Chapter 3 Basic Procedures
This chapter covers common administrative procedures when configuring a Trusted Solaris host. Later chapters point to the procedures in this chapter.
Note -
Installation and configuration commands and actions are limited to particular roles and particular labels. Read each task for the administrative role that can perform it, and the label required. After doing the task, return to the installation and configuration chapter you were working from.
How to Log In
The predefined user install logs in immediately after installation to configure the workstation. At most sites, two or more administrators, an install team, are present when configuring the workstation. "You", in the following procedure, refers to the install team.
To Log In as the User Install
-
Log in to the workstation as the user install.
-
Enter install as the user name and press the Return key.
The Password dialog box is displayed.
-
Enter install for the password.
The Enable Logins dialog offers four choices, as shown in the following figure:
Figure 3-1 The Enable Logins Dialog
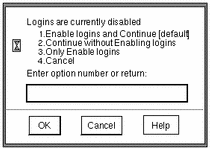
-
Depending on site security requirements, enter 1 or 2, then click OK.
The Message Of the Day dialog is displayed; the label is
ADMIN_LOW. -
Click OK to dismiss the dialog.
The Trusted Solaris screen appears briefly; then you are in a CDE workspace, as shown in Figure 3-2. The trusted stripe below the front panel shows the window sensitivity label.
-
-
Return to the procedure and chapter you are working from.
To Log In as a Regular User
-
Enter your password.
Note -Users must not disclose their passwords to another person, as that person may then have access to the data of the user and will not be uniquely identified or accountable. Note that disclosure can be direct, through the user deliberately disclosing his/her password to another person, or indirect, such as through writing it down, or choosing an insecure password. Trusted Solaris provides protection against insecure passwords, but cannot prevent a user disclosing his/her password or writing it down.
The Enable Logins dialog, shown in Figure 3-1, is displayed if you are authorized to enable logins.
If you see the error message:
Logins are currently disabled. Please ask your system administrator to enable logins.
then your user was not assigned the Enable Login right (see Table 3-4). To fix, give the user the Enable Login right, or have someone else log in and enable logins.
-
Choose a login option and dismiss the dialog.
The Message Of the Day dialog is displayed. In a multilevel session, the default is to log in at the lowest label in your label range. You can also restrict your session to a single label.
-
Click OK to accept the default given to you by the security administrator.
Once the login process is complete, the Trusted Solaris screen appears briefly, and you are in a CDE session with four workspaces. If your user account is configured to display labels, the label of your session (a user account cannot be
ADMIN_LOW) will show in the trusted stripe.
Note -The install team must log off or utilize the lockscreen functionality before leaving a workstation unattended. Otherwise a person may have access to the workstation without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
-
Return to the procedure and chapter you are working from.
How to Assume a Role
An administrative role configures the workstation, however, a role cannot log in. Users log in, and assume one or more of their assigned roles. The role root has been pre-assigned to the user install.
To Assume a Role
-
Log in to the workstation as a user, such as install.
-
Right click on the middle of the Front Panel.
-
Assume a role from the roles displayed on the TP (Trusted Path) menu.
Figure 3-2 A Trusted Solaris User Workspace
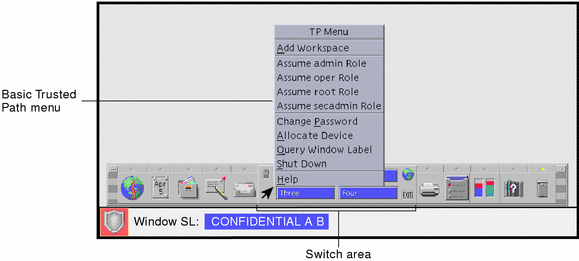
After initial installation from a CD-ROM, only the root role will be displayed on the TP menu, since no other roles have been created.
-
Return to the procedure and chapter you are working from.
How to Launch a Terminal
Use the background menu to launch a terminal. The terminal displays the default shell for the user or role who launches the terminal.
To Launch a Terminal
-
Right-click on the workstation background and select Tools > Terminal from the Workspace Menu.
Note -The Options menu enables you to customize the appearance of the terminal. Customizations for the user "install" are not saved.
-
Return to the procedure and chapter you are working from.
How to Create an Admin_High Workspace
Some administrative actions require a process at a higher label than the default. To get a higher-labeled process, create a workspace at that higher label, and launch actions and terminals from the new workspace.
Note -
If you are not allowed to change the workspace label, the Change Workspace Label menu item is not displayed.
To Create an Admin_High Workspace
-
Click the right menu button on workspace label for the TP menu.
-
Choose Change Workspace Label from the menu, select the
ADMIN_HIGHlabel and click OK.Actions, terminals, commands and windows originating from the newly labeled workspace run at the label of the workspace.
-
Return to the procedure and chapter you are working from.
How to Protect Machine Hardware
For security, access to the PROM should also be protected with a password.
SPARC: To Set the PROM Mode and Password
-
Choose the value command or full (see the eeprom(1M) man page for more details).
You are prompted to enter and confirm the PROM password.
# eeprom security-mode=command Changing PROM password: New password: password Retype new password: password
-
If you are not prompted to enter a PROM password, the workstation already has a PROM password. To change it, run the command:
# eeprom security-password=Return Changing PROM password: New password: password Retype new password: password
As root, label ADMIN_LOW, in the profile shell, enter the PROM security mode.
The new PROM security mode and password are in effect immediately, but are most likely to be noticed at the next boot.
Do not forget this password. The hardware is unusable without it.
For more information on PROM values that you can set, see OpenBoot 2.x Command Reference Manual or OpenBoot 3.x Command Reference Manual.
