Chapter 2 Basic Procedures
This chapter covers common administrative procedures when configuring a Trusted Solaris host.
Note -
Installation and configuration commands and actions are limited to particular roles and particular labels. Read each task for the administrative role that can perform it, and the label required.
How to Log In
The predefined user install logs in immediately after installation to configure the workstation.
To Log In as the User Install
At most sites, two or more administrators, an install team, are present when configuring the workstation. "You", in the following procedure, refers to the install team.
-
Log in to the workstation as the user install.
-
Enter install as the user name and press the Return key.
The Password dialog box is displayed.
-
Enter install for the password.
The Enable Logins dialog offers four choices, as shown in Figure 2-1.
Figure 2-1 The Enable Logins Dialog
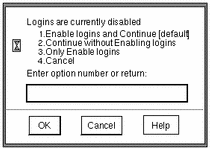
-
Depending on site security requirements, enter 1 or 2, then click OK.
The Message Of the Day dialog is displayed; the label is
ADMIN_LOW. -
Click OK to dismiss the dialog.
The Trusted Solaris screen appears briefly; then you are in a CDE workspace. The trusted stripe below the front panel shows the window sensitivity label.
-
To Log In as a Regular User
-
Log in to the workstation using your user account name.
-
Enter your password.
Note -Users must not disclose their passwords to another person, as that person may then have access to the data of the user and will not be uniquely identified or accountable. Note that disclosure can be direct, through the user deliberately disclosing his/her password to another person, or indirect, e.g. through writing it down, or choosing an insecure password. Trusted Solaris provides protection against insecure passwords, but cannot prevent a user disclosing his/her password or writing it down.
The Enable Logins dialog, shown in Figure 2-1, is displayed if you are authorized to enable logins.
If you see the error message:
Logins are currently disabled. Please ask your system administrator to enable logins.
then your user was not assigned the Enable Login profile (see Table 5-1). To fix, give the user the Enable Login profile, or have someone else log in and enable logins.
-
Choose a login option and dismiss the dialog.
The Message Of the Day dialog is displayed. In a multilevel session, the default is to log in at the lowest label in your label range. You can also restrict your session to a single label.
-
Click OK to accept the default given to you by the security administrator.
Once the login process is complete, the Trusted Solaris screen appears briefly, and you are in a CDE session with four workspaces. If your user account is configured to display labels, the label of your session (a user account cannot be
ADMIN_LOW) will show in the trusted stripe.
Note -The install team must log off or utilize the lockscreen functionality before leaving a workstation unattended. Otherwise a person may have access to the workstation without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
How to Assume a Role
An administrative role configures the workstation, however, a role cannot log in. Users log in, and assume one or more of their assigned roles. The role root has been pre-assigned to the user install.
To Assume a Role
-
Log in to the workstation as a user, such as install.
-
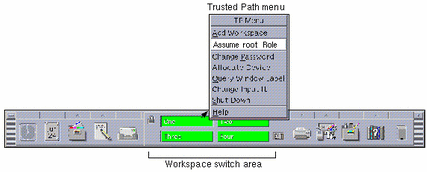
Right click on the middle of the Front Panel.
-
Assume a role from the roles displayed on the TP (Trusted Path) menu.
How to Launch a Terminal
Use the background menu to launch a terminal. The terminal displays the default shell for the user or role who launches the terminal.
To Launch a Terminal
Right-click on the workstation background and select Programs > Terminal.
How to Open a Profile Shell
The profile shell, pfsh(1M), is a special shell that enables execution of security-relevant commands. A profile shell inherits the required privileges from the user or role's execution profile, hence the name profile shell.
Note -
The default shell of all administrative roles (root, secadmin, and admin) is a profile shell.
To Open a Profile Shell in an Administrative Role
To Open a Profile Shell as a User or Non-Administrative Role
-
Launch a terminal from a user's or non-administrative role's workspace.
-
Type pfsh in the terminal to change the shell to a profile shell, if the profile shell has not been assigned as your default shell.
