Oracle Application Object Library Security
Overview of Oracle E-Business Suite Security
As System Administrator, you define Oracle E-Business Suite users, and assign one or more responsibilities to each user.
Defining Application Users
You allow a new user to sign-on to Oracle E-Business Suite by defining an application user. An application user has a username and a password. You define an initial password, then the first time the application user signs on, they must enter a new (secret) password.
When you define an application user, you assign to the user one or more responsibilities.
Responsibilities Define a User's Context
A responsibility provides a context in which a user operates. This context can include profile option values, navigation menus, available concurrent programs, and so on.
For example, a responsibility can allow access to:
-
A restricted list of windows that a user can navigate to; for example, a responsibility may allow certain Oracle Planning users to enter forecast items, but not enter master demand schedule items.
-
A restricted list of functions a user can perform. For example, two responsibilities may have access to the same window, but one responsibility's window may have additional function buttons that the other responsibility's window does not have.
-
Reports in a specific application; as system administrator, you can assign groups of reports to one or more responsibilities, so the responsibility a user choose determines the reports that can be submitted.
Each user has at least one or more responsibilities, and multiple users can share the same responsibility. A system administrator can assign users any of the standard responsibilities provided with Oracle E-Business Suite, or create new custom responsibilities if required.
HRMS Security
The Human Resources Management Systems (HRMS) products have an additional feature using Security Groups. For more information, see: Customizing, Reporting, and System Administration in Oracle HRMS.
Related Topics
Defining a Responsibility
When you define a responsibility, you assign to it some or all of the components described below.
Menu (Required)
A menu is a hierarchical arrangement of application functions (forms). In the definition of a responsibility, the specified menu defines what is displayed in the navigator. The specified menu does not necessarily define the functions that can be accessed by the responsibility, which are granted. See: Overview of Function Security.
Data Group (Required)
A data group defines the mapping between Oracle E-Business Suite products and ORACLE database IDs. A data group determines which Oracle database accounts a responsibility's forms, concurrent programs, and reports connect to. See: Defining Data Groups, Oracle E-Business Suite System Administrator's Guide - Configuration.
Oracle Application Framework functionality does not support data groups.
For almost all cases, you should accept the default value in defining a responsibility.
Function and Menu Exclusions (Optional)
A responsibility may optionally have function and menu exclusion rules associated with it to restrict the application functionality enabled for that responsibility. See: Overview of Function Security.
Additional Notes About Responsibilities
Predefined Responsibilities
All Oracle E-Business Suite products are installed with predefined responsibilities. Consult the reference guide for your Oracle E-Business Suite product for the names of those predefined responsibilities.
Additionally, instances of the major components that help define a responsibility (data groups, request security groups, menus, and functions) are predefined for Oracle E-Business Suite.
Responsibilities and Request Security Groups
Note: The Request Security Groups feature is for backward compatibility only.
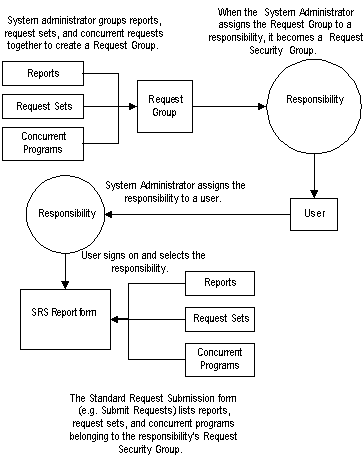
When a request group is assigned to a responsibility, it becomes a request security group.
From a standard submission form, such as the Submit Requests form, the choice of concurrent programs and request sets to run are those in the user's responsibility's request security group.
If you do not include the Submit Requests form on the menu for a responsibility, then you do not need to assign a request security group to the responsibility.
Responsibilities and Function Security
Oracle E-Business Suite architecture may aggregate several related business functions into a single form. Parts of an application's functionality may be identified as individual Oracle E-Business Suite functions, which can then be secured (i.e. included or excluded from a responsibility).
See: Overview of Function Security
Defining Request Security
You can control user access to requests and request sets using request security groups or Role-Based Access Control (RBAC). Beyond this short introduction, request groups and request security groups are discussed in greater detail, as part of a broader range of topics not necessarily limited to application security, in Oracle E-Business Suite System Administrator's Guide - Configuration.
Using Request Security Groups
You can use request security groups to specify the reports, request sets, and concurrent programs that your users can run from a standard submission form, such as the Submit Requests form.
Define a request group using the Request Groups form. Using the Responsibilities form, you assign the request group to a responsibility. The request group is then referred to as a request security group. See: Request Security Groups, Oracle E-Business Suite System Administrator's Guide - Configuration.
You can define a request group to contain single requests, request sets, or all the requests and request sets in an application.
If you choose to include all the requests and requests sets in an application, the user has automatic access to any new requests and request sets (without owners) in the future.
A request security group can contain requests and request sets from different applications. If you want to define request security groups that own requests from different applications, refer to the discussion on Data Groups. See: Defining Data Groups, Oracle E-Business Suite System Administrator's Guide - Configuration.
Note: A request security group or request group is not the same as a security group.
Individual Requests and Request Sets
Reports or concurrent programs which are not included in a request security group on an individual basis, but do belong to a request set included in a request security group, have the following privileges:
-
Users can, however, run request sets that contain requests that are not in their request security group, if the request set is in their request security group.
If you assign a request set, but not the requests in the set, to a request security group, the user:
-
Can edit the request set by deleting requests from it or adding other requests to it, only if the user is the assigned owner of the request set.
-
Cannot edit request information in the request set definition.
-
Cannot stop specific requests in the set from running.
The Request Security Groups figure below illustrates the relationship between a request security group, application user, and a responsibility.
Responsibilities, Request Groups, and Request Security Groups
Request Security using RBAC
By using RBAC, administrators have more granular control in granting submission privileges to users. In short, administrators can assign individual programs/sets, all programs/sets in a request group, programs/sets belonging to one or more applications, and so on, either to the user directly or to a role that can then be assigned to one or more users.
If applications are included in the request groups, all programs/requests sets that are created in these applications will also be automatically included. Please note that request submission applies to both programs and request sets.
See: Controlling Access to Concurrent Programs with Role-Based Access Control (RBAC), Oracle E-Business Suite System Administrator's Guide - Configuration
Related Topics
Overview of Oracle E-Business Suite Security
Request Sets and Owners, Oracle E-Business Suite System Administrator's Guide - Configuration
User Session Limits
Using the following profile options you can specify limits on user sessions.
ICX:Session Timeout
Use this profile option to enforce an inactivity time-out. If a user performs no Oracle E-Business Suite operation for a time period longer than the time-out value (specified in minutes), the user's session is disabled. The user is provided an opportunity to re-authenticate and re-enable a timed-out session. If re-authentication is successful, the session is re-enabled and no work is lost. Otherwise, Oracle E-Business Suite exits without saving pending work.
If this profile option to 0 or NULL, then user sessions will never time out due to inactivity.
ICX: Limit time
Use this profile option to specify the absolute maximum length of time (in hours) of any user session, active or inactive.
Guest User Account
In Oracle E-Business Suite Release 12.1, credentials (username and password) for the Guest user are stored in a secure repository that was specifically designed to store sensitive data such as credentials, certificates and keys. Oracle E-Business Suite products can read Guest user information from this repository using standard APIs.
Note: Prior to Release 12.1, such items were stored in a FND profile option, GUEST_USER_PWD. This profile option did not offer the advanced security features now employed, and is not supported in Release 12.1.
The only supported way to change the Guest user password is to update the context variable s_guest_pass and run AutoConfig, which runs the AdminAppServer utility. See My Oracle Support Knowledge Document 387859.1, Using AutoConfig to Manage System Configurations with Oracle E-Business Suite Release 12. Also see Chapter 2 of Oracle E-Business Suite Administrator's Guide - Configuration for details of AdminAppServer.
Oracle E-Business Suite User Passwords
The following are features related to passwords for end users of Oracle E-Business Suite.
Passwords can be defined in the Users Window; see: Users Window for more information on setting user passwords.
Case Sensitivity in Oracle E-Business Suite User Passwords
In previous releases of Oracle E-Business Suite, user passwords were treated as case insensitive. Now, Oracle E-Business Suite user passwords can optionally be treated as case sensitive, depending on the mode you choose.
Case-sensitivity in passwords is controlled by the site-level profile option Signon Password Case. This profile has two possible settings:
-
Sensitive - Passwords are stored and compared as they are, with the password case preserved. During comparison, if the entered password does not match the decrypted version, then an error message is displayed. With Release 12, this option is the default behavior. All newly created or changed passwords are treated as case sensitive.
Note: Users who have not changed their passwords since the installation of release 12 are not affected until they do change their passwords.
A password expiration utility is available if the System Administrator requires that all users convert to case sensitive passwords upon the next login. This utility expires all passwords in FND_USER, including that of SYSADMIN and default Vision accounts, and can be run as a SQL Script ($FND_TOP/sql/AFCPEXPIRE.sql) or as a Concurrent Program (FNDCPEXPIRE_SQLPLUS).
-
Insensitive (or unset) - Passwords are treated as case insensitive. In Insensitive mode, passwords are stored and compared in uppercase, similar to that in earlier releases. The entered password and the decrypted password are converted to uppercase prior to comparison.
