Administering Oracle E-Business Suite Secure Enterprise Search
Overview of Oracle E-Business Suite Secure Enterprise Search
Oracle E-Business Suite Secure Enterprise Search is a centralized, secure search vehicle with consistent user interfaces throughout the Oracle E-Business Suite. By leveraging Oracle Secure Enterprise Search (SES), Oracle E-Business Suite Secure Enterprise Search enables a powerful keyword search on applications content in a faster, user-friendly way without compromising on the security and context sensitive information.
Before users can search on applications content, searchable objects must be set up first, constructed with secure context, and indexed into a full text search engine by Oracle SES in order to be ready for query. To accomplish this goal, Oracle E-Business Suite Secure Enterprise Search uses a flexible mechanism to help analyze these searchable objects, group related objects into categories, and build security rules around them for easier, secure search and fast result display.
In fact, searchable objects are business objects that are made available for text search. For example, a purchase order is a searchable object that can be defined as a set of searchable properties or business attributes along with its relationship to other searchable objects. This abstraction allows searchable objects to be bound to different context at run time and grouped into searchable categories.
Searchable objects are created with searchable attributes. These attributes allow the objects to be indexed, applied with security rules, and displayed with structured search results. Before users query, a search administrator grants appropriate data access privileges to users to secure application sensitive data from unauthorized access before deploying these objects to an Oracle SES instance.
At crawl time, the Oracle SES search engine starts a crawling job for a specific business object type. Based on a object type, searchable business objects or attributes get retrieved, indexed, and stored in the Oracle SES index store.
At query time, when a user performs a search through the centralized user interface, he or she is actually searching against a preindexed store which contains numerous objects or metadata that has been preprocessed with indexes at crawl time. The search engine queries the results enforced by security rules and constructs the hits returning as search results displayed to the user.
Key features of Oracle E-Business Suite Secure Enterprise Search include:
-
A centralized global search capability provides user rich experience of searching text across the entire Oracle E-Business Suite.
-
It allows you to search structured and unstructured data like attachment through business categories and further narrow down your search results by business entities or attributes.
-
Security context defined at multiple levels controls the accessibility of application sensitive data to only authorized users.
-
It leverages extensive search capabilities provided by Oracle SES to search application content in a secure and user-friendly way.
-
It provides pluggable search region capability which allows a specific searchable object to be embedded in a page for context sensitive search.
-
A search administrator can proactively control and manage crawling schedules and statuses using the administrative pages.
-
It provides multiple language support allowing application users to perform internationalized searches.
To have a better understanding of Oracle E-Business Suite Secure Enterprise Search, the following topics are discussed in this section:
Oracle E-Business Suite Secure Enterprise Search Related Terms and Definitions
To better understand and administer Oracle E-Business Suite Secure Enterprise Search, this section provides relevant terminologies and their definitions used in Oracle E-Business Suite Secure Enterprise Search.
Searchable Objects
Searchable objects are business objects that are made available for text search; they are used in an abstract way for exposing business data to search engines. For example, a purchase order as a searchable object would be defined as a set of searchable properties and its relationship to other searchable objects.
Search Category
Related searchable objects can be grouped into a search category and it is also called a searchable group.
Oracle E-Business Suite Secure Enterprise Search leverages Role-Based Access Control (RBAC) model to associate searchable groups with permission sets and grant the group access privileges to authorized users.
Search Context
The binding information could be specific to a search engine. In order to make the search service open, Oracle E-Business Suite Secure Enterprise Search needs to abstract out the search engine internals and makes search engine a service that can be replaced by one another at the deploy time.
Search context is an application within which search services will be provided for searchable objects.
Search Engine
Search engine is an application or service that encapsulates the need of text search on a resource. It uses a number for well-defined sub modules to perform the necessary tasks. For Oracle E-Business Suite Secure Enterprise Search, Oracle SES is the search engine that makes search service feasible.
Crawler
Crawlers are software agents used by a search engine to retrieve content for a given data source.
Indexer
An indexer is a software module that is used by a search engine to create an index from each crawled document.
Once indexes are created for a particular data source, they are available for search through a set of Web Service APIs (Searcher interface).
Searcher
A searcher is a software module that allows external users to query into pre crawled and indexed stores. It is responsible for matching keywords and predicates to documents, and then return them to the user.
Security Plug-in
To help protect unauthorized access to application information, security plug-in is used to enforce search security at the object level. Security plug-in is a Java class that implements the security methods to generate the access control list (ACL) for a document and to fetch Security Keys for a user.
An ACL is a list of permissions attached to an object specifying who or what is allowed to access the object and what operations are allowed to be performed. Oracle SES authorization plug-in works on the basis of the ACL-based security model and Security Keys for a document to authorize users or revoke the access to a search result.
User Authorization Cache (UAC)
This Oracle SES feature provides a framework allowing the Security Keys for a particular user, a specific data source, or a search object in Oracle E-Business Suite can be cached in Oracle SES.
By leveraging this framework from Oracle SES, when a user performs a search, the UAC is first looked up for the availability of the Security Keys for that user. If the keys are not found, then the Security Keys will be fetched synchronously during the query.
Query Rewrite
Query rewrite is a feature offered through a plug-in component that can rewrite the query to reflect current user context such as security before the query is sent to a search engine.
Data Security
Data security is a generic authorization model used by many applications within the Oracle E-Business Suite. It controls what users can see on application data through security grants.
Function Security
Function security is the basic access control in Oracle E-Business Suite. It restricts user access to individual menus and menu options within the system regardless of which application data in the row.
Oracle E-Business Suite Secure Enterprise Search uses the function security feature to guard the application content access through the menus and responsibilities assigned to each application user.
Architecture Overview
Oracle E-Business Suite Secure Enterprise Search development framework establishes searchable objects from search metadata. This search metadata is then used during crawl time to conduct searches and store data, and used during query time to qualify results.
The following architecture diagram illustrates how metadata is used in defining searchable objects, and the interaction between Oracle E-Business Suite Secure Enterprise Search and Oracle SES:
Architecture Diagram
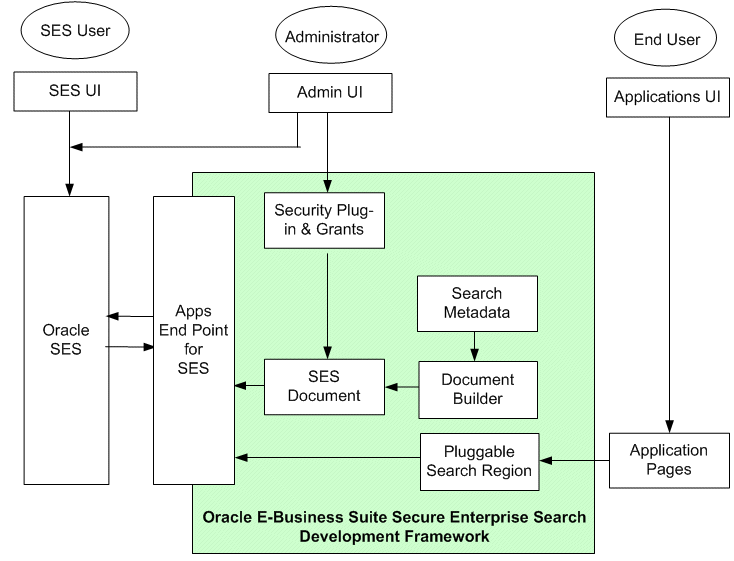
Business objects with searchable attributes become searchable metadata. Oracle E-Business Suite Secure Enterprise Search utilizes SES Document Builder to construct this searchable metadata or object which may contain complex business structure into a flattened searchable document. This document is also known as SES Document.
A search administrator creates security grants through roles or responsibilities, and necessary security plug-ins to secure searchable objects.
The search administrator or system administrator configures the necessary Oracle SES proxy parameters and setup tasks both in Oracle E-Business Suite Secure Enterprise Search and Oracle SES. This enables Oracle SES to crawl Oracle E-Business Suite (EBS), and Oracle E-Business Suite to query Oracle SES.
When an application user performs a search through application interfaces, a query is executed by invoking a search against a preindexed search store in SES.
Design Time
During the design phase, searchable objects with searchable attributes are created in Search Modeler and loaded to Oracle E-Business Suite as search metadata. These attributes allow searchable objects to be indexed, applied with security rules, and displayed with structured search results.
The search administrator grants appropriate data access privileges to users through roles or responsibilities to secure application sensitive data from unauthorized access before or after deploying objects to Oracle SES; the Oracle SES administrator then manages crawling schedules so that deployed data sources can be crawled for a specific object type and indexed.
Note: Once searchable objects are deployed, crawling schedules are automatically created along with data sources in Oracle SES. For more information on how to manage crawling schedules, see Administering Crawls in Oracle SES.
The following diagram illustrates the interaction flow during the design time:
Design Time Process Diagram
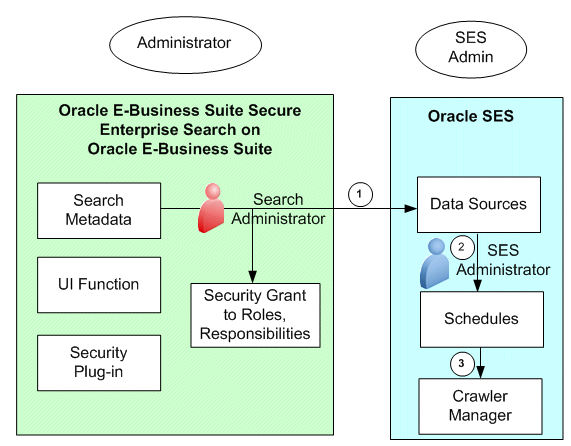
-
The search administrator creates security grants to users through roles or responsibilities before or after deploying searchable objects to Oracle SES as data sources.
-
The Oracle SES administrator manages crawling schedules that contain data sources.
-
The crawler manager picks the data source for crawl based on the schedules.
For more information about how to create searchable objects in Search Modeler, see Creating Searchable Objects, Oracle E-Business Suite Search Modeler User's Guide available from My Oracle Support Knowledge Document 781366.1, Search Modeler 1.1 for Oracle E-Business Suite Readme.
Crawl Time
To produce satisfying search results in a timely fashion, crawling and indexing are essential tasks to a successful search. At crawl time, crawling is done by several distributed crawlers. Oracle SES crawler is a Java process activated by a set schedule. When activated, the crawler spawns a configurable number of processor threads that fetch information from various sources and index the documents. This index is used for searching sources.
Some crawlers are designed to crawl Oracle E-Business Suite users and provide user documents to Oracle SES. Oracle SES in turn invokes its authorization plug-in to generate document security access keys for each user crawled pertaining to the Oracle E-Business Suite source type and caches these keys for the authorized users and specific searchable objects or data sources. When a user performs a search, these previously cached security access keys will be used which provides a quick search result with security enforced.
Crawl Time for Indexable Documents
After searchable objects are deployed to Oracle SES as data sources contained in crawling schedules, Oracle SES starts crawling jobs in the Oracle E-Business Suite. A "crawlable" Oracle E-Business Suite means a secure end point that has been made crawlable to Oracle SES. This allows application data to be crawled and indexed into an Oracle SES store. The following diagram illustrates the interaction flow of Oracle SES crawler tasks:
Crawl Time Interaction Diagram for Indexable Documents
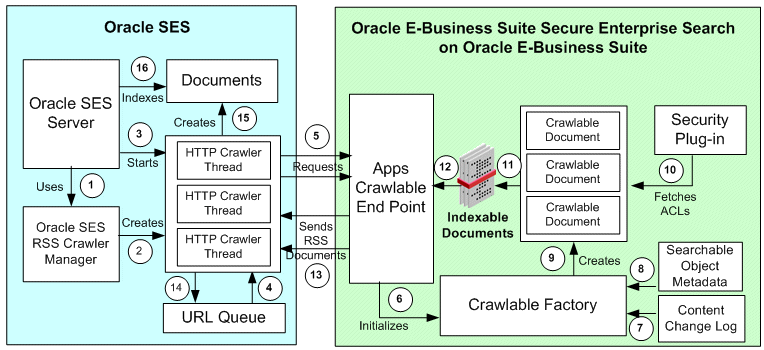
-
Oracle SES initializes RSS Crawler Manager.
-
Oracle SES Crawler Manager spawns and initializes a preconfigured number of crawler threads.
-
Oracle SES Starts the crawlers.
Note: The crawler maps links and analyzes relationships. Whenever the crawler encounters embedded non-HTML, or non-textual documents during the crawling, it automatically detects the document type and filters and indexes the document.
-
Crawler threads pick up crawlable URLs from the URL Queue. URL Queue is populated using controlFeed mechanism as described in step 5.
-
Crawler threads contact Oracle E-Business Suite Crawling End Point, which is a servlet registered in oafm container.
The requests come as post requests with URL parameters as in http(s)://<ebs apache host>:<web host>/webservices/AppSearch/[ConfigFeed | ControlFeed | DataFeed]/Search Object Name>?user<ebs user having FND_SEARCH_CRAWLER resp>&password=<password>.
Note: ConfigFeed and ControlFeed are crawling mechanisms to generate crawlable URLs in multiple batches of preconfigured sizes, so that crawling can proceed in parallel. These are used to generate the initial “URL Queue” in Oracle SES.
DataFeed is the actual crawling request, which has been illustrated in the diagram.
-
Once the Oracle E-Business Suite Crawlable End Point receives the crawling requests, it initializes the Crawlable Factory whose purpose is to fetch the content from Oracle E-Business Suite database.
Please note that Crawlable Factory is also responsible for splitting the original application content large data set into smaller work units through AD Parallel Update package, and then crawling the units in parallel by using the multi-thread crawling mechanism provided by Oracle SES.
Note: The Crawlable Factory is the place where an initial crawl taken place. The initial crawl refers to the first time a searchable object is crawled.
-
Content change log provides application changes that are indexed to the Crawlable Factory.
-
Search metadata is loaded to the Crawlable Factory.
-
Crawlable Factory creates crawlable documents, which conform to some schema provided by the indexing vendor.
-
While creating indexable documents, the Access Control List (ACL) is fetched for each document using the search plug-in associated with the searchable object definition. The getAcl() and getSecureAttrAcl() methods of the search plug-in are invoked to generate the ACLs.
For more information about security plug-in, see Search Security Plug-ins.
-
Documents are ready to be consumed by a search/indexing engine.
-
Oracle E-Business Suite crawler threads pick the documents.
-
The indexable documents which are in the form of a RSS feed are passed to Oracle SES through the Oracle E-Business Suite End Point URL in response to the crawling request mentioned in step 5.
These documents conform to Oracle SES crawlable schema and should have following information:
-
Metadata
-
Content to be indexed
-
Dependent document URLs (such as actionable links, attachments, or related documents or links)
-
-
On retrieving the document, Oracle SES indexing engine analyzes the RSS feed received from Oracle E-Business Suite and places the neighboring URLs into the URL Queue.
Typically the neighboring URLs in Oracle E-Business Suite are the attachment fetch URLs.
-
Oracle SES indexing engine transforms the documents in Oracle SES readable format by extracting keywords.
-
Finally indexing process indexes the documents.
Indexed documents are stored in the precrawled index store in Oracle SES.
Crawl Time for User Authorization Cache Source
To reduce the search response time of synchronously fetching Security Keys for an authorized user during user query, cached Security Keys for a particular user and a searchable object or data source are precrawled and stored in Oracle SES and then used directly at query time. This solution by using cached access keys to authorize a document access privilege for a user at query time is leveraged from Oracle SES User Authorization Cache (UAC) feature. For more information about this feature, see User Authorization Cache.
Note: To protect sensitive application data from unauthorized access, Access Control List (ACL) and Security Keys are generated through a security plug-in that is attached to a searchable object to enforce security at the object level.
An ACL is a list of permissions attached to an object specifying who or what is allowed to access the object and what operations are allowed to be performed. Security Keys are generated for a user to match the prebuilt ACLs to access specific documents based on user privileges.
For more information about security plug-in, see Search Security Plug-ins.
