How SLs and Clearances Are Used in Access Control Decisions
Sensitivity labels and clearances are compared when access control decisions are made. The clearance of a process executing an application is equal to the session clearance. The sensitivity label and clearance of the process are compared to the sensitivity label of anything that the application tries to access. The labels are compared for dominance. For more details about the mandatory access control rules that are enforced when sensitivity labels are compared, see the DEFINITIONS section in Intro(1).
Within the window system, the sensitivity label of the process generally must equal the sensitivity label of the thing being accessed or access is not allowed. (A notable exception to the read equal/write equal rule include email readers, for which the write up/read down (wurd) rule applies. Writes up are limited by the session clearance.)
Example Mandatory Access Control Decision
If an employee brings up a text editor in a workspace with a sensitivity label of PUBLIC, the process executing the text editor is assigned the same sensitivity label as the workspace.
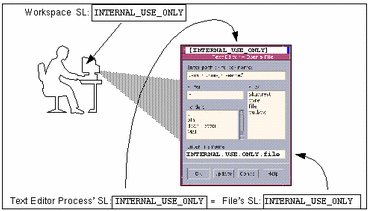
Figure 1-1 shows a comparison between two sensitivity labels used in making an access control decision. The user is in a workspace with the sensitivity label INTERNAL_USE_ONLY. When he brings up a text editor, the sensitivity label of the process running the text editor is automatically set to be equal to the sensitivity label of his current workspace, and the text editor displays a label of INTERNAL_USE_ONLY. When the text editor attempts to open a file for editing, the sensitivity label of the text editor is compared to the sensitivity label of the file. In the example, because the two sensitivity labels are equal, access is allowed.
Figure 1-1 Comparing the SL of a Text Editor with the SL of the File to be Edited
- © 2010, Oracle Corporation and/or its affiliates
