| C H A P T E R 2 |
|
Initial ILOM Setup Procedures Using the Web Interface |
To log in to the ILOM web interface for the first time, you use the default root user account and its default password changeme.
|
To log in to the ILOM web interface for the first time using the root user account, open a web browser and do the following:
1. Type http://system_ipaddress into the web browser.
If ILOM is operating in a dual-stack network environment, the system_ipaddress can be entered using either an IPv4 or IPv6 address format.
For IPv4 - http://10.8.183.106
For IPv6 - http://[fec0:a:8:b7:214:4fff:5eca:5f7e/64]
The web interface Login page appears.
For more information about entering IP addresses in a dual-stack environment, and for diagnosing connection issues, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Concepts Guide.
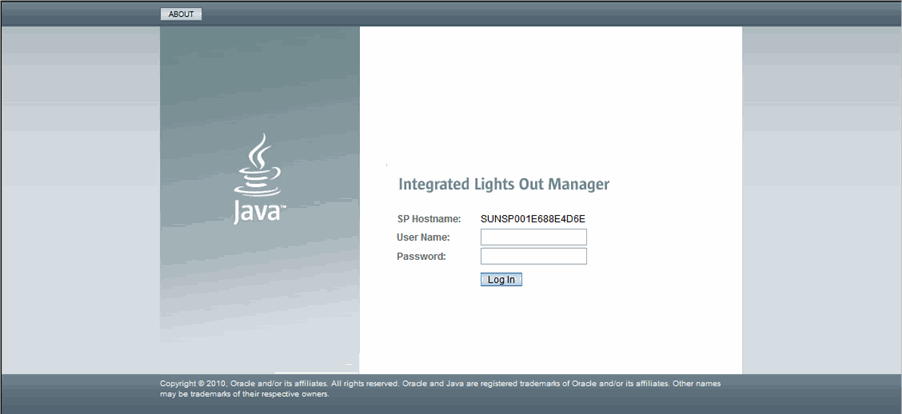
2. Type the user name and password for the root user account:
The Version page in the web interface appears.
You are now ready to configure your network settings and to access all of ILOM’s features and functionality. To learn about ILOM’s features and the procedures you can perform to access ILOM’s functions, refer to the other documents in the ILOM 3.0 Documentation Collection. You can access the ILOM 3.0 Documentation Collection at:
http://docs.sun.com/app/docs/prod/int.lights.mgr30#hic
The following web interface procedure provides instructions for configuring ILOM 3.0.12 and later versions to operate in a dual-stack IPv4 and IPv6 network environment. For a detailed description about configuring ILOM in the IPv4 and IPv6 network environment, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Concepts Guide.
If you are configuring ILOM to operate in an IPv4-only network environment, as is supported in ILOM 3.0.10 and earlier versions of ILOM, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Web Interface Procedures Guide.
By default, ILOM will attempt to obtain the IPv4 address using DHCPv4 and the IPv6 address using IPv6 stateless.
|
1. Log in to the ILOM SP web interface or the CMM ILOM web interface.
2. Navigate to the IPv4 and IPv6 network settings that are available on the Network tab.
| Note - The Network Settings page at the CMM level of the web interface does not support the dual-stack IPv4 and IPv6 properties. However, it does support IPv4 only properties. To change the IPv6 network settings for a CMM, see Configure IPv4 and IPv6 Settings Using the CLI. |
3. Verify that the network State is enabled.
4. Perform the network configuration instructions below that apply to your network environment.
|
Type the IP address for the device in the IP address text box. |
|
|
Type the subnet mask of the network on which the device resides. |
|
5. Click Save to apply the changes made.
All changes to the network settings are considered pending within the ILOM session until you click Save.
To test the IPv4 or IPv6 network configuration from ILOM, use the Network Test Tools (Ping or Ping6). For details, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Web Interface Procedures Guide.
