Security Rules
Security Overview
Defining which records and information users can access is fundamental to HRMS security.
As part of your implementation plan, you identify who will use Oracle HRMS, what information they require, and how they use it. You can control a user's access to database elements such as records, fields, forms, and functions, and you can also control a user's access to other user records and data.
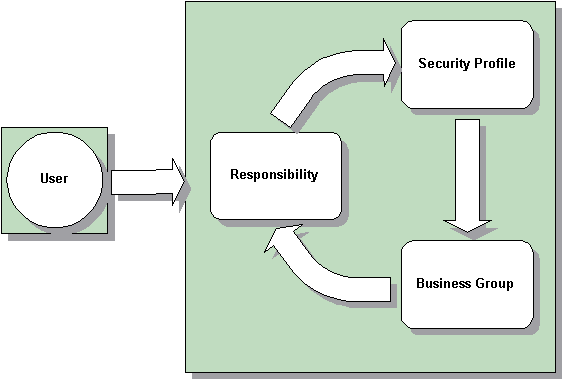
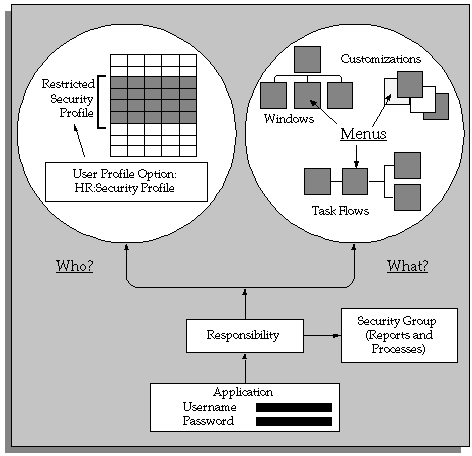
All Oracle Applications users access the system through a responsibility that is linked to a security group and a security profile. The responsibility is the primary means of defining security. The security group determines which business group the user can access. The security profile determines which records (related to organizations, positions and payrolls) the user can access within the business group. For example, you can restrict a manager's security permissions so that the manager can only access the person records for those employees and workers within a supervisor hierarchy. This restriction enables secure, reliable data access and ensures that only people with the correct permissions can access personal data.
See: Responsibilities
Security and Business Groups
In general, a user can only view the records for one business group at a time. However, depending on the value of the HR:Cross Business Group Profile option, you can view specific information across business groups. See: User Profiles
See also: Single and Multiple Business Groups, Oracle HRMS Enterprise and Workforce Management Guide
Within a business group you can control:
-
Who the user can access, using security profiles. You can restrict access by:
-
organization hierarchy
-
position hierarchy
-
supervisor hierarchy
-
payroll
-
supervisor assignment
You can also restrict access to specific person types, for example, employees, applicants, contingent workers, and, if you are using iRecruitment, candidates.
You can also create your own custom restrictions and combine them with the standard restrictions.
Note: You can configure the above security restrictions to be user-based. The application evaluates the security permissions dynamically for the user currently logged on to the system. User-based security profiles can be used by multiple employees which reduces set-up and administration tasks.
-
-
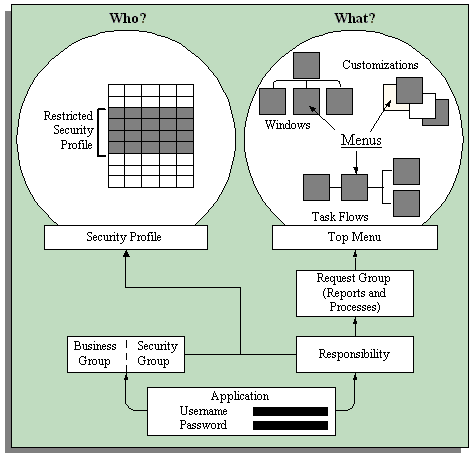
What the user can access. You control user access to specific functions using function security. You attach functions to menus which you then attach to responsibilities. By linking the functions to responsibilities, you can restrict which users can access particular functions, and on which menus the functions appear. By modifying the function parameter information, you can define how the function operates and processes information.
See: Menus
Key Concepts
For more detailed information on security concepts, see:
Security
You can set up and maintain security of access for different classes of users. Once you have identified who will use Oracle HRMS, what information they require, and how they will use it, you can group together users with similar requirements and give them the same view of the system.
In what ways can you use Security of access for different users?
You can set up menus using structures and names that make sense to the users. You can also restrict the data users can view and edit in certain windows, so they only see what they need to see.
This provides security for your data and an efficient interface designed for your users' needs.
How does Oracle HRMS allow data restriction for display in a window?
If you want different users to view the same window for different purposes, you can restrict their views in different ways. For example:
-
Limit access to list of values for faster data entry
-
Limit access to certain types of information
For example, you might create a customized version of the View Element Entry History for Employee form that does not display the birth date or citizenship in compliance with EEO regulations. Most users' menus would only give them access to this customized version of the form. Those personnelist authorized to view salary, bonus, and commission figures, would have a menu function defined to allow access to the uncustomized form.
How does Oracle HRMS enable users to view multiple Business Groups?
Oracle HRMS is installed with two security models, each enabling you to set up security for an enterprise which uses multiple Business Groups. Using both models you can only view records for one business group at any one time, except in cases where the HR:Cross Business Group user profile allows access to specific fields across all Business Groups. The difference between the models is as follows:
-
Using Standard HRMS security yyou can only link one business group to one responsibility. You must set up different responsibilities for each business group.
-
Using Security Groups Enabled security you can set up more than one business group for a single responsibility. However, you still only view records for one business group at a time.
How does the application restrict access to workflow transactions?
The workflow role you assign an employee and that person's assignment to routing groups and routing lists limit the workflow activities he or she may perform, such as initiating or approving a Request for Personnel Action or Position Description (PD).
Workflow security prevents a form from being routed outside of its routing group. The application also maintains a complete tracking history of an RPA or PD during the routing process.
Security in Oracle HRMS
Key Concepts
The following definitions describe the key concepts in Oracle HRMS security.
Menu Structures
Using menu structures, you can limit the functions a user can access. You can also restrict access to information types by choosing which information types a user can view.
You can also create multiple versions of the same form, each one used for just one task. This approach restricts the list of values on certain fields and therefore provides for faster data entry. It also enables you to limit access to certain types of information.
Reporting Access
You can set up access restrictions for employees who never use the product's windows and do not change database information, but do access the database.
Request Groups
You can specify which processes and reports a reporting user can run by setting up request groups. Within the request group, you use security profiles to restrict the records accessed by the reporting user, who may run reports against the system without having online access through the system's forms.
Responsibility
The responsibility is your primary means of defining security. Business groups, menu structures, task flows, and information types are linked to a responsibility.
Security Groups
Security groups are a method of partitioning data. If you are using the Security Groups Enabled security model, you can manage information for multiple business groups using one responsibility. This is particularly useful if you are a Service Center. Security Groups Enabled security is also useful for organizations using Oracle Self Service HR and organizations with employees that must access and manage records from different business groups.
Security Models
The two security models, Standard HRMS Security (Security Groups Disabled) and Security Groups Enabled security (formerly called Cross Business Group Responsibility Security), both control security by restricting who and what the user can see. What differs is how you set up security, menus and how users log in. For more detailed information about each of the security models, see Security Models.
Security Processes
System security processes enable you to:
-
Grant permissions to a new reporting user.
-
Maintain the lists of organizations, positions, payrolls, employees and applicants that security profile holders can access.
-
Set up and update your system to use the Security Groups Enabled security model.
Security Profiles
By defining security profiles, you can control access to records of employees at or above a certain level in an organization. For example, you can give a department's administrator access to all department employee records except those of the manager and assistant manager.
User Profiles
A user profile is a set of changeable options that affects the way your application runs. You can set user profile options at site level, application level, responsibility level and user level.
You can restrict access to query-only for all or a selection of your HR and Payroll forms using a user profile option and the parameter QUERY_ONLY=YES at form function level.
Security Models
Oracle HRMS provides two different security models which enable you to set up security specifically for your enterprise: Standard HRMS security and Security Groups Enabled security (formerly called Cross Business Group Responsibility Security).
Note: If you want to set up security for employees who can access the database, but do not change database information, see: Reporting Access and Setting Up Reporting Users.
A further option exists which enables users to simultaneously view selected fields from all business groups in your organization regardless of the security model. For more information see HR: Cross Business Group Profile option.
Standard Security Model
Standard HRMS security restricts access to your enterprise's records and data. To set up Standard HRMS Security, you first create responsibilities and then define the windows, menus items, workflows, data and records the user can access. The System Administrator then assigns users to as many of these responsibilities as is required to complete their business tasks.
If you are using Standard HRMS Security, you must ensure that the Enable Multiple Security Groups profile option is set to the default value No. You must then create a security profile for each distinct security grouping of employees your enterprise requires.
You then create a responsibility for each user type you require, for example HR Manager, Branch Manager and Salesperson, and link the security profile and responsibility to a business group. These three elements create a security grouping to which you assign employees.
Assigning Users to a Responsibility, Security Profile, and Business Group
Note: Each security grouping you create restricts access to the business group to which the security profile and responsibility are assigned.
By assigning users to the security grouping, you grant them access to the records, menus and data defined in the security profile and responsibility. You can add further users to this security component, but you cannot re-use the security profile and responsibility within another business group.
Your enterprise can also set up request groups to restrict user access to reports and processes. The request group is associated with a security profile which defines the data a user can view, and is then assigned to a responsibility. It is also possible to set up reporting only request groups for users who access the database, but who are not permitted to change any of the records within the system.
For more information, see Setting up Standard Security.
Access to Multiple Business Groups using Standard Security
In Standard HRMS Security, you can grant users access to more than one business group within your enterprise. To do this, you must create security profiles and responsibilities and assign them to each additional business group. If a user's responsibility is assigned to more than one business group, they will not be able to view data from more than one business group at any time.
Note: The HR: Cross Business Group Profile option enables users to view some limited information across all business groups within an enterprise. For more information, see HR: Cross Business Group Profile option.
Standard HRMS Security (Security Groups Disabled) is commonly used in organizations which operate within a single legislation and a single business group.
Important: After setting up Standard HRMS Security, you can switch to the Security Groups Enabled security model. You cannot, however, to revert back to Standard HRMS Security after this change has been made.
The Completed Standard HRMS Security Model
Security Groups Enabled Model
The main difference between the two security models is that the Security Groups Enabled model enables your enterprise to share security profiles and responsibilities between users and business groups. This reduces the set up time, and also increases the flexibility of this security model. The key to re-usability is the relationship between the security elements and the users that you create during the set up process.
Important: Once you have set up Security Groups Enabled security, you cannot revert to Standard HRMS Security.
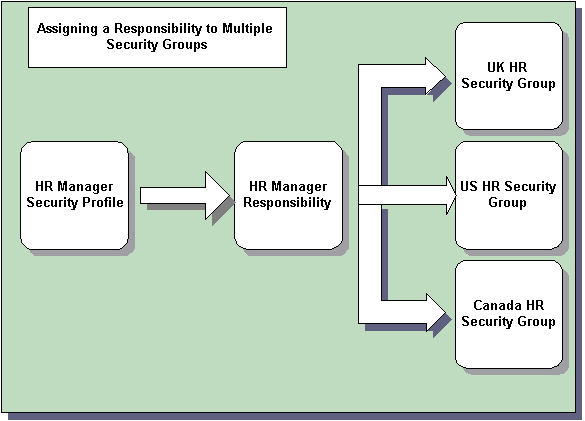
Access to Multiple Security Groups using Security Groups Enabled Model
The Security Groups Enabled security model enables you to assign a single responsibility to more than one business group, and hence enable users to access records from numerous business groups, although users cannot view information from different business groups simultaneously.
To set up Security Groups Enabled security, you set the Enable Security Groups Profile option to Yes, and run the Enable Multiple Security Groups process. These steps in combination create a Security Group which has the same name as the business group from which it was created. For more information, see Security Groups, Oracle HRMS Configuring, Reporting, and System Administration Guide.
Note: To make the administration of your security setup easy to maintain, it is recommended that you leave the names of the Security Groups the same as your business groups.
Like Standard HRMS Security, your enterprise must create Security Profiles for each distinct security grouping within your enterprise. Security Profiles function slightly differently in the Security Groups Enabled model than they do in Standard HRMS security. Rather than one security profile being assigned to one responsibility, Security Groups Enabled security enables your enterprise to assign numerous security profiles to a responsibility. For example, an HR Manager and an Assistant HR Manager may be able to access the same menus and windows, but may be able to view different data. The following example illustrates the benefits of this function.
Assigning Multiple Security Profiles to a Responsibility
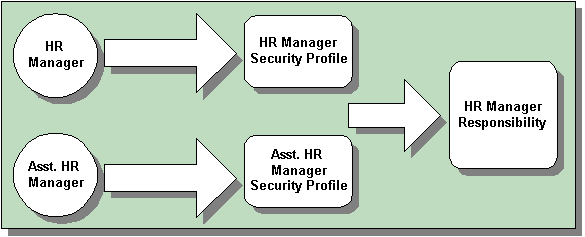
Note: The limitation of this is that a user can only be assigned one Security Profile per responsibility.
The functionality of responsibilities is also enhanced in the Security Groups Enabled security model. Increasingly, users require access to the records in more than one business group. To accomplish this, you can assign a responsibility to multiple business groups when you use Security Groups Enabled. The records, forms and type of data a user can access will be the same in each of the business groups to which they have access.
Note: When a responsibility is assigned to more than one business group, the user can only view records from one business group at any time.
The ability to assign one responsibility to multiple business groups makes the set up of security quicker and more efficient.
Note: The HR: Cross Business Group Profile Option enables users to view some information across all business groups within an enterprise. For more information, see HR: Cross Business Group Profile option.
Assigning a Responsibility to Multiple Security Groups
As with Standard HRMS Security, you can set up a request group to restrict user access to reports and processes. The request group is associated with a responsibility which defines the data a user can view. It is also possible to set up reporting only request groups for users who access the database, but who are not permitted to change any of the records within the system.
Once your enterprise has defined the security profiles and responsibilities, you must assign them to the relevant security groups. The final stage is to assign users to this group of information. The example below illustrates how the final security set up may look within your enterprise.
For more information see Setting Up Security Groups Enabled Security.
The Completed Security Groups Enabled Model
Three distinct enterprise types can benefit from the functionality offered by the Security Groups Enabled model; Service Centers, Multinationals and SSHR enterprises. Of course, the simplified set up and maintenance is of benefit to any enterprise.
Typically, Service Centers create a new business group for each customer they serve. Furthermore, Service Centers only require one responsibility and security profile to enable users to access and change data within the system. As the Security Groups Enabled model enables sharing of security profiles and responsibilities, the security set up process for Service Centers becomes quicker and more efficient.
In the case of Multinational enterprises, it is common to create a business group for each country in which the enterprise operates, and for each legislation the enterprise uses. Using the Security Groups Enabled model enables users to share records and data across business groups and countries.
For enterprises that use SSHR within a global implementation, the advantages of using Security Groups Enabled include quicker set up and easier maintenance. An additional benefit is that transferring employees or employee information between business groups is simplified.
Security Groups (Security Groups Enabled Model Only)
When you use the Security Groups Enabled security model (formerly called Cross Business Group Responsibility security), a security group is automatically created for each business group when you run the Enable Multiple Security Group Process. Because security groups are tied to business groups by set up, partitioning data using this method is the same as partitioning data by business group. See: Setting Up Security Groups Enabled security.
Important: Security groups are only used if you have set up your enterprise using the Security Groups Enabled security model.
Security groups are the key component in Security Groups Enabled security. They enable you to set up one responsibility and link this to a number of different business groups.
Before you can start using this security model you ensure that HRMS is set up to use security groups. To do this you set the Enable Security Groups profile option to Yes and run the Enable Multiple Security Group process.
Important: You can change from Standard HRMS security to Security Groups Enabled security, however, you cannot switch from Security Groups Enabled security back to Standard HRMS security. See: Updating the Security Model.
Once you have set up your enterprise to use security groups, Oracle HRMS automatically creates a security group when you set up a business group. The security group has the same name as the business group. For example, if you create a business group called UK Headquarters, Oracle HRMS automatically creates a security group called UK Headquarters. The Setup Business Group, however, uses the predefined security group Standard.
Note: If you change the name of your business group, the security group name is not updated. To make the maintenance of your security setup easier, Oracle recommends that you leave the names of the security groups the same as the business groups from which they are created.
Using the Assign Security Profile window you link the user, responsibility and business group to a security profile. By entering a business group you are automatically linking the responsibility to the security group.
You then log on using the responsibility and security group pairing. As security groups are automatically linked to a business group, you can then view and manage the records for that business group.
When you log on, Oracle HRMS displays all the pairings you have created between business groups and responsibilities. You could have the same responsibility listed twice with different security groups and therefore business groups. By looking at the security group you can select the correct responsibility for the business group you want to access.
To ensure the integrity of your business data, you can only view records for one business group at any time. To view records from a different business group you must switch to an alternative responsibility and business group pairing.
Important: Security groups are automatically created for you when you use Oracle HRMS. Do not use the System Administrator's Security Groups window to add security groups as these will not be linked to your business groups.
End-Dating Unwanted Responsibilities
When you first enable security groups and run the Enable Multiple Security Groups concurrent process, the process creates two sets of records for existing user/responsibility pairs:
-
For each responsibility connected to a user it creates a record linking the user, the responsibility and the Standard security group.
-
For each HRMS responsibility connected to a user it creates a record linking the user, the responsibility, the security group associated with the business group, and the security profile.
If you are updating from Standard security, there may be many such records. For each existing user responsibility with a security group value of 'Standard', you need to decide whether or not the user requires access to the responsibility. Users who may need to update global lookup codes need access to the Standard security group.
In most cases, users will not require access to the Standard security group. In this case, enter an end date to remove access to the responsibility. This reduces the number of responsibilities the user sees on logging in, and prevents users from accidentally entering data into the wrong business group.
Note: By default, the Standard security group is associated with the Setup business group.
Example
For example, if your user is set up with a responsibility called US Federal HQ, you could link this to:
-
East Region Processing (Business Group)
-
Operations Manager (Security Profile)
Using the same responsibility (US Federal HQ), you could also link to a different Business Group:
-
West Region Processing (Business Group)
-
Services Manager (Security Profile)
Therefore, using just one responsibility (US Federal HQ), you can access two Business Groups (East and West Region Processing).
When the Business Group East Region Processing was set up, a security group East Region Processing would automatically have been created. When you linked the Business Group to the user's responsibility, the security group East Region Processing would also be linked.
To view the records for Business Group East Region Processing you would select the US Federal HQ responsibility and the East Region Processing security group.
If you then wanted to view the records for the West Region Processing Business Group you would switch responsibility and security group pairing, selecting the same responsibility (US Federal HQ) and the different security group West Region Processing.
Categorizing Information By Security Groups
Warning: You can only categorize information by security groups if you are using Security Groups Enabled security.
You can categorize the following information within your enterprise using security groups:
-
Lookups
Using the Application Utilities Lookups window you can set up lookups specifically for a security group. These lookups are only available to users who access the business group associated with the security group.
-
Concurrent Programs
Using the Concurrent Parameters Program window you can enter a security group against a concurrent program, this creates a specific list of concurrent programs for a security group and therefore business group. When a user selects a concurrent program using the Submit Request window, they can select from the concurrent programs for their business group.
Note: You do not have to enter a security group against all the concurrent programs. Concurrent programs which are not linked to a security group display for all security groups/business groups.
See: Concurrent Parameters Program window, Oracle Applications System's Administrator's Guide.
Secure User View Support for Oracle US Federal HR
The application supports secure user view and cross-business group functionality for the following:
-
RPA and NPA Reports
See:Printing RPA, Oracle HRMS Workforce Sourcing, Deployment, and Talent Management Guide, Printing NPA, Oracle HRMS Workforce Sourcing, Deployment, and Talent Management Guide
-
Mass Actions
See: Mass Action Overview, Oracle HRMS Workforce Sourcing, Deployment, and Talent Management Guide
-
Position Descriptions
See: Position Description Classification Overview, Oracle HRMS Enterprise and Workforce Management Guide
-
Future Dated RPAs concurrent process
See: Processing Future Actions, Oracle HRMS Workforce Sourcing, Deployment, and Talent Management Guide
-
Central Personnel Data File (CPDF) reports, including CPDF Dynamics, Status, and OCT reports as well as the Monthly Report of Federal Civilian Employment (SF-113A) report.
See: Central Personnel Data File Report, Oracle HRMS Enterprise and Workforce Management Guide, Standard Form 113-A Monthly Report of Federal Civilian Employment, Oracle HRMS Enterprise and Workforce Management Guide
The responsibility you choose at login determines what information you can view and update and what reports and processes you can run. If your login's responsibility and associated business group has a security profile assigned to it (a secure view), the application filters the information.
For example, when you create a mass action, the application filters the Selection Criteria list of values for organizations, positions, and hierarchies. It also filters the information that can be displayed and updated in the Preview window and for the Final execution.
Additionally, when you save a mass action or position description, the application stores the business group ID attached to your login's responsibility. From then on, only users with the same business group ID can access and retrieve the mass action, and run reports and processes for it.
Use the following guidelines when choosing a responsibility. Choose:
-
Secure view responsibility to access and update mass actions and position descriptions, and to run only processes and reports created in that secure view responsibility
-
Non-secure responsibility to access and update mass actions and position descriptions, and to run all processes and reports
Cross business group
If you have cross-business group functionality set up, the application includes the values for all business groups. If you are running reports or concurrent processes, the processes or reports run across all business groups. If you do not have cross-business group functionality set up, the application bases your lists of values and access to reports and processes on your current login's business group and your associated secure view.
Reporting Access
Oracle HRMS enables you to set up reporting users who can query and report on the information in the database, but cannot insert, update or delete information. Reporting users can use Oracle tools, or other tools connected to the Oracle database, to report on information. Regardless of the tools used to access the database, reporting users can only read information, they cannot update information.
Using Oracle HRMS you can set up similar security restrictions to users who can update, insert or delete information. This ensures reporting users can only query and report on appropriate records.
All secure users connect to the APPS ORACLE ID. This is created when the system is installed. However, for reporting users, you should create one or more new reporting user ORACLE IDs. By associating these with a restricted security profile you can control whose records a reporting user can access.
You can make any of your restricted security profiles available not only for regular users, but also for reporting users. The security profile restricts a reporting user's access to employee records in exactly the same way as it limits regular users' access.
Reporting users can see all the details about the records they can access. To restrict the access of what a reporting user can view you must use view-based accesses. To support this need of reporting users you can use third party reporting tools to create business views.
For information about how to set up database access without on-line access, see: Setting Up Reporting Users.
Security Processes
There are four system security processes:
-
Enable Multiple Security Groups
Run this process when you first set up Security Groups Enabled security.
-
Generate Secure User
Run this process when you create a new security profile that references a reporting user.
-
Security List Maintenance
Run this process every night.
You run these processes using an HRMS responsibility from the Submit Request window.
-
Grant Permissions to Roles
This process is run automatically as part of the autoinstall process.
Enable Multiple Security Groups Process (HRSECGRP)
You must run the Enable Multiple Security Groups process if you set the Enable Security Groups profile option to Yes. This process must be run when:
-
You set up Security Groups Enabled security for the first time to enable HRMS to use multiple security group features.
-
You change from Standard HRMS security to Security Groups Enabled security. This ensures that all your existing business groups have security groups and all the multiple security group features are enabled.
Note: To avoid errors when running the Enable Multiple Security Groups process, make sure that you set the Enable Security Groups profile option to Yes at the Application level.
Generate Secure User Process (SECGEN)
This process grants permissions to new reporting users. It grants the "hr_reporting_user" role to the REPORTING_ORACLE_USERNAME specified in the security profile.
Run this process when you have created a new security profile that references a reporting user. In the Submit Requests window, select the name of the new security profile. This is the only parameter for the process.
Security List Maintenance Process (PERSLM)
This process maintains the lists of organizations, positions, employees, contingent workers and applicants that security profile holders can access. You should schedule it to run every night to take account of changes made during the day to security profiles, organization and position structures, and person records. If a disruption, such as a power cut, occurs while the process is running, you can manually restart it from the Submit Request window.