The following diagram illustrates the interaction flow of Oracle SES crawler tasks for Oracle E-Business Suite "User Authorization Cache" (UAC) source:
Crawl Time Interaction Diagram for User Authorization Cache Source
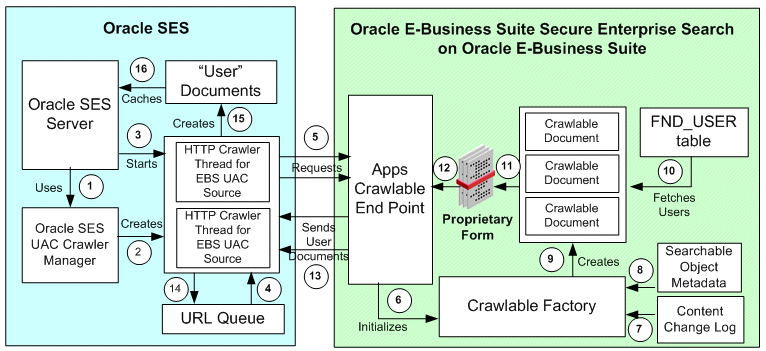
This interaction diagram for UAC source is similar to the crawling tasks for indexable documents. The major differences between these two are highlighted as follows:
-
UAC Crawler Manager is initialized to preconfigure the crawler threads specifically for Oracle E-Business Suite UAC source type (step 2).
-
While creating documents for User Crawl, crawlable instances use FND_USER, which is the source of Oracle E-Business Suite users. This holds true for Single Sign-On integrated Oracle E-Business Suite instances as well (step 10).
-
Oracle E-Business Suite End Point URL responds to the crawling request mentioned in step 5 by sending the user documents, which are XML-based documents conforming to a mutually agreed upon schema.
Oracle E-Business Suit calculates the total number of users satisfying user list criteria mentioned in Oracle SES. If the number is less than the profile value defined in the FND: Search Crawl Batch Size profile option, it directly gives user list to Oracle SES. Otherwise, it gives a 'User Control Feed' which in turn is used again by Oracle SES to create final user list feeds. (step 13).
-
On retrieving the document, Oracle SES indexing engine analyzes the XML feed received from Oracle E-Business Suite and places the neighboring URLs into the URL Queue (step 14).
-
Finally Oracle SES engine caches the Oracle E-Business Suite users. The precrawled UAC sources are stored in Oracle SES (step 16).
This crawling process generates a list of Oracle E-Business Suite users for whom the Security Keys need to be cached in Oracle SES for the predefined "User Authorization Cache" source type.
Fetching Security Keys Offline
In order to provide quick search results back to a user and eliminate possible time-outs of fetching Security Keys simultaneously during query due to complex application logic of deriving the keys, by leveraging the User Authorization Cache framework from Oracle SES, the user Security Keys can be generated as an offline process.
The following diagram illustrates the interaction flow for fetching Security Keys offline:
Interaction Diagram for Fetching Security Keys Offline
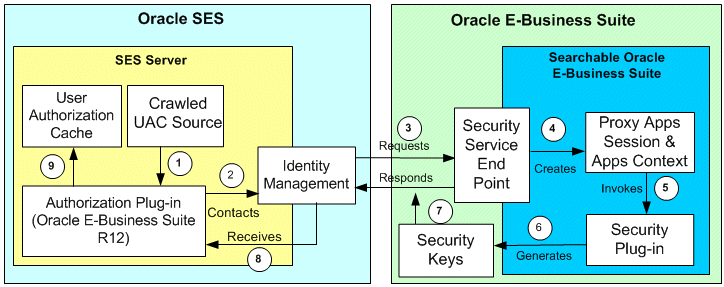
-
The crawled UAC source retrieves users and associated data sources from Oracle E-Business Suite.
Based on each user and data source, the authorization plug-in is invoked
-
Authorization plug-in contacts Identity Management to initiate the Security Key fetch process.
-
Identity Management plug-in sends a request to the Oracle E-Business Suite Security Service End Point to fetch the Security Keys for an Oracle E-Business Suite user and a data source (i.e. search object in Oracle E-Business Suite).
The request is in the form: http://<ebs server>:<port>/AppSearch/SecurityService?user=<proxy user>&password=<proxy password>.
An XML message containing the user for whom the Security Keys are requested and the search object name is posted.
-
Security establishes the proxy session and applications context. The credential is verified for the proxy user name and password, which Oracle SES posts with the request.
The session is trusted or updated on behalf of the actual search user for whom the Security Keys have been requested.
-
The search plug-in is invoked by the Security Service End Point to generate the Security Keys. It is executed in the same proxy session.
-
The getSecurityKeys( ) and getSecureAttrKeys( ) methods are executed to generate the Security Keys for the proxy context.
Since the context is always incomplete, security plug-ins have to be aware of such scenarios.
-
Security Service End Point responds to the request mentioned in step 3 by sending the Security Keys for the requested user.
-
The authorization plug-in receives the Security Keys.
-
Security Keys are cached for a given user and a specific search object or data source.
Query Time
When an application user performs a search from the centralized search user interfaces, the user actually queries from a preindexed store in Oracle SES.
It is important to note that searchable group security rule and search plug-in security are enforced for a user query. For the searchable group security, not every searchable group can be seen or displayed to a user. Only those who have the group access privileges can find the group names displayed from the list of values for search selection. For search plug-in security, it can be used at crawl time and query time to fetch ACLs and generate Security Keys to protect unauthorized access to application data.
For information on how to secure searchable objects through searchable group security and security plug-in, see Securing Searchable Objects. For information on how to perform a search, see Oracle E-Business Suite User's Guide.
Query from Oracle E-Business Suite
You can perform a search from the Oracle E-Business Suite centralized search user interfaces.
The following diagram illustrates the query time interaction flow when performing a search through Oracle E-Business Suite:
Query Time Interaction Flow from Oracle E-Business Suite
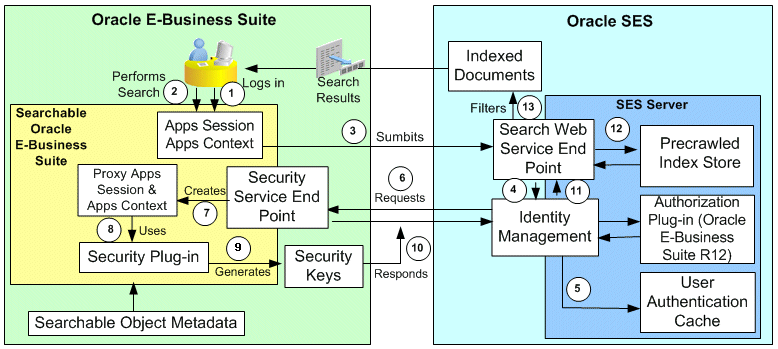
-
A user logs on to Oracle E-Business Suite. A proxy session is created along with the initialization of applications context for the user.
The applications context may be incomplete at this stage depending on whether the user has selected a responsibility or not.
-
The user accesses the Oracle E-Business Suite Secure Enterprise Search toolbar and submits a search query within the same session and context.
-
The query is submitted to the Oracle SES client APIs, which are hosted within Oracle E-Business Suite. The Oracle SES client APIs in turn make Web service calls to the Search Web Service End Point published by Oracle SES server.
The Web service call includes the search keywords, filters if any, and user information amongst the most important parameters.
-
Once the search service is invoked, Oracle SES contacts the Identity Manager.
Identity Management is set up as part of the configuration for the integration between Oracle E-Business Suite and Oracle SES. Oracle SES has specific identity manager for Oracle E-Business Suite Release 12. This Identity Manager configuration needs Oracle E-Business Suite Security Service End Point and a proxy application user name and password to establish a proxy session.
For setup configuration for Oracle SES integration, see Setting Up Oracle E-Business Suite Secure Enterprise Search for Oracle SES Integration.
-
If a User Crawler initiates at the crawl time, the Security Keys for a user, data source, or searchable object can be retrieved offline and cached in Oracle SES.
Oracle SES first looks up the Security Keys for the object and logged-in user in User Authentication Cache (UAC).
-
If a match is found and the cache is usable, proceed to Step 12.
-
If there is no match found, proceed to the next Step 6.
For more information on this feature, see User Authorization Cache.
-
-
Identity Manager requests Security Key information for the search user from the Security Service End Point. The Security Service End Point is registered as a servlet in oafm container.
-
Once the Security Service End Point receives a request for Security Keys, it initializes a proxy session. The proxy username/password credential is verified for the request. The session is then trusted or updated on behalf of the actual search user for whom the Security Keys have been requested.
Note: The proxy applications context may be incomplete since the responsibility information may or may not be there. Therefore, a special plug-in mechanism is provided to create the complete context information. For more information about the plug-in mechanism, see Understanding Security Logic and General Plug-in Mechanism.
-
The search plug-in is invoked in the same proxy session by the Security Service End Point to generate the Security Keys.
-
The getSecurityKeys() and getSecureAttrKeys() methods of the search plug-in are executed to generate the Security Keys for the proxy context.
Since the context may be incomplete, security plug-ins have to be aware of such scenarios.
-
The Security Service End Point responds to the request mentioned in Step 5 by sending the Security Keys for the search user. The request-response happens over HTTP protocol.
Oracle SES ensures that it does not wait indefinitely for the response to complete by setting a time-out on the request.
Note: The time-out value is configurable. This is done to ensure responsiveness of the overall search solution.
-
The search service receives the authorization keys from Identity Management.
-
Search service retrieves indexed documents from the index store as per the search criteria given.
-
Indexed documents are filtered by Oracle SES after applying the Security Keys/Authorization Keys. This way, only the authorized documents are retrieved for the search user. The filtered indexed documents are returned to the query user for viewing and further action.
Query from Oracle SES
If an Oracle E-Business Suite user tries to log on and performs a search through the Oracle SES search user interface instead, the user's login credentials need to be authenticated first. At this stage, user login validation does not require any search plug-in.
Once the login is authenticated, the user can perform a search in the Oracle SES search UI with similar query time architecture as query in the Oracle E-Business Suite.
The following diagram illustrates the query time interaction flow when performing a search through Oracle SES:
Query Time Interaction Flow from Oracle SES
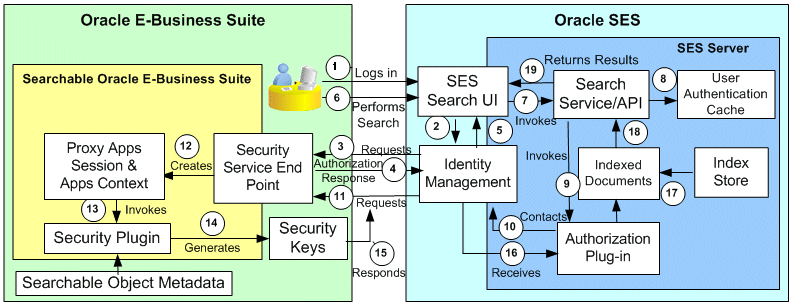
-
An Oracle E-Business Suite user attempts to sign in to Oracle SES Search UI using Oracle E-Business Suite username and password.
-
Oracle SES contacts Identity Manager to verify the user credentials.
-
Identity Manager sends an authentication request to the Security Service End Point of Oracle E-Business Suite. The request is sent over HTTP protocol.
It is typically of the form http(s)://<ebs server>:<port>/webservices/AppSearch/SecurityService. An XML message containing the exact authentication service requested is posted.
-
The Security Service End Point validates the login credentials and responds to the request by sending another XML message.
-
Identity Manager parses the response message and sends the success or failure response to the Oracle SES Search UI.
-
After successful login, the user submits a search query. It may consist of keywords, filters, and other search criteria.
-
Upon receiving the search request, Oracle SES invokes an appropriate search service or API.
-
If a User Crawler initiates at the crawl time, the Security Keys for a user, data source, or searchable object can be retrieved offline and cached in Oracle SES.
Oracle SES first looks up the Security Keys for the object and logged-in user in User Authentication Cache (UAC).
-
If a match is found and the cache is usable, proceed to Step 17.
-
If there is no match found, proceed to the next Step 9.
For more information on this feature, see User Authorization Cache.
-
-
The search service in turn invokes the authorization plug-in to get the Security Keys for the current search user.
-
Authorization plug-in contacts the Identity Manager to fetch the Security Keys.
-
Identity Manager requests Security Key information for the search user from the Security Service End Point. This is done over HTTP. The request message contains the proxy username and password, which is stored in Oracle SES as part of the configuration.
-
Security establishes the proxy session and applications context. The proxy username/password credential is verified for the request from Oracle SES. The session is then trusted or updated on behalf of the actual search user for whom the Security Keys have been requested.
Note: Please note that the proxy applications context is always incomplete since the responsibility information may not be there while logging into Oracle SES. This is the major difference between searching from Oracle E-Business Suite and searching from Oracle SES Search user interface.
-
The search plug-in is invoked in the same proxy session by the Security Service End Point to generate the Security Keys.
-
The getSecurityKeys() and getSecureAttrKeys() methods of the search plug-in are executed to generate the Security Keys for the proxy context.
Since the context is always incomplete, security plug-ins have to be aware of such scenarios.
-
The Security Service End Point responds to the request mentioned in Step 5 by sending the Security Keys for the search user. The request-response happens over HTTP protocol.
Oracle SES ensures that it does not wait indefinitely for the response to complete by setting a time-out on the request.
Note: The time-out value is configurable. This is done to ensure responsiveness of the overall search solution.
-
The authorization plug-in receives the Security Keys for the query user.
-
The Oracle SES search service or API retrieves indexed documents from index store, matching the search keywords and filters.
-
Indexed documents are filtered by the Security Keys retrieved for the query user.
-
Filtered search results are returned back to the query user.
Performing Administrative and Setup Tasks
Since all searchable objects are precrawled and indexed in the Oracle SES index store before a search invokes, a search administrator or system administrator must perform administrative setup tasks. These tasks include enabling searches in the E-Business Suite, creating a search administrator who is responsible for setting up, and configuring Oracle E-Business Suite Secure Enterprise Search for Oracle SES integration.
This section includes the following topics:
Creating a Search Administrator
To have Oracle E-Business Suite Secure Enterprise Search work properly, a search administrator must be set up first in order to configure and maintain administrative tasks before users can perform searches on applications data.
Note: It is important to know that a search administrator is not only responsible for configuring and setting up essential tasks, but also responsible for managing crawling schedules and administering crawls in Oracle SES which are typically not performed by a system administrator. It is highly recommended that you create a new user (such as sesadmin/welcome) for that role, instead of using an existing system administrator user (sysadmin/sysadmin) assigned with necessary responsibilities. For more information, see Oracle E-Business Suite Secure Enterprise Search Best Practices, Release 12, My Oracle Support Knowledge Document 744820.1.
Use the following steps to create a search administrator:
-
Create a user (such as sesadmin/welcome) who will be the search administrator.
-
Assign the following responsibilities to the user sesadmin/welcome:
-
Application Search Administrator responsibility (FND_SEARCH_ADMIN)
-
FND Search Crawler responsibility (FND_SEARCH_CRAWLER)
-
Once a search administrator is created, the same user name and password information (such as sesadmin/welcome) will be entered in the Application Search Administration page as part of the setup parameters for Oracle SES Integration, as well as entered in the Oracle SES administrative pages to validate and authenticate users for secured searches on Oracle E-Business Suite or add secure federated searches.
For detailed configuration and setup steps, see Configuring Search Proxy Parameters for Oracle SES and Performing Setup Steps in Oracle SES.
Setting Up Oracle E-Business Suite Secure Enterprise Search
Setup Overview
Oracle E-Business Suite Secure Enterprise Search is comprised of database, middle-tier, and UI components. It also relies on external dependencies to have the function work properly. Before setting up Oracle E-Business Suite Secure Enterprise Search and performing administrative tasks, a search administrator or system administrator must first understand the product dependencies and the integration between Oracle SES.
Product Dependencies
Oracle E-Business Suite Secure Enterprise Search has dependencies on the following products in order to have its features work properly:
-
Oracle Secure Enterprise Search (SES)
Oracle E-Business Suite Secure Enterprise Search relies on an external search engine to provide text search capability, and this search function is provided by Oracle SES.