After you log in to ILOM using the root user account, you can choose either to create a local user account or to configure a directory service. For detailed information about ILOM user accounts and directory services, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Concepts Guide.
|
Learn how to add a user account and assign user roles (privileges) |
|
|
Learn how to verify that the new user account or directory service is working properly |
|
|
1. Log in to the ILOM web interface.
2. Select User Management --> User Accounts.
The User Account Settings page appears.
3. In the Users table, click Add.
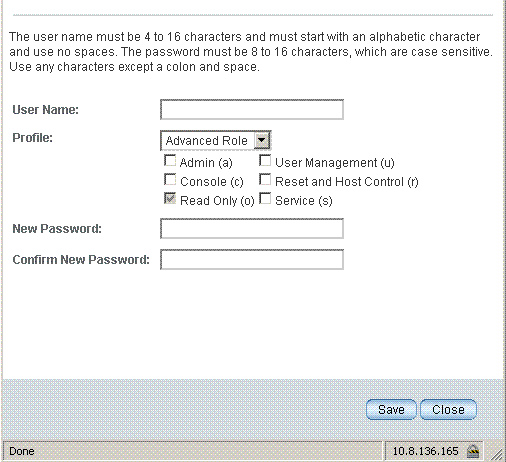
4. Complete the following information:
a. Type a user name in the User Name field.
b. Choose a profile. Options include Advanced Role for all new ILOM 3.0 installations.
c. Select the appropriate roles.
See the following table for descriptions of advanced roles for user accounts.
d. Type a password in the New Password field.
The password must be at least 8 characters and no more than 16 characters. The password is case-sensitive. Use alphabetical, numeric, and special characters for better security. You can use any character except a colon. Do not include spaces in passwords.
e. Retype the password in the Confirm New Password field to confirm the password.
f. When you are done entering the new user’s information, click Save.
The User Account Settings page is redisplayed. The new user account and associated information is listed on the User Account Settings page.
|
1. Log in to the ILOM web interface
2. Select User Management --> Active Directory.
The Active Directory page appears.
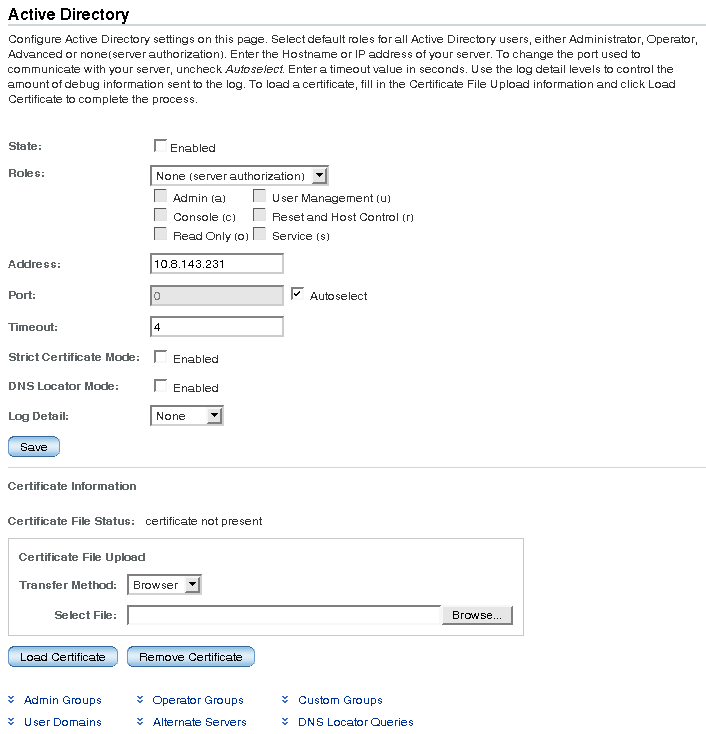
3. Configure the Active Directory settings.
See the following table for a description of the Active Directory settings.
