15 Setting Up JD Edwards EnterpriseOne Single Sign-On Through Oracle Access Manager 10g
This chapter contains the following topics:
-
Section 15.1, "Understanding JD Edwards EnterpriseOne Single Sign-On Through Oracle Access Manager"
-
Section 15.2, "Setting Up Oracle Access Manager Single Sign-On for JD Edwards EnterpriseOne"
Note:
You can also set up single sign-on between JD Edwards EnterpriseOne and Oracle applications through the Oracle AS Single Sign-On Server, which is not discussed in this chapter.In addition, you can enable support of long user IDs and passwords in a JD Edwards EnterpriseOne single sign-on configuration with Oracle Access Manager or Oracle AS Single Sign-On Server. See "Using Long User IDs and Passwords in JD Edwards EnterpriseOne" in the Red Paper Library on the My Oracle Support Web site for more information.
15.1 Understanding JD Edwards EnterpriseOne Single Sign-On Through Oracle Access Manager
Oracle Access Manager provides single sign-on functionality for Oracle applications, including JD Edwards EnterpriseOne. It provides a secure internet infrastructure for identity management for JD Edwards EnterpriseOne applications and processes. This infrastructure provides:
-
Identity and access management across JD Edwards EnterpriseOne applications, enterprise resources, and other domains.
-
Foundation for managing the identities of customers, partners, and employees across internet applications. These user identities are protected by security policies for web interaction.
Integration with Oracle Access Manager provides JD Edwards EnterpriseOne implementations with these features:
-
Oracle Access Manager authentication, authorization, and auditing services for JD Edwards EnterpriseOne applications.
-
Oracle Access Manager single sign-on for JD Edwards EnterpriseOne applications and other Oracle Access Manager-protected resources in a single domain or across domains.
Note:
JD Edwards EnterpriseOne single sign-on through Oracle Access Manager is supported only by the JD Edwards EnterpriseOne Web client, not Collaborative Portal. -
Oracle Access Manager authentication schemes that provide single sign-on for JD Edwards EnterpriseOne applications:
-
Basic Over LDAP (Lightweight Directory Access Protocol): Users enter a user name and password in a window supplied by the Web server.
This method can be redirected to Secure Socket Layer (SSL).
-
Form: Similar to the basic challenge method, users enter information in a custom HTML form.
You choose the information that users must provide in the form.
-
X509 Certificates: X.509 digital certificates over SSL.
A user's browser must supply a certificate.
-
Integrated Windows Authentication (IWA): Users will not notice a difference between an Oracle Access Manager authentication and IWA when they log on to the desktop, open an Internet Explorer (IE) browser, request an Oracle Access Manager-protected web resource, and complete single sign-on.
-
Microsoft .NET Passport: NET Passport is a component of the Microsoft .NET framework. The .NET plug-in is a Web-based authentication service that provides single sign-on for Microsoft-protected web resources.
-
Custom: You can use other forms of authentication through the Oracle Access Manager Authentication Plug-in API.
-
-
Session timeout: Oracle Access Manager enables you to set the length of time that a user session is valid.
-
Ability to use the Oracle Access ManagerIdentity System for identity management. The Identity System provides identity management features such as portal inserts, delegated administration, workflows, and self-registration to JD Edwards EnterpriseOne applications.
You can determine how much access to provide to users upon self-registration. Identity System workflows enable a self-registration request to be routed to appropriate personnel before access is granted. Oracle Access Manager also provides self-service, enabling users to update their own identity profiles.
See Also:
-
Oracle Access Manager Integration Guide and the Oracle Identity Manager documentation.
15.1.1 JD Edwards EnterpriseOne Integration Architecture
JD Edwards EnterpriseOne has a configurable authentication mechanism that allows it to authenticate a user against:
-
Native tables (through a security kernel).
-
Lightweight Data Access Protocol (LDAP).
-
Custom plug-ins, including the ability to read HTTP Headers.
JD Edwards EnterpriseOne single sign-on through Oracle Access Manager involves:
-
Protection through a WebGate, which is a plug-in that intercepts Web resource (HTTP) requests and forwards them to the Access Server for authentication and authorization.
-
Populating a header variable with an attribute value that is stored in the LDAP directory used by Oracle Access Manager.
-
Configuring JD Edwards EnterpriseOne to invoke the Oracle Access Manager authentication process, overriding the default authentication mechanism.
15.1.1.1 Single Sign-On Architecture
Single sign-on with Oracle Access Manager requires a JD Edwards EnterpriseOne HTML Web Server configuration with an application server, such as Oracle Application Server 10g, that contains an HTTP server and a J2EE container, which is required for the Java servlets and Java code to run. In addition, WebGate must be installed on the HTTP Server, and it must be configured to protect the JD Edwards EnterpriseOne URLs that are used to access the HTML Web Server.
