Chapter 1 Installation Overview
This chapter introduces SunScreen 3.1 installation concepts.
Topics covered include:
-
What is SunScreen?
-
Operating the firewall in routing mode
-
Operating the firewall in stealth mode
-
Operating the firewall in mixed mode
-
Before installing SunScreen
-
Upgrading from EFS 1.1, 2.0, or 3.0 to SunScreen 3.1
-
Upgrading from SPF-200 to SunScreen 3.1
-
Converting from FireWall-1 to SunScreen 3.1
-
Trusted SolarisTM
-
Security issues
-
Software and hardware requirements
-
Web browser requirements
What Is SunScreen?
SunScreen 3.1 is a software security solution, which is installed on a SolarisTM-based machine. It lets companies connect their departmental networks to public internetworks securely. Depending on how you install it, SunScreen can function as a firewall and router for hosts on the network it protects.
The Screen is the firewall responsible for screening packets. You use an Administration Station to define the objects and rules that form the security policy and administer the Screen. The number of Screens and Administration Stations depends on your site's network topology and security policies. You can install all of SunScreen on a single machine (local administration) or you can put the Administration software and the Screen software on different machines (remote administration).
You need a Screen at every point in the network where you want to restrict access. In the strictest sense, you need one Screen for each point in the network that has direct public access (usually one per site). One Administration Station can manage multiple Screens, although you can install more Administration Stations for redundancy and ease of access. Encryption and authentication protects access and limits management of a Screen to an authorized Administration Station.
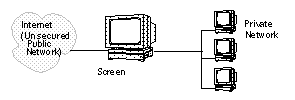
Local Administration
With Local administration, you administer the Screen on the Screen itself, as shown in FIGURE 1-1. Local administration does not require an encrypted connection as no network traffic is generated.
Figure 1-1 Example of a Locally Administered Screen
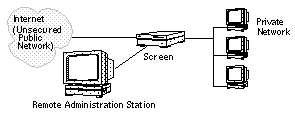
Remote Administration
With Remote administration, you use a separate machine called an Administration Station to administer the Screen (as shown in Figure 1-2.) Remote administration uses encrypted communication (using SKIP) between the Screen and Administration Station so the information about the security policy in place on the Screen can not be obtained by others.
Figure 1-2 Example of a Remotely Administered Screen
Firewall Operation Modes
You typically install SunScreen in either routing mode (where the Screen performs routing as well as firewall functions (or stealth mode (where no IP interfaces are exposed to the public or private network). You can also set up your Screen to operate in a "mixed mode" where the interfaces protecting you from the outside network are stealth and the interfaces to your internal network are routing. This configuration is not covered in this manual but you can find an example configuration in the SunScreen Configuration Examples manual.
Routing Mode
Typically, you operate the Screen in routing mode if you need a machine to act both as a router and a firewall. Another reason to choose Routing mode is if you want to use proxies with the firewall. In this mode, you need at least two exposed IP interfaces, and a hop visible to traceroute and other network utilities. In routing mode your firewall is visible and you have a slightly greater exposure to attack than when operating in stealth mode.
Be aware of the following considerations when operating in Routing mode:
-
The existing Solaris machine must be acting as a router. The Screen uses Solaris to provide IP routing.
-
The Screen makes use of the Solaris IP stack on the filtering interfaces, so it does not possess stealth characteristics.
-
You must divide up different networks as you would with any router.
-
The addition of a SunScreen to your network may require re-numbering IP addresses on your hosts (if you did not already have a router where your SunScreen is being placed.)
Stealth Mode
You can operate SunScreen in stealth mode if you do not need routing functions, or if you want to decrease possibilities for attacks. In stealth mode, SunScreen acts much like a bridge in that no IP interfaces are exposed to the public or private network, and packets are transparently filtered by the Screen. While operating in this mode, the Screen cannot be attacked through any means other than a denial of service attack, and cannot be seen or detected through traceroute or similar network tools.
Be aware of the following considerations when operating in stealth mode:
-
The Screen acts similar to a bridge and does not route packets.
-
Stealth mode does not require IP address re-numbering on hosts.
-
You only need to configure the network interface you plan on using for remote administration.
Mixed Mode
It is possible to configure a hybrid Screen combining both stealth and routing interface configurations. If you want to use mixed mode, it is easiest to install the Screen software in Routing mode and then configure the Stealth interfaces. Please see the SunScreen Configuration Examples manual for details on how to configure a mixed-mode Screen.
Configuring additional interfaces for mixed-mode requires some care. Please refer to the SunScreen Administration Guide and the SunScreen Configuration Examples before you attempt to configure more than one interface in mixed mode.
