| System Management Services (SMS) 1.6 Administrator Guide
|
   
|
SMS Administrative Privileges
|
This chapter provides a brief overview of administrative privileges as they pertain to SMS 1.6 and the Sun Fire high-end server system. This chapter contains the following sections:
Administrative Privileges Overview
SMS splits domain and platform administrative privileges. It is possible to assign separate administrative privileges for system management over each domain and for system management over the entire platform. There is also a subset of privileges available for platform operator and domain configurator-class users. Administrative privileges are granted so that audits can identify the individual who initiated any action.
SMS uses site-established Solaris user accounts and grants administrative privileges to those accounts through the use of Solaris group memberships. This allows a site considerable flexibility with respect to creating and consolidating default privileges. For example, by assigning the same Solaris group to represent the administrator privilege for more than one domain, groups of domains can be administered by one set of domain administrators.
SMS also allows the site considerable flexibility in assigning multiple administrative roles to individual administrators. For example, you can set up a single user account with group membership in the union of all configured administrative privilege groups.
- The platform administrator has control over the platform hardware. Limitations have been established with respect to controlling the hardware used by a running domain, but ultimately the platform administrator can shut down a running domain by powering off server hardware.
- Each domain administrator has access to the Solaris console for that domain and the privilege to exert control over the software that runs in the domain or over the hardware assigned to the domain.
- Levels of each type of administrative privilege provide a subset of status and monitoring privileges to a platform operator or domain configurator.
SMS provides an administrative privilege that grants access to functions provided exclusively for servicing the product in the field.
Administrative privilege configuration can be changed at will, by the superuser, using smsconfig -g without the need to stop or restart SMS.
SMS implements Solaris access control list (ACL) software to configure directory access for SMS groups using the -a and -r options of the smsconfig command. ACLs restrict access to platform and domain directories providing file system security. For information on ACLs, refer to the Solaris 9 System Administration Guide: Security Services.
Platform Administrator Group
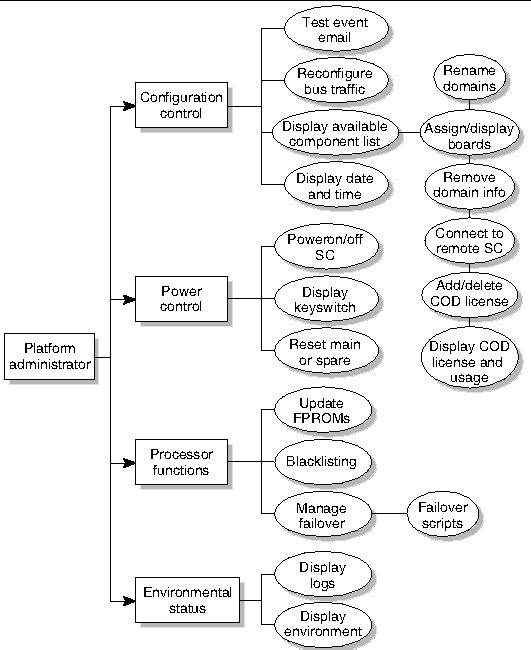
The group identified as the platform administrator (platadmn) group provides configuration control, a means to obtain environmental status, the ability to assign boards to domains, power control, and other generic service processor functions. In short, the platform administrator group has all platform privileges excluding domain control and access to installation and service commands (FIGURE 3-1).
FIGURE 3-1 Platform Administrator Privileges
Platform Operator Group
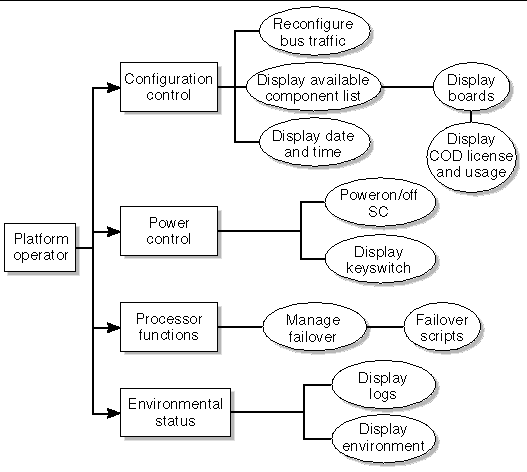
The platform operator (platoper) group has a subset of platform privileges. This group has no platform control other than being able to perform power control. Therefore, this group is limited to platform power and status privileges (FIGURE 3-2).