IA: To Protect the BIOS
On Intel architecture, the equivalent to protecting the PROM is to protect the BIOS.
Refer to your machine's manuals for how to protect the BIOS.
How to Allocate and Deallocate a Device
Users and roles must allocate a device for exclusive use before using it. Allocatable devices include audio, floppy, CD-ROM, and tape devices. The Device Allocation action handles device allocation and administering device allocation.
To Allocate a Device
-
In a workspace at the target label, click the left mouse button on the triangle above the Style Manager icon on the Front Panel.
Its Tools subpanel includes the Device Allocation icon.
-
Double-click the device to be allocated from the list of available devices.
floppy_0 allocates a diskette.
-
Click Yes to the mount question.
A File Manager pops up showing the mount point. (If it does not pop up, open a File Manager from the Front Panel, navigate to /, and double-click floppy.)
-
If you are in the admin role allocating a CD-ROM for network installation, see "Additional Steps to Set up Software Installation" for additional steps. Otherwise, return to the procedure and chapter you are working from.
To Deallocate a Device
-
Go to the workspace where the Device Allocation action is displayed.
If it is not displayed, click the Device Allocation icon on the Tools subpanel, at the same label and in the same role as the one who allocated the device.
-
Double-click the device to be deallocated from the list of allocated devices.
-
Remove the device and click OK in the Deallocation dialog.
-
Return to the procedure and chapter you are working from.
How to Copy to and from a Portable Medium
When copying to a portable medium, label the medium with the sensitivity label of the information.
Note -
During installation, the role root copies administrative files to and from portable media. Most files are copied at label ADMIN_LOW. The two exceptions are the label_encodings and vfstab_adjunct
files, that are labeled ADMIN_HIGH.
To Copy to a Diskette
-
First, in a workspace at the target label, allocate the floppy device at the correct label using the Device Allocation action, and insert a clean diskette.
For a fuller description, see "To Allocate a Device".
-
Open a second File Manager from the Front Panel and navigate to the folder that contains the files to be copied, such as /export/clientfiles.
-
Rename the label_encodings file that you are copying.
For example, name it label_encodings.site (for SPARC architecture), or lblcdsit (for Intel architecture). Audit system files such as audit_event, and routing files such as nsswitch.conf, and resolv.conf do not need to be renamed.
-
Highlight the icon for the file and drag the file to the floppy disk folder.
-
Deallocate the device, as described in "To Deallocate a Device".
-
On the floppy disk folder, choose Eject from the File menu.
Note -Remember to physically affix a label to the medium with the sensitivity label of the copied files.
-
Return to the procedure and chapter you are working from.
To Copy from a Diskette
It is safe practice to rename the original Trusted Solaris file before copying in a file to replace it. During installation, the root role renames and copies administrative files at ADMIN_LOW
-
Allocate the floppy device using the Device Allocation action and insert the diskette.
For a fuller description, see "To Allocate a Device". The label_encodings file requires a diskette allocated at the label
ADMIN_HIGH. -
If the workstation has a file of the same name, copy it to a new name and remove the original.
Note -Exception: If the file you are copying is to replace the current label_encodings file, do not rename or remove the original file. See "How to Install a Label Encodings File" for the full procedure.
-
Open a second File Manager from the Front Panel and navigate to the desired destination directory, such as /etc/security/tsol.
-
Highlight the icon for the file and drag the file from the floppy disk folder to the destination directory.
-
Deallocate the device as described in "To Deallocate a Device".
-
Click OK on the dialog when prompted to manually eject /dev/rdiskette, and eject the floppy.
-
Return to the procedure and chapter you are working from.
How to Run Administrative Actions
The Application Manager contains a folder that holds administrative applications for the local machine, System_Admin and an action, Solaris Management Console, for administering local and distributed databases.
How To Use System_Admin Actions
The System_Admin folder contains CDE actions for administering the local workstation. See the following table for a list of actions used during installation and configuration. For a full list of System_Admin actions, read the CDE online help.
Table 3-1 Trusted Solaris Actions in the System_Admin Folder|
Action Name |
Action Behavior |
|---|---|
|
Add Allocatable Device |
Edit /etc/security/device_maps |
|
Admin Editor |
Create or edit any file |
|
Audit Classes |
Edit /etc/security/audit_class |
|
Audit Control |
Edit /etc/security/audit_control |
|
Audit Events |
Edit /etc/security/audit_event |
|
Audit Startup |
Edit /etc/security/audit_startup |
|
Audit Users |
Edit /etc/security/audit_user |
|
Check Encodings |
Check syntax (and install) a label encodings file |
|
Check TN Files |
Check local tnrhdb and tnrhtp files |
|
Check TN NIS+ Tables |
Check NIS+ tnrhdb and tnrhtp databases |
|
Create NIS Client |
Make this host a NIS client |
|
Create NIS+ Client |
Make this host a NIS+ client |
|
Create NIS Server |
Establish a NIS server with NIS maps |
|
Create NIS+ Server |
Establish a NIS+ domain |
|
Configure Selection ... |
Edit /usr/dt/config/sel_config |
|
Edit Encodings |
Edit a label encodings file |
|
Name Service Switch |
Edit /etc/nsswitch.conf |
|
Populate NIS+ Tables |
Populate NIS+ tables from a files directory |
|
Set Default Routes |
Edit /etc/defaultrouter |
|
Set DNS Servers |
Edit /etc/resolv.conf |
|
Set Mount Attributes |
Edit /etc/security/tsol/vfstab_adjunct |
|
Set Mount Points |
Edit /etc/vfstab |
|
Set TSOL Gateways |
Edit /etc/tsolgateways |
|
Share Filesystems |
Edit /etc/dfs/dfstab |
To Run a System_Admin Action
-
In an administrative role, open the Application Manager by right-clicking the background to bring up the Workspace menu. Choose Applications > Application Manager from the top of the menu.