Before You Install
Before you install SunScreen 3.1 , you should complete the following tasks:
-
Be acquainted with these documents:
-
SunScreen Release Notes
-
SunScreen SKIP 1.5.1 User's Guide
-
-
Ensure that the system that is to run SunScreen is secure--consider reinstalling the Solaris operating environment from CD-ROM to ensure that it has not been altered.
-
If you are using issued keys and certificates, make sure you have a set available for each host.
After installing SunScreen, you are ready to set up and implement the security policy for your network. For instructions on administering your SunScreen, refer to the SunScreen Administration Guide for detailed examples of SunScreen configurations, please see the SunScreen Configuration Examples manual.
Upgrading to SunScreen 3.1
You can upgrade previous versions of SunScreen EFS, SPF-200, or Firewall-1 to SunScreen 3.1 as described in the following sections.
Upgrading From Previous Versions of SunScreen
If you are presently running SunScreen EFS 1.1, 2.0, or 3.0 and you want to use the same configurations when you upgrade to SunScreen 3.1, read the information and instructions in "Upgrade Overview (SunScreen EFS 1.1, 2.0, or 3.0)". Since SunScreen 3.1 uses ordered packet filtering rules and ordered NAT mappings, you must review your packet filtering rules after the conversion is complete to verify the filtering order is correct. NAT mappings have changed considerably since the release of EFS1.1 and EFS 2.0. See the SunScreen 3.1 Reference manual for detail on NAT mappings.
To avoid corruption of your existing configurations, do not attempt to manually remove or add packages. Upgrading is not an initial installation, and the upgrade script removes packages as needed.
Upgrading From SPF-200 to SunScreen 3.1
You can upgrade the machine that presently operates as your SPF-200 Screen to become a SunScreen 3.1 Screen operating in stealth mode. You can also transfer your SPF-200 configurations to a new machine, and perform the conversion on the new machine. This second method is recommended and will decrease network downtime.
Since SunScreen 3.1 uses ordered packet filtering rules and ordered NAT mappings, you must review your packet filtering rules after the conversion is complete to verify the filtering order is as you want. NAT mappings have changed considerably since the release of SPF-200. See the SunScreen 3.1 Reference manual for detail on NAT mappings.
Instructions for upgrading from SPF-200 are in "Upgrading From SunScreen SPF-200 to SunScreen 3.1 in Stealth Mode."
Converting From FireWall-1 to SunScreen 3.1
If you are presently using FireWall-1 and plan to use a similar security policy on SunScreen, you have two ways to do this:
-
You can convert the FireWall-1 machine to become the SunScreen Screen.
-
You can convert the FireWall-1 security policies and use them on a SunScreen machine.
Conversion instructions are in "Converting FireWall-1 to SunScreen in Routing Mode.".
Trusted Solaris
You can install and use SunScreen 3.1 on a machine running Trusted Solaris 7. See "Installing on Trusted Solaris" for more information.
Security Issues
The machines that are used as gateways, or that are in vulnerable positions on the network, should have only the minimum Solaris packages installed. This action reduces the number of potentially exploitable applications.
If you do not need Solaris applications on a SunScreen machine, consider installing the software in stealth mode with the hardened OS feature. This configuration is discussed in "Installing in Stealth Mode.".
Software and Hardware Requirements
The following table lists the minimum hardware and operating system requirements for installing SunScreen.
Table 1-1 SunScreen 3.1 Installation Requirements
Operating System Package Requirements
You should ensure that the required Solaris packages reside on both the Screen and the Administration Station.
Screen Solaris Packages
If you do not plan on using the administration GUI on your Screen (either because you are doing remote administration or you have chosen to use only the command line interface for administration) you will only need to install the Core distribution of Solaris as well as the packages listed in this section.
Note -
If you only install the Core Distribution of Solaris, you will either have to change your DISPLAY variable for using the installer to a machine with a windowing system or install using the command line installation procedure described in "Command Line Installation."
If you plan on using the administration GUI on your Screen itself, you will need to install the End User Distribution of Solaris, as well as the packages listed in the following table.
Table 1-2 Screen Solaris Packages|
Type of Package |
Package Name |
Description |
|
system |
SUNWeuluf |
TF-8 L10N For Language Environment User Files |
|
system |
SUNWjvjit |
Java JIT compiler |
|
system |
SUNWjvrt |
JavaVM run time environment |
|
system |
SUNWlibC |
SPARCompilers Bundled libC |
|
system |
SUNWlibms |
SPARCompilers Bundled shared libm |
|
system |
SUNWsprot |
SPARCompilers Bundled tools |
|
system |
SUNWtoo |
Programming Tools |
|
system |
SUNWvolr |
Volume Management (Root) |
|
system |
SUNWvolu |
Volume Management (Usr) |
|
system |
SUNWxwice |
ICE components |
|
system |
SUNWxwplt |
X Window System platform software |
|
system |
SUNWxwrtl |
X Window System & Graphics Runtime Library Links |
|
system |
SUNWmfrun |
Motif RunTime Kit |
|
system |
SUNWloc |
System Localization |
|
system |
SUNWdoc |
Documentation Tools |
Administration Station Solaris Packages
If you will be using a remote Administration Station, add the following packages to the Administration Station from your Solaris CD, if not already on your system:
Table 1-3 Administration Station Solaris Packages|
Type of Package |
Package Name |
Description |
|---|---|---|
|
system |
SUNWjvrt |
JavaVM run time environment |
|
system |
SUNWmfrun |
Motif RunTime Kit |
|
system |
SUNWxwplt |
X Window System Platform software |
Note -
In addition to the patches provide by SunScreen, make sure you install all recommended security patches available for your operating environment. For security reasons, you should always keep your operating environment up to date with available patches.
