Chapter 8 Converting FireWall-1 to SunScreen in Routing Mode
This chapter explains how to convert from FireWall-1 (Release 3.0, 4.0, or 4.1) to a SunScreen system in routing mode.
Topics covered include:
Before installing the software, review the SunScreen 3.2 Release Notes for the latest information about this product.
Preparing Your FireWall-1 Configuration
Before you convert your FireWall-1 system, read this section carefully. There are certain limitations that you must address before running the conversion utility. You can experience unrecoverable errors that require restarting the migration. Your existing FireWall-1 configurations are not modified by this tool. You must first review your existing FireWall-1 configurations and modify those that will not convert directly to SunScreen rules. This section lists these known limitations.
Check your FireWall-1 configuration files and edit any that contain:
If any of the following reserved characters or words are used, you need to remove or replace them.
Known FireWall-1 Reserved Characters
- ` ` (space)
- `*'
- `)`
- `{`
- `[`
- `!'
- `<`
- `='
- `:' (colon)
- `'' (quote)
- `"' (double quote)
- `\' (back slash)
- `+'
- `?'
- `)'
- `}'
- `]'
- `#'
- `>'
- `,' (comma)
- `:' (semicolon)
- ``' (back quote)
- `/' (slash)
- `\t' (tab)
Known FireWall-1 Reserved Words
The following are known reserved words that must not appear in the FireWall-1 object names, and must be edited prior to conversion:
- "accept"
- "and"
- "black"
- "blue"
- "broadcasts"
- "call"
- "cyan"
- "dark green"
- "dark orchid"
- "date"
- "day"
- "define"
- "delete"
- "direction"
- "do"
- "domains"
- "drop"
- "dst"
- "dynamic"
- "expcall"
- "expires"
- "firebrick"
- "foreground"
- "forest"
- "forest green"
- "format"
- "from"
- "fwline"
- "fwrule"
- "gateways"
- "get"
- "gold"
- "gray 101"
- "green"
- "if"
- "ifaddr"
- "ifid"
- "in"
- "inbound"
- "interface"
- "interfaces"
- "ipsecdata"
- "ipsecmethods"
- "hold"
- "host"
- "hosts"
- "kbuf"
- "keep"
- "limit"
- "log"
- "magenta"
- "medium slate"
- "medium slate blue"
- "modify"
- "navy blue"
- "netobj"
- "netof"
- "nets"
- "nexpires"
- "not"
- "or"
- "orange"
- "origdst"
- "origsport"
- "origsrc"
- "other"
- "outbound"
- "packet"
- "packetid"
- "pass"
- "r_arg"
- "r_cdir"
- "r_cflags"
- "r_ckey"
- "r_connarg"
- "r_ctype"
- "r_entry"
- "r_proxy_action"
- "r_tab_status"
- "r_xlate"
- "record"
- "red"
- "resourceobj"
- "refresh"
- "reject"
- "routers"
- "servers"
- "servobj"
- "set"
- "sienna"
- "skippeer"
- "src"
- "static"
- "sync"
- "targets"
- "to"
- "tod"
- "tracks"
- "ufp"
- "vanish"
- "wasskipped"
- "xlatedport"
- "xlatedst"
- "xlatesport"
- "xlatesrc"
- "xor"
- "yellow"
What Configurations Convert From FireWall-1
The following limitations apply when converting FireWall-1 configurations to SunScreen. Some object-types and rules migrate with no difficulty, while others do not. FireWall-1 rules that do not migrate, contain an operation (on the Source, Destination, or Service) that SunScreen does not support. The following table lists what will and what will not migrate from FireWall-1 to SunScreen.
Table 8-1 What Converts From FireWall-1|
Does Convert |
Does Not Convert |
|---|---|
|
Host objects |
Resources |
|
Group objects |
NAT mappings |
|
Network objects |
Gateway objects |
|
Most rules |
Encryption and authentication information and rules |
|
|
Domain objects |
|
|
Router objects |
|
|
Switch objects |
|
|
Logical objects |
|
|
FW-1 services or user defined services |
|
|
Install objects |
|
|
Rules containing any object or service that will not migrate |
|
|
Using an object type as an object name |
SunScreen Conversion Utility
The following procedures explain how to install, generate, and run the conversion utility.
To Install the Conversion Utility
-
Open a terminal window and become root on the FireWall-1 system.
-
Change to the directory containing the SunScreen 3.2 product.
#cd /cdrom/cdrom0/Solaris_9/ExtraValue/CoBundled/SunScreen_3.2/sparc
-
Add the software by typing:# pkgadd --d . SUNWfwcnv
-
Continue the installation when prompted by pressing Return.