-
Double-click the appropriate action. For more details, see "To Create or Open a File from the Trusted Editor", "To Open a File that has a Defined Action" and "To Run a Script from the System_Admin Folder".
To Create or Open a File from the Trusted Editor
-
To create or open a file that does not have its own action, double-click the Admin Editor action.
A prompt appears for you to specify the file to be opened.
-
Enter the name of the file to be opened.
If the file exists, it is opened. If the file does not exist, it is created. You can create an empty file (touch) by exiting the editor.
Note -You cannot save a file to a different name from the trusted editor.
-
Return to the procedure and chapter you are working from.
To Open a File that has a Defined Action
-
To open a file that has its own action, double-click its action in the System_Admin folder.
The file associated with the action appears in the trusted editor.
-
Enter the required information, write the file, and exit the editor.
-
Return to the procedure and chapter you are working from.
To Run a Script from the System_Admin Folder
-
To run a script that has its own action, double-click the action in the System_Admin folder.
When the script requires input, the prompts are displayed.
-
Follow the instructions.
The script is finished when all prompt windows have been dismissed.
-
Return to the procedure and chapter you are working from.
How to Use the Solaris Management Console
The Solaris Management Console action in the Application Manager folder invokes a Java-based administrative GUI for configuring and maintaining a Trusted Solaris environment. The GUI lists toolboxes in a Navigation pane.
The following can be configured through the Solaris Management Console, using the Trusted Solaris Management Console > Trusted Solaris Configuration toolboxes in the Navigation pane:
- User Accounts
-
Part of the Users tool, for administering users.
- Administrative Roles
-
Part of the Users tool, for administering roles.
- Rights
-
Part of the Users tool, for constructing rights profiles. A user account is not usable until the user's Rights have been assigned.
- Mailing Lists
-
Part of the Users tool, for administering mail aliases.
- Computers and Networks
-
For setting up networks.
- Computers
-
Part of the Computers and Networks tool, for setting up hosts (the hosts database).
- Security Families
-
Part of the Computers and Networks tool, for creating and assigning remote host templates (the tnrhtp(4) and tnrhdb(4) databases).
- Interface Manager
-
For securing network interfaces (the tnidb(4) database). Accessible only when Scope=Files.
The following are configured through the Solaris Management Console, using Trusted Solaris Management Console toolboxes:
- Mounts
-
Part of the Storage tool, for mounting file systems. Accessible only when Scope=Files.
- Shares
-
Part of the Storage tool, for sharing file systems. Accessible only when Scope=Files.
To Initialize the SMC Server
-
In the root role, open the Application Manager by right-clicking the background to bring up the Workspace menu. Choose Applications > Application Manager from the top of the menu.
-
Double-click the Solaris Management Console action.
Note -The Solaris Management Console action initiates the SMC server. The first time the server is launched, it performs several registration tasks, which can take from 5 to 10 minutes. The following message may appear briefly: "There is no Solaris Management Console server ...". The message goes away, and can be ignored.
-
If the Navigation Pane is not visible and no toolboxes are displayed, do the following:
-
In the Open Toolbox dialog that is displayed, click Load next to where this machine's name is listed under Server.
If this machine does not have the recommended amount of memory and swap, it may take a few minutes for the toolboxes to display. See "Recommendations for the Trusted Solaris Environment".
-
From the list of toolboxes, select Trusted Solaris Management Console, then click the Open button.
-
Before continuing, save the current setting as described in "To Save the Current Toolbox".
-
-
If the Navigation pane is visible, but the toolbox icons are stop signs, do the following:
-
Select the Trusted Solaris Management Console toolbox.
-
Click the Open Toolbox button.
-
Click Load next to Server: this_machine_name.
-
From the list of toolboxes, select Trusted Solaris Management Console, then click the Open button.
-
Before continuing, save the current setting as described in "To Save the Current Toolbox".
-
To Save the Current Toolbox
Save the toolbox preference to provide the Trusted Solaris Management Console toolboxes by default. The preferences are saved per role, per host (SMC server).
-
From the Console menu, choose Preferences.
-
Click the Use Current Toolbox button, then OK.
-
Return to the procedure and chapter you are working from.
To Select a Toolbox of the Appropriate Scope
Prerequisite: The Solaris Management Console (SMC) server has been initialized on this computer, the Trusted Solaris Management Console toolboxes have been saved as the current toolbox, and they are displayed in the Navigation pane.
-
OPTION 1: Select this_host: Scope=Files, Policy=TSOL if you plan to administer each machine locally, or are administering files that can only be administered locally, such as local users (like root or install), the tnidb(4) database, or the local tnrhdb(4) database before the name service has been established.
-
OPTION 2: Select name_server: Scope=name_service, Policy=TSOL if you are administering name service maps or tables, and have established the name service domain and have edited the toolbox with the name of the server and the domain on this client machine (see "To Edit Name Service Toolbox Definitions").
Select the toolbox of the appropriate scope:
To Locate a Solaris Management Console Tool
Scope=Files and Scope=name_service contain different tools.
-
To find aand use a tool in this_host: Scope=Files, Policy=TSOL in the Navigation pane:
-
Click the System Status key to view the Processes and Log Viewer tools.
-
To manage and monitor system processes, double-click Processes.
-
To see the logs monitored by WBEM, double-click Log Viewer.
