Detailed NAT Configuration
The following steps are needed to complete the NAT configuration for this example:
-
Install and configure Screen sf-screen1 in routing mode using the remote Administration Station sf-host4.
For instructions on configuring a Screen in routing mode, refer to the section "Installing the Screen in Routing Mode" as described in the first example in this document.
-
Create an address object for the host sf-host1 with the private, unregistered address 10.0.1.1.
-
Create an address object for the public, registered IP address (192.168.2.101 for this example) and give it a name (sf-host1-legal for this example).
-
Check that the packet filtering rule(s) have been created to ALLOW appropriate traffic to pass to and from the web server sf-host1.
-
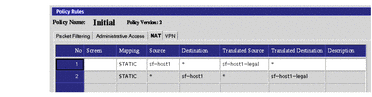
Create a STATIC NAT rule to translate the addresses from sf-host1-legal to sf-host1.
This enables hosts on the Internet to connect to the IP address for sf-host1-legal, which translates to sf-host1. Because the SunScreen firewall software keeps state information about its NAT connections, return packets from sf-host1 to a host on the Internet are translated back to sf-host1-legal (192.168.2.101 in this example) as they leave the Screen.
When it is required for host sf-host1 to initiate a connection to a host on the Internet (* in this example), add a second NAT rule to translate sf-host1 to sf-host1-legal, as shown in the following figure.
Figure 3-2 STATIC NAT Rules
-
Add an arp entry on sf-screen1 to enable it to respond to ARP requests from sf-router1 for the public, registered IP addresses it is performing NAT on by typing:
# arp -s translated-ip-addr screen-ethernet-addr pub
where translated-ip-addr is the public, registered IP address (192.168.2.101 for this example) and screen-ethernet-addr is the Ethernet address of the Screen.
Run the arp command for each legal IP address that sf-screen1 is performing NAT on.
Place this command in a start-up script to run each time the system boots as it is only valid until the Screen is rebooted.
The following shows an example of an arp start-up script used for STATIC and DYNAMIC NAT (see the following section on DYNAMIC NAT):
# /etc/rc2.d/S70sunscreenARP #!/bin/sh # startup script example to publish ARP entries # for IP addresses sunscreen performs NAT on # # First STATIC mapping arp -s 192.168.2.101 8:0:20:a3:ec:27 pub # Second STATIC mapping arp -s 192.168.2.102 8:0:20:a3:ec:27 pub # Next three are the addresses used by DYNAMIC NAT arp -s 192.168.2.103 8:0:20:a3:ec:27 pub arp -s 192.168.2.104 8:0:20:a3:ec:27 pub arp -s 192.168.2.105 8:0:20:a3:ec:27 pub
-
Save and activate your policy.
-
Verify that connections work to and from the host being translated, and that the translation is actually taking place.
For example, run snoop both inside and outside the sf-screen1 Screen and try a ping from sf-host1 to sf-router. If the configuration is set up correctly, the result should be that sf-router is alive, and the snoop output should look like the following:
Inside the Screen:
sf-host1 -> sf-router ICMP Echo request sf-router -> sf-host1 ICMP Echo reply |
Outside the Screen:
192.168.2.101 -> sf-router ICMP Echo request sf-router -> 192.168.2.101 ICMP Echo reply |
DYNAMIC NAT
The other type of NAT supported by SunScreen is DYNAMIC. For this example the hosts sf-host2, sf-host3, and so forth, need access to the Internet. Their source addresses are translated to a legal address sf-dynamic (192.168.2.103 in this example).
-
Define an address GROUP object called sf-internal and add all the internal hosts (sf-host1, and so forth) that need to use DYNAMIC NAT to this group.
-
Define an address HOST object (sf-dynamic in this example) that contains the legal address (192.168.2.103 in this example).
Note -DYNAMIC NAT can use a range of addresses. In this example, sf-dynamic can be a RANGE or GROUP object.
-
Add an ARP entry for the legal address sf-dynamic, as described in the proceeding STATIC example.
-
Add a rule to translate sf-internal to sf-dynamic, as shown in the following figure:
Figure 3-3 DYNAMIC NAT Rule

- © 2010, Oracle Corporation and/or its affiliates