4. Click Save for your settings to take effect.
5. View the Active Directory certificate information.
See the following table for a description of Active Directory certificate settings:
|
Click on “details” for information about issuer, subject, serial number, valid_from, valid_to, and version. |
6. Complete the Certificate File Upload section by selecting a transfer method for uploading the certificate file and the requested parameters.
| Note - This section is required only if Strict Certificate Mode is used. |
The following table describes the required parameters for each transfer method:
7. Click the Load Certificate button or Remove Certificate button.
8. If a certificate is loaded, the following read-only details appear if you selected “certificate present (details)”:
9. At the bottom of the Active Directory page, click the radio button next to the configuration option you want to configure:
10. Enter the required data in the tables.
The Admin Groups, Operator Groups, and Custom Groups tables contain the names of the Microsoft Active Directory groups in the Distinguished Name (DN) format, Simple Name format, or NT-Style Name. Custom Groups require the configuration of user roles to have Advanced Roles or Administrator/Operator privileges to perform various tasks.
User Domains are the authentication domains used to authenticate a user. When the user logs in, the name used is formatted in the specific domain name format template that appears in the cell. <USERNAME> will be replaced by the user’s login name during authentication. Either the principle or Distinguished Name format is supported. User authentication is attempted based on the user name that is entered and the configured user domains.
The Alternate Servers table provides redundancy for authentication. If a certificate is not supplied, a top-level primary certificate is used. The alternate servers have the same rules and requirements as the top-level certificate mode. Each server has its own certificate status, and its own certificate command to retrieve the certificate if it is needed.
The DNS Locator Queries table is used to query DNS servers to learn about the hosts to use for authentication. The DNS Locator queries are only used when DNS Locator is enabled and DNS is configured and functioning.
In the following tables, default data shows the expected format of the Active Directory data.
The name listed in entry 1 uses the Distinguished Name format.
The name listed in entry 1 uses the Distinguished Name format.
The name listed in entry 1 uses the Simple Name format.
|
Admin, User Management, Console, Reset and Host Control, Read Only (aucro) |
The domain listed in entry 1 shows the principle format that is used in the first attempt to authenticate the user. Entry 2 shows the complete Distinguished Name, which Active Directory would use if the attempt to authenticate with the first entry failed.
| Note - In the example below, <USERNAME> represents a user’s login name. During authentication, the user’s login name replaces <USERNAME>. |
The entries below provide redundancy for authentication.
The DNS Locator service query identifies the named DNS service. The port ID is generally part of the record, but it can be overridden by using the format <PORT:636>. Also, named services specific for the domain being authenticated can be specified by using the <DOMAIN> substitution marker.
11. Click Save for your changes to take effect.
|
Follow these steps to configure the LDAP server. Refer to your LDAP documentation for detailed instructions.
1. Ensure that all users authenticating to ILOM have passwords stored in "crypt" format or the GNU extension to crypt, commonly referred to as "MD5 crypt."
userPassword: {CRYPT}ajCa2He4PJhNo
userPassword: {CRYPT}$1$pzKng1$du1Bf0NWBjh9t3FbUgf46.
ILOM only supports LDAP authentication for passwords stored in these two variations of the crypt format.
2. Add object classes posixAccount and shadowAccount, and populate the required property values for this schema (RFC 2307).
3. Configure the LDAP server to enable LDAP server access to ILOM user accounts.
Either enable your LDAP server to accept anonymous binds, or create a proxy user on your LDAP server that has read-only access to all user accounts that will authenticate through ILOM.
|
1. Log in to the ILOM web interface.
2. Select User Management --> LDAP.
The LDAP Settings page appears.