The various files in SUNWfwcnv are displayed as they are installed. The installation ends with the following message: Installation of SUNWfwcnv was successful.
The SunScreen conversion utility is now installed in /opt/SUNWfwcnv/bin.
Generating Conversion Files
The following procedures explain how to generate conversion files.
The fwconvert utility (located in /opt/SUNWfwcnv/bin) generates files that create the SunScreen configuration from the original FireWall-1 configuration. fwconvert examines the rules and objects in your FireWall-1 security policy and generates new configuration files with commands for configuring SunScreen.
fwconvert uses the following FireWall-1 configuration files:
-
policyname.W, for FireWall-1, Release 2.1, files
-
policyname.pf, for FireWall-1, Release 3.0 and later files
-
objects.C, for FireWall-1, Releases 3.0, 4.0, and 4.1 files, where policyname is either default or the name you have given your policy. These files are located in the /opt/SUNWfw/conf directory.
Verify the location of these files and the name of the policy file (indicated by the .pf or .W extension) before you run fwconvert.
Note -
You must run the conversion utility on the FireWall-1 system even if you are configuring SunScreen on a different system.
To Run the Conversion Utility
-
Open a terminal window and become root on the FireWall-1 system.
-
Run the conversion utility by typing:
# /opt/SUNWfwcnv/bin/fwconvert &
fwconvert displays the FW-1 Configuration Converter dialog box with the default values already inserted.
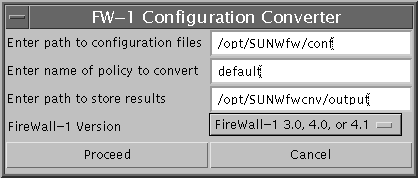
-
Type the path name where the FireWall-1 conversion files are located, or accept the default, if appropriate.
-
Type the name of the policy file you want to convert, if different from the default.
Note -Do not type the .pf or .W extension.
-
Type the name of the directory where you want to store the new configuration files. Make sure the directory actually exists before you proceed. Otherwise, accept the /opt/SUNWfwcnv/output default.
-
Choose the release number of your FireWall-1 software from the Version menu, or accept the default, if appropriate.
-
Click Proceed to begin the conversion.
fwconvert reads the file policyname.pf (or policyname.W) and the objects.C files and generates the files used to create the SunScreen configuration.
When fwconvert completes successfully, the FireWall-1 Configuration Converter dialog box displays a DONE button.
-
Click DONE to exit fwconvert.
-
Verify the converted rules.
For more information, see "Verifying the Converted Rules."
After the conversion completes, the generated configuration files are located in the directory you specified in the FireWall-1 Configuration Converter dialog box (/opt/SUNWfwcnv/output by default). The policyname_Objects and policyname_Rules files must reside in the same directory as policyname_sscfg before you can run the policyname_sscfg generation program. Look at these files to confirm that the information converted correctly.
Troubleshooting the fwconvert Utility
The following describes how to troubleshoot the fwconvert utility.
The following conditions can cause the conversion to fail:
-
You do not have permission to read files in /opt/SUNWfw/conf or the directory you specified as the location of the FireWall-1 configuration files.
-
You do not have permission to write files into the directory that you specified for storing the results of fwconvert.
-
The path names that you specified to the Converter are incorrect.
-
The policy name that you specified is incorrect.
-
One of the FireWall-1 configuration files you need to convert is missing.
When fwconvert encounters these conditions, it displays an error message in the FW-1 Converter dialog box, as shown in the following figure.
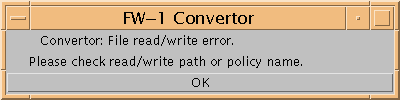
Note -
When data cannot be parsed, this error is displayed on the terminal window and not in the FW-1 Converter dialog box.
To Clear Conversion Errors (Except Parse Errors)
-
Click the OK bar to clear the error message in the FW-1 Converter dialog box.
-
Change permissions on the affected directories, if applicable.
-
Fill in the corrected information in the fwconvert FW-1 Converter dialog box, making sure you have the accurate path names and file names that you need to specify.
-
Click the Retry button.
When it completes successfully, the FireWall-1 Configuration Converter displays the DONE button.
-
Click DONE to exit fwconvert.
fwconvert creates a set of files that are used to generate the SunScreen 3.2 configuration.
-
Verify the converted rules.
For more information, see "Verifying the Converted Rules" in SunScreen Installation Guide.