-
AD Parallel
Oracle E-Business Suite Secure Enterprise Search utilizes the AD Parallel Update package to facilitate the crawlable factory in expediting the performance of an initial crawl which usually involves a large set of data.
-
OA Framework
Oracle E-Business Suite Secure Enterprise Search depends on OA Framework to enable the reusable search region displayed in the OA Home page.
Note: Since Oracle E-Business Suite Secure Enterprise Search can embed reusable search regions either in the OA Home Page or as a plug-in, the OA Home Page is dependent on Oracle E-Business Suite Secure Enterprise Search as well.
-
Function Security
Oracle E-Business Suite Secure Enterprise Search uses function security to guard the application content access through the menus and responsibilities assigned to an application user.
-
Data Security
Oracle E-Business Suite Secure Enterprise Search uses data security to control what users can see on the application data through security grants. Only authorized users can view searchable objects.
Note: The security access to searchable objects are also implemented through the Role-Based Access Control Security for Oracle E-Business Suite Secure Enterprise Search.
-
Web Service Technology Stack
Oracle E-Business Suite Secure Enterprise Search forms query and performs a search against Oracle SES through Web Service Technology Stack.
Setup Tasks
Since all searchable objects are precrawled and indexed in the Oracle SES index store before a search is invoked, a search administrator or system administrator needs to perform general setup tasks in Oracle E-Business Suite and search-related setup tasks both in Oracle E-Business Suite Secure Enterprise Search and Oracle SES administrative pages.
This section contains the following topics:
Enabling Searches in Oracle E-Business Suite
The setup steps in Oracle E-Business Suite include the following tasks:
-
Setting language preferences
-
Setting profile options
-
Assigning the FND Search Crawler responsibility to an FND user
-
Performing personalization setup steps for displaying the Enterprise Search region
Setting Language Preferences
To have the search and result displayed in your preferred language, a search administrator must set a default language in the General Preferences page if it is not English.
For information on how to set language preferences, refer to Set Preferences section, Getting Started with Oracle E-Business Suite chapter, Oracle E-Business Suite User's Guide for details.
Setting Profile Options
Oracle E-Business Suite Secure Enterprise Search uses profile options to define necessary setup parameters so that searches can be enabled in the Oracle E-Business Suite. These profiles determine the following features:
-
The availability of the Oracle E-Business Suite Secure Enterprise Search feature
-
The valid URL for an external Oracle SES instance access
-
The version of Oracle SES to be used for integrating with Oracle E-Business Suite Secure Enterprise Search
-
The timeout value in seconds for an FND user logging into Oracle SES for query
Note: A valid FND user indicates that the user's application login information such as user name and password must be stored in the FND_USER table.
-
The timeout value in seconds for an administrator logging into Oracle SES for administrative tasks
-
The site-wide batch size used by AD Parallel for crawling
The following table lists the profile options used in Oracle E-Business Suite Secure Enterprise Search:
| Profile Option | Description | Required | Default Value |
|---|---|---|---|
| FND: Search Enabling Flag | Use this site level profile option to control whether Oracle SES integration is enabled for the site. Oracle E-Business Suite Secure Enterprise Search must have it set to Yes indicating this feature is enabled. | Yes | N |
| FND: Search Engine URL | Use this site level profile option to specify a valid URL with the format http://<hostname>:<portnumber> for an external Oracle SES instance to which query will be made against. This profile value must be provided if the site is Oracle SES enabled. | Yes | N/A |
| FND: Search SES Version | Use this site level profile option to specify a valid version of Oracle SES for integrating with Oracle E-Business Suite Secure Enterprise Search. The profile value should have minimum two characters, and the first two characters should be digits (such as 10.1.8.4, 11.1.2, 11G). |
Yes | No default value for this option. However, if this profile is not set, Oracle SES version 10.1.8.4 will be considered. |
| FND: Search Session Timeout Value for Query | Use this site level profile option to control the timeout value in seconds for an FND user logging into Oracle SES. The session expires if this amount of time passes since the last activity by the user. | Yes | 1200 |
| FND: Search Session Timeout Value for Admin Tasks | Use this site level profile option to control the timeout value in seconds for an administrator logging into Oracle SES. The session expires if this amount of time passes since the last activity by the administrator. | Yes | 1200 |
| FND: Search Crawl Batch Size | This profile allows application administrators to set the site-wide batch size used by AD Parallel. | Yes | 1000 |
Assigning the FND Search Crawler Responsibility to an FND User
The FND Search Crawler responsibility must be assigned to an FND user and its user name and password must also be provided in the search administrative page before synchronizing applications metadata with Oracle SES. If the user information changes, you must update it and synchronize the data again.
Performing Personalization Setup Steps for Displaying the Enterprise Search Region
To ensure that the Enterprise Search region appears on top of the Oracle E-Business Suite Home page, you need to perform the following personalization steps:
-
Log in to Oracle E-Business Suite with the system administrator's user name and password.
-
Select the Functional Administrator responsibility from the Navigator menu.
-
Select the Personalization tab and the Application Catalog subtab to open the Application Catalog page.
-
In the Search region, enter /oracle/apps/fnd/search/webui in the Document Path field as the search criteria and click Go.
All document names that match the search criteria should be displayed in the search result table.
-
Click the Personalize Page icon for the /oracle/apps/fnd/search/webui/AppsSearchRG document name listed in the result table to open the Choose Personalization Context page.
-
Enter 'Applications Home Page' (OAHOMEPAGE) in the Set Function field and click Apply to open the Personalization Region page for your document.
-
In the Personalization Structure region, select the Personalize icon for the Row Layout field to open the Personalize Row Layout page.
-
Set the rendered property to 'true' at the 'Function: Applications Home Page' level.
-
Navigate back to the Home page after applying the personalization change.
-
Review if the Enterprise Search region is getting rendered on the Oracle E-Business Suite Home page.
-
Perform a search by entering search criteria and click Go to verify if the search result is displayed in the search result page.
Setting Up Oracle E-Business Suite Secure Enterprise Search for Oracle SES Integration
To have seamless integration with Oracle SES, after enabling searches in Oracle E-Business Suite, the system administrator or search administrator must perform configuration tasks in Oracle E-Business Suite Secure Enterprise Search and Oracle SES.
The following diagram illustrates the high-level integration flow for Oracle E-Business Suite and Oracle SES integration:
Oracle SES and Oracle E-Business Suite Integration Workflow
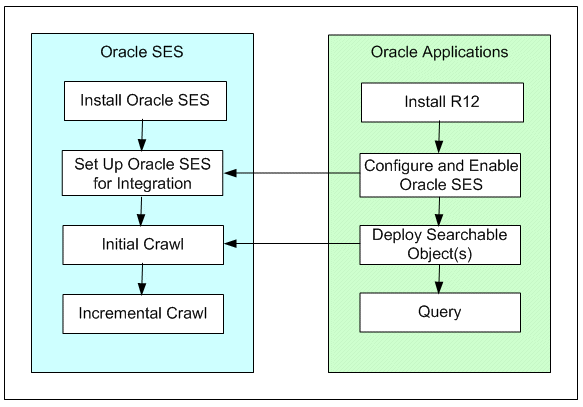
After the installation of Oracle SES and Oracle E-Business Suite, search related metadata and business objects must be created and made it available in Oracle SES; metadata and relevant security rules are implemented and employed by Oracle E-Business Suite. To make the search available in Oracle E-Business Suite, necessary setup tasks must be performed in Oracle E-Business Suite, Oracle E-Business Suite Secure Enterprise Search, and Oracle SES.
For example, these tasks include setting language preferences and profile options for the applications to enable Oracle E-Business Suite Secure Enterprise Search, configuring search proxy parameters to facilitate remote access to Oracle SES, and performing administrative setup steps in Oracle SES for integration.
With appropriate setup and configuration between Oracle SES and Oracle E-Business Suite Secure Enterprise Search, searchable objects can be successfully deployed to Oracle SES instance, and initial and incremental crawls can be launched in Oracle SES. Users can perform queries from Oracle E-Business Suite against a precrawled index store in Oracle SES.
Important: For troubleshooting frequently encountered issues during installation and setups, see Oracle E-Business Suite Secure Enterprise Search Troubleshooting Guidelines, Release 12, My Oracle Support Knowledge Document 726239.1 for details.
This section covers the following setup tasks in Oracle E-Business Suite Secure Enterprise Search and Oracle SES:
-
Installing Oracle E-Business Suite Secure Enterprise Search
This section provides installation information so that Oracle E-Business Suite Secure Enterprise Search can integrate with Oracle SES.
-
Configuring Search Proxy Parameters for Oracle SES
This step includes setting administrative proxy and query proxy parameters, such as user name, password, and timeout value in seconds for an administrator and a valid FND user to access a remote Oracle SES instance.
-
Performing Setup Steps in Oracle SES
To ensure the seamless integration between Oracle E-Business Suite Secure Enterprise Search and Oracle SES, the system administrator or search administrator must perform additional setup steps in Oracle SES. These steps include setting up connections between Oracle SES and an identify management system, and adding federation entities to Oracle SES.
Installing Oracle E-Business Suite Secure Enterprise Search
Oracle E-Business Suite Secure Enterprise Search is released with Oracle E-Business Suite and Oracle Secure Enterprise Search (SES). To have it installed properly, perform the following installation steps:
-
Install or upgrade your instance to Oracle E-Business Suite Release 12.1.3.
-
Install Oracle SES 11.1.2 from Oracle Technology Network (OTN) page (http://www.oracle.com/technology/), or upgrade to Oracle SES 11.1.2 from Oracle SES 10.1.8.4.
Refer to Oracle Secure Enterprise Search Installation and Upgrade Guide 11g Release 1 (11.1.2.0.0) for installation details and upgrade information from Oracle SES 10.1.8.4 to Oracle SES 11.1.2.
Oracle SES can be integrated with Oracle E-Business Suite Release 12.1.3. The minimum supported version of Oracle SES in this 12.1.3 release is SES 11.1.2. To have a successful integration with SES 11.1.2, a few mandatory Oracle SES one-off patches need to be applied. Refer to Installing Oracle E-Business Suite Secure Enterprise Search, Release 12, My Oracle Support Knowledge Document 462377.1 for details.
Note: Oracle SES 11.1.2 uses two separate JVMs for running the crawler and search applications. The crawler is run using Sun JRE whereas the search application is run using JRockit JRE. Both JREs are available under $ORACLE_HOME of Oracle SES installation. If Oracle E-Business Suite is on SSL enabled environment, when integrating with Oracle SES 11.1.2 instance, the Oracle E-Business Suite SSL certificate has to be imported into both the Oracle SES keystores (JRE truststores) using keytool.
Remember the port and 'eqsys' password during the installation. This information will be used later in configuring Oracle E-Business Suite Secure Enterprise Search to enable Oracle SES integration.
Note: Since Oracle SES defaults to TNS database port 1521 during the installation and it does not appear to be changeable, when trying to install Oracle SES, you must have port 1521 free in order to have Oracle SES successfully installed in your system.
Once you complete the installation for both Oracle E-Business Suite and Oracle SES, you must also perform administrative setup tasks both in Oracle SES and Oracle E-Business Suite Secure Enterprise Search to configure the system.
See:
For more installation information, see Installing Oracle E-Business Suite Secure Enterprise Search, Release 12, My Oracle Support Knowledge Document 462377.1 for details.
To ensure that the Enterprise Search region appears on top of the Oracle E-Business Suite Home page, perform the personalization steps mentioned earlier. See: Performing Personalization Setup Steps.
Configuring Search Proxy Parameters in the Configuration Tab
Use the Configuration tab to set proxy parameters to enable Oracle SES instance access. This includes setting proxy parameters for an administrator and a valid FND user who has the FND Search Crawler responsibility.
Important: Changes in the proxy parameters including user name and password will require redeploying all searchable objects. If these objects have been crawled, then redeployment will not make data updates in Oracle SES. To resynchronize Oracle SES data, you must manually delete the data source of the same name in Oracle SES first, and then redeploy the objects.
Configuring Parameters to Access Oracle SES
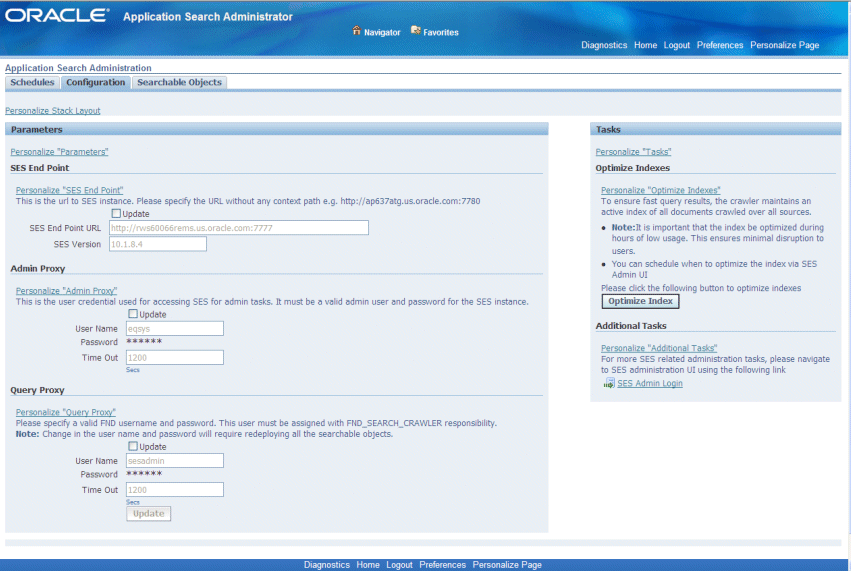
Use the following steps to configure search proxy parameters for an administrator and a valid FND user:
-
Log on to Oracle E-Business Suite with the Application Search Administrator responsibility and select the Application Search Administration link from the Navigator window.
-
From the Application Search Administration window, select the Configuration tab.
-
Specify the following information in the SES End Point region:
-
SES End Point URL: Enter an URL address with the format http://<hostname>:<portnumber>, such as http://my.host.com:portnumber in this field. This is an external Oracle SES instance to which query will be made against.
If you have the FND: Search Engine URL profile value defined, then you should see the URL value populated automatically.
To update this field, select the Update check box in the SES End Point region to enter new URL address. Click Update at the bottom of the page to save your change.
-
SES Version: Enter an appropriate Oracle SES version that your system will be integrated with. It should have minimum two characters, and the first two characters should be digits, such as 10.1.8.4, 11.1.2, or 11g.
Values entered here will be stored in the 'FND: Search SES Version' profile option.
-
-
Specify the administrative proxy parameters including User Name, Password, and Time Out values in the Admin Proxy region.
The Time Out value field can be populated automatically if you set the 'FND: Search Session Timeout Value for Admin Tasks' profile value.
Note: To integrate Oracle E-Business Suite Secure Enterprise Search with Oracle SES, you need to set the Admin Proxy section as follows:
-
User Name: eqsys
-
Password: Use the same password (such as Oracle10g) for eqsys user name when you installed the Oracle SES.
-
Time Out: 1200 secs
To update these fields, select the Update check box in the Admin Proxy region to make the changes. Click Update at the bottom of the page to save your change.
-
-
Specify the query proxy parameters including User Name, Password, and Time Out values for a valid FND user with the FND Search Crawler responsibility. This query user name and password is usually set to the system administrator sysadmin/welcome or search administrator sesadmin/welcome who has appropriate search responsibilities.
Like the Admin Proxy region, the Time Out value field can be populated automatically if you set the 'FND: Search Session Timeout Value for Query' profile value.
To update these fields, select the Update check box in the Query Proxy region to make the changes. Click Update at the bottom of the page to save your work.
Important: Once you change the query proxy parameters, the Oracle SES instance needs to be restarted to reflect the changes.
Performing Setup Steps in Oracle SES
Oracle E-Business Suite Secure Enterprise Search integrates with Oracle Secure Enterprise Search (SES) to provide powerful text search features. It allows Oracle SES to crawl application content and return results for query.