-
-
Click the Trusted Solaris Configuration key to view the Users, Computers and Networks, and Interface Manager tools.
-
To add or modify a user, a role, a right, a group, or a mailing list on this machine, double-click Users.
-
To add or modify a remote host definition for this machine, double-click Computers and Networks.
-
To add or modify a host, double-click Computers, select a computer, then choose an item from the Action menu.
-
To add or modify a remote host template, double-click Security Families, then choose an item from the Action menu.
-
To add or modify a remote host template assignment, double-click Security Families, double-click a template name, then choose Add Host(s) from the Action menu.
-
-
To modify the security attributes of a network interface, double-click Interface Manager.
-
-
Click the Services key to view the SMC Server and the Scheduled Jobs tools.
-
The SMC Server tool is not fully implemented.
-
To see this machine's scheduled jobs, double-click Scheduled Jobs.
-
-
Click the Storage key to view the Mounts and Shares and Disks tools.
-
To mount a remote file system, double-click Mounts and Shares, then Mounts.
-
To share a file system, double-click Mounts and Shares, then Shares.
-
To view and format disks, double-click Disks.
-
-
Click the Devices and Hardware key to view the Serial Ports tool. Double-click Serial Ports to configure and manage existing serial ports.
-
-
To find and use a tool in the name_server: Scope=name_service, Policy=TSOL toolbox in the Navigation pane, click the Trusted Solaris Configuration key to view the Users and the Computers and Networks tools:
-
To add or modify a user, a role, a right, a group, or a mailing list on the domain, double-click Users.
-
To add or modify a remote host definition on the domain, double-click Computers and Networks.
-
-
When prompted, enter the role password in the Role Login prompt.
-
Read and follow the online help for assistance with each tool.
-
Return to the procedure and chapter you are working from.
To Edit Name Service Toolbox Definitions
If you are running a NIS or NIS+ name service, the tsol_nis.tbx or tsol_nisplus.tbx file must be edited on the name service master before it can be used on the domain.
If administrators plan to administer the name service's tables or maps from a client machine, this procedure must be done on the client.
Note -
Administrators who want to administer a name service using SMC must do this procedure on every machine that will be used to administer the name service.
-
In the root role at the label
ADMIN_LOW, change to the toolboxes directory and list the toolboxes.
# cd /var/sadm/smc/toolboxes # ls tsol*/*tbx tsol_files/tsol_files.tbx tsol_nis/tsol_nis.tbx tsol_smc/tsol_smc.tbx tsol_nisplus/tsol_nisplus.tbx
-
If you are running the NIS+ name service, your toolbox file is tsol_nisplus/tsol_nisplus.tbx
-
If you are running the NIS name service, your toolbox file is tsol_nis/tsol_nis.tbx
-
-
Invoke the Admin Editor, as described in "To Create or Open a File from the Trusted Editor".
-
Copy and paste the full pathname to the toolbox into the dialog, as in: /var/sadm/smc/toolboxes/tsol_nisplus/tsol_nisplus.tbx
-
In the editor, replace each instance of <?server ?> with either the name of the master server or the name of the domain.
-
In the line beginning with <Scope>, replace the first instance of <?server ?> with the name service master, and the second with the fully-qualified domain name, as in:
<Scope>nisplus:/toucan/aviary.eco.org</Scope>
-
Replace every other instance of <?server?> or <?server ?> with the name service master, as in:
<Name> toucan: Scope=NIS+, Policy=TSOL</Name> services and configuration of toucan.</Description> and configuring toucan.</Description> <ServerName>toucan</ServerName> <ServerName>toucan</ServerName
-
-
Write (:wq!) and quit the editor.
-
Return to the procedure and chapter you are working from.
How to Install a Label Encodings File
Consult Trusted Solaris Label Administration for requirements, procedures, and suggestions for the label encodings file.
You can edit the placeholder label_encodings(4) file that the Trusted Solaris installation program installed, or install your own. The security administrator is responsible for editing, checking, and maintaining the label_encodings file.
Note -
The label_encodings file is protected at the label ADMIN_HIGH. For security, copy, edit, check and install your label encodings file at ADMIN_HIGH.
To Install a Site-Specific Label Encodings File
-
In the root role (before other roles are created), or in the secadmin role (after roles have been created and verified), create an
ADMIN_HIGHworkspace.See "How to Create an Admin_High Workspace" if you are unfamiliar with operating at the label
ADMIN_HIGH. -
Copy your site's label encodings file from an
ADMIN_HIGHdiskette to a writable location, such as /export/clientfiles/label_encodings.site using the File Manager.If you are unsure of the steps, see "To Copy from a Diskette".
If you plan to tweak the file, make sure that the file itself is writable.
-
Check the syntax of the new label encodings file.
-
Double-click the Check Encodings action in the System_Admin folder in the Application Manager.
For more information on running a script from the System_Admin action, see "To Run a Script from the System_Admin Folder". You can ignore any Trash Can Error dialog error messages.
-
In the dialog box, enter the full path name of the file: /export/clientfiles/label_encodings.site
-
-
Read the contents of the Check Encodings dialog box that is displayed.
The chk_encodings(1M) command checks the syntax of the file. If the file passes the check, the action asks whether you want to overwrite the currently-installed label_encodings file. If the answer is yes, the action creates a backup copy (naming it label_encodings.orig), installs the checked version, then restarts the label daemon.
- CONTINUE
-
Only if it reports no errors can you continue installing.
- RESOLVE ERRORS
-
If it reports errors, they must be resolved before continuing with installation.
For detailed procedures and explanation, consult "Creating or Editing the Encodings File" in Trusted Solaris Label Administration.