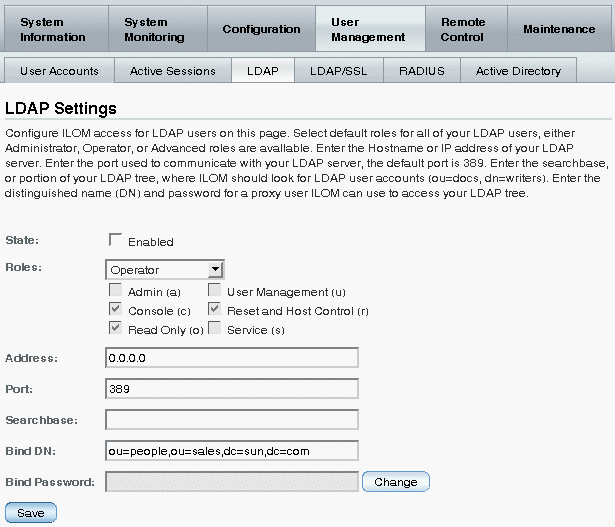
3. Enter the following values:
4. Click Save for your changes to take effect.
5. To verify that LDAP authentication works, log in to ILOM using an LDAP user name and password.
| Note - ILOM searches local users before LDAP users. If an LDAP user name exists as a local user, ILOM uses the local account for authentication. |
|
LDAP/SSL offers enhanced security to LDAP users by way of Secure Socket Layer (SSL) technology. Certificates are optional if Strict Certificate Mode is used.
Follow these steps to configure ILOM for LDAP/SSL:
1. Log in to the ILOM web interface.
2. Select User Management --> LDAP/SSL.
The LDAP/SSL page appears, displaying the configuration settings and the LDAP/SSL tables.
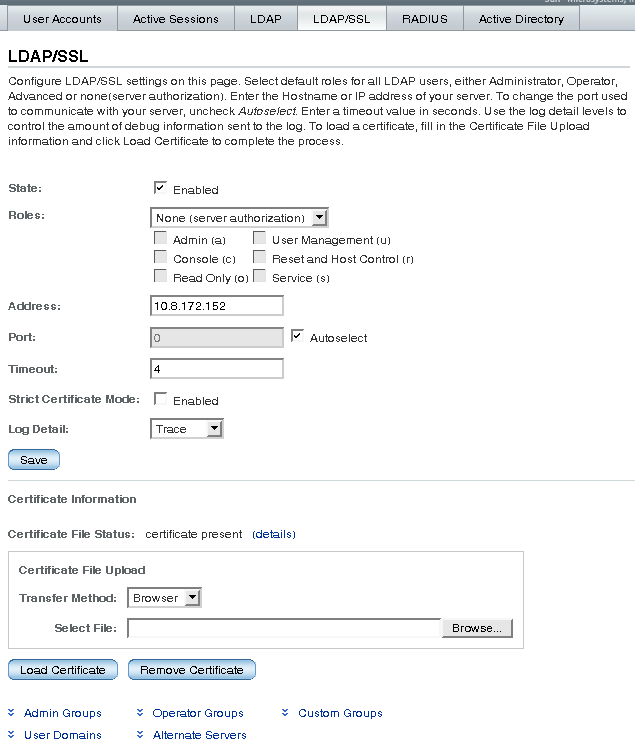
3. Configure the LDAP/SSL settings.
See the following table for a description of the LDAP/SSL settings.
4. Click Save for your settings to take effect.
5. View the LDAP/SSL certificate information in the middle section of the LDAP/SSL page.
See the following table for a description of LDAP/SSL certificate settings.
|
Click on “details” for information about issuer, subject, serial number, valid_from, valid_to, and version. |
6. Complete the Certificate File Upload section by selecting a transfer method for uploading the certificate file and the required parameters.
| Note - This section is required only if Strict Certificate Mode is used. |
The following table describes the required parameters for each transfer method.