To ensure its seamless integration with Oracle SES, the search administrator needs to perform the following administrative tasks in Oracle SES after completing necessary setup steps in Oracle E-Business Suite Secure Enterprise Search:
-
Log on to the Oracle SES administrative user interface using http://<hostname>:<portnumber>/search/admin. You can also access it from the SES Admin Login link in the Configuration tab of the Oracle E-Business Suite Secure Enterprise Search administrative page.
-
Select the Global Settings tab from the Secure Enterprise Search page to configure the following settings:
-
Select Identity Management Setup from the System section to set up connections between Oracle SES and an identity management system to validate and authenticate users for secured searches.
Select oracle.search.plugin.security.identity.ebs.EBSIdentityPluginMgr from the Available Identity Plug-in region and click Activate.
In the Activate Identity Plug-in page, enter the following parameter values to define the selected Identity Plug-in settings for all authentication and validation activity in Oracle SES:
-
HTTP endpoint for authentication: Enter an end point URL for Oracle E-Business Release 12 authentication, such as http://my.host.com: port/webservices/AppSearch/SecurityService.
-
User ID: Enter the search administrator's user name that you created earlier. See: Creating a Search Administrator.
-
Password: Enter the search administrator's login password.
Click Finish to return to the Global Settings page.
-
-
Select Federation Trusted Entities from the Search section to add federation entities. Oracle SES uses these entities to provide secure federated searches.
In the Federation Trusted Entities page, enter the following information:
-
Entity Name: Enter the search administrator's user name that you created earlier. See: Creating a Search Administrator.
-
Entity Password: Enter the search administrator's login password.
-
Select the Use Entity Plug-in for authentication check box to authenticate through the active identity plug-in.
Click Add to return to the Global Settings page.
-
-
Select the Crawler Configuration link from the Sources section to ensure the crawler logging setting is appropriate.
In the Crawler Logging region, ensure the crawler log file directory path including log file name defined in the Crawler Log File Directory field is less than the supported length of 100 characters for Oracle SES 11.1.2 integration.
Click Apply.
-
-
Restart both Oracle SES and Oracle E-Business Suite instances.
Important: You must make sure that the search.properties file in Oracle SES server is also properly configured. Use the following steps to set the time in milliseconds to wait for security filter refresh task to finish during query processing:
-
Locate the search.properties file in $ORACLE_HOME/search/webapp/config directory.
-
Set the security filter refresh task wait time value: sec_filter_refresh_wait_time=20000
For more information on Oracle SES integration setup steps, see the Oracle Secure Enterprise Search Administrator's Guide for details.
Securing Searchable Objects
Security is the most critical feature that is designed to guard application content from unauthorized access. To ensure that the right person has access to appropriate data at the right time, searchable objects or metadata must be enforced by security rules before they can be made available for search within the Oracle E-Business Suite.
Oracle E-Business Suite Secure Enterprise Search provides a flexible mechanism to enforce and secure searchable objects without compromising on the data integrity and content sensitivity. To effectively manage search security both at the group and object levels, and reduce the search response time, the following security mechanisms are used in enabling Oracle E-Business Suite Secure Enterprise Search:
-
Role-Based Access Control (RBAC) Security
With RBAC security model, search security can be enforced at the group level through security grants. This section discusses the Role-Based Access Control (RBAC) security model and steps in creating security grants to ensure the application content sensitive data is only accessed by authorized people.
-
Security plug-ins provide another layer of security control at the object level. A security plug-in can be added to a searchable object at the design time; it can also be used at crawl time to fetch ACLs and generate Security Keys offline or at query time if needed to protect unauthorized access to application data. Sample security plug-ins are also described in this section.
-
User Authorization Cache (UAC) feature allows previously cached Security Keys for a specific user and a searchable object or data source to be used at query time. This greatly reduces the search response time and provides a quick result with security enforced. When a user performs a search, the cached information is first examined to look up the query user or an object. If the match is found, the associated keys will be compared with the pre-built ACLs to authorize or revoke the document access privileges. In case there is no match found, then the Security Keys are fetched synchronously.
Role-Based Access Control (RBAC) Security
Oracle E-Business Suite Secure Enterprise Search uses Role-Based Access Control (RBAC) security to secure searchable objects through roles, and user access to applications data is determined by the roles granted to the user. This approach builds upon Data Security and Function Security, but it goes beyond both of them.
Role-Based Access Control Security
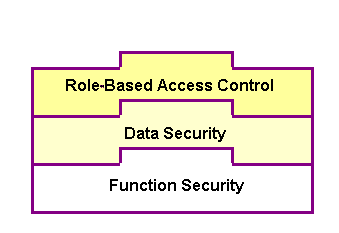
Function security is the base layer of access control in Oracle E-Business Suite. It restricts user access to individual menus and menu options within the system, but it does not restrict access to the data contained within those menus. Data security provides access control on the application data, and the actions a user can perform on the data. With data security, users can be restricted by security rules to access or view only certain types of data on the screen once they have selected a menu while an administrator can have more data access to the same page.
With RBAC, access control is defined through roles, and a role can be configured to consolidate the responsibilities, permissions, function and data security policies that users require to perform a specific task. This solution simplifies mass updates of user permissions because changes can be done through roles which inherit the new sets of permissions automatically. Based on the job functions, each role can be assigned a specific permission or permission set if needed. For example, a sales organization may include 'Sales Representative', 'Sales Manager', and 'Sales Support' roles. The 'Sales Manager' role would include a permission set allowing the manager role to perform a job function for both the representative and support roles.
By leveraging the concept of permission sets, Oracle E-Business Suite Secure Enterprise Search allows related searchable objects to be grouped and sequenced to construct searchable groups; these searchable groups are associated with a function role and then they are assigned to users through security grants. When a user logs on to the E-Business Suite and performs a search, Oracle E-Business Suite Secure Enterprise Search filters the secured searchable objects based on the grant and displays the list to the user who has authorized privileges.
For example, Oracle E-Business Suite Secure Enterprise Search uses search function security to provide a permission on searchable objects and then grant to different roles. When a searchable object 'purchase order' is defined, in order for a user to search on this purchase order object, she or he must have been assigned to a role that holds a grant of purchase order access permission. Once the user logs on the applications, she or he should be able to see the purchase order displayed from the searchable object list for search selection.
For more information on Data Security, Function Security, and RBAC security models, see Oracle E-Business Suite System Administrator's Guide - Security for details.
Creating Security Grants
To secure application data access to a user with right privileges, the system administrator or search administrator needs to administer the security grant which includes:
Prerequisites: Please note that the system or search administrator needs to have Functional Developer role to create objects, permissions, and permission sets, as well as the Functional Administrator role to create grants.
To create security grants:
-
Log on to Oracle E-Business Suite with the Functional Developer responsibility.
-
From the Security tab, click the Objects subtab, and select Create Object.
-
Enter the following fields to create an object:
-
Name: Enter a display name.
-
Code: Enter a name, such as WF_SEARCHABLE_NTF.
-
Application Name: Select an application name.
-
Database Object: This must be FND_OBJECTS.
-
Description: Enter a proper description for the object you want to create.
-
Column: Select the first column name as CRAWL_CRAWLABLE. The Type field populated automatically with VARCHAR2.
-
-
Click Apply.
-
Select the Object Instance Set tab and click Create Instance Set.
-
Enter the following information to create an instance set:
-
Name: Enter a display name for the instance set.
-
Code: Enter a code.
-
Description: Enter a proper description for the instance set.
-
Predicate: Enter a predicate.
-
-
Log in with the Functional Developer responsibility. From the Security tab, select the Permissions subtab and click Create Permission.
-
Enter the following fields to create a permission:
-
Name: Enter a name for the permission, such as WF: Searchable Notifications.
Note: The permission name entered here will be displayed as a searchable object name in the Narrow By region which allows you to refine your search from the Search Results page. For more information on how to use Oracle E-Business Suite Secure Enterprise Search, see Oracle E-Business Suite User's Guide.
-
Code: Enter a standard code, such as WF_SEARCHABLE_NTF.
-
Description: Enter a proper description for the permission.
-
Object Name: Select the object you created in the previous steps.
-
Add to Permission Set: Select a permission set for this field if you have a permission set created.
-
-
Click Apply.
-
Log in with the Functional Developer responsibility. From the Security tab, select the Permission Sets subtab and click Create Permission Set.
-
Enter the following fields to create a permission set:
-
Name: Enter a name for the permission set, such as ATG Searchables.
Note: If you are authorized to have the security access to the permission set name you entered here, when you perform a search on the Oracle E-Business Suite Home Page or a product home page, you should find this permission set name displayed from the business category drop-down list for your selection. For more information on how to use Oracle E-Business Suite Secure Enterprise Search, see Oracle E-Business Suite User's Guide.
-
Code: Enter a standard code, such as SESG_WF_NTF.
Important: Your permission set must be prefixed with SESG.
-
Description: Enter a proper description for the permission set.
-
-
Click Add Another Row and enter the following information:
-
Permission: Select a permission you created earlier, such as WF: Searchable Notifications.
-
Add more permissions as appropriate.
-
-
Click Apply.
This process requires the 'Functional Administrator' role to create grants.
-
Log in with the Functional Administrator responsibility. From the Security tab, select the Grants subtab and click Create Grant.
-
Enter the following fields in the Create Grant: Define Grant page:
-
Name: Enter a name for the grant, such as ATG Searchables Grant.
-
Description: Enter a proper description for the grant.
-
Enter proper information in the Effective From and Effective To fields.
-
-
Enter the following information in the Security Context region:
-
Grantee Type: Select a proper grantee type, such as Group of Users.
-
Grantee: Enter System Administrator.
-
-
Click Next.
-
In the Set region, select a permission set to grant, such as ATG Searchables and click Next.
-
Review the grant details and click Apply.
Search Security Plug-ins
In addition to securing your search at the group level through security grants, Oracle E-Business Suite Secure Enterprise Search uses security plug-in to strengthen security further down to the object level. Since searchable objects are the key elements in the crawling mechanism, this type of security mechanism can be easily implemented and enforced at crawl time and even can be dynamically executed during user query. Its flexible, object-based security plug-in feature can effectively guard and protect application sensitive data such as HRMS employee data, General Ledger data in a legal entity from unauthorized access or transactions across organizations if in a multiple-organization environment.
Security plug-in is a Java class that implements security methods to support custom or user-defined security rules at the object level and in turn to secure your search.
At design time, a security plug-in can be added to a searchable object during the object creation through the metadata-based Search Modeler user interface.
At crawl time, while creating indexable documents, two search methods (getAcl() and getSecureAttrAcl()) of the plug-in associated with the object definition are invoked to generate the access control list (ACL) for each document.
Note: An ACL is a list of permissions attached to an object specifying who or what is allowed to access the object and what operations are allowed to be performed.
Oracle SES authorization plug-in works on the basis of the ACL-based security model and Security Keys for a document to authorize users or revoke the access to a search result. Through the authorization plug-in implementation of Oracle E-Business Suite connector in Oracle SES, all searches within Oracle E-Business Suite can be authorized and leveraged from the SES search engine.
At query time, when a user performs a search, different sets of search methods ( getSecurityKeys() and getSecureAttrKeys()) of the plug-in are executed to generate the Security Keys for the user in order to match the pre-built ACLs. Any matched indexed documents will then be retrieved for the user. Unmatched or unauthorized documents get dynamically filtered out in the process.
Security Keys and User Authorization Cache (UAC)
To reduce the search response time of fetching Security Keys simultaneously during user query, User Authorization Cache (UAC) framework in Oracle SES is leveraged to allow Security Keys to be generated as an offline process if a User Crawler initiates at the crawl time.
This user crawling process generates a list of Oracle E-Business Suite users for whom the Security Keys needs to be cached in Oracle SES. Security Keys are then generated against the user list by executing (getSecurityKeys() and getSecureAttrKeys()) methods of the plug-in. These generated keys for a given user and a specific searchable object or data source are cached as User Authorization Cache and will be looked up during user query to see if any match for a given source and user and whether the cache is usable.
For more information about User Authorization Cache feature and how it works, see User Authorization Cache.
How to add a search security plug-in to an object, see Creating Searchable Objects, Oracle E-Business Suite Search Modeler User's Guide available from My Oracle Support Knowledge Document 781366.1, Search Modeler 1.1 for Oracle E-Business Suite Readme.
This section includes the following topics:
How Security Plug-in Works
To effectively guard application content from unauthorized access and support various business requirements within Oracle E-Business Suite, security plug-in mechanism is implemented to ensure the search security and context sensitive information only accessible to appropriate users.
This section highlights and further explains the roles of security plug-in from crawl and query different perspectives. It includes the following topics:
Crawl Time to Generate ACLs
Security plug-ins are used to fetch ACLs at crawl time.
When Oracle E-Business Suite Crawlable End Point receives crawl requests from Oracle SES crawler threads, the Crawlable Factory is initialized to fetch the indexable content from Oracle E-Business Suite database and create crawlable documents. While creating indexable documents, the security plug-in associated with the searchable object definition will be used through the invocation of the getAcl() and getSecureAttrAcl() methods to generate ACLs for the documents.
At this time, these indexable documents in the form of RSS feed is ready to be consumed. Oracle E-Business Suite crawler threads pick up the documents; the Crawlable End Point sends them back to the SES indexing engine as crawling responses. The SES indexing engine will then analyze the documents and transform them into indexed documents with readable format.
Query Time to Generate Security Keys
At query time, security plug-ins are used to generate Security Keys for the query user.
Query through Oracle E-Business Suite
When a user performs a search through the Oracle E-Business Suite user interface, a search session is created and the applications context is also initialized for the user. The applications context may be incomplete at this stage depending on if the user has selected a responsibility or not after logging on to the Oracle E-Business Suite.
Note: Applications context information is required for application users to perform certain business transactions or to be used in security plug-in to generate the ACLs and Security Keys for the users. It contains username, responsibility, responsibility application, and security group information.
When the query is submitted to the SES client APIs, the APIs in turn invoke the Web service calls in the Oracle SES server. To ensure the user is authorized for a search, Oracle SES first looks up the previously cached Security Keys for the object and logged-in user in User Authentication Cache (UAC). If a match is found and the cache is usable, the associated keys will be used to compare the pre-built ACLs. Any matched indexed documents will be retrieved for the user. If no match is found, Identity Manager in Oracle SES requests Security Keys for the user through Security Service End Point. A proxy session is initialized to verify the credentials of the proxy username and password required by Oracle SES for the user. This proxy session is trusted or updated on behalf of the actual search user for whom the security keys have been requested.
Please note that the proxy applications context may be incomplete since the search can be performed either with or without the responsibility information. To generate Security Keys for the user in order to perform certain business transactions or activities that require full applications context information, you must extend the oracle.apps.fnd.search.impl.ContextSecurable plug-in class to create the complete context information. For more information about the plug-in mechanism, see Understanding Security Logic and General Plug-in Mechanism.
Security plug-in is also invoked by the Security Service End Point to generate the Security Keys through the execution of the getSecurityKeys() and getSecureAttrKeys() methods for the proxy content.
Once the Security Keys are generated, the Security Service End Point sends the keys back in response to the earlier request from Identity Manager. This request-response happens over HTTP protocol.
To ensure that it does not wait indefinitely for the response to complete, Oracle SES can set a timeout message on the request. The timeout value is configurable.
Query through Oracle SES
When an Oracle E-Business Suite user performs a search through the Oracle SES user interface, the security checks can be performed in the following two stages:
-
Login Security Authentication: This stage validates the user's login credentials through Oracle SES without security or authorization plug-ins.
-
Search Security Authorization: This stage begins when a user submits a search query after successful login. Search plug-in is used in the same way as described in querying through Oracle E-Business Suite that is to generate Security Keys for the query user.
Note: The major difference between searching from within Oracle E-Business Suite and from Oracle SES Search UI is that while searching from the Oracle SES Search UI, the proxy applications context is always incomplete since the responsibility information may not be there.
If certain business transactions or activities that require full applications context information, you must extend the oracle.apps.fnd.search.impl.ContextSecurable plug-in class to create the complete context information. For more information about the plug-in mechanism, see Understanding Security Logic and General Plug-in Mechanism.