 Caution -
Caution - Your label encodings file must pass the Check Encodings test before you continue.
How to Set Up Static Routing
Routing is required only if the security administrator has planned for an open network. There are three routing methods available: dynamic routing (the default), and static routing (using a defaultrouter or tsolgateways file).
For small networks, an /etc/defaultrouter file provides a simple routing method. If your workstation or site accesses a complex network of gateways, the /etc/tsolgateways file offers more control over static routing. See "Administering Trusted Networking" in Trusted Solaris Administration Overview and the tsolgateways(4) man page for more information.
To Set Up Simple Static Routing
Note -
For static routing, do either this procedure, or "To Set Up Complex Static Routing".
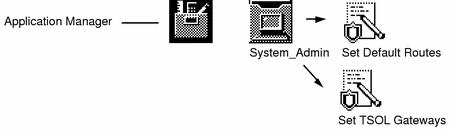
-
Double-click the Set Default Routes action in the System_Admin folder.
See "To Open a File that has a Defined Action" if you are unfamiliar with using trusted actions.
An empty /etc/defaultrouter file appears in the trusted editor.
-
Enter the name or the IP address of the defaultrouter. If there is more than one, enter them all, one per line, and then save the file.
For example, if the workstations trustworthy and forwardho are routers, enter them, one per line:
trustworthy forwardho
-
Return to the procedure and chapter you are working from.
To Set Up Complex Static Routing
-
Double-click the Set TSOL Gateways action in the System_Admin folder.
See "To Open a File that has a Defined Action" if you are unfamiliar with using trusted actions.
An empty /etc/tsolgateways file appears in the trusted editor. See the tsolgateways(4) man page for examples of how to format the file.
-
Enter the IP address of the net, the name of the gateway and its metric. Repeat for every gateway and save the file.
For example, if the workstations trustworthy and forwardho are gateways:
129.150.150.0 trustworthy 1 129.150.8.0 forwardho 2
Note -If the workstation has an /etc/defaultrouter file and an /etc/tsolgateways file, only the /etc/tsolgateways file is used for routing decisions.
-
Return to the procedure and chapter you are working from.
How to Add Hosts
The install team enters every host that the local machine should contact upon booting into the local hosts database. If the local machine is a name service client, it will find its file servers, home directory server, and other servers from the name service master.
To Add Hosts to Local Machine's Known Network
-
At the label
ADMIN_LOW, in an administrative role, initially the root role, invoke the Solaris Management Console from the Application Manager.If you are unfamiliar with accessing the Solaris Management Console, see "To Initialize the SMC Server". Note that the SMC must be initialized before use.
-
Click this_host: Scope=Files, Policy=TSOL under Trusted Solaris Management Console in the Navigation pane.
-
Click Trusted Solaris Configuration, then Computers and Networks, then double-click Computers.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
The known hosts are displayed in the View pane. This workstation should already be in the database. You should add the following hosts:
-
Name service master, if any.
-
Static routers, if any.
-
Audit servers for this workstation.
-
If this workstation does not use a name service, add all computers that this machine can contact.
-
-
Choose Add Computer from the Action menu.
-
Click Apply to add a computer, and click OK when the entries are complete.
-
If the network 0.0.0.0 is defined under Computers and Networks, remove it. It is a security risk. See "Modifying the Boot-time Trusted Network Databases" in Trusted Solaris Administrator's Procedures
-
Return to the procedure and chapter you are working from.
How to Add a Remote Host Template
The tnrhtp(4) file installed by the Trusted Solaris installation CDs contains examples of templates that match the label_encodings(4) file installed by the Trusted Solaris installation CDs. Sites who install a site-specific label_encodings file must create templates that match the labels that they recognize, as described the following procedure.
To Add a Remote Host Template
-
At the label
ADMIN_LOW, in an administrative role, initially the root role, invoke the Solaris Management Console from the Application Manager.If you are unfamiliar with accessing the Solaris Management Console, see "To Initialize the SMC Server". Note that the SMC must be initialized before use.
-
Click this_host: Scope=Files, Policy=TSOL under Trusted Solaris Management Console in the Navigation pane.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click Trusted Solaris Configuration, then Computers and Networks, then double-click Security Families.
The existing templates are displayed in the View pane.
Note -If you installed a site-specific label_encodings file, it is highly likely that the existing templates will not work with your file. The tnrhtp must contain templates that reflect the labels of machines and networks your site can contact.
You should have templates for:
-
The Trusted Solaris hosts that this machine can contact.
-
Any unlabeled hosts/networks that this machine can contact..
-
-
Choose Add Template from the Action menu.
-
In the Basic Information tab, create a template named unlab_userlabel, of host type Unlabeled, with an
ADMIN_HIGHclearance and a process label of low_user_label.The default Failed Cross Reference Format must dominate the default label. The label ADMIN_HIGH dominates all labels.
-
Return to the procedure and chapter you are working from.
How to Assign a Remote Host Template
The trusted network remote host database, tnrhdb(4), enables this host to communicate with remote hosts. The man page describes the format of the tnrhdb, and suggests how to minimize the number of entries required.
To Assign a Template to a Host
-
At the label
ADMIN_LOW, in an administrative role, initially the root role, invoke the Solaris Management Console from the Application Manager.If you are unfamiliar with accessing the Solaris Management Console, see "To Initialize the SMC Server". Note that the SMC must be initialized before use.
-
Click this_host: Scope=Files, Policy=TSOL under Trusted Solaris Management Console in the Navigation pane.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click Trusted Solaris Configuration, then Computers and Networks, then double-click Security Families.
The remote host templates display in the View pane.
-
Double-click the tsol security family.