% pfsh
To List the Commands Available to a Profile Shell
Enter the clist command and pipe it through more.
% clist | more |
If the shell does not recognize the clist command, it is not a profile shell. If it prints a list of commands, it is a profile shell.
To See Process and Privilege Information in a Profile Shell
To see the process label, enter the plabel(1) command in a profile shell.
% plabel pid: [ADMIN_LOW] |
If the plabel command is in your execution profile, the label of the process is displayed.
To see what privileges have been accorded to you, enter the ppriv(1) command.
$ ppriv pid: none |
If the ppriv command is in your execution profile, the privileges available to commands run in the profile shell are displayed.
How to Create an Admin_High Workspace
Some administrative actions require a process at a higher label than the default. To get a higher-labeled process, create a workspace at that higher label, and launch actions and terminals from the new workspace.
Note -
If you are not allowed to change the workspace SL, the Change Workspace SL menu item does not appear.
-
Click the right menu button on the center of the front panel for the TP menu.
-
Choose Change Workspace SL from the menu, and select the workspace Sensitivity Label
ADMIN_HIGH. -
Click OK.
Actions, terminals, commands and windows originating from the workspace after it is relabeled run at the label of the workspace.
How to Protect Machine Hardware
For security, access to the PROM should also require a password.
SPARC: To Set the PROM Mode and Password
-
Choose the value command or full (see the eeprom(1M) man page for more details).
You are prompted to enter and confirm the PROM password.
# eeprom security-mode=command Changing PROM password: New password: password Retype new password: password
-
If are not prompted to enter a PROM password, the workstation already has a PROM password. To change it, run the command:
# eeprom security-password=<Return> Changing PROM password: New password: password Retype new password: password
As root, label admin_low, in the profile shell, enter the PROM security mode.
The new PROM security mode and password are in effect immediately, but are most likely to be noticed at the next boot.
Do not forget this password. The hardware is rendered unusable without it.
For more information on PROM values that you can set, see OpenBoot 2.x Command Reference Manual or OpenBoot 3.x Command Reference Manual.
IA: To Protect the BIOS
On an Intel machine, the equivalent to protecting the PROM is to protect the BIOS . Refer to your machine's manuals for how to protect the BIOS.
How to Limit Contact During Booting
For greater security, edit the boot-time database, /etc/security/tsol/boot/tnrhdb.
Note -
Editing the boot-time databases is required only if the default setting is more permissive than your site's security requirements.
-
See "Special Boot-time Trusted Network Databases" in Trusted Solaris Administrator's Procedures for the security implications of the boot-time network databases.
-
See "Administering the Boot-time Trusted Network Databases" in Trusted Solaris Administrator's Procedures for steps to take to modify the boot-time network database defaults.
How to Copy Files To and From a Portable Medium
When copying to a portable medium, label the medium with the sensitivity label of the information.
To Copy One or More Files to a Diskette
Note -
During installation, the role root copies administrative files to and from movable media, at the label admin_low.
-
First, allocate the floppy device at the correct label using the Device Allocation action, and insert a clean diskette. Mount the device.
Do you want floppy_n mounted: (y,n)? y
For a fuller description, see "To Allocate a Device".
-
Copy the file to the diskette by double-clicking the File Manager icon in the Front Panel.
-
In the File Manager, navigate to the folder that contains the files to be copied, such as /setup/files.
-
Rename the label_encodings file that you are copying.
For example, name it label_encodings.site (for SPARC architecture), or lblcdsit (for Intel architecture). Audit system files such as audit_user, and routing files such as nsswitch.conf, and resolv.conf do not need to be renamed.
-
Choose Open Floppy from the File menu.
-
Highlight the icon for the file and drag the file to the floppy disk folder..
-
On the floppy disk folder, choose Eject from the File menu.
-
Deallocate the device before continuing.
For the procedure, see "To Deallocate a Device".
Note -Remember to physically affix a label to the medium with the sensitivity label of the copied files.
To Copy One or More Files from a Diskette
It is safe practice to rename the original Trusted Solaris file before copying in a file to replace it. During installation, the root role renames and copies administrative files at admin_low.