If you want to preserve case insensitivity in passwords, i.e. retain the behavior from previous releases, ensure that Signon Password Case value is either set to 'Insensitive', or not set at all.
There are no upgrade or data migration issues with this new feature. The profile option affects only how new passwords are stored. Existing passwords are tested using the policy in effect when they were created.
Non-Reversible Hash Password Scheme
For enhanced security of passwords, you can use the FNDCPASS utility to migrate local Oracle E-Business Suite user passwords from their current encryption scheme to a non-reversible hash that makes them non-recoverable.
For specific information on FNDCPASS usage, see My Oracle Support Knowledge Document 457166.1, FNDCPASS Utility New Feature: Enhance Security With Non-Reversible Hash Password.
For additional information on FNDCPASS and the related AFPASSWD utility, see: Oracle E-Business Suite Schema Password Change Utilities, Oracle E-Business Suite System Administrator's Guide - Configuration.
Restriction on the GUEST User Password
The GUEST User password cannot include the special character "#".
Overview of Security Groups in Oracle HRMS
Security groups, used exclusively by Oracle HRMS, allow data to be partitioned in a single installation. A single installation can use a particular set of configuration data, but store data for multiple clients, where the data is partitioned by security groups. A user with a responsibility assignment of one security group can only access data within that security group.
A security group represents a distinct client or business entity. Data that must be distinct for each client in an installation is partitioned by security group. All other data is shared across all security groups.
For Oracle Application Object Library, the data items that are "striped" by security groups are responsibility assignments, lookups, and concurrent programs.
Security is maintained at the level of responsibility/security group pairs. That is, users are assigned specific responsibilities within each security group. When signing on to Oracle E-Business Suite, a user, if assigned more than one responsibility, will be asked to choose a responsibility and security group pair. Partitioned data accessed through security group sensitive views will show only data assigned to the current security group.
Use the Enable Security Groups profile option to enable this feature.
Defining Security Groups
Every installation will have a single "Standard" security group seeded in. If no other security groups are created, this single group will be hidden from users when they sign on.
In the Users form, you assign a security group when you assign a responsibility.
For more information, see: Configuring, Reporting and System Administration in Oracle HRMS.
Overview of Function Security
Function security is the mechanism by which user access to applications functionality is controlled.
Function security can be considered as "global data security", in that it grants access to a function regardless of the current row of data.
Oracle E-Business Suite architecture aggregates several related business functions into a single form. Because all users should not have access to every business function in a form, Oracle E-Business Suiteprovides the ability to identify pieces of applications logic as functions. When part of an application's functionality is identified as a function, it can be secured (i.e., included or excluded from a responsibility).
Application developers register functions when they develop forms. A system administrator administers function security by creating responsibilities that include or exclude particular functions.
Terms
Function
A function is a part of an application's functionality that is registered under a unique name for the purpose of assigning it to, or excluding it from, a responsibility.
There are two types of functions: executable functions (formerly called form functions), and non-executable functions (formerly called subfunctions).
Executable Function
Executable functions have the unique property that you may navigate to them using the Navigate window.
Non-executable Function
A non-executable function) is a securable subset of a form's functionality: in other words, a function executed from within a form.
A developer can write a form to test the availability of a particular non-executable function, and then take some action based on whether the non-executable function is available in the current responsibility.
Non-executable functions are frequently associated with buttons or other graphical elements on forms. For example, when a non-executable function is enabled, the corresponding button is enabled.
However, a non-executable function may be tested and executed at any time during a form's operation, and it need not have an explicit user interface impact. For example, if a non-executable function corresponds to a form procedure not associated with a graphical element, its availability is not obvious to the form's user.
Menu
A menu is a hierarchical arrangement of functions and menus of functions. Each responsibility has a menu assigned to it.
Menus can map to permission sets as well.
Menu Entry
A menu entry is a menu component that identifies a function or a menu of functions. In some cases, both a function and a menu of functions correspond to the same menu entry. For example, both a form and its menu of subfunctions can occupy the same menu entry.
Responsibility
A responsibility defines an application user's current privileges while working with Oracle E-Business Suite. When an application user signs on, they select a responsibility that grants certain privileges, specifically:
-
The functions that the user may access. Functions are determined by the menu assigned to the responsibility.
-
The concurrent programs, such as reports, that the user may run.
-
The application database accounts that forms, concurrent programs, and reports connect to.
Related Topics
Functions, Menus, and the Navigate Window
Overview of Oracle E-Business Suite Security
Implementing Function Security
Executable functions vs. Non-executable functions
An executable function, as a whole, including all of its program logic, is always designated as a function. Subsets of a form's program logic can optionally be designated as subfunctions if there is a need to secure those subsets.
For example, suppose that an executable function such as a form contains three windows. The entire form is designated as a function that can be secured (included or excluded from a responsibility). Each of the form's three windows can be also be designated as non-executable functions, which means they can be individually secured. Thus, while different responsibilities may include this form, certain of the form's windows may not be accessible from each of those responsibilities, depending on how function security rules are applied.
Related Topics
Functions, Menus, and the Navigate Window
Functions, Menus, and the Navigate Window
Executable functions are selected using the Navigate window. The arrangement of form names in the Navigate window is defined by the menu structure assigned to the current responsibility.
The following types of menu entries are not displayed by the Navigate window:
-
Non-executable functions
-
Menus without Entries
-
Menu Entries without a Prompt
If none of the entries on a menu are displayed by the Navigate window, the menu itself is not displayed.
Menu Entries with a Submenu and Functions
If a menu entry has both a submenu and a function defined on the same line, then the behavior depends on whether or not the function is executable. If it is executable, then the submenu on the same line is treated as content to be rendered by the function. The submenu will not appear on a navigation tree, but will be available in function security tests (FND_FUNCTION.TEST calls). If the function is not executable, then it is treated as a "tag" for enforcing exclusion rules, and the submenu on the same line is displayed in the navigation tree.
A function is considered executable if it can be executed directly from the current running user interface. For example, an Oracle E-Business Suite form using Oracle Forms is an executable function from within Oracle Forms, but not within the Self Service applications.
How Function Security Works
Registering Functions
-
Developers can require parts of their Oracle Forms code to look up a unique function name, and then take some action based on whether the function is available in the current responsibility. Function names are unique.
-
Developers can register functions. They can also register parameters that pass values to a function. For example, a form may support data entry only when a function parameter is passed to it.
Warning: In general, you should not modify names, parameters, or other material features of predefined functions for Oracle E-Business Suite products. The few exceptions are documented in the relevant manuals or product notes.
Excluding Functions
Each Oracle E-Business Suite product is delivered with one or more predefined menu hierarchies. System Administrators can assign a predefined menu hierarchy to a responsibility. To tailor a responsibility, System Administrators exclude functions or menus of functions from that responsibility using exclusion rules.
Note: The ability to exclude functions is to be used for backward compatibility only. Menu exclusions do not apply to grants.
Available Functions for a User
Functions are available to a user through responsibilities (as well as grants).
When a user first selects or changes their responsibility, a list of functions obtained from the responsibility's menu structure is cached in memory.
Functions a System Administrator has excluded from the current responsibility are marked as unavailable.
Executable functions in the function hierarchy (i.e. menu hierarchy) are displayed in the Navigate window. Available non-executable functions are accessed by working with the application's forms.
Related Topics
Overview of Oracle E-Business Suite Security
Implementing Function Security
Securing Functions Using New Menus
Use the Menus form to define menus pointing to functions that you want to make available to a user.
-
Use forms and their associated menus of non-executable functions to define new menus.
The new menu can be then granted to a user.
Defining a New Menu Structure
When defining a new menu structure:
-
Create a logical, hierarchical listing of functions. This allows for easy exclusion of functions when customizing the menu structure for different responsibilities.
-
Create a logical, hierarchical menu that guides users to their application forms.
Tasks for Defining a Custom Menu Structure
-
Determine the application functionality required for different job responsibilities.
-
Identify predefined menus, forms, and form subfunctions to use as entries when defining a new menu. Understand predefined menus by printing Menu Reports using the Submit Requests window.
Tip: To simplify your work, use predefined menus for your menu entries. You can exclude individual functions after a menu structure is assigned to a responsibility.
-
Plan your menu structure. Sketch out your menu designs.
-
Define the lowest-level menus first. A menu must be defined before it can be selected as an entry on another menu.
-
Assign menus and functions to higher-level menus.
-
Assign menus and functions to a top-level menu (root menu).
-
Document your menu structure by printing a Menu Report.
Warning: Always start with a blank Menus form (blank screen). See Notes About Defining Menus, below.
Notes About Defining Menus
Define Menus for Fast and Easy Keyboard Use
-
Design menu prompts with unique first letters, so typing the first letter automatically selects the form or menu.
-
Design the sequence of menu prompts with the most frequently used functions first (i.e. lower sequence numbers).
Menu Compilation
The Compile Security (FNDSCMPI) concurrent program is used to compile menus so that the system can more quickly check if a particular function is available to a particular responsibility/menu.
You should compile your menus after you make changes to your menu data. A request for this concurrent program is automatically submitted after you make changes using the Menus form.
