The Log Browser Tabs on the Information Page
Clicking one of these tabs displays the status, logs, and the traffic and SKIP statistics.
Status Tab
The Status tab is displayed by default. The Status tab displays the information shown in FIGURE 5-3. This information is derived from the system and the configuration of the firewall when you installed the SunScreen or modified the configuration. You cannot edit any of the fields on this page.
Figure 5-3 SunScreen Information Page--Status Tab
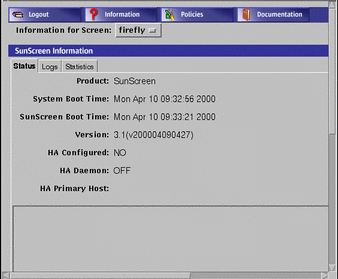
TABLE 5-3 describes the information presented on this page.
Table 5-3 Status Information|
Title |
Description |
|---|---|
|
Product |
The name of the software product. |
|
System Boot Time |
Date and time when the system was last restarted. |
|
SunScreen Boot Time |
Date and time when the system was last restarted. |
|
Version |
The release of the software that is running. |
|
HA Configured |
Whether high availability (HA) is configured (YES or NO). |
|
HA Daemon |
Whether the high availability daemon is running (OFF or ON). If the HA daemon is running, the members of the HA cluster appear in the area below along with the state of each member of the HA cluster (Active or Passive). |
|
HA Primary Host |
The name or IP address of the primary host of the high availability cluster. |
|
Host Names |
Lists the hosts configured for HA. This information appears in the area set off from the rest of the information and is updated by default every 30 seconds. You can change the update interval by changing the poll interval in the Logs tab. |
|
Status |
Shows the status of the primary and secondary HA hosts. The status is ACTIVE, PASSIVE, and NONRESPONSIVE. This information appears in the area set off from the rest of the information and is updated by default every 30 seconds. You can change the update interval by changing the poll interval in the Logs tab. |
|
Help button |
Displays the online help for this page. |
Logs Tab
The logs tab displays the Log Browser panel, as shown in FIGURE 5-4.
Figure 5-4 SunScreen Information Page--Logs Tab
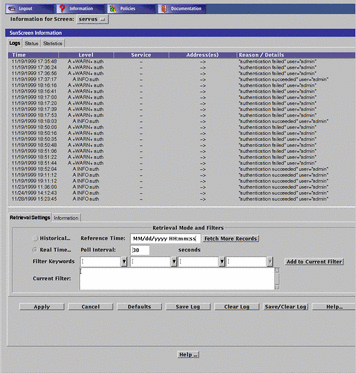
TABLE 5-4 describes the column headings for the log panel of the SunScreen Information page.
Table 5-4 Column Headings on the Log Panel of the SunScreen Information Page|
Field |
Description |
|---|---|
|
Time |
Indicates the time that the packet or event represented by this record was logged by the Screen. Use this time field to retrieve records in Historical mode as set in the Log Browser Tab Retrieval Setting. |
|
Level |
Indicates the type and severity level of the logged event. |
|
Service |
Indicates the network service or protocol, such as TCP, IP, NFS, Telnet, or HTTP, over which this packet was sent or to which the event is related. |
|
Address(es) |
Shows the address from which and to which a packet was sent. Arrows indicate direction. Some events that, by themselves, are not related to IP traffic will not have an address or addresses, as shown in the example. |
|
Reason/Detail |
Shows the reason a packet or event was logged or the detail regarding the logging. This information depends on the requirements of the rules within a policy. |
The logs tab also displays the Retrieval Setting tab and Information tab for the logs.
Logged packets are configured in the packet filtering rules so that a packet or an event is displayed which meets the requirements of a rule in a policy. The log has two retrieval modes: Historical and Real Time.
-
The Historical mode allows you to examine a particular segment for a particular time.
-
The Real Time mode displays information as the packets pass through the Screen while you are looking at the log.
For more information setting the values for the log browser, see the section on the "Retrieval Setting Tab" below.
Retrieval Setting Tab
FIGURE 5-5 shows the Retrieval Setting tab for the SunScreen Information page and the log browser in particular. The Filter Keywords, Add to Current Filter, and Current Filter controls are discussed in greater detail in the following section, "Setting a Log Viewing Filter."
Figure 5-5 Retrieval Setting Tab
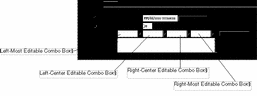
TABLE 5-5 describes the controls on the Retrieval Setting tab.
Table 5-5 Controls on the Retrieval Setting Tab
Setting a Log Viewing Filter
The Log Browser filters log events to be displayed. The language that it uses is identical to the filtering options of the logdump command in the command-line program; it is a superset of the language used by the Solaris snoop packet monitor tool.
You have full access to this language typing an arbitrary logdump expression in the Current Filter text entry box in its Retrieval Settings tab and clicking the Apply button to activate it.
In addition, the Filter Keywords controls provide the ability to create many simple filtering expressions. These controls reduce typing effort as well as serving as reminders of filtering options.
The Filter Keywords controls are used by selecting one or more operations from their choice lists or entering a target (operand) in the rightmost editable combo box. After this choosing or typing your entry, click the Add to Current Filter button to add these items to the Filter Keywords text entry box at its current insertion pointer.