-
Allocate the floppy device using the Device Allocation action and insert the diskette. Mount the device.
Do you want floppy_n mounted: (y,n)? y
For a fuller description, see "To Allocate a Device".
-
If the workstation has a file of the same name, copy it to a new name and remove the original.
Note -Exception: If the file you are copying is to replace the current label_encodings file, do not rename or remove the original file. See "How To Install a Site-Specific Label Encodings File" for the full procedure.
-
Double-click the File Manager icon in the Front Panel and navigate to the desired destination directory, such as /etc/security/tsol.
-
Choose Open Floppy from the File menu.
-
Highlight the icon for the file and drag the file from the floppy disk folder to the destination directory.
-
On the floppy disk folder, chose Eject from the File menu.
-
If you copied a site version of the label encodings file, see "How To Install a Site-Specific Label Encodings File" for the full procedure.
-
Deallocate the device before continuing.
This is described in "To Deallocate a Device".
How To Install a Site-Specific Label Encodings File
If you are installing a site-specific label_encodings file, consult Trusted Solaris Label Administration for requirements, procedures, and suggestions for the label encodings file..
You can edit the placeholder label_encodings(4) file that the Trusted Solaris installation program installed or install your own. The security administrator is responsible for editing, checking, and maintaining the label_encodings file.
-
Have the medium (diskette) with your site's label_encodings file ready to use.
-
As root (before roles are verified), or as secadmin (after roles have been verified), copy the file to a writable location, such as /etc/security/tsol/label_encodings.site using the File Manager.
If you are unsure of the steps, see "To Copy One or More Files from a Diskette".
-
Check the syntax of the new label_encodings file.
-
Double-click the Check Encodings action in the System_Admin folder in the Application Manager.
For more information on using the actions in the System_Admin folder, see "To Run a System_Admin Action".
-
In the dialog box, enter the full path name of the file: /etc/security/tsol/label_encodings.site
-
-
Read the contents of the Check Encodings dialog box that is displayed.
The chk_encodings(1M) command checks the syntax of the file. If the file passes the check, the action asks whether you want to overwrite the currently-installed label_encodings file. If the answer is yes, the action creates a backup copy (naming it label_encodings.orig), and installs the checked version.
-
If it reports no errors, continue.
-
If it reports errors, resolve them before continuing.
For detailed procedures and explanation, consult "Creating or Editing the Encodings File" in Trusted Solaris Label Administration.
 Caution -
Caution - Your label_encodings file must pass the Check Encodings test before you continue.
-
-
Read the new label_encodings file into your environment by clicking the right mouse button on the workspace background and choosing Windows > Restart Workspace Manager.
How to Allocate and Deallocate a Device
Users and roles must allocate a device for exclusive use before using it. Allocatable devices include audio, floppy, cdrom, and tape devices. The Device Allocation action handles device allocation and administering device allocation.
To Allocate a Device
-
Click the left mouse button on the triangle above the Style Manager icon on the Front Panel.
Its Trusted Desktop subpanel includes the Device Allocation icon.
-
Double-click the device to be allocated from the list of available devices.
floppy_0 allocates a diskette.
-
Click OK in the label builder that appears.
The file you load will be labeled at the label of your workspace. For most installation tasks, the files are labeled
admin_low.
Note -Depending on the value of Label View in your /etc/security/label_encodings file, a substitute label name may display for the administrative label
admin_low.
-
Follow the directions in the window that is displayed.
-
If the device can be mounted, answer the question:
Do you want device_n mounted: (y,n)?
For most installation tasks, answer y to mount the device:
To Deallocate a Device
-
Go to the workspace where the Device Allocation action is displayed.
If it is not displayed, click the Device Allocation icon on the Trusted Desktop subpanel, at the same label and in the same role as the one who allocated the device.
-
Double-click the device to be deallocated from the list of allocated devices.
-
Follow the directions in the window that appears.
A mounted device is automatically unmounted when it is deallocated.
-
To close the Device Allocation window, click the top left button and select Close.