Note: The PERSLM process replaces the earlier LISTGEN and GLISTGEN processes.
See also Running the Security List Maintenance Process
Important: The Security List Maintenance process should normally run when there are no users logged on to the system. Users attached while this process is running may experience unexpected results; for example, additional employees may become visible or previously visible employees may disappear from view.
Grant Permissions To Roles Process (ROLEGEN)
All reporting users in the system share access to a set of public synonyms for tables and views. Reporting users are granted permissions to make them usable. The Grant Permissions To Roles process creates these public synonyms and grants permissions to them.
Important: The Grant Permissions to Roles process is unrelated to setting up workflow roles for Oracle products that support security by workflow.
This process runs automatically as part of the autoinstall process when you install HR, or when you upgrade the system.
The process creates public synonyms for each of the required HR objects and then grants SELECT permissions to the role 'hr_reporting_user'. Permissions are not granted on the secured tables, but only on the secure views of those tables. All permissions previously granted to the role are revoked before the new grants are made. This ensures that the correct grants exist for the valid HR objects.
Setting Up Standard HRMS Security
Use the following setup steps if your enterprise sets up a different responsibility for each business group.
To set up users for Standard HRMS security:
-
Ensure that the Enable Security Groups profile option is set to No at site and application level, using the System Profile Values window.
If this option is set to Yes then you are not using Standard HRMS security.
See: System Profile Values, Oracle Applications System Administrator's Guide.
-
Note: For each restricted security profile you create that references a reporting user, you must run the Generate Secure User (SECGEN) process. This is a one-off process that is not required for view-all security profiles.
-
Ensure that the required functions or menus are set up.
This is required for the responsibility. For menu functions calling configured forms or task flows, you must enter a parameter in the Parameter field of the Form Functions window.
See: Defining Menus
See: Set Up Menus
-
Ensure that the required request group is set up.
You can define the groups of standard reports and processes that a user can run from the Submit a New Request window. Every responsibility can have access to one request group.
Use the Request Groups window.
See: Request Groups window, Oracle Applications System Administrator's Guide
-
Define a responsibility using the Responsibility window.
See: Responsibilities Window, Oracle Applications System Administrator's Guide
-
Set the HR User Profile Options for the new responsibility using the System Profile Values window. You must set up the:
-
HR: User Type
Use this profile option to limit field access on windows shared between Oracle Human Resources and Oracle Payroll.
-
HR:Security Profile
Enter the security profile for the responsibility. This must be set up at responsibility level, otherwise the default view-all security profile is used. Using Standard HRMS security you can only set up one security profile for a responsibility.
-
HR:Cross Business Group Profile
This option enables you to view some information across all business groups within your enterprise.
You can set also set up other User Profile Options.
See: System Profile Values Window, Oracle Applications System Administrator's Guide
-
-
Create the username and password using the User window.
Link the user to as many responsibilities as they need using the User window.
Important: Do not use the HRMS Assign Security Profile window if you are setting up Standard HRMS security.
See: Users Window, Oracle Applications System Administrator's Guide
-
Run system security process using the Submit Request window:
-
Security List Maintenance
Ensure this process is run every night.
-
Setting Up Security Groups Enabled Security
Use the following setup steps if your enterprise wants to enable many business groups for one responsibility.
Note: You only need to perform steps 1 and 2 when you first implement Oracle HRMS security. You can perform the other steps at any time.
You can update your security model from Standard HRMS Security to Security Groups Enabled security by following these steps.
Important: Once you have changed to Security Groups Enabled Security you cannot revert to the Standard Security model.
To set up users for Security Groups Enabled Security:
-
Set the Enable Security Groups Profile Option using the System Profile Values window.
Ensure the Enable Security Groups profile option is set to Yes at the application level for Oracle Human Resources.
Note: If this option is set to No then you are not using Security Groups Enabled security.
See: System Profile Values, Oracle Applications System Administrator's Guide.
-
Run the Enable Multiple Security Group Process using the Submit Request window.
You must run the Enable Multiple Security Group process to set up Oracle HRMS to use security groups.
See: Submitting a Request, Oracle Applications System Administrator's Guide
Warning: The creation of security groups is more complex with Oracle HRMS 11.5.10 and later releases. For this reason, the Enable Multiple Security Group process may appear slow, particularly if you have a large number of business groups.
The Enable Multiple Security Group process sets the Enable Security Groups profile option to Yes for all HRMS applications. We strongly recommend that you do not change the value of this profile option to another value.
-
Note: For each restricted security profile you create that references a reporting user, you must run the Generate Secure User (SECGEN) process. This is a one off process that is not required for view all security profiles.
-
Ensure that the functions or menus you require are set up.
This is required for the responsibility. For menu functions calling configured forms or task flows, you must enter a parameter in the Parameter field of the Form Functions window.
See: Set Up Menus.
See: Defining Menus.
-
Ensure that the request group you require is set up.
You can define the groups of standard reports and processes that a user can run from the Submit a New Request window. Every responsibility can have access to one request group.
Use the Request Group window.
See: Request Group window, Oracle Applications System Administrator's Guide
-
Define a responsibility using the Responsibility window.
See: Responsibility Window, Oracle Applications System Administrator's Guide
-
Set the HR User Profile Options for the new responsibility using the System Profile Values window. You must set up the HR: User Type option.
You can also set the HR:Cross Business Group Profile option. This enables you to view some information across all business groups within your enterprise. See HR:Cross Business Group Profile option for more information.
Note: For Security Groups Enabled security donot set up or amend the HR:Security Profile profile option or the HR: Business Group profile option using the System Profile Values window. To set up or change this profile option use the Assign Security Profile window.
You can set also set up other User Profile Options.
See: System Profile Values Window, Oracle Applications System Administrator's Guide
-
Create usernames and passwords using the User window.
Important: Do not link responsibilities and security groups (business groups) to users in this window. Instead, use the Assign Security Profile window. If you do enter a responsibility and security group in this window, you still need to use the Assign Security Profile window, to link your user to a responsibility and security profile. If you do not use the Assign Security Profile window, the default view-all security profile is used and your user will be able to see all records in the business group.
See: Users Window, Oracle Applications System Administrator's Guide
-
End-date unwanted user responsibilities linked to Standard security group
When you first enable security groups and run the Enable Multiple Security Groups concurrent process, the process creates two sets of records for existing user/responsibility pairs:
-
For each responsibility connected to a user it creates a record linking the user, the responsibility and the Standard security group.
-
For each HRMS responsibility connected to a user it creates a record linking the user, the responsibility, the security group associated with the business group, and the security profile.
If you are updating from Standard security, there may be many such records. For each existing user responsibility with a security group value of 'Standard', decide whether the user requires access to the responsibility. Users who may need to update global lookup codes need access to the Standard security group.
In most cases, users will not require access to the Standard security group. In this case, enter an end date to remove access to the responsibility. This reduces the number of responsibilities the user sees on logging in, and prevents users from accidentally entering data into the wrong business group.
Note: By default, the Standard security group is associated with the Setup business group.
Use the Users window.
See: Users Window, Oracle Applications System Administrator's Guide
-
-
Associate a security profile with a user, responsibility and business group using the Assign Security Profile window.
-
Run system security process using the Submit Request window:
-
Security List Maintenance
Ensure this process is run every night.
-
Setting Up Security for Applications Using Some HRMS Windows
If you are setting up an Oracle application that uses HRMS windows (such as Organization or Position), you need to set up some features of HRMS security.
Note: If you have licensed Oracle HRMS, do not follow these setup steps. Instead, follow the steps in Implementing Oracle HRMS.
Using the following procedure you can either set up a responsibility that can view all records in the Business Group, or restrict access to the records for selected organizations or positions. You can also set up organization security for Financials and Manufacturing business views.
Organization Security for Financials and Manufacturing Business Views
You can set up security for Oracle Financials and Manufacturing applications that use organizations and organization hierarchies in their business views.
To do this, you create a single security profile that secures data either by single operating unit or by operating unit and inventory organizations, as required. You must also set the MO:Security Profile profile option at site or application level, to point to this new security profile.
To establish multi-operating unit access for some business view users, you can create for each type of user a security profile that secures organizations by organization hierarchy, using the security profile functionality. You can then set the MO:Security Profile option at responsibility level for these users.
The show_bis_record function secures data according to the definition of the security profile that is referenced by the MO:Security Profile profile option. If this profile option is not set, the HR:Security Profile profile option is used. This function is called by financials and manufacturing business views.
Single Operating Unit Security
In the Organization Security tab of the Security Profile window, select the Secure organizations by single operating unit option from the Security Type poplist. The operating unit is determined using the operating unit specified in the MO:Operating Unit profile option.
Single Operating Unit Plus Inventory Organizations
In the Organization Security tab of the Security Profile window, select the Secure organizations by operating unit and inventory organizations option from the poplist. The operating unit is determined using the operating unit specified in the MO:Operating Unit profile option. The inventory organizations you wish to include must exist within this operating unit.
Impact on Security Implementations
Financial and manufacturing business view users who have not created security profiles have unrestricted access to their data.
Financial and manufacturing business view users can secure their business view data by security profiles identified by the HR:Security Profile profile option, as long as they have not set the MO:Security Profile profile option. If this has been set, they must modify their security setup to reflect the fact that the financial and manufacturing business views secure data using the MO:Security Profile profile option.
HRMS security is not affected by these options. The HRMS business views and forms secure data according to the setting of the HR:Security Profile profile option.
To set up security
-
If you are setting up a restricted access responsibility, create a restricted security profile to define the organizations or positions the responsibility can access.
Note: Ensure your Application supports restricted access security. Not all Oracle Applications support this type of security.
If you are setting up a responsibility which can view all the records in the Business Group, you do not need to set up a security profile.
Note: A view-all security profile is automatically created when you set up a Business Group. The view-all security profile always has the same name as the Business Group.
-
Define a responsibility using the Responsibility window.
See: Responsibilities Window, Oracle E-Business Suite System Administrator's Guide - Security
-
Select a security profile for the new responsibility.
In the System Profile Values window, enter a security profile at the responsibility level for the HR:Security Profile profile option.
-
Create a new user and link the user to a responsibility using the User window.
See: Users Window, Oracle E-Business Suite System Administrator's Guide - Security
-
If you are setting up restricted access security, run the Security List Maintenance Process (PERSLM) from the Submit a New Request Window. If you are setting up view-all security you do not need to run the Security List Maintenance process.
This process maintains the list of organizations, positions, employees and applicants that security profile holders can access. You should schedule it to run every night to take account of changes made during the day.
See: Running Reports and Programs, Oracle E-Business Suite User's Guide
Setting Up Reporting Users
Reporting users do not have online access to the database through system forms. They use reporting tools to prepare reports on the information their security profiles grant.
All secure users connect to the APPS ORACLE ID. This is created when the system is installed. However, for reporting users, you should create one or more new reporting user ORACLE IDs and associate each with a restricted security profile. Only users that have been registered as Restricted Oracle Users are available for selection as reporting users in the Security Profile windows.
The first step in this procedure is the job of the ORACLE database administrator. The other steps are normally completed by the system administrator.
To set up a new reporting user
-
Create a new reporting user ORACLE ID.
-
Register the new ORACLE ID with Application Object Library using the Oracle Users window, selecting Restricted in the Privilege field.
-
Define a security profile for the new ORACLE ID.
-
Run the HR security processes using the Generate Secure User Process.
See: Running Reports and Programs, Oracle E-Business Suite User's Guide
Defining a Context for Mass Actions
The Contexts window determines what information the user can view, enter, and change based on the Application, Legislation, and Responsibility.
A predefined global Context contains the default attribution that appear on the forms. When you create a new Context, these attributes serve as a basis for selecting which attributes to include as display, change, and criteria attributes.
The predefined global Context does not specify values for Application, Legislation, or Responsibility. You can restrict who can process mass actions by specifying these attributes. The system always applies the most defined Context, so as soon as you define these fields, the system applies the new Context instead of the global one.
You define a new context in the Contexts window.
To define a Context
-
Choose New from the File menu.
-
In the Context field, enter a name.
-
In the Transaction Name field, choose the Transaction Category to affect.
-
In the Application field, select an application.
-
Optionally, choose one or more of the following fields to restrict a user's ability to view and change data:
-
In the Legislation field, select a Legislation
-
In the Responsibility field, select a Responsibility
-
-
Choose the Find Attributes button.
The system displays the attributes from the global Context window on the Display and Change List tabbed regions.
-
Choose the Display tab and select those items to display on the Columns portion of the transaction template.
-
Choose the Change List tab and select those items to display for the Change List values.
-
Choose the Criteria tab and select the items you want to have appear on the Other Criteria list of values in Selection Criteria block on the Original tab.
-
Choose the Compile button to save your work and compile the flexfield definitions.
-
Save your work.
Security Profiles
Security Profiles
The security profile determines which applicant, employee, contingent worker and other person type records are available to holders of the responsibility the profile is linked to.
If you are using HRMS Standard security, you link a security profile to one responsibility using the HR:Security Profile profile option.
If you are using Security Groups Enabled security, you link a security profile to the user's responsibility and business group using the Assign Security Profile window. You can also link more than one security profile to a responsibility, as long as the user is different. This saves you setting up a new responsibility for each security profile you use.
Note: If you are using the Security Groups Enabled security model you must not use the HR:Security Profile profile option. This is automatically set up when you assign security profiles using the Assign Security Profile window.
See also Defining a Security Profile
Restricting Access to Records
You set up a security profile by identifying records of employees, applicants, contingent workers, and candidates in the system which you want users to be able to access. You identify the records by selecting work structures or other criteria in the application to which employees, applicants, contingent workers, or candidates are attached. For example, you could give users access only to the records of employees, applicants, contingent workers, or candidates in a single organization.
You can also create restrictions on records with a person type of "Other". This includes contacts for employees or applicants, and any other people with a person type in the category of "Other". You do this using the "View Contacts" option.
You can combine different types of restriction to create a set of rules giving exactly the security access permissions you require.
When you create a business group a view-all security profile is automatically created. This has the same name as the business group. The security profile provides access to all employee, contingent worker, and applicant records in the business group. The system administrator links this view-all profile to users who are setting up the system. They in turn can set up security for other users.
The criteria you can use to identify records are:
-
Internal organizations and organization hierarchies
-
Positions and position hierarchies
-
Payrolls
-
Supervisors and supervisor hierarchies
-
Custom restrictions
-
Assignments
Tip: Oracle recommends that you use either a supervisor or position hierarchy for Self-Service Human Resources (SSHR).
For more information on hierarchies in SSHR, see: People in Hierarchy, My List, and Search Pages, Oracle SSHR Deploy Self-Service Capability Guide.
Internal Organizations and Organization Hierarchies
Organizations include structures like departments, sections, groups and teams. You can restrict access to a single organization, a list of organizations, or an organization hierarchy. If you restrict on an organization hierarchy, you can exclude specific organizations that are in the hierarchy, or add other organizations that are not in the hierarchy.
Positions and Position Hierarchies
Positions are jobs performed within specified organizations. The position is derived from an organization and a job, for example, you may have a position of Shipping Clerk associated with the organization Shipping and the job Clerk.You can define security restrictions based on a position hierarchy.
Payrolls
You can restrict access to employee records by payroll. For example, you can give payroll staff who work on the payroll at a particular location access to records of employees on this payroll only.
Controlling security by payroll assignment limits the employee records users can see and update on employee-related windows, such as those for employee information, and element entry.
Of course, if an employee assignment does not include a payroll, payroll security cannot apply to this assignment. Payroll security also applies to applicants if they are assigned to a payroll.
Additional Information: Payroll security is not available for contingent workers since they are not assigned to a payroll.
The windows for compensation definition are unrelated to any particular employee records or payroll assignments. Therefore limiting access by payroll does not affect users' access to these windows.
Supervisors and Supervisor Hierarchies
The supervisor for an employee, applicant or contingent worker is the person identified in the Supervisor field in HRMS applications. Supervisor profiles are dynamic, in that they do not have to specify a particular person or hierarchy level. You can therefore set up a single security profile and use it for multiple users, who will each be able to access a different set of records depending on their own location in the hierarchy.
Note: If you choose to use supervisor hierarchy, you must also set the HR: Supervisor Hierarchy Usage profile option. This profile defines how supervisor hierarchies are built. You can choose whether to create person-based or assignment-based supervisor hierarchies.
Person-based supervisor hierarchy
A person-based supervisor hierarchy is a hierarchy based on a person's supervisor and direct reports.
Assignment-based supervisor hierarchy
As an alternative to the person hierarchy, you can choose to build a hierarchy based on the supervisor assignment. In this case, you also specify the supervisor assignment number for a person and the security processes use this assignment to generate an assignment-based supervisor hierarchy. As for the other supervisor-based hierarchy, the assignment-based hierarchy is dynamic and this security profile can be used for multiple users.
Note: When you set up security based on supervisor hierarchies, the list of employees visible to a user is usually generated at the start of the session. Therefore, for profiles that only restrict access by supervisor there is usually no need to run the Security List Maintenance process. However, for supervisors with a large number of subordinates (for example, at higher management levels) this may result in a delay in generating the list. You can improve performance by limiting the number of hierarchy levels a supervisor can access or by using the Static Lists functionality to store the security permissions in a list.
For more information, see Static Lists.
Alternatively, for the highest levels of management, consider setting up security using organization hierarchies.
Custom Restrictions
You can set up your own restrictions using SQL statements (for example, you might want to create a restriction allowing users access only to temporary part-time employees). Your custom restriction statements are automatically validated by the system. Valid restrictions are incorporated in the security profile, further restricting the list of employees, applicants and contingent workers specified using any of the other methods mentioned above.
Since you are defining additional restrictions using SQL, you need to ensure your SQL statements are tuned for performance. Otherwise, they will have an adverse effect on the time it takes to execute the Security List Maintenance process.
Important: Custom restrictions directly restrict employees, applicants and contingent workers only; you cannot create custom restrictions on people with a system person type of Other. However, if you add custom restrictions on employees, applicants or contingent workers, related people with a system person type of Other are restricted according to the setting of the "View Contacts" option.
As for other forms of security set-up, you can choose whether to enable user-based custom security. This means that Oracle HRMS uses your custom rules to evaluate security permissions for a user when that user logs on to the HR application. The alternative is to use static lists to store the security information for users or to run the Security List Maintenance process to regularly update the permissions.
Assignment-Level Security
Assignment-level security enables you to restrict security access based on individual assignments. This means that the security processes evaluate permissions on an individual assignment basis, rather than displaying all assignments if a manager has access to one assignment.
For more information, see: Assignment-Level Security.
User-Based Security
With user-based security, the application evaluates the security rules and permissions for the user logged on to the application. For example, if Bob Wright logs on to Self-Service Human Resources (SSHR), his access to organizations, positions, people, and assignments is based on his personal assignment details. The advantage of user-based security is that you can use one user-based security profile for multiple users. User-based security is available for security profiles based on organizations, positions, and supervisors, and can also be used in conjunction with custom security.
HR users can access ex-employee and future-dated records. For more information, see: Access to Ex-Employee and Future-Dated Employee Records
For more information on user-based security, see the individual sections in Defining a Security Profile.
Static Lists
Static lists enable you to choose whether to assess security permissions for a user when that user logs on (dynamically) or whether to store the permissions in static lists. The advantage of using static lists is that Oracle HRMS can quickly retrieve the permissions when the user logs on as the data is already available. A typical use of static lists may be for a senior manager who has access to many people.
When a user is in the static list, security permissions remain frozen until the next time you run the Security List Maintenance process. You can choose how often to run the Security List Maintenance process and schedule the process to run frequently if users' permissions are likely to change frequently.
A static list can contain any number of users. You can run the Security List Maintenance process for all users in the static list or use the Process in Next Run option on the Static Lists tab of the Security Profile window to select a specific user or group of users. You use this option in conjunction with the Security List Maintenance parameters; you can run the process for either all users in the static list or only users you select using the Process in Next Run option. By selecting specific users for inclusion in the run, you reduce the time and resources required to run the Security List Maintenance process.
See: Running the Security List Maintenance Process
The choice of whether to use static lists instead of dynamic security assessments depends on several factors, including:
-
If slow system performance is unacceptable at sign-on, you can reduce the processing requirement at sign-on by using static lists. Static lists can be particularly useful in the case of a top manager who has a large number of subordinate employees or organizations, for example. In this case, the process to evaluate security permissions may be lengthy at sign-on.
-
Static lists require additional maintenance to run the process. In addition, the static lists stores details of every person that the user included in the static list can access so if you include several users in a static list, you may experience an increase in data for processing and may need to consider running the process for selected users only.
-
The other factors above become more significant as the size of an organization increases. Large numbers of users logging on to Oracle HRMS at the same time would result in a huge processing requirement at the point of sign-on. In this case, it may be advisable to add users most affected by sign-on issues to the static lists.
Global Security Profiles
You can create global security profiles that enable users to work on organizations in multiple business groups.
You do this by setting up a global hierarchy, which can contain organizations from any business group on your database, and associating it with a global security profile. This enables you to create a security hierarchy that gives users access to organizations across business groups.
If you want to read more information about organization hierarchies, see: Organization Hierarchies, Oracle HRMS Enterprise and Workforce Management Guide
If you use the Oracle HRMS Forms Interface, you cannot access data across business groups using one responsibility, even if you associate a global security profile to your responsibility. Your access is limited to organizations in the business group defined in the HR:Business Group profile option. However, you can use people management templates to query and update worker information across business groups.
Access to Ex-Employee and Future Dated Employee Records
If you use user-based security profiles either based on organization, position, or custom security, then you can enable HR users to access ex-employee and future-dated employee records using the HR: Access Non-Current Employee Data profile option. If you enable this profile option, then HR users can access ex-employee records, for example, to manage retirement benefits. HR users can update future dated records.
Note: The HR: Access Non-Current Employee Data profile option does not apply to security profiles based on the supervisor hierarchy.
See: User Profiles
Related Topics
Running the Security List Maintenance Process
Assignment-Level Security
The security features in Oracle HRMS enable you to restrict security access based on individual assignments. The security processes evaluate permissions on an assignment-by-assignment basis, rather than displaying all assignments if a manager has access to any assignment.
For example, without assignment-level security, a manager with access to an employee's primary assignment would also have access to the employee's other assignments even though the supervisor for the other assignments may be a different manager. To allow supervisors to view only the relevant employees and assignments, you can enable assignment-level security in the Security Profile window. You use this functionality in conjunction with your security profile settings (for example, organization, position, supervisor security).
The following examples show how a manager's access to person records differs when assignment-level security is enabled and when it is disabled for a supervisor hierarchy, organization hierarchy, and position hierarchy.
Supervisor Hierarchies and Assignment-Level Security
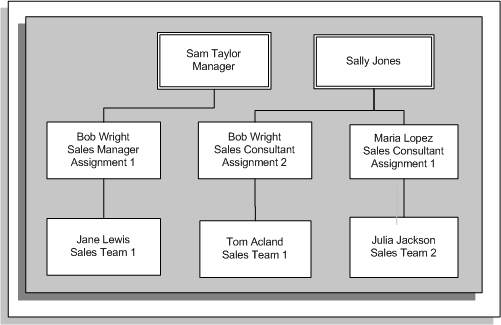
The graphic below shows the direct reports for Sam Taylor and Sally Jones. The subsequent examples show how the managers' access to the direct reports varies with the different security configurations.
