Defining a VPN
A VPN is a group of Screens that transfer encrypted data among themselves. A VPN simulates a private network using a public network, with IP level encryption providing privacy.
After a VPN has been defined, you can refer to this VPN when adding rules to your security policy. VPNs make it possible for you to define your security policy with fewer rules. The system automatically generates the multiple rules that the VPN defines.
In defining a VPN:
-
Choose a name for the VPN. This name is used in the Name field in the VPN gateway entries. It is also used in any policy rules that refer to this VPN.
-
Define a VPN gateway object for each Screen in a VPN. You define VPN gateway objects in the administration GUI using the VPN Definition dialog box that is accessible from the VPN tab in the Policy Rules. page
When defining a VPN gateway object, specify the following information:
-
Rule Index - (Optional) Assigns a number to the VPN gateway entry. This affects the position within the VPN gateway list. By default, the GUI will place new entries at the end of the current list. Remember that SunScreen uses ordered rules, so be sure to place the rule in the order in which you want it to take effect.
-
Name - This is the name of the VPN to which this VPN gateway is a member. Use the name you chose for the VPN.
-
Address - Specify the addresses protected by this Screen. Generally, this address will be the same as one of the interface addresses for this Screen.
Note -You can use any address in the VPN rules. Only addresses that interact with a VPN gateway and the address specified in the rule will apply. The simplest rule uses * for the source and destination address. This rule allows encrypted use of the specified service for all addresses in the VPN.
-
Certificate - Specify the certificate used for this Screen when encrypting packets to other Screens in the VPN. For a particular VPN, all certificates must refer to keys of the same strength (for example, 512-, 1024-, 2048-, or 4096-bit Diffie-Hellman keys).
-
Key Algorithm - Specify the key algorithm that is used when encrypting packets to other Screens in the VPN. This field must be identical in all VPN gateway entries with the same VPN name.
-
Data Algorithm - Specifies the data algorithm that is used when encrypting packets to other Screens in the VPN. This field must be identical in all VPN gateway entries with the same VPN name.
-
MAC Algorithm - Specifies the MAC algorithm that is used when encrypting packets to other Screens in the VPN. This field must be identical in all VPN gateway entries with the same VPN name.
-
Tunnel Address - Specifies the Screen's tunnel address that is used when encrypting packets to other Screens in the VPN.
-
Description - Optionally, specify a short description of this VPN gateway entry.
Consider a site, similar to that shown in Figure 6-4, that has ten Screens. One of the systems protected by each Screen is a mail server. Assume that your security policy allows the exchange of encrypted mail between all these mail servers and you want to define rules to allow SMTP between all of the mail servers.
Figure 6-4 A Site of Ten Networks, Each with a Mail Server, Protected by Ten Screens
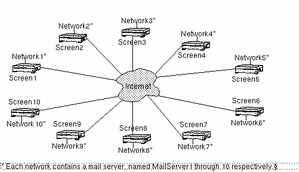
Without a VPN, you must define nine rules for each mail server to send mail encrypted to the other nine mail servers. Because you have ten mail servers, you must define a total of 90 rules. If, instead you defined a VPN, you only need a single rule: one that allows the mail servers to send mail to the other mail servers using the VPN. Because you have ten Screens in the VPN, you must define ten VPN gateway entries.
Looking at this example in detail, FIGURE 6-4 shows the configuration. The Screens are labeled Screen1 through Screen10. The mail servers behind them are labeled mail1 through mail10 and are part of network1 through network10.
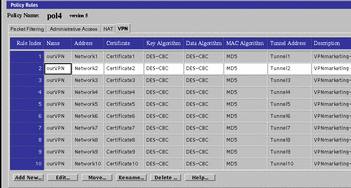
The first step is defining the VPN itself. Choose a name for the VPN. In this example, that name is "ourVPN." Next, for each Screen that is a member of that VPN, define a VPN gateway object. For each VPN gateway object, specify the VPN name (ourVPN), the addresses of the systems that the Screen protects, the Screen's certificate, the tunnel address, and the encryption parameters that will be used for the VPN. All VPN gateway objects in a particular VPN must have identical encryption parameters, and the certificates must refer to keys of the same strength (512-, 1024-, 1124-, 1280-,2048-, 2176-, 3072-, or 4096-bit Diffie-Hellman keys).
Once you have defined the VPN objects, as shown in FIGURE 6-5, you can use the VPN in any rule. Select SECURE as the action for the data between the sender and the SMTP server, and specify the name of the VPN.
Figure 6-5 Policy Rules Panel Showing the VPN Tab with VPN Entries
Adding a VPN Rule
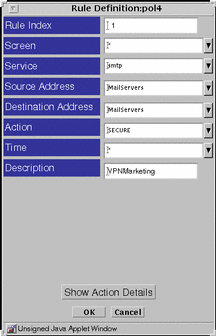
Assuming an address group MailServers containing all the mail servers exchanging encrypted mail, define the rule in the Rule Definition dialog box shown in FIGURE 6-6.
Figure 6-6 Completed Rule Definition Dialog Box for the VPN Rule
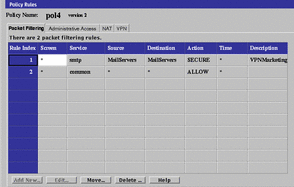
The VPN rule appears on the Packet Filtering tab of the Policy Rules page. The more restrictive a rule is, the earlier it should be ordered in the list of rules because the rules take effect in order. The more restrictive VPN rule comes before the more general rule and so will take effect earlier.
Figure 6-7 VPN Rule
There is no limit to the number of VPNs to which a Screen can belong. For example, you can to define two VPNs--one for encryption at 1024 bits, and one for encryption at 4096 bits. A single Screen can belong to both of those VPNs: one entry specifying the 1024-bit certificate, and the other specifying the 4096-bit certificate.
VPN Limitations
Currently, the VPN object has the following limitations:
-
All certificates on the gateways of a particular VPN must be of the same strength. If you want to have different encryption strengths in your configuration, you must define multiple VPNs, one for each strength.
-
The key, data, and MAC algorithms must be the same for all gateways within a VPN.
- © 2010, Oracle Corporation and/or its affiliates