How to Open the Application Manager
The Application Manager is an Applications subpanel action. It contains two folders that hold administrative applications, System_Admin and Solstice_Apps.
To Open the Application Manager
Click the arrow above the icon to the left of the mail icon on the Front Panel, and single-click the Applications action.
The Application Manager window appears, with several folders with distinctive icons.
How to Use the Solstice_Apps Folder
The Solstice_Apps folder holds applications that are used when configuring and maintaining a Trusted Solaris environment. These applications handle local files and their corresponding NIS+ table databases.
The following programs are accessible through the Solstice_Apps folder and are used when configuring a Trusted Solaris workstation:
- Host Manager
-
For setting up network installation.
- User Manager
-
For administering users.
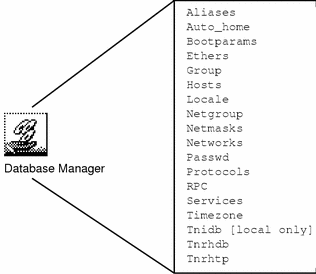
- Database Manager
-
For administering the following databases. One database is a local database only; the others are both local and NIS+ databases.
- Profile Manager
-
For adding and removing commands from a role's execution profile.
Figure 2-2 Databases Managed by the Database Manager in Solstice_Apps
To Open and Modify a Solstice_Apps Database
-
Left-click the Applications action.
The Applications icon is on the Applications subpanel to the left of the mail icon on the front panel.
-
Double-click the Solstice_Apps folder.
-
Double-click the appropriate icon, for example, one of --

-
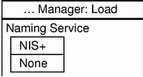
In the Load window choose None or NIS+ for the Naming Service.
Figure 2-3 Load Window for Naming Service
-
Choose NIS+ for the Naming Service if you want the changes to be in a NIS+ table, seen by all workstations on the network.
-
Choose None if you want the changes to be in a local file, or if you are on a workstation that is not running the NIS+ naming service.
-
-
If you are loading a database managed by the Database Manager, select the database and press Return.
-
To modify entries:
-
To add an entry, choose Edit > Add.
-
To modify an existing entry, select the entry and choose Edit > Modify.
-
To change an entry, select the entry, choose Edit > Delete, then add the correct entry using Edit > Add.
-
-
Choose File > Exit to exit the database after making your changes.
To Modify the Password for a Role or User Account
The install team in the role root initially modifies the secadmin, admin, and oper passwords. The install team also gives the first users their passwords.
When the install team chooses a password, the team must select one that is not easy to guess, thus reducing the chance of an attacker gaining unauthorized access by attempting to guess passwords.
-
As secadmin (as root during installation), at label
admin_lowopen the User Manager using the appropriate name service, NIS+ for a networked installation, None for no name service. -
Select from the list of users and press the Return key.
-
Click the Password... button.
-
Make sure that for a user, the value of Status is Open.
Note -For all administrative roles, and for the user who can assume the secadmin role, use the status Always Open. Also, do not set password expiration dates on administrative roles.
-
Make sure that the Cred Table Setup box is checked for networked installations.
-
Set other password information for the account.
See "Managing User Accounts" in Trusted Solaris Administrator's Procedures for a fuller explanation.
-
Exit the Password dialog and save the information.
To Customize Idle Time
Note -
The idle time for a role is not calculated. Roles time out when their user's session times out.
-
As secadmin at label
admin_lowin User Manager, select a user, not a role. -
Click the Idle... button.
-
Press the Idle button labeled 5 mins.
-
Choose a convenient setting in keeping with your site security policy.
The options are to lock the screen or to log the user out; different time lengths are possible.
-
Click OK, then Done.
To Delete a Local User
-
In the role admin, label
admin_low, open the User Manager as a local database.The user "install" is defined locally.
-
Select the user to be deleted, such as install.
-
Select Edit > Delete.
For the user install, you do not have a home directory or mail files to delete. Other local users may have home directories and mail files to delete.