Related Topics
Compile Security Concurrent Program
Preserving Custom Menus Across Upgrades
Preserve custom menus during upgrades of Oracle E-Business Suite by using unique names for your custom menus. For example, you can start the menu's name with the application short name of a custom application. Define a custom application named Custom General Ledger, whose application short name is XXCGL. Define your custom menu names to start with XXCGL, for example, XXCGL_MY_MENU.
Remember that the Oracle E-Business Suite standard menus may be overwritten with upgrade versions. Therefore, if you attached your custom menu as a submenu to one of the preseeded Oracle E-Business Suite menus, recreate the attachment to it following an upgrade. An alternative is to attach a standard Oracle E-Business Suite menu as a submenu to your custom menu; the link from your custom menu to the standard menu should survive the upgrade.
Related Topics
Overview of Oracle E-Business Suite Security
Implementing Function Security
Overview of Data Security
Data Security allows administrators to control user access to specific data, as well as what functions users can apply to that data.
Function security can be considered "global" data security, in that access to a function is granted regardless of the data.
Concepts and Definitions
Objects
Data Security uses the concept of an Object to define the data records that are secured.
Object
Data security permissions are managed on objects. Business entities such as Projects and Users are examples of objects. Only a securable business-level concept should be registered as an object.
An object definition includes the business name of the object and identifies the main table and primary key columns used to access the object.
Object Instance
An object instance is a specific example of an object, such as Project Number 123 or User JDOE. An object instance generally corresponds to a row in the database. An instance is identified by a set of one or more primary key values as defined by the object.
In addition, "All Rows" for an object indicates all data rows of the object.
Object Instance Set
An object instance set is a group of related object instances within an object. A set is specified as a predicate on the keys or attributes of an object, expressed as a SQL "WHERE clause". All instances that satisfy the predicate are considered members of the object instance set. For example:
STATUS = 'ACTIVE'
could determine a set of object instances with the "Active" status.
The specific instances in the set can vary over time as object instance attributes change, or as new object instances are created.
An example is:
OWNER = FND_GLOBAL.USER_ID
The predicate can also be parameterized, so that the logic can define instance sets as a function of one or more input parameters. An example is:
COLOR = :PARAM1
Object instance sets are also called "data instance sets".
Users and Groups
Users and groups are Oracle Workflow roles. See the Oracle Workflow documentation for more information on roles.
Privileges given to users and groups determine their access to secured objects.
The data security system allows you to assign privileges to groups of users instead of assigning privileges to each user individually.
Users
Users are individuals who have access to software applications at a particular enterprise.
A user must have a unique name and should map one-to-one with an individual human or system. "Group" accounts are not correct uses of the user entity.
Groups
Users can belong to Groups. The grouping can come from position or organization relationships modeled in applications such as Oracle Human Resources. Alternatively, ad-hoc groups can be created explicitly for security purposes. A group is sometimes referred to as a role.
Functions and Permissions
A function or a permission is the smallest unit of securable product functionality. You can register function definitions with the security system to represent actions that can be performed on an object or on the system in general. Granting a function to a set of users gives them permission to perform that function, and so a function may also be referred to as a permission.
There are two broad categories of functions and permissions:
-
An executable function/permission can be invoked from a generic navigator user interface. An executable function definition must contain all information necessary to launch the function; often this includes the form name or URL plus parameters.
-
An abstract function/permission does not refer to a specific piece of code, but represents permission to perform a higher-level business action. The code that implements an abstract function calls the function security system to test whether the abstract function is granted. The system only allows the action if the abstract function is granted.
Examples of these are a particular JSP page (executable) and View Person (abstract).
Functions and permissions can either be at the system level or be sensitive to a data context.
Navigation Menus and Permission Sets
Functions and permissions are grouped into related sets so that administration of these functions can be performed in higher-level business terms.
Functions and permissions are bundled into named sets, which can be defined for two purposes: as navigation menus and/or permission sets. Each set can also contain other sets.
Menus are defined for navigation purposes and group UI pages into functional areas. Users access menus by selecting responsibilities. Each menu item maps to a permission which optionally may be granted to the user as part of the menu/responsibility assignment. Menu items that are not granted as part of the menu/responsibility assignment will not be rendered unless the user is granted the permission separately.
Permission sets are granted to users or roles independently of menus/responsibilities. Permission sets are granted to users in order to enable menu items and other operations (functions) that should not be available to all users assigned a given menu/responsibility. Permission sets are granted to users or roles through permission assignments (grants).
Grants
A grant authorizes a particular role to perform a specified action or actions (set of functions) on a specified object instance (or object instance set).
Note that where you are creating a data security policy for an object by creating a grant, you need to include that object in your grant definition. Other than in this specific type of case, you do not need to specify an object in your definition.
Security Context
Security context refers to the context of the data in which the user is working. For example, data context could be the organization or responsibility with which the user is logged in.
Implementation of Data Security
Implement data security by granting access to a set of functions (either a navigation menu or a permission set) to a user or group of users.
Data security policies can reflect access to:
-
A specific instance (row) identified by a primary key value
-
All instances (rows) of an object
-
An instance set defined by a SQL predicate (WHERE clause)
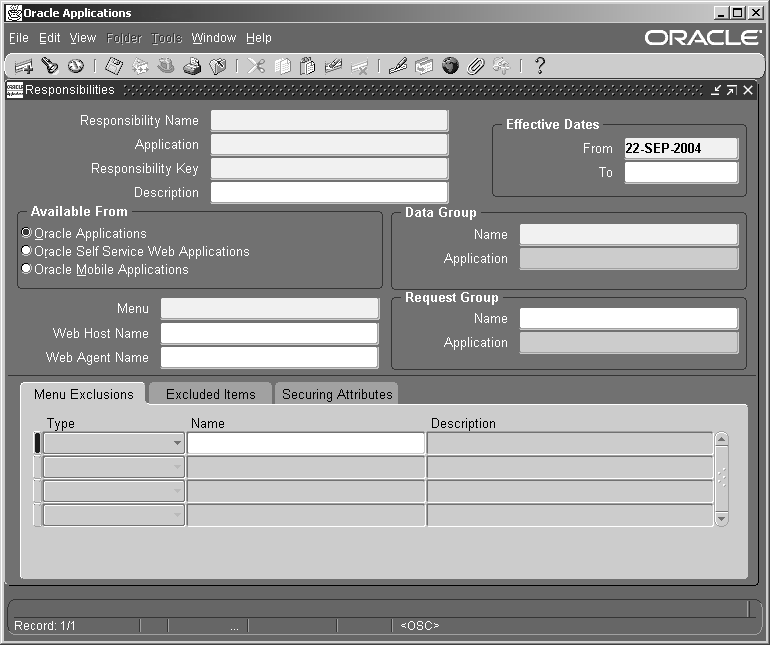
Responsibilities Window
Use this window to define a responsibility. Each application user is assigned at least one responsibility.
A responsibility determines whether the user accesses Oracle E-Business Suite or Oracle Mobile Applications; which applications functions a user can use; which reports and concurrent programs the user can run; and which data those reports and concurrent programs can access.
Responsibilities cannot be deleted. To prevent a responsibility from being used, set the Effective Date's To field to a past date and restart Oracle E-Business Suite.
See: Overview of Function Security
Before defining your responsibility, do the following:
-
Use the Data Groups window to list the ORACLE username your responsibility's concurrent programs reference on an application-by-application basis.
-
Use the Request Groups window to define the Request Group you wish to make available with this responsibility.
-
Use the Menus window to view the predefined Menu you can assign to this responsibility.
Responsibilities Block
An application name and a responsibility name uniquely identify a responsibility.
Responsibility Name
If you have multiple responsibilities, a pop-up window includes this name after you sign on.
Application
The owning application for the responsibility.
This application name does not prevent the user of this responsibility from accessing other applications' forms and functions if you define the menu to access other applications.
Responsibility Key
This is the internal key for the responsibility that is used by loader programs, (concurrent programs that load messages, user profiles, user profile values, and other information into Oracle E-Business Suite tables). The responsibility key is unique per application.
Avoid using the following characters in the responsibility keys: !, ", ;, [, ], (, ), {, }, %, |, <, >.
Effective Dates (From/To)
Enter the start/end dates on which the responsibility becomes active/inactive. The default value for the start date is the current date. If you do not enter an end date, the responsibility is valid indefinitely.
You cannot delete a responsibility, because its information helps to provide an audit trail. You can deactivate a responsibility at any time by setting the end date to the current date. If you wish to reactivate the responsibility later, either change the end date to a date after the current date, or clear the end date.
Available From
This is the navigator from which the responsibility will be available (Oracle E-Business Suite forms navigator, mobile navigator).
A responsibility may be associated with only one Oracle E-Business Suite system.
Data Group
Note: Data groups are used for backward compatibility only. Oracle Application Framework does not support the data groups feature.
Name/Application
The data group defines the pairing of application and ORACLE username.
Select the application whose ORACLE username forms connect to when you choose this responsibility. The ORACLE username determines the database tables and table privileges accessible by your responsibility. Transaction managers can only process requests from responsibilities assigned the same data group as the transaction manager.
Menu
The menu whose name you enter must already be defined with Oracle E-Business Suite. See: Menus.