The user accesses a JD Edwards EnterpriseOne application using a web browser. WebGate intercepts the user's HTTP request and checks for an obSSOCookie. The obSSOCookie is an encrypted cookie that the Oracle Access Manager Access System uses to implement single-domain and multi-domain single sign-on. If the cookie does not exist or has expired, the user is prompted to enter credentials. Oracle Access Manager verifies the user credentials, and if the user is authenticated, the WebGate redirects the user to the requested resource and passes the required header variable to JD Edwards EnterpriseOne. The header variable is read by JD Edwards EnterpriseOne and is used to generate the PS_TOKEN. The following illustration shows the integration environment and process flow:
Figure 15-1 JD Edwards EnterpriseOne Single Sign-On through Oracle Access Manager
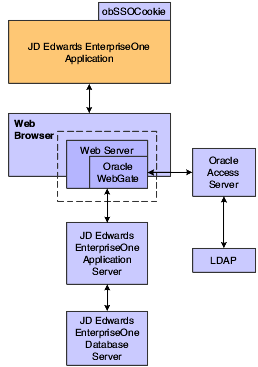
Description of "Figure 15-1 JD Edwards EnterpriseOne Single Sign-On through Oracle Access Manager"
The following steps describe the single sign-on process:
-
A user attempts to access a JD Edwards EnterpriseOne program.
-
A WebGate that is deployed on the JD Edwards EnterpriseOne HTTP Server intercepts the request.
-
The WebGate checks the Access Server to determine whether the resource (JD Edwards EnterpriseOne URL) is protected.
The security policy consists of an authentication scheme, authorization rules, and allowed operations based on an authentication and authorization success or failure.
-
If a valid session does not exist and the resource is protected, WebGate prompts the user for credentials.
-
If the credentials are validated, Oracle Access Manager performs the actions that are defined in the security policy for the JD Edwards EnterpriseOne resource and sets an HTTP header variable that maps to the JD Edwards EnterpriseOne user ID.
-
If a valid session cookie exists and the user is authorized to access the resource, WebGate redirects the user to the requested JD Edwards EnterpriseOne resource.
-
JD Edwards EnterpriseOne receives the request for the JD Edwards EnterpriseOne resource and runs the code that is defined in its authentication configuration.
-
The code reads the HTTP header variable and sets that value as the signed-on JD Edwards EnterpriseOne user. It then generates the PS_TOKEN, which contains the same information.
-
JD Edwards EnterpriseOne generates the applications, subject to further authorization verification within JD Edwards EnterpriseOne.
15.1.2 Supported Versions and Platforms
This section describes the integration of Oracle Access Manager 10g (10.1.4.0.1) with JD Edwards EnterpriseOne Tools 8.98 and JD Edwards EnterpriseOne applications. However, any references to specific versions and platforms in this chapter are for demonstration purposes.
For supported versions and platforms for this integration, see Certifications on the My Oracle Support Web site.
15.2 Setting Up Oracle Access Manager Single Sign-On for JD Edwards EnterpriseOne
This section lists prerequisites and discusses how to set up Oracle Access Manager single sign-on for JD Edwards EnterpriseOne, which includes these tasks:
-
Create a host identifier for the JD Edwards EnterpriseOne HTTP Server.
-
Create a policy domain and policies to restrict access to JD Edwards EnterpriseOne URLs.
-
Define a resource that controls the highest-level URL prefix to protect.
-
Define two authorization rules.
-
Define an authorization action.
-
Define an authentication rule.
-
Define an access policy and add the JD Edwards EnterpriseOne URL pattern to it.
-
Define an authentication rule for the JD Edwards EnterpriseOne resources.
-
Define an authentication action that sets a custom HTTP header variable upon successful authentication.
-
Define an authentication expression for the JD Edwards EnterpriseOne resources.
Note:
JD Edwards EnterpriseOne single sign-on through Oracle Access Manager is supported only with the JD Edwards EnterpriseOne Web client, not Collaborative Portal.15.2.1 Prerequisites
Before you set up Oracle Access Manager and JD Edwards EnterpriseOne for single sign-on, you must:
-
Install a supported directory server according to vendor instructions.
-
Install and configure Oracle Access Manager using the directory server as the LDAP repository.
See Oracle Access Manager Installation Guide..
-
Configure the HTML Web Server so that JD Edwards EnterpriseOne applications are rendered and accessed through the HTTP Server.
-
Install a WebGate on the JD Edwards EnterpriseOne HTTP Server.
See Oracle Access Manager Installation Guide.
-
Configure the Web browser to allow cookies, according to vendor instructions.
15.2.2 Creating a Host Identifier for the JD Edwards EnterpriseOne HTTP Server
Sign in to Oracle Access Manager.
-
From the Access System Landing page, select the Access System Console.
-
Click Access System Configuration, and then click Host Identifiers.
-
Add information about the server.
15.2.3 Creating a Policy Domain and Policies to Restrict Access to JD Edwards EnterpriseOne URLs
In Oracle Access Manager, access the System Landing page.