When a user is deleted from the system, the administrator must ensure that the user's home directory and any objects owned by that user are also deleted. As an alternative to deleting objects owned by the user, the administrator may change the ownership of these objects to another user who is defined on the system.
The administrator must also ensure that all batch jobs still to run that are associated with the deleted user are also deleted. The administrator must ensure that there are no objects or processes belonging to a deleted user that remain on the system.
-
Close the User Manager by selecting File > Exit when you are done.
How to Use the System_Admin Folder
The System_Admin folder contains CDE actions for administering a single workstation. These actions do not overlap with the databases in Solstice_Apps. Double-clicking an action causes the action to run. An action that modifies a file invokes the Admin Editor, a trusted editor that prevents file renaming.
To create a file, invoke the Admin Editor and supply the name of the new file. Actions also run executables and may elicit input from the administrator. The following actions are accessible from the System_Admin folder. When the icon is the Admin Editor, the action is to edit the file.
Actions in the System_Admin Folder
- Add Allocatable Device
-
Edit /etc/security/tsol/device_maps
- Admin Editor
-
Create or edit any file
- AnswerBook2 Admin
-
Administer AnswerBook2TM
- Audit Classes
-
Edit /etc/security/audit_class
- Audit Control
-
Edit /etc/security/audit_control
- Audit Events
-
Edit /etc/security/audit_event
- Audit Startup
-
Edit /etc/security/audit_startup
- Audit Users
-
Edit /etc/security/audit_user
- Check Encodings
-
Check syntax (and install) label_encodings file
- Check TN Files
-
Check local tnrhdb and tnrhtp files
- Check TN NIS+ Tables
-
Check NIS+ tnrhdb and tnrhtp databases
- Create NIS+ Client
-
Create NIS+ client
- Create NIS+ Server
-
Establish root NIS+ domain
- Configure Selection ...
-
Edit /usr/dt/config/sel_config
- Edit Encodings
-
Edit /etc/security/tsol/label_encodings
- Eject CD-ROM
-
Eject CDROM
- Eject Floppy
-
Eject Floppy
- Format CD-ROM
-
Format CDROM
- Format Floppy
-
Format Floppy
- Open CD-ROM
-
Open CDROM
- Open Floppy
-
Open Floppy
- Power Manager
-
Manage auto-shutdown features
- Name Service Switch
-
Edit /etc/nsswitch.conf
- Populate NIS+ Tables
-
Populate NIS+ Tables
- Rename Floppy
-
Rename Floppy
- Set Daily Message
-
Edit /etc/motd
- Set Default Routes
-
Edit /etc/defaultrouter
- Set DNS Servers
-
Edit /etc/resolv.conf
- Set Mail Options
-
Edit /etc/mail/sendmail.cf
- Set Mount Attributes
-
Edit /etc/security/tsol/vfstab_adjunct
- Set Mount Points
-
Edit /etc/vfstab
- Set TSOL Gateways
-
Edit /etc/tsolgateways
- Share Filesystems
-
Edit /etc/dfs/dfstab
- Suspend System
-
Shut down system
- System Load
-
View system load
- Terminal Console
-
Open terminal console
- Terminal Remote
-
Open remote terminal
- Terminal Rlogin
-
Remote login to terminal
- View Table Attributes
-
View internal representation of a NIS+ table
- View Table Contents
-
View contents of a NIS+ table
- Watch Errors
-
Generate error log
- X Server Information
-
X Server information
To Run a System_Admin Action
-
In an administrative role, open the Application Manager by clicking the icon once with the mouse.
The Applications icon is on the Applications subpanel to the left of the mail icon on the front panel.
-
Double-click the appropriate action.
To Create or Open a File from the Trusted Editor
-
To create or open a file that does not have its own action, double-click the Admin Editor.
A prompt appears for you to specify the file to be opened.
-
Enter the name of the file to be opened.
If the file exists, it is opened. If the file does not exist, it is created.
Note -You cannot save a file to a different name from the trusted editor.
To Open a File that has a Defined Action
-
To open a file that has its own action, double-click its action.
The file associated with the action appears in the trusted editor.
