| C H A P T E R 5 |
|
Security |
This chapter lists the major security threats, provides important information about the system controller, explains password requirements for the platform and the domains, describes domain separation requirements, explains how to secure the system controller with the setkeyswitch command, provides references to Solaris operating environment security, and briefly describes SNMP.
This chapter contains the following topics:
Some of the threats regarding host break-ins that can be imposed are:
In order to secure the system controller in your system, read about the system controller security issues. System controller security issues have a great impact on the security of the system controller installation. Refer to the articles available online, including Securing the Sun Fire Midframe System Controller, at:
When you set up the software for your system, you performed software tasks needed to set up system controller security in Chapter 3. The basic steps to secure the system controller are:
1. Setting the platform shell password by using the password command.
2. Setting up the platform-specific parameters by using the setupplatform command.
3. Setting the domain shell password for all domains by using the password command.
4. Setting the domain-specific parameters by using the setupdomain command.
5. Saving the current configuration of the system by using the dumpconfig command.
This list of parameters is only a partial list of what you need to set up. For step-by-step software procedures, see Chapter 3.
For technical information on the setupplatform and setupdomain settings involving system controller security, see the system controller commands in the Sun Fire 6800/4810/4800/3800 System Controller Command Reference Manual. Also refer to the articles available online. See System Controller Security for the URL.
|
Note - Make sure that you know who has access to the system controller. Anyone who has that access can control the system. |
When you set up your system for the first time:
This section discusses domain separation and the setkeyswitch command.
The domain separation requirement is based on allocating computing resources to a specific domain. These mid-range systems enforce domain separation, which prevents users of one domain, who only have access to the Solaris operating environment running in that domain, from accessing or modifying the data of another domain.
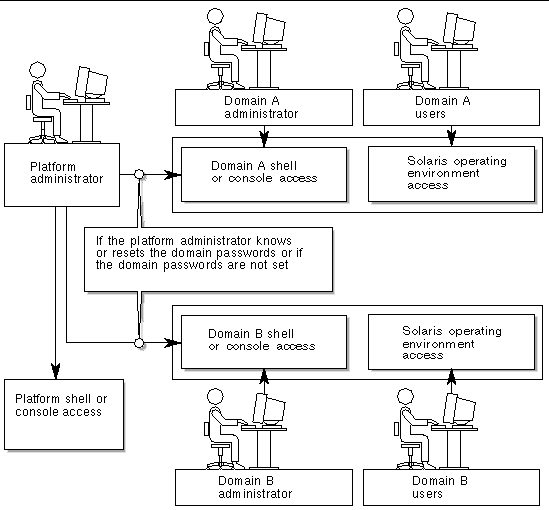
This security policy enforcement is performed by the software (FIGURE 5-1). In this figure, a domain user is a person who is using the Solaris operating environment and does not have access to the system controller. The domain administrator is responsible for:
As this figure shows, the domain administrator has access to the domain console and domain shell for the domain the administrator is responsible for. Also note in FIGURE 5-1 that the platform administrator has access to the platform shell and the platform console. If the platform administrator knows the domain passwords, the platform administrator also has access to domain shells and consoles. You should always set the domain shell passwords for each domain.
The following are security items to consider in each domain:
The Sun Fire 6800/4810/4800/3800 systems do not have a physical keyswitch. You set the virtual keyswitch in each domain shell with the setkeyswitch command. To secure a running domain, set the domain keyswitch to the secure setting. For more information about setkeyswitch, refer to the online article, Securing the Sun Fire Midframe System Controller available online at
With the keyswitch set to secure, the following restrictions occur:
For information on securing the Solaris operating environment, refer to the following books and articles:
The system controller uses SNMPv1, which is an insecure protocol. This means that the SNMPv1 traffic needs to be kept on a private network, as described in the online article, Securing the Sun Fire Midframe System Controller available online at
Copyright © 2003, Sun Microsystems, Inc. All rights reserved.