Request Group - Name/Application
Specify a request security group to associate the responsibility to a set of requests, request sets, or concurrent programs that users logged in with this responsibility can run from the Submit Requests window. Note that such users can also access requests from a Submit Requests window you customize with a request group code through menu parameters
Note: The Request Security Groups feature is provided for backward compatibility.
New responsibilities should be created in accordance with Role-Based Access Control and should not have a default request security group.
See:
Overview of Oracle E-Business Suite Security
Customizing the Submit Requests Window Using Codes, Oracle E-Business Suite System Administrator's Guide - Configuration
Request Groups, Oracle E-Business Suite System Administrator's Guide - Configuration
Menu Exclusions Block
Note: Menu exclusions should be used for backward compatibility only.
Define function and menu exclusion rules to restrict the application functionality accessible to a responsibility.
Type
Select either Function or Menu as the type of exclusion rule to apply against this responsibility.
-
When you exclude a function from a responsibility, all occurrences of that function throughout the responsibility's menu structure are excluded.
-
When you exclude a menu, all of its menu entries, that is, all the functions and menus of functions that it selects, are excluded.
Name
Select the name of the function or menu you wish to exclude from this responsibility. The function or menu you specify must already be defined in Oracle E-Business Suite.
HTML-Based Applications Security
Oracle HTML-based applications use columns, rows and values in database tables to define what information users can access. Table columns represent attributes that can be assigned to a responsibility as Securing Attributes or Excluded Attributes. These attributes are defined in the Web Application Dictionary.
Excluded Items
Use the List of Values to select valid attributes. You can assign any number of Excluded Attributes to a responsibility.
Securing Attributes
Use the List of Values to select valid attributes. You can assign any number of securing attributes to the responsibility.
Security Groups Window
This form is for HRMS security only.
For more information on setting up system administration for the HRMS products, see: Customizing, Reporting, and System Administration in Oracle HRMS.
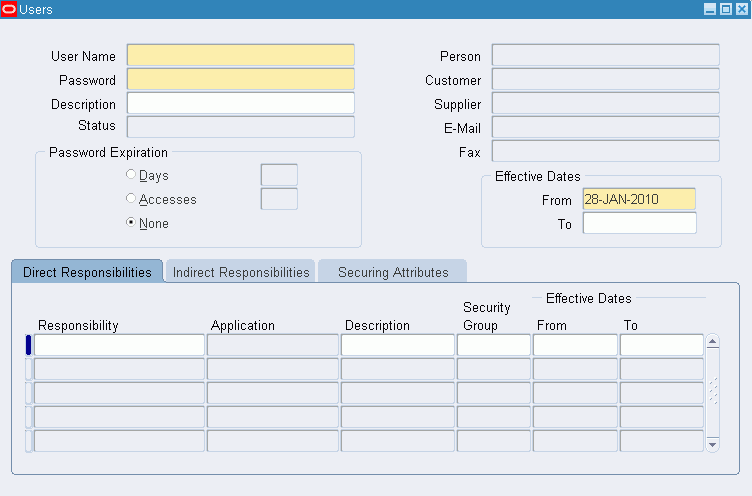
Users Window
Use this window to define an Oracle E-Business Suite user. This user is an authorized user of Oracle E-Business Suite, and is uniquely identified by a username.
Once defined, a new Oracle E-Business Suite user can sign on to Oracle E-Business Suite and access data through Oracle E-Business Suite windows.
Note: If you have upgraded from a previous release of Oracle E-Business Suite, ensure that you have run the Party Merge concurrent program to update your user data. If you have not run this program, you may receive errors in querying your user data.
For more information, see the Oracle Trading Community Architecture documentation.
Users Block
Enter these fields for the user.
User Name
An application user enters this username to sign on to Oracle E-Business Suite.
The username should only contain characters allowed by Oracle Single Sign-On.
Tip: We recommend that you define meaningful usernames, such as the employee's first initial followed by their last name. Or, for a group account, you can define the application username so as to indicate the purpose or nature of the group account.
Password
Enter the initial password of an application user. An application user enters this password along with his username to sign on to Oracle E-Business Suite.
-
A password must be at least five (5) characters and can be up to thirty (30) characters.
-
All characters are allowed except control characters, which are non-printable. Oracle encourages the use of non-alphanumeric characters because they add complexity, making passwords harder to guess.
This window does not display the password you enter. After you enter a password, you must re-enter it to ensure you did not make a typing error.
If the application user already exists and the two entries do not match, the original password is not changed and an error message is displayed.
If you are defining a new application user and the two entries do not match, you are required to enter the password again. For a new user, you cannot navigate to the next field until the two entries match.
The first time an application user signs on, he must change his password. If a user forgets his password, you can reassign a new password in this field.
As System Administrator, you can set an initial password or change an existing password, but you cannot access the user's chosen password.
You can set the minimum length of Oracle E-Business Suite user passwords using the profile option Signon Password Length. If this profile option is left unset, the minimum length defaults to 5.
You can set the minimum number of days that a user must wait before being allowed to reuse a password with the Signon Password No Reuse profile option.
You can use the profile option Signon Password Hard to Guess to set rules for choosing passwords to ensure that they will be "hard to guess." A password is considered hard-to-guess if it follows these rules:
-
The password contains at least one letter and at least one number.
-
The password does not contain the username.
-
The password does not contain repeating characters.
The Signon Password Failure Limit profile option determines the maximum number of login attempts before the user’s account is disabled.
For information on case sensitivity in passwords, see: Case Sensitivity in Oracle E-Business Suite User Passwords.
Status
The Status field indicates the status of the user account. This field is display-only and values are generated by the system. This field is similar to Status in Oracle User Management for managing user accounts.
Possible statuses of a user account are:
-
Unassigned - This status is used for the moment of creating a new user in the form, before committing the transaction. Since a user ID hasn't been assigned yet at that moment, the record status is Unassigned.
-
Pending - This user account exists but cannot be used yet. For example, a user account with "Effective Dates" that are in the future would have a Pending status.
-
Locked - This user account is locked. For example, if a user has unsuccessfully tried to log in over the maximum number of tries allowed (per the profile option "Signon Password FailureLimit"), then the user account becomes locked.
-
Active - The status for a user account is Active if both of the following conditions are true:
-
The start date is not NULL and is before or equal to the current date
-
The end date is NULL or is after the current date
-
-
Inactive - This user has an inactive account. For example, a user account with "Effective Dates" that are in the past would have an Inactive status.
Person, Customer, and Supplier
Use these fields to enter the name of an employee (person), customer, or supplier contact. Enter the last name and first name, separated by a comma, of the employee, customer, or supplier who is using this application username and password. Use the List of Values to select a valid name.
For more information on using these fields, see the Oracle Trading Community Architecture documentation.
Email/Fax
Enter the email address and/or fax number for this user.
Password Expiration
-
Days - Enter the maximum number of days between password changes. A pop-up window prompts an application user to change his password after the maximum number of days you specify has elapsed.
-
Accesses - Enter the maximum allowed number of sign-ons to Oracle E-Business Suite allowed between password changes. A pop-up window prompts an application user to change his password after the maximum number of accesses you specify has elapsed.
Tip: We recommend that you requireall application users to make regular password changes. This reduces the likelihood of unauthorized access to Oracle E-Business Suite.
Effective Dates (From/To)
The user cannot sign on to Oracle E-Business Suite before the start date or after the end date. The default for the start date is the current date. If you do not enter an end date, the username is valid indefinitely.
You cannot delete an application user from Oracle E-Business Suite because this information helps to provide an audit trail. You can deactivate an Oracle E-Business Suite user at any time by setting the End Date to the current date.
If you wish to reactivate a user, change the End Date to a date after the current date, or clear the End Date field.
Direct Responsibilities
Direct responsibilities are responsibilities assigned to the user directly.
Responsibility
Select the name of a responsibility you wish to assign to this application user. A responsibility is uniquely identified by application name and responsibility name.
Security Group
This field is for HRMS security only. See: Customizing, Reporting, and System Administration in Oracle HRMS.
This field is enabled only if the profile Enable Security Groups is enabled.
From/To
You cannot delete a responsibility because this information helps to provide an audit trail. You can deactivate a user's responsibility at any time by setting the End Date to the current date.
If you wish to reactivate the responsibility for the user, change the End Date to a date after the current date, or clear the End Date.
Indirect Responsibilities
Indirect responsibilities are used with Oracle User Management only. A user may "inherit" an indirect responsibility through membership of a group to which the responsibility has been assigned.
This block is read-only.
Securing Attributes
Securing attributes are used by some Oracle HTML-based applications to allow rows (records) of data to be visible to specified users or responsibilities based on the specific data (attribute values) contained in the row.
You may assign one or more values for any of the securing attributes assigned to the user. If a securing attribute is assigned to both a responsibility and to a user, but the user does not have a value for that securing attribute, no information is returned for that attribute.
For example, to allow a user in the ADMIN responsibility to see rows containing a CUSTOMER_ID value of 1000, assign the securing attribute of CUSTOMER_ID to the ADMIN responsibility. Then give the user a security attribute CUSTOMER_ID value of 1000.
When the user logs into the Admin responsibility, the only customer data they have access to has a CUSTOMER_ID value of 1000.
Attribute
Select an attribute you want used to determine which records this user can access. You can select from any of the attributes assigned to the user's responsibility.