-
Choose Add Host(s) from the Action menu.
-
In the Add Host(s) dialog, click Add Wildcard to assign this template to all hosts on your Trusted Solaris 8 subnet.
-
Choose Add Host(s) from the Action menu and click Add Host in the Add Host(s) dialog to enter any exceptions to the subnet template assigment. Click OK to end the entry.
For example, enter 129.150.110.3 and unlab_user_label. This host on the subnet is an unlabeled host, an exception to the tsol wildcard entry.
-
Choose Add Host(s) from the Action menu and click Add Host to enter the IP address of every host in your /etc/defaultrouter or /etc/tsolgateways file, and assign to each an appropriate template name. Click OK to end each entry.
-
Enter the details of other subnets and hosts.
-
Enter the wildcard designation of each subnet and choose its appropriate template by choosing Add Host(s) -- Choose Wildcard.
-
Individually assign a different template to any host that is an exception to its subnet's assigned template by choosing Add Host(s) -- Choose Host.
Use the details provided by your system administrator, then choose the appropriate template name from the menu. See Table 1-3 for host types and their associated templates provided by Trusted Solaris software.
-
-
Open a terminal and reload and verify the updated tnrhdb database.
# tnctl -H /etc/security/tsol/tnrhdb # tninfo -h
-
Return to the procedure and chapter you are working from.
How to Share a File System
The install team performs this procedure on the home directory or on a file server. If the directory is being shared before the admin role is created, the install team performs the procedure in the root role.
Do not use proprietary names for shared file systems. The names of shared file systems are visible to every user.
To Share File Systems
See the NIS+ and FNS Administration Guide for ways to restrict home directory access to particular groups.
-
In the admin role, (or root if the admin role does not exist), at label
ADMIN_LOW, under Trusted Solaris Management Console, click this_host: Scope=Files, Policy=TSOL.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click Storage, then double-click Mounts and Shares, then double-click Shares.
-
Choose Add Shared Directory from the Action menu.
-
Follow the online help to share the /export/home directory.
The tool shares the directory and starts the NFS daemons,
-
Verify that the directories are shared.
$ showmount -e export list for homedir_server: /export/home
-
Return to the procedure and chapter you are working from.
How to Mount a File System
In the Trusted Solaris environment, unlabeled and labeled hosts can be mounted on a Trusted Solaris labeled host.
Do not use proprietary names for mounted file systems. The names of mounted file systems are visible to every user.
To Mount a File System
-
In the admin role, (or root if the admin role does not exist), at label
ADMIN_LOW, under Trusted Solaris Management Console, click this_host: Scope=Files, Policy=TSOL.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click Storage, then double-click Mounts and Shares, then double-click Mounts.
-
Choose Add NFS Mount from the Action menu.
-
Follow and answer the prompts to mount the file system.
You are prompted to allow creation of the mount point if it does not exist. The tool adds an entry in the /etc/vfstab file, creates the mount point, and mounts the file system
-
Return to the procedure and chapter you are working from.
How to Create Administrative Roles
The install team creates the administrative roles (other than root) to be used at the site. The team assigns each role its rights profiles. Initial rights profiles are provided on the installation CD-ROM.
Prerequisite: If you are using a name service, the name service and home directory must be set up before you create the administrative roles secadmin, admin, and oper.
To Create a Role
Note -
In previous releases, roles were local. In Trusted Solaris 8, roles (other than root) can be distributed, and are created by the install team. Profiles are hierarchical, so each role can be assigned a profile that includes other profiles.
-
In the root role, at label
ADMIN_LOW, invoke the Solaris Management Console action from the Application Manager.See "To Initialize the SMC Server" if you are unsure of how to start the SMC server.
-
Select the appropriate toolbox.
See "To Select a Toolbox of the Appropriate Scope" for assistance.
-
Click Trusted Solaris Configuration, then double-click Users.
-
Enter the role password at the prompt.
-
Double-click Administrativ... (Administrative Roles).
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Choose Add Administrative Role from the Action menu.
The Add Administrative Role wizard enables you to enter all values that are required for a role to work well. Values that you are not prompted to enter will get the default. If you want to view or modify all fields of a role, double-click the role after creating it.
-
Create the secadmin role to be the security administrator. Use the following table when creating the role.
The secadmin password, and all passwords, should be one that is not easy to guess, thus reducing the chance of an attacker gaining unauthorized access by attempting to guess passwords.
Note -For all administrative roles make the account Always Available, and do not set password expiration dates.
Table 3-2 secadmin Values in Add Role DialogTab
Role Field
(Recommended) Value
Role Name
Role name
secadmin
Full Name
Security Administrator
Description
No proprietary info here.
Role ID Number
>=100
Role shell
Administrator's Bourne (profile shell)
Create a role mailing list
checked
Password
Password and confirm
Assign a password of at least 6 alphanumeric characters.
Rights
Available and Granted
Rights Security
Home Directory
Server
home directory server
Path
/mount_path
Assign Users
Add and Delete
This will be automatically filled in when you assign a role to a user.
-
After creating the role, select it and double-click it to modify it using information from the following table as a guide.
Table 3-3 secadmin Values in Properties/Modify DialogTab
Role Field
(Recommended) Value
Password
Set password by Type in or Choose from list
(Set in Table 3-2.)
Update password by Choose from list or Type in
Group
Available Groups
Trusted Solaris Attributes
Minimum Label: Edit
Default value is correct.
Clearance: Edit
Default value is correct.
View: External or Internal
The default value is External.
Label: Show or Hide
If your site is a no-label site, choose Hide.
Lock account ...
Default value, No, is correct.