Figure 15-2 Create Policy Domain page: General tab
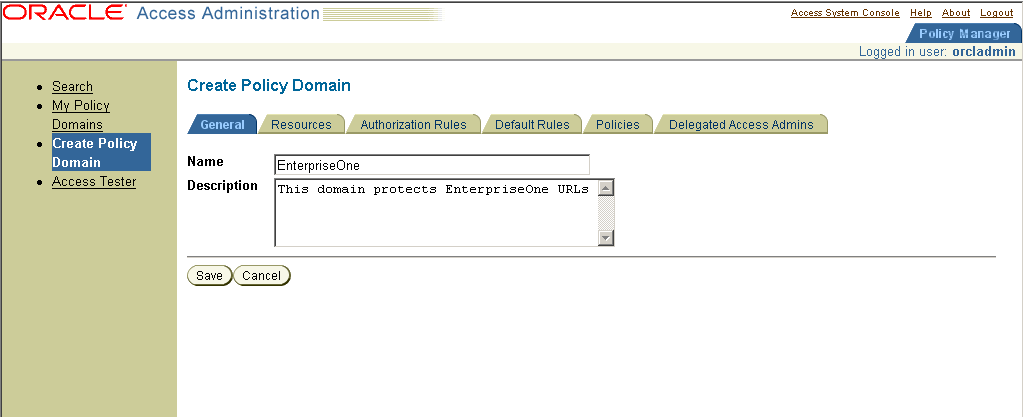
Description of "Figure 15-2 Create Policy Domain page: General tab"
-
From the Access System Landing page, select the Policy Manager, and then click create Policy Domain.
-
Define a policy domain and policies.
The policy domain should protect all JD Edwards EnterpriseOne URLs that users access. For example, if you use JD Edwards EnterpriseOne Portal to consolidate access to various JD Edwards EnterpriseOne applications, the policy must protect the portal and application URLs.
URL prefix formats are specific to your JD Edwards EnterpriseOne implementation. For example, the version 8.98 URLs have the format /jde/E1Menu.maf.
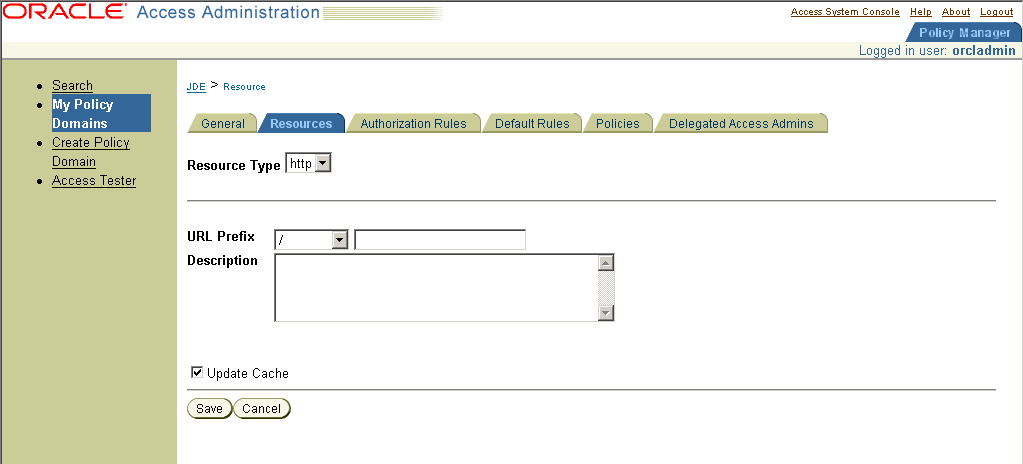
15.2.4 Defining a Resource That Controls the Highest-Level URL Prefix to Protect
If you are already viewing the new policy domain, click Resources. Otherwise, click My Policy Domains, the link for the policy domain, and then Resources.
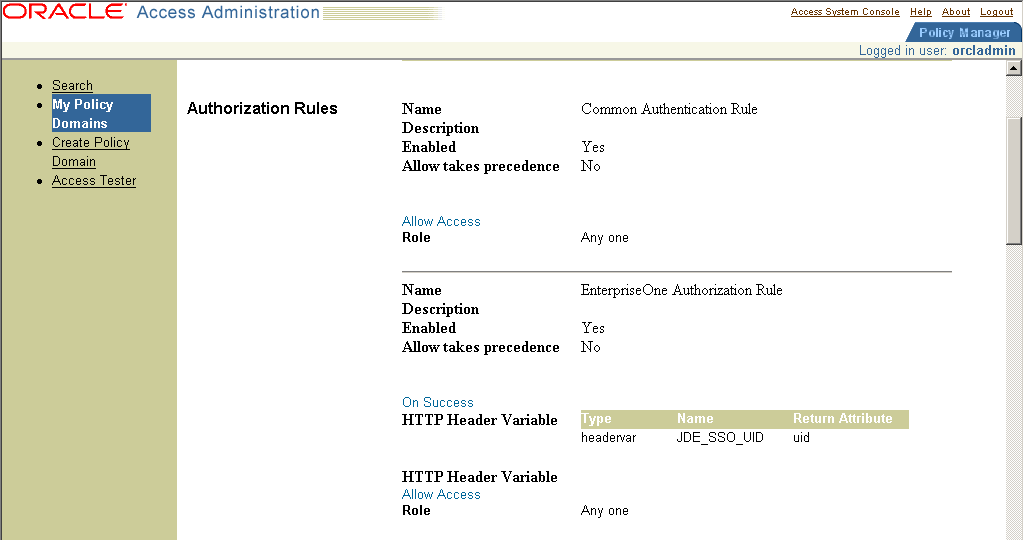
15.2.5 Defining Two Authorization Rules
You must define two authorization rules that determine which users have access to all resources, including JD Edwards EnterpriseOne resources.