7. Click the Load Certificate button or Remove Certificate button.
8. If a certificate is loaded, the following read-only details will appear if you selected “certificate present (details)”:
|
Follow these steps to modify information for Admin Groups, Operator Groups, Custom Groups, User Domains, or Alternate Servers:
1. Log in to the ILOM web interface.
2. Select User Management --> LDAP/SSL.
3. At the bottom of the LDAP/SSL page, select the links next to the type of information you want to edit:
4. Select the radio button next to the individual table you want to edit, then click Edit.
The appropriate page appears: Edit LDAP/SSL Admin Groups page, Edit LDAP/SSL Operator Groups page, Edit LDAP/SSL Custom Groups page, Edit LDAP/SSL User Domains page, or Edit LDAP/SSL Alternate Servers page.
5. In each Edit page, edit the information you want to modify.
See the procedure Configure ILOM for Active Directory for examples of the information you can add or edit in the LDAP/SSL tables. Information in the Active Directory tables is similar to LDAP/SSL tables.
For example, in the User Domains table, enter the information in the Name field as text. Use the <USERNAME> substitution marker to hold a place for the user’s name.
domain=uid=<USERNAME>,OU=people,DC=sales,DC=east,DC=oracle,
DC=com
You would be authenticated to ILOM with the supplied name.
6. Click Save for your changes to take effect.
|
1. Log in to the ILOM web interface.
2. Select User Management --> RADIUS.
The RADIUS Settings page appears.
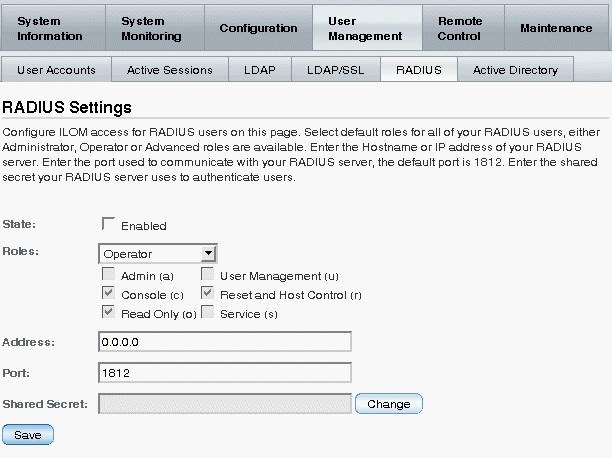
3. Complete the RADIUS settings.
4. Click Save for your settings to take effect.
|
To log in to the ILOM web interface using a non-root user account, open a web browser and do the following:
1. Type http://system_ipaddress into the web browser.
If ILOM is operating in a dual-stack network environment, the system_ipaddress can be entered using either an IPv4 or IPv6 address format.
For IPv4 - http://10.8.183.106
For IPv6 - http://[fec0:a:8:b7:214:4fff:5eca:5f7e/64]
The web interface Login page appears.
For more information about entering IP addresses in a dual-stack environment, and for diagnosing connection issues, refer to the Oracle Integrated Lights Out Manager (ILOM) 3.0 Concepts Guide.
2. Type the user name and password for the user account:
User Name: <assigned_username>
The ILOM web interface appears, displaying the Version page.
|
 Click the Log Out button in the ILOM web interface.
Click the Log Out button in the ILOM web interface.
The Log Out button is located in the top right corner of the ILOM web interface. Do not use the Log Out button on your web browser to exit ILOM.
You can now continue to customize your ILOM configuration for your system and data center environment. Before you configure ILOM for your environment, refer to the Oracle Integrated Lights Out Manager 3.0 Concepts Guide for an overview of the new ILOM 3.0 features and functionality. Knowing how the new ILOM features will affect your environment will help you configure ILOM settings so that you can access all of ILOM’s capabilities in your system and data center.
Also refer to the Oracle ILOM 3.0 Procedures Guides for descriptions of how to perform ILOM tasks using a specific user interface and to your platform ILOM Supplement or platform Administration guide for platform-specific configuration instructions.
The ILOM 3.0 Documentation Collection can be found at:
http://docs.sun.com/app/docs/prod/int.lights.mgr30#hic
Copyright © 2010, Oracle and/or its affiliates. All rights reserved.