Value
Enter the value for the attribute you want used to determine which records this user can access.
Related Topics
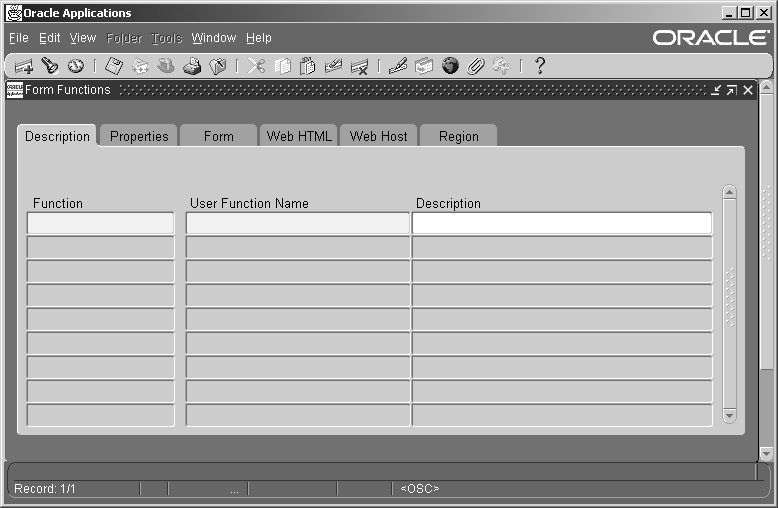
Form Functions Window
Used to define new functions. A function is a part of an application's functionality that is registered under a unique name for the purpose of assigning it to, or excluding it from, a responsibility.
Description
Fields include:
Function
Users do not see this unique function name. However, you may use this name when calling your function programmatically. You should follow the naming conventions for functions.
User Function Name
Enter a unique name that describes your function. You see this name when assigning functions to menus. This name appears in the Top Ten List of the Navigator window.
Properties
Fields include:
Type
A function's type describes its use. A function's type is passed back when a developer tests the availability of a function. The developer can write code that takes an action based on the function's type.
Standard function types include the following:
| Variable | Description |
|---|---|
| ADFX | External ADF Application. Used for linking an external Application Developer Framework (ADF) 11g application deployed on an Oracle Application Server 11g container from the Oracle E-Business Suite home page. |
| DBPORTLET | Database provider portlet. |
| FORM | Oracle E-Business Suite form functions are registered with a type of FORM. |
| JSP | Functions used for some products in the Oracle Self-Service Web Applications. These are typically JSP functions. |
| REST | REST service. |
| SERVLET | Servlet functions used for some products in the Oracle Self-Service Web Applications. |
| SUBFUNCTION | Subfunctions are added to menus (without prompts) to provide security functionality for forms or other functions. |
| WEBPORTLET | Web provider portlet. |
| WWK | Functions used for some products in the Oracle Self-Service Web Applications. These are typically PL/SQL functions that open a new window. |
| WWR or WWL | Functions used for some products in the Oracle Self-Service Web Applications. |
| WWJ | OA Framework JSP portlet. |
| WWW | Functions used for some products in the Oracle Self-Service Web Applications. These are typically PL/SQL functions. |
For information on functions used by Oracle Application Framework, see the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1087332.1, Oracle Application Framework Release Notes, Release 12.1.3.
Maintenance Mode Support
This field determines whether this function will be supported while the system is in Maintenance Mode. See Oracle E-Business Suite Concepts for more information on Maintenance Mode.
Context Dependence
In general, the context dependence determines the required context for the function to work properly. The context dependence controls whether the user must choose a specified context (if not already in that context) before executing the function.
For example, some functions are controlled by profile options that affect what the user can perform within the current context. Types of context dependence are:
-
Responsibility - The function is controlled by the user's responsibility (RESP_ID/RESP_APPL_ID (includes ORG_ID)).
-
Organization - The function is controlled by the user's organization (ORG_ID).
-
Security Group - The function is controlled by the user's security group (service bureau mode).
-
None - There is no dependence on the user's session context.
Form
Fields include the following:
Form/Application
If you are defining a form function, select the name and application of your form.
Parameters
Enter the parameters you wish to pass to your function. Separate parameters with a space.
For an executable (form) function:
-
If you specify the parameter QUERY_ONLY=YES, the form opens in query-only mode. Oracle Application Object Library removes this parameter from the list of form parameters before opening the form in query-only mode.
-
You can also specify a different form name to use when searching for help for a form in the appropriate help file. The syntax to use is:
HELP_TARGET = "alternative_form_name"
Your form name overrides the name of the form. See: Help Targets in Oracle E-Business Suite, Oracle E-Business Suite System Administrator's Guide - Configuration.
For a concurrent program submitted through the Standard Request Submission form, the following syntax may be used:
TITLE="appl_short_name:message_name"
where appl_shortname:message_name is the name of a Message Dictionary message. See: Customizing the Submit Requests Window using Codes, Oracle E-Business Suite System Administrator's Guide - Configuration.
Warning: In general, system administrators should not modify parameters passed to predefined functions for Oracle E-Business Suite products. The few exceptions are documented in the relevant manuals or product notes.
Web HTML
The fields in the Web HTML and Web Host are only required if your function will be accessed from Oracle Application Framework. You do not need to enter any of these fields for functions based on Oracle Developer forms.
HTML Call
The last section of your function URL is the HTML Call. The HTML Call is used to activate your function. The function may be either a static web page or a procedure.
The syntax for this field depends on the function type.
For functions used with Mobile Application Server, enter the full name of your java class file, including <package name>.<class name>. The class name and package name are case sensitive. Mobile Application Server will try to load this class from the classpath as it is. For example, 'oracle.apps.mwa.demo.hello.HelloWorld'.
Web Host
The fields in the Web HTML and Web Host are optional and only enabled for some types of functions. These fields apply only to Oracle Application Framework functions.
Host Name
The URL (universal resource locator) or address required for your function consists of three sections: the Host Name, Agent Name, and the HTML Call. The Host name is the IP address or alias of the machine where the Web server is running.
Agent Name
The second section of your function URL is the Oracle Web Agent. The Oracle Web Agent determines which database is used when running your function. Defaults to the last agent used.
Icon
Enter the name of the icon used for this function.
Secured
Secured is only required when your function is accessed by Oracle Workflow. Checking Secured enables recipients of a workflow email notification to respond using email.
Encrypt Parameters
Checking Encrypt Parameters adds a layer of security to your function to ensure that a user cannot access your function by altering the URL in their browser window. You must define Encrypt Parameters when you define your function to take advantage of this feature.
Region
The fields on this page are for future use.
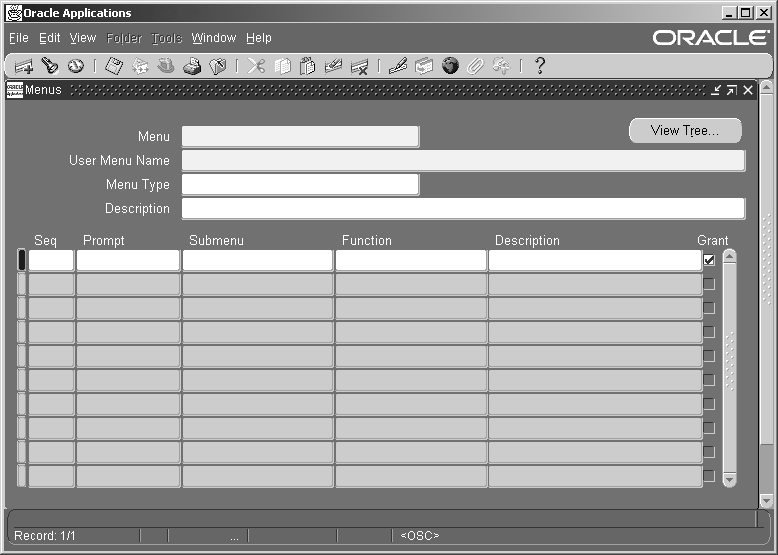
Menus Window
Used to define a new menu or modify an existing menu.
A menu is a hierarchical arrangement of functions and menus of functions. Each responsibility has a menu assigned to it.
You can build a custom menu for that responsibility using predefined forms. However, we recommend that you do not disassociate a form from its developer-defined menus.
After you save your changes in this form, a request is submitted to compile the menu data.
See:
Implementing Function Security
Before you define your menu, perform the following:
-
Register your application with Oracle Application Object Library using the Applications window.
-
Register any forms you wish to access from your menu with Oracle Application Object Library using the Forms window.
-
Define any functions you intend to call from your menu.
-
Define any menus that you intend to call from your menu. Define the lowest-level submenus first. A submenu must be defined before it can be called by another menu.
Tip: By calling submenus from your menu, you can group related windows together under a single heading on your menu. You can reuse your menu on other menus.
Menus Block
Menu entries detail the options available from your menu.
Menu
Choose a name that describes the purpose of the menu. Users do not see this menu name.
Note: Once the menu is saved, this menu name cannot be updated.
View Tree...
Once you have defined a menu, you can see its hierarchical structure using the "View Tree..." button. See: Menu Viewer.
User Menu Name
You use the user menu name when a responsibility calls a menu or when one menu calls another.