The user query is submitted to the SES client APIs which in turn invoke the Web service calls in the Oracle SES server. To ensure the user is authorized for a search, Oracle SES first looks up the previously cached Security Keys for the object and logged-in user in User Authentication Cache (UAC). If a match is found and the cache is usable, the associated keys will be used to compare the pre-built ACLs. Any matched indexed documents will be retrieved for the user. If no match is found, authorization plug-in contacts the Identity Manager to fetch the Security Keys. Identity Manager sends a request message containing the proxy username and password to Oracle E-Business Suite Security Service End Point. Security End Point establishes the proxy session and Applications Context. After the user credential (proxy username and password) is verified, the proxy session is trusted or updated on behalf of the actual search user for whom the Security Keys have been requested.
Security plug-in is invoked by the Security Service End Point to generate the Security Keys through the execution of the getSecurityKeys() and getSecureAttrKeys() methods for the proxy content.
Once the Security Keys are generated, the Security Service End Point sends the keys back in response to the earlier request from Identity Manager. Authorization plug-in receives the Security Keys for the search user.
Use Security Keys to Match the Pre-built ACLs
Oracle SES search service or APIs retrieve indexed documents from index store, matching the search keywords and filters. Indexed documents with pre-built ACLs are filtered by the Security Keys retrieved for the search user. Filtered search results are returned back to the query user. Unmatched or unauthorized documents get dynamically filtered out in the process.
Understanding Security Logic and General Plug-in Mechanism
Implementing Security Logic
Oracle E-Business Suite Secure Enterprise Search provides security through an interface. Once implemented, various methods of this interface can be called at different stages to enforce the security on the content of a searchable object. Each searchable object can have a plug-in Java class, nominated at design time through the Search Modeler user interface. If this class implements the Securable interface, the rules implemented by this class are enforced on the searchable object.
This Securable interface security plug-in Java class includes the following security methods:
-
isAclEnabled
Crawlers use this method to determine if a document is ACL guarded or not. The getAcl() and getSecurityKeys() methods are called only when this method returns a value of true.
-
getAcl
This method returns a list of tokens as access control during crawl time to extract each doc with ACL. This method is called for every document before they are sent to Oracle SES for indexing. The string value must be uppercase, alphanumeric, and not longer than 30 characters. This list is used as a predicate when the query is sent to Oracle SES. For example, if you return a string value of "XYZ123ABC", then only the person who holds the key "XYZ123ABC" can access this document, which is then returned by the getSecurityKeys() method.
-
getSecurityKeys
This method returns an array of keys that the user holds at the time the query is made. You can get the session user from search context that is passed into this method. This method is called only once per session.
-
getSecureAttrAcl
In some cases, ACLs may be related to an attribute of the searchable object. If this is true, then you must specify which attribute of the searchable object is a secure attribute. When it is specified and the Securable interface is implemented by its plug-in, this method is called for each secure attribute of each document. This method returns a list of ACL for secure attributes at crawl time. It uses the same rules as for getAcl(), except it is associated with a particular attribute. This method is paired with getSecureAttrKeys() as getSecurityKeys() is with getAcl().
-
getSecureAttrKeys
This method is called for each secure attribute per session. It returns a match string list based on the user's access.
General Security Plug-in Mechanism
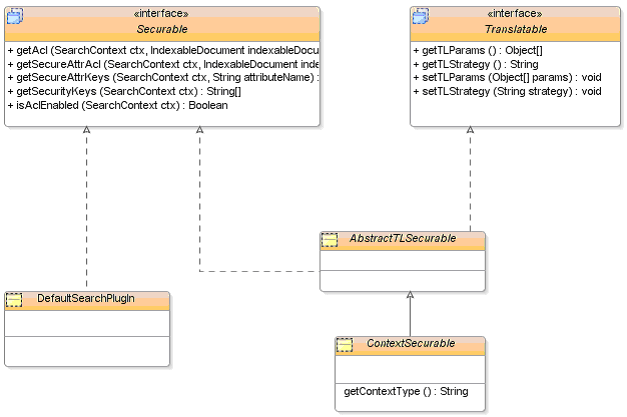
Certain security plug-ins not only provide Securable feature, but also provide translation feature to searchable attribute. The relationship between Securable interface, translation interface, and other associated Java classes is illustrated in the following plug-in class hierarchy diagram:
General Plug-in Class Hierarchy Diagram
-
oracle.apps.fnd.search.AbstractTLSecurable: It is an abstract Java class which supports translation of Searchable and Displayed attribute names. Any business requirement which requires the displayed attribute names to be translated should extend this class.
-
oracle.apps.fnd.search.impl.ContextSecurable: It is an abstract Java class which can have the full applications context information in order to generate the ACLs and Security Keys. Any plug-in business logic which would require full applications context should extend this class. It is imperative that any subclass of ContextSecurable plug-in class has to implement translations as well.
-
oracle.apps.fnd.search.impl.DefaultSearchPlugIn: It is a concrete Java class which secures the search results based on whether the search user has access to the target UI function or not. This Java class (and any of its subclass) does not support translation of attribute names and full applications context.
ACL-based Security
An access control list (ACL) is a list of permissions attached to an object. The list specifies who or what is allowed to access the object and what operations are allowed to be performed on the object.
In the ACL-based security, each entry in the list specifies a subject and an operation. For example, the entry (Alice, delete) on the ACL for file WXY gives Alice permission to delete file WXY. Each crawled entry is associated with a locker, which is created in the form of an ACL. Both the locker and the content get indexed in Oracle SES.
When a user performs a search on an object in Oracle E-Business Suite, the system first checks the list for an applicable entry in order to decide whether to proceed with the query.
When crawled, the getAcl() method for each document is called by the crawler and it returns an ACL, which is indexed by Oracle SES along with the document.
Please note that the ACL-based security approach can also be used at query time along with getSecureAttrKeys() for additional security based on secure attributes. For more information, see Supporting Security Models with Search Plug-ins.
A Security Example with ACL-based Security
In this example, the ACL is a list of responsibilities that have access to functions in FND_FORM_FUNCTIONS. Resolving this relationship requires some complex logic and a number of tables including FND_MENUS and FND_MENU_ENTRIES.
| Function ID | Name | Content | ACL |
|---|---|---|---|
| 1 | Edit | Oracle Workflow | 10 20 |
| 2 | Update | Oracle Test | 10 |
| 3 | Create | Oracle Financial | 30 |
| 4 | Delete | Oracle Personnel | 40 |
At query time, a search user needs to acquire key(s) for a secure searchable object. In this example, it is a list of responsibilities assigned to the user. The getSecurityKeys() method returns this list when it is called. The query is rewritten with the key(s) and posted to Oracle SES. (This is the equivalent of adding security predicates to a query in SQL before hitting the database table).
The user SYSADMIN logs in and issues a query search on the content Oracle. Before hitting Oracle SES, the getSecureAttrKeys() method is called with the proper user context and returns a list of responsibilities assigned to SYSADMIN, which is "10", "20", and "30". The query is rewritten as:
(ACL_KEY: 10 OR 20 or 30) AND content: oracle
Using the above example, this query returns the following:
| Function ID | Name | Content | ACL |
|---|---|---|---|
| 1 | Edit | Oracle Workflow | 10 20 |
| 2 | Update | Oracle Test | 10 |
| 3 | Create | Oracle Financials | 30 |
This approach incurs some cost at crawl time because it calls the getAcl() method for each row in FND_FORM_FUNCTIONS. However, this is acceptable if the underlying table is relatively small.
Tip: In this example, there are approximately 40,000 records in FND_FORM_FUNCTIONS and it takes about ten minutes to crawl the entire table.
Query Rewrite Security
By leveraging the searchable attribute feature, Query Rewrite provides another layer of security mechanism during user query to secure application content.
To use this Query Rewrite security, one or more searchable object attributes have to be marked as "Secured" at design time during object creation so that the getSecurityKeys() method of the search plug-in can be invoked for each "Secured" attribute at the time of user query.
At crawl time, since the secure attribute concept is used in this mechanism, no access control list will be generated during crawl for the documents of a searchable object.
At query time, when a user performs a search, the user acquires key(s) for a secure object to authenticate the operation based on the applications context. Oracle SES fetches the run-time keys for the user by invoking getSecurityKeys() method for each secure attribute, and returns a list of Security Keys for the user to access the secure object. The query is rewritten with keys and posted to Oracle SES. This query rewrite concept is similar to add security predicates to a query in SQL before hitting the database table. As a result, only proper data for the authorized user will be returned as the search result, but the entire query rewritten process is transparent to the user.
For example, a Purchase Order should be visible only to the buyer who places the order. With this design principle, BUYER_ID acting as an identifier should be marked as a secure attribute and it should be associated with the document of Purchase Order searchable object during the design time to secure the order content. When a user searches for "laptop docking station" related purchase orders, the query will be rewritten with the predicate, BUYER_ID = "<buyer id of user>". This approach reinforces the secured object Purchase Order and only allows the person who places the order to have the relevant UI and order access privileges.
Tip: Query rewrite method should be used when the number of keys is limited in number. If the number of keys is higher, use ACL method instead.
With the query oriented approach, you nominate one or more attributes as secure attributes for each searchable object. For example, the BUYER_ID can be a secure identifier for a purchase order.
At query time, (before searching Oracle SES), a getSecureAttrKeys() method is called for each secure attribute such as BUYER_ID. The getSecureAttrKeys() method implementation should map the number of IDs that the current user has access to.
Note: The query only returns results that the user has access to.
When using this approach, there is no need to form Access Control Lists (ACLs) and security is basically enforced at query time, which means there is less risk of security data being out of date. However, this approach does not work if a user has too many keys. To rewrite a query that has thousands of keys is unrealistic. In order for this approach to perform you must provide a way to limit the number of keys returned by getSecureAttrKeys().
Tip: When there is no clear way to limit keys, or it is too expensive to resolve keys at query time, you should use the crawl oriented approach.
A Security Example with ACL with Query Rewrite
The ACL-based security approach can also be used at query time along with getSecureAttrKeys() for additional security based on secure attributes.
Security Rule Based on Employee Hierarchy
Take purchase orders as an example to explain the security mechanism that combines both ACL-based security and Query Rewrite security.
Purchase orders are usually owned by the user (employee) who initiates the purchase, and the employee hierarchy is usually used as the rule for its visibility to others. For example, an employee can access only his or her own purchase orders, whereas a manager can access the purchase orders he or she owns and those that are initiated by his or her reportees.
The following diagram illustrates a typical entity relationship for a purchase order.
Purchase Order Entity Relationships
The following list of attributes have been selected for displaying:
| Entity | Attribute |
|---|---|
| FWK_TBX_PO_HEADERS | HEADER_ID (PK) STATUS_CODE DESCRIPTION BUYER_ID (FK) |
| FWK_PO_LINES | LINE_ID (PK) HEADER_ID (FK) ITEM_ID (FK) ITEM_DESCRIPTION |
| FWK_TBX_ITEMS | ITEM_ID (PK) ITEM_DESCRIPTION |
| FWK_TBX_EMPLOYEE | EMPLOYEE_ID (PK) FIRST_NAME LAST_NAME EMAIL_ADDRESS MANAGER_ID |
To use Query Rewrite security, you should mark the BUYER_ID attribute as a "Secured" attribute. The content is then indexed in Oracle SES during crawl time without an ACL.
The following is a sample listing of purchase orders that are initiated by different employees. Employees adillon and bcarey report to ekane, ekane reports to rlavery, and rlavery reports to khart.
| Header ID | Status Code | Description | Content | BUYER_ID |
|---|---|---|---|---|
| 1 | Open | Dell Computer | Oracle Workflow | 12 (adillon) |
| 2 | Closed | Apple, Inc | Oracle SES | 13 (khart) |
| 3 | Open | Oracle | Oracle Test | 14 (ekane) |
| 4 | Approved | Microsoft | Oracle Financial | 15 (bcarey) |
| 5 | Approved | Oracle | Oracle | 13 (khart) |
| 6 | Closed | Dell Computer | Oracle Framework | 10 (rlavery) |
| 7 | Open | Oracle | Oracle Personnel | 14 (ekane) |
At query time, an authenticated user acquires a key, or keys, via the getSecureAttrKeys() method. This method passes applications context information along with the secure attribute such as BUYER_ID. It returns a list of keys to access purchase orders. The query is rewritten with the keys and posted to Oracle SES.
Using the above list of purchase orders, if the user ekane performs a keyword search on 'Oracle', she would have the keys 12, 14, and 15. The results would be:
| Header ID | Status Code | Description | Content | BUYER_ID |
|---|---|---|---|---|
| 1 | Open | Dell Computer | Oracle Workflow | 12 (adillon) |
| 3 | Open | Oracle | Oracle Test | 14 (ekane) |
| 4 | Approved | Microsoft | Oracle Financial | 15 (bcarey) |
| 7 | Open | Oracle | Oracle Personnel | 14 (ekane) |
If adillon performs the same search only one row is returned. However, this approach becomes more complicated when the head of a real department performs a search because they own the entire hierarchy and may have thousands of keys. For this case you can add logic in the getSecureAttrKeys() method so that only a specific number of keys or levels of hierarchy is returned.
Supporting Security Models with Search Plug-ins
To secure sensitive application data from authorized access and support complex security needs within Oracle E-Business Suite, Oracle E-Business Suite Secure Enterprise Search provides seeded security search plug-ins. These plug-ins are pre-built public Java classes which support well-known application security models. With the flexible plug-in security mechanism, users can search and navigate to appropriate transaction pages with security enforced to obtain needed information.
Oracle E-Business Suite Secure Enterprise Search supports the following security models with seeded search plug-ins:
-
Business Group Based Security Search
-
Legal Entity Based Security Search
-
Organization Based Security Search
-
Employee Hierarchy Based Security Search
Common Security Features of Seeded Search Plug-ins
Although these seeded search plug-ins are provided for various business reasons to secure sensitive application data, they all have the following common security features:
-
Designed Based on ACL and Query Rewrite Security Models
All these four seeded search plug-ins are designed based on both the ACL and Query Rewrite security models. As a result, the isAclEnabled() method must return “true” in order for the getAcl() and getSecurityKeys() methods to be called later on during the crawl and query.
-
Crawl Time ACL Implementation
In order to fetch ACLs while creating indexable documents at crawl time, the getAcl() and getSecureAttrAcl() methods of the plug-in have to be implemented.
Additionally, the getAcl() method should extend the DefaultSearchPlugIn concrete Java class (oracle.apps.fnd.search.impl.DefaultSearchPlugIn), so that the access to specific target UI function can be securely enforced. For more information about DefaultSearchPlugIn, see Understanding Security Logic and General Plug-in Mechanism.
-
Query Time Security Key Implementation
At query time, after a query user's credential (proxy username and password) is verified and updated in response to a request of the user security validation, the getSecurityKeys() method should be simply invoked with super class implementation, and the getSecureAttrKeys() method returns the list of matched business groups that the query user has access to.
-
-
A Secure Attribute Needed for Query Rewrite
A secure attribute is needed to implement the Query Rewrite security mechanism.
A searchable object contains a number of database tables or views; each table or view contains a number of columns that are bound to business data. While defining a searchable object through Search Modeler, you can select needed columns for each selected table name (entity) for your object. These table columns are called attributes that can be indexed for search. If an attribute contains certain feature that can be used to secure documents during search, then this attribute can be considered as a secure attribute. For example, the BUSINESS_GROUP_ID column that acts as a Business Group identifier can be a secure attribute for HR tables.
At query time, in order for query engine to generate Security Keys, (before searching Oracle SES) the getSecureAttrKeys() method is called for each secure attribute such as BUSINESS_GROUP_ID. The getSecureAttrKeys() method then returns a number of Business Group IDs that the query user has access to. As a result, the query to Oracle SES is rewritten.
"Secured" and "Stored" Attribute
To ensure the security check of each search plug-in can be enforced, all seeded plug-ins must contain an unique, secure table column (attribute) as a secure identifier. To differentiate the "secure" feature from other attributes, the attribute property "Secured" should be selected while defining a searchable object in Search Modeler. An attribute marked with "Secured" property indicates that this attribute can be used for securing the document using search plug-in. Additionally, select "Stored" property for the attribute. This indicates that this attribute can be stored in Oracle SES.