If you are already viewing the new policy domain, click Authorization Rules. Otherwise, click My Policy Domains, the link for the policy domain, and then Authorization rules.
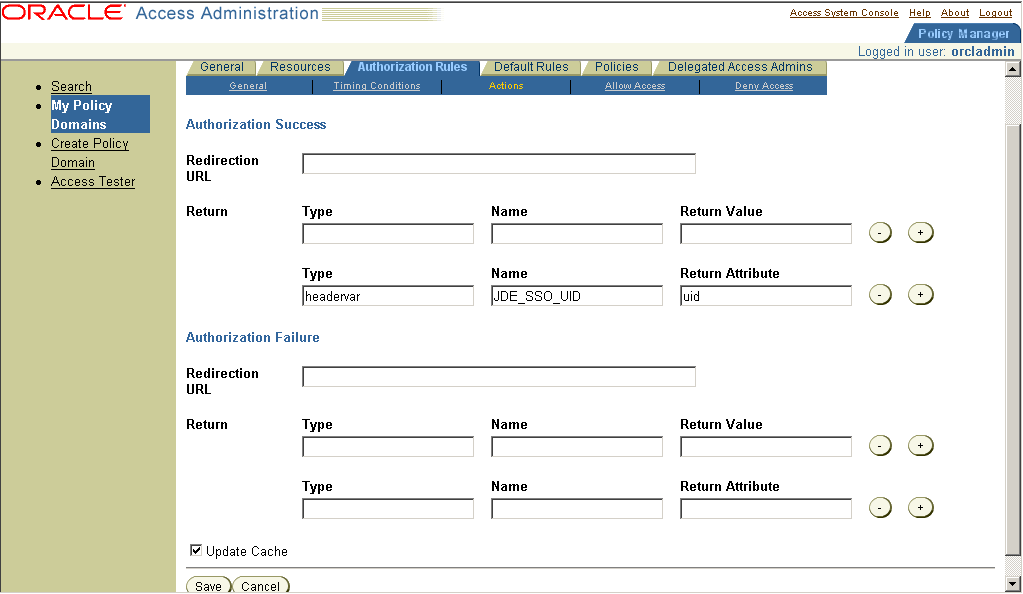
15.2.6 Defining an Authorization Action
You must define an authorization action that sets a custom HTTP header variable upon successful authorization.
If you are already viewing the new policy domain, click Authorization Rules, Actions. Otherwise, click My Policy Domains, the link for the policy domain, Authorization Rules, and then Actions.
The header variable should contain a value that maps to the JD Edwards EnterpriseOne user ID.
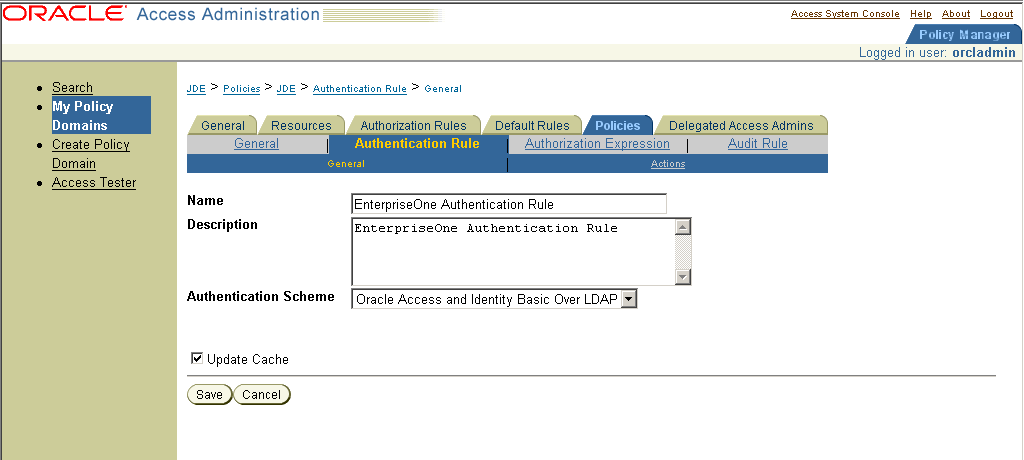
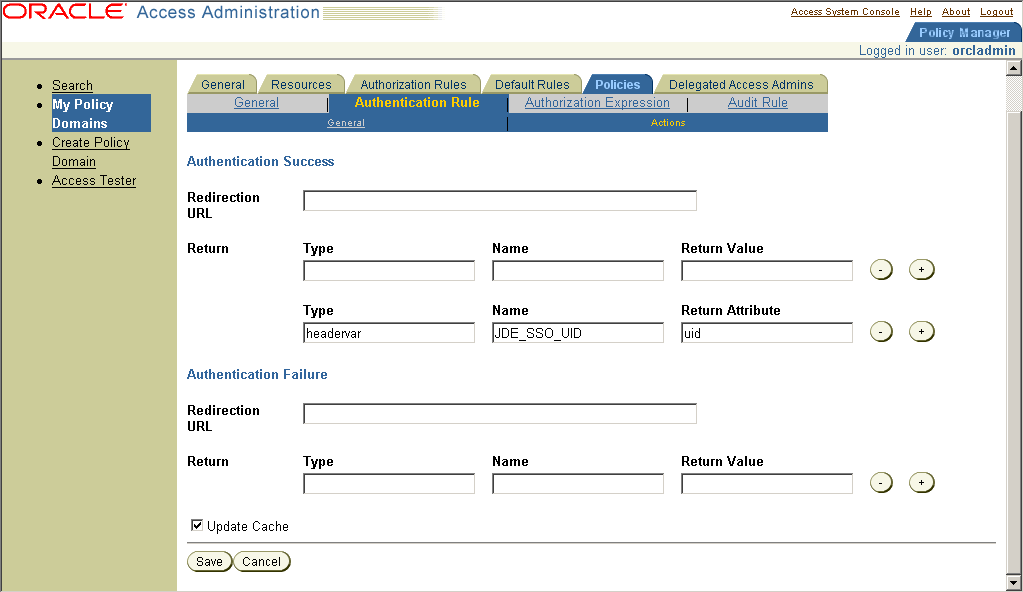
15.2.7 Defining an Authentication Rule
If you are already viewing the new policy domain, click Default Rules, Authentication Rule. Otherwise, click My Policy Domains, the link for the policy domain, Default Rules, and then Authentication Rule.
