Chapter 2 Installation Considerations
This chapter describes the issues you should consider before installing SunScreen.
These issues include:
-
Determining your security policy
-
Mapping out your network configuration
-
Deciding on your initial level of security
-
Choosing which interfaces to use
Before installing, review the SunScreen Release Notes for the latest information about this product.
Determining Your Security Policy
Before installing the SunScreen software, you should first determine your network security policy. For a more thorough discussion of this topic, we suggest you read Computer Security Policies and SunScreen Firewalls by Kathryn M. Walker and Linda Croswhite Cavanaugh. Additional resources are listed in the Preface.
In brief, considerations when creating a security policy are:
-
what services do employees need to access?
-
what services do customers need to access?
-
will you allow Internet access, and if so, what services do users need to access?
-
what type of threat are you trying to protect your company from?
-
Do you need to use Network Address Translation (NAT)?
Mapping Your Network Configuration
Prior to installing SunScreen, you should make a map of your network. This will help identify any potential security problems inherent in the way the network is currently connected. A diagram of your network will aid installation and should include:
-
Routers to the Internet
-
FTP, WWW or TELNET servers
-
Application relay servers
-
Remote networks
-
Internal subnetworks
-
Your HA configuration
Deciding on Your Initial Security Level
You must determine your initial level of security. You have three possible security levels to choose from when installing SunScreen in Routing mode. Each security level corresponds to a different set of network services permitted to, from, and through the Screen. If you are in doubt about which security level to select for the Initial configuration, use a more permissive security mode. You can always reconfigure it to be more secure by changing the rules using the Administration GUI.
Note -
If you only install the Core Distribution of Solaris, you will either have to change your DISPLAY variable for using the installer to a machine with a windowing system or install using the command line installation procedure described in Appendix A, Command Line Installation.
Security Levels
The security levels are:
-
Restrictive--This level of security denies all traffic to, from, and through the Screen, except encrypted administration traffic. This level is best for deploying the Screen in a hostile network environment. It requires that static routing and the naming service have been configured on the host (that is, names must be resolved by means of a local hosts file).
-
Secure--This level of security denies all traffic to and through the Screen, except encrypted administration traffic. It allows common services (like NFS) from the Screen, naming service selection (such as, DNS and NIS), and routing (RIP). This level is a good starting point to get a Screen up and running on a friendly network, where the Screen may not be a stand-alone machine and may depend on NIS, DNS, or NFS to function properly.
-
Permissive--This level allows the same traffic as the Secure level and also allows inbound connections to the Screen itself and allows all traffic through the Screen. This security level is appropriate for installing the Screen on a machine that has multiple network interfaces and is acting as a router, or on a machine that is acting as a server (for example, for NFS, NIS, or HTTP).
Naming Services
You must also choose which naming service to use. You may choose one (NIS or DNS), both (NIS and DNS), or no naming service. Selection of NIS, DNS, or both NIS and DNS allows the name service packets to pass to the screen. To use a local host file, deselect both services.
Interfaces
In Routing mode, SunScreen automatically configures all plumbed Ethernet interfaces to filter. In Stealth mode, only the administrative port should be plumbed and all filtering interfaces should be configured using the SunScreen administration GUI after installation has completed. Stealth interfaces must not be configured in Solaris.
Once the following preparation criteria are met, continue to the appropriate chapter for your particular installation.
Worksheets for Defining Security Policies
Here are directions and worksheets to help you analyze and define your company's security policy requirements. Once established, SunScreen controls access to the network through a set of rules and interface definitions that are created in the administration GUI. The information you accumulate in this section will be used to define your policies. See the SunScreen Reference manual for more information. You can also find some useful examples in the SunScreen Configuration Examples manual.
To begin the process, create a group of all the IP addresses that SunScreen needs to know. SunScreen identifies network elements--network, subnetworks, and individual hosts--by IP address. Before you can define the rule, you must define all the elements or parts that make up the rule. Several types of addresses need to be defined in SunScreen.
Creating Service Groups
Use the following tables to assist you in creating service groups that use any combination of the individual network services. A useful group to define at many sites is an "internet services" group, consisting of public services, such as FTP, e-mail, and WWW. You might want to familiarize yourself with the set of pre-defined network services to avoid creating unnecessary duplicates.
Table 2-1 Services or Service Groups|
Name |
Definition |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Addresses
SunScreen uses IP addresses to define the network elements that make up the configuration. These addresses are then used in defining the Screen's network interfaces and as the source and destination addresses for rules and NAT.
The address can be for a single computer, or it can be for a whole network or subnetwork. Additionally, addresses (individual and network) can be grouped together to form an address group. SunScreen allows you to define address groups that specifically include or exclude other defined addresses (single IP hosts, ranges, or groups).
Table 2-2 Address Explanations
The following is an example of various types of addresses and can be used as a reference when completing your own network map.