Note: If an attribute is marked not "stored", it cannot be displayed in the search result summary.
Other available attribute properties can be like "displayed", "title", "Is attachement", etc. For more attribute property information, see Creating Searchable Objects, Oracle E-Business Suite Search Modeler User's Guide available from My Oracle Support Knowledge Document 781366.1, Search Modeler 1.1 for Oracle E-Business Suite Readme.
For example, to ensure business group based security, Business Group Search Plug-in will require that the search object definition should have BUSINESS_GROUP_ID attribute, which should be marked at least “Stored” and “Secured”.
For more information about ACL and Query Rewrite security models, see ACL-based Secuirty and Query Rewrite Security.
In addition to the common security features, each search plug-in contains various security requirements and secure attribute information. They are further explained in the following sections:
Business Group Based Security Search
A good example of this type of security model is Oracle E-Business Suite Core HRMS system.
-
Security Requirements: A Business Group is an organization that is set up and configured in Oracle Human Resources. It is the highest level classification in the organization hierarchy of the Oracle E-Business Suite, and it often relates to country-specific legislation. It may correspond to your entire enterprise or to a major grouping such as a subsidiary or operating division. If your payroll tax and employment authorities permit it, you can group employees of different registered companies together for reporting.
In this security model, data within a business group is only visible to members of that business group. Even an HRMS superuser (e.g. HR Director) can only see data pertaining to the same business group.
For example, an XYZ Organization has Consulting, Manufacturing, and Projects business groups. Consulting business group data can only be seen by the Consulting group members, not by the Manufacturing and Projects group members.
Oracle E-Business Suite Organization Model
To secure the group data access only limited to the associated group members while retrieving search results, data is striped in the HRMS tables using BUSINESS_GROUP_ID identifier.
-
Business Group Search Plug-in (oracle.apps.fnd.search.impl.BusinessGroupSearchPlugin) Java Class: Use this seeded business group search plug-in to secure search results depending on the search user’s access to one or more HRMS Business Groups. This search plug-in must extend the DefaultSearchPlugIn concrete Java class (oracle.apps.fnd.search.impl.DefaultSearchPlugIn) to ensure that the secure access to the target UI function is also validated.
-
Secure Attribute: Since a secure attribute is needed to implement the Query Rewrite security mechanism, all HRMS tables are striped with BUSINESS_GROUP_ID column, which acts as a Business Group identifier.
Since a secure attribute is needed to implement the Query Rewrite security mechanism, all HRMS tables are striped with BUSINESS_GROUP_ID column, which acts as a Business Group identifier.
This plug-in requires that the search object definition should have BUSINESS_GROUP_ID attribute, which should be marked at least “Stored” and “Secured”.
Legal Entity Based Security Search
-
Security Requirements: Legal Entity in the Oracle E-Business Suite corresponds closely to "company" in the legal world. It has the right to own property, the right to trade, and the responsibility to comply with appropriate laws. You can store information about a registered company or other real world legal entity in the "legal entity".
The Ledger represents an accounting representation for an organization that is accountable in a self-contained way. A ledger owner might be a legal entity. Thus, the General Ledger (GL) application in Oracle E-Business Suite secures data at Legal Entity level.
To secure GL data during search, Legal Entity level security needs to be enforced by using the LEDGER_ID identifier in GL tables while retrieving search results.
-
Legal Entity Search Plug-in ( oracle.apps.fnd.search.impl.LegalEntitySearchPlugin) Java class: Use this legal entity search plug-in to restrict search results by the legal entities, which are accessible to the query user.
Similar to the business group search plug-in, this legal entity search plug-in must extend the DefaultSearchPlugIn concrete Java class (oracle.apps.fnd.search.impl.DefaultSearchPlugIn) to ensure that the secure access to the target General Ledger UI function is also validated.
-
Secure Attribute: Since a secure attribute is needed to implement the Query Rewrite security mechanism, all GL tables are striped with LEDGER_ID column, which acts as an unique identifier as a business group identifier does to a business group security model.
This plug-in requires that the search object definition should have LEDGER_ID attribute, which should be marked at least “Stored” and “Secured”.
Organization Based Security Search
Oracle E-Business Suite supports the concepts of multiple organizations as well as "Multiple Organizations Access Control (MOAC)" security model.
-
Security Requirements: Multiple Organizations can be sets of books, business groups, legal entities, operating units, or inventory organizations. You can define multiple organizations and the relationships between them through a single installation of Oracle E-Business Suite.
Operating Units (OUs) are good examples of multiple organizations and they are often identified with security. (The "Manufacturing Units” mentioned in the Oracle E-Business Suite Organization Model diagram in the Business Group Based Security Search closely resemble the multiple organizations.)
With MOAC security model, users are given access to the data they handle though "responsibilities". A responsibility is associated with a specific OU, or with several OUs. By securing application data in this way, users can access and process transaction only for the particular operating unit or set of operating units to which they have been granted access. In other words, data pertaining to one organization is normally not visible to another organization unless the user has permission to transact across organizations.
While performing a search on such objects, the organization level data security needs to be enforced through ORG_ID identifier for a wide variety of business entities including Purchase Orders, Sales Orders, Payables Invoices, Receivables Invoices, etc.
-
Organization Search Plug-in (oracle.apps.fnd.search.impl.OrganizationSearchPlugin) Java Class: Use this organization search plug-in to restrict search results by organizations, which are accessible to the query user.
Similar to the business group search plug-in, this legal entity search plug-in must extend the DefaultSearchPlugIn concrete Java class (oracle.apps.fnd.search.impl.DefaultSearchPlugIn) to ensure that the secure access to the target UI function associated with organizations is also validated.
-
Secure Attribute: Since a secure attribute is needed to implement the Query Rewrite security mechanism, most Oracle Financial applications tables (e.g. AP, AR, FA etc.) are striped with ORG_ID column, which acts as an unique identifier as a business group identifier does to a business group security model.
This plug-in requires that the search object definition should have ORG_ID attribute, which should be marked at least “Stored” and “Secured”.
Employee Hierarchy Based Security Search
This type of security model secures data based on employee hierarchy. Good examples can be iExpense, iProcurement, and iLearning within Oracle E-Business Suite. These application modules search on a particular employee's expenses, procurement, and training information based on employee hierarchy.
-
Security Requirements: Based on the employee hierarchy, data for a particular employee is only visible within his reporting hierarchy. Therefore, while performing a search on such object, search results have to be secured through an unique person identifier.
-
Employee Hierarchy Search Plug-in (oracle.apps.fnd.search.impl.EmployeeHierarchySearchPlugin) Java Class: Use this organization search plug-in to restrict search results by employee hierarchy in an organization, which are accessible to the query user.
Similar to other seeded search plug-ins, this legal entity search plug-in must extend the DefaultSearchPlugIn concrete Java class (oracle.apps.fnd.search.impl.DefaultSearchPlugIn) to ensure that the secure access to the target UI function associated with organizations is also validated.
-
Secure Attribute: Since a secure attribute is needed to implement the Query Rewrite security mechanism, most applications which require employee hierarchy, refer to PER_ALL_PEOPLE_F table. The PERSON_ID column is the unique person identifier (along with effective dates).
This plug-in requires that the search object definition should have PERSON_ID attribute, which should be marked at least “Stored” and “Secured”.
Other Considerations
Oracle E-Business Suite Secure Enterprise Search allows various security rules to be added to secure your searchable objects and application content. However, there are some security limitations and performance need to be considered.
Limitations
If you have more than one security attribute implemented, the principle is that both security rules must be satisfied. This may prevent some use cases from working.
For example, purchase orders are allowed to be seen by buyer, approver, and accountant. However, the accountant is actually a role which can be held by different people at different times, while the buyer and approver are recognized by their employee Ids. If this case occurs, set the emp_id as a secure attribute. This way, when getSecureAttrAcl for emp_id is called, the buyer_id is returned along with a list of responsibilities that are granted to access purchase order. The logic is paired with getSecureAttrKeys, which basically returns the buyer's direct employee Id as well as their responsibilities.
Performance
Since a search plug-in is used both during crawl and query, it adds overhead to performance in various times of the object life cycle. This is especially true in getAcl and getSecureAttrAcl since these methods are called row by row.
Crawl Time Performance
For crawl time performance, there are two possible expensive operations when crawling a searchable object:
-
Get Content
Get content implies JDBC calls to collect information to form indexable documents for Oracle SES to index. The performance of this operation depends on how well the view objects are defined, and how complex a searchable object is.
For example, if a searchable object assembles a large set of objects, such as a purchase order, it will take time to crawl because each document will need to source data from a number of tables (views).
-
Get Acl
Get ACL is performed on a row-by-row basis by definition because each document will have different ACLs. For a complex security model, getAcl might involve multiple database trips. This could incur a high cost and should be carefully balanced with query time performance in order to achieve overall performance.
Query Time Performance
Security also has impact on query time performance. This is due to the fact that for a securable searchable object, the query must be rewritten with access keys by calling getSecurityKeys. This function call usually involves database calls.
For example, during query execution, Oracle SES authorization plug-in mechanism contacts Oracle E-Business Suite Security Service End Point over HTTP protocol. The Security Service End Point is used to authenticate an Oracle E-Business Suite user and generate the Security Keys for the query user. The Security Service End Point is implemented as a servlet and registered as “AppSearch” servlet in oafm container. Therefore, any security service request is subject to the risk of HTTP Timeout. That is when Oracle SES authorization plug-in mechanism contacts the Security Service in Oracle E-Business Suite, the request has to be completed within a predefined amount of time.
As a guideline, the HTTP time-out value should be set to 30000 milliseconds. The time taken to execute the search plug-in is quite proportional to the overall execution time of a query. Hence for a responsive application, the order of execution has to be classified as follows:
-
Simple plug-in execution: 5000 milliseconds
-
Medium complexity plug-in execution: 10000 milliseconds
-
Complex plug-in execution: 20000 milliseconds
Please note that this has to irrespective of the data volume, which a customer might encounter. Query time performance normally has higher priority than crawl time performance. It must be balanced on a case-by-case basis.
Note: During query, Oracle SES fetches the runtime keys for the current application user using getSecurityKeys() or getSecureAttrKeys(). Oracle SES waits for a predetermined but configurable amount of time for these methods to retrieve the results. In case of a timeout, Oracle SES assumes the security keys are null for the current user and caches them. Most of the cases, it results in getting no search hits. This is one of the foremost reasons of not getting desired search results.
Improving Query Time Performance Using Cache
Please note that query time performance can be greatly improved by using previously cached security access keys stored in Oracle SES for a particular user, data source, or object. This greatly reduces the query response time of synchronously fetching the Security Keys for a user or gets timed out if the cache exists. For more information on how to use this feature, see User Authorization Cache.
User Authorization Cache
User Authorization Cache (UAC) framework provides a mechanism allowing the security access keys for a particular user, a specific data source, or a searchable object in Oracle E-Business Suite can be precrawled, cached, and stored in Oracle SES.
By leveraging this UAC feature from Oracle SES 11.1.2, when a user performs a search, instead of fetching the access keys synchronously for that user or object during user query, the previously cached Security Keys will be first looked up in SES for the availability of the keys for that user or object. If a match is found and the cache is usable, the associated keys will be used to compare with the pre-built ACLs. Any matched indexed documents will then be retrieved for the user. Unmatched or unauthorized documents get dynamically filtered out in the process. If there is no match found, the Security Keys will then be fetched and built security filters synchronously during the query. Any matched indexed documents based on the Security Keys and ACLs will be retrieved for the user.
Note: Although Oracle SES 11.1.2 contains UAC feature, UAC for Oracle E-Business Suite will be fully enabled in a later release of Oracle SES. Full benefits of UAC will be visible only until then.
By using the previously cached keys to authorize or revoke the document access privilege (in contrast of generating the keys real time during user query), this feature greatly reduces the search response time and in turn provides quick search results with security enforced.
Note: Security Keys are generated through the execution of the getSecurityKeys() and getSecureAttrKeys() methods of a security plug-in. For more security plug-in information, see Search Security Plug-ins.
How Does User Authorization Cache Work
To enable UAC feature, a specific User Crawler should be initialized to crawl Oracle E-Business Suite users and provides User documents to Oracle SES while other crawlers are for crawling and indexing searchable documents.
The following diagram illustrates the high level crawler tasks:
Crawler Interaction Flow
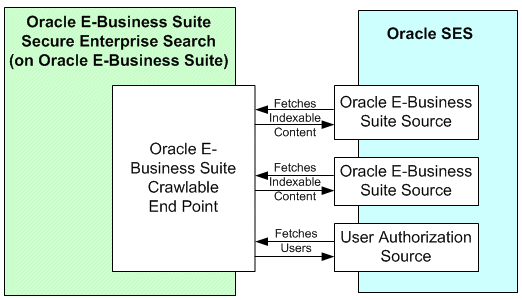
The User Crawler process generates a list of Oracle E-Business Suite users for whom the Security Keys need to be cached in Oracle SES for the predefined "User Authorization Cache" source type. See Defining and Updating UAC Source.
Fetching Security Keys Offline
In order to provide quick search results back to a user and eliminate possible time-outs of fetching Security Keys simultaneously during query due to complex application logic of deriving the keys, the user Security Keys can be generated as an offline process.
The following diagram illustrates the high level authorization cache population flow:
Authorization Cache Population High Level Flow Diagram
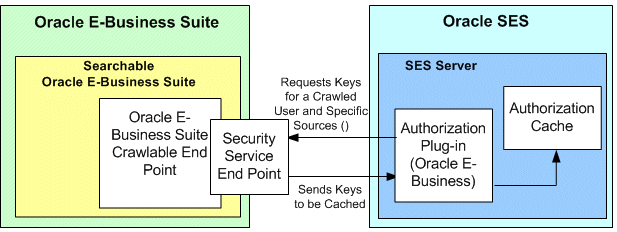
When a list of Oracle E-Business Suite user documents is generated by the User Crawler, Oracle SES invokes its Authorization Plug-in to contact Identity Management to fetch the Security Keys. This is done by sending a request for the keys of a crawled user and a specific data source to Oracle E-Business Suite Security Service End Point. The Service End Point in turn invokes the search plug-in to generate the Security Keys which is executed in the same proxy session where the user credential (username and password) is verified. The getSecurityKeys() and getSecureAttrKeys() methods of a search plug-in are executed to generate the Security Keys. The Service End Point sends the generated keys for a given user and a specific searchable object or data source to be cached to the Authorization Plug-in and have them cached and stored in Oracle SES.
Using Cached Keys for Query Time
When a user performs a search, these previously cached Security Keys will be examined first in Oracle SES to see if the cache exists for a given source and user, as well as whether the cache is usable.
-
If a match is found and the cache is usable, the associated keys will be used to compare with the pre-built ACLs. Any matched indexed documents will be retrieved for the user.
-
If there is no match found, the Security Keys will be fetched real time during the query and built security filters. Any matched indexed documents based on the Security Keys and ACLs will be retrieved for the user. Unmatched or unauthorized documents get dynamically filtered out in the process.
Please note that the user authentication cache is populated only when the User Crawler gets executed at the crawl time. If the Security Keys are fetched synchronously during user query, the cache will not be populated.
Defining and Updating UAC Source
In order to crawl Oracle E-Business Suite users in a source system, a special "User Authorization Cache" source type should be defined.
Creating UAC Source
For Oracle E-Business Suite which has seamless integration with Oracle SES, whenever any searchable object is deployed either from Oracle E-Business Suite or from Search Modeler for the first time, one source of "User Authorization Cache" type will be transparently created. This source will have the following information:
| Parameter Name | Value |
|---|---|
| Name | Oracle E-Business Suite UAC |
| Type | User Authorization Cache |
| User Search Query | " "
Note: Query expression defines the set of users to be crawled. For example, a* means to crawl all users whose names begin with the letter a, and null value (*) means to crawl all Oracle E-Business Suite users. The SES Administrator can enter comma separated user names in wild card format, for example, OPERATIONS, BPALMER, SYSADMIN*. The names entered will be preserved during successive deployment of objects. |
| Source names for which security attributes should be crawled | This parameter will have comma separated values of Sources already deployed. These source names will be automatically updated on deployment of objects. |
The above information lets Oracle SES know about the Oracle E-Business Suite "Sources" for a specific user for which the security keys need to be fetched. In other words, the UAC source maps users with the sources whose security keys need to be cached.