FIGURE 3-2 Platform Operator Privileges
Platform Service Group
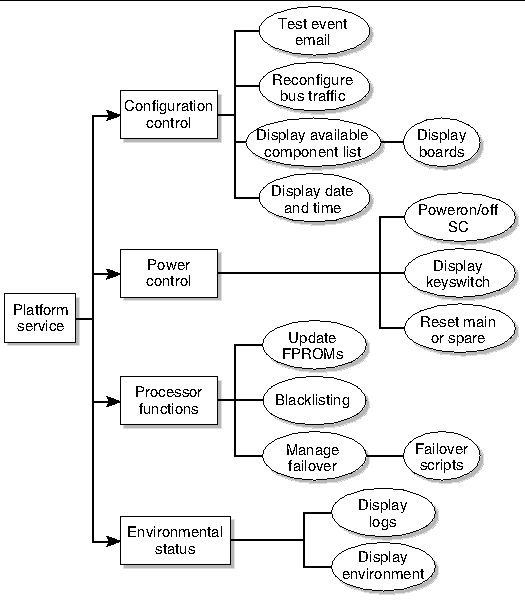
The platform service (platsvc) group possesses platform service command privileges in addition to limited platform control and platform configuration status privileges (FIGURE 3-2).
FIGURE 3-3 Platform Service Privileges
Domain Administrator Group
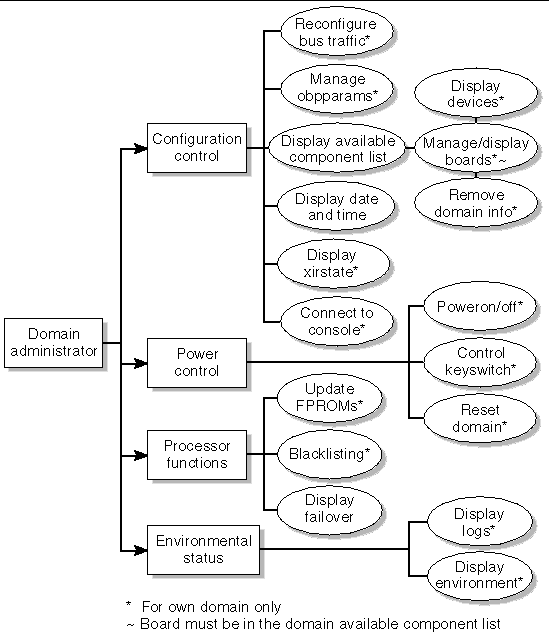
The domain administrator (dmn[domain-id]admn) group provides the ability to access the console of its respective domain as well as perform other operations that affect, directly or indirectly, the respective domain. Therefore, the domain administrator group can perform domain control, domain status, and console access, but cannot perform platform-wide control or platform resource allocation (FIGURE 3-4).
There are 18 possible Sun Fire domains, A-R, identified by domain-id. Therefore, there are 18 domain administrator groups, each providing strict access over their respective domains.
FIGURE 3-4 Domain Administrator Privileges
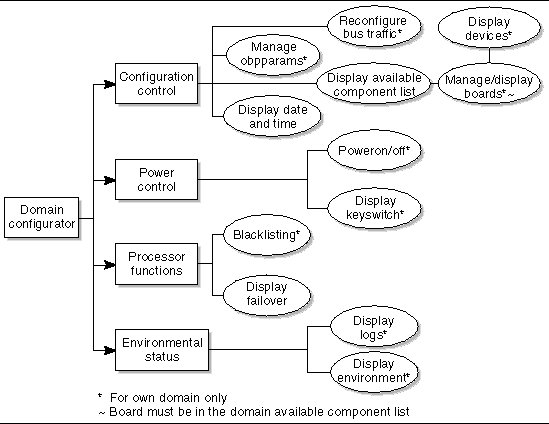
Domain Configuration Group
The domain configuration (dmn[domain-id]rcfg) group has a subset of domain administration group privileges. This group has no domain control other than being able to power control boards in its domain or (re)configure boards into or from its domain (FIGURE 3-5).
There are 18 possible Sun Fire domains, identified by domain-ids. Therefore, there are 18 domain configuration groups, each allowing strict access over their respective domains.
FIGURE 3-5 Domain Configurator Privileges
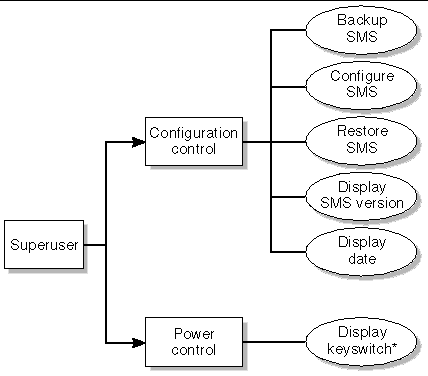
Superuser Privileges
The superuser privileges are limited to installation, help, and status privileges (FIGURE 3-6).