After the conversion completes, the generated configuration files are located in the directory you specified in the FireWall-1 Configuration Converter dialog box, (/opt/SUNWfwcnv/output by default). The policyname_Objects and policyname_Rules files must reside in the same directory as policyname_sscfg before you can run the policyname_sscfg generation program. Look at these files to confirm that the information was correctly converted.
To Clear Parse Errors
Note -
The most common parse error is caused by the use of a reserved character (such as a ` ` space) in an object name.
-
Edit the line containing the error manually.
-
Restart fwconvert.
See the procedure "To Install the Conversion Utility" in SunScreen Installation Guide, if needed.
Verifying the Converted Rules
fwconvert creates three types of files from the FireWall-1 configuration files: command, executable, and log files. See the following table for a complete list.
Table 8-2 Generated Configuration Files|
File Type |
File Name |
Description |
|---|---|---|
|
Data file |
policyname_Objects |
Contains the commands for configuring the SunScreen objects. |
|
Data file |
policyname_Rules |
Contains the commands for adding SunScreen rules that use the generated objects. |
|
Executable script |
policyname_sscfg |
Generates a SunScreen configuration from the commands in policyname_Objects and policyname_Rules. |
|
Log file |
policyname_Obj.log |
Contains the objects from FireWall-1 that are not supported by SunScreen. |
|
Log file |
policyname_Rule.log |
Contains the rules from FireWall-1 that could not be added. The rule is shown as a SunScreen rule command with an explanation of the reason why the rule is not supported. |
|
Log file |
policyname_Unused.log |
Lists the FireWall-1 objects that cannot be used in SunScreen. |
Command and Executable Files
When you create the new SunScreen configuration, you run the configuration program, which then executes the command files. You do not need to take further action on the command and executable files.
The following shows examples of these files.
Example 8-1 policyname_Objects File
# The address commands may contain other addresses which need to be created. # These objects are logged in the policyname_Obj.log file add_nocheck Address "mailhost-INT" HOST 205.167.60.6 COMMENT "Object from FW-1" add_nocheck Address "mailhost-EXT" HOST 207.82.121.5 COMMENT "Object from FW-1" add_nocheck Address "localnet" NETWORK 205.167.60.00 255.255.255.00 COMMENT "Object from FW-1" add_nocheck Address "talon" HOST 205.167.60.200 COMMENT "Object from FW-1" add_no |
check Address "exosecure-alc" HOST 207.82.121.254 COMMENT "Object from FW-1" save |
Example 8-2 policyname_Rules File
add_nocheck Rule "ip all" "*" "*" ALLOW LOG SUMMARY save |
Example 8-3 policyname_sscfg File (where policyname is 4complex)
#!/bin/csh setenv PATH .:/usr/bin:/usr/sbin:/bin:/usr/sbin echo Creating Policy: 4complex ssadm policy -a 4complex echo Adding Policy Addresses /usr/sbin/ssadm edit -P 4complex < 4complex_Objects echo Adding Policy Rules /usr/sbin/ssadm edit -P 4complex < 4complex_Rules echo Finished! |
Log Files
The log files describe instances where fwconvert could not directly convert your FireWall-1 policy to an equivalent SunScreen policy. After conversion, you should review the contents of the log files to see what else you may need to do to the new SunScreen configuration.
policyname_Obj.log
The policyname_Obj.log file lists objects found in your FireWall-1 security policy that were not directly supported in SunScreen 3.2. The following table lists the FireWall-1 objects and shows whether they were converted to SunScreen 3.2.
Table 8-3 How Conversion to SunScreen 3.2 Affects FireWall-1 Objects|
FireWall-1 Object |
SunScreen Equivalent |
Conversion Status |
|---|---|---|
|
Host |
Host |
Yes. |
|
Network |
Range |
Yes. |
|
Router |
None |
No. See the policyname_Obj.log file for details. |
|
Switch |
None |
No. See the policyname_Obj log file for details. |
|
Domain |
None |
No. See the policyname_Obj log file for details. |
|
Group |
Group |
Yes. |
|
Gateways |
None |
No. However, they are logged in the policyname_OBJ.log file. Gateways require more configuration within SunScreen to assure that the IP addresses of the gateway are correct. See the SunScreen 3.2 Administration Guide for more information. |
The following figure shows a sample policyname_Obj.log file, similar to the file that you can generate from your FireWall-1 policy.