Figure 15-6 Authentication Rule Configuration page
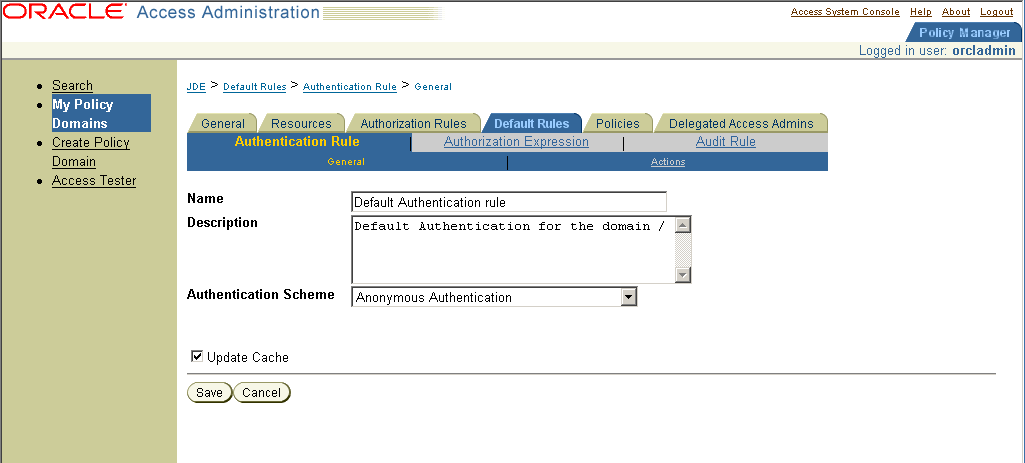
Description of "Figure 15-6 Authentication Rule Configuration page"
Note:
An authentication rule could be, for example, Oracle Access and Identity Basic Over LDAP, form authentication, and so on.15.2.8 Defining an Access Policy and Adding the JD Edwards EnterpriseOne URL Pattern to It
If you are already viewing the new policy domain, click Policies, Add. Otherwise, click My Policy Domains, the link for the policy domain, Policies, and then Add.
Figure 15-7 Policies page with an example of a saved policy
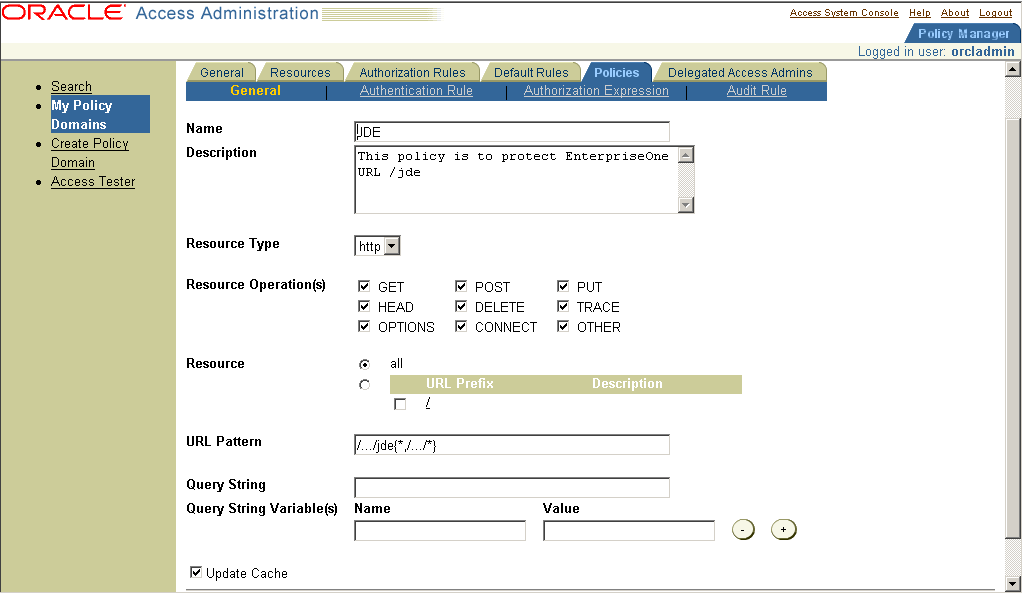
Description of "Figure 15-7 Policies page with an example of a saved policy"
15.2.9 Defining an Authentication Rule for the JD Edwards EnterpriseOne Resources
If you are already viewing the new policy domain, click Policies, JDE, and then Authentication Rule. Otherwise, click My Policy Domains, the link for the policy domain, Policies, JDE, and then Authentication Rule.
