Setting Up Telnet User Authentication
This example shows six user names that need access to the 10.0.3.0 network: William, Henry, Beatrice, Eugenie, Peter, and Zara.
-
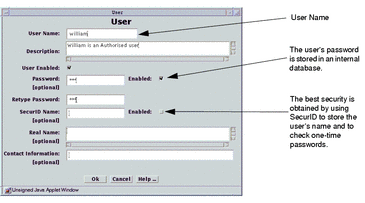
Define each of your users as an Authenticated User, as shown in the following figure:
Figure 9-2 Authenticated User Definition
-
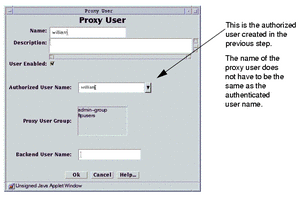
Define each of your users as a Proxy User, as shown in Figure 9-3.
That is, define only those users who are qualified to use the proxy for authentication.
Figure 9-3 Proxy User Definition

-
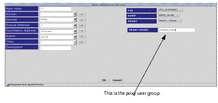
Create a rule to ALLOW proxy access that references either a single Proxy User, or, more usually, a GROUP of Proxy Users, as shown in the following figure.
Figure 9-4 Proxy User Name Used in the Rule
-
Define a Proxy User GROUP with all the your users.
-
Add a rule to ALLOW telnet with Proxy AUTHENTICATION, as shown in the following figure.
Figure 9-5 ALLOW telnet Rule
-
Save and activate the configuration.
- © 2010, Oracle Corporation and/or its affiliates
