Mutual Authentication
With mutual authentication, the server and the client authenticate one another. There are two types of mutual authentication:
-
Certificate-based mutual authentication (see Figure 30–4)
-
User name- and password-based mutual authentication (see Figure 30–5)
-
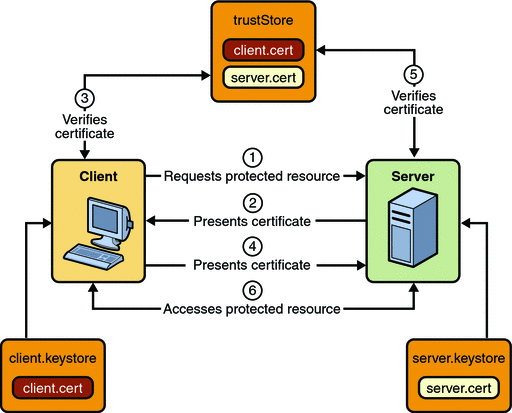
A client requests access to a protected resource.
-
The web server presents its certificate to the client.
-
The client verifies the server’s certificate.
-
If successful, the client sends its certificate to the server.
-
The server verifies the client’s credentials.
-
If successful, the server grants access to the protected resource requested by the client.
When using certificate-based mutual authentication, the following actions occur:
Figure 30–4 shows what occurs during certificate-based mutual authentication.
Figure 30–4 Certificate-Based Mutual Authentication
-
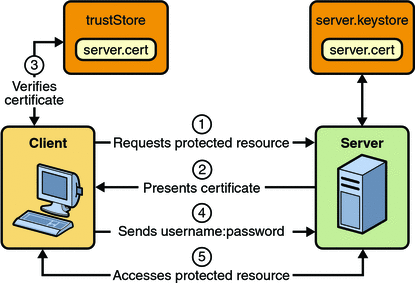
A client requests access to a protected resource.
-
The web server presents its certificate to the client.
-
The client verifies the server’s certificate.
-
If successful, the client sends its user name and password to the server, which verifies the client’s credentials.
-
If the verification is successful, the server grants access to the protected resource requested by the client.
In user name- and password-based mutual authentication, the following actions occur:
Figure 30–5 shows what occurs during user name- and password-based mutual authentication.
Figure 30–5 User Name- and Password-Based Mutual Authentication
- © 2010, Oracle Corporation and/or its affiliates