The leftmost editable combo box contains the Boolean operators and, or, and not.
The left-center editable combo box provides filtering terms that are complete and restrict the type of log event displayed. TABLE 5-6 describes the terms in the left-center editable combo box.
Table 5-6 Filter Terms of the Left-Center Editable Combo Box|
Term |
Description |
|---|---|
|
loglvl pkt |
Allows displaying network packet-type events |
|
loglvl sess |
Allows displaying network session-type events |
|
loglvl auth |
Allows displaying events related to authentication operations |
|
loglvl app |
Allows displaying events related to screen application (usually proxy) operations |
|
logapp auth |
Allows displaying events from the authentication subsystem |
|
logapp edit |
Allows displaying events related to registry or policy editing |
|
logapp ftpp |
Allows displaying events from the FTP proxy |
|
logapp log |
Allows displaying events related to the logging facilities themselves |
|
logapp httpp |
Allows displaying events from the HTTP proxy |
|
logapp smtpp |
Allows displaying events from the SMTP proxy |
|
logapp telnetp |
Allows displaying events from the Telnet proxy |
|
logsev emerg |
Allows displaying events of an emergency severity |
|
logsev alert |
Allows displaying events of an alert severity or above |
|
logsev crit |
Allows displaying events of a critical severity or above |
|
logsev err |
Allows displaying events of an erroneous severity or above |
|
logsev warn |
Allows displaying events of a warning severity or above |
|
logsev note |
Allows displaying events of a notice severity or above |
|
logsev info |
Allows displaying events of an informative severity or above (all events that are not of debug severity) |
|
logsev debug |
Allows displaying events of a debug severity or above (all events) |
The right-center editable combo box provides filtering terms most of which are incomplete and require an operand value, You type these in the rightmost editable combo box. They are added to the choice list of the rightmost editable combo box for reference so that you need not retype the value if you want to use it again. TABLE 5-7 describes the filter terms in the right-center editable combo box.
Table 5-7 Filter Terms in the Right-Center Editable Combo Box|
Term |
Description |
|---|---|
|
logwhy reason# |
Restricts display to packets that have the given logging reason why code (See Appendix D, Error Messages, TABLE 11-16 |
|
logiface iface |
Restricts display to packets that arrived on the interface named iface |
|
host hostname |
Restricts display to events either from or to hostname |
|
dst hostname |
Restricts display to events destined for hostname |
|
src hostname |
Restricts display to events origination from hostname |
|
port hostname |
Restricts display to events related to the service svcname |
|
dstport hostname |
Restricts display to events targeted to the service svcname |
|
srcport svcname |
Restricts display to events originating from the service svcname |
|
net netaddr |
Restricts display to events either from or to the network whose number is netaddr |
|
gateway gwyaddr |
Restricts display to packets that used gwyaddr as a gateway |
|
udp |
Restricts display to events related to the UDP transport protocol |
|
tcp |
Restricts display to events related to the TCP transport protocol |
|
icmp |
Restricts display to packets of the ICMP control protocol |
|
rpc |
Restricts display to packets of the RPC protocol |
|
etheraddr etheraddr |
Restricts display to packets that have arrived from this Ethernet address |
The terms in italics are variables for which you must supply a value or values in the when you choose this term from the choice list. The values for the variable are as follow:
-
reason # The reason number is shown in TABLE 11-16 in Appendix D, Error Messages.
-
hostname can be:
-
svcname can be:
-
A numeric TCP or UDP port number (for example, 23 for Telnet)
-
A numeric TCP or UDP port number range (for example, 6000. .6023 for X windows)
-
A service name known to the screen's naming service (for example, domain found in /etc/services)
-
-
iface can be:
-
The name of an interface (for example hme0)
-
-
netaddr can be:
-
The IP network number (for example 199.12.200)
-
-
gwyaddr can be:
-
The name of an Ethernet address (link-layer address gateway through which packets are flowing)
-
-
etheraddr can be:
-
The 6-octet Ethernet address (for example 8:0:20:A0:EE:E4)
-
The Information Tab
The log-browser Information tab on the Screen Information page and shown in FIGURE 5-6, provides the statistics for the current log.
Figure 5-6 Information Tab
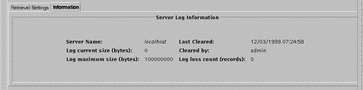
TABLE 5-8 describes the fields on the Information tab. You cannot edit the fields on this page.
Table 5-8 Fields on the Information Tab|
Control |
Description |
|---|---|
|
Server Name field |
Indicates the name of the Screen to which the Log Browser is connected. |
|
Log current size field (bytes) |
Indicates the current size of the log file in bytes on the server. |
|
Log maximum size filed (bytes) |
Indicates the maximum size of the log file in bytes on the server. |
|
Last Cleared field |
Indicates the date and time the log file was last cleared. |
|
Cleared By field |
Identifies the login name of the administrator who last cleared the log file. |
|
Log loss count (records) field |
Indicates the number of log records that have been thrown away since the last "clear" operation. Log records are lost if the log grows beyond its maximum size or if the file system on which the log is written fills before that maximum is reached. Packets that cannot be logged because the traffic load exceeds the logger's ability to store entries are not counted. |
- © 2010, Oracle Corporation and/or its affiliates
