External Policy Check Integration
The external policy check integration allows an external policy product, such as SAP BusinessObjects Access Control, to perform a risk analysis when a user account is created or updated. Waveset gathers the relevant data and submits it to SAP Access Control. If risk analysis or SoD violations are returned, then the Waveset administrator determines whether to approve the violations or to reject the request entirely. If the administrator wants to change the SAP role assignments in a compliance violation, the request must be rejected and submitted again.
The following diagram illustrates the interaction between Waveset and SAP Access Control in this integration.
Figure 6–1 External Policy Check Integration
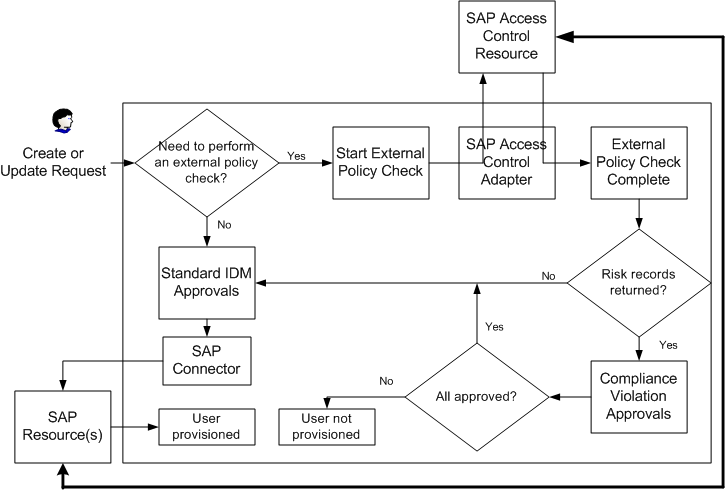
Waveset uses web services to communicate with the SAP Access Control resource. When Waveset receives a request to create or update a user, the Create User or Update User workflow launches the Check External Policy workflow.
The user view is queried for an accounts[Lighthouse].properties.externalPolicy[ResourceName] object. Each ResourceName in the list specifies a resource on which to execute the external policy check. If objects for a resource do not exist, control is returned to the Create User or Update User workflow, respectively.
If objects exist, the Check External Policy workflow starts a deferred task that executes the external policy check on each resource. For SAP Access Control, this deferred task executes the risk analysis web service. While the risk analysis is executing, the workflow generates a temporary work item that suspends the create or update request until the external policy check is complete. The task runs synchronously, therefore the task monitors for the completion of the policy check and returns the risk analysis results to the workflow.
If the SAP Access Control resource returns one or more violations, the policy check creates a compliance violation work item. The Compliance Violation Owner rule determines who the owner of the work item and therefore who it is assigned to. By default, the rule assigns the work item to the manager defined in Waveset. If the rule cannot determine who to assign the rule to, it assigns it to the requestor.
Once the compliance violation has been assigned an owner, the owner can process the work item in the following ways:
-
Approve the policy check. In this case, any violations are ignored, and Waveset continues to provision the user.
-
Reject the request. The account is not provisioned on the SAP resource.
-
If a previously-provisioned user has had a compliance violation check, any roles added in the future will generate compliance violation work items, regardless if the items would cause a compliance violation. If the request is rejected, only the requested roles will be rejected. The previous roles and provisioned users remain intact. This is because Waveset does not make any decisions or assumptions regarding the external policy service.
The $WSHOME/sample/rules/SAPAccessControlRules.xml file defines the SAPAccessControl rule library, which is used in the SAP Access Control and External SAP Access Control user forms and through a FormRef in the SAP Connector User Form. You may need to customize the following rules:
-
Aggregate Roles
-
Compliance Violation Owner
-
Process Policy Result
-
Risk Analysis Status
If you change the name of these rules, you must modify the prototype XML in the SAP Access Control adapter to match the renamed rule.
Note –
The SAP Access Control Check Status rule is not used in an external policy check integration.
The forms used in this integration are defined in the SAPAccessControlUserForm.xml and the SAPAccessControlCompViolForm.xml files. The SAP Access Control user form aggregates the data required for performing a risk analysis. This data is placed in the accounts[Lighthouse].properties.externalPolicies[ResourceName] property in the User view. Also refer to the Javadocs for the classes in the com.sun.idm.ws package for detailed information about the SAP Access Control web services.