Menu Type
Specify a menu type to describe the purpose of your menu. Options include:
-
Standard - for menus that would be used in the Navigator form
-
Tab - for menus used in self service applications tabs
-
Security - for menus that are used to aggregate functions for data security or specific function security purposes, but would not be used in the Navigator form
In addition, see the section on Oracle Application Framework menu types.
Menu Entries Block
Fields include the following:
Sequence
Enter a sequence number to specify where a menu entry appears relative to other menu entries in a menu. The default value for this field is the next whole sequence number.
Important: You can only use integers as sequence numbers.
A menu entry with a lower sequence number appears before a menu entry with a higher sequence number.
You cannot replace a menu entry sequence number with another sequence number that already exists. If you want to add menu entries to a menu entry sequence, carefully renumber your menu entries to a sequence range well outside the sequence range you want, ensuring that you do not use existing sequence numbers. Once you save this work, you can go back and renumber each entry to have the final sequence number you want.
Navigator Prompt
Enter a user-friendly, intuitive prompt your menu displays for this menu entry. You see this menu prompt in the hierarchy list of the Navigator window.
Tip: Enter menu prompts that have unique first letters so that power users can type the first letter of the menu prompt to choose a menu entry.
Submenu
Call another menu and allow your user to select menu entries from that menu.
Function
Call a function you wish to include in the menu. A form function (form) appears in the Navigate window and allows access to that form. Other non-form functions (subfunctions) allow access to a particular subset of form functionality from this menu.
Description
Descriptions appear in a field at the top of the Navigate window when a menu entry is highlighted.
Grant
The Grant check box should usually be checked. Checking this box indicates that this menu entry is automatically enabled for the user. If this is not checked then the menu entry must be enabled using additional data security rules.
For more information on grants, see Overview of Data Security and Grants.
Menu Viewer
The Menu Viewer is a read-only window that provides a hierarchical view of the submenus and functions of a menu, and also lists properties of the menus and functions.
You can launch the viewer from the Menus form by clicking on the "View Tree..." button. The viewer will appear for the menu specified in the Menus form.
Note: When you are creating or editing a new menu, your changes must be committed to the database before you will be able to see them in the Menu Viewer.
Functionality
The Menu Viewer consists of two panes, one showing the menu tree and the other the node properties.
Menu Tree
To view the menu tree, click on the plus (+) sign next to the menu. You will see a hierarchical tree with a number of nodes. Each node represents a function or submenu of your main menu.
Note: The menu tree displays the user menu name for the main menu, and displays the prompts from the Menus form for submenus and functions. If no prompt has been specified, then no label will appear for the node.
To print a menu tree, choose Print from the File menu.
Node Properties
To view properties of a particular menu or function, highlight the node in the menu tree. The node properties will appear in the Properties pane. You can create a separate Properties page for a node by clicking the "push pin" button at the top of the Properties pane.
The entry's sequence number, prompt, and description are shown.
View Options
The View menu provides options on how the viewer displays your menu.
You can specify whether the Node Properties pane, the toolbar, or the status bar are displayed. You can also choose the display style in which you view your menu tree.
Display Styles
There are three styles for viewing your menu tree. You can select one from the View menu or from the buttons on the toolbar.
| Variable | Description |
|---|---|
| Vertical | Menu entries are displayed vertically, similar to how they appear in the Navigator window when you log on to Oracle E-Business Suite. |
| Interleaved | Menu entries are displayed horizontally and vertically. |
| Org-Chart | Menu entries are displayed horizontally as in an organizational chart. |
Edit Menu
From the Edit menu you can bring up a Properties window for the node you have highlighted in the menu tree.
Note: You can view the properties for your menu or function here, but you cannot edit them.
You can view and edit your Preferences for the Menu Viewer. You can choose colors for your menu tree pane as well as the text font and size.
Objects
Use these pages to find, create, and edit data objects. You define objects to be secured in the Data Security system.
Objects can be tables or views. An object must be queryable in SQL, and the combination of primary key columns specified must be a unique key.
In these pages, objects are described with the following
-
The Name is the name that appears in the Object Instance Set and Grants pages. This name should be user-friendly.
-
The Code is the internal name of the object.
-
The Application Name is the owning application.
-
The Database Object Name is the name of the underlying database object.
Related Topics
Find Objects
Use this page to find an existing object.
Simple Search
Name
The display name of the object.
Code
The object name.
Application Name
The object's owning application.
Database Object Name
The database object name.
Advanced Search
Use the Advanced Search screen to find data that meet a set of criteria. With the Advanced Search screen, you can enter in special conditions based on the given fields, and the search results will consist of all data that match the conditions.
For example, for a specified application, you can search for all objects whose name begins with a letter before "P". (Note: all uppercase letters precede all lowercase letters for this type of search).
Search Results
The search results are shown in a table with the following columns:
-
Name - click on the object name to view details on the object.
-
Code
-
Application Name
-
Database Object
-
Description
-
Last Update
To update an object, click on the icon under the Update column.
Update Object
Use this page to update the fields listed below for an object. You cannot change the internal Object Name of an existing object.
Display Name
Enter a user-friendly name for the object.
Application Name
The owning application for the object. This application owns the database table on which the object is based.
Database Object Name
Typically this is a table in the database.
Description
Enter a description for the object.
Create Object
Use this page to create a new object. Enter the following information:
Name
Enter a user-friendly name for the object.
Code
Enter a code that will be used as an internal name for the object. This name cannot include spaces and can include underscores and hyphens. You cannot update the object name after the object is created and saved.
Application Name
The owning application for the object. This application owns the database table on which the object is based.
Database Object
Typically this is a table in the database.
Description
Enter a description for the object.
Object Column Details
Enter in information on the primary key for the object (n below indicates an integer between 1 and 5). The primary key is used to identify rows (object instances) for inclusion in object instance sets.
PKn Column Name
The primary key column name.
PKn Column Type
The datatype for the column.
Object Detail
This page provides the following information for an object:
-
Object Name
-
Display Name
-
Application
-
Database Object Name
-
Description
Columns
You can also view details on columns that comprise the primary key (n below indicates an integer between 1 and 5):
-
PKn Column Name
-
PKn Column Type
Instances of an object can be grouped together into an object instance set. For example, you may want to create a group of projects or a group of items. To create and manage objects instance sets, click on the "Manage Object Instance Sets" button.
Click on the "Return to Object Search" link to go back to the main Objects page.
Delete Object
Confirm the deletion of an object from this page. Review the information shown, and click the "Delete" button.
Related Topics
Object Instance Sets
After you create an object you can create a set of instances of the object. For example, you could define the object "User" corresponding to the User table. Each row in the User table becomes an instance of the User object. Users in the sales organization could then be grouped into an Object Instance Set named "Sales Organization".
Object Instance Sets are described by the following:
-
The Object Instance Set Name is its internal name. This name must not contain any spaces and can include underscores.
-
The Display Name is a user-friendly name for the object that appears in the Grants pages.
-
The Predicate is the WHERE clause used to define the object instances in the set. It must be a valid SQL predicate for the database object.
Manage Object Instance Set
Use this page to manage existing object instance sets or create new ones.
The following object information is displayed:
-
Object Name
-
Display Name
-
Application
-
Database Object Name
-
Description
Existing Object Instance Sets
-
Instance Set Name - click on the Instance Set Name to view details
-
Display Name
-
Description
To update an object, click on the icon under the Details column to open up the Update Object page.
To delete a row, click on the icon under the Delete icon, or select the object and click the Delete button.
To return to the main Objects page, click on the "Return to Object Search" link.
Related Topics
Create Object Instance Set
The containing object's Name, Display Name, Application ID, Database Object Name, and Description are shown.
Enter the following for the Object Instance Set:
Code
Enter a name that will be used internally for the object instance set. This name cannot include spaces and can include underscores and hyphens. The Object Instance Set Name cannot be updated once the object instance set has been created and saved.
Name
Enter a user-friendly, descriptive name to appear in the Grants pages.
Description
Enter a description for the object instance set.
Predicate
This predicate determines which object instances are included in the set. Do not include "WHERE" in your entry, but only the body of the WHERE clause.
Update Object Instance Set
The containing object's Name, Display Name, Application ID, Database Object Name, and Description are shown.
Note: The Object Instance Set Name cannot be updated after the object instance set has been created and saved.
Display Name
Enter a user-friendly, descriptive name to appear in the Grants pages.
Description
Enter a description for the object instance set.
Predicate
This predicate determines which object instances are included in the set. Do not include "WHERE" in your entry, but only the body of the WHERE clause.
Delete Object Instance Set
Confirm the deletion of an object from this page. Review the information shown, and click the "Delete" button.
Related Topics
Object Instance Set Details
Details of an object instance set are shown on this page.
The containing object's Name, Display Name, Application ID, Database Object Name, and Description are shown.
The following is shown for the object instance set:
-
Code
-
Name
-
Description
-
Predicate
Use the "Return to Manage Object Instance Sets" to return to the main page.
Related Topics
Grants
The HTML-based pages for maintaining Grants can be accessed from the Functional Administrator responsibility. For more information on this responsibility, see:Overview of Functional Administrator and Functional Developer Responsibilities, Oracle E-Business Suite System Administrator's Guide - Configuration.
Search Grants
Use this page to search for grants.
