 [Top]
[Prev]
[Next]
[Bottom]
[Top]
[Prev]
[Next]
[Bottom]
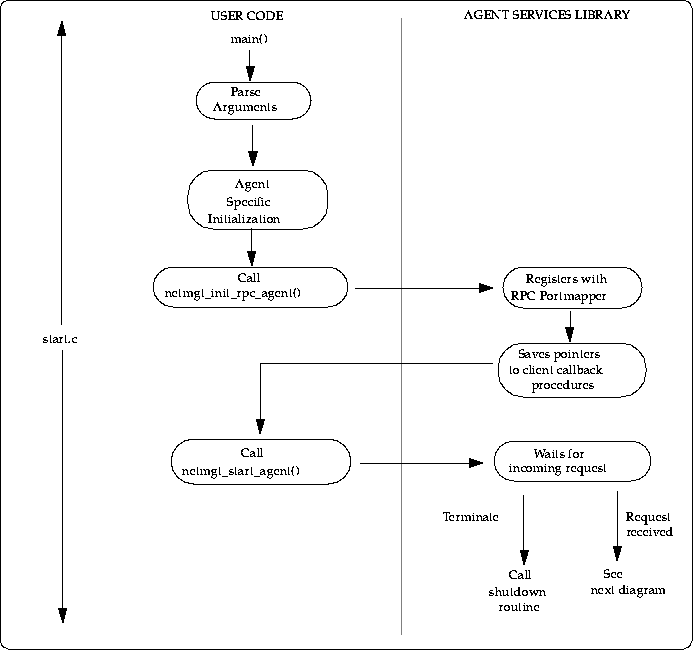
Upon successful validation of the request, the Agent Services library creates a child process and calls the agent-supplied dispatch function in the context of the child process.
NOTE - Although Site/SunNet/Domain Manager forks a subprocess before calling your dispatch function, your verification function should not cache request arguments as global data. Caching request arguments may save a little time but it will probably make your agent incompatible with future Site/SunNet/Domain Manager releases.
The dispatch function should execute the request,
reporting data at the requested times. When all request servicing is completed,
the dispatch function returns to the Agent Services library, who shuts down
the child process.
NOTE - If the verification routine
opens files or allocates memory, it must be able to close the files or free
the memory after control has passed to the child process. Otherwise, memory
and file descriptor leakage may occur. For this reason, you should avoid agent
setup tasks in the verification routine.
12.3.1 Verification and Dispatching Routine Parameters
The verify and dispatch routines share a common
set of parameters. When an agent is used with the Console, most of these
parameters come from the information in the request property window.
The following parameters are passed to the agent-supplied verification and dispatching procedures:
| Count |
Interval |
Interpretation |
When servicing a request, the child process should:
Check whether the values to set the attributes have the correct data types and are within acceptable ranges. (See Table 11-1 on page 11-3 for a list of valid data types.) If your agent can take optional arguments, fetch the arguments using netmgt_fetch_argument(3n).
Fetch the set request arguments
using netmgt_fetch_setval. This function specifies the <group>
name, optional <key> name if the group is a table, <attribute>
name, and <value> to set the attribute. Unlike data and
event requests, a manager can request your agent set attributes in more than
one group. Continue calling netmgt_fetch_setval until the
<group> name is NETMGT_ENDOFARGS which indicates the
end of the request arguments. If you determine the request is well-formed,
your request verification functions should return the boolean value
TRUE. Otherwise, it should call netmgt_send_error(3n) to
send an error report to the requester and return the boolean value FALSE
.
NOTE - The
Console snm and command-line manager snm_cmd set the
optional argument name to NETMGT_OPTSTRING and the optional argument
type to NETMGT_STRING.
12.5.2 Set Attribute Values
If you determined the request
was well-formed, your request dispatch procedure will be called just like
your verification function. Once again, you should fetch any request options
and the set request arguments.
12.5.3 Send a Status Report
Whether or not you were
successful in setting the requested attribute values, you should send a status
message to the requester. If you were successful, call netmgt_send_error
(3n) setting the <service_error> code to NETMGT_SUCCESS
. If you encountered an error setting the attributes, send an error report
just like you would for a data or event request.
12.5.4 Sample Code
The following code fragment
is an example of a routine which receives a set request and sends a status
message to the requester:
if (!netmgt_send_error(&status)) NETMGT_DBG("netmgt_send_error failed: %s\n", netmgt_sperror());
return; } |
an error code from the enumerated type Netmgt_stat as defined in netmgt_errno.h .
signals an agent-specific non-fatal error. The agent_error field provides the agent error code.
signals an agent-specific fatal error. The agent_error field provides the agent error code.
The following shows
the syntax of the netmgt_start_trap() function:
NOTE - Reporting data and issuing traps should occur in separate processes.
If an agent collects and sends data in addition to issuing traps, then the
agent should issue a trap by calling the fork() system routine
to spawn a child process and the building and sending of the trap should be
carried out by the child process. This procedure is necessary to ensure that
the parent process is not interrupted from collecting and reporting data
while the trap is being built and sent. This will prevent loss or delay of
reports, especially if the reporting interval is very short.
12.7.1 Sample
Code
The
following code fragment is an example of a routine that calls netmgt_start_trap()
, then calls netmgt_build_report() for each attribute in the
trap, and then calls netmgt_send_report() to send the trap report.
 [Top]
[Prev]
[Next]
[Bottom]
[Top]
[Prev]
[Next]
[Bottom]