The SAP Access Control Compliance Violation Form controls the display of the compliance violation details on the Compliance Violations page. If you change the name of this form, you must modify the prototype XML in the SAP Access Control adapter to match the renamed form.
An SAP connector handles all provisioning requests. You must create an SAP connector for each SAP Access Control application name (SAP system) that SAP Access Control manages. SAP Access Control performs the risk analysis for all these systems, but the SAP connector performs the provisioning. Refer to the SAP connector documentation for detailed information.
Note –
You cannot use an SAP adapter to provision. If you have an existing SAP adapter, you must migrate to the adapter to an SAP connector. Refer to Chapter 57, Identity Connectors Overview, in Oracle Waveset 8.1.1 Resources Reference for information about migrating.
For information on this connector, and the Identity Connector project, refer to the https://identityconnectors.dev.java.net website.
The SAP Access Control AuditLog Report can be used to return information that is contained in the SAP Access Control audit log. This report is not installed by default, but is provided in the $WSHOME/sample/sapreports.xml file.
Supported Web Services
The external policy check integration supports the following web services for Risk Analysis and Remediation (RAR):
-
SAPGRC_AC_IDM_SUBMITREQUEST
-
SAPGRC_AC_IDM_RISKANALYSIS
In addition, the SAP Access Control AuditLog Report uses the SAPGRC_AC_IDM_AUDITTRAIL web service.
Implementing a External Policy Check Integration
Use the following guidelines to implement the external policy check integration in an environment in which you have not integrated Access Enforcer 5.2 or earlier. Before beginning this procedure, you must set up SAP Access Control as described in the “Access Control and Identity Manager” Integration chapter in the SAP GRC Access Control Configuring SAP with Release 5.3 guide, which is available from SAP. If you have previously integrated Access Enforcer, see “Migrating from Access Enforcer Version 5.1 or 5.2” in this document.
Note –
Disable the autoprovisioning feature within SAP Access Control for the external policy check integration. Otherwise, the user will be provisioned by Access Control, and not by Waveset. If you want autoprovisioning, then implement the external resource integration.
-
Create an SAP Access Control adapter.
-
Create an SAP connector. Be sure to configure the following parameters.
-
Select the Configure Policy Resource check box.
-
Select the SAP Access Control resource from the Policy Resource menu.
-
Select the SAP Access Control application associated with this connector from the Instance ID menu.
Repeat this step for each SAP Access Control application.
-
-
Copy the following files and make any required modifications. Be sure to save the original files.
-
$WSHOME/sample/rules/SAPAccessControlRules.xml
-
$WSHOME/sample/forms/SAPAccessControlUserForm.xml
-
$WSHOME/sample/forms/SAPAccessControlCompViolForm.xml
Then import the modified files.
-
-
The SAP connector glue code contains a sample SAP Connector User Form (SAPUserForm.xml). This file contains commented code that needs to be enabled. Delete the comment marks around the Include statement near the top of the file. Then delete the comment marks around the Field that contains the FormRef to the SAP Access Control User Form. Then import this file.
-
Configure the User Deferred Task Scanner to run periodically. The default interval is 1 hour. To obtain the risk analysis results as quickly as possible, the interval for the deferred task should be set as low as possible.
Managing Compliance Violations
View compliance violations from the Work Items area of the administrator interface. Selecting the Compliance Violations tab in the Work Items area lists all the violations requiring approval or rejection for the current administrator. From this page, you can also list compliance violations for all of your direct reports and for specified users for which you have direct or indirect control.
The following are possible responses to a compliance violation:
-
Approve. Accepts the risk displayed in the compliance violation. This will probably generate a risk violation on the external system.
-
Reject. Does not accept the risk. The provisioning operation ends.
-
Refresh. Updates the list of compliance violations.
-
Forward. Enables you to specify another recipient to review the compliance violation.
Click the Request link to view detailed information about the compliance violation. The risk code, SAP application, description, severity level, violation count, and violation details are displayed. Refer to the SAP Access Control documentation for more information about these fields.
- © 2010, Oracle Corporation and/or its affiliates