Supervisor Hierarchy
Example 1: Assignment-Based Supervisor Hierarchy (No Assignment-Level Security)
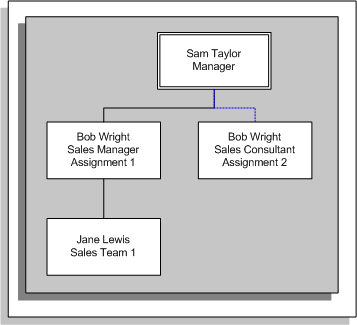
If you set up a supervisor hierarchy that is based on the supervisor assignment, Sam can see the direct report for Bob's first assignment (Jane). Because there is no assignment-level security, Sam can also see Bob's second assignment, however, Sam cannot access the direct reports for the second assignment. Sally Jones can see Bob's first assignment but cannot see the direct reports for this assignment (Jane). The following graphic illustrates the new hierarchy for Sam Taylor:
Assignment-Based Hierarchy for Sam Taylor (No Assignment-Level Security)
Example 2: Assignment-Based Supervisor Hierarchy (Assignment-Level Security)
With assignment-level security, Sam can only see Bob's first assignment and the direct reports for this assignment (Jane). Sally can see Bob's second assignment and Maria's assignment and the direct reports for these assignments. The following graphic illustrates the hierarchy with assignment-level security for Sam:
Assignment-Based Hierarchy with Assignment-Level Security
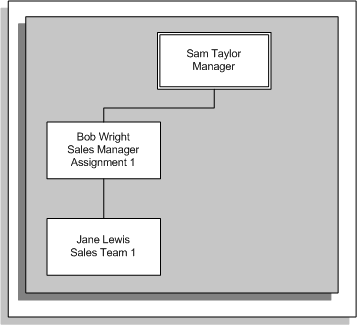
Note: If you are using an assignment-based hierarchy, it is advisable to use assignment-level security.
Organization Hierarchies and Assignment-Level Security
The graphic below shows two organization hierarchies. Within the first hierarchy (Eastern Region Sales) there is an employee with multiple assignments. The subsequent examples show how the hierarchy changes with assignment-level security disabled and enabled.
Organization Hierarchy
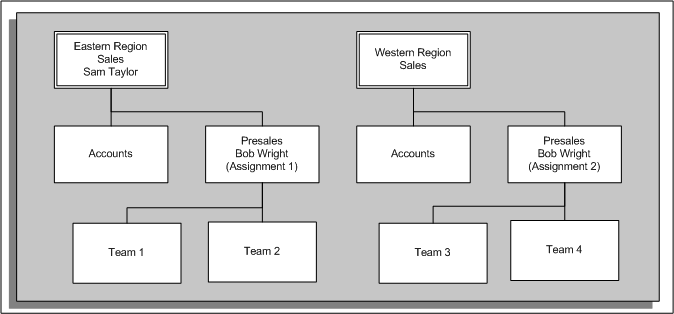
Organization Hierarchy (No Assignment-Level Security)
In this situation, Sam can see the people within the Accounts and Presales organizations. He can also see the people in organizations below Presales in the organization hierarchy (Team 1 and Team 2). Bob Wright has a second assignment in a different organization (Western Region Sales/Presales). Because assignment-level security is disabled, Sam can see this assignment (if a manager can access one assignment, he can access them all). Sam cannot see the organizations below the organization for Bob's second assignment. The following graphic illustrates the hierarchy without assignment-level security for Sam Taylor:
Organization Hierarchy (No Assignment-Level Security)
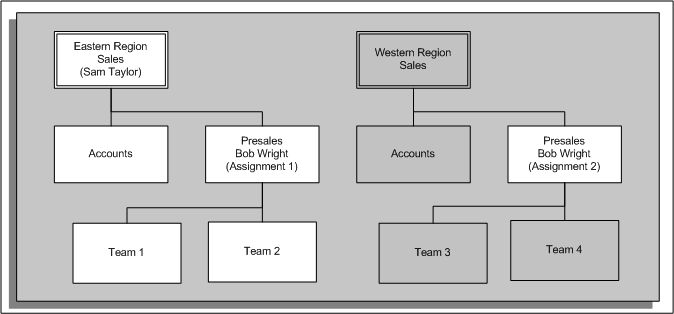
Organization Hierarchy (With Assignment-Level Security)
In this situation, Sam can see all people within the Accounts and Presales organizations. However, Sam cannot see Bob's second assignment (Western Region Sales/Presales) because the organization for the second assignment is not within the organization hierarchy to which Sam has access. The following graphic illustrates the hierarchy with assignment-level security for Sam Taylor:
Organization Hierarchy (With Assignment-Level Security)
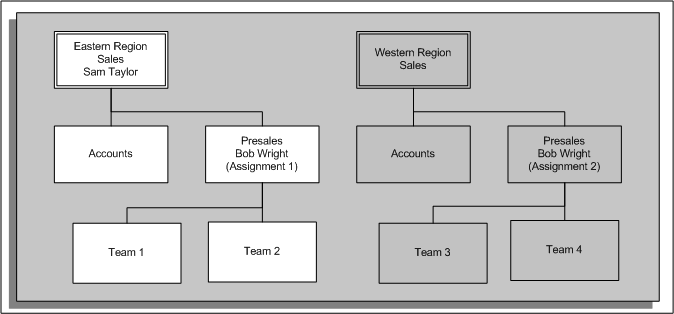
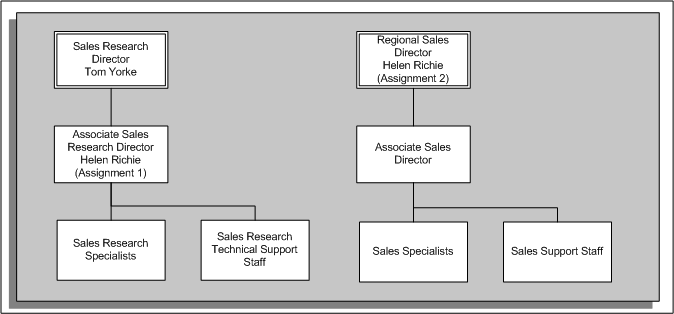
Position Hierarchies
The graphic above shows two position hierarchies. Within the first hierarchy (Sales Research Director) there is an employee with multiple assignments. The following examples show how the hierarchy changes with assignment-level security disabled and enabled.
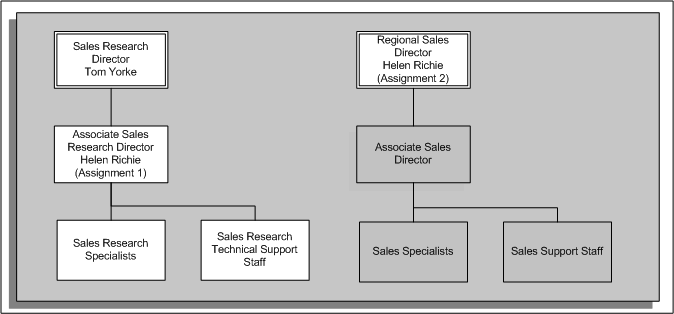
Position Hierarchy (No Assignment-Level Security)
In this situation, Tom can see the position below him in the hierarchy (Associate Sales Research Director). He can also see the reporting positions (Sales Research Specialists and Sales Research Technical Support Staff). Helen Richie has a second assignment for a different position (Regional Sales Director). Because assignment-level security is disabled, Tom can see this assignment (if a manager can access one assignment, he can access them all). Tom cannot see the positions below the position for Helen's second assignment. The following graphic illustrates the hierarchy without assignment-level security for Tom Yorke:
Position Hierarchy (No Assignment-Level Security)
Position Hierarchy (With Assignment-Level Security)
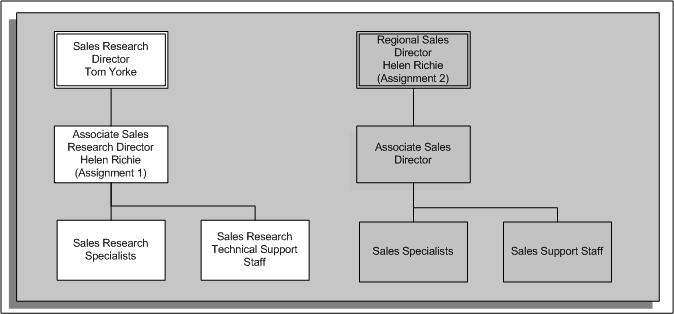
In this situation, Tom can see the position below him in the hierarchy (Associate Sales Research Director). However, Tom cannot see Helen's second assignment (Regional Sales Director) because the position for the second assignment is not within the position hierarchy to which Tom has access. The following graphic illustrates the hierarchy with assignment-level security for Tom Yorke:
Position Hierarchy (With Assignment-Level Security)
Implementing Assignment-Level Security
You enable assignment-level security in the Security Profiles window. To enable assignment-level security, select the Restrict on Individual Assignments option.
For more information, see: Defining a Security Profile
Assignment-level security is available for several areas of Oracle HRMS. The areas that currently support assignment-level security are:
-
Self-Service Human Resources (SSHR)
-
The following Oracle HRMS forms:
-
Combined Person and Assignment
(PERWSHRG)
-
Enter Assignment (PERWSEMA)
-
People Management (PERWSQHM)
-
Define Assignment Extra Info (PERWSAEI)
-
View Benefits (PERWSVBI)
-
View Salary History (PERWSSLH)
-
Salary Review (PERWSEPY)
-
View Worker Assignment History (PERWSASH)
-
Assignments Folder (PERWSFAS)
-
-
The following Oracle Payroll forms:
-
View Employee Run Result History (PAYWIELH)
-
Payroll and Assignment Processes (PAYWSACT)
-
Run QuickPay (PAYWSRQP)
-
Batch Element Entry (PAYWSQEE)
-
View Element Entry History for Employee (PAYWIEEH)
-
List Employees by Element (PAYWSLEE)
-
Element Entry (PAYWSMEE)
-
Adjust Balances (PAYWSABL)
-
Pay Method (PAYWSEPM)
-
Irish P45 Form (PAYIEP45)
-
Irish SOE Form (PAYIESOE)
-
Reverse Payroll Run (PAYWSRPR)
-
Irish Tax Information (PAYIETAX)
-
Security Profiles by Supervisor Hierarchy
You can set up a security profile that permits access to a supervisor hierarchy. This means that when a manager logs on to Oracle HRMS, the application uses assignment or supervisor attributes to build a person tree with the manager at the top level. The person tree shows the direct reports for the manager and also any direct reports at lower levels of the hierarchy to which the manager has access.
The structure of the person tree depends on whether you are using an assignment-based or person-based supervisor security profile. The following examples highlight the differences between the two types of supervisor security:
Supervisor Hierarchies
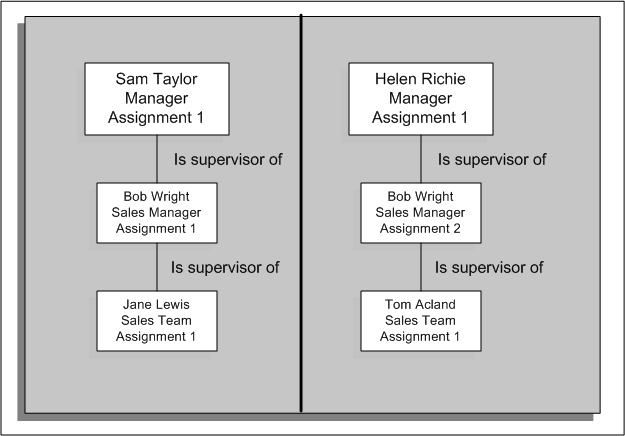
Person-Based Supervisor Hierarchy
This type of security uses the Supervisor field in HRMS applications to generate a supervisor hierarchy. When a manager logs on to the HRMS application, the application assesses security permissions for the manager (user) and builds a hierarchy showing the manager's direct reports and, if applicable, additional subordinate levels of employees. In this case, a manager can see all assignments for the direct reports. In the example, Sam Taylor can see both assignments for Bob Wright (assignments 1 and 2) and both direct reports for these assignments (Jane Lewis and Tom Acland).
Assignment-Based Supervisor Hierarchy
This type of security also uses the Supervisor field in HRMS applications but when the user enters the supervisor information, he or she can also select a particular assignment for the supervisor. When the supervisor logs on to Oracle HRMS or Oracle SSHR, the supervisor hierarchy is based on the supervisor's assignment.
Note: You should only use an assignment-based supervisor hierarchy if you have enabled multiple assignments in your organization.
In the example, Sam Taylor's access to person records depends on whether assignment-level security is enabled. If it is enabled, Sam can only access the records for Bob Wright's first assignment and direct report. If assignment-level security is not enabled, Sam can access the records for both of Bob's assignments and also for the direct report for the first assignment.
For more information, see Assignment-Level Security in Security Profiles.
HR: Supervisor Hierarchy Usage Profile Option
You use this profile option to specify the behavior of the supervisor hierarchy in HRMS applications by specifying whether the supervisor hierarchy is assignment or person-based.
Security Profiles by Organization and Organization Hierarchy
To set up a security profile that permits access to employee records of certain organizations only, you make use of organization hierarchies. You can build any number of additional hierarchies to meet your security requirements.
For example, suppose you build the agency hierarchy below:
Government Agency Hierarchy
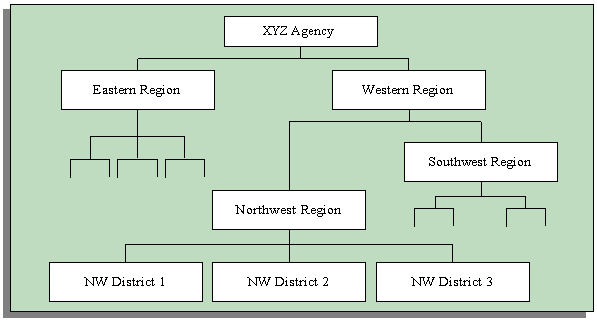
You can create a security profile that permits access to employee records throughout an agency. This profile references the XYZ Agency as the highest organization in the hierarchy through which profile holders have access to employee records.
Next, you want the directors of the two agency regions to have access to all employee records in their region only. You create Eastern and Western Director security profiles. These profiles also reference the XYZ Agency hierarchy. But, they name the Eastern and Western Regions, respectively, as the top organizations for these profiles' access to employee records.
When you name an organization as the top organization, you specify whether it is inclusive or not. You must include the top organization if you want holders of the profile to access records of people assigned to the top organization.
With User-Based Security
If you are using user-based security, you can choose to use the organization linked to the user's assignment as the top organization. The top organization is then determined dynamically when the user logs on or when the Security List Maintenance process is run. To illustrate the advantage of using user-based security in this way, take the above example. Instead of having to create two security profiles so that the two regional directors can only access the records for the employees in their regions, you would only need to create one security profile which would identify the top organization based on the user's assignment. In the example, the security process would identify that the top organization for one director is Eastern Region and for the other director it is Western Region.
If a user has multiple assignments, the application builds a hierarchy for each assignment, using each assignment's organization as the top organization. The user can then see the people and assignments in any of their assignments' subordinate organizations.
Security Profiles by Position and Position Hierarchies
After establishing limits on record access using organization hierarchies, you can further restrict access by means of position hierarchies.
Suppose, for example, within the XYZ Agency, you want to give the Chief of Personnel Operations access to her subordinates' records only. There are two ways of doing this: either with or without user-based security.
You can start by building the following agency hierarchy.
Sales Positions Hierarchy
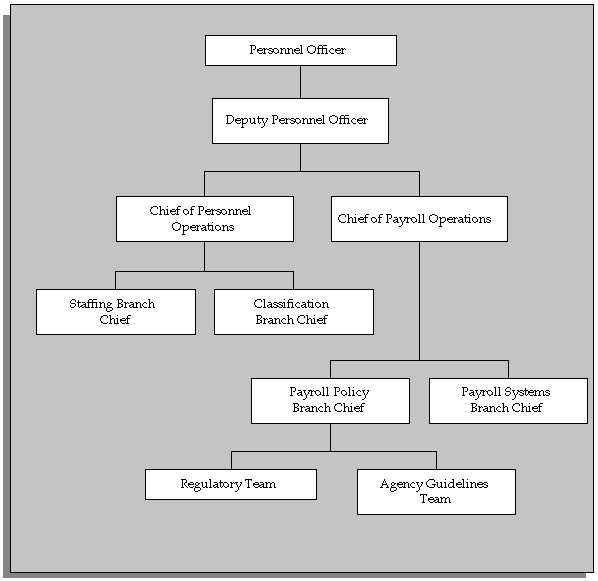
Without User-Based Security
Create the Chief of Personnel Operation security profile. This profile references the agency hierarchy and names the Chief of Personnel Operations as the top position for access to employee records.
| Security Profile: | Chief of Personnel Operations |
| Organization Hierarchy: | XYZ Agency |
| Top Organization: | XYZ Agency |
| Position Hierarchy: | Personnel Operations |
| Top Position: | Chief of Personnel Operations |
| Include Top Position: | Yes |
When you give the Chief of Personnel Operations a responsibility including this security profile, she can access the records of her subordinates. But, she cannot access records of:
-
the Personnel Officer or the Deputy Personnel Officer
-
the Chief of Payroll Operations
-
the Chief of Payroll Operations' subordinates
As with organization hierarchies, you can specify that profiles do not include access to the top position.
With User-Based Security
If you are using user-based security, you can choose to use the position linked to the user's assignment as the top position. The top position is then determined dynamically when the user logs on or when the Security List Maintenance process is run. To illustrate the advantage of using user-based security in this way, take the above example. Instead of having to create a separate security profile for each position hierarchy, for example, a Chief of Personnel Operations profile and a Chief of Payroll Operations profile, you could create one security profile which would identify the top position based on the user's assignment. In the example, the security process would identify that the top position for the Chief of Personnel Operations is different from the top position for the Chief of Payroll Operations and build the position hierarchy accordingly.
If a user has multiple assignments, the application builds a hierarchy for each assignment, using each assignment's position as the top position. The user can then see the people and assignments in any of their assignments' subordinate position hierarchies.
Defining a Security Profile
You can define security profiles in the Security Profile window (to give access to a single business group) or the Global Security Profile window (to allow users to access records from more than one business group).
See also: Security Profiles
Note: Using the Global Security Profile window does not give Oracle HRMS users access to records from multiple business groups within the same responsibility; users must still switch responsibilities to see records from different business groups. However, HRMS users can see a restricted set of information in records from more than one business group within a single responsibility if the HR:Cross Business Profile profile option is set to Yes. In addition, you can use people management templates to query and update worker information across business groups using a single responsibility.
If you want to associate a reporting user with the new security profile, the ORACLE database administrator must create a new reporting user ORACLE ID. The system administrator must register the new ORACLE IDs as restricted privilege users with the Application Object Library.
See: Setting up Reporting Users
To define a security profile
-
Enter a name for the security profile.
-
If you are using the Security Profile window, select a business group. Users will have access only to records within this business group. This does not need to be the business group associated with your responsibility.
If you are using the Global Security Profile window, users will have security access to records from all business groups, subject to other restrictions you set up.
-
If you want reporting users to be able to use this security profile, select the Reporting User name for the ID set up by the database administrator (this option is not available when setting up Global Security).
Applying Restrictions by Person Type
-
You can choose to apply the security restrictions you set up to employees, applicants, contingent workers, contacts, candidates or any combination of these.
Note: You can only restrict access to candidates if you have iRecruitment installed. If you do not have iRecruitment, the application uses the default setting of All for the View Candidates box.
For example:
-
If you want the security restrictions to apply to employees, select Restricted from the View Employees box.
-
To ignore the security restrictions for employees and allow access to all employees, select All from the View Employees box.
-
To prevent access to any employee records, even if the other security restrictions allow access, select None from the View Employees box.
You can set the View Applicants, View Contingent Workers, and, if you have iRecruitment, View Candidates, options independently, giving different security access to employees, applicants, contingent workers, and candidates using the same security profile.
For contacts, or other people of person type Other, you can choose one of two options:
-
All: Access is unrestricted, so that all people of type Other are visible to the security profile
-
Restricted: The profile restricts access to contacts to those people who are related to employees, applicants, or contingent workers who are visible within the security profile. If you can see the record of an employee, applicant, or contingent worker, you can also see the records of people of type Other specified as related to them (using the Contact Relationship field). All people of type Other who are unrelated to any employee, applicant, or contingent worker are also visible to the security profile.
Allowing Access to Granted User Records (SSHR only)
-
-
Select the Allow Granted Users option to allow a self-service user with this security profile to access the records of other self-service users, provided that the other users grant them access using the self-service application.
Note: This setting applies to the self-service application only and has no effect on users of Oracle HRMS.
Restricting Access by Individual Assignment
-
Select the Restrict on Individual Assignments option to build security hierarchies based on a person's individual assignments. Oracle HRMS builds the security hierarchy and assesses each individual assignment. The hierarchies generated by the security process will then only contain the particular assignments to which the manager has access. If you do not select this option, a manager who can see one assignment for a person can see all other assignments.
For more information on restricting by individual assignment and securing your forms, see: Assignment-Level Security.
Restricting Access by Organization
-
In the Organization Security tabbed region:
-
To restrict by organization list, select the Secure organizations by organization hierarchy and/or organization list option in the Security Type poplist. Select the organizations in the Organization Name field, and choose the Include option button.
-
To restrict by organization hierarchy, select the Secure organizations by organization hierarchy and/or organization list option. Select an organization hierarchy, and a top organization. Select the Include Top Organization option if you want to allow access to this organization.
If you are using user-based security, you can choose to use the organization linked to a person's assignment as the top organization by selecting the corresponding option. The security process identifies the organization linked to the user's assignment when the user logs on (or when the Security List Maintenance process is run).
If required, you can add organizations not in the hierarchy to the list, by selecting the organizations in the Organization Name field and choosing the Include option button. You can also remove specific organizations from the selected hierarchy by selecting an organization in the Organization Name field and choosing the Exclude option button.
Note: The Secure organizations by single operating unit and Secure organizations by operating unit and inventory organizations options are for use by non-HRMS users, and have no effect on the HRMS application.
-
-
By default, the Exclude Business Groups check box is unchecked, giving users access to the business groups themselves, and therefore to employees or applicants who have the business group(s) as their organization. Check the box to prevent access to the business group(s) and the employees or applicants attached to them (for example, to prevent users from seeing new starters and other employees who have been assigned to the business group by default).
Restricting Access by Position (not Global Security)
-
In the Position Security tabbed region, deselect the View All Positions option. Select a position hierarchy, and a top position. Check the Include Top Position check box if you want to allow access to this position.
If you are using user-based security, you can choose to use the position linked to a person's assignment as the top position by selecting the corresponding option. In this case, the security process identifies the position linked to the user when the user logs on (or when the Security List Maintenance process is run).
Restricting Access by Payroll (not Global Security)
-
In the Payroll Security tabbed region:
-
To give access to all payrolls, check the View All Payrolls check box.
-
To give access to many payrolls, uncheck the View All Payrolls check box, and uncheck the Include check box. Select the payrolls you want to exclude.
-
To give access to a small number of payrolls, uncheck the View All Payrolls check box, and check the Include check box. Select the payrolls to include.
Restricting Access by Supervisor
-
-
In the Supervisor Security tabbed region, you can further specify how to create your supervisor hierarchy. You can either create a hierarchy based on a person's supervisor assignment or based on a person's supervisor.
For more information, see: Security Profiles for Supervisor Security.
Select either the person-based or assignment-based option and enter the number of levels of access you want to allow the supervisor to see in the Maximum Hierarchy Levels box (or leave the field blank to allow access to all levels).
Note: When you set up security based on supervisor hierarchies, you can choose to generate the list of employees visible to a user at the start of the session (user-based security). For supervisors with a large number of subordinates (for example, at higher management levels) leaving the Maximum Hierarchy Levels box blank may result in a delay in generating the list. You can improve performance by limiting the number of hierarchy levels a supervisor can access or by using the Static List functionality.
For more information, see: Static Lists.
Alternatively, for the highest levels of management, consider setting up security using organization hierarchies.
-
If you are using person-based supervisor security, you can choose whether to display multiple assignments in the supervisor hierarchy. By default, the Primary Assignments Only option is not selected, which gives users access to people who report to them in any assignment. If you only want to give users access to people who report to them in their primary assignment, select this option.
Miscellaneous Restrictions
-
The list of people whose records are accessible using a security profile can change with the user name of the person who logs in (if you are using user-based security). If you want the application to evaluate permissions based on a specific person (and not vary depending on the user name of the person who logs in) enter a name in the Named User field. For example, to set up supervisor-based security for reporting users who do not have any association with employees, enter the name of a person at the required supervisory level.
To prevent users from seeing their own records, check the Exclude User check box (if you have entered a name in the Named User box, users will be prevented from seeing the records of the named user rather than their own records).
Note: This functionality is not supported in Self-Service Human Resources (SSHR).
