Configuring a VPN
To define the systems that are taking part in a particular VPN, you need to create a VPN gateway for each Screen involved in the VPN. You create these gateway definitions by using the VPN tab in the Policy Rules area of the Policy Rules page.
Each VPN gateway definition associates a particular certificate with a set of hosts that are protected by that gateway. The protected hosts will have traffic protected by that certificate and its private key.
To Add a VPN Gateway Definition
-
Execute the steps in "To Modify Rules".
-
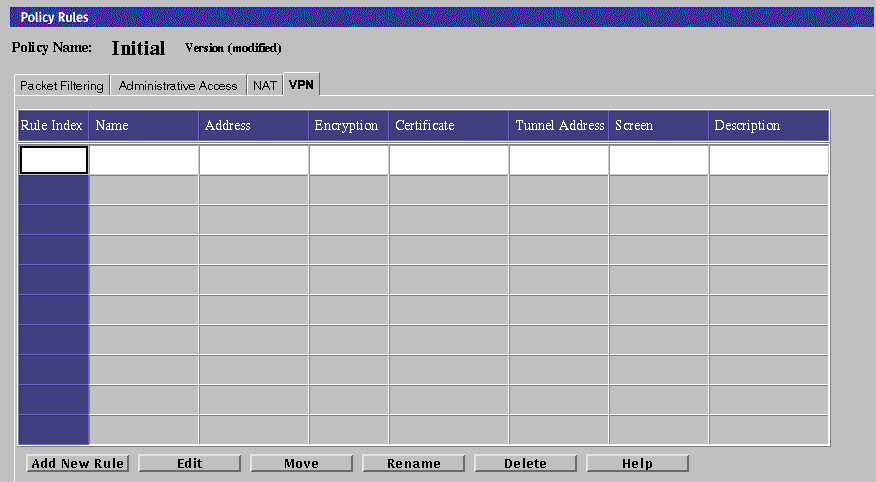
Click the VPN tab in the Policy Rules area.
-
Click the Add New Rule button in the VPN area.
The VPN Definition dialog box appears.
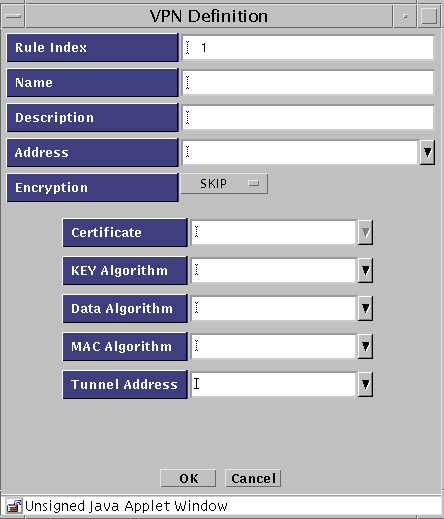
The following table describes the controls in the VPN Definition dialog box for defining VPN gateways.
Table 3-6 Controls in the VPN Definition Dialog BoxControl
Descriptions
Rule Index
(Optional) Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed the end of the list). Typing a lower number inserts the new rule into the specified position in the list and renumbers the rules currently in the configuration. Rules take effect in order.
Name
Specifies the Name of the VPN to which this gateway belongs. Type the same name in the Name field for each gateway that is in the VPN.
Description
(Optional) Provides a short description of the VPN gateway.
Address
Specifies the addresses to be protected by this VPN gateway.
Encryption
Specifies the type of encryption. Select either SKIP or IPsec IKE.
Certificate
Specifies the name of the certificate for this VPN gateway.
Key Algorithm
(SKIP only) Specifies the secret (key) algorithm the VPN uses. All gateways in the same VPN must use the same (key) algorithm.
Data Algorithm
(SKIP only) Specifies the data algorithm the VPN uses. All gateways in the same VPN must use the same data algorithm.
MAC Algorithm
(SKIP only) Specifies the MAC algorithm the VPN uses. All gateways in the same VPN must use the same MAC algorithm.
Tunnel Address
(SKIP only) Specifies the destination address on the outer (unencrypted) IP packet to which tunnel packets are sent.
-
In the Name field, type the name of the VPN to which the gateway belongs.
Type the same name for each gateway to be included in the VPN.
-
(Optional) Type a description of the VPN gateway in the Description field.
-
In the Address field, select the addresses to be protected by this VPN gateway.
-
Select the encryption type. If you select IPSEC IKE, the following panel appears. Go to Step 13 below for the IPsec IKE definitions
-
In the Certificate field, select the gateway's Certificate ID.
-
In the Key Algorithm field, select the key algorithm (or "none") to be used by the VPN.
All gateways in the same VPN must use the same key algorithm.
-
In the Data Algorithm field, select the data algorithm (or "none") to be used by the VPN.
All gateways in the same VPN must use the same data algorithm.
-
In the MAC Algorithm field, select the MAC algorithm (or "none") to be used by the VPN.
All gateways in the same VPN must use the same MAC algorithm.
-
In the Tunnel Address field, select the tunnel address to be used by the VPN.
-
If you selected IPSEC IKE for encryption, you can select the algorithms to be used as follows:

-
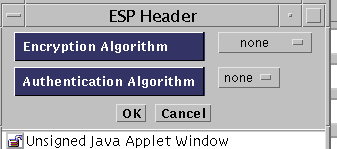
Click the ESP Edit button to define the ESP header encryption and authentication algorithms.