Figure 2-1 Example of a Network Map
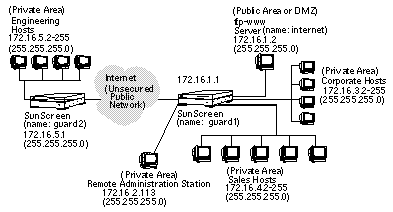
In this figure, the following examples of different types of addresses can be seen:
-
The ftp-www server is an example of a single host address (172.16.1.2).
-
Corporate, sales, and the engineering hosts are examples of ranges of addresses. For example, the range of addresses in the engineering hosts, 172.16.5.2 with the netmask 255.255.255.0, is defined as a range of addresses from 171.16.5.2 to 172.16.5.255.
The Internet is an example of a group of addresses, in this case defined as all. The ftp-www server is an example of a single address. The corporate, sales, and engineering hosts are examples of ranges of addresses.
The following worksheets help you organize the IP addresses. Expand them as necessary. Group the IP addresses and names for the following network elements:
Rules are used to control access to your computer network and to control encryption for access to your data. In preparing to implement rules, you have:
-
Determined the overall services that are available on your network
-
Determined the services available to a particular user or host and user groups over particular IP addresses
-
Determined the correct action for the service and addresses for that user or host.
Note -By default, the Screen drops any packets that do not specifically match a rule. This makes it easier to create rules, since you only have to write a rule for the services you want to pass.
|
Name |
IP Address |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-4 Address Ranges
|
Name |
Address |
|
|---|---|---|
|
|
Beginning |
Ending |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-5 Address Group
|
Name |
Address |
|
|---|---|---|
|
|
Include |
Exclude |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
NAT
NAT enables you to map from unregistered addresses to registered addresses allocated by your Internet service provider (ISP). The NAT function of SunScreen uses this translation to replace the IP addresses in a packet with other IP addresses. This allows you to use unregistered addresses to number your internal networks and hosts and yet have full connectivity to the Internet. With this approach, with a small Class C network, which supports only 254 hosts (externally), you can use a private Class B network, which supports as many as 65,000 hosts or 255 networks of 254 hosts (internally).
Table 2-6 NAT Map Table|
Type |
Address |
Translated Address |
||
|
Static/Dynamic |
Source |
Destination |
Source |
Destination |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-7 Screen's Interfaces
|
Type |
Interface Name |
Group Address |
Logging Details |
||
|
SNMP Alert |
Logging |
ICMP Reject |
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-8 Authorized Users
|
Name |
Authorized User |
Details |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-9 Administration Stations
|
Name of Certificate associated with Admin Station |
Address of Admin Station |
Key Algorithm |
Data Algorithm |
MAC Algorithm |
Admin User Name |
Access Level |
|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Rules
Use the Rules worksheet to organize the individual rules you want to use. Space is provided for you to create your own service groups. Make copies of the worksheet, as necessary.
A filled-in sample of the Rules worksheet with the requisite services that you may want for a particular network is shown below. Table 2-11.
Table 2-10 Rules|
Ordered Rule Index |
Service or Service Group |
Source Address |
Destination Address |
Action |
Encryption |
User or Groups of Users Optional |
Time of Day Optional |
Screen Optional |
|---|---|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 2-11 Sample for "Rules" Worksheet
|
Ordered Rule Index |
Service or Service Group |
Source Address(es) |
Destination Address(es) |
Action |
Encryption |
|
1 |
ftp |
Internal-net |
Internet |
ALLOW |
NONE |
|
2 |
ftp |
* |
ftp Server |
ALLOW |
NONE |
|
3 |
ftp |
Internet |
Internal-net |
DENY |
NONE |
Four Action Types
-
ALLOW options:
-
LOG_NONE
-
LOG_SUMMARY
-
LOG_DETAIL
-
SNMP_NONE
-
SNMP
-
A proxy type may be chosen if the service can be proxied by one of the SunScreen proxies.
-
-
DENY options:
-
LOG_NONE
-
LOG_SUMMARY
-
LOG_DETAIL
-
SNMP_NONE
-
SNMP
-
ICMP_NONE
-
ICMP_NET_UNREACHABLE
-
ICMP_HOST_UNREACHABLE
-
ICMP_PORT_UNREACHABLE
-
ICMP_NET_FORBIDDEN
-
ICMP_HOST_FORBIDDEN
-
-
ENCRYPT options:
-
NONE
-
SKIP_Version_1 (for connection to a SunScreen SPF-100 only)
-
You must decide on:
-
Key Algorithm list (depends on the SKIP version chosen: Domestic or Global)
Data Algorithm list (depends on the SKIP version chosen: Domestic or Global)
SKIP_Version_2 (for connection to all other SKIP-enabled devices) (Optional: Tunnel addresses are allowed.)
You must decide on:
-
From Encryptor list
-
To Encryptor list
-
Key Algorithm list (depends on the SKIP version chosen: Domestic or Global)
-
Data Algorithm list (depends on the SKIP version chosen: Domestic or Global)
After you define and map out your network and decide on your policy, you use data objects, such as services and addresses, to configure SunScreen with the policy rules to control access to your network. When you installed SunScreen, you automatically created a Policy named "Initial," which you can use connect build your own Security Policies.
- © 2010, Oracle Corporation and/or its affiliates