15.2.10 Defining an Authentication Action That Sets a Custom HTTP Header Variable Upon Successful Authentication
If you are already viewing the new policy domain, click Policies, JDE, Authentication Rule, and then Actions. Otherwise, click My Policy Domains, the link for the policy domain, Policies, JDE, Authentication Rule, and then Actions.
The header variable should contain a value that maps to the JD Edwards EnterpriseOne user ID.
15.2.11 Defining an Authorization Expression for the JD Edwards EnterpriseOne Resources
If you are already viewing the new policy domain, click Policies, JDE, and then Authorization Expression. Otherwise, click My Policy Domains, the link for the policy domain, Policies, JDE, and then Authorization Expression.
Figure 15-10 Authorization Expression page
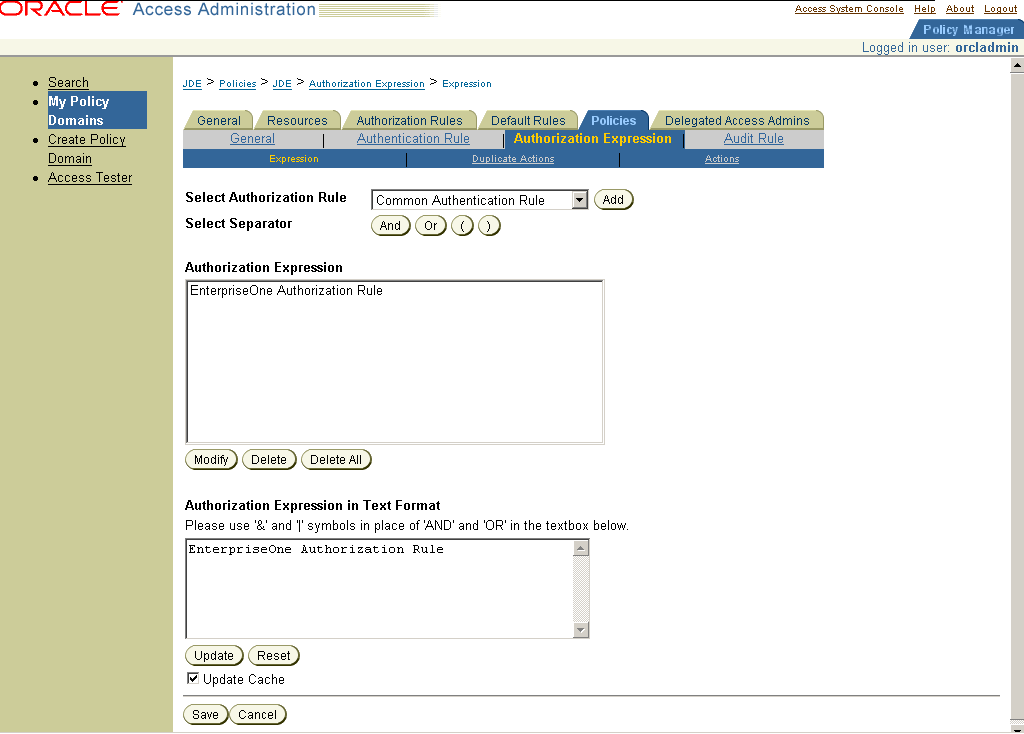
Description of "Figure 15-10 Authorization Expression page"
15.3 Setting Up JD Edwards EnterpriseOne for Single Sign-On Integration with Oracle Access Manager
This section discusses how to set up JD Edwards EnterpriseOne for single sign-on integration with Oracle Access Manager.
-
Access the JD Edwards EnterpriseOne Web client jas.ini file located on the HTML Web Server machine.
-
In the Security section, complete these settings:
Setting Value OracleAccessSSO= TRUE OracleAccessSSOSignOffURL= http://fullyqualifiedhostname:port/access/oblix/lang/en-us/EnterpriseOnelogout.html -
Make sure that the HMTL Web Server machine is set up as a trusted node.
In addition, when setting up the trusted node, you might have to change the key for the encryption and decryption of the authenticate token. The settings for this key are set during the installation of the JD Edwards EnterpriseOne HTML Web Server and are stored in the TokenGen.ini file on the security server.