You can search using the following criteria:
-
Name
-
Grantee Type - Select from one of the following:
-
All Users - The grant applies to all users.
-
Group of Users - The grant applies to a group of users.
-
Specific User - The grant applies to a single user.
If you select Group of Users or Specific User, you will be prompted to specify the group or the user.
-
-
Set - The Navigation Menu or Permission Set included in the grant.
-
Object Type - A grant can apply to either all objects or only a specific object. Under Object Type, specify if your search should include only grants that apply to all objects ("All Objects"), only grants that apply to a specific object ("Specific Object"), or both ("Any").
If you select Specific Object, you will be prompted to specify the object.
-
Effective Dates.
Create Grant
Use these pages to create a grant. Grants are used to manage user access to product functionality. In these pages you give access to functions to specified users.
Related Topics
Define Grant
In this page you specify basic information for the grant.
To define a grant:
-
Enter a name and description for your grant.
-
Enter effective dates for your grant.
-
Enter the security context information.
The security context defines the circumstances in which the grant is active.
For Grantee, you can select a single user, a role, or global (all users and roles).
-
For Operating Unit, specify an operating unit if you want your grant to apply to a specific one.
-
For Responsibility, specify a responsibility if you want your grant to apply to a specific one.
-
Enter the Data Security information if you are creating a data security policy for an object. The grant applies to the object you specify.
If you are not creating a data security policy, you will skip the next step.
Note: You cannot change a data security policy once it has been saved. You can delete it or provide an end date to a data security policy.
Select Object Data Context
If you specified that your grant applies to a single object, you add context for that object in this page.
Choose one of the following:
-
Global (All Rows) - Indicates that the set of functions is being granted for all rows of the object (for a function security grant).
-
Instance - Indicates that the set of functions are being granted for a single row, specified by value(s) for the primary key.
-
Instance Set - Indicates that the set of functions are being granted for a set of rows which is specified by an instance set predicate.
Define Object Parameters and Select Set
If you selected either an object instance or an instance set earlier, you can further customize the resulting set by additional information for the data context.
Additionally, you can select either a permission set or a navigation menu that can additionally specify how the grant will be applied in the security context.
For an instance set:
-
In the Predicate region, the predicate that defines the instance set is shown. In the Instance Set Details region, specify the values for the parameters to be used in the predicate above.
-
Select the permission set or navigation menu set that defines the grantee's access.
For an instance:
-
In the Instance Details region, specify information identifying the instance.
-
Select the permission set or navigation menu set that defines the grantee's access.
Review and Finish
Use this page to review the definition of your grant. Click Finish to save your work.
Update Grant
Use this page to update the definition of your grant.
View Grant
Use this page to view details for a grant, including:
-
Security Context
-
Object information, if applicable
-
Set information
You can update or delete a grant from this page.
Functions
Use these pages to define new functions. A function is a part of an application's functionality that is registered under a unique name for the purpose of assigning it to, or excluding it from, a responsibility.
You can search for functions from the main page.
Function Types
When you define a function, you assign it one of the following types:
-
External ADF Application - Used for linking an external Application Developer Framework (ADF) 11g application deployed on an Oracle Application Server 11g container from the Oracle E-Business Suite home page.
-
Database Provider Portlet
-
Form - an Oracle Forms form function.
-
JSP Interoperable with OA
-
SSWA JSP function
-
Mobile Application - A function used in an Oracle mobile application.
-
Process
-
REST service - Used for REST services. For more information on REST services and other Oracle Application Framework functions, see the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1087332.1, Oracle Application Framework Release Notes, Release 12.1.3.
-
SSWA servlet function
-
Web Provider portlet
-
SSWA PL/SQL function that opens a new window (kiosk mode)
-
Plug
-
Generic Plug
-
SSWA PL/SQL function
Related Topics
Search
Using Simple Search, You can search for functions using the following criteria:
-
Name
-
Code
-
Type
Advanced Search
Using Advanced Search, you can be more flexible with your criteria, as well as search on the description field.
Create Function
Use these pages to create a function.
-
Specify a name for the function.
-
Specify a code for the function. The code is the internal name for the function. Once the function has been saved, the code cannot be updated.
-
Specify a type for the function.
-
For context dependence, specify 'None' or Responsibility.
-
If you are defining a form function, select the name and application of your form. If the function applies to a specific object, select the object name and specify parameters.
Note: Maintenance Mode Support is reserved for future use only.
Update Function
Use this page to update an existing function. Note that you cannot update the code for an existing function.
To update a function:
-
Specify a name for the function.
-
If this function applies to a specific object, specify the object.
-
Specify a type for the function.
-
For context dependence, specify 'None' or Responsibility.
To update function details:
-
If this is a form function, select the name and application of your form.
-
If the function applies to a specific object, you can update the object name and specify parameters.
In updating menus,
-
You can remove the function from menus containing it using the Menus subtab.
-
You can also update menu prompts and descriptions for the function here.
Note: Maintenance Mode Support is reserved for future use only.
Duplicate Function
Use this page to duplicate an existing function.
Note that you must enter a unique code for the new function you are creating.
To duplicate a function:
-
Specify a name for the function.
-
Specify a code for the function. The code is the internal name for the function. Once the function has been saved, the code cannot be updated.
-
Specify a type for the function.
-
Specify the level of maintenance mode support for the function.
-
For context dependence, specify 'None' or Responsibility.
-
If you are defining a form function, select the name and application of your form. If the function applies to a specific object, select the object name and specify parameters.
View Function
Use this page to view details on an existing function.
You can update and duplicate a function from this page. If the function is not on a menu, you can also delete the function.
Delete Function
Use this page to delete a function.
Navigation Menus
Define a new menu or modify an existing menu.
A menu is a hierarchical arrangement of functions and menus of functions. Each responsibility has a menu assigned to it.
You can build a custom menu for that responsibility using predefined forms. However, we recommend that you do not disassociate a form from its developer-defined menus.
Before creating a menu, perform the following:
-
Register your application with Oracle Application Object Library using the Forms-based Applications window.
-
Define any menus that you intend to call from your menu. Define the lowest-level submenus first. A submenu must be defined before it can be called by another menu.
Tip: By calling submenus from your menu, you can group related windows together under a single heading on your menu. You can reuse your menu on other menus.
Terms
Terms used in defining menus include:
-
Name - The display name for the menu
-
Code - The internal name for the menu
Type - The purpose of the menu
-
Permission Set - For menus that are used to aggregate functions for data security or specific function security purposes, but would not be used in the Navigator form.
-
Standard - For menus used in the Navigator form
-
App Pref Menu Container - For preferences
-
Global Menu - For providing access to tasks and content that are applicable to the entire application
-
HTML Side Navigator Menu
-
HTML SideBar
-
HTML SideList
-
HTML Sub Tab - A tab-like control for switching content or action views in the page's content area. Sub tabs can be used with a horizontal navigation element, with a tab and horizontal navigation elements, or with a side navigation
-
HTML Tab
-
Homepage
-
If you are creating a menu to be used with Oracle Application Framework, see the Oracle Application Framework Developer's Guide, available from My Oracle Support Knowledge Document 1087332.1, Oracle Application Framework Release Notes, Release 12.1.3.
Search for Menus
Enter any of the following criteria for the menu:
-
Name
-
Code
-
Type
Create Navigation Menu
Use this page to create a navigation menu.
-
Choose a user-friendly name that describes the purpose of the menu.
-
Enter a code for the menu. Choose an internal name that indicates the purpose of the menu. Users do not see this menu code.
-
Optionally specify a menu type and description to describe the purpose of your menu.
Add your information for your menu entries using the Menu Builder.
-
Enter a prompt for your menu entry.
Enter a user-friendly, intuitive prompt your menu displays for this menu entry. You see this menu prompt in the hierarchy list of the Forms Navigator window.
Tip: Enter menu prompts that have unique first letters so that power users can type the first letter of the menu prompt to choose a menu entry.
-
If this menu entry is a menu itself (a submenu), enter in the menu name.
You can call another menu and allow your user to select menu entries from that menu.
-
If this menu entry is a function, enter in the function name.
Call a function you wish to include in the menu.
-
Specify the function type.
-
Apply your changes.
If you want to reorder the menu entries, click the Reorder button.
Menu Manager
Once you have your menu defined, you can update its list of entries in the Menu Manager tab.
Hierarchy of Children
The Hierarchy of Children subtab provides information on the child nodes within the menu structure. Child nodes are either functions or menus (submenus). Child nodes are displayed in a hierarchy with the following information, as applicable: display name, internal menu name, function name, type, and description.
Direct Parents
The Direct Parents subtab allows the user to see the direct parent(s), if any, of the navigation menu. A direct parent is a menu that contains this menu directly as a submenu. This feature is useful in identifying the direct impact of any changes that may be made to this menu.
For each parent, the prompt and internal menu name is shown.
Grants
The Grants subtab displays the associated grants that secure the navigation menu.
For each associated grant the following is shown: name, grantee type, grantee, valid dates, data context type, object, and instance set.
Update Menu
Use this page to update an existing navigation menu.
All fields can be updated except for the menu code.
The direct parents of a menu can be deleted in the Direct Parents tab.
You cannot update a parent menu from this tab. You must navigate to the parent menu record itself to update it.
