| C H A P T E R 2 |
|
SMS Security Options and Administrative Privileges |
This chapter provides a brief overview of security and administrative privileges as they pertain to SMS and the Sun Fire high-end server system.
The Sun Fire high-end system platform hardware can be partitioned into one or more environments capable of running separate images of the Solaris operating environment. These environments are called dynamic system domains (DSD)s or domains.
A domain is logically equivalent to a physically separate server. The Sun Fire high-end system hardware has been designed to enforce strict separation of the domain environments. This means that, except for errors in hardware shared by multiple domains, no hardware error in one domain affects another. In order for domains to act like separate servers, Sun Fire software was designed and implemented to enforce strict domain separation.
SMS provides services to all DSDs. In providing those services, no data obtained from one client DSD is leaked into data observable by another. This is particularly true for sensitive data such as buffers of console characters (including administrator passwords) or potentially sensitive data such as I/O buffers containing client DSD-owned data.
SMS limits administrator privilege to control the extent of damage that can occur due to administrator error, as well as to limit the exposure to damage caused by an external attack on a system password.
This chapter includes the following sections:
The following security options are available in SMS 1.4:
Use Secure Shell (ssh) as an alternative transport for fomd (failover management daemon).
Disable ARP (Address Resolution Protocol) on the I1 MAN network between the SCs and domains.
Disable all IP traffic between the SC and a domain by excluding that domain from the SC's MAN driver.
By using ssh as an alternative transport for fomd, the SCs no longer require a /.rhosts file. Secure Shell provides user authentication and encrypts all network traffic; it prevents an intruder from being able to read an intercepted communication or from spoofing the system.
To protect against ARP spoofing and IP-based attacks, We strongly recommend that you disable ARP on the MAN network in all multi-domain configurations. For systems where domain separation is critical, we also recommend disabling IP connectivity between the SC and specific domains that require separation.
Before you implement the above security options, we strongly recommend that you modify (harden) your Solaris operating environment configurations on the SCs and domains to improve overall system security. For details, refer to following Sun BluePrints Online articles available at:
http://www.sun.com/security/blueprints
Solaris Operating Environment Security - Updated for Solaris 8 Operating Environment
Solaris Operating Environment Security - Updated for Solaris 9 Operating Environment
For step-by-step instructions on implementing the three options, which involve the use of the Solaris Security Toolkit (SST, a.k.a JASS), and detailed description of all security recommendations for Sun Fire high-end systems, refer to the following Sun BluePrints Online articles available at:
http://www.sun.com/security/blueprints
Securing the Sun Fire 12K and 15K System Controllers: Updated for SMS 1.4
Securing the Sun Fire 12K and 15K Domains: Updated for SMS 1.4
SMS splits domain and platform administrative privileges. It is possible to assign separate administrative privileges for system management over each domain and for system management over the entire platform. There is also a subset of privileges available for platform operator and domain configurator-class users. Administrative privileges are granted so that audits can identify the individual who initiated any action.
SMS uses site-established Solaris user accounts and grants administrative privileges to those accounts through the use of Solaris group memberships. This allows a site considerable flexibility with respect to creating and consolidating default privileges. For example, by assigning the same Solaris group to represent the administrator privilege for more than one domain, groups of domains can be administered by one set of domain administrators.
SMS also allows the site considerable flexibility in assigning multiple administrative roles to individual administrators. A single user account with group membership in the union of all configured administrative privilege groups can be set up.
The platform administrator has control over the platform hardware. Limitations have been established with respect to controlling the hardware used by a running domain, but ultimately the platform administrator can shut down a running domain by powering off server hardware.
Each domain administrator has access to the Solaris console for that domain and the privilege to exert control over the software that runs in the domain or over the hardware assigned to the domain.
Levels of each type of administrative privilege provide a subset of status and monitoring privileges to a platform operator or domain configurator.
SMS provides an administrative privilege that grants access to functions provided exclusively for servicing the product in the field.
Administrative privilege configuration can be changed at will, by the superuser, using smsconfig -g without the need to stop or restart SMS.
SMS implements Solaris access control list (ACL) software to configure directory access for SMS groups using the -a and -r options of the smsconfig command. ACLs restrict access to platform and domain directories providing file system security. For information on ACLs, refer to the Solaris 9 System Administration Guide: Security Services.
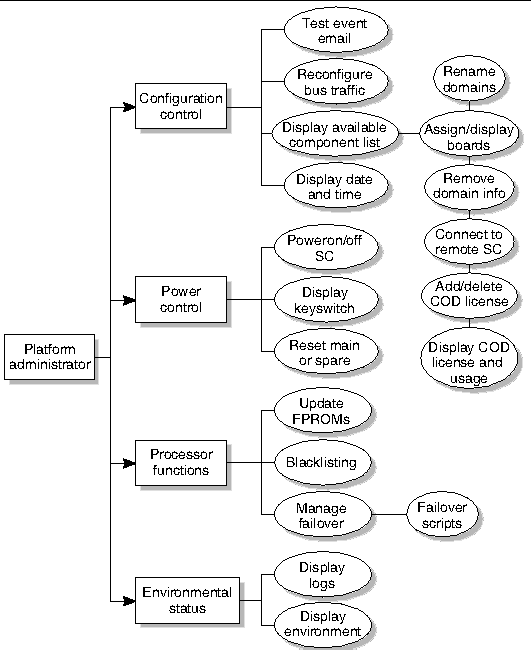
The group identified as the platform administrator (platadmn) group provides configuration control, a means to get environmental status, the ability to assign boards to domains, power control, and other generic service processor functions. In short, the platform administrator group has all platform privileges excluding domain control and access to installation and service commands (FIGURE 2-1).