15.4 Configuring Single Sign-Off
This section discusses how to configure single sign-off for JD Edwards EnterpriseOne.
Note:
If you use the Basic Over LDAP authentication scheme on some versions of Microsoft Internet Explorer, you may get unexpected results with the single sign-off URL. Internet Explorer caches user credentials when a Basic Over LDAP authentication scheme is used. For some versions of Internet Explorer, this means that users can continue to access resources after logging out. If you experience this problem with the single sign-off URL, Oracle recommends that you use a Form over LDAP authentication scheme.-
Create a new HTML page called EnterpriseOneLogout.html.
-
Open the EnterpriseOneLogout.html file in an editor and add the following information to it:
Note:
You can customize the sign-off page if desired.<!doctype html public "-//w3c//dtd html 4.0 transitional//en"> <html lang="en-US"> <head> <title>Oracle Access Manager</title><link rel="stylesheet" type="text/css" href=⇒ "style2/coreid.css"></link> <meta http-equiv="PRAGMA" name="PRAGMA" content="NO-CACHE"> <meta http-equiv="Expires" name="Expires" content="Mon, 06 Jan 1990 00:00:01⇒ GMT"> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <meta name="Description" content="Oracle Access Manager"> <meta name="Robot" content="none"> <meta name="Copyright" content="Copyright © 1996-2006, Oracle. All Rights⇒ Reserved."> <style type="text/css"> <!--.unnamed1 { font-family: Arial, Helvetica, sans-⇒ serif; font-size: 2pt} --></style> <script language="JavaScript"> function delCookie(name,path,domain) { var today = new Date(); var deleteDate = new Date(today.getTime() - 48 * 60 * 60 * 1000); // minus 2⇒ days var cookie = name + "=" + ((path == null) ? "" : "; path=" + path) + ((domain == null) ? "" : "; domain=" + domain) + "; expires=" + deleteDate; document.cookie = cookie; } function delOblixCookie() { // set focus to ok button var isNetscape = (document.layers); if (isNetscape == false || navigator.appVersion.charAt(0) >= 5) { for (var i=0; i<document.links.length; i++) { if (document.links[i].href == "javascript:top.close()") { document.links[i].focus(); break; } } } delCookie('ObTEMC', '/'); delCookie('ObSSOCookie', '/'); delCookie('ObSSOCookie', '/'); delCookie('OBBasicAuth', '/'); delCookie('JSESSIONID', '/jde'); // in case cookieDomain is configured // delete same cookie to all of subdomain var subdomain; var domain = new String(document.domain); var index = domain.indexOf("."); while (index > 0) { subdomain = domain.substring(index, domain.length); if (subdomain.indexOf(".", 1) > 0) { delCookie('ObTEMC', '/', subdomain); delCookie('ObSSOCookie', '/', subdomain); delCookie('OBBasicAuth', '/', subdomain); delCookie('JSESSIONID', '/jde', subdomain); } domain = subdomain; index = domain.indexOf(".", 1); } } </script> </head> <link rel="stylesheet" type="text/css" href="/css/webguistylesheet.jsp"> <body bgcolor="#ffffff" marginwidth="0" marginheight="0" topmargin="0" leftmargin=⇒ ⇒ ⇒ ⇒ ⇒ ⇒ ⇒ "0" onload="delOblixCookie();"> <table width="100%" height="100%" cellpadding="0" cellspacing="0"> <tr> <td height="148" valign="middle"> <p align="center"> <img src="./images/Oracle_JDEE1.gif" alt="Oracle JD Edwards EnterpriseOne⇒ Logo"> </p> </td> </tr> <tr> <td height="250" align="center" valign="middle"> <h3><font size="5">Oracle Access Manager Applications</font></h3> <h3>You have been logged out.</h3> <h3>For security reasons, please close the browser window </h3> <h3>by clicking the OK button.</h3> <a href="javascript:top.close()" onmouseover="self.status='Close the browser⇒ window.'; return true"> <img border="0" alt="Close the browser window." src="style2/NAVok.gif"></a> <script language="JavaScript1.2"> var jdeLegalInfo = "The Programs (which include both the software and⇒ documentation) contain proprietary information; they are provided under a license⇒ agreement containing restrictions on use and disclosure and are also protected by⇒ copyright, patent, and other intellectual and industrial property laws. Reverse⇒ engineering, disassembly, or decompilation of the Programs, except to the extent⇒ required to obtain interoperability with other independently created software or⇒ as specified by law, is prohibited.\nThe information contained in this document⇒ is subject to change without notice. If you find any problems in the⇒ documentation, please report them to us in writing. This document is not⇒ warranted to be error-free. Except as may be expressly permitted in your license⇒ agreement for these Programs, no part of these Programs may be reproduced or⇒ transmitted in any form or by any means, electronic or mechanical, for any⇒ purpose.\nSubject to patent protection under one or more of the following U.S.⇒ patents: 5,781,908; 5,828,376; 5,950,010; 5,960,204; 5,987,497; 5,995,972;⇒ 5,987,497; and 6,223,345. Other patents pending.