Audit
Excluded and Included
Set flags per site security policy
-
Using the preceding tables as a guide, create the following roles with unique IDs:
Role Name
Granted Rights
admin
System Administrator
primaryadmin
Primary Administrator
oper
Operator
 Caution -
Caution - You must create the administrative roles before you create the users, since you will assign a role to each user.
-
Return to the procedure and chapter you are working from.
How to Create Users to Assume Roles
The install team in the root role creates users to assume the roles secadmin, admin, and primaryadmin. Where site security policy permits, the team can choose to create one user who can assume more than one administrative role.
Prerequisite: Administrative roles must be created before creating users who will assume those roles.
To Create a User
-
In the root role, at label
ADMIN_LOW, invoke the Solaris Management Console action from the Application Manager.See "To Initialize the SMC Server" if you are unsure of how to start the SMC server.
-
Select the appropriate toolbox.
See "To Select a Toolbox of the Appropriate Scope" for assistance.
-
Click Trusted Solaris Configuration, then double-click Users.
-
Enter the role password at the prompt.
-
Double-click User Accounts.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Choose Add User > Use Wizard from the Action menu.
 Caution -
Caution - Role and user IDs come from the same pool of IDs. Do not use existing names or IDs for the users you add.
-
Begin to create a user who can assume the secadmin role and use Table 3-4 to fill out the fields.
The Add User > Use Wizard dialog boxes create most aspects of a user.
-
After creating the user, double-click the created user to modify some user properties.
Use Table 3-5 as a guide.
-
Read the (Recommended) Values columns for guidance.
Parentheses enclose suggestions. Requirements or defaults are not enclosed in parentheses.
Note -When the install team chooses a password, the team must select one that is not easy to guess, thus reducing the chance of an attacker gaining unauthorized access by attempting to guess passwords.
Table 3-4 User Values in Add User DialogTab
User Field
(Recommended) Value
User Name
User name
Full name
Description
No proprietary info here.
User ID number
(1001 or higher)
Password
Set password by Type in or Choose from list
Assign a password of at least 6 alphanumeric characters.
Confirm
Group
Primary group
Staff
Home directory
Server
home directory server
Path
Mail
Server
Path
For the user who can assume the secadmin role, select the Always Available for Account Availability under General, below. Choose an appropriate account availability for other users.
Table 3-5 User Values in Properties/Modify DialogTab
User Field
(Recommended) Value
General
Shell
Account Availability
Always Available
Password
Set password by Type in or Choose from list
(Set in Table 3-4.)
Update password by Choose from list or Type in
Group
Additional Groups
Roles
Available Roles and Assigned Roles
secadmin
Trusted Solaris Attributes
Minimum Label: Edit
Default value is correct.
Clearance: Edit
Default value is correct.
View: External or Internal
Label: Show or Hide
If your site is a no-label site, choose Hide.
Account Usage
Idle time
Idle action
Lock account ...
No -- for user who will assume a role
Rights
Available and Granted
Audit
Excluded and Included
Set flags per site security policy
Note -Although Basic Solaris User does not appear in the Granted column, this right is assigned automatically to a user that is created using the Add User wizard. Do not assign the right explicitly.
-
Create and modify another user, one who can assume the admin role.
-
(Optional) Create and modify third and fourth users to assume the primaryadmin and oper roles, and provide them with unique IDs, and appropriate Rights.
Note -If site security permits, users can assume more than one role.
These first users should each have at least the Enable Login right -- user can enable logins after a workstation reboot.
After checking your site security policy, you may want to add the Convenient Authorizations right -- user can allocate devices, enable logins, print PostScript files, print without labels, remotely log in, and shut down the workstation.
-
Return to the procedure and chapter you are working from.
Note -
Setting up users is a two-role, trusted procedure. See Table 1-1 for the security defaults that the security administrator can set. Once the security defaults are set, the system administrator can set up user accounts.
In a multilabel environment, users are set up with a useful file, Failed Cross Reference Format. See "Managing Initialization Files" in Trusted Solaris Administrator's Procedures for further discussion.
See "Using the SMC User Manager to Manage User and Role Accounts and Profiles" in Trusted Solaris Administrator's Procedures for details on setting up users and user files.
How to Verify that Users and Roles Work
Being able to modify a user's details in User Accounts confirms that the administrative roles secadmin and admin are working correctly.
To Verify that the Roles secadmin and admin Work
-
For each role, log in as a user who can assume the role and assume it.
-
In the role workspace, open the Solaris Management Console, select the Trusted Solaris Management Console with the appropriate scope for your site, and navigate to User Accounts.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click a user.
-
The admin role should be able to modify fields under the tabs General, Home Directory, and Group.
-
The secadmin role should be able to modify fields under all tabs.
-
To Verify that the Role primaryadmin Works
-
Log in as a user who can assume the primaryadmin role and assume it.
-
In the role workspace, open the Solaris Management Console, select the Trusted Solaris Management Console with the appropriate scope for your site, and navigate to Rights.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Create a new right by choosing Add Right from the Action menu.
-
Save the new right, then delete it before continuing.
-
Return to the procedure and chapter you are working from.
How to Delete a Local User
When a user is deleted from the system, the administrator must ensure that the user's home directory and any objects owned by that user are also deleted. As an alternative to deleting objects owned by the user, the administrator may change the ownership of these objects to another user who is defined on the system.
The administrator must also ensure that all batch jobs still to run that are associated with the deleted user are also deleted. The administrator must ensure that there are no objects or processes belonging to a deleted user that remain on the system.