-
Enter the required information, write the file, and exit the editor.
To Run a Script from the System_Admin Folder
-
To run an script that has its own action, double-click the action.
When the script requires input, the prompts are displayed.
-
Follow the instructions.
The script is finished when all prompt windows have been dismissed.
How to Add Network Interfaces
For every network interface, a file /etc/hostname.interface file must exist. The installation program creates the file for the primary interface only.
Note -
If this procedure is done by the install team before the roles secadmin and admin have been credentialed, they use root to do the procedure.
To Determine the Network Interfaces
-
As role admin, at label
admin_low, use the prtconf command to find the network interfaces.
# prtconf | grep instance ... le, instance #0 qe2, instance #0... qe3, instance #0...
-
List the secondary interfaces.
# ls /etc/hostname* hostname.le
The primary interface was configured during installation; its file exists.
Continue with "To Create the Network Interface Files".
If you know that you have created an /etc/hostname.interface entry for every interface, use the ifconfig(1M) command.
# ifconfig -a le0: flags= 863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> MTU 1500 inet 129.150.118.111 netmask ffffff00 broadcast 129.150.118.255 ether 8:0:21:62:13:a9 qe2: flags= 863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 129.150.117.22 netmask ffffff00 broadcast 129.150.117.255 ether 8:0:21:64:20:a3 qe3: flags= 863<UP,BROADCAST,NOTRAILERS,RUNNING,MULTICAST> mtu 1500 inet 129.150.119.111 netmask ffffff00 broadcast 129.150.119.255 ether 8:0:21:52:11:a2 |
Continue with "To Create the Network Interface Files".
To Create the Network Interface Files
-
As secadmin, at label
admin_low, for each secondary interface, open a file named /etc/hostname.interface in the Admin Editor.See "To Run a System_Admin Action" if you are unfamiliar with the steps.
For example, if the host grebe-118 is a secondary interface and uses a quad ethernet card, the file name is /etc/hostname.qe.
-
As secadmin, at label
admin_low, add every interface to the local /etc/hosts file using the Database Manager with no naming service.See "To Open and Modify a Solstice_Apps Database" if you are unfamiliar with editing the Hosts database.
-
As secadmin, at label
admin_low, add every interface to the local tnrhdb file using the Database Manager with no naming service.
How to Share a File System
Administrators access the /etc/dfs/dfstab file through the Share Filesystems action in the System_Admin folder.
Do not use proprietary names for shared file systems. The names of shared file systems are visible to every user.
To Share Home Directories and Other Filesystems
Perform this procedure on the home directory or on a file server. If the directory is being shared before the secadmin and admin roles are credentialed, the install team performs the procedure in the role root.
-
As role admin, at label
admin_low, run the Share Filesystems action from the System_Admin folder in the Application Manager.The Share Filesystems action opens the /etc/dfs/dfstab file.
-
As the role admin, at label
admin_low, run the share(1M) command to share the file systems.For example, to share home directories:
$ share /export/home
For example, to share a network install directory:
$ share /export/install/tsolfiles $ share /jumpstart
See the NIS+ and FNS Administration Guide for ways to restrict home directory access to particular groups.
-
Check that the directories are shared.
To Check That a Directory Is Shared
To Start the nfs.server Daemon
-
In the role admin, at label
admin_low, start the nfs server program.
$ /etc/init.d/nfs.server stop $ /etc/init.d/nfs.server start
-
Check that the directory is shared.
For example, when home directories are shared:
$ showmount -e export list for home_directory_server: /export/home (everyone)
How to Set the Label on an Unlabeled File System
The security administrator uses the System_Admin folder to access the /etc/security/tsol/vfstab_adjunct file.
-
Log in as a user who can assume the role secadmin and assume the role.
-
As secadmin, at label
admin_low, edit the file /etc/security/tsol/vfstab_adjunct using the Set Mount Attributes action in the System_Admin folder. -
Copy the template entry, and modify it for the file system to be protected.