Restricting Access by Custom Security
-
In the Custom Security tabbed region, select the custom restriction option. The options are as follows:
-
No custom security
-
Restrict the people visible to this profile
The Security List Maintenance process is the basis for this type of custom security. The security data is held in a static list.
-
Restrict the people visible to each user using this profile
Oracle HRMS assesses the custom security when the user signs on. In addition, the custom security code can include references to user specific variables, for example, fnd_profile.value() and fnd_global.employee_id.
-
-
Enter a valid SQL WHERE clause fragment to select a group of records. For example, to add a restriction that assignments must be based in either London or Paris, add the following SQL fragment:
ASSIGNMENT.location_id in (select LOC.location_id from hr_locations_all LOC where LOC.location_code in ('London','Paris'))Alternatively, you could create custom code to use user-specific variables. The following example illustrates the use of user-specific variables:
In this example, the custom code creates a rule whereby a user can display employees or contingent workers whose last name begins with the same letter as their own. The security profile is called "Same first letter of last name".
substr(person.last_name,1,1) = (select substr(i.last_name,1,1) from per_all_people_f i where i.person_id = fnd_global.employee_id and trunc(sysdate) between i.effective_start_date and i.effective_end_date)Note: In addition, the View Employees or View Contingent Workers option is set to Restricted, and the "Restrict the people visible to each using this profile" option is set on the Custom Security tab.
If the clause is valid, it is automatically incorporated in an SQL select statement that the system generates to restrict access to records, based on the restrictions you have set up in the other tabbed regions. The list of employees, contingent workers, and applicants specified by these other restrictions is therefore further restricted by the custom restriction.
The clause fits into the system-generated statement in the following way (this statement is not visible on screen):
select 1 from per_all_assignments_f ASSIGNMENT, per_all_people_f PERSON, per_person_type_usages_f PERSON_TYPE where ASSIGNMENT.assignment_id=:asg_id and:effective_date betweeen ASSIGNMENT.effective_start_date and ASSIGNMENT.effective_end_date and PERSON.person_id=ASSIGNMENT.person_id and :effective_date between PERSON.effective_start_date and PERSON.effective_end_date and PERSON.person_id=PERSON_TYPE.person.id and :effective_date between PERSON_TYPE.effective_start_date and PERSON_TYPE.effective_end_date and {your custom where clause fragment goes here}Important: Custom restrictions directly restrict employees, contingent workers, and applicants only; you cannot create custom restrictions on people with a system person type of Other. However, if you add custom restrictions on employees, contingent workers, or applicants, related people with a system person type of Other are restricted according to the setting of the "View Contacts" option.
-
Choose the Verify button to check that the clause you have entered is valid. If it is invalid, an error message appears explaining the reasons.
Using Static Lists
Static lists enable you to assess security periodically and store the data. You add users to the static list and their security permissions are evaluated when the Security List Maintenance process is run. Oracle HRMS stores the permissions for quick retrieval when the user logs on and freezes the permissions until you run the Security List Maintenance process again.
To specify which users to include in a static list, enter the user ID in the field.
-
To include a specific user or group of users in the next Security List Maintenance run, select the Process in Next Run option for those users.
-
Save your work.
When you have modified or created new security profiles, it may be necessary to run security processes to activate your changes.
See: Security Processes
See: Running the Security List Maintenance Process
Assigning Security Profiles
Use the Assign Security Profile window to link user names, and security profiles to responsibilities. Only use this window if you are using Security Groups Enabled security (formerly called Cross Business Group Responsibility security).
Important: When using Security Groups Enabled security even if you have linked a user to a responsibility using the User window, you must still link your user to responsibility and security profile using the HRMS Assign Security Profile window. If you do not use the Assign Security Profile window, HRMS uses the default view-all security profile for the Business Group and the user will see all records for the Business Group.
The Assign Security Profile window is an essential part of setting up and maintaining HRMS security for Security Groups Enabled security. You must use this window to update your security profile assignment. Any changes entered for the security profile assignment are also shown on the User window. However, if you end date a user's responsibility using the User window, this is not shown on the Assign Security Profile window.
When you navigate to the Assign Security Profile window, the Find Security Profile Assignments window displays automatically. Select New to create a new assignment. For information about querying existing security profile assignments, see Using the Find Security Profile Assignment window.
To assign a new security profile
-
Enter the user name you want to link to a responsibility.
-
Enter the application and responsibility you want to link to the user.
-
To assign a local security profile, select a business group to assign to the user's responsibility. The local security profile for the business group is automatically entered when you click in the Security Profile field.
-
To assign a global security profile, first select the security profile to assign to the user's responsibility, then select a business group.
Note: If you enter a value in the Business Group field first, the list of security profiles is filtered and does not display security profiles for any other business groups.
You can link more than one security profile to a responsibility as long as the user is different.
-
Enter the time period of security profile assignment.
You must enter a start date. Optionally, enter an end date if you want the security profile assignment to end on a particular date.
-
Save the security profile assignment.
To end a security profile assignment
You cannot delete security profile assignments. If a user no longer needs an assignment you must enter an end date.
-
Query the security profile assignment you want to end.
-
Enter an end date. The user cannot use this responsibility, Business Group and security profile from this date.
Using the Find Security Profile Assignment window
This window enables you to search for security profile assignments that have already been set up. You only use security profile assignments if you are setting up Security Groups Enabled security.
If you want to set up a new security profile assignment select the New button. For more information on setting up new security profile assignments, see Assigning Security Profiles.
Note: When you navigate to the Assign Security Profiles window, the Find Security Profile Assignment window automatically displays.
To query a security profile assignment
-
Enter a full or partial query on one, a selection or several of the following:
-
User name
-
Application
-
Responsibility
-
Business group
-
Security profile
Note: If you enter a value in either the Business Group or the Security Profile field, any value entered in the other field is blanked out if it is not valid to select both. For example, you cannot select both business group A and a security profile which is specific to business group B.
-
-
Check the Retrieve Only Active Assignments check box if you want to query security profile assignments that are active as of today's date. Uncheck the Retrieve Only Active Assignments check box if you want to query security profile assignments which are no longer active or assignments which will be available in the future.
-
Choose the Find button.
The security profile assignments found by the query are displayed in the Assign Security Profile window.
Running the Security List Maintenance Process
You run the Security List Maintenance process to update the lists of organizations, positions, employees and applicants that security profiles can access. You should run this process regularly, for example nightly, to take account of changes made during the day.
You run the Security List Maintenance process from the Submit Requests window.
To run the Security List Maintenance Process
-
In the Name field, select Security List Maintenance.
-
In the Parameters window, enter the date for which you want to run the report in the Effective Date field. If you do not enter a date the process runs for the current system date.
-
In the Generate lists for field, select the range of security profiles for which you want to run the process. You can choose to update:
-
All Global Security Profiles (all profiles created using the Global Security Profile window)
-
All Security Profiles
-
All Security Profiles in One Named Business Group
-
One Named Security Profile
-
One Specified User in One Named Security Profile
-
-
If you have selected All Security Profiles in One Named Business Group, select a business group.
-
If you have selected One Named Security Profile, select a security profile.
-
If you have selected One Specified User in One Named Security Group, select a security profile and the user name.
-
In the Process field, select the type of people to be processed. You can choose from the following values:
-
Current people only
-
Terminated people only
-
Current and Terminated people
Note: If you have selected One Named Security Profile, the only available option is Current and Terminated people.
-
-
In the Static User Processing field, choose whether to run the process for all static users or only those users selected for inclusion in the next processing run (selected on the Static Users tab of the Security Profile window).
Note: You can use this parameter only if you have chosen a processing option other than One Specified User in One Named Security Group.
-
Choose OK.
-
Complete the batch process details and choose the Submit button.
User Profiles
User Profiles
A user profile is a set of changeable options that affects the way your application runs. You can set user profiles at different levels. The levels below are used by the standard Security hierarchy type:
-
Site level: These settings apply to all users at an installation site.
-
Application level: These settings apply to all users of any responsibility associated with the application.
-
Responsibility level: These settings apply to all users currently signed on under the responsibility.
-
User level: These settings apply to individual users, identified by their application usernames.
Values set at a higher level cascade as defaults to the lower levels. Values set at a lower level override any default from a higher level.
Levels For Setting User Profile Options
Tip: Set site-level options first to ensure that all options have a default. If a profile option does not have a default value, it might cause errors when you use windows, run reports, or run concurrent requests.
There are two other Hierarchy Types that are used by some profile options: Organization hierarchy type, and Server hierarchy type. These hierarchy type values also cascade as defaults from Site down to User level. They have the following levels:
-
Organization hierarchy type
-
User level
-
Organization level
-
Site level
-
-
Server hierarchy type
-
User level
-
Server level
-
Site level
-
The Organization hierarchy type enables you to set profile options for users in different operating units that are used by other applications, particularly Financials. These are not used by HRMS at all.
The Server hierarchy type should only be used by Database Administrators. It enables you to set values for a particular server on which you are running the application.
For more information on these hierarchy types see: Profiles Window, Oracle Applications Developer's Guide
You use the System Profile Values window to set profile options at each level for your user community. If you change a user profile option value, your change takes effect as soon as your users log on again or change responsibilities.
See: System Profile Values Window, Oracle Applications Developer's Guide
Application users can use the Personal Profile Values window to set their own profile options at the user level. Not all profile options are visible to users, and some profile options, while visible, cannot be updated by end users. Any changes users make to their personal profile options take effect immediately.
See: Defining Preferences with User Profile Options, Oracle Applications User's Guide
Profile Options Summary
The table below indicates whether users of the system can view or update the profile option, and at which System Administrator levels (either user, responsibility, application, or site) the profile options can be updated. These System Administrator levels are included in the table as Site, App, Resp, and User.
For the User column, Yes indicates that you can update the profile, View Only indicates that you can view the profile but you cannot update it, and No indicates that you can neither view nor update the profile.
A "Required" profile option requires you to provide a value. Otherwise the profile option already provides a default value, so you only need to change it if you do not want to accept the default.
For details of profile options applicable to all Oracle Applications, see: Profile Options in Oracle Applications Object Library, Oracle Applications Developer's Guide
| Profile Option | Admin UpdateLevels | User | Required | Default Value |
|---|---|---|---|---|
| Apply Assessment Competencies to Person | Site | No | No | No |
| AME:Installed | App | Yes | No | NA |
| AuditTrail:Activate | AppSite | No | No | No |
| BEN:BEN HOURLY ANNUALIZATION FACTOR | SiteAppResp | Yes | No | 2080 |
| BEN:Benefits Preferred Currency | SiteAppRespUser | Yes | No | NA |
| BEN: Carry Forward Certification | SiteAppRespUser | No | No | No |
| BEN: Check Enrollment Limits | Site | No | No | No |
| BEN:Compensation Manager | SiteAppRespUser | Yes | No | NA |
| BEN:Comp Objects Display Name Basis | SiteApp | No | No | Session |
| BEN: Cross Business Group for Plan Design Copy | SiteAppResp | Yes | No | Yes |
| BEN: CWB Approval Mode | Site | No | No | Submission at any time |
| BEN: CWB Allocation as Percent of Eligible Salary Decimals | ||||
| BEN: CWB Budget as Percent of Eligible Salary Decimals | ||||
| BEN: CWB Budget Rows Displayed | SiteAppRespUser | |||
| BEN: CWB Download Expire Seconds | SiteAppRespUser | Yes | No | 60 |
| BEN:CWB Display Currency Type | SiteAppRespUser | Yes | No | Corporate Currency |
| BEN: CWB Encrypt/Decrypt Key | SiteAppRespUser | No | No | NA |
| BEN: CWB Estimated Market Price | SiteAppRespUser | Yes | No | NA |
| BEN: CWB History Type Display | SiteAppResp | Yes | No | Basic Stock History |
| BEN: CWB Home Plans Displayed | SiteAppRespUser | Yes | No | NA |
| BEN: CWB Layout Lock Time | SiteAppRespUser | Yes | No | 10 |
| BEN: CWB Maximum Number of Layouts | SiteAppRespUser | Yes | No | 10 |
| BEN: CWB Plan Context for Reporting | Site | Yes | No | Plan |
| BEN: CWB Spreadsheet Version | SiteAppRespUser | |||
| BEN:CWB Summary Level | SiteAppRespUser | Yes | No | NA |
| BEN:CWB Table Population | SiteAppRespUser | Yes | No | |
| BEN: CWB Show In-Progress Compensation | SiteAppRespUser | Yes | No | |
| BEN: CWB Valid Grade Filtering | SiteAppRespUser | Yes | No | Yes |
| BEN: CWB Validate Performance/Assignment Changes Online | SiteAppRespUser | Yes | No | No |
| BEN: CWB Wizard Compratio Range | SiteAppRespUser | Yes | No | 5 |
| BEN: CWB Wizard Years Worked Range | SiteAppRespUser | Yes | No | 1 |
| BEN: CWB Worksheet Rows Displayed | SiteAppRespUser | |||
| BEN:Designation No Change | SiteAppResp | Yes | No | No |
| BEN:Eligible Profile Rule | SiteAppResp | Yes | No | AND |
| BEN: Enable Absence Plans Functionality | SiteAppResp | Yes | No | No |
| BEN:Enable Quartile in Grade Life Event | SiteAppResp | Yes | No | Yes |
| BEN:Imputed Income Post Tax Deduction | SiteAppRespUser | Yes | No | No |
| BEN:Max Extract Line Size | SiteAppRespUser | Yes | No | 10000 |
| BEN:VAPRO Rule | SiteAppResp | Yes | No | AND |
| DateTrack:Date Security | SiteAppRespUser | Viewonly | No | NA |
| DateTrack:Delete Mode | - | - | Not in use | |
| DateTrack:Enabled
Note: This profile option applies to Full HR only. |
App | Viewonly | No | Yes |
| DateTrack:Login Date (YYYY/MM/DD) | SiteAppRespUser | Viewonly | NA | NA |
| DateTrack:Override Mode | - | - | Not in use | |
| DateTrack:Reminder | SiteAppRespUser | Yes | No | No |
| DateTrack:Update Mode | - | - | Not in use | |
| Disable Self-Service Personal | SiteAppRespUser | Yes | No | No |
| Display Messages | SiteAppRespUser | Yes | ||
| Enable Security Groups | SiteApp | No | Yes | Security groups are not enabled |
| Flexfields:Open Descr Window | SiteAppRespUser | Yes | Yes | Yes |
| Flexfields:Open Key Window | SiteAppRespUser | Yes | Yes | Yes |
| GHR: Allow Ex-Emp Purge | Site , Responsibility, User | Yes | No | No |
| Help Localization Code | RespUser | Yes | Yes, by HRMS | The Responsibility is associated with the Global set of help files rather than a localized or verticalized set. |
| HR: Absence Duration Auto Overwrite | SiteResp | No | No | No |
| HR: Absence Start Date | SiteAppRespUser | No | No | The start date of the Absence being recorded on the Absence form |
| HR: Absence View Layout | SiteAppRespUser | Yes | No | FORM or TABLE |
| HR: Access Non-Current Employee Data | SiteResp | No | No | No |
| HR: Accrual Plan Element Set Displayed to User | SiteAppRespUser | Yes | No | Null |
| HR:Action Parameter Group Name | SiteAppRespUser | Yes | ||
| HR: Actions - Validation | SiteAppRespUser | Yes | No | Validate all Functions |
| HR:Allow Approver Updates to Self Service Actions | Site | No | No | No |
| HR:Allow Concurrent Self Service Actions | Site | No | No | No |
| HR:Allow Functions Access During Hrglobal Run | View only | Viewonly | No | No |
| HR:Allow Online W-2 Viewing as of (MM/DD) | SiteAppRespUser | Yes | ||
| HR:Allow Processing of Ineligible Self Service Actions | Site | No | No | No |
| HR:Allow Use of Eligibility for Self Service Actions | Site | No | No | No |
| HR: Applicant Assignment Cleanup Run Mode | Site | No | No | In Patch Process |
| HR: Applications View Layout | SiteAppRespUser | Viewonly | No | FORM or TABLE |
| HR: Appraisal Template Lov | SiteAppRespUser | Yes | No | No |
| HR: Appraisee Can Add Participants | SiteAppRespUser | No | No | Yes |
| HR: Assignment ID | - | - | Internal use only. | |
| HR: Authoria Integration Enabled | SiteAppRespUser | Yes | Yes (if linking to Authoria HR) | No |
| HR: Authoria UK URL | Site | No | Yes (if linking to Authoria HR) | |
| HR: Authoria US URL | Site | No | Yes (if linking to Authoria HR) | |
| HR: Auto Apply Collective Agreement Entitlements | SiteAppResp | Yes | Yes | No |
| HR: Auto Evaluate Collective Agreement Entitlements | SiteAppResp | No | Yes | No |
| HR: Automatically synchronize single GL company cost centers with HR | Site | Yes | Yes | No |
| HR: Base Salary Required | Site | No | No | Null |
| HR: BIS Job Hierarchy - Job Grouping Level 1 | Site | No | No | Null |
| HR: BIS Job Hierarchy - Job Grouping Level 2 | Site | No | No | Null |
| HR: BIS Reporting Hierarchy | - | - | Obsolete. | |
| HR:Blank Effective Date | SiteAppRespUser | Yes | No | No |
| HR:Business Group | SiteResp | Viewonly | Yes | Default Setup Business Group at Site level. |
| HR: Cancel Application | SiteAppResp | Viewonly | No | Default is Null. This is interpreted by the system as No. |
| HR: Check Entitlement Cache | SiteAppResp | No | Yes | Yes |
| HR: Collective Agreement Logging | SiteAppRespUser | Yes | Yes | Low |
| HR:Contingent Worker Manager Actions Menu | SiteAppRespUser | Yes | Yes | Contingent Worker Manager Actions Menu |
| HR:Contingent Worker Personal Actions Menu | SiteAppRespUser | Yes | Yes | Contingent Worker Personal Actions Menu |
| HR: Copy period details for budget | SiteAppRespUser | Yes | No | Default is No. |
| HR:Cross Business Group | Site AppResp | Viewonly | NA | Default is No. |
| HR: Cross BG Duplicate Person Check | SiteAppResp | No | No | Yes |
| HR: CWK in Head Count Reports | SiteAppRespUser | Yes | No | Yes |
| HR: Data Exchange Directory | SiteAppResp | Viewonly | No | |
| HR: Data Migrator Business Group Lockout | Site | No | NA | NA |
| HR:Data Pump Action Parameter Group | SiteAppRespUser | Yes | No | Null |
| HR: Date From | - | - | Internal use only. | |
| HR:Default Assignment Costing | SiteAppRespUser | Yes | No | . |
| HR:Default Check/Cheque Number Method | SiteAppRespUser | Yes | No | Null |
| HR: Default Correspondence Language | SiteAppRespUser | Yes | No | No default. |
| HR: Default Full Name Format | SiteAppRespUser | Viewonly | No | Surname Prefix Initials Prefix (Partner) Surname (Partner) |
| HR: Default Nationality | SiteAppRespUser | Yes | No | NA |
| HR: Defer Update After Approval | SiteAppRespUser | Yes | Yes | Yes |
| HR: Disable Ethnicity Tab | SiteAppRespUser | Viewonly | No | Enabled |
| HR: Disallow Template Reference | SiteAppRespUser | Yes | ||
| HR: Display All Candidate Offers | - | - | Obsolete. | |
| HR:Display Competencies | SiteAppresp | Yes | ||
| HR:Display Brief Person Name | Site | No | No | No |
| HR:Display Person Name | SiteAppRespUser | Yes | No | Brief Name |
| HR:Display Person Search | SiteAppRespUser | Yes | No | Yes |
| HR: Display Position Hierarchy | Site | No | No | No |
| HR:Employee Directory Global Menu | Site | No | No | Employee Directory Global Menu |
| HR: Employment View Layout | SiteAppRespUser | Yes | No | FORM or TABLE |
| HR:Enable Bank Branch Validation | SiteAppRespUser | Yes | No | Null |
| HR: Enable Initiator to Delete a Pending-Approval Transaction | SiteAppRespUser | Yes | No | No |
| HR:Enable Security for Batch Element Entry | SiteAppRespUser | Yes | Yes | |
| HR: Enable DTW4 defaulting
Note: This profile option is US legislation specific profile related to tax rules and works with Full HR only. |
Site | Viewonly | No | Yes |
| HR:Enable Multiple Assignments in SSHR | SiteAppRespUser | Yes | No | No |
| HR:Enforce Costing Mandatory Segment Check at Data Entry | SiteAppRespUser | Yes | Default is Null. This is interpreted by the application as No. | |
| HR:Execute Legislative Check Formula within Run | SiteAppRespUser | Yes | No | NA |
| HR: Expand Role of Contingent Worker | Site | Yes | Yes | Default is Null. This is interpreted by the application as No. |
| HR: Extension Agent | SiteUser | No | No | |
| HR: Extension Agent Client Timeout | Yes | No | NA | |
| HR: Extension Agent Enabled | Site | No | Yes (if using Info online) | No |
| HR: FastFormula Debug Level | SiteAppRespUser | Yes | NA | NA |
| HR: Free text school name allowed in Self Service | SiteAppRespUser | Yes | No | Null |
| HR:French HRMS check mandatory payroll assignment attributes exist | SiteAppRespUser | Yes | Yes | |
| HR: FTE Factor | ||||
| HR: GL Cost Center Org Classifications | Site | Viewonly | Yes (if you want to use Auto Orgs to synchronize GL cost centers with HR) | None |
| HR: GL Cost Center Synchronization Options | Site | Viewonly | No - This profile option is obsolete. | NA |
| HR: GL Organization Name Format | Site | Viewonly | Yes (if you want to use Auto Orgs to synchronize GL cost centers with HR) | NA |
| HR:Global Competence Flex Structure | Site | Viewonly | Yes (if you want to create global competencies) | NA |
| HR:Grade Key Flex-Identify 1st Segment | SiteAppResp | Yes | No | NA |
| HR:Grade Key Flex-Identify 2nd Segment | SiteAppResp | Yes | No | NA |
| HR:HR/Payroll Representative Source | Site | Viewonly | No | No default |
| HR:Hide Work Phone on Person | - | Obsolete. | ||
| HR:IE P35 Reporting Year | Site | Yes | Yes | NA |
| HR: Info Online: Open in New Window | No | No | ||
| HR: Info Online: RIA Password | SiteAppRespUser | Yes | ||
| HR: Info Online: RIA Username | SiteAppRespUser | Yes | ||
| HR: Info Online Toolbar Icon | NA | NA | No | |
| HR: Info Online: Use Field Context | SiteAppRespUser | Yes | ||
| HR: Informal Name Format | Site | No | No | NA |
| HR:Job Key Flex-Identify 1st Segment | SiteAppResp | Yes | No | NA |
| HR:Job Key Flex-Identify 2nd Segment | SiteAppResp | Yes | No | NA |
| HR: Job Level | SiteAppResp | No | No | NA |
| HR: KI Framework Version | SiteAppRespUser | Yes | Yes | Default is Null. This is interpreted by the system as Version 1. |
| HR: KI Maximum Topics and Integrations | SiteAppRespUser | Yes | No | Default is Null. This is interpreted by the system as Version 3. |
| HR: Class Name to Fetch KI Data | Site | No | Yes (if linking to Enwisen) | Default is Null. |
| HR: KI Providers Enabled | SiteRespUser | Yes | No | Default is No. |
| HR: KI User Options Enabled | SiteRespUser | Yes | No | Default is No. |
| HR: KI Topics Enabled | SiteRespUser | Yes | No | Default is Null. This is interpreted by the application as Yes. |
| HR: Enwisen Login URL | Site | No | Yes (if linking to Enwisen) | Default is Null. |
| HR: Local or Global Name Format | SiteAppRespUser | Yes | No | Local Format |
| HR: Localization in SSHR | - | - | Valid for SSHR 3.4 only. | |
| HR: Location ID | - | - | Internal use only. | |
| HR: Local Nationality | - | - | - | No default value exists, and the system administrator can set the value at any level. |
| HR:Manage Self Service Actions When Future-Dated Changes Exist | Site | No | No | Stop with an Error |
| HR:Manager Actions Menu | SiteAppRespUser | Yes | Yes | Manager Actions Menu |
| HR: Manager Appraisals Menu | SiteAppRespUser | Yes | No | Manager Appraisals Menu |
| HR: Mask Characters | SiteAppRespUser | No | ||
| HR: Metalink Integration Application | SiteAppRespUser | Yes | No | Human Resource Management Systems |
| HR: Metalink Integration Enabled | SiteAppRespUser | Yes | No | Yes |
| HR:Monitor Balance Retrieval | SiteAppRespUser | Yes | No | |
| HR:NI Unique Error or Warning | SiteResp | No | No | NA |
| HR:National Identifier Validation | SiteAppRespUser | No | No | Error on Fail |
| HR:Non-Updateable Element Set | SiteAppRespUser | Yes | No | NA |
| HR: Number Separator | Site | No | No | NA |
| HR:OAB New Benefits Model | SiteAppRespUser | Yes | No | NA |
| HR: Offers - Hiring Manager Initiation | - | - | Obsolete | |