\nContains GNU libgmp library;⇒ Copyright © 1991 Free Software Foundation, Inc. This library is free software⇒ which can be modified and redistributed under the terms of the GNU Library⇒ General Public License.\nIncludes Adobe® PDF Library, Copyright 1993-2001 Adobe⇒ Systems, Inc. and DL Interface, Copyright 1998-2001 Datalogics Inc. All rights⇒ reserved. Adobe® is a trademark of Adobe Systems Incorporated.\nPortions of this⇒ program contain information proprietary to Microsoft Corporation. Copyright 1985-⇒ ⇒ ⇒ ⇒ ⇒ ⇒ ⇒ 1999 Microsoft Corporation.\nPortions of this program contain information⇒ proprietary to Tenberry Software, Inc. Copyright 1992-1995 Tenberry Software,⇒ Inc.\nPortions of this program contain information proprietary to Premia⇒ Corporation. Copyright 1993 Premia Corporation.\nThis product includes code⇒ licensed from RSA Data Security.\nAll rights reserved.\nThis product includes⇒ software developed by the OpenSSL Project for use in the OpenSSL Toolkit http:⇒ //www.openssl.org/).\nThis product includes cryptographic software written by Eric⇒ Young (eay@cryptsoft.com).\nThis product includes software written by Tim Hudson ⇒ (tjh@cryptsoft.com).All rights reserved."; </script> </td> </tr> <tr> <td valign="bottom"> <table width="100%" border="0" cellspacing="0" cellpadding="5"> <tr> <td width="325"><div class="fineprint"> <script> jdeLegalInfo = "The Programs (which include both the software and⇒ documentation) contain proprietary information; they are provided under a license⇒ agreement containing restrictions on use and disclosure and are also protected by⇒ copyright, patent, and other intellectual and industrial property laws. Reverse⇒ engineering, disassembly, or decompilation of the Programs, except to the extent⇒ required to obtain interoperability with other independently created software or⇒ as specified by law, is prohibited.\nThe information contained in this document⇒ is subject to change without notice. If you find any problems in the⇒ documentation, please report them to us in writing. This document is not⇒ warranted to be error-free. Except as may be expressly permitted in your license⇒ agreement for these Programs, no part of these Programs may be reproduced or⇒ transmitted in any form or by any means, electronic or mechanical, for any⇒ purpose.\nSubject to patent protection under one or more of the following U.S.⇒ patents: 5,781,908; 5,828,376; 5,950,010; 5,960,204; 5,987,497; 5,995,972;⇒ 5,987,497; and 6,223,345. Other patents pending.\nContains GNU libgmp library;⇒ Copyright © 1991 Free Software Foundation, Inc. This library is free software⇒ which can be modified and redistributed under the terms of the GNU Library⇒ General Public License.\nIncludes Adobe® PDF Library, Copyright 1993-2001 Adobe⇒ Systems, Inc. and DL Interface, Copyright 1998-2001 Datalogics Inc. All rights⇒ reserved. Adobe® is a trademark of Adobe Systems Incorporated.\nPortions of this⇒ program contain information proprietary to Microsoft Corporation. Copyright 1985-⇒ ⇒ ⇒ ⇒ ⇒ ⇒ ⇒ 1999 Microsoft Corporation.\nPortions of this program contain information⇒ proprietary to Tenberry Software, Inc. Copyright 1992-1995 Tenberry Software,⇒ Inc.\nPortions of this program contain information proprietary to Premia⇒ Corporation. Copyright 1993 Premia Corporation.\nThis product includes code⇒ licensed from RSA Data Security.\nAll rights reserved.\nThis product includes⇒ software developed by the OpenSSL Project for use in the OpenSSL Toolkit http:⇒ //www.openssl.org/).\nThis product includes cryptographic software written by Eric⇒ Young (eay@cryptsoft.com).\nThis product includes software written by Tim Hudson ⇒ (tjh@cryptsoft.com).All rights reserved."; </script> <a href="#content"><img src="./images/1pix_shim.gif" border="0" alt="Skip⇒ navigation links"></a><a class="fineprint" style="COLOR: black" href="javascript:⇒ alert(jdeLegalInfo);">Legal Terms</a><br> Copyright © 2003-2005, Oracle. All rights reserved. Oracle, JD Edwards, PeopleSoft, and Retek are registered trademarks of Oracle Corporation and⇒ /or its affiliates. Other names may be trademarks of their respective⇒ owners.</div> </td> <td><a name="content"></a></td> </tr> </table> </td> </tr> <noscript>A script enabled browser is required for this page to function properly</noscript> </td> </table> </body> </html> -
Place the EnterpriseOneLogout.html file in a path that is not protected by a WebGate.
The default path is:
Policy_Manager_install_dir/access/oblix/lang/en-us/EnterpriseOneLogout.html
Where Policy_Manager_install_dir is the directory where the Policy Manager is installed.
The file contains Javascript that deletes the ObTEMC, ObSSOCookie, ObBasicAuth, and JSESSIONID cookie. See the appendix on configuring logout in the Oracle Access Manager Access Administration Guide for details.