Note -
The tsolconvert utility requires the root role to be available. Do not delete the install user until you have completed all the steps required on a Trusted Solaris 8 system. See "How to Save and Restore Trusted Solaris Databases" for more information on converting Trusted Solaris 7 to Trusted Solaris 8 databases.
To Delete the install User
-
In the admin role, label
ADMIN_LOW, in the Solaris Management Console, choose the this_host: Scope=Files, Policy=TSOL, and then select User Accounts.The user "install" is defined locally.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
Click the user to be deleted and click the Delete button.
For the user install, you do not have mail files to delete. Other local users may have home directories and mail files to delete.
How to Modify a Role's Rights
When setting up a network or custom JumpStart install, some required commands may not be available to the role because they are in a path that is not assigned to the role. To add commands, programs, or scripts to the role's rights, the security administrator must modify the role's rights.
To Add a Command to a Role's Rights
-
Log in as a user who can assume the role secadmin and assume it.
-
In the secadmin role, at label
ADMIN_LOW, invoke the Solaris Management Console from the Application Manager. -
Click the appropriate toolbox under Trusted Solaris Management Console.
-
Choose this_host: Scope=Files, Policy=TSOL if you are adding a command for a locally-defined role, or are not using a name service.
-
Choose name_server: Scope=name_service, Policy=TSOL if you are adding a command for a role defined on the network, such as for the admin role when setting up network install.
-
-
In the Navigation pane, click Trusted Solaris Configuration, then Users, then double-click Rights. Enter the role password when prompted.
Note -If toolbox icons display as red stop signs, the toolboxes will not load. To load them, do Step 4.
-
In the View pane, scroll to the Custom Rolename Role and double-click.
-
Follow the online help for assistance in setting up the Custom Rolename Role right.
For a network installation example, use the Commands tab to add the add_install_client command from a non-standard directory, such as /export/ultra_install/sparc/tsol_policy/Trusted_Solaris_8/Tools to the Custom Admin Role right. The command should have all privileges.
-
Make sure that the Custom Rolename Role right is assigned to Rolename. If it is not, assign it to Rolename.
-
Navigate to Administrative Roles.
-
Double-click the Rolename role.
-
Click the Rights tab.
-
Open the rights displayed in the Granted Rights column.
If the Custom Rolename Role right is not granted, continue. If it has already been granted, click the Cancel button.
-
Add Custom Rolename Role to the role's Granted Rights.
-
Click OK to save your work.
-
-
Return to the procedure and chapter you are working from.
To Verify That a Command is Available to a Role
-
Log in as a user who can assume the role whose profile has been updated.
-
Assume the role and launch a terminal from the role's workspace.
-
Verify that the new profile is in effect in the new terminal by using the profiles(1) command.
For example, to verify that the command in the network installation example is included in the admin role's rights profile with all privileges, as admin enter the following:
$ profiles -l | grep setup_install_server /export/ultra_install/sparc/tsol_policy/Trusted_Solaris_8/Tools/setup_install_server: all
-
Return to the procedure and chapter you are working from.
To Remove a Command from a Role's Rights
-
As secadmin, at label
ADMIN_LOW, in the Solaris Management Console use the same toolbox that you used to add the command to the rights profile, and navigate to Rights. -
In the View pane, select the Custom Rolename Profile.
-
Follow the online help for how to remove the command from the profile.
-
Return to the procedure and chapter you are working from.
How to End a Session
Users can lock their screen or log out at the end of a session. Users authorized to shut down the workstation can halt it and reboot.
Note -
Users must log off or utilize the lockscreen functionality before leaving a workstation unattended. Otherwise a person may have access to the data of a user without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
To Lock the Screen
To Log Out
-
Right-click the workspace background and select Log out... from the Workspace Menu, or left-click the EXIT icon on the Front Panel.
-
When prompted, confirm that you want to log out.
To Reboot the Workstation
-
Right click the CDE front panel and select Shut Down from the TP (Trusted Path) menu.
The menu appears when the user or role is authorized to shut down the workstation.
-
Confirm the shutdown.
-
Enter boot at the ok prompt or b at the > prompt:
Type help for more information <#2> ok boot
Type b (boot), c (continue), or n (new command mode) > b
-
Return to the procedure and chapter you are working from.
How to Save and Restore Trusted Solaris Databases
The Trusted Solaris 8 user and profile databases are in new formats with new names. To retain the usable data from their previous versions requires an administrator, before installing Trusted Solaris 8, to run the tsolconvert utility on a Trusted Solaris 7 system, to save the output directory to a safe storage area, and then to restore the files and run a shell script on the Trusted Solaris 8 machine.
The following table shows the name or content difference between earlier releases and the Trusted Solaris 8 release.
|
Trusted Solaris Databases |
Trusted Solaris 8 Database Description |
|---|---|
|
/etc/security/tsol/tsoluser |
user_attr(4) |
|
/etc/security/tsol/tsolprof |
exec_attr(4) and prof_attr(4) |
|
/etc/security/tsol/tnidb |
Format is extended for IPv6.No conversion required. |
|
/etc/security/tsol/tnrhtp |
Format is extended for IPv6. New templates with doi and ip_label changes.See the tnrhtp(4) man page. |
|
/etc/security/tsol/tnrhdb |
Format is extended for IPv6.No conversion required. |
To Save Profile and User Attribute Information
See the README file and tsolconvert(1M) man page on the Trusted Solaris web site, http://www.sun.com/software/solaris/trustedsolaris/ts_tech_faq/ for instructions.
Backup and conversion must be completed on the Trusted Solaris 2.5.1 or Trusted Solaris 7 NIS+ master before Trusted Solaris 8 is installed.
- © 2010, Oracle Corporation and/or its affiliates