| HR:Online Tax Forms Update Method | SiteUser | Viewonly | No | All |
| HR: Organization ID | - | - | Internal use only. | |
| HR: Override Grade Defaults | SiteAppRespUser | Yes | No | Defaults to Yes |
| HR:Payroll Payments Self-Service Enable Multiple Assignments | SiteAppRespUser | Yes | No | No |
| HR:Payroll Payments Self-Service Payment Function | SiteAppRespUser | Yes | No | |
| HR:Payroll Payments Self-Service Payments List Mode | SiteAppRespUser | Yes | No | Null |
| HR:Performance View Layout | SiteAppRespUser | Yes | No | FORM or TABLE |
| HR: Person ID | - | - | Internal use only. | |
| HR:Personal Actions Menu | SiteAppRespUser | Yes | Yes | Personal Actions Menu |
| HR:Personal Info Check Pending | - | - | Obsolete. | |
| HR: PL NI Unique Error or Warning | SiteAppRespUser | Yes | Yes | Warn |
| HR:Position Key Flex-Identify 1st Segment | SiteAppResp | Yes | No | NA |
| HR: Position Default Options for SSHR | SiteAppRespUser | Yes | Yes | Default with User Decision |
| HR:Position Key Flex-Identify 2nd Segment | SiteAppResp | Yes | No | NA |
| HR:Propagate Data Changes | Site | Yes | No | Default is Null. This is interpreted by the application as No. |
| HR:Purge Element Entry Permission | SiteAppRespUser | Viewonly | NA | NA |
| HR:Query Only Mode | SiteAppRespUser | Viewonly | No | NA |
| HR: Refresh Self Service Actions with Data from Intervening Actions | No | No | No | No |
| HR: Restrict Letter by Vacancy or Event | Site | Viewonly | No | Default is Null |
| HR:Restrict Transactions across Legislations for SSHR | SiteResp | No | No | No |
| HR: RIA Integration Enabled | SiteAppRespUser | Yes | No | Yes |
| HR:Run BENMNGLE When Processing a Self Service Action | Site | No | No | No |
| HR:Salary View Layout | SiteAppRespUser | Yes | No | FORM or TABLE |
| HR: Save and Stay in Appraisals Page | SiteUser | Yes | No | Yes |
| HR: Schedule Based Absence Calculation | SiteResp | No | ||
| HR: Security Profile | SiteResp | No | Yes | Default view-all security profile at Site level |
| HR: Self Service HR Licensed | Site | No | No | Defaults to No |
| HR:Self Service Hire and Placement Default Values | SiteAppRespUser | No | Yes | |
| HR:Self-Service Save for Later | Site | No | No | Yes |
| HR: Servlet Timeout | SiteAppRespUser | Yes | No | Default is Null. This is interpreted by the system as 40 (seconds). |
| HR: SM Employee Find Work Opp Menu | Resp | No | Yes | HR_SM_EMP_PERSONAL_FUNCTIONS |
| HR: SM Manager Find Person Menu | Resp | No | Yes | HR_SM_MANAGER_FUNCTIONS |
| HR: SM Manager Find Work Opp Menu | Resp | No | Yes | HR_SM_PERSONAL_FUNCTIONS |
| HR:Subrogation | SiteAppRespUser | Yes | No | No |
| HR: Supervisor Hierarchy Usage | Site | Yes | No | |
| HR:TCA Unmerge Options | Site | No | No | In Patch Process |
| HR:Training View Layout | SiteAppRespUser | Yes | No | FORM or TABLE |
| HR: US Address Line Length | SiteAppRespUser | Yes | Yes | NA |
| HR: Use Fast Formula Based PTO Accruals | Site | No | Yes | No |
| HR:Use Global Applicant Numbering | Site | Viewonly | Yes | No |
| HR:Use Global Contingent Worker Numbering | Site | Viewonly | Yes | No |
| HR:Use Global Employee Numbering | Site | Viewonly | Yes | No |
| HR:Use Grade Defaults | SiteAppRespUser | Viewonly | Defaults to Yes | |
| HR:Use Standard Attachments | SiteAppRespUser | No | Yes | Yes at Site Level, No at Seeded Responsibility Level |
| HR:User Type | AppResp | Viewonly | Yes | NA |
| HR: Use Title in Person's full name | Site | No | NA | Yes |
| HR: Verification External Node | SiteResp | No | Yes | No default value |
| HR: View Payslip From Date for WEB (MM/DD/YYYY) | SiteAppRespUser | Yes | Yes | 01/01/1997 |
| HR:View Unpublished Employee 360 Self Appraisal | SiteAppResp | Yes | No | Default value is Null |
| HR: Views Layer Size | SiteAppRespUser | Yes | Yes | 300 pixels |
| HR:Webapps Tips Test Mode | User | Yes | No | No |
| HR: Web Proxy Host | No | |||
| HR: Web Proxy Port | No | |||
| HR: Worker Appraisals Menu | SiteAppRespUser | No | Yes | Employee Appraisals Menu |
| HR: ZA Nature of Person Mandatory at Person Level | SiteAppRespUser | Yes | No | |
| HRI: Collect Manager Snapshots | Site | No | Yes | Yes |
| HRI: Collect Open Enrollment in Progress | Site | No | Yes | No |
| HRI:DBI Chief HR Officer Named User | Site | No | Yes | No |
| HRI:DBI Force Foundation HR Processes | Site | No | Yes | No |
| HRI:DBI Link to Transaction System | Site | No | Yes | Disable Link |
| HRI:Enable Benefits Collections and Event Queue | Site | No | Yes | Yes |
| HRI:Enable Captured Events Archive | Site | No | Yes | No |
| HRI:Enable Detailed Logging | Site | No | Yes | No |
| HRI: Manager Snapshot Threshold | Site | No | Yes | 2500 |
| HRI:Multithreading Chunk Size | Site | No | Yes | 200 |
| HRI:Number of Threads to Launch | Site | No | Yes | 8 |
| HRI:Period of Service / Placement Date Start Source | Site | No | Yes | Start Date |
| HRI:Populate Assignment Events Queue | Site | No | Yes | Yes |
| HRI:Populate Supervisor Hierarchy Events Queue | Site | No | Yes | Yes |
| HRI:Populate Supervisor Status History Events Queue | Site | No | Yes | Yes |
| HRI: Workforce in Period Calculation Method | Site | No | No | Null |
| HZ: Protect HR Person Information | Site | No | No | No |
| Limit By Persons Organization | SiteAppRespUser | Yes | No | No |
| OAB: Enable Self-Service Benefits Trace | Yes | No | Null | |
| OAB:Self Registered User Responsibility | SiteAppRespUser | Yes | No | Self Registered Employee Default responsibility |
| OAB:User to Organization Link | SiteAppRespUser | Yes | No | Null |
| OAB:User to Payroll Link | SiteAppRespUser | Yes | No | Null |
| PAY: Enable Workflow for Assignment Costing | SiteAppRespUser | View only | No | Null. A system administrator can set the value at any level. |
| PAY: Display Reset Years in Payroll | SiteAppRespUser | Yes | No | No |
| PAY: Generate Periods for Tax Year | SiteAppRespUser | Yes | ||
| PAY:Statement of Earnings User Category | SiteRespUser | Yes | ||
| PER:Automatic Save | Site | Yes | ||
| PER:Navigation | Site | Yes | ||
| Personalize Self-Service Defn | SiteAppRespUser | Yes | No | No |
| PO: Services Procurement Enabled | Site | Viewonly | No | No |
| Performance Management Source Type | Site | No | Yes (if you enable automatic update of competency profiles) | NA |
| Workforce Measurement Type | Site | No | Yes |
Profile Options
Apply Assessment Competencies to Person
Controls whether HRMS updates an appraisee's competency profile automatically when an appraisal is complete. Set this option to Yes to enable automatic update of competency profiles.
AME:Installed
Determines whether Oracle Approvals Management (AME) is installed. Integrating applications such as Internet Expenses or iProcurement use this profile option to indicate if AME is installed.
AuditTrail:Activate
Determines whether the AuditTrail functionality is enabled or disabled.
When you enter or update data in your forms, you change the database tables underlying the forms you see and use. AuditTrail tracks which rows in a database table were updated at what time and which user was logged in using the form(s).
You can turn AuditTrail on or off (Yes or No). The default setting is No. You must set this option to Yes before you can audit any Oracle Applications table.
BEN:BEN HOURLY ANNUALIZATION FACTOR
Determines how to convert an hourly rate to an annual rate, and vice versa, if you want to use the Hourly activity reference period for Compensation Workbench plans. The default value is 2080 hours (8 hours * 5 days * 52 weeks).
BEN: Carry Forward Certification
Determines if benefits administrators can carry forward interim and suspended coverage created due to coverage restrictions configured for a life event when subsequent life events do not have coverage restrictions.
BEN:Benefits Preferred Currency
Controls the preferred currency in which a manager views and enters budget and worksheet distributions for the Compensation Workbench. Actual amounts are paid in the currency of the Compensation Workbench plan, not the preferred currency.
BEN: Check Enrollment Limits
Determines if the application should execute the check for minimum and maximum Plan Type in Program when an event is processed and the person cannot make elections.
BEN:Compensation Manager
Gives access to features in the Compensation Workbench that are available only to Compensation Managers.
BEN:Comp Objects Display Name Basis
Determines whether the compensation object names displayed in various application windows (both in the professional and self-service user interfaces) are based on the user's session date or the life event occurred on date.
BEN: Cross Business Group for Plan Design Copy
Controls whether a user can copy plan design data between business groups using the Plan Design Copy function. The default value for the profile option is 'Y.' If you set the value to 'N,' the user will only be able to export a plan design or copy the plan design within the business group attached to their responsibility.
Ben: CWB Approval Mode
Controls CWB Approval behavior. If you set the value to 'Y,' then the CWB Approval Mode enables you to enforce the submission and approval of all lower-level manager worksheets before higher-level managers may submit their worksheets for approval. The default approval mode allows the submission of a worksheet by a higher-level manager at any time regardless of the status of the lower-level manager worksheets.
BEN: CWB Allocation as Percent of Eligible Salary Decimals
Determines if the application displays decimals for percent of eligible salary based on allocated amounts.
BEN: CWB Budget as Percent of Eligible Salary Decimals
Determines if the application displays budgets as percent of eligible salary
BEN: CWB Budget Rows Displayed
Controls the number of rows available for display on budgetsheets, for example, if you set the profile option to 10, then managers and compensation administrators can choose to display between 1 and 10 rows on their budgetsheets.
Note: This profile option is available only in Oracle Applications Release 12
BEN: CWB Download Expire Seconds
Specifies the length in seconds available to download worksheets. The default value is 60 seconds. Increase this value if you have problems downloading large worksheets.
BEN:CWB Display Currency Type
Determines the last selected currency in Compensation Workbench for each manager. The application displays this value the next time managers log into CWB.
BEN: CWB Encrypt/Decrypt Key
Determines the key the application uses to decrypt security key information for downloaded Compensation Workbench worksheets. You can modify this key to any characters, however you must not change the key between a download and an upload.
BEN: CWB Estimated Market Price
This profile controls the estimate market price that the application uses to calculate the walk-away value of stock option grants. This is the default value of the market price that displays on the Extended Stock Option History page and Employee Stock Option History Report. Managers can override the value in CWB, which is retained for the session. However, the value defaults to the profile value upon re-login or session loss.
BEN: CWB History Type Display
Set this profile option to Extended Stock Option History for use with the Employee Stock Options Total Position Report. If you load stock history from a third party administrator into Oracle HRMS, you can use the Grant Detail Report Style of the Total Position Report to view details about grants held by individual employees.
BEN: CWB Home Plans Displayed
This determines how many plans the application displays on the home page before table navigation links display. The recommended value is 5 or more.
BEN: CWB Layout Lock Time
BEN: CWB Maximum Number of Layouts
BEN: CWB Plan Context for Reporting
Determines the Plan Name and Period that the application uses to obtain the Manager Hierarchy and Employee Information for the Reports available from the CWB Home Page. If you do not specify a Plan Name and Period, then the application uses the latest plan for which the manager is a participant. The Employee Stock Option History, and Employee Compensation History use this profile option.
BEN: CWB Spreadsheet Version
Controls the versions of MS Excel available for download of spreadsheets from CWB.
Note: This profile option is available only in Oracle Applications Release 12.
BEN:CWB Summary Level
Determines the last viewed display of the worksheet summary for each manager. The application displays this value during the next session. By default, this is set to Direct Employees.
BEN:CWB Table Population
Determines the last selected population filter on the worksheet. The application displays this value during the next session. By default, this is set to Direct Employees.
BEN: CWB Show In-Progress Compensation
Determines if the application displays in-progress salary records in Employee History. Set the new profile option to No to suppress in-progress salary records from being displayed in Employee History when managers do not or should not have access to view salary-based plans. By default, this profile option is set to Yes.
BEN: CWB Valid Grade Filtering
Determines if the application validates grades. If you set this profile to Yes (default), then the application displays only valid grades for a proposed job/position within the business group. If you set this profile to No, then the application displays all grades for the business group.
BEN: CWB Validate Performance/Assignment Changes Online
Determines if the application validates assignment changes online. If you set the profile option to Yes, then you enable assignment API edits for the worksheet and the application enforces the integrity between jobs, positions, and grades. If you set this profile option to No (default), then API edits are not online and the Compensation Workbench Post Process validates all assignment changes.
BEN: CWB Wizard Compratio Range
Determines the incremental range that displays on all pages using comparatio criteria. For example if you use 5, then the application displays comparatios in 5% ranges. The Allocation Wizard criteria option, the Employee Stock Option History report, the Employee Compensation History report, and the Summary By Directs report use this profile option. The default value is 5.
BEN: CWB Wizard Years Worked Range
Determines the incremental range that displays on all pages using Years Worked criteria. For example if you use 5, then the application displays the Years Worked in 5 Year Ranges. The Allocation Wizard criteria option, the Employee Stock Option History report, Employee Compensation History report, and the Summary By Directs report use this profile option. The default value is 1.
BEN: CWB Worksheet Rows Displayed
Controls the number of rows available for display on worksheets, for example, if you set the profile option to 10, then managers and compensation administrators can choose to display between 1 and 10 rows on their worksheets.
Note: This profile option is available only in Oracle Applications Release 12.
BEN: Designation No Change
Determines the contents of the Dependent Eligibility Audit log. If you set the profile option to No (the default value), the audit log returns information only for dependents with eligibility changes. If you set it to Yes, the audit log returns all dependents, even if they have no eligibility change.
BEN:Eligible Profile Rule
Controls how FastFormula rules are evaluated in an eligibility profile. The default value is AND. This means that a participant must satisfy all the rules you attach to an eligibility profile. If you set the profile option to OR, the participant need only satisfy one of the rules.
BEN:Enable Absence Plans Functionality
Displays the Enroll Absences button on the Absence Detail window. If you set this profile option to Yes for the users or responsibilities who will enter absences for absence benefit plans, they can run the Participation Process to process the absence life events.
BEN:Enable Quartile in Grade Life Event
Detemines whether the system triggers the Quartile in Grade Life Event when a change in a person's grade, salary basis, or salary moves them into a new quartile in grade. If you set this profile option to Yes, these conditions trigger the Quartile in Grade life event. If you set this profile option to No, the system never creates a Quartile in Grade potential life event.
BEN:Imputed Income Post Tax Deduction
Controls whether after-tax employee contributions are deducted from the imputed income total for a benefits plan subject to imputed income. If you set this profile set to N (the default value) the application assumes that the employer pays 100% of the given benefit.
BEN:Max Extract Line Size
Sets the maximum length of a record generated by the Extract Write Process for compensation and benefits system extracts.
BEN:VAPRO Rule
Controls how FastFormula rules are evaluated in a variable rate profile (VAPRO). The default value is AND. This means that a participant must satisfy all the rules you attach to a variable rate profile. If you set the profile option to OR, the participant need only satisfy one of the rules.
DateTrack:Date Security
Controls the way users can change their effective date:
-
All (users can change to any date)
-
Past (users can change to dates in the past only)
-
Present (users cannot change their effective date)
-
Future (users can change to dates in the future only)
The meaning of Past and Future here is with respect to the user's login date, which is usually today's date, but may be set to another value by the DateTrack:Login Date profile option.
See: How DateTrack Works, Oracle HRMS Implementation Guide
DateTrack:Enabled
Controls whether the DateTrack functionality is enabled. Set to Yes at the Application level for Oracle HRMS.
Important: This profile option applies to Full HR only. If you are installing Shared HR, the profile option value must be set to No.
See: How DateTrack Works, Oracle HRMS Implementation Guide
DateTrack:Login Date (YYYY/MM/DD)
Defines the log-in date for a user. Normally a user logs onto the system with an effective date of today's date. Use this profile option to change a user's default date to another date. This profile option works in conjunction with DateTrack:Date Security. For example, if a user has DateTrack:Date Security set to Future and DateTrack:Login Date set to 1900/01/01, they can change their effective date to any date after January 1 1900, but not before.
DateTrack:Reminder
Determines whether the Decision window appears when you open a window in which you can enter, update, or delete datetracked information. Notice that the Decision window never appears on windows where you can query datetracked information but not update it. There are three possible values:
-
Always (the window always appears)
-
Never (the window never appears)
-
Not Today (the window appears only if the effective date is not the system date)
Disable Self-Service Personalizations
Controls whether personalizations created for self-service functions using the Personalization Framework are applied. If the profile option is Yes, no personalizations are applied and only the original definition of each self-service page is displayed.
This profile option is used in SSHR.
Enable Security Groups
Controls whether you use multiple security groups. There are three possible values for the profile:
-
No - If using standard security
-
Y - If using multiple security groups
-
Hosted - Reserved for use by VPD Hosting implementations
Change the profile option to Yes at application level only if your enterprise is implementing a Security Groups Enabled system (multiple security groups). If you change the profile option to Yes, you must run the Enable Multiple Security Groups process. See Security Models.
Important: Once you have changed to Security Groups Enabled Security you cannot revert to the Standard Security model.
Note: Non-HRMS applications do not support multiple security groups in Release 11i.
Flexfields:Open Descr Window
Determines whether a descriptive flexfield window automatically opens when you navigate to the corresponding field.
Set the profile option to Yes if you want the flexfield to pop open automatically. If you set this option to No, you can open the flexfield by choosing Edit Field from the Edit menu or pressing CTRL+L.
Flexfields:Open Key Window
Determines whether a key flexfield window automatically opens when you navigate to the corresponding field.
Set the profile value to Yes if you want the flexfield to pop open automatically. If you set this option to No, you can open the flexfield by choosing Edit Field from the Edit menu or pressing CTRL+L.
GHR: Allow Ex-Emp Purge
This profile option is applicable to Oracle US Federal Human Resources only.
Use this profile option to determine whether data related to separated or ex-employees can be removed from the database. If the value is set to Yes, then when the system administrator runs the Ex-Employees Report/Purge process after selecting the Purge option, the application removes all data that is associated with separated or terminated employees.
See: Running the Ex-Employees Report/Purge Process
Help Localization Code
Controls which set of help files are linked to each responsibility. If you accept the default value, then the set of help files for Global HRMS will be associated with the responsibility. However, if you want to specify a legislative or vertical variant of HRMS, then you must set the Help Localization Code as shown in the following table:
| Help Localization Code | Localization |
|---|---|
| AE | UAE |
| AU | Australia |
| BE | Belgium |
| CA | Canada |
| CN | China |
| DE | Germany |
| DK | Denmark |
| ES | Spain |
| FD | US Federal |
| FI | Finland |
| FR | France |
| HK | Hong Kong |
| HU | Hungary |
| IE | Ireland |
| IN | India |
| IT | Italy |
| JP | Japan |
| KR | Korea |
| KW | Kuwait |
| MX | Mexico |
| NL | Netherlands |
| NO | Norway |
| NZ | New Zealand |
| PL | Poland |
| RU | Russia |
| SA | Saudi Arabia |
| SG | Singapore |
| SE | Sweden |
| UK | UK |
| US | US |
| ZA | South Africa |
Note: These entries must be in upper case.
HR: Absence Duration Auto Overwrite
Controls whether the absence duration formula automatically recalculates the duration of an absence when the date or time of the absence is changed. Set the profile option to Yes if you have created an absence duration formula (or one is supplied by your localization team) and you want absence durations to be recalculated automatically.
See: Absence Recording, Oracle HRMS Compensation and Benefits Management Guide
HR: Absence View Layout
Controls whether a manager sees the Detail Summary View in a Form or Tabular Format.
This profile option is used in SSHR.
HR: Access Non-Current Employee Data
Controls the display of records of ex-employees and future dated employees. Set the profile option value to Yes to enable HR users to view data of ex-employees and future dated employees if you are using user-based security.
Note: This profile option does not apply to security profiles based on the supervisor hierarchy. You can use this profile option if your security profiles are based on user-based organization security, or user-based position security, or user-based custom security. For information on user-based security, see: Security Profiles
HR: Accrual Plan Element Set Displayed to User
Enables the display of accrual balances in the SSHR Leave of Absence page, when you attach the required element set to this profile at the appropriate levels.
See: Viewing Accrual Balances in SSHR, Oracle SSHR Deploy Self-Service Capability Guide
HR:Action Parameter Group Name
Identifies the set of action parameter values for all payroll processes supported by the Action Parameter group. You use action parameter values to control the process run, for example, to enable parallel processing, to control the number of API batch calls, and to specify the number of errors allowed before the process run fails.
See: Maintaining Parameters and Parameter Groups for Payroll Processes, Oracle HRMS Implementation Guide
HR: Actions - Validation
Controls the point at which the application runs validation checks for Pending workflow transactions within SSHR. The validation can be carried out using one of the following options:
-
All actions are validated
-
Only the preselected action is validated. The other actions are validated after selection.
-
All actions are validated after selection.
This profile option is used in SSHR.
HR:Allow Approver Updates to Self Service Actions
Controls whether an approver can make updates to self-service actions. The self-service actions functionality uses Oracle Approvals Management (AME) to determine the list of approvers for the action. If you set this profile option to No, the approver can approve or reject the action or return the action to a previous approver on the chain after receiving the workflow notification. If you set this profile option to Yes, the approver can also update the action, for example, change the effective date.
See: Approving a Self-Service Action, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Allow Concurrent Self Service Actions
Controls whether Oracle SSHR can process multiple actions on a selected person at the same time. If you set this profile option to No, the Pending column is displayed on the Actions page. This indicates to the user whether pending transactions are present. The user can then review the pending transaction. If you set the profile option to Yes, you allow multiple simultaneous self-service actions. This means that the Pending column is not displayed, and users can perform actions against all assignments. On final approval, each action takes effect on its own effective date, superseding any actions with a previous effective date.
See: Managing Conflicting Actions, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Allow Functions Access During Hrglobal Run
Set this profile option to Yes to enable access to HRMS responsibilities during an hrglobal run.
HR:Allow Online W-2 Viewing as of MM/DD
Enables your employees to view and download their online W-2 statements as PDF files. You specify the month and day from when the employees can view the W-2 statements for the current year.
See: Tax Information Form (W-2) (US), Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Allow Processing of Ineligible Self Service Actions
Controls whether self-service users, usually managers, can process ineligible self-service actions. If you set the profile option to Yes, users can process actions for which a selected person is not eligible. They may wish to do this if the action will become eligible by its effective date.
