Web Client Sign-On in the Oracle Single Sign-On Configuration
JD Edwards EnterpriseOne non-web clients, such as Windows, JAVA Connector, and COM Connector, cannot use OracleAS Single Sign-On. However, this diagram shows how JD Edwards EnterpriseOne can use Oracle Internet Directory, which is an LDAP compliant directory service, to authorize non-web client users:
Figure 14-3 JD Edwards EnterpriseOne non-web client sign-on in the Oracle single sign-on configuration
Description of "Figure 14-3 JD Edwards EnterpriseOne non-web client sign-on in the Oracle single sign-on configuration"
OracleAS Single Sign-On uses the Oracle Internet Directory (OID) to manage user information. If enabled for LDAP, JD Edwards EnterpriseOne security server can validate the user ID and password of the non-web client user from Oracle Internet Directory.