For example, the following example shows a vfstab_adjunct entry for an unlabeled, remote file system, /cpublic, being mounted at the label Confidential ([C]) on a Trusted Solaris 7 network.
Example 2-1 vfstab_adjunct Entry for Unlabeled Remote Host
# Modified template. # /cpublic; \ acc_acl=; \ mode=; \ attr_flg=; \ gid=; \ uid=; \ slabel=C; \ forced=; #
Every file in the /cpublic file system will be protected at the label Confidential.
Note -This example requires the security administrator to have created a new template. See "To Edit the Tnrhtp Database (Example)".
How to Mount a File System
Administrators access the /etc/vfstab file through the System_Admin folder, and create the mount points in a profile shell.
Do not use proprietary names for mounted file systems. The names of mounted file systems are visible to every user.
To Mount a Labeled or Unlabeled File System
The Set Mount Points action opens the /etc/vfstab file.
-
As role admin, at label
admin_low, run the Set Mount Points action in the System_Admin folder.For example, the grebe:/opt/tools file system will be mounted every time the workstation is booted.
grebe:/opt/tools - /opt/tools nfs - yes bg,intr,soft
-
Write the file and exit the editor.
-
As role admin, at label
admin_low, create the mount point and mount the home directories.
$ mkdir -p /opt/tools $ mount /opt/tools
The following is a sample entry in the vfstab file for /cpublic, an unlabeled file system:
chincoteague:/cpublic - /cpublic nfs - yes bg,intr
How to Update the Commands in a Role's Profile
When setting up a network or custom JumpStart install, some required commands are not available to the role because they are not in an execution profile assigned to the role. To add commands, programs, or scripts to the role's profile, you modify the "Custom Rolename Role" profile. For example, to add a command to the profile shell of the role root, you modify the Custom Root Role profile.
To Add a Command to a Role's Profile
-
Log in as a user who can assume the role secadmin.
-
As secadmin, at label
admin_low, open the Profile Manager from the Solstice_Apps folder using the NIS+ naming service. -
Load the "Custom Rolename Role" into the Profile Manager.
-
In the Commands view, type the pathname to the command.
For example, to access the Trusted Solaris CDROM, type:
Pathname: /cdrom/cdrom0
-
In the list of Excluded commands, double-click the directory /cdrom/cdrom0.
-
From the list of Excluded commands, choose the command to be added to the profile.
To continue the above example, add setup_install_server to the Included list.
-
Give the command all privileges and save the Custom Rolename Role profile.
To Verify That a Command is in a Role's Profile
-
Log in as a user who can assume the role whose profile has been updated.
-
Assume the role and launch a terminal from the role's workspace.
-
Verify that the new profile is in effect in the new terminal by using the clist(1M) command.
For example, to verify the command in the preceding example:
# clist -p | grep setup_install_server It should display: /cdrom/cdrom0/setup_install_server: all # clist -i | grep setup_install_server It should display: none none /cdrom/cdrom0/setup_install_server
To Remove a Command from a Role's Profile
-
As secadmin, at label
admin_low, load the "Custom Rolename Role" into the Profile Manager. -
In the Commands view, locate and select the pathname to the command.
-
From the list of Included commands, double-click the command to be moved to the Excluded list.
How to End a Session
Users can lock their screen or log out at the end of a session. Users authorized to shut down the workstation can halt it and reboot.
Note -
Users must log off or utilize the lockscreen functionality before leaving a workstation unattended. Otherwise a person may have access to the data of a user without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
To Lock the Screen
To Log Out
-
Right-click the workspace background and select Log out... from the Workspace Menu, or left-click the EXIT icon on the Front Panel.
-
When prompted, confirm that you want to log out.
To Reboot the Workstation
-
Right click the CDE front panel and select Shut Down from the TP (Trusted Path) menu.
The menu appears when the user or role is authorized to shut down the workstation.
-
Confirm the shutdown.
-
Enter boot at the ok prompt or b at the > prompt:
Type help for more information <#2> ok boot Type b (boot), c (continue), or n (new command mode) > b
- © 2010, Oracle Corporation and/or its affiliates