Note: This option depends on also enabling the profile option HR:Allow Use of Eligibility for Self Service Actions in order to display ineligible actions in the first instance.
See: HR:Allow Use of Eligibility for Self Service Actions
See: Set Up Eligibility Processing, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Allow Use of Eligibility for Self Service Actions
Controls whether the Eligibility column is displayed on the Actions page for self-service actions. If you set this profile option to Yes, both eligible and ineligible actions are displayed on the Actions page along with the Eligibility column. The Eligibility column distinguishes between eligible and ineligible actions.
If you set this profile option to No, the Actions page only displays eligible actions and the Eligibility column is not displayed.
Note: Managers will not be able to process ineligible actions unless the profile option HR:Allow Processing of Ineligible Self Service Actions is also set to Yes.
See: HR:Allow Processing of Ineligible Self Service Actions
See: Set Up Eligibility Processing, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR: Applicant Assignment Cleanup Run Mode
Controls how the HR Applicant Assignment Cleanup script (delivered in PER Family Pack J) is run.
See: Guide to the HR Applicant Assignment Cleanup Process (available on My Oracle Support Note ID 295319.1)
HR:Applications View Layout
Enables a manager to see the Detail Summary View in a Form or Tabular Format.
This User Profile Option is used in SSHR.
HR: Appraisal Template LOV
Controls whether the Appraisal Template field in V3.4 of the SSHR Appraisals function is available as a list of values (LOV) or a poplist. Set this profile option to Yes to display the field as an LOV or set it to No to display the field as a poplist.
This profile option is used in SSHR 3.4.
HR: Appraisee Can Add Participants
Controls whether appraisees can add participants to their appraisals. If yu set this profile option to Yes (the default value), appraisees can add participants. If you set this profile option to No, appraisees cannot add participants.
See: Appraisals (Self-Service), Oracle SSHR Deploy Self-Service Capability Guide
HR: Authoria Integration Enabled
Controls whether conext-sensitive links to the third-party information product Authoria HR are enabled. If you are using context-sensitive links from a button on the Oracle toolbar to Authoria HR, set this profile option to Yes to enable the integration, or No to disable the integration. If you set this option to No, the 'Info Online' toolbar button does not link to Authoria HR from the applicable windows, and hyperlinks do not appear in the applicable self-service pages.
See: Info Online Links to Authoria HR, Oracle HRMS Configuring, Reporting, and System Administration Guide
HR: Authoria UK URL
Defines the URL of the Authoria HR engine providing UK-related content if you are using context-sensitive links from a button on the Oracle toolbar to the third-party information product Authoria HR.
See: Configuring Links Between Oracle Standard and Advanced Benefits and Authoria HR, Oracle HRMS Configuring, Reporting, and System Administration Guide
HR: Authoria US URL
Defines the URL of the Authoria HR engine providing US-related content if you are using context-sensitive links from a button on the Oracle toolbar to the third-party information product Authoria HR.
See: Configuring Links Between Oracle Standard and Advanced Benefits and Authoria HR, Oracle HRMS Configuring, Reporting, and System Administration Guide
HR: Auto Apply Collective Agreement Entitlements
Controls whether values calculated for a collective agreement during the entitlement evaluation process are applied automatically to an employee. For each entitlement item, the most beneficial value that the employee is entitled to is applied. Instances where the application cannot automatically establish the most beneficial value are noted in the log file and you can manually make a selection using the Collective Agreement Entitlements window.
See: Collective Agreement Administration, Oracle HRMS Enterprise and Workforce Management Guide
HR: Auto Evaluate Collective Agreement Entitlements
Controls whether the entitlement evaluation process is run automatically when an employee is first placed on a collective agreement.
See: Collective Agreement Administration, Oracle HRMS Enterprise and Workforce Management Guide
HR:Automatically Synchronize Single GL Company Cost Centers with HR
Controls whether the Synchronize Single GL Company Cost Centers with HR concurrent program runs automatically following the creation of a new GL account code combination. You use this profile option if you have set the HR: Generate Organizations from GL profile so that organizations are automatically created in HR based on GL cost centers.
See: Implementing Automatic Company Cost Center Creation, Oracle HRMS Enterprise and Workforce Management Guide
HR: Base Salary Required
Controls whether the Description and Salary fields are mandatory if a person's assignment has a salary basis assigned but no pay proposal. If you set this profile option to Yes, the fields are mandatory. The user must enter values for these fields.
HR: BIS Job Hierarchy - Job Grouping Level 1
Defines the value set that represents the first level job grouping in the Job Hierarchy. Ensure that the value set you select is associated with a Job Key Flexfield structure, otherwise the Job Hierarchy will not use it.
See: Structuring the Job Hierarchy, Oracle HRMS Deploy Strategic Reporting (HRMSi)
HR: BIS Job Hierarchy - Job Grouping Level 2
Defines the value set that represents the second level job grouping in the Job Hierarchy. Ensure that the value set you select is associated with a Job Key Flexfield structure, otherwise the Job Hierarchy will not use it.
See: Structuring the Job Hierarchy, Oracle HRMS Deploy Strategic Reporting (HRMSi)
HR:Blank Effective Date
Controls the default value of the effective date field on the Effective Date page that appears at the start of a self-service action. When you set this profile to Yes, the effective date field is blank. When you set it to No, the page displays the default date.
The default date can differ, depending on:
-
Future-dated changes for the person whose record you are updating
-
The value of the profile HR:Manage Self Service actions when future-dated changes exist
The default date is usually the system date. The default date is the effective date of the future change if (1) you do not enable managing actions and (2) future-dated changes exist.
HR:Business Group
This profile option determines the business group linked to a responsibility. The Setup Business Group is defaulted at Site level.
If you use Standard HRMS security this option is automatically set up when you enter the HR: Security Profile profile option, except in cases where you are using a global security profile (that is, a security profile that does not specify a business group). In this case, you must specifically set up this option for each responsibility.
If you use Security Groups Enabled security, this option is not user-configurable. The business group is determined when you create a security profile assignment using the Assign Security Profile window.
HR: Cancel Application
This profile option enables you to delete an applicant's record that has been entered in error. The default value is set to Null, this is interpreted as No and the function will not work.
HR: Check Entitlement Cache
This profile option is supplied primarily for Oracle Development or Third Party Suppliers to use. It currently has no impact on delivered functionality.
This profile option enables you to control whether the entitlement evaluation process first looks to see if a value for a particular entitlement exists in the cache before re-evaluating.
HR: Collective Agreement Logging
This profile option enables you to control whether the log file generated during the entitlement evaluation or entitlement population processes shows high or low detail. This profile only affects the processed that run from the Entitlement Results window, The log generated when you run the Collective Agreement Entitlement Evaluation process from the Submit Requests window always displays high detail and is not affected by this profile option.
HR:Contingent Worker Manager Actions Menu
Controls which Manager Actions menu SSHR displays for managers who are also contingent workers. If you create a custom Manager Actions menu for contingent workers, you must change this profile option to point to your custom menu.
See: Actions, Oracle SSHR Deploy Self-Service Capability Guide
HR:Contingent Worker Personal Actions Menu
Controls which Personal Actions menu SSHR displays for users who are also contingent workers. If you create a custom Personal Actions menu for contingent workers, you must change this profile option to point to your custom menu.
See: Actions, Oracle SSHR Deploy Self-Service Capability Guide
HR: Copy Period Details for Budget
You use this user profile option for HRMS budgets. When you set the profile option to Yes, the application copies all budget details (budget periods, budget sets, and funding sources) to a new budget worksheet when the worksheet is a copy of an existing budget version.
HR:Cross Business Group
Controls whether users of some HRMS windows can see certain information for more than one business group.
For example, when defining contacts, you can see contacts in one business group, even if they have been created in another. Similarly, when nominating a supervisor for a person, you can select a supervisor from another business group.
In addition, if you set this option to Yes, it:
-
Enables users to select benchmark jobs from other business groups
-
Checks for the uniqueness of job names across all business groups and issues a warning if you attempt to enter a non-unique name
-
Enforces that there can only be one master job group
-
Enables users to create global competencies and rating scales
-
Controls whether users can select people from other business groups in the following fields in HRMS windows:
-
Absence: authorizing person, replacement person
-
Applicant Assignment: recruiter, supervisor, referred by
-
Assignment: supervisor
-
Organization Manager Relationship: manager - also controls whether organizations from other business groups are available.
-
Events: event participants, internal contact person
-
Employee review: reviewers
-
Requisitions and Vacancies: requisition raised by, recruiter
-
Recruitment Activity: authorized by, internal contact
-
Termination: accepted by
-
This profile option also controls the filtering of HRMS secure views. If you set this profile option to Yes, secure views display data across all business groups. If you set this profile option to No, the views filter data by the business group of the current security profile.
Note: If you have built custom code that references HRMS secure views, the setting of the HR: Cross Business Group profile option may affect the functionality of your code.
Set to Yes if users need to see this information across all business groups. Set to No if users only work with the information defined for one business group. The default is No.
HR: Cross BG Duplicate Person Check
Controls the duplicate person check functionality across multiple business groups in Oracle HRMS and Oracle SSHR. Set to Yes to enable the duplicate person check functionality across business groups. Oracle HRMS uses the global name format to search for duplicate person records across business groups.
Note: To use the HR: Cross BG Duplicate Person Check profile option, you must also enable the HR:Cross Business Group profile option.
For information about the global name format (Global List Name), see: Person-Name Formats, Oracle HRMS Workforce Sourcing, Deployment, and Talent Management Guide
The following table explains the searches that Oracle HRMS performs when you set up the HR: Cross BG Duplicate Person Check and HR:Cross Business Group profile options.
| Value set for HR:Cross Business Group | Value set for HR: Cross BG Duplicate Person Check | Records that Oracle HRMS searches to identify duplicate person records |
|---|---|---|
| No | No | HR tables in a business group. The application uses the last name, first name, date of birth, or national identifier values to search in HR tables. |
| No | Yes | HR tables in a business group. The application uses the last name, first name, date of birth, or national identifier values to search in HR tables. |
| Yes | Yes | HR tables in all business groups and TCA (Trading Community Architecture) tables. The application uses the global name format to search in HR tables. |
| Yes | No | The application does not search for duplicate person records either across multiple business groups or in a single business group. |
HR: CWK in Head Count Reports
Determines whether contingent workers are included in head-count reports. The default value is Yes. Set this option to No to exclude contingent workers from head-count reports.
HR: Data Exchange Directory
This profile option is used by Data Uploader and other areas of the system which need to read or import files. Set this profile to the full path for a directory accessible to the Oracle database. Files stored in this directory can then be accessed by Oracle HRMS.
HR: Data Migrator Business Group Lockout
This profile option is for a future release.
HR:Data Pump Action Parameter Group
Data pump may now be configured using action parameter groups instead of the default action parameters. This configuration enables data pump configuration to be separate to that of payroll processes that share action parameters (e.g. the THREADS action parameter) with Data Pump. You can use the HR:Data Pump Action Parameter Group profile option to specify the default action parameter group to use for Data Pump action parameters. HRMS also provides an extra concurrent program parameter to enable the action parameter group to be changed for the Data Pump run.
The default value for this profile option is Null and it is treated as Null in the code (the default action parameter group).
HR:Default Assignment Costing
Set this profile option to Yes to enable default costing for position assignments. For position control budgets, the default value is the proportional value for the budget. You can write a FastFormula to override the budget value with other costing segments and proportions.
HR:Default Check/Cheque Number Method
Use this profile option to set the automatic check/cheque number process. You can set this profile with the Organization Payment Level value to enable automatic check/cheque numbering. This profile option is for US and Canadian Payroll only.
HR: Default Correspondence Language
Specifies a default language for the Correspondence Language field.
This profile option is for users of the Italian legislation only.
HR: Default Full Name Format
Controls the default value for the full name format.
This profile option is for users of the Dutch legislation only.
HR: Default Nationality
Defines the default nationality for a user. When a new person is entered in the People window, the nationality entered here is automatically displayed in the Nationality field.
HR: Defer Update After Approval
Defers save of SSHR transactions after the final approval. The transaction is saved automatically when the Workflow Background Proces runs.
This applies to Self Service.
HR: Disable Ethnicity Tab
Enables you to disable the ethnicity tab in the People window.
This profile option is for users of the Dutch legislation only.
HR:Display Competencies
Controls the display of competencies in an Advanced Search. It is used to control the display of skill categories in:
-
Apply for a Job
-
Enroll in a Class
This User Profile Option is used in SSHR.
HR:Display Brief Person Name
By default this profile option is set to Brief Name, which means that on the Enter Process pages, employee names are displayed in brief format. If you prefer to see the full employee name, set this profile option to Full Name.
HR: Display Position Hierarchy
If set to Yes position hierarchy will be used in the HGrid on the Enter Process page in SSHR. By default the HGrid uses supervisor hierarchy.
HR:Employee Directory Global Menu
Enables you to specify a menu to provide global buttons in addition to the standard Self Service Global Menu buttons if a user accesses the Employee Directory anonymously. You can specify any menu with the menu type Global Menu.
See: The Employee Directory Module, Oracle SSHR Deploy Self-Service Capability Guide
HR: Employment View Layout
Enables a manager to see the Detail Summary View in a Form or Tabular Format.
This User Profile Option is used in SSHR.
HR:Enable Bank Branch Validation
Set this profile option to Yes to turn the Sort Code validation on and off. Sort Code will only appear for territories, for example GB, where branch code validation is supported. You disable the validation if you don't set this profile option or set it to N.
Note: Note: As this profile option is a global profile option, you should take care in a multi-territory Oracle HRMS implementation not to set it on with too wide a scope.
HR: Enable DTW4 defaulting
This profile option is for use by US and Canadian customers who use Vertex geocodes data to validate US and Canadian addresses. It enables or disables the defaulting of DTW4 employee tax data when an employee primary address or work address is changed. For example, set this option to No to prevent DTW4 data from being defaulted when an employee address is changed to an overseas address.
The default is Yes. This option can be set at site level only.
Important: This profile option is US legislation specific profile related to tax rules and works with Full HR only. If you are installing Shared HR, the profile option must be set to No.
HR: Enable Multiple Assignments in SSHR
Controls whether a manager can view and update multiple assignments for an employee in SSHR. If you set the profile option to Yes, all the assignments of a person are displayed on the Hierarchy page. If you set the profile option to No, only primary assignments are displayed.
See: People in Hierarchy, My List, and Search Pages, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR: Enable Initiator to Delete a Pending-Approval Transaction
Determines whether managers or workers can delete any transactions that they have initiated before approval in Oracle SSHR. If you set this profile option to Yes, then the initiator of the transaction can view the transaction in the list of Pending-Approval action items or in the All Actions Awaiting Your Attention table, and use the Delete icon to remove that transaction. The default value is No.
For information about the delete transactions pending approval functionality, see: Self-Service Functionality, Oracle Self-Service Human Resources Deploy Self-Service Capability Guide
HR: Enable Security for Batch Element Entry
Enables you to prevent unauthorized viewing and updating of batch lines for a confidential assignment by setting the profile option to Yes.
HR: Enforce Costing Mandatory Segment Check at Data Entry
Set this profile option to Yes to specify that users must enter a value for a mandatory costing segment at each costing level where it is qualified.
HR: Execute Legislative Check Formula within Run
Determines whether the legislation-specific check is performed during a payroll run.
HR: Expand Role of Contingent Worker
Determines whether you can select contingent workers to perform many of the roles fulfilled by employees. For example, if you set this option to Yes, you can select a contingent worker to be a supervisor in the Assignment window and an authorizer in the Absence window.
You can select a contingent worker to fulfill the following roles:
-
Supervisor
-
Recruiter
-
Interviewer
-
Cost center manager
-
Reviewer
-
Event attendee
-
Termination authority
-
Manager
-
Preparer
-
Requester
-
Approver
-
Buyer
HR: Extension Agent
If you are using Info Online to allow users to access to information provider web sites from a button on the Oracle toolbar, use this profile option to launch dynamic content via a web server different from the one specified by the Applications Servlet Agent.
HR: Extension Agent Client Timeout
If you are using Info Online to allow users to access information provider web sites from a button on the Oracle toolbar, this profile sets the maximum time in seconds that the system waits to contact the web server mediating the connection to Authoria HR.
You should not set this value unless asked to do so by Support.
HR: Extension Agent Enabled
If you are using Info Online to allow users to access information provider web sites from a button on the Oracle toolbar, this profile option controls whether or not the feature is enabled for a user or group of users. Set to Yes to enable the feature and display the Info Online button on the Oracle toolbar. Set to No to disable the feature and hide the button.
This is similar to the way that Applications Help Web Agent acts as an override to the default.
HR: FastFormula Debug Level
Enables debugging information to be output from the FastFormula compiler and execution engine.
HR: Free text school name allowed in Self Service
If this profile option is set to No, the user will not be able to enter text freely for the school name. Instead their entry will be restricted to a list of values. If the profile option is set to Yes they can enter free text, or choose from the list of values.
HR:French HRMS check mandatory payroll assignment attributes exist
Determines whether to perform the mandatory checks for establishment, contract, and employee category attribution on payroll assignments when your business group is French.
HR: FTE Factor
Determines the FTE (Full Time Equivalent) factor that the application uses to calculate full-time annual pay. You can set the option to:
-
Budget Full Time Equivalent - if you select this, then the application determines the FTE based on the information in the FTE factor unit in the Budgets region of the Person Assignment window.
-
Budget Percent of Full Time - if you select this, then the application determines the FTE based on the information in the Head Count factor unit in the Budgets region of the Person Assignment window.
-
No Conversion - if you select this, then the application uses an FTE factor of 1 so that no conversion occurs. This is the default value.
-
Normal Hours/Business Group Working Hours - if you select this, then the application determines the FTE based on the information in the Working Hours fields in the Standard Conditions region of the Person Assignment window. To calculate FTE, the application divides the person's working hours by the business group's working hours.
HR: GL Cost Center Org Classifications
This profile option defines which organization classifications are created when you synchronize your GL cost centers with your organizations in HRMS. It has the following settings:
-
None
-
Company Cost Centers
-
HR Organizations and Company Cost Centers
HR: GL Cost Center Synchronization Options
This profile option is obsolete.
HR: GL Organization Name Format
This profile option enables you to define the name format for organizations created automatically in HRMS based on a GL cost center.
HR:Global Competence Flex Structure
Defines the competence key flexfield structure for use when creating global competencies. If you do not set this option, then you cannot create global competencies.
HR:Grade Key Flex-Identify 1st and 2nd Segments
These options are used to control which two segments of the key flexfields appear in Person Search.
This profile option is used in SSHR.
HR: HR/Payroll Representative Source
SSHR offers three methods for determining an organization's default payroll representative:
-
From Payroll (Further Payroll Information).
-
From GRE (Organization Information).
-
From custom (PL/SQL) code.
This profile option is used in SSHR.
HR:IE P35 Reporting Year
Determines the tax year for which you want to report the P35. If you do not set this option, you cannot report P35.
HR: Info Online: Open in New Window
If you are using Info Online to allow users to access information provider web sites from a button on the Oracle HRMS toolbar, this profile option controls whether the results are displayed in a separate browser window each time the user follows a link. Set to Yes to open a new window for each link followed; set to No to use the same window for each link.
HR: Info Online: RIA Password
If you are using Info Online to allow users to access the third party information product RIA from a button on the Oracle toolbar, this profile option controls the single sign-on capability between Oracle and RIA. Enter a valid password at user level.
Note: If you change your password on PCP then you must also update this user profile option.
HR: Info Online: RIA Username
If you are using Info Online to allow users to access the third party information product RIA from a button on the Oracle toolbar, this profile option controls the single sign-on capability between Oracle and RIA. Enter a valid username at user level.
HR: Info Online Toolbar Icon
If you are using Info Online to allow users to access information provider web sites from a button on the Oracle toolbar, you can optionally use this profile option to identify an alternative icon for the Info Online toolbar button.
The image file should be in GIF format with the following attributes:
-
Size: 18x18 pixels
-
Transparent background colour RGB:192,192,192 (grey)
-
216 colour depth
Place the file in the virtual directory (relative to the web server used to start forms):
/OA_JAVA/oracle/apps/media
In most installations this would be the directory:
$JAVA_TOP/oracle/apps/media.
HR: Info Online: Use Field Context
If you are using Info Online to allow users to access information provider web sites from a button on the Oracle toolbar, this profile option narrows the search using predefined contexts associated with your current field and window.
Set to Yes to use the predefined contexts to narrow the search; set to No to display a list of all predefined options that are available from the selected window.
HR:Informal Name Format
Use this profile option to define the way a person's name appears in your workflow notifications. If you do not set the HR: Informal Name Format profile option, the application uses the default name structure.
Use the following values:
-
$FI - First Name
-
$MI - Middle Name
-
$LA - Last Name
-
$PR - Prefix
-
$SU - Suffix
-
$TI - Title
-
$FU - Full Name
-
$KN - Known As
-
$IF - Initial First
-
$IM - Initial Middle
HR:Job Key Flex-Identify 1st and 2nd Segments
These options are used to control which two segments of the key flexfields appear in Person Search.
This profile option is used in SSHR.
HR: Job Level
The job level options are used to determine the seniority of a person's job. You can set a default for the job level at Site, Application and Responsibility level.
HR: KI Framework Version
If you are using Info Online to allow users to access information provider web sites, use this profile to set the version of Knowledge Integrator Framework.
HR: KI Maximum Topics and Integrations
If you are using Info Online to allow users to access information provider web sites, use this profile to set the maximum number of topics or providers to display in the Content Container before the More link appears.
HR: Enwisen Login URL
Defines the URL of Enwisen web site, a third-party information provider that end users can access from Oracle iRecruitment, Oracle Performance Management, Oracle SSHR, and Oracle Time and Labor pages.
See: Info Online Links to Information Provider Web Sites
HR: KI Providers Enabled
If you are using Info Online to allow users to access information provider web sites, then this profile option controls the Providers region in the Info Online content container. Set to Yes to display the Providers region.
See: Info Online Content Container
HR: KI Topics Enabled
If you are using Info Online to allow users to access information provider web sites, then this profile option controls the Topics region in the Info Online content container. Set to Yes to display the Topics region.
See: Info Online Content Container
HR: KI User Options Enabled
If you are using Info Online to allow users to access information provider web sites, then this profile option controls the User Options region in the Info Online content container. Set to Yes to display the User Options region.
See: Info Online Content Container
HR: Class Name to Fetch KI Data
Use this profile option to implement additional security when accessing Enwisen, a third-party information provider. The value for this profile option must be a fully qualified name of a Java class that implements Oracle's predefined Java interface: oracle.apps.per.ki.kiserver.KIDataFetcher. The Java class contains the method to retrieve login values when end users access Enwisen from Oracle HRMS product pages.
See: Configuring Links between HRMS Products and Enwisen, Oracle HRMS Configuring, Reporting, and System Administration Guide
HR:Local Nationality
Use this profile to set a value for nationality. This profile option is for users of the Saudi Arabia Payroll only.
The system administrator sets this option at any level of standard Security hierarchy type - Site, Application, Responsibility, and User.
The system administrator must enter a nationality code, available in the user defined-lookup_type, NATIONALITY. You cannot run the payroll until you set this profile option. If you attempt to run payroll before setting this option, the application will display an error message.
HR: Localization in SSHR
Identifies the localization for SSHR. This profile option is only valid for SSHR releases prior to SSHR 4.0.
HR: Local or Global Name Format
Determines whether the user sees person names in local or global formats. The value Local Format enables users to display names in a character set appropriate to their legislation. The value Global Format enables users in multinational enterprises, which generally use multiple character sets, to display person names in a single (typically, Western) character set. This option applies to the supplied Display Name and List Name formats, to edited versions of those formats, and to user-defined format masks.
HR: Make National Identifier Optional
Enables recording employee information without entering the SOFI Number in the Person window, the People Management Templates, and the Self-Service page. To make entering the BSN/SOFI Number optional, set this option to Yes. To make it a mandatory field, set this option to No.
HR:Manage Self Service Actions When Future-Dated Changes Exist
Controls potential data conflicts if future-dated changes exist for self-service actions. If you have set the profile option HR:Allow Concurrent Self Service Actions to Yes, this profile option allows you to determine how SSHR processes the actions.