Additional Requirements and Restrictions
-
SunScreen 3.1 only supports IPv4 in the Solaris 8 operating environment.
-
The SunScreen 3.1 CD includes the SunScreenTM SKIP for Solaris software. The PC version of SKIP is available separately or as part of the Secure Net bundle.
-
A remote Administration Station can connect directly to a Screen only through an Ethernet local area network (LAN) or a Fiber Distributed Data Interface (FDDI). An Administration Station can connect to the Screen by an Asynchronous Transfer Mode (ATM) or Token Ring LAN, but only after it is connected directly to the network by way of an Ethernet or FDDI connection first.
-
If you will be operating the Screen in routing mode, configure all network interfaces that will be used. See the documentation accompanying the Solaris operating environment, if needed.
-
If you will be operating the Screen in stealth mode, configure only the network interface that will be used for remote administration. See the documentation accompanying the Solaris operating environment, if needed.
Web Browser Requirements
SunScreen allows any machine with a Java-enabled web browser compliant with JDK 1.1.3 or later to function as as an Administration Station. But, the version of the JVM or plug-in you are using with the browser dictates the operations you are able to perform on the Administration Station. You can use any supported browser to look at status information and logs as well as modify and save policy configurations. However, some browser configurations do not support local system access.
Accessing Local System Resources
Because Netscape Navigator and Internet Explorer do not support the Java mechanism for applet signing, the administration GUI cannot get access to your system's local resources (browser security mechanisms prevent this type of access.)
The operations that require access to your local system resources are:
-
Loading certificates from a diskette
-
Backing up all policies
-
Restoring all policies
-
Saving log files
-
Loading jar signatures
If you do not need to perform any of these operations, you can use any of the supported browsers without local file access. To work around local access limitation you can use one of the following options:
-
Use the Java plug-in.
-
Use the HotJava browser version 1.1.
Browsers Without Local File Access
-
Netscape Navigator 4.5, or higher, with its own Java VM has the limitation that you cannot read or write files.
-
IE 4.01 with its own JVM has the limitation that you cannot read or write files.
Browsers With Local File Access
The following Web browsers support local file access using the required Java plug-in.
-
HotJava browser.
-
IE 5.0 with its own JVM, this configuration can read or write files but is not a supported configuration.
Note -The Netscape Navigator default Java plug-in provided with Solaris 8 is not compatible with the SunScreen administration applet. To save log files and load certificates using Netscape Navigator 4.5 or 4.7, you must install the older version of the Java plug-in or use the HotJava browser (included).
SunScreen 3.1 provides the required Java plug-in (version 1.1.2) as part of its distribution. The plug-in is located in the directory javaplugins.To install it, see the following plug-in installation instructions.
To Install the Required Java Plug-In
This procedure shows how to install the Java plug-in 1.1.2, save the identitydb.obj file, and set the NPX_PLUGIN_PATH environment variable.
-
Ensure that the SunScreen CD-ROM is inserted in the CD-ROM drive.
-
Navigate down the SunScreen directory structure to the plug-in location.
-
Install the Java plug-in by typing:
"% cp plugin-112i-solsparc.sh /tmp ""% cd /tmp ""% sh plugin-112i-solsparc.sh"
-
Save the identitydb.obj file by typing:
"% cd /opt/SUNWicg/SunScreen/admin/htdocs/plugin/plugins/""% cp identitydb.obj $HOME""% cd"
-
Set the environment variable if using sh or ksh by typing:
"$ NPX_PLUGIN_PATH=$HOME/.netscape/plugins:$NPX_PLUGIN_PATH""$ export NPX_PLUGIN_PATH""or if using csh:""% setenv NPX_PLUGIN_PATH $HOME/.netscape/plugins:$NPX_PLUGIN_PATH"
-
Run the Netscape browser and use the URL for the plug-in version of the administration GUI:
% netscape http://localhost:3852/plugin &
- © 2010, Oracle Corporation and/or its affiliates