-
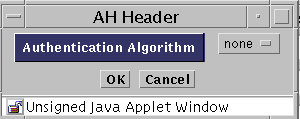
Click the AH Edit button to define authentication headers.
-
Select the Encryption Algorithm for IKE. The options are none, null, DES, 3DES, BLOWFISH, or AES.
-
Select the Hash Algorithm. The options are MD5 or SHA1.
-
Select the Oakley Group. The options are 1, 2, or 5.
-
Select the Authentication Method. The options are RSA-SIGNATURES, or DSS-SIGNATURES.
-
Select the Source Certificate. Click the arrow to see a list of available IKE certificated.
-
-
Click the OK button.
Note -
Repeat Step 3 through Step 14 to define a VPN gateway for each Screen in the VPN. To make sure they are all included in this particular VPN, be sure to give all of them the same VPN name.
To Create Packet Filtering Rules for a VPN
To use the VPN you have defined by creating VPN gateways, perform the following steps to add packet filtering rules:
-
Execute the steps in "To Modify Rules".
-
Click the Packet Filtering tab of the Policy Rules area.
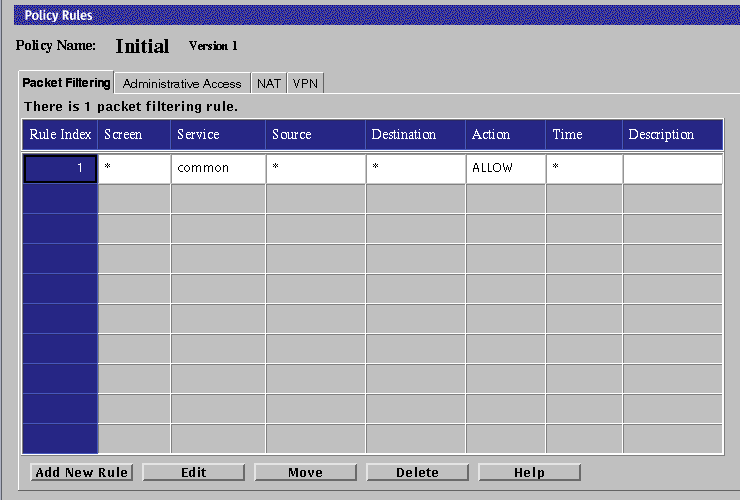
-
Click the Add New Rule button at the bottom of the rules.
The Rule Definition dialog box appears.
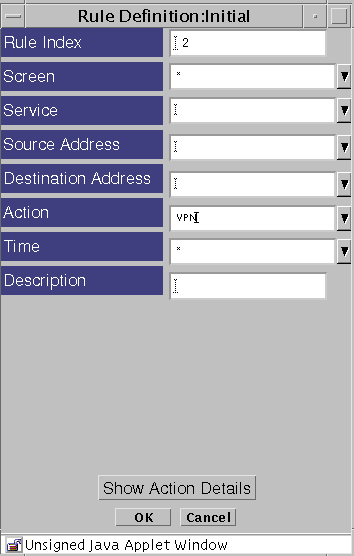
-
Type the information into the fields as desired.
You may use the asterisk, or wildcard, character ("*") in the source and destination fields. Using a wild card will check all traffic to see if it is part of the specified VPN.
Select VPN in the action field. When the Action Details dialog box requires a VPN, select the name of the VPN used when defining the VPN gateways.
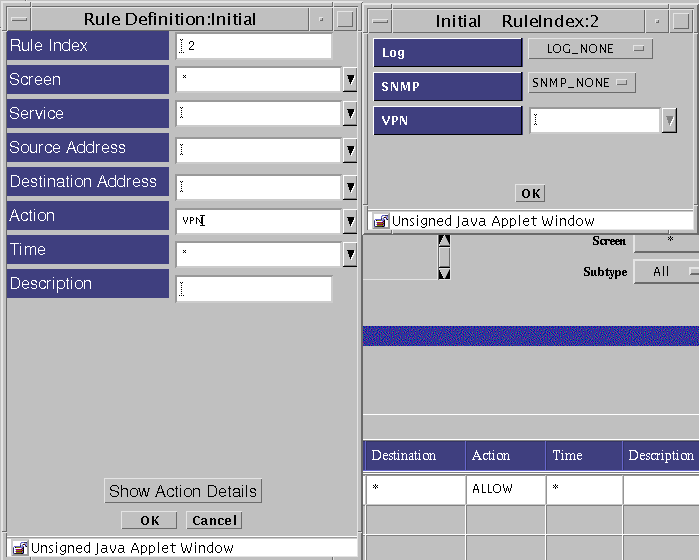
The one VPN-based rule will then generate all the VPN gateway pair-wise rules so that the hosts at each site can communicate with each other securely. Any host that cannot be secured (for example, if it is not protected by a VPN gateway) will not be allowed to communicate by the VPN-based rule. You can create a rule that allows that particular host to communicate, but you must set that up separately and explicitly.
-
Click the OK button for both the Action Details and the Add Rule dialog boxes.
Note -If you did not use "*" for source, destination, and service, repeat steps 2 through 4 for any additional rules. You must add VPN rules for each Screen that is part of the VPN.
- © 2010, Oracle Corporation and/or its affiliates