Updating UAC Source
Any searchable object deployed subsequently will automatically update the "Source names for which security attributes should be crawled" parameter value to include the name of the source currently being deployed.
Manually Updating UAC Source
However, in case a "User" crawl is in progress while such deployment is attempted, the update to the UAC source might fail. Therefore, a Search Administrator might have to manually add the source name later on.
To manually update the UAC source, log on to Oracle SES and select Sources tab. For Source Type, select "User Authorization Cache" and then click the Update icon. The Update User-Defined Source page is displayed allowing you to update the source information.
Managing the UAC Crawling Schedules
A Search Administrator needs to schedule the crawling job of "E-Business Suite UAC" source at a regular interval to fulfill your business needs.
How to set the crawling frequency and manage crawling schedules, see Administering Crawls in Oracle SES and Managing Crawling Schedules.
Administering Searchable Objects
Searchable objects are business objects that are made available for text search; they are used in an abstract way for exposing business data to search engines. For example, a purchase order as a searchable object would be defined as a set of searchable properties and its relationship to other searchable objects. Oracle E-Business Suite Secure Enterprise Search uses this abstraction concept to group objects in a logical way at runtime.
To secure all searchable objects containing sensitive application context only exposed to appropriate users before they are deployed to Oracle SES, and to effectively manage and administer data sources after the deployment, system administrator or search administrator needs to perform the following tasks:
-
Securing Searchable Objects Using Security Grants
Before deploying searchable objects to Oracle SES and making them available to users, these objects must be secured first. By leveraging the concept of the Role-Based Access Control (RBAC) security model, administrators can create security grants to ensure the application content sensitive data is only accessed by authorized people.
-
Deploying Searchable Objects to Oracle SES
Once searchable objects are ready to be deployed, the system administrator or search administrator can deploy them to the Oracle SES instance. Since not all searchable objects can be successfully deployed to Oracle SES, deployment guidelines and additional tasks are described in this section.
-
Administering Crawls in Oracle SES
Once searchable objects are deployed to the Oracle SES instance, the crawling schedules by default are automatically created in Oracle SES and visible in the Oracle E-Business Suite. The system administrator or search administrator must first manually edit the default schedules with desired crawling frequencies and start the initial crawl.
Securing Searchable Objects Using Security Grants
As soon as a searchable object is created and patched into Oracle E-Business Suite, it is crawlable in Oracle SES. To make it available for users to search without compromising the data integrity and content sensitivity, the security context must be constructed around the searchable object first. By leveraging the Role-Based Access Control (RBAC) security model, Oracle E-Business Suite Secure Enterprise Search provides a flexible solution that can easily embed application security into a full text search service, and this solution allows only authorized users with appropriate access privileges to search on or view applications data against a preindexed Oracle SES store.
For more information about the RBAC model and how to create security grants, see Role-Based Access Control (RBAC) Security.
Deploying Searchable Objects to Oracle SES
Once searchable objects are ready to be deployed to the Oracle SES instance that you set up earlier in the Configuration tab, the system administrator or search administrator can deploy a single object or deploy all objects simultaneously from a search.
The deployment process can create the following items in Oracle SES:
-
Create a data source for each deployed searchable object
-
Create a 'Oracle E-Business Suite Release 12' data source type associated with each data source
-
Create a schedule per data source
-
Create all source groups
This creation includes a source group per data source, and a source group per permission set.
Important: Once searchable objects are deployed to Oracle SES, default schedules for each searchable object are created automatically in Oracle SES, but they are set to have a manual launch for the initial crawl. A system administrator or search administrator must manually edit the default schedule by setting up crawling frequency through the use of the administrative page in Oracle SES and starting the initial crawl. Otherwise, the initial crawl will not be automatically started. For more information on setting up crawling frequency and starting an initial crawl, see Administering Crawls.
Please note that this synchronization process with an Oracle SES instance can only deploy the objects that have never been deployed to Oracle SES. Once they are deployed, any future deployment will not update the Oracle SES instance unless you manually delete the data source of the same name in Oracle SES and redeploy it again. Also, if you change the proxy user name and password, business objects that have already been crawled cannot be updated or resynchronized with the Oracle SES instance.
For more details on deployment, see Deployment Concepts and Guidelines in Oracle SES.
Deploying Searchable Objects
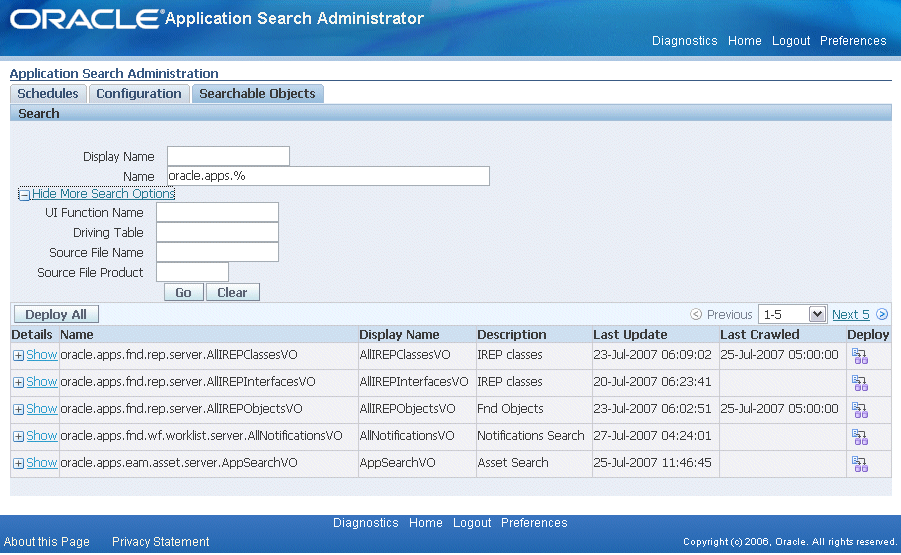
To deploy searchable objects:
-
Log on to Oracle E-Business Suite with the Application Search Administrator responsibility and select the Application Search Administration link from the Navigator window.
-
From the Application Search Administration window, select the Searchable Objects tab.
-
Enter simple search criteria in the Search region, such as Display Name and Name fields. Click Go to execute the search.
Optionally, click the Show More Search Options link to enter more search criteria, such as UI Function Name, Driving Table, Source File Name, and Source File Product fields.
-
From the search result table, you can choose one searchable object you want to deploy to an Oracle SES instance and click the Deploy icon for the object.
-
Click Deploy All to deploy all the objects from the result table.
Note: The selection of Deploy All is to deploy all the objects from the search result to an Oracle SES instance, and this would mean a reload of Oracle SES references.
-
Click the Show link for an object to view the object details. These details include the searchable object's properties information and detailed breakdown for each object member's attributes whether it is displayed, titled, indexed, stored, or secured.
Displaying Searchable Object Details
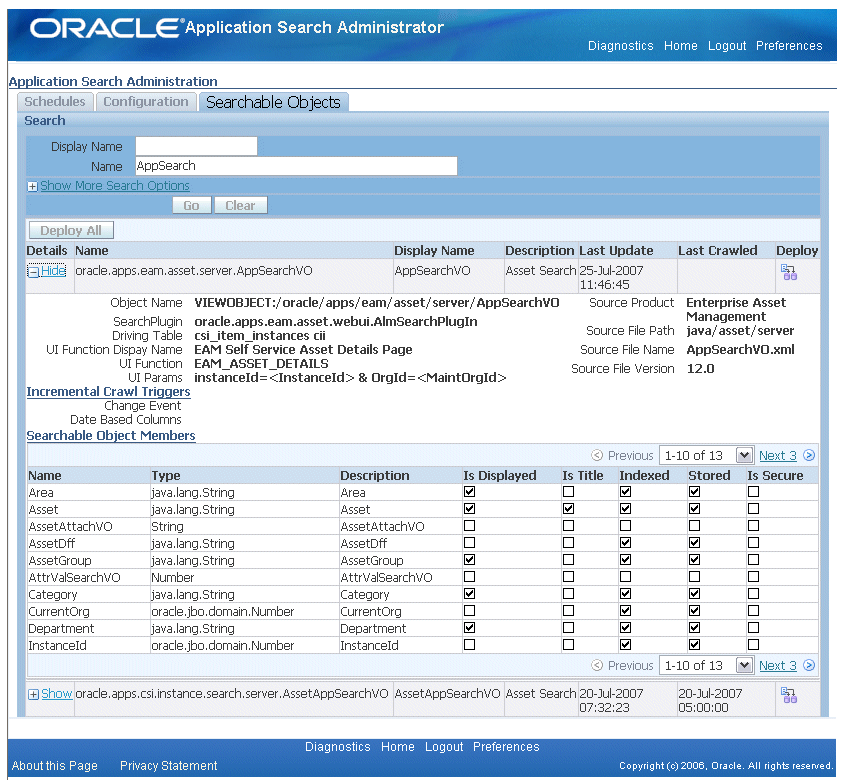
Click the Hide link to close the detailed view.
Deployment Concepts and Guidelines in Oracle SES
In addition to deploying searchable objects to an Oracle SES instance, the system administrator or search administrator must be aware of the following concepts and may need to perform additional tasks if necessary:
-
Data sources
-
Crawling schedules
-
Data source groups
Data Sources
A data source is one kind of data that you might want to search on. For example, if your data is in Web pages, then Web source is your data source. In other words, it is a particular end point where data can be retrieved. Each data source has a data type associated with it, such as Oracle E-Business Suite 12. Searchable objects contain many business attributes and these attributes can be retrieved and indexed for a given data source type during crawling.
Since the deploy process will only synchronize objects that they have never been deployed to an Oracle SES instance, if an object has been deployed, any future deployment for the same object will not update the instance unless you manually delete the data source of the same name in the instance and then deploy it again. Also, if you change the proxy user name and password, business objects that have already been crawled cannot be resynchronized with the Oracle SES instance.
Use the following guidelines to have searchable objects successfully deployed to the Oracle SES instance:
-
If a data source of the same name does not exist, create the data source with new parameters.
-
If a data source is created, you can only delete the data source if it is not crawled and create the data source with new parameters.
-
If a data source exists and has been crawled already, do not delete the source or create a new one. Instead, you need to manually update the data source parameters in the Oracle SES administrative pages and redeploy it from the E-Business Suite.
To access the Oracle SES administrative user interfaces, select the Configuration tab in the Applications Search Administration page. In the Tasks region, click the SES Admin Login link under the Additional Tasks section to navigate to the Oracle SES administrative user interfaces. In the Oracle SES instance, use the Home tab and the Source subtab to edit or create data sources. For more information on data source creation and parameters, see the Oracle Secure Enterprise Search Administrator's Guide for details.
Crawling Schedules for Searchable Objects
Once searchable objects are deployed to Oracle SES, default schedules for each searchable object are generated automatically in Oracle SES, but they are set to have manual launch the initial crawl. It is very important that system administrator or search administrator must manually edit the default schedule by setting up crawling frequency through the use of the administrative page in Oracle SES and starting the initial crawl. Otherwise, the initial crawl will never be automatically started. See: Administering Crawls in Oracle SES
During the data deployment process, if the data source gets created, the existing schedule will be deleted and a new one should be created. However, for a data source that has been crawled already, its schedule will not be recreated.
Data Source Groups
A data source group is a concept used in Oracle SES to group a number of crawled indexes for an aggregated search. For each searchable object, a default data source group is created with the same name which includes only the data source for this object.
To enable Oracle SES to perform searches on groups, all the groups that have been created in the E-Business Suite application instance should have corresponding source groups created in the Oracle SES instance as well.
For example, for each permission set that starts with SESG, a data source group will also be created and populated with Oracle SES references. The permissions included in the permission set that is linked to a searchable object will have their data sources included in the group.
For example, a permission set SESG_SEARCH_CRM includes the following permissions:
-
ServiceRequest permission (contains 'ServiceRequest' searchable object)
-
Customer permission (contains 'Customer' searchable object)
-
Contract permission (contains 'Contract' searchable object)
Oracle E-Business Suite Secure Enterprise Search uses this mechanism to allow an application user to perform text search in a searchable group and refine or narrow down the search result using the searchable objects contained in the group:
-
Each individual searchable object within the group SESG_SEARCH_CRM:
-
ServiceRequest
-
Customer
-
Contract
-
For more information on permission sets used in building security context, see Securing Searchable Objects Using Security Grants.
Administering Crawls in Oracle SES
Crawling schedules define the frequency at which the index is updated with information about each source. Once searchable objects are deployed to Oracle SES, crawling schedules are automatically created along with the data sources in Oracle SES and visible in the Oracle E-Business Suite. However, these automatically created crawling schedules have the crawling frequency type set to the default value 'Manual Launch' which requires you to manually start the initial crawl. Otherwise, these schedules will never be started automatically.
Note: The initial crawl refers to the first time a searchable object is crawled. Since it usually involves a large set of data, it is highly recommended that an initial crawling job should be scheduled by a low bandwidth job in non-peak hours.
To have fast performance on initial crawl, Oracle E-Business Suite Secure Enterprise Search uses the AD Parallel Update package to help split the large data set into smaller work units, and crawl the units in parallel by using the multi-thread crawling mechanism provided by Oracle SES.
If you want the source or index updated more frequently after the initial crawl is completed, you can update the crawling frequency for a schedule in the Edit Schedule page through the Oracle SES administrative UI.
Setting Crawling Frequency
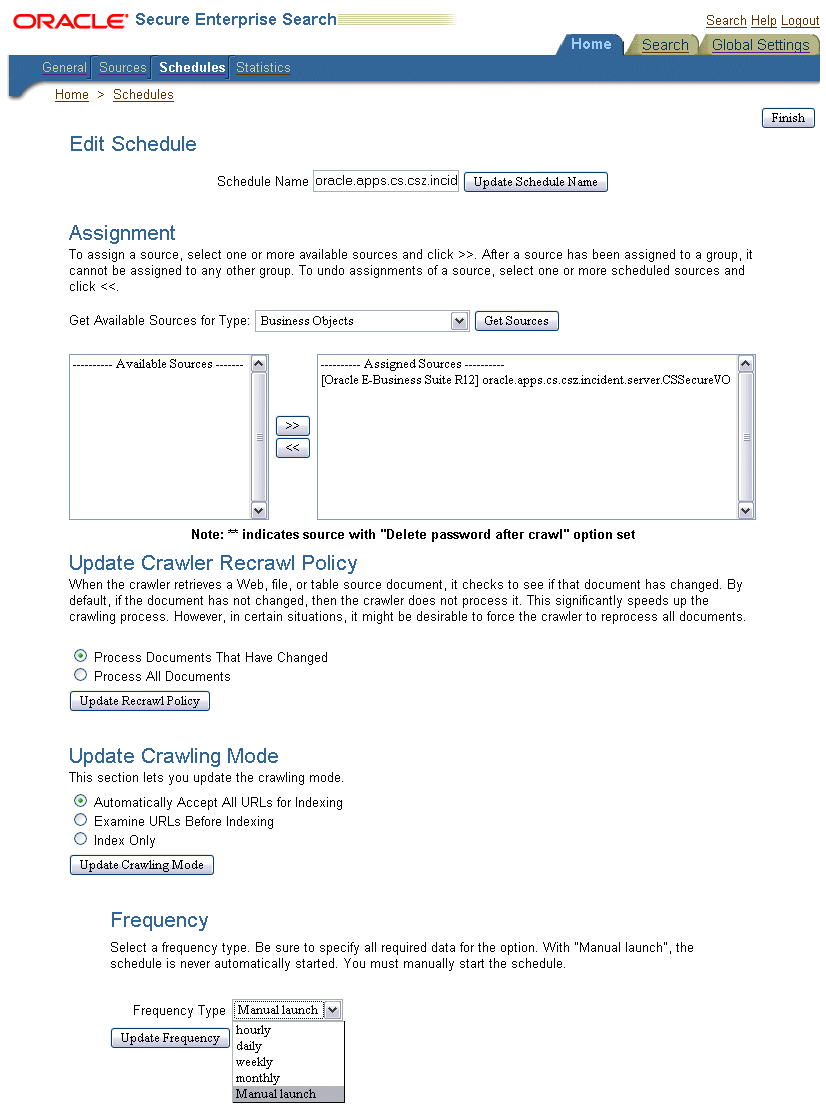
To set crawling frequency in Oracle SES administrative page from Oracle E-Business Suite Secure Enterprise Search:
-
Log on to Oracle E-Business Suite with the Applications Search Administrator responsibility.