Example 8-4 policyname_Obj.log File
/***** SunScreen: Firewall-1 conversion log *****/ /***** @(#)ObjStore.java 3.7 99/11/09 Sun Microsystems, Inc. *****/ Objects of type: gateway, need some user decisions You had a gateway with name "skil" ipaddr 205.167.60.13 If this is the gateway on which SunScreen is being installed please refer to the 'ssadm edit' command to enable the interfaces |
policyname_Rule.log
This file shows rules generated from FireWall-1 rules that cannot be used in the SunScreenenvironment without modification. The policyname_Rule.log file explains why these rules were not added to the SunScreen firewall, for example:
-
Source, Destination, or Installed on objects are of a type not supported by SunScreen
-
FireWall-1 Service is of a type not supported by SunScreen
-
FireWall-1 Action is not supported by SunScreen
SunScreen does not support FireWall-1 encryption, user authentication, or client authentication. Encryption in SunScreen is accomplished through SunScreen IKE or SunScreen SKIP, as explained in the SunScreen 3.2 Administrator's Overview. For more information regarding SKIP, see the SunScreen SKIP User's Guide, Release 1.5.1.
All FireWall-1 rules are generated during the conversion. You must remove any rules that you do not need manually.
The following shows a sample policyname_Rule.log file that might be generated after the FireWall-1 to SunScreen conversion.
Example 8-5 policyname_Rule.log File
/***** SunScreen: Firewall-1 conversion log *****/ /***** @(#)RuleStore.java 3.6 99/11/09 Sun Microsystems, Inc. *****/ Rule below not added as the action Encrypt is configured differently in SunScreen. add_nocheck Rule "smtp" "aiims" "*" Encrypt Rule below not added as the action Encrypt is configured differently in SunScreen. add_nocheck Rule "echo" "aiims" "*" Encrypt Rule below not added as the action User Authentication is not valid in SunScreen. add_nocheck Rule "ftp" "*" "aiims" User Rule below not added as the action Client Encryption/Authentication is not valid in SunScreen. add_nocheck Rule "dns" """ "*" Client |
|
|
policyname_Unused.log
The following figure lists FireWall-1 objects encountered in your policy that are not supported by SunScreen.
Example 8-6 policyname_Unused.log File
#Invalid Objects from FW-1 #Wed Mar 31 17:40:23 PST 1999 invalidobj1=gateway skil |
Creating the SunScreen Configuration
The following procedures explain how you prepare for and generate the new SunScreen configuration.
Choosing which of the next two procedures to follow depends on whether you plan to run SunScreen on the former FireWall-1 system or on a new system. Option 1 discusses preparing the FireWall-1 system to become a SunScreen system. Option 2 discusses preparing a new system to run the converted FireWall-1 configurations.
Note -
Choose only one of the four options.
Option 1: To Prepare the FireWall-1 System to Run SunScreen
-
Open a terminal window and become root, if not already.
-
Save the existing FireWall-1 configuration files located in the /opt/SUNWfw/conf directory as a backup.
-
Use the pkgrm command to remove the SUNWfw package by typing:
# pkgrm SUNWfw
# pkgrm SUNWwfwvpn
# pkgrm SUNWwfwdes
-
Upgrade to at least the Solaris 9 operating environment (if not already done).
See your Solaris documentation for instructions, if necessary.
-
Install the additional Solaris software packages and kernel packages required as listed in "Installation Overview" in SunScreen Installation Guide (if not already done).
Note -Prior to installing the SunScreen software, make sure that the system is performing properly as a router.
-
Install the SunScreen software as described in "Installing in Routing Mode With Local Administration" in SunScreen Installation Guide.
Continue to the section, "To Generate the New SunScreen Configuration".
Option 2: To Prepare a New SunScreen System to Run the Converted FireWall-1 Configuration
Note -
Prior to installing the SunScreen software, make sure that the system is performing properly as a router.
-
Open a terminal window and become root, if not already.
-
Upgrade to at least the Solaris 2.6 operating environment (if not already done).
See your Solaris operating environment documentation for instructions, if necessary.
-
Install the additional Solaris software packages and kernel packages required as listed in "Installation Overview" in SunScreen Installation Guide (if not already done).
-
Copy the generated configuration files to a directory on the new SunScreen system.
-
Install the SunScreen software as described in "Installing in Routing Mode With Local Administration" in SunScreen Installation Guide.
Continue to the section, "To Generate the New SunScreen Configuration".
To Generate the New SunScreen Configuration
-
Open a terminal window and become root, if not already.
-
Change to the directory where the conversion files were saved and make the policyname_sscfg file executable by typing:
# chmod 544policyname_sscfg
-
Verify that the commands in the generated file are accurate by typing:
# ./policyname_sscfg
policyname_sscfg creates the new SunScreen configuration from the FireWall-1 configuration, which is similar to the FireWall-1 policy.
See the SunScreen 3.2 Administration Guide for instructions on activating the configuration.
- © 2010, Oracle Corporation and/or its affiliates