FIGURE 3-6 Superuser Privileges
All Privileges
TABLE 3-1 lists all group privileges.
TABLE 3-1 All Group Privileges
|
Command
|
Group Privileges
|
|
Platform Administrator
|
Platform Operator
|
Domain Administrator
|
Domain Configurator
|
Platform Service
|
Superuser
|
|
addboard
|
A user with only platform administrator privileges can perform only the -c assign.
|
No
|
Users with only domain X administrator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
Users with only domain X configurator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
No
|
No
|
|
addcodlicense
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
addtag
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
cancelcmdsync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
console
|
No
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
deleteboard
|
A user with only platform administrator privileges can perform -c unassign only if the boards are in the assigned state and not active in a running domain.
|
No
|
Users with only domain X administrator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
Users with only domain X configurator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
No
|
No
|
|
deletecodlicense
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
deletetag
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
disablecomponent
|
Yes (platform only)
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
enablecomponent
|
Yes (platform only)
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
flashupdate
|
Yes
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
help
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
|
initcmdsync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
moveboard
|
A user with only platform administrator privileges can perform the -c assign only if the board is in the assigned state and not active in the domain the board is being removed from.
|
No
|
Users must belong to both domains affected. If the boards are not already assigned to the domain the boards are being moved into, the boards must be in the available component list of that domain.
|
Users must belong to both domains affected. If the boards are not already assigned to the domain the boards is being moved into, the boards must be in the available component list of that domain.
|
No
|
No
|
|
poweron
|
Yes
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
poweroff
|
Yes
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
rcfgadm
|
A user with only platform administrator privileges can perform-x assign. The user can execute -x unassign only if the boards are in the assigned state and not active in a running domain.
|
No
|
Users with only domain X administrator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
Users with only domain X configurator privileges can execute this command on their respective domain. If the boards are not already assigned to the domain, the boards must be in the available component list of that domain.
|
No
|
No
|
|
reset
|
No
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
resetsc
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
runcmdsync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
savecmdsync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
setbus
|
Yes
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
setcsn
|
Yes
|
No
|
No
|
No
|
Yes
|
No
|
|
setdatasync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
setdate
|
Yes
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
setdefaults
|
Yes
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
setfailover
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
setkeyswitch
|
No
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
setobpparams
|
No
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
setupplatform
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
showboards
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showbus
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showcmdsync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
showcodlicense
|
Yes
|
Yes
|
No
|
No
|
No
|
No
|
|
showcodusage
|
Yes
|
Yes
|
No
|
No
|
No
|
No
|
|
showcomponent
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showdatasync
|
Yes
|
Yes
|
Yes
|
Yes
|
Yes
|
No
|
|
showdate
|
Yes (platform only)
|
Yes (platform only)
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes (platform only)
|
No
|
|
showdevices
|
No
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
showenvironment
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showfailover
|
Yes
|
Yes
|
No
|
No
|
Yes
|
No
|
|
showkeyswitch
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showlogs
|
Yes (platform only)
|
Yes (platform only)
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes (platform only)
|
No
|
|
showobpparams
|
No
|
No
|
Yes (for own domain)
|
Yes (for own domain)
|
No
|
No
|
|
showplatform
|
Yes
|
Yes
|
Yes (for own domain)
|
Yes (for own domain)
|
Yes
|
No
|
|
showxirstate
|
No
|
No
|
Yes (for own domain)
|
No
|
No
|
No
|
|
smsbackup
|
No
|
No
|
No
|
No
|
No
|
Yes
|
|
smsconfig
|
No
|
No
|
No
|
No
|
No
|
Yes
|
|
smsconnectsc
|
Yes
|
No
|
No
|
No
|
No
|
No
|
|
smsrestore
|
No
|
No
|
No
|
No
|
No
|
Yes
|
|
smsversion
|
No
|
No
|
No
|
No
|
No
|
Yes
|
|
testemail
|
Yes
|
No
|
No
|
No
|
Yes
|
No
|
| System Management Services (SMS) 1.6 Administrator Guide
|
819-4660-10
|
   
|
Copyright © 2006, Sun Microsystems, Inc. All Rights Reserved.