-
Select the Configuration tab and click the SES Admin Login link from the Tasks region. This opens the Oracle SES login page.
-
Enter the user name and password you defined for an administrator in order to access an Oracle SES instance.
-
In Oracle SES, select the Home tab and Schedules subtab to access the Crawler Schedules page.
-
Select a schedule name and click the Edit icon to see the Edit Schedules page.
-
The selected schedule name is populated automatically in the Schedule Name field. You can select another schedule to update it if you want.
-
Leave the Assignment and Update Crawler Recrawl Policy regions unchanged with the default values.
-
In the Update Crawling Mode region, leave the Automatically Accept All URLs for Indexing radio button selected. This selection crawls and indexes all URLs in the source. It also extracts and indexes any links found in those URLs. If the URL has been crawled before, then it will be reindexed only if it has changed.
-
In the Frequency region, change the frequency type from the default 'Manual Launch' to daily, hourly, weekly, or monthly. Click Update Frequency.
-
Click Finish to save your changes.
Starting an Initial Crawl
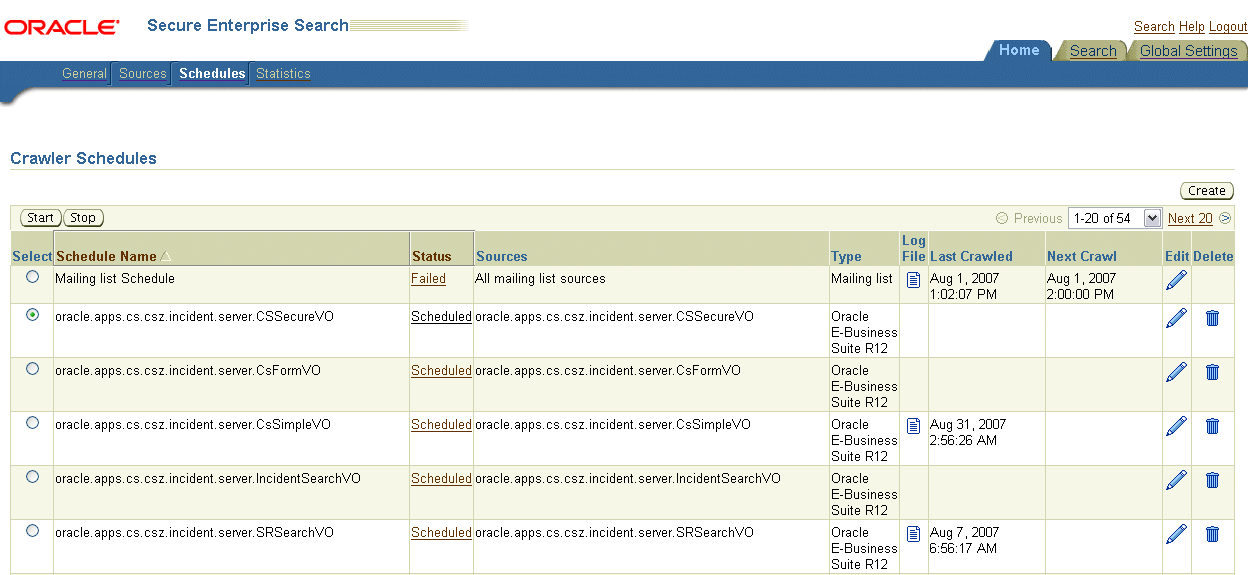
To start, stop, or delete a crawl in Oracle SES:
-
Log on to Oracle E-Business Suite with the Applications Search Administrator responsibility.
-
Select the Configuration tab and click the SES Admin Login link from the Tasks region. This opens the Oracle SES login page.
-
Enter the user name and password you defined for an administrator in order to access an Oracle SES instance.
-
In Oracle SES, select the Home tab and Schedules subtab to access the Crawler Schedules page.
-
Select a schedule name that you want to start the initial crawl and click Start. If you want to stop an existing crawl, select the schedule name and click Stop or click Delete to delete a schedule.
-
To update a schedule, select a schedule name and click Edit. See: To set crawling frequency in the Oracle SES administrative page from Oracle E-Business Suite Secure Enterprise Search.
-
To view a schedule status, click the link in the Status column, such as scheduled, disabled, launching, or failed, to see the schedule details.
-
Click the Log File icon to see detailed crawler settings and status.
-
Click Create to manually create a new schedule.
For more information on managing crawling schedules in Oracle SES, see the Oracle Secure Enterprise Search Administrator's Guide for details.
Testing Oracle E-Business Suite Secure Enterprise Search Setups
Use the following sections to validate whether you have successfully set up the Oracle E-Business Suite Secure Enterprise Search:
Validating General Setups
Use the following steps to validate general setups in Oracle E-Business Suite Secure Enterprise Search:
-
Test whether you have set the FND: Search Enabling Flag profile value to Yes. If it is not set to Yes, crawling should be disabled.
-
Assign the FND Search Crawler (SES_SEARCH_CRAWLER) responsibility and Application Search Administrator responsibility to a system administrator or search administrator. This administrator must be a valid FND user used as a proxy user for query.
-
Ensure you have set the correct value for the proxy parameters. To verify, log on to Oracle E-Business Suite with the Application Search Administrator responsibility, and select Configuration tab to view your setup parameters.
Use the Update check box to reset SES admin proxy and query proxy. For example, set SES admin proxy with user name egsys and password Oracle10g; query proxy with user name sysadmin and password welcome. The query user name must be a valid FND user with FND Search Crawler responsibility.
Important: Once you change the query proxy parameters, the SES instance needs to be restarted to reflect the changes.
Testing Deployment
Use the following steps to test whether you can deploy an object:
-
Log on to Oracle E-Business Suite with the Application Search Administrator responsibility.
-
Select the Searchable Objects tab and search for the object that you want to deploy.
-
Select the object to be deployed and click the Deploy icon.
Testing Schedules
Once searchable objects are deployed to the Oracle SES instance, you should be able to find their corresponding schedules automatically created in Oracle SES. Use the Oracle SES instance to start the crawling schedules.
Use the following steps to test crawling schedules whether they work properly:
-
Log on to the Oracle SES administrative page through the Configuration tab in the Application Search Administration page.
-
Select the Home tab and Schedules subtab. Refresh the page and you should be able to see the schedule for object you just deployed.
-
Select the schedule and click Start to observe the schedule status change for the selected schedule. Refresh the page if necessary to view the status updates.
Testing Searches
Once the setup tasks are completed, application users with appropriate privileges should be able to perform searches within the Oracle E-Business Suite.
Use the following steps to perform searches:
-
From the home page of the Oracle E-Business Suite, select a searchable group form the search drop-down list.
-
Enter a keyword in the text field, such as 'oracle' and click Go.
You should be able to find the search results populated in the results region.
Additional Administrative Tasks
In addition to setting up necessary tasks for Oracle E-Business Suite Secure Enterprise Search to ensure its seamless integration with Oracle SES, and performing administrative tasks to secure and deploy searchable objects, the system administrator and search administrator also need to perform the following tasks to proactively manage crawling schedules and optimize indexes:
Managing Crawling Schedules
Once searchable objects are deployed, crawling schedules are automatically created along with data sources in Oracle SES. After an initial crawl is completed, subsequent incremental crawls are scheduled and can be executed automatically triggered by business events, date changes, or crawling frequency, as well as other necessary manual crawls.
When a crawling job starts, each crawler retrieves business objects of a given type and then pushes the retrieved objects to be indexed by Oracle SES indexers. Finally, these objects with indexes are stored in the Oracle SES index store for user queries.
For example, a searchable object, such as a purchase order, may have source data from a number of tables (views), such as product description, employee e-mail address, and so on. When these fields change, the last updated date for the purchase order is also updated. In this way, when a scheduled crawl is performed, the purchase order gets reindexed and stored in the Oracle SES index store.
Oracle E-Business Suite Secure Enterprise Search allows the administrator to proactively manage the crawling schedules in the following ways:
-
View the latest crawling status, last crawled, and next crawling schedule for a given schedule
-
Stop a manual crawling job
-
Recrawl all the data for a selected schedule
-
Create an incrementally crawling job for a selected schedule once the initial crawling is completed
-
The initial crawl refers to the first time a searchable object is crawled. Since it usually involves a large set of data, it is highly recommended that an initial crawling job should be scheduled by a low bandwidth job in non-peak hours.
To have fast performance on initial crawl, Oracle E-Business Suite Secure Enterprise Search uses the AD Parallel Update package to help split the large data set into smaller work units, and crawl the units in parallel by using the multi-thread crawling mechanism provided by Oracle SES.
-
The incremental crawl refers to crawling the data to the original data source after the initial crawl.
-
Managing Crawling Schedules
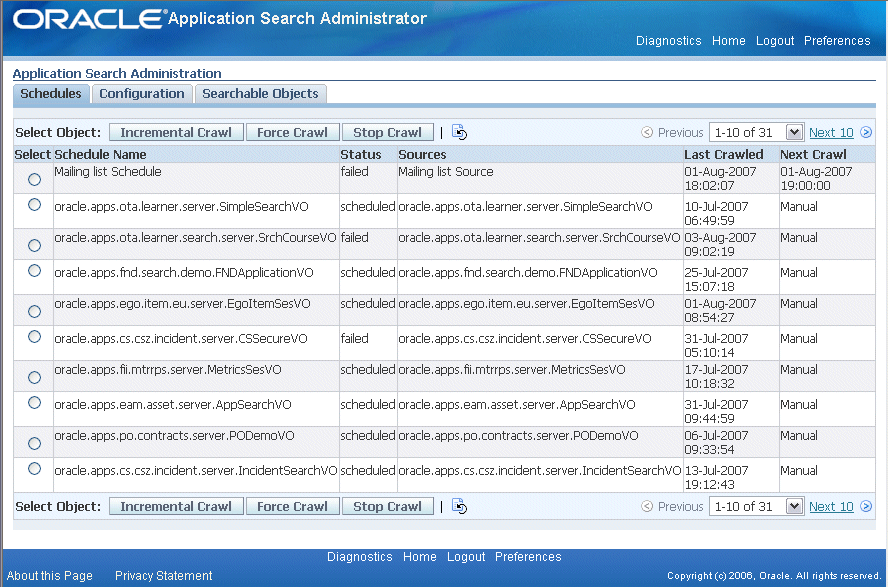
To manage crawling schedules:
-
Log on to Oracle E-Business Suite with the Application Search Administrator responsibility and select the Application Search Administration link from the Navigator window.
-
From the Application Search Administration window, select the Schedules tab.
-
From the Schedules page, you can view the crawling details for a given schedule including schedule name, crawling status, source, last crawled, and next crawling schedule.
-
To view the latest schedule details, click the Refresh Crawler Schedules icon to get the schedule refreshed.
-
To create incremental crawling schedules, select a schedule name by clicking the Select radio button and click Incremental Crawl to have the next crawling schedule created in the Next Crawl field.
Incremental crawling can be raised by a business event or a date change to a searchable object since the last time it was crawled.
-
To stop an existing crawling job, after selecting a schedule name, click Stop Crawl to stop the crawling job for the selected schedule.
-
To recrawl all the data for a selected schedule, click Force Crawl.
Optimizing Indexes
Crawlers maintain active indexes of all documents crawled over all sources. To reduce fragmentation from crawls and increase the speed of searches, the administrator needs to create schedules for optimizing indexes through the Oracle SES administrative pages.
Oracle E-Business Suite Secure Enterprise Search also facilitates the index optimization performed in Oracle SES through a request.
Optimzing Indexes
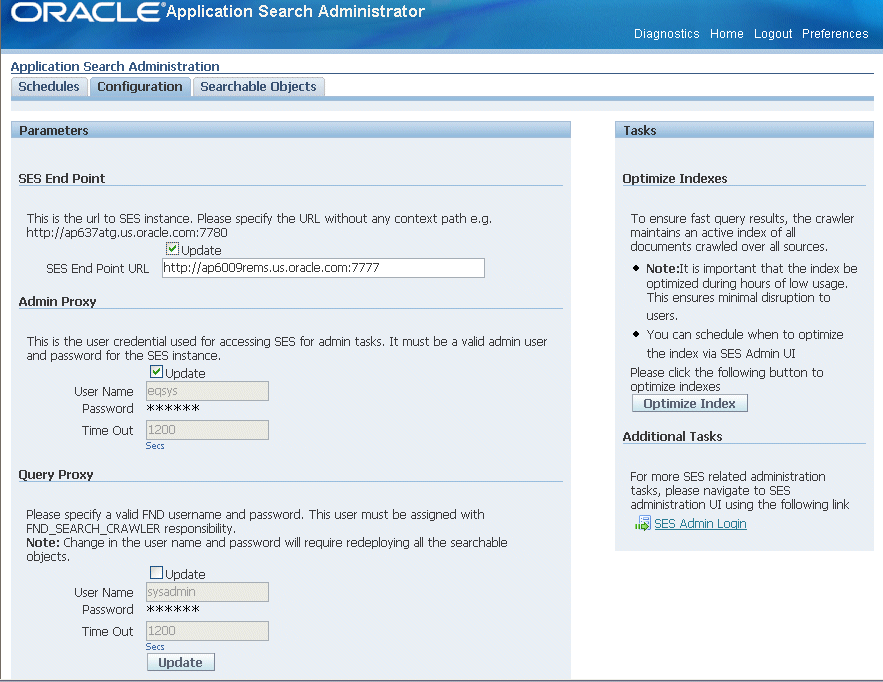
To optimize indexes:
-
Log on to Oracle E-Business Suite with the Application Search Administrator responsibility and select the Application Search Administration link from the Navigator window.
-
From the Application Search Administration window, select the Configuration tab.
-
Click Optimize Index in the Optimize Indexes section. This raises an optimization request to Oracle SES and the indexes get optimized.
Important: In order to have minimal disruption to users, it is highly recommended that the index optimization should be done during hours of low usage.
For more information on optimizing indexes in Oracle SES, see the Oracle Secure Enterprise Search Administrator's Guide for details.
Error Messages
The following is a list of seeded error messages that Oracle E-Business Suite Secure Enterprise Search uses to notify or alert users when violations occur in interacting with the Oracle SES engine or during query:
| Error Message Code | Description |
|---|---|
| FND_SEARCH_SECURITY | This message occurs when security rules are violated by a query. The query module will terminate the process and throw security exception along with this message. Parameters in this message might include current FND user name. User-specified filters in a secured attribute is a security error. For example, you can enter keyword "oracle" to query. However, if you query on "EMP_ID:dlam content:oracle", an error message is returned because 'EMP_ID' is a secured attribute. |
| FND_SEARCH_TOO_MANY_ENTRIES | This message occurs when the query engine is to perform a post-query row-by-row process and there were too many rows. The query engine might perform some heuristic actions or throw an exception to the API user. |
| FND_SEARCH_SYNTAX_ERROR | This message occurs when the query syntax does not conform with Oracle SES. The query engine might rewrite the query. |
| FND_SEARCH_SES_ERROR | This message relays any potential error originating from Oracle SES when Oracle E-Business Suite Secure Enterprise Search interacts with the Oracle SES engine. |
The following table lists the error message type for the types of errors that occur during the integration with Oracle SES engine or query:
| Error Message Type | Description |
|---|---|
| FND_SEARCH_0001 | Indicates search engine general errors. |
| FND_SEARCH_0002 | Indicates security errors. |
| FND_SEARCH_0003 | Indicates crawl time errors. |
| FND_SEARCH_0004 | Indicates metadata errors. |
| FND_SEARCH_0005 | Indicates query errors. |