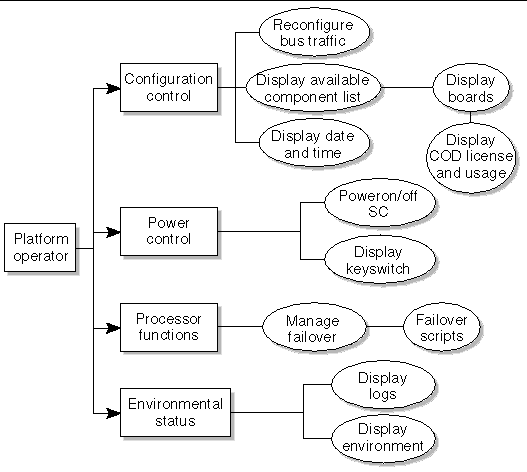
The platform operator (platoper) group has a subset of platform privileges. This group has no platform control other than being able to perform power control. Therefore, this group is limited to platform power and status privileges (FIGURE 2-2).
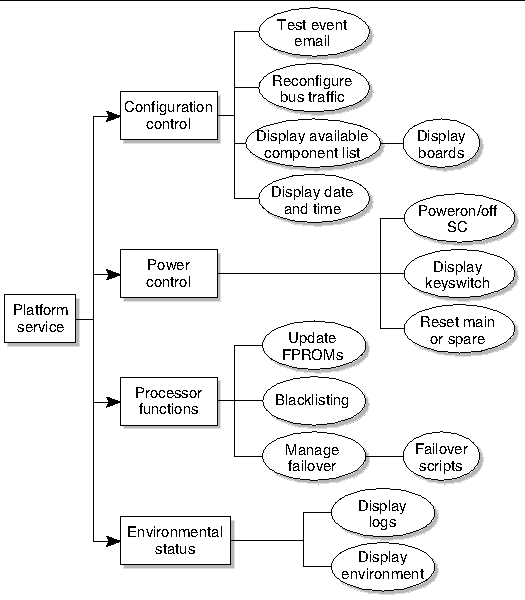
The platform service (platsvc) group possesses platform service command privileges in addition to limited platform control and platform configuration status privileges (FIGURE 2-3).
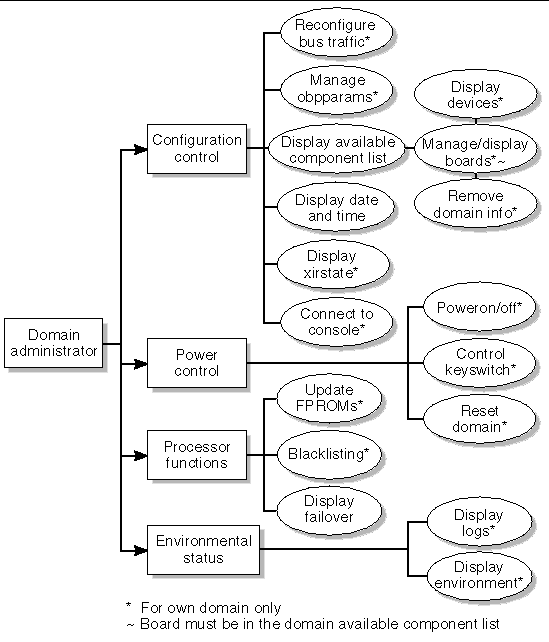
The domain administrator (dmn[domain_id]admn) group provides the ability to access the console of its respective domain as well as perform other operations that affect, directly or indirectly, the respective domain. Therefore, the domain administrator group can perform domain control, domain status, and console access, but cannot perform platform wide control or platform resource allocation (FIGURE 2-4).
There are 18 possible Sun Fire domains, A-R, identified by domain_id. Therefore, there are 18 Domain Administrator groups, each providing strict access over their respective domains.
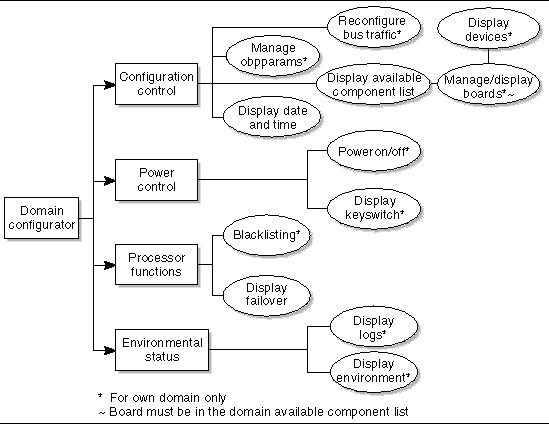
The domain configuration (dmn[domain_id]rcfg) group has a subset of domain administration group privileges. This group has no domain control other than being able to power control boards in its domain or (re)configure boards into or from its domain (FIGURE 2-5).
There are 18 possible Sun Fire domains identified by domain_ids. Therefore, there are 18 domain configuration groups, each allowing strict access over their respective domains.
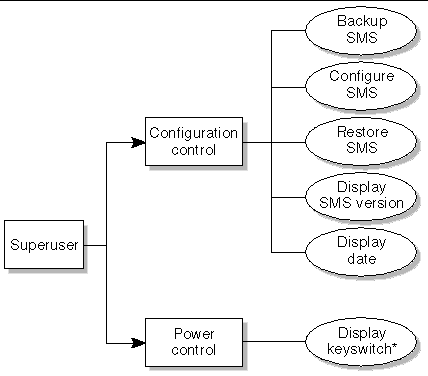
The superuser privileges are limited to installation, help, and status privileges (FIGURE 2-6).
The following is a list of all group privileges.
Copyright © 2003, Sun Microsystems, Inc. All rights reserved.