The default value for the profile option is Stop with an Error. This forces the user to choose an effective date subsequent to any future-dated change.
If you change the profile option to Allow Approval (Notify HR Rep), you allow the user to select a date prior to any future-dated changes. After final approval, the transaction is forwarded to an HR Representative for review and manual entry into the database.
Important: If you are setting this profile option to Allow Approval, and you have enabled HR:Allow Approver Updates to Self Service Actions, Oracle recommends that you also enable HR:Refresh Self Service Actions with Data from Intervening Actions.
See: Managing Conflicting Actions, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Manager Actions Menu
Controls which actions menu is displayed for managers within SSHR. If you create a custom Manager Actions menu, you must change this profile option to point to your custom menu.
See: Actions, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR: Manager Appraisals Menu
Controls the types of appraisal a manager can initiate (for example, Standard, 360 degree) from the Appraisals home page.
HR: Mask Characters
Use this profile option to set the number of characters or digits to display in numbers such as bank account or credit card numbers. Enter a positive number of digits to display from the back (for example, xxxx345) or a negative number of digits to display from the front (for example, 123xxxx).
HR: Metalink Integration Application
Use this profile option to select the first MetaLink page that appears when you choose the Info Online toolbar button in an HRMS window. You can select a page for a specific application (for example, Human Resources or Payroll), or you can add your own choice of pages to the list using the HR MetaLink Application lookup.
HR: Metalink Integration Enabled
Set this profile option to Yes to enable links from Oracle HRMS windows to MetaLink via the Info Online toolbar button. Set to No to disable the links.
HR:Monitor Balance Retrieval
This profile enables the Monitor Balance Retrieval Debug Tool, which allows you identify database items associated with the values held in the latest balance tables, in order to reference them in the formula called by the payroll run. Set to Yes to enable monitoring, or No to disable monitoring.
HR: NI Unique Error or Warning
Enables you to change the default warning to an error message.
If you want to warn users that the national identifier they have entered already exists, leave the default as warning. If you want to prevent a user entering the same national identifier more than once, you can change the message to an error. This stops the user entering the same national identifier.
HR: National Identifier Validation
Enables you to define the validation that is used for a national identifier. There are three possible values:
-
Error on Fail (default value). If a user enters an invalid national identifier, an error message is displayed and the user cannot save the national identifier until they have entered it in the correct format.
-
Warning on Fail. If a user enters an invalid national identifier, a warning is displayed, but the user can save the national identifier.
-
No Validation. A user can enter and save the national identifier in any format. No validation is performed and no message is displayed.
HR:Non-Updateable Element Set
Select a customization element set to define the element entry values that are view-only on the Element Entries window. Typically you use this user profile option to prevent updates to elements that are maintained using legislation-specific windows.
HR: Number Separator
Enables you to format integer, money and number values that are consistent with the ICX number format set at the Self-Service page. This profile has a value of either Yes or No. You can set it at the site level to ensure a consistent format across the application. The profile settings determine the group separator, decimal separator, and format of values. These settings will affect number formats on windows such as Element Entry, Element Description, Batch Element Entry, and User Tables.
HR: Online Tax Forms Update Method
Controls how SSHR processes multiple person assignments when dealing with tax information. SSHR supports multiple person assignments and keeps tax information for each assignment; however, since a person can file only one withholding form you must select one of the following options:
-
Primary. Only the tax information for the primary assignment is updated when a user changes tax information using the Online Tax Form.
-
All (default value). The tax information for all assignments is updated when a user changes tax information.
-
None. Users cannot update tax information using the Online Tax Form. The update functionality is disabled.
See: Tax Withholdings Form (W-4) (US), Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR: OAB New Benefits Model
Enables you to set up whether you are using the new benefits model, that is, Standard or Advanced Benefits. Enter Yes, if you are using the new benefits model. Enter No, if you are using the compensation and benefit models from previous releases.
HR: Override Grade Defaults
Controls whether the end user can override the default grade values when updating organization, position, or job information. If the profile option is set to No, the user can only select grade values from the defined list of values.
See: Assignment, Oracle SSHR Deploy Self-Service Capability Guide
This profile option is used in SSHR.
HR:Payroll Payments Self-Service Enable Multiple Assignments
This profile option is used by Payroll Payments Self-Service version 4. If it is set to No, employees can only specify payroll payments for their primary payroll assignment. If set to Yes, employees can specify payroll payments for additional payroll assignments. The default is No.
This profile option is used in SSHR.
HR:Payroll Payments Self-Service Payment Function
This profile option determines the defaults for the Organizational Payment Method (OPM). It operates differently depending on whether you have applied a foreign payment method enhancement.
Before Applying a Foreign Payment Method Enhancement:
-
Null Value. If the profile value is null, then each of the allowed payment categories takes the default from the first valid payment method in the cursor for that payment method.
-
Valid Function Name. If you supply a valid function name, then the organizational payment method is dynamically determined for each payment category. The returned OPM id becomes the default payment method.
After Applying a Foreign Payment Method Enhancement:
-
ALL. If the profile value is ALL, then there is no single default organizational payment method. Instead, all available payment methods are returned in a list of values so that the employee can select from them.
-
Null Value. If the profile value is null, then each of the allowed payment categories takes the default from the first valid payment method in the cursor for that payment method.
-
Valid Function Name. If you supply a valid function name, then the organizational payment method is dynamically determined for each payment category. The returned OPM id becomes the default payment method.
HR:Payroll Payments Self-Service Payments List Mode
If you set this profile option to Like, you can select the organization payment method name on the basis of it being like an entry in the payments list configuration attribute instead of an exact match. The setting of Like also enables you to perform an exact match. The default of this profile option is null, which performs an exact match.
HR: Performance View Layout
Enables a manager to see the Detail Summary View in a Form or Tabular Format.
This profile option is used in SSHR.
HR:Personal Actions Menu
Controls which actions menu is displayed for users within SSHR. If you create a custom Personal Actions menu, you must change this profile option to point to your custom menu.
This profile option is used in SSHR.
HR: PL NI Unique Error or Warning
Controls whether HRMS generates an error or a warning for duplicate PESEL values at the legal-employer level. Valid values are Error, Warn, and None. Set to None if no validation is required.
See: HR: NI Unique Error or Warning
HR: Position Default Options for SSHR
These options control whether or not the application displays default information based on the position you select for an assignment. You can set one of four values:
-
Default with No Warning
-
Default with User Decision
-
Default with Warning
-
No Defaulting
HR:Position Key Flex-Identify 1st and 2nd Segments
These options are used to control which two segments of the key flexfields appear in Person Search.
This profile option is used in SSHR.
HR: Propagate Data Changes
Controls the synchronization of person records for an individual in multiple business groups.
To propagate changes made to a person record in one business group to records for the same person in all business groups, set this profile option to Yes.
Note: You can propagate changes to only those business groups your security profile allows you to update.
HR:Purge Element Entry Permission
Controls whether users can purge element entries (irrespective of whether those entries have been processed by a payroll run). It does not affect a user's ability to perform datetracked deletions or updates. The possible values are:
-
All (the user can purge all element entries)
-
Information (the user can purge only informational (non-payment) element entries)
-
None (the user cannot purge any element entries)
Note: If you have installed a third party payroll interface, you cannot purge any element entries attached to the interface. If you are using a setting of All or Information, an error message to this effect appears when you attempt to purge an element entry.
HR:Query Only Mode
Set to Yes to restrict access to view-only for all HR and Payroll forms on a menu.
You can set this profile for individual responsibilities or users, or at the site or application level.
If you want to give query-only access to some forms and full access to other forms, set the HR:Query Only Mode profile to No and use the parameter QUERY_ONLY=YES at form function level to restrict access to individual forms.
Note: You can set the parameter QUERY_ONLY=YES for a form function that also launches a task flow. In this case, specify two parameters in the Form Function window:
QUERY_ONLY=YES
WORKFLOW_NAME="task flow name"
The entire task flow will be query-only, not just the first form.
See: Restricting Access to Query-Only Mode.
HR:Refresh Self Service Actions with Data from Intervening Actions
This profile allows you to control the effect of concurrent actions. If this profile is set to Yes, when a pending change is approved which affects the current transaction the application will display a warning message listing changed attributes and the data will be refreshed. If it is set to No, the default, the application will display a warning message and the transaction will fail.
Oracle recommends that this profile option is set to Yes if HR: Allow Approver Updates to Self Service Actions is also set to Yes.
Note: Oracle recommends that you enable this option if you have set the system profile HR:Manage Self Service Actions When Future-Dated Changes Exist to Allow Approval (Notify HR Rep). Otherwise you should disable this option.
HR: Restrict Letter by Vacancy or Event
This profile serves both HR and OTA letter requests. It enables you to generate separate letter requests for each event (OTA) and for each vacancy (HR).
If you set the profile to Yes, it displays the Vacancy Name field on the Request Letter window. Choosing a value in this field restricts the letter generation to applicants associated with the vacancy you choose in the Vacancy Name field.
HR:Restrict Transactions across Legislations in SSHR
If the HR:Cross Business Group profile is set to Yes, this profile can prevent SSHR managers from carrying out transactions on employees (within their supervisor hierarchy) who are from different legislations.
HR: RIA Integration Enabled
Set this profile option to Yes to enable links from Oracle HRMS windows to the web pages of third party information provider RIA via the 'Info Online' toolbar button. Set to No to disable the links.
HR:Run BENMNGLE When Processing a Self Service Action
In order to ensure that the list of eligible actions and sub-actions is up to date, you must periodically run the Participation Batch Process (Run Benefits Manage Life Events Process) for that individual. This can be set to run automatically every time a manager initiates an action by setting the profile option, HR:Run BENMNGLE When Processing a Self Service Action, to Yes.
HR: Salary View Layout
Enables a manager to see the Detail Summary View in a Form or Tabular Format.
This User Profile Option is used in SSHR.
HR: Save and Stay in Appraisals Page
Controls what happens when the user clicks Save as Draft in an SSHR Appraisals page. When this option is set to Yes, which is the default value, the user remains in the current page and can continue to edit the appraisal. When this option is set to No, the Appraisals home page appears.
HR: Schedule Based Absence Calculation
Set this profile option to Yes at the site level if you want the application to take into account the schedules and calendar events information from the worker's primary assignment to calculate the actual duration of an absence. The default is No. If you leave the default value for this profile, and have already created a basic formula for absence duration, the application calculates the absence duration on the basis of the absence start and end dates, without using the schedules and calendar events information.
HR: Security Profile
Restricts access to the organization, positions and payrolls defined in the security profile. This option is predefined at Site Level with the view-all security profile created for the Setup Business Group.
If you use Standard HRMS security you must set up the HR: Security Profile profile option for each responsibility.
If you use Security Groups Enabled security you must not set up the HR: Security Profile profile option. This is set up automatically when you assign security profiles using the Assign Security Profile window. You must only change the HR: Security Profile option by assigning a different security profile to a responsibility using the Assign Security Profile window.
HR: Self Service HR Licensed
Controls whether Self-Service HRMS (SSHR) is available. If the customer has obtained a license for SSHR, they must set this profile option to Yes at the site level.
This profile option is used in SSHR.
HR:Self Service New Hire Default Values
Specifies whether values for the new person record should be defaulted or not.
For the New Hire function, if the profile is set to Yes, then the following values are defaulted based on the primary assignment, as of the system date, of the person logged in:
-
Organization
-
GRE (if US)
-
Payroll
-
Salary Basis
The supervisor for the new person defaults to the person logged in. For both New Hire and Applicant Hire, this profile also controls which person type is defaulted.
-
If the profile is set to No and there is only one person type available, then this person type is defaulted. If there is more than one available then the field remains blank and you can select a value.
-
If the profile is set to Yes and there is only one person type available, then this person type is defaulted. If there is more than one available, then the field displays the person type set as the default for the system person type of Employee.
This profile is used in SSHR.
HR:Self-Service Save for Later
This profile options allows the Save for Later button to be displayed on all transaction pages in Self Service. Set it to No to disable this feature.
HR: Servlet Timeout
If you are using Info Online to allow users to access information provider web sites, use this profile to set the maximum time in seconds that the system waits for a response from the web server mediating the connection to the integration partner.
HR: SM Employee Find Work Opp Menu
Controls suitability-matching functions for finding a work opportunity available to employees using the Employee Self-Service responsibility.
HR: SM Manager Find Person Menu
Controls suitability-matching functions available to managers using the HR Professional or Manager Self-Service responsibility for finding a person for a work opportunity.
HR: SM Manager Find Work Opp Menu
Controls suitability-matching functions available to managers using the HR Professional or Manager Self-Service responsibility for finding a work opportunity for a person.
HR: Subrogation
Use this profile option to set a value for subrogation. This profile option is for users of the French legislation only.
HR: Supervisor Hierarchy Usage
If you are using supervisor hierarchies for security within your organization, you use this profile option to specify whether the supervisor hierarchy is person-based or assignment-based.
HR: Training View Layout
Enables a manager to see the Detail Summary View in a Form or Tabular Format.
This profile option is used in SSHR.
HR:TCA Unmerge Options
The Trading Community Architecture (TCA) Unmerge function, which removes the records of people who are only contacts from the TCA party tables, is delivered in patch 3625452 and is part of the November 2003 Family Pack (PER Family Pack G). The TCA Unmerge function uses the TCA purge parties process, which checks references to party IDs throughout the E-Business Suite. This process can take a long time to complete. Patch 3621712 provides you with an alternative approach to the TCA Unmerge process. If you apply patch 3621712 prior to installing PER Family Pack G you can use this profile option to control how the unmerge process is run. Select one of the following options:
-
Pre Stage Process If you select this option, then the TCA Unmerge process does not run during auto patch. Instead, you can log in as a System Administrator and submit the concurrent program Unmerge Contacts from TCA (HR TCA process) at a convenient time.
-
In Patch Process If you select this option (which is the default option), then the HRMS component of the unmerge process is run during auto patch. A concurrent program is then submitted automatically during the auto patch process to run the TCA component of the process.
-
Deferred Process If you select this option, then a concurrent program is submitted automatically during the auto patch process to run both the HRMS and TCA components of the process.
HR: US Address Line Length
This profile option, which specifies the maximum length of an address line, affects U.S. addresses only; it has no effect in other legislations. Oracle HRMS displays a warning message when you view or enter address lines longer than the value you specify here. The value of this profile option overrides any maximum address line length specified in the Personal Address Information descriptive flexfield for the current local U.S. address style.
HR: Use Fast Formula Based PTO Accruals
This user profile option is disabled.
HR: Use Global Applicant Numbering
Enables the global sequence for applicant-number generation. This sequence is shared among all business groups.
To set this profile option, you run the process "Change automatic person number generation to global sequencing". You cannot set this option in the System Profile Values window.
HR: Use Global Contingent Worker Numbering
Enables the global sequence for contingent-worker-number generation. This sequence is shared among all business groups.
To set this profile option, you run the process "Change automatic person number generation to global sequencing". You cannot set this option in the System Profile Values window.
HR: Use Global Employee Numbering
Enables the global sequence for employee-number generation. This sequence is shared among all business groups.
To set this profile option, you run the process "Change automatic person number generation to global sequencing". You cannot set this option in the System Profile Values window.
HR:Use Grade Defaults
This profile option allows you to restrict the list of values for the grade to include only those values permitted by the parent organization, job, or position.
This Profile Option is used in SSHR.
HR:Use Standard Attachments
Disables the facility to attach short text comments to records. Enables the attachment of multiple items of various types including OLE objects, Web pages, images, and word processed documents.
HR:User Type
Limits field access on windows shared between Oracle Human Resources and Oracle Payroll. If you do not use Oracle Payroll, it must be set to HR User for all responsibilities.
Note: You must set this profile option at responsibility level.
If you do use Oracle Payroll, you can give each responsibility one of the following user types, depending on the work role of the holders of the responsibility:
-
HR User
-
HR with Payroll User
-
Payroll User
The windows that are dependent on the setting of this profile option are as follows:
| Form | Profile Setting | Behavior |
|---|---|---|
| Define Element Classification (PAYWSDEC) | HR User | You cannot create secondary element classifications. |
| Define Element Type (PAYWSDET) | HR User | Some payroll fields are not available. |
| Define Payroll (PAYWSDPG) | HR User | The Statutory Information field is not visible.
Note: Statutory Information is not available at payroll level for all localizations, for example, it is not available for the UK. |
| Element Entries (PAYWSMEE) | HR User | The Processing Priority field in the Element Entry Values window is not available. |
| Define Assignment Status (PERWSDAS) | HR User | You cannot use the Payroll Status as a query criterion in Enter Query mode. |
| Define Benefit Contributions (PERWSEBC) | Payroll User | You cannot change the coverage type or contribution amounts for an existing benefit contributions record. You cannot create benefit contribution records. |
| SSP/SMP (SSPWSENT) (UK Only) | HR User | You must enter the average earnings amount for your employee before you can calculate their entitlement to statutory payments. |
| SSP/SMP (SSPWSENT) (UK Only) | Payroll User or HR with Payroll User | You can derive the average earnings automatically. |
| Employee Assignment (PERWSEMA) | HR User | Payroll field is display only. |
| Employee Address and Define Location (US Federal Only) | HR User | The default address style is United States (International). |
| Employee Address and Define Location (US Federal Only) | Payroll User or HR with Payroll User | The default address style is United States. |
| Define Element Type (US Federal Only) | HR User | The application uses the predefined Federal element names. |
| Define Element Type (US Federal Only) | HR with Payroll User | The application uses the element names you define for the Federal elements. |
| Terminate (US Federal Only) | HR with Payroll User | You can update the Final Process Date. |
HR: Use Title in Person's full name
Enables you to remove title from a person's full name so that it does not appear in person search lists, such as the Find window on the Person window.
This user profile option is only effective when you insert new records or update existing records. To remove title from existing records without updating them you should run the Remove Title from Person's Full Name concurrent process.
HR: Verification External Node
Defines the URL for the external node for the Employment Verification function. The node redirects the access request from outside the security firewall to the HTML page containing the released employment information.
This profile option is used in SSHR.
HR: View Payslip From Date for WEB
Limits the number of pay periods an employee can view.
This profile option is used in SSHR.
HR: Views Layer Size
Enables you to set the width of the Employee Name and Employee Number floating layer to the longest name and number you have.
This profile option is used in SSHR.
HR:View Unpublished Employee 360 Degree Self Appraisal
Enables a manager to view employees' unpublished 360 Degree appraisals. (This option does not affect self appraisals.) Set this option to Yes to view employees' unpublished 360 Degree appraisals. The default value is Null.
HR:Webapps Tips Test Mode
Forces all tip icons in SSHR to be displayed whether tip text is defined or not.
This User Profile Option is used in SSHR.
HR: Web Proxy Host
This option is used as part of the Knowledge Management which allows the Proxy Host to be used when accessing an external site.
HR: Web Proxy Port
This option is used as part of the Knowledge Management which allows the Proxy Port to be used when accessing an external site.
HR: Worker Appraisals Menu
Controls the types of appraisal a worker can initiate. The default value is Employee Appraisals Menu.
HR: ZA Nature of Person Mandatory at Person Level
Set this profile option to Yes to make the Nature of Person mandatory at the Person level. This ensures the application validates the Nature of Person during data entry. If you set this profile option to No, then Nature of Person is optional at the person level, and the application performs validations only when you run the Tax Year End Validation report. You must run the Generic Upgrade Mechanism process using the South Africa: Populate Nature of Person at the Person Level parameter to display the Nature of Person details at the person level for existing employees.
HRI: Collect Manager Snapshots
If you turn this profile option on, the DBI for HRMS collection process collects an additional summary layer for managers who have more staff than a specified number reporting to them. The default value is No. Use in conjunction with HRI: Manager Snapshot Threshold.
HRI: Collect Open Enrollment in Progress
Determines the enrollment data that DBI for HRMS collects. Set this profile option to Yes to collect data for the current open enrollment period. To collect historic data of enrollments along with the open enrollment data, set the profile option to No.
HRI:DBI Chief HR Officer Named User
Enables users of the Chief HR officer responsibility to access the Chief HR Officer dashboards effectively as the CEO of the enterprise.
Note: You must have successfully run an Initial Load before you set this profile option.
Select the name of the user from the profile option list. The list of managers shown for the profile is only those at level 1 (the top of the hierarchy). To turn this profile off, set the profile option value to No.
Note: This new profile option only affects the Chief HR Officer responsibility.
HRI:DBI Force Foundation HR Processes
Determines whether the HRI Collection Programs run in Foundation HR mode (on a Full HR Installation). The Foundation HR mode only collects data as of the system date; it does not maintain historical data. If you are an HRI DBI customer, you must set this profile option to No.
Non-DBI for HRMS customers, who do not require any more than the basic data collected in a Foundation HR implementation, can set the HRI:DBI Force Foundation HR Processes profile option to Yes. This setting reduces the amount of data collected and improves load times.
HRI:DBI Link to Transaction System
Enables users of DBI for HRMS to drill from detail reports to employee records in the HR Self Service Employee Directory.
Set this profile option to HR Employee Directory to turn this feature on. The default value is Disable Link.
HRI:Enable Benefits Collections and Event Queue
Enables managers to view the life event statuses for participants in the open enrollment period. Set this profile option to display the life event statuses in the DBI for HRMS Enrollment Process Status report.
HRI:Enable Captured Events Archive
Controls the archive mode for the events capture process in DBI for HRMS. Set this option to Yes to archive all events that trigger incremental processing.
HRI:Enable Detailed Logging
Enables you to include a debug message in the concurrent manager log to troubleshoot errors during the HRI data collection process. Set the HRI:Enable Detailed Logging profile option to Yes. The default is No.
Caution: Only set this profile option to Yes if you encounter an error. Debugging the collection process impacts the collection timings.
HRI: Manager Snapshot Threshold
Determines the minimum number of staff required to enable snapshot collection for a manager. The default is 2500. Use this profile in conjunction with HRI: Collect Manager Snapshots.
HRI:Multithreading Chunk Size
Determines the number of objects processed at one time during the DBI for HRMS collection phase. The default value is 200. You can change this to a value between 1 and 16000. However, you should avoid processing a large numbers of objects, as the default value is the result of benchmark tests. If you receive the error "Oracle exception: cannot extend rollback segment" during the collection process, then reduce the value for this profile option.
HRI:Number of Threads to Launch
Determines the number of threads, or sub-processes, that run in parallel on multi-processor machines. If you have already installed PYUGEN on your system, then set this profile option to equal the THREADS parameter defined for PYUGEN. The default value for this parameter is 8.
Caution: Your Applications System Administrator must define the concurrent manager to allow the required number of sub-processes to run in parallel.
HRI:Period of Service / Placement Date Start Source
Determines how DBI for HRMS calculates the employee's periods of service. The default value is Start Date. With this setting, DBI for HRMS calculates periods of service from the beginning of employees' current period of service.
To calculate the employee's period of service from the beginning of their first period of service, change the value to Adjusted Service Date.
Caution: HRMS also uses the Adjusted Service Date to calculate benefits. You must therefore consider the effect on benefits if you use this feature.
HRI:Populate Assignment Events Queue
Determines whether the events collection process in DBI for HRMS populates the incremental update queue for the assignment events collection process. If you never run the assignment events process, set this profile option to No to reduce the load times of other processes. If you are a DBI for HRMS customer, you must set this profile option to Yes.
HRI:Populate Supervisor Hierarchy Events Queue
Determines whether the events collection process in DBI for HRMS populates the incremental update queue for the supervisor hierarchy collection process. If you never run the supervisor hierarchy process, set this profile option to No to reduce the load times of other processes. If you are a DBI for HRMS customer, you must set this profile option to Yes.
HRI:Populate Supervisor Status History Events Queue
Determines whether the events collection process in DBI for HRMS populates the incremental update queue for the supervisor status history collection process. If you never run the supervisor status history process, set this profile option to No to reduce the load times of other processes. If you are a DBI for HRMS customer, you must set this profile option to Yes.
HRI: Workforce in Period Calculation Method
Determines the calculation that DBI reports use in averaging values over a period, for example, workforce turnover or average employee absence. Select from:
-
Workforce End: headcount at the end date of the reporting period.