Note: You cannot replace an existing parent menu with another menu, as the parent menu is used as the primary key of the hierarchy mapping. Instead, you have to delete this existing (child) menu and add a new menu. Also, the sequence number cannot be updated since it is the primary key. You can update the prompt and description.
Duplicate Menu
Use this page to duplicate a menu and copy its hierarchy of children. You must give the duplicate menu and new code (internal name).
View Menu
Use this page to view details of a menu.
Delete Menu
Use this page to delete a menu.
Note that you cannot delete a referenced menu. A menu can be referenced by any of the following:
-
Children (menu or function)
-
Menu parents
-
Grants
Permissions
A permission is the smallest unit of securable action that can be performed on the system. A permission can either be abstract permissions or executable functions (menu). It can either be a system level permission or be sensitive to a data context. For example, a particular JSP page may be an executable permission and "View Person" may be an abstract permission.
The Permissions pages can be accessed from the Functional Administrator and Functional Developer responsibilities. For more information on these, see:Overview of Functional Administrator and Functional Developer Responsibilities, Oracle E-Business Suite System Administrator's Guide - Configuration.
You can search for permissions from the main page. You can update, duplicate, or remove a permission found in your search results. You can also create a new permission from this page.
Search for permissions using the following criteria:
-
Name
-
Code
-
Object Name
Create Permission
Use these pages to create a permission.
-
Specify a name for the permission.
-
Specify a code for the permission. The code is the internal name for the permission. Once the permission has been saved, the code cannot be updated.
-
If this permission applies to a specific object, specify the object.
-
If you want to add this permission to a permission set now, select a permission set.
Update Permission
Use this page to update an existing permission.
Note that you cannot update the code (internal name) for the permission.
-
You can specify a new name for the permission.
-
You can specify a new object if the permission applies to a specific object.
You can update the permission set information as well:
-
To add this permission to a permission set, select a permission set from the list of values for "Add this to a Permission Set".
-
To delete this permission from a permission set, select the permission set in the table and click the Remove button.
Select the Apply button to save your changes.
Duplicate Permission
Use this page to duplicate an existing permission.
Note that you must enter a unique code for the new permission you are creating.
-
Specify a name for the permission.
-
Specify a code for the permission. The code is the internal name for the permission. Once the permission has been saved, the code cannot be updated.
-
If this permission applies to a specific object, specify the object.
-
If you want to add this permission to a permission set now, select a permission set.
View Permission
Use this page to view details on an existing permission.
You can update or duplicate a permission from this page. You can delete a permission from this page if it does not belong to a permission set.
Delete Permission
Use this page to delete a permission.
Permission Sets
Permission sets provide a way to group related permissions together. You can create a new permission set from this page.
The Permission Sets HTML-based pages can be accessed from the Functional Administrator and Functional Developer responsibilities. For more information on these, see:Overview of Functional Administrator and Functional Developer Responsibilities, Oracle E-Business Suite System Administrator's Guide - Configuration.
You can search for permission sets using the following criteria:
-
Name
-
Code
You can update, duplicate, or delete permission sets found in your search.
Create Permission Set
Use this page to create a permission set.
-
Specify a name for the permission set.
-
Specify a code for the permission set. The code is the internal name for the permission set. Once the permission set has been saved, the code cannot be updated.
Use the Permission Set Builder to add permissions to your new permission set. You can also add existing permission sets to the new permission set.
Update Permission Set
Use this page to update an existing permission set.
You can specify a new name for the permission set. Note that you cannot update the code (internal name) for the permission set.
If you want to update which permissions and permission sets belong to this permission set, use the Permission Set Builder to do so.
Permission Set Manager
Once you have your permission set defined, you can update the contents of the permission set in the Permission Set Manager tab.
Hierarchy of Children
The Hierarchy of Children subtab provides information on the child nodes in the permission set structure. A child node is either a permission or permission set. Child nodes are displayed in a hierarchy with the following information: display name, permission set name (if applicable), permission name (if applicable), and description.
Direct Parents
The Direct Parents subtab allows you to see the permission sets, if any, that include the current permission set. This feature is useful in identifying the direct impact of any changes that may be made to this permission set.
Grants
The Grants subtab displays the associated grants that secure the navigation menu.
For each associated grant, the name, grantee type, grantee, valid dates, data context type, object name, and instance set name is displayed.
Duplicate Permission Set
Use this page to duplicate an existing permission set.
Note that you must enter a unique code for the new permission set you are creating.
-
Specify a name for the permission set.
-
Specify a code for the permission set. The code is the internal name for the permission set. Once the permission set has been saved, the code cannot be updated.
If you want to update which permissions and permission sets belong to this permission set, use the Permission Set Builder to do so.
View Permission Set
Use this page to view details on an existing permission set.
Click Update to update the permission set.
Delete Permission Set
Use this page to delete a permission set. If a permission set is a child of another permission set, it cannot be deleted without first being removed from its parent permission set.
Compile Security Concurrent Program
Use this concurrent program to compile your menu data. Compiling your menu data allows for the system to determine more quickly whether a function is available to a particular responsibility/menu.
A request to run this program is automatically submitted when you make changes using the Menus form.
Parameter
Everything
This parameter takes the value Yes or No. "No" is used to recompile only those entities that are marked as needing recompilation. "Yes" is used to recompile all entities, and can take a long time. "No" is the default value.
Function Security Reports
Use the function security reports to document the structure of your menus. You can use these reports as hardcopy to document your customized menu structures before upgrading your Oracle E-Business Suite software.
The function security reports consist of the Function Security Functions Report, the Function Security Menu Report, and the Function Security Navigator Report.
These reports are available through the Function Security Menu Reports request set. For each report, specify the responsibility whose function security you want to review.
Note: If a function and a menu are associated with the same menu entry and the function is excluded then the submenu and its children are also excluded.
If the submenu is also included on another branch of the menu (same level or higher) than the submenu and functions will be included and should be on the reports assuming all other function security conditions are met.
Function Security Function Report
Specify a responsibility when submitting the report. The report output lists the functions accessible by the specified responsibility.
The report does not include items excluded by function security rules.
Function Security Menu Report
Specify a responsibility when submitting the report. The report output lists the complete menu of the responsibility, including all submenus and functions.
The report indicates any excluded menu items with the rule that excluded it.
Function Security Navigator Report
Specify a responsibility when submitting the report. The report output lists the menu as it appears in the navigator for the responsibility specified.
This report does not include items excluded by function security rules, or non-form functions that do not appear in the navigator.
Users of a Responsibility Report
This report documents who is using a given responsibility. Use this report when defining or editing application users.
Report Parameters
Application Name
Choose the name of the application to which the responsibility you want in your report belongs.
Responsibility Name
Choose the name of the responsibility you want in your report.
Report Heading
The report heading indicates the application name and responsibility for which you requested a report.
Column Headings
User Name
The name of the user who is assigned to the responsibility.
Start Date
The date the responsibility became active for the user.
End Date
The date the responsibility either becomes inactive or became inactive for the user. If no end date appears for a user, then this responsibility is always enabled for the user.
Description
The description of the user who is assigned to the responsibility.
Related Topics
Overview of Oracle E-Business Suite Security
Active Responsibilities Report
This report shows all the responsibilities that are currently active, the users who can currently access each responsibility, and the start and end dates when they can access the responsibility.
Report Parameters
None.
Report Heading
This displays the name of the report, the date and time the report was run, and the page number.
Column Headings
Application Name
The name of the application associated with the responsibility.
Responsibility Name
The name of the currently active responsibility.
User Name
The name of the user who can currently access the responsibility.
Start Date
The date when the user can begin accessing the responsibility.
End Date
The date when the user can no longer access the responsibility. See: Overview of Oracle E-Business Suite Security.
Related Topics
Overview of Oracle E-Business Suite Security
Active Users Report
This report shows all the usernames that are both currently active and have at least one active responsibility. It also displays all the responsibilities that users can access, and the start and end dates when they can access each responsibility.
Report Parameters
None.
Report Heading
The report heading displays the name of the report, the date that the report was run, and the page number.
Column Headings
User Name
The Oracle E-Business Suite name of the currently active user. The start and end dates that you specify in the Users window determine whether a username is currently active.
Application Name
The name of the application associated with the responsibility.
Responsibility Name
The name of the currently active responsibility.
Start Date
The date when the user can begin accessing the responsibility. You can specify a start date when you assign the responsibility to the user in the Responsibilities block of the Users window.
End Date
The date when the user can no longer access the responsibility. You specify an end date when you assign the responsibility to the user in Responsibilities block of the Users window.
Reports and Sets by Responsibility Report
This report identifies which reports (and other concurrent programs) and report sets are included in the request security groups available to any given responsibility. Use this report when defining or editing responsibilities.
Report Parameters
If you enter no parameters, the report documents all reports and report sets accessible from each responsibility.
Application Short Name
Choose the application name associated with the responsibility whose available reports and report sets you wish to report on.
If you do not choose an application name, the report documents all reports and report sets accessible from each responsibility.
Responsibility Name
Choose the name of a responsibility whose available reports and report sets you wish to report on. You must enter a value for Application Short Name before entering a value for Responsibility Name.
Report Headings
The report headings list the report parameters you specify, and provide you with general information about the contents of the report.
Related Topics