-
Workforce Start + End Average: average of the headcount at the start date and the headcount at the end date of the reporting period.
The default is null, which means that the calculation will use the headcount at the end date of the reporting period
HZ: Protect HR Person Information
Controls the synchronization of common data between Oracle HRMS and Oracle Student System (OSS). By default (when this option is set to No) data synchronization is enabled.
Limit by Persons Organization
Set this profile option to Y to limit the Compensation Objects selected by the Participation Process to only those linked to the employee's organization.
OAB:Self Registered User Responsibility
Identifies the responsibility to be granted to new users who successfully self-register in SSHR using the New User Registration processes. This profile option is seeded at site level with the seeded responsibility Self Registered Employee Default Responsibility. You can set this profile at responsibility level if you have created several responsibilities for different groups of users to use after initial registration.
This profile option is used in SSHR.
OAB:Enable Self-Service Benefits Trace
This profile option enables to you to generate a PYUPIP trace file for a particular Self-Service Benefits user that you select. Use this profile option to debug Self-Service Benefits election problems.
This profile option is used in SSHR.
OAB:User to Organization Link
In the self-service New User Registration processes, links the responsibility you give to new users to register on SSHR with the organization to which they belong.
This profile option is used in SSHR.
OAB:User to Payroll Link
In the self-service New User Registration processes, provides a default employee payroll linked to the responsibility you give to new users to register on SSHR.
This profile option is used in SSHR.
PAY: Enable Workflow for Assignment Costing
Enables the user to toggle between the two processes of using with or without the workflow option. If the profile is set to Yes, the application saves the data on approval. If the rule is set to No, the application saves the data immediately. The default is No.
PAY: Generate Periods for Tax Year
Since the lunar month has only 28 days, the yearly start date of a period would be always less than the legislation specific start date. This profile option enables you to reset the generated payroll period start date back to the legislation start date. You should set the profile option to Yes to display Reset Years in the Payroll window. The default value is No.
PAY:Statement of Earnings User Category
You use this profile when setting up a global statement of earnings to be viewed online. It enables you to select user category when setting up the global statement of earnings.
PER:Automatic Save
You use this profile when setting up iRecruitment. Set the profile option to Y to enable an automatic Save For Later operation when users navigate to a new web page.
PER:Navigation
You use this profile when setting up iRecruitment. Set the profile option to Y if you want the application to validate data on the current web page when users navigate to a new page (Next or Previous).
Personalize Self-Service Defn
This profile option enables or disables the global Personalize link and Personalize Region link that appear on self-service functions from SSHR 4.0 and above.
This profile option is used in SSHR.
PO: Services Procurement Enabled
Controls the availability of purchase-order information from Oracle Services Procurement to Oracle HRMS. If you use Oracle Services Procurement to provide purchase order information for contingent worker assignments, you must set this profile option to Yes.
Performance Management Source Type
Enables you to select a default value from the "PROFICIENCY_SOURCE" (Source of Proficiency Rating) user lookup. HRMS uses this value when updating a person's competency profile automatically after an appraisal.
Note: This profile option was previously known as Talent Management Source Type.
Workforce Measurement Type
Determines how DBI for HRMS measures the size of your workforce. The application currently only supports the value of Headcount.
Menus, Functions, and Responsibilities
Responsibilities
You can control users' access to human resources information by record, window and function.
The responsibility is your primary means of defining security. To define what a user can access you link a user, responsibility and Business Group to a security profile. Other important components of the responsibility are the menu structures, task flows and information types. These also help you limit the employee records a user can access.
Users can sign on to the system only through the responsibilities you give them. So their responsibilities control what they can see and do in the system.
Responsibility
A responsibility is linked to a security profile and composed of:
-
A menu structure
-
A request group for reporting users (optional)
-
Extra information types available to the user
Responsibilities are also linked to business groups. However, depending on which security model you use, you link responsibilities differently.
-
Standard HRMS Security
You can only link one business group to one responsibility using Standard HRMS security. You must set up different responsibilities for each business group.
-
Security Groups Enabled Security
You can enable more than one business group for a single responsibility. However, you still only view records for one business group at a time.
Each model enables you to set up multiple responsibilities. You can assign multiple responsibilities to users who need to:
-
Access applicant, employee, and contingent worker records from two or more security profiles.
-
Use more than one menu structure to view or make changes to the records they can access.
-
Access records for more than one business group if you use Standard HRMS security. For example, an enterprise with international operations may have a US-Based business group and a UK-Based business group. A few of your employees might need to access both.
The Oracle HRMS responsibilities available globally include:
-
HR Manager: to access HR features only
-
HRMS Manager: to access HR and Payroll features
-
Super HRMS Manager: to access HR, Payroll, and Advanced Benefits features
Note: You can access standard benefits features using the HR manager or HRMS manager responsibilities. Only use Super HRMS Manager if you have licensed Oracle Advanced Benefits.
Access Control Through Responsibility
The following key components help control user access to Oracle HRMS:
-
Security profiles determine the organizations, positions and payrolls whose applicant, employee and contingent worker records responsibility holders can access.
-
Business Groups determine the set of records a user can access. Using Security Groups Enabled security you can enable one responsibility for many business groups. Using Standard HRMS security you must set up a new responsibility for each business group.
-
Menu structures and functions control:
-
The particular windows and functions a responsibility holder can access
When you create a responsibility, you assign a menu structure to the responsibility. You can assign either a delivered menu or a custom menu. If required, you can restrict access to particular functions or menus using function or menu exclusions.
See: Overview of Menus and Function Security, Oracle Applications Developer's Guide
See: How Function Security Works, Oracle Applications Developer's Guide
Warning: If you exclude a function from a responsibility, a user with the responsibility can no longer access the function from any menu assigned to the responsibility. However, the function may still be attached to a task flow. If this is the case, the user will be able to access the excluded function when working through the task flow sequence. To avoid this situation, you may need to modify your task flows to remove the function.
See: Task Flow
-
Whether he or she can perform data entry, change or deletion on these windows
You can produce configured versions of some windows. Each configured version enables access to a subset of certain types of information, such as person types, special information types, or elements. You define additional menu functions to call configured windows or task flows, and then you add these functions to a menu structure, which is linked to a responsibility.
-
-
Request groups determine the group of processes and reports a responsibility holder can initiate. A request group is an optional component of a responsibility. If holders of a responsibility should not initiate any reports or processes, you do not include a request group in the responsibility.
-
Extra Information types are an optional component of a responsibility. By defining which extra information types are included in a responsibility, you effectively create a configured version of a window for users who are assigned the responsibility.
Important: If you do not associate any extra information types with a responsibility, a person assigned to this responsibility will not have access to any extra information types in the product.
For each responsibility, you must also define the user profile option HR:User Type.
Responsibility Ownership
If you are using Self-Service Human Resources (SSHR) you can use the Responsibility Ownership functionality to administer and control access to responsibilities by assigning an owner relationship. You can use the Responsibility Ownership functionality in SSHR to display a hierarchy of functions and menus attached to the responsibility and also display information on users of the responsibility. If appropriate, you can revoke access to a responsibility using the self-service interface.
See: Responsibility Ownership, Oracle SSHR Deploy Self-Service Capability Guide
Menu Structure
Users access standard windows, configured windows, and the first window in a task flow through the menu structure displayed in the Navigator window. Each responsibility includes a menu structure to restrict the windows users can access, and what they can do on these windows.
A function is a part of an application's functionality that is registered under a unique name for the purpose of assigning it to, or excluding it from, a responsibility. There are two types of functions: form functions, and non-form functions. For clarity, we refer to a form function as a form, and a non-form function as a subfunction, even though both are just instances of functions in the database.
Using Function Security system administrators can further restrict access to individual menu options. You can include:
-
Standard windows, displayed in edit or view-only mode
-
Configured windows, on which you have restricted the range of data that can be displayed
-
The first window in task flows that link a number of windows that are used in sequence to complete a task
By defining menus with function security for groups of users, you can:
-
Limit the range of information users can access for the applicant and employee records available to them
-
Improve users' efficiency in using the system by reducing menu choices
-
Restrict users to query-only access to some or all windows
Each responsibility you define must be linked to a root menu. The root menu lists the menu options when the Navigator window first opens.
The Default Menu Structure
The AutoInstall program creates a default menu structure for your HRMS product. This menu structure enables you to access all of the windows for your system. Normally, only a system administrator has access to the full default menu structure.
The supplied menus give you access to all of the available submenus. However, a number of predefined functions are not enabled on these menus. If your localization requires these menus, you need to add them for the responsibilities that should have access to these functions.
-
HR View Medical
This causes the Medical Information tabbed region to display in the People window.
-
HR View Background
This causes the Background Information tabbed region to display in the People window.
-
HR View Benefits
This causes the Benefits tabbed region to display in the People window.
-
HR View Rehire
This causes the Rehire Information tabbed region to display in the People window.
-
Salary Administration: Approve
This enables the user to approve salary proposals in the Salary Administration window and the Salary Management folder.
-
HR View Projects Information
This causes the Projects Information tabbed region to display in the Assignment window. You must have Oracle Projects installed to display this region.
Caution: Oracle HRMS with DateTrack and task flows does not fully support multiple active windows. When you define a new menu for use with Oracle HRMS the top menu must include the following function as a separate menu option:
Disable Multiform
See: Disabling Multiple Windows
Request Groups
When you build a responsibility for employees who must initiate reports or processes, you can attach a request group to the responsibility. The request group lists a group of processes and reports its holders can run. Holders of responsibilities with no request groups cannot run any processes or reports.
The group Reports and Processes gives access to all predefined reports and processes.
Structuring Menus
Using function security and the Menus window, you can use the default menu for any number of responsibilities and restrict access to the default menu options. You can also define any number of new functions and menus to restrict the access of other users. To view the hierarchy of menus you have defined, you can run the Menu Structures report.
Caution: You should not modify the default functions and menus supplied with the system. On upgrade, these defaults will be overwritten.
If you want to add window configuration options or task flows you should define your own menus.
The supplied menus give you access to all of the available submenus. However, a number of predefined functions are not enabled on these menus. You need to add them for the responsibilities that should have access to these functions.
Structuring Menus
-
Start by drawing it out on paper. This helps you to decide the best structure and the best prompts and descriptions.
-
Decide how to structure your menus. Menus can be structured in different ways:
-
Following a Sequence of Tasks.
For example:
1. Define a Requisition and Vacancy
2. Define a Recruitment Activity
3. Enter Applicant Information
-
By Type:
For example, all inquiry windows grouped together. If you structure the menu by type, the grouping is important but the sequence is not.
-
-
Work from the lowest level of sub-menu to the highest and define the root menu as the last step in the sequence.
-
Define as many submenus as you require under each menu option. We recommend that you restrict the number of menu levels to three because a menu structure with more levels is cumbersome to use.
Defining Menus
Use the Menus window to add predefined functions to a menu.
Caution: Oracle HRMS with DateTrack and task flows does not fully support multiple active windows. When you define a new menu for use with Oracle HRMS the top menu must include the following function as a separate menu option:
Disable Multiform
See: Disabling Multiple Windows
A number of predefined functions are not provided on the supplied menus. You can add them to your own menus. See: Menu Structure for a list of these functions.
To define a menu
-
Query the menu onto which to add the function.
-
Add a new line and select the function.
For example, select Salary Administration: Approve to enable users to approve salary proposals.
-
Save your changes.
See: Menus Window, Oracle Applications System Administrator's Guide if you need further information about using the Menus window.
Disabling Multiple Windows
In most Oracle Applications, you can open multiple windows from the Navigator window without closing the window you already have open. HRMS, however, does not support Multiform functionality.
Important: You must disable this feature on menu structures that accesses Oracle HRMS windows.
To disable the Multiple Open Window feature
-
Add a Function type menu entry to the top-level menu referenced by your new responsibility.
-
Select the function whose User Function Name and Function Name are:
-
Navigator: Disable Multiform
-
FND_FNDSCSGN_DISABLE_MULTIFORM
-
-
Save your changes.
Defining Menu Functions
Use the Form Functions window to define your menu functions.
Function Security helps you to control the menu options you make available to each responsibility. When you define a responsibility you can restrict the submenus or functions for that responsibility using exclusion rules.
See: How Function Security Works, Oracle Applications Developer's Guide
Define Menu Functions
-
Define your menu function using the Form Functions window.
See: Form Functions Window, Oracle Applications Developer's Guide
-
When you have created your custom functions, add them to a menu.
See: Menus Window, Oracle Applications System Administrator's Guide
Caution: You should not modify the default functions and menus supplied with the system. On upgrade, these defaults will be overwritten.
If you want to add window configuration options or task flows you should define your own menus.
Restricting Access to Query-Only Mode
To restrict access to query-only mode for an individual form
-
In the Form Functions window, select the form and specify the parameter QUERY_ONLY=YES. If you want to specify other parameters for this form function, separate them with a space.
-
Enter a user function name to identify your new function, and save it.
-
In the Menus window, select your new function instead of the supplied form function.
Using Parameters for HRMS Form Functions
To use parameters in Form Functions
For certain options you must define menu functions that include a parameter in the Parameters field of the Form Functions window, as follows:
-
If the menu entry calls a configured form, use the following parameter:
HR_CUSTOMIZATION = "customization name"
-
If the menu entry calls the first form in a task flow, use the following parameter:
WORKFLOW_NAME = "task flow name"
-
If the menu entry calls a form in query-only mode, use the following parameter:
QUERY_ONLY=YES
-
If the menu entry calls a people management template, use the following parameter:
TEMPLATE_NAME="name of your template"
-
If the menu entry calls the Define Rate form (PAYWSGEV), use the following parameter:
FORM_MODE = "grade" (for the Grade Rate window)
FORM_MODE = "spine" (for the Scale Rate window)
-
If the menu entry calls the Payroll and Assignment Processes form (PAYWSACT - used in Oracle Payroll), use the following parameter:
FORM_MODE = "assignment" (for the Assignment Processes window)
FORM_MODE = "payroll" (for the Payroll Processes window)
-
If the menu entry calls the Organization Manager Relationship form (PERWSCCM), use the following parameter to limit the list of organizations to those with a particular classification. You can find the organization classification code for a classification from the ORG_CLASS Lookup Type, for example the code for HR Organization is HR_ORG:
RESTRICT_CLASSIFICATION = "organization classification code"
-
If the menu entry calls the Enter Person window (PERWSEMP), you use the following parameter to hide sensitive data:
HIDE_SENSITIVE_DATA = Y
-
To prevent position users from attaching a position to an existing control budget and entering budget data, set the form function parameter DISABLE_BUDGETS="Y" for the Position window (HRWSPSF).
-
The Position, Position Transaction, and Position Copy forms enable you to perform secondary queries when searching for positions, using a Combinations button. The Combinations button enables you to see positions across business groups. If you want to restrict the positions users can see to those within their own business group, hide the Combinations button by setting the parameter SHOW_COMBINATIONS=N.
If you need to specify more than one parameter for a form function, separate the parameters with a space.
For more information about using the Form Functions window see: Form Functions Window, Oracle Applications Developer's Guide
AuditTrail
AuditTrail Overview
The system administrator is responsible for performing AuditTrail on Oracle HRMS data.
Performing AuditTrail
AuditTrail provides a flexible approach to tracking the changes to your data. It enables you to keep a history of changes to your important data: what changed, who changed it, and when. With AuditTrail, you can easily determine how any data row or element obtained its current value. You can track information on most types of fields, including character, number and date fields.
You enable auditing for audit groups. These are groups of tables and columns you want to audit, where you do not necessarily need to include all the columns in a given table. You typically group together those tables that belong to the same business process, such as employee compensation tables.
During your AuditTrail implementation, you need to decide your audit requirements:
-
Which tables and columns you want to audit
-
How you plan to report on the audit data
-
How long you want to keep the audit data active
-
Audit information reports
-
Custom audit reports
-
See: Oracle Applications System Administrator's Guide.
Audit Information Reports
The AuditTrail process creates a shadow table for each audited table, to hold the audit information.
For tables that are not datetracked, you can write a report that uses the views on the shadow tables to access the audit data. However, for datetracked tables, the information from the shadow tables must be extracted and written to the HR_AUDITS table and the HR_AUDIT_COLUMNS table before you can report on it.
The system's audit report performs this additional processing. You can use it as supplied or as an example of how to report on audit information. It can report on both datetracked and non-datetracked tables that have a numeric primary key.
Note: It can report on up to approximately 90 columns in datetracked tables and 80 columns in non-datetracked tables.
The report lists every change made to the table you select in the time period you specify when you run the report. You can restrict the reported changes to those made by a specified username. The changes are listed by date and time of the change. For each change, the report shows:
-
The date and time of the change
-
The user ID who made the change
-
The type of change
-
The fields that changed and either their old values, or their new values, or both, depending on the type of change
Table of Transaction Types in the Audit Report
The following table lists the 12 types of change and the information shown in the audit report for each type.
| Type of Change | Field Values Shown in the Report |
|---|---|
| Normal Insert (creates a non-datetracked record) |
The non-null values in the new record. |
| Normal Update (updates a non-datetracked record) |
The old and new values for all fields that changed. |
| Normal Delete (deletes a non-datetracked record) |
The non-null values in the record that was deleted. |
| DT First Insert (creates a datetracked record) |
The non-null values in the new record. |
| DT Update (date-effectively ends the last row on a datetracked record and creates a new row) |
The old and new values of all fields that changed, and the new effective end date on the old row. |
| DT Correction (corrects a row of a datetracked record and does not change the effective dates) |
The old and new values of all fields that changed, and the effective dates of the corrected row. |
| DT Replace (creates a new row on a datetracked record that replaces all rows that start after its start date) |
The non-null values in the rows that were deleted, the new effective end date on the row preceding the new row, and the old and new values of all fields that changed. |
| DT Insert (creates a new row on a datetracked record that ends on the old effective end date of the preceding row) |
The old and new values of all fields that changed, and the new effective end date on the row preceding the new row. |
| DT Purge (deletes all rows of a datetracked record) |
The non-null values in all rows of the record that was deleted. |
| DT End Date (adds an effective end date to the last row of a datetracked record) |
The new effective end date of the row. |
| DT All (sets a new effective end date on a row of a datetracked record and deletes all following rows) |
The non-null values in the rows that were deleted, and the new effective end date on the last row. |
| DT Next (deletes a row of a datetracked record and uses its effective end date to set an new end date on the preceding row) |
The non-null values in the row that was deleted, and the old and new effective end dates on the preceding row. |
Custom Audit Reports
If you want to design your own audit report, you can copy the supplied report and use it as the basis of your own version. The supplied report uses a dynamic SQL structure to retrieve information for the report, and an Oracle Report to format it.
Dynamic SQL Structure
For a non-datetracked table, the dynamic SQL structure retrieves information and uses a private procedure to retrieve the new values for an update.
For a datetracked table, the dynamic SQL structure retrieves information from the function and procedure created for each datetracked table by the Audit Trail Update Datetracked Tables process:
-
The tablename_TT function identifies the type of datetracked transaction represented by each row of the shadow table.
-
The tablename_VP procedure gets new values from the shadow table for update and insert transactions. It writes these to the HR_AUDITS and HR_AUDIT_COLUMNS tables.
The dynamic SQL structure comprises several character strings, which are concatenated into one long string, then parsed and executed using the dynamic SQL generator. If you change a string, you must ensure that you do not exceed the text space allocated to it, as listed in the package header.
The structure is built up by identifying the audited table column information, which is retrieved from the FND_AUDIT_COLUMNS table. The logic varies depending on the data type being audited.
The package for the dynamic SQL is called py_audit_report_pkg. It is found in the script pyadyn.pkh/pyadyn.pkb.
HR Audit Tables
The HR_AUDITS table holds audit information about the transaction. The HR_AUDIT_COLUMNS table holds the changed column information for that transaction.
HR_AUDITS Table
The following table shows the structure of the HR_AUDIT table:
| COLUMN | TYPE | NULL |
|---|---|---|
| audit_id | number(15) | not null |
| commit_id | number(9) | not null |
| current_session_id | number | not null |
| primary_key | varchar2(30) | not null |
| primary_key_value | number(15) | not null |
| sequence_id | number(9) | not null |
| session_id | number | not null |
| table_name | varchar2(30) | not null |
| timestamp | date | not null |
| transaction | varchar2(30) | not null |
| transaction_type | varchar2(30) | not null |
| user_name | varchar2(100) | not null |
| effective_end_date | date | null |
| effective_start_date | date | null |
HR_AUDIT_COLUMNS Table
The following table shows the structure of the HR_AUDIT_COLUMNS table:
| COLUMN | TYPE | NULL |
|---|---|---|
| audit_id | number(15) | not null |
| column_id | number(9) | not null |
| column_name | varchar2(30) | not null |
| new_value | varchar2(240) | null |
| old_value | varchar2(240) | null |
Setting Up AuditTrail
Setting up AuditTrail is usually a task for the system administrator.
The first six steps are required to enable auditing of any Oracle Applications table. They are explained in more detail in the Oracle Applications System Administrator's Guide. The final step is required only for tables in the HR application.
To set up AuditTrail
-
Have your database administrator grant SELECT privileges on SYS.DBA_TABLES to the APPLSYS account. Normally this step will already have been done as part of your installation or upgrade.
Using a System Administrator responsibility:
-
In the System Profile Values window, set the AuditTrail:Activate profile option to Yes at Site or Application level.
-
In the Audit Installations window, query the application(s) you want to audit, and check the Audit Enabled box next to the Oracle User Name.
-
In the Audit Groups window, query the application and enter a name for the audit group, then select the tables you want to audit (using the User Table name). For a new audit group, select Enable Requested in the Group State field.
-
In the Audit Tables window, query each table you want to audit, and select which columns in these tables you want to audit.
Note: You cannot audit LONG, RAW, or LONG RAW columns.
-
In the Submit Request window, run the AuditTrail Update Tables process. This process:
-
Creates database triggers on your audited tables
-
Creates one shadow table for each audited table, to contain the audit information
-
Builds special views on non-datetracked tables, which you can use to retrieve your audit data for reporting
Using an HR Manager responsibility:
-
-
In the Submit Request window, run the AuditTrail Update Datetracked Tables process. For each datetracked table, this process:
-
Creates an index on the shadow table
-
Creates the function tablename_TT and the procedure tablename_VP, which extracts information from the shadow table when you run the predefined audit report
Important: You must rerun the AuditTrail Update Tables process and the AuditTrail Update Datetracked Tables process if you make any changes in the Audit Groups or Audit Tables windows.
-
Disabling AuditTrail
-
You can disable the auditing of an audit group at any time by selecting a Disable state in the Audit Groups window.
Tip: If you are planning high volume transactions on an audited table, such as loading a batch of information from another system, consider disabling auditing for the table's audit group. This will enable the batch loading to complete more quickly.
Before you restart auditing, you should archive your audit data, according to your business needs, and purge the shadow tables. You purge the tables by setting the audit group to Disable - Purge Table and running the Audit Trail Update Tables report. To restart auditing, you set the audit group to Enable Requested and rerun the Audit Trail Update Tables process and the Audit Trail Update Datetracked Tables process.
Running the Predefined Audit Report
You can run an audit report using the system's predefined structure, or you can design your own audit report.
To run the predefined audit report
-
Using an HR Manager responsibility, open the Submit Request window and select Audit Report in the Name field.
-
Enter the Parameters field to open the Parameters window.
-
Select an audited table (that is, one in an audit group) using the Table name.
-
Select a value for the Initialization parameter:
-
Yes means that the report removes any existing data related to your selected table from the HR_AUDITS table and the HR_AUDIT_COLUMNS table. It then populates these tables with the current values from your selected table and reports on these.
-
No means that the report runs on the existing data in the HR_AUDITS table and the HR_AUDIT_COLUMNS table.
-
Refresh means that the report removes existing data for all tables from the HR_AUDITS table and the HR_AUDIT_COLUMNS table. It then populates these tables with the current values for your selected table and reports on these.
-
-
If you only want to report on the changes made by one user, enter the user name.
-
Enter start and end dates to limit the time period for reporting audit information.
-
Choose the Submit button.
You can use the View Requests window